Module 9 Configuring ISA Server for the Enterprise







































































- Slides: 187

Module 9: Configuring ISA Server for the Enterprise

Overview n Introducing ISA Server Enterprise Edition n Installing ISA Server in the Enterprise n Using Enterprise Policies and Array Policies n Managing Network Connections n Scaling ISA Server n Extending and Automating ISA Server Functionality

n Microsoft® Internet Security and Acceleration (ISA) Server 2000 provides many features to support an enterprise wide deployment. Some of these features are available in only the Enterprise Edition of ISA Server. The security, caching, management, performance, and extensibility capabilities of ISA Server are the same in both the Standard Edition and the Enterprise Edition. The Standard Edition, however, is limited to a stand alone server, a local policy only, and computers with up to four processors. For large scale deployments, server array support, multi level policy, and computers with more than four processors, you must use the ISA Server Enterprise Edition.

n After completing this module, you will be able to: l Describe the use of ISA Server in an enterprise environment. l Install ISA Server in an enterprise environment. l Use enterprise and array policies. l Scale ISA Server. l Manage network connections. l Extend automate ISA Server functionality.

u. Introducing ISA Server Enterprise Edition n Benefits of ISA Server Enterprise Edition n Using ISA Server Enterprise Edition

n There are many benefits for an organization to deploy ISA Server Enterprise Edition in an enterprise environment. When you deploy ISA Server Enterprise Edition, you must select an installation configuration and a policy configuration.

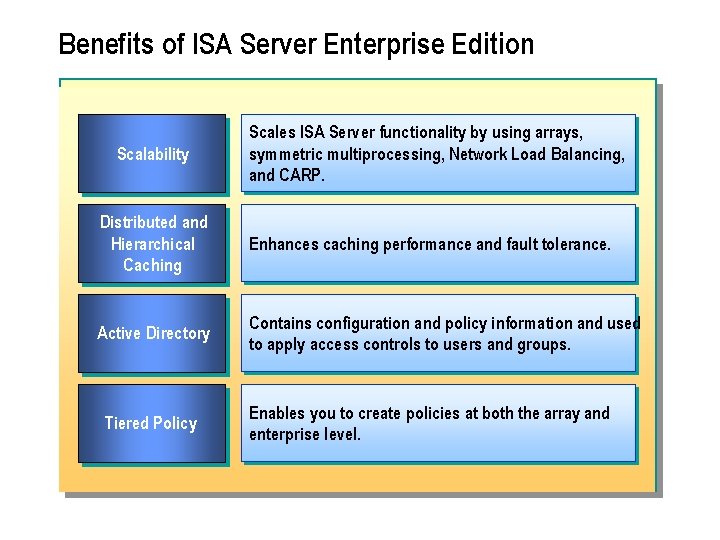
Benefits of ISA Server Enterprise Edition Scalability Scales ISA Server functionality by using arrays, symmetric multiprocessing, Network Load Balancing, and CARP. Distributed and Hierarchical Caching Enhances caching performance and fault tolerance. Active Directory Contains configuration and policy information and used to apply access controls to users and groups. Tiered Policy Enables you to create policies at both the array and enterprise level.

n ISA Server Enterprise Edition offers several benefits to organizations that want fast, secure, and manageable Internet connectivity in an enterprise environment.

Scalability n ISA Server Enterprise Edition provides scalability by using arrays, enhanced symmetric multiprocessing support, the Network Load Balancing feature of Microsoft Windows® 2000 Advanced Server, and the Cache Array Routing Protocol (CARP) protocol.

Scalability: Arrays n ISA Server Enterprise Edition uses arrays to manage a group of ISA Server computers as a single, logical entity. Array installations increase performance and bandwidth savings by distributing client requests between multiple ISA Server computers. In addition, because the load is distributed across all of the servers in the array, you can achieve good performance even with moderate hardware. Arrays also provide fault tolerance. Moreover, because the array members share the same configuration, management and administration is simplified.

Scalability: Symmetric Multiprocessing n ISA Server uses Windows 2000 symmetrical multiprocessing (SMP) to improve performance on computers with multiple processors. ISA Server Enterprise Edition uses the SMP capabilities of Windows 2000 Advanced Server, which supports up to 8 processors, and Microsoft Windows 2000 Datacenter Server, which supports up to 32 processors.

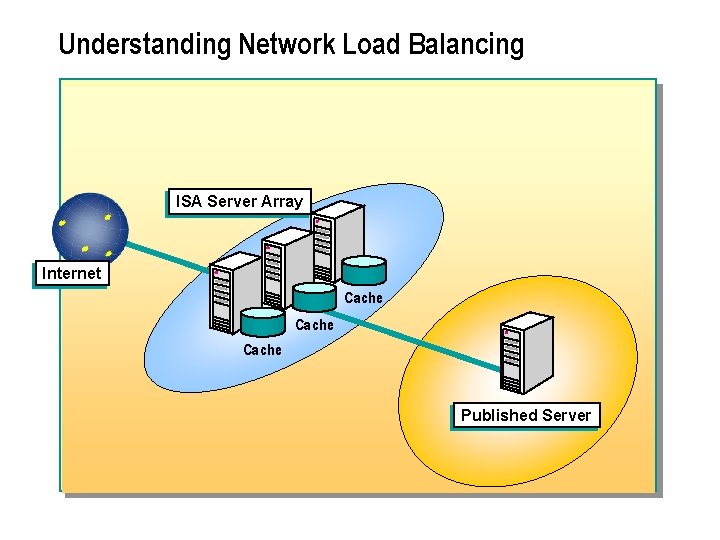
Scalability: Network Load Balancing n ISA Server Enterprise Edition efficiently uses Network Load Balancing, which is available in Windows 2000 Advanced Server and Windows 2000 Datacenter Server, to provide fault tolerance, high availability, efficiency, and performance through the clustering of multiple ISA Server computers. You can use Network Load Balancing to make multiple ISA Server computers respond to a single Internet Protocol (IP) address, which provides load balancing and fault tolerance for publishing internal resources to the Internet.

Scalability: CARP n ISA Server Enterprise Edition uses CARP to provide scaling and efficiency when deploying an array of ISA Server computers as forward and reverse caching servers. CARP eliminates the duplication of content among array members and automatically adjusts to additions or deletions of servers in the array.

Distributed and Hierarchical Caching n ISA Server Enterprise Edition uses CARP to perform distributed caching among an array of ISA Server computers to enhance the caching performance and the fault tolerance if an ISA Server computer becomes unavailable. n In addition, ISA Server supports hierarchical, or chained, caching. Chained caching is a hierarchical connection between individual ISA Server computers or arrays of ISA Server computers. Chained caching enables caching to take place closer to the users. Client requests are sent upstream through the chain of cache servers until the requested object is found. When the object is located on an upstream server, it is cached in both the upstream server's cache and the downstream server's cache. Both the Standard Edition and the Enterprise Edition support hierarchical caching.

Active Directory n ISA Server stores configuration and policy information of arrays in the Active Directory™ directory service. Active Directory provides a central point for storing and gaining access to ISA Server policies and configuration settings. In addition, both the Standard Edition and the Enterprise Edition can apply access controls by using user accounts and groups that are defined in Active Directory.

Tiered Policy n ISA Server Enterprise Edition supports atiered policy, which enables you to create access policies at both the enterprise level and the array level. You can set a centralized enterprise policy that unconditionally applies to all of the arrays in the enterprise, or you can set an enterprise policy that administrators can augment at the array level.

Using ISA Server Enterprise Edition ISA Management Action View Tree Internet Security and Acceleration Server Set Defaults… Back Up… Restore… View Refresh Export List… Properties Help Configure enterprise You can create one or more enterprise policies that can be applied to arrays. At the enterprise level, you control whether additional rules can be created at the array level. Use this taskpad to configure how the enterprise policy affects the array policy. Servers and Arrays: Array LONDON PERTH VANCOUVER Configure Enterprise Policies Welcome Description Type Array Mode Integrated Created 1/4/2001 7: 19… 1/4/2001 7: 52… 1/4/2001 7: 33… Applied Enterprise Policy 1 Configure Enterprise Set Enterprise Policy for Policy Default Settings the Selected Array Servers and Arrays Enterprise Backup Monitoring Help

n You can install ISA Server Enterprise Edition as a stand alone server or as an array member. When you install ISA Server as an array member, you can select a policy configuration that meets the needs of your organization.

Selecting an Installation Configuration n When you install ISA Server Enterprise Edition as a stand alone server, the computer does not have to belong to a Windows 2000 domain. ISA Server stores the configuration information for the stand alone server in the registry. Stand alone servers do not use array policies or enterprise policies. n When you install ISA Server as an array member, the computer must be a member of a Windows 2000 domain. ISA Server Enterprise Edition stores configuration information for arrays in Active Directory. You can apply an enterprise policy to an array, which allows you to centralize management for multiple arrays in your enterprise.

Selecting a Policy Configuration n When you set up ISA Server in an enterprise configuration, you must select a policy configuration to apply to the arrays in the domain. You can use enterprise policies, which apply a centralized policy to arrays, or you can use array policies, which apply a policy to only the ISA Server computer in one array. Each type of policy includes the following:

• Enterprise Policy. n Includes site and content rules and protocol rules. You can create one or more enterprise policies. In addition, you can configure an enterprise policy to permit an array policy to augment the enterprise policy. This configuration enables administrators at branch offices and specific departments in an organization to use enterprise policies and be able to configure rules at the array level that further restrict an access policy.

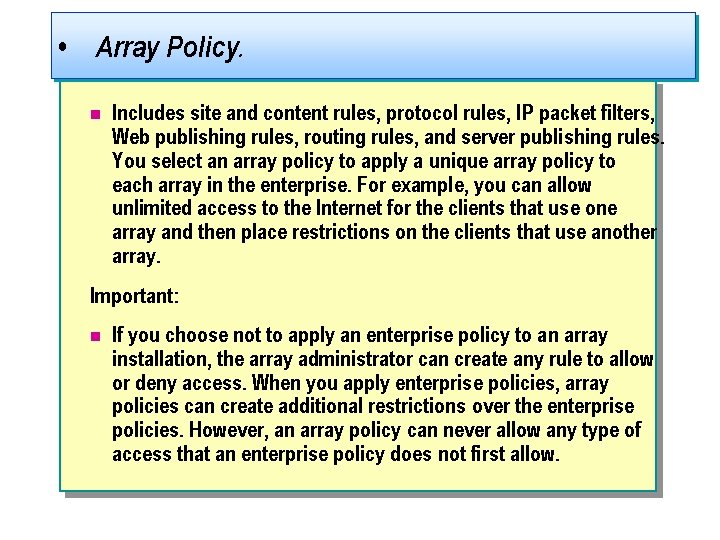
• Array Policy. n Includes site and content rules, protocol rules, IP packet filters, Web publishing rules, routing rules, and server publishing rules. You select an array policy to apply a unique array policy to each array in the enterprise. For example, you can allow unlimited access to the Internet for the clients that use one array and then place restrictions on the clients that use another array. Important: n If you choose not to apply an enterprise policy to an array installation, the array administrator can create any rule to allow or deny access. When you apply enterprise policies, array policies can create additional restrictions over the enterprise policies. However, an array policy can never allow any type of access that an enterprise policy does not first allow.

u. Installing ISA Server in the Enterprise n Installing ISA Server Schema in Active Directory n Using Arrays n Installing ISA Server in an Array n Creating and Deleting Arrays in ISA Management n Promoting a Stand Alone Server n Maintaining Enterprise Configurations

n Before you can set up ISA Server Enterprise Edition as an array member, the ISA Server schema must be installed in Active Directory. ISA Server includes an Enterprise Initialization utility that you can use to install the ISA Server schema in Active Directory. You can also promote stand alone servers to array members. When you modify an array, it is recommended that you back up the configuration information.

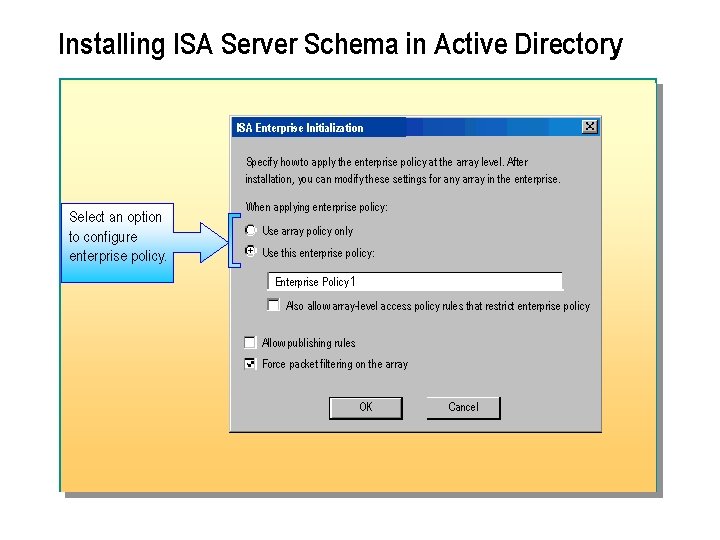
Installing ISA Server Schema in Active Directory ISA Enterprise Initialization Specify how to apply the enterprise policy at the array level. After installation, you can modify these settings for any array in the enterprise. Select an option to configure enterprise policy. When applying enterprise policy: Use array policy only Use this enterprise policy: Enterprise Policy 1 Also allow array-level access policy rules that restrict enterprise policy Allow publishing rules Force packet filtering on the array OK Cancel

n Before you can set up ISA Server as an array member, you must install the ISA Server schema in Active Directory. Installing the ISA Server schema adds new object classes and attributes to Active Directory. Caution: n Applying a schema change to Active Directory is a major operation that normally requires planning. Because Active Directory does not support deletion of schema objects, the enterprise initialization process is irreversible. For more information about schema changes to Active Directory, see Module 4, "Designing a Schema Policy, " in Course 1561 B, Designing a Microsoft Windows 2000 Directory Services Infrastructure.

Using the Enterprise Initialization Utility n ISA Server includes an Enterprise Initialization utility that you can use to install the ISA Server schema in Active Directory. After you install the ISA Server schema, all subsequent ISA Server installations to computers in the Active Directory forest can use the ISA Server schema. You do not have to install the schema again. Important: n To install the ISA Server schema in Active Directory, you must be an administrator on the local computer. In addition, you must be a member of the Enterprise. Admins group and the Schema Admins group. In addition, the domain controller that holds the schema master role for your Active Directory forest must be available. For more information about operation master roles, see Module 12, "Managing Operations Masters, " in Course 2154 A, Implementing and Administering Microsoft Windows 2000 Directory Services.

Initializing the Enterprise n To initialize the enterprise by installing the ISA Server schema: 1. At a command prompt, type pathisai 386msisaent. exe (where path is the location of the ISA Server installation files). The location can be the root folder of the ISA Server CD ROM or a shared folder on your network that contains the ISA Server files. 2. In the ISA Enterprise Initialization Tooldialog box, click Yes to acknowledge that the schema installation is not reversible.

Initializing the Enterprise (continued) 3. In the ISA Enterprise Initializationdialog box, select one of the following policy options: l Use array policy only. Allows the array administrator to create rules for allowing or denying access at the array level. ISA Server does not apply enterprise policy to the array. l Use this enterprise policy. Creates an enterprise policy with the name that you type. You can modify the policy and additional enterprise policies after you have installed ISA Server.

Initializing the Enterprise (continued) 4. If you select to use an enterprise policy, in the. ISA Enterprise Initializationdialog box, select one or more of the following options, and then click. OK twice. Note: n Because of Active Directory replication latency, there may be a delay until the schema changes are applied to all domain controllers in your organization.

Initializing the Enterprise (continued) To Do this Allow array administrators to create Select the Allow array level access array policies that further restrict rules that restrict enterprise an enterprise policy policies check box. Allow administrators to create publishing rules Select the Allow publishing rules check box. Enforce packet filtering on all arrays Ensure that the Force packet filtering on the arraycheck box is selected.

Using Arrays n Guidelines for Setting Up Arrays n Configuration Settings for Arrays n Permissions Required for Adding Arrays

n Before you set up an array, consider the following guidelines, configuration settings, and permissions required for adding arrays.

Guidelines for Setting Up Arrays n The guidelines for setting up arrays are as follows: l All of the array members must be in the same Windows 2000 domain and on the same site. l All of the array members should use the same installation mode: Cache mode, Firewall mode, or Integrated mode. l All of the array members should have the same set of extensions installed.

Configuration Settings for Arrays n Array members have the following configuration settings: l Policy configuration for arrays includes all access policy rules, publishing rules, and bandwidth rules. Similarly, the cache policies are centrally configured at the array level, and the cache policy and scheduled content download jobs apply to all computers in an array. l Alert configuration. Alerts can be configured for each server in the array or for all of the servers in the array. l Reports display information about the activity on all of the ISA Server computers in the array. The report data is stored in a database on a computer and in a directory that you specify. By default, the report data is stored on the ISA Server computer on which you configure the report jobs.

Configuration Settings for Arrays (continued) l Cache. Disk space for caching is allocated separately on each ISA Server computer according to the amount that you specify when you install or reconfigure the cache. However, all of the cache configuration properties are common for all of the servers in an array. These properties include the Hypertext Transfer Protocol (HTTP) protocol caching properties, the File Transfer Protocol (FTP) protocol caching properties, and the CARP protocol properties.

Permissions Required for Adding Arrays n By default, the members of the Domain. Admins group for the domain and the members of the Enterprise. Admins group for the Active Directory forest can create new arrays. Only the members of the Enterprise. Admins group are prompted to configure how the enterprise policies apply to the array because only the members of this group have the required permissions to administer enterprise policies. When a user who is not a member of the Enterprise Admins group creates an array, the default enterprise policy automatically applies to the array.

Installing ISA Server in an Array Start Run Setup Install ISA Server as an Array Create and Name Array Select an Enterprise Policy Setting Select Custom Policy Settings Finish

n When you install the first ISA Server computer after importing the ISA Server schema into Active Directory, the setup program provides you with additional choices that are not available before you modify the schema. After you set up the first ISA Server computer in an array, when you install additional array members, these array members automatically retrieve most of the configuration information from Active Directory.

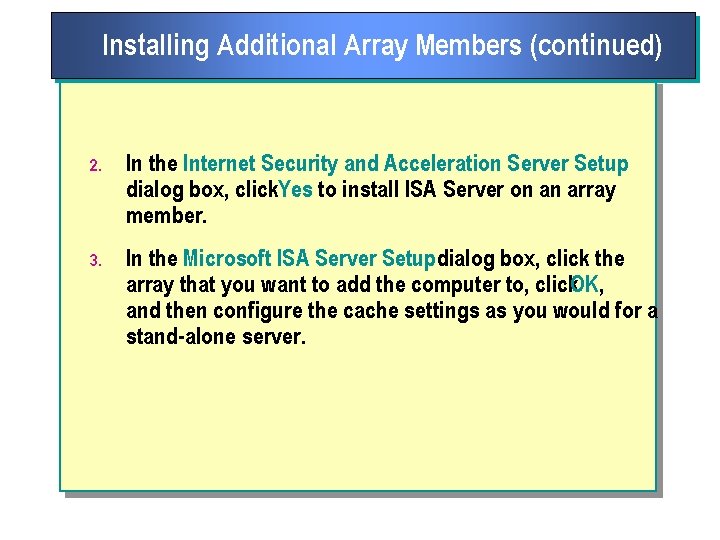
Installing the First ISA Server Computer n To install ISA Server on the first computer in an array: 1. Start the Microsoft Internet Security and Acceleration Server Enterprise Edition Setup program, and choose whether to perform a typical, custom, or full installation. 2. In the Microsoft ISA Server Setupdialog box, click. Yes to install ISA Server as an array member. 3. If the domain already contains arrays, in the. Microsoft ISA Server Setup dialog box, click. New. 4. In the New Array dialog box, type a name for the array that you are creating, and then click. OK.

Installing the First ISA Server Computer (continued) 5. In the Configure enterprise policy settingdialog box, select one of the following options: l Use default enterprise policy settings. The array will use the default enterprise policy settings. These settings are normally the policy settings that you configured when you imported the ISA Server schema. l Use custom enterprise policy settings. The array will not use the default enterprise policy settings. 6. If you chose to use a custom enterprise policy, select the appropriate policy option and settings, and then click Continue. 7. In the Microsoft. ISA Server Setup dialog box, select the installation mode, and then configure the cache settings and the Local Address Table (LAT) as you would for a stand alone server.

Installing Additional Array Members n When you install additional members of an array, the new members retrieve the existing array configuration from Active Directory. n To install additional array members: 1. Start the Microsoft Internet Security and Acceleration Server Enterprise Edition Setup program, and choose whether to perform a typical, custom, or full installation.

Installing Additional Array Members (continued) 2. In the Internet Security and Acceleration Server Setup dialog box, click. Yes to install ISA Server on an array member. 3. In the Microsoft ISA Server Setupdialog box, click the array that you want to add the computer to, click. OK, and then configure the cache settings as you would for a stand alone server.

Creating and Deleting Arrays in ISA Management n Creating New Arrays n Deleting Arrays

n You can create a new array before installing ISA Server on the first computer in the array, which allows you to configure the array before you install ISA Server on the first computer in the array. When you create a new array, you can create a new configuration or you can copy a configuration from another array. After you have created an array, computers can join the array when you install ISA Server or when you promote a stand alone server to an array member. n Important: You must be a member of the Domain. Admins group or the Enterprise. Admins group to create an array. You must be a member of the Enterprise. Admins group to configure how the enterprise policies apply.

Creating New Arrays n To create a new array: 1. In ISA Management, in the console tree, right click Servers and Arrays, point to New, and then click Array. 2. In the New Array Wizard, type a name for the array, and then click. Next. 3. On the Domain Name page, select the site and domain in which to create the new array, and then click. Next.

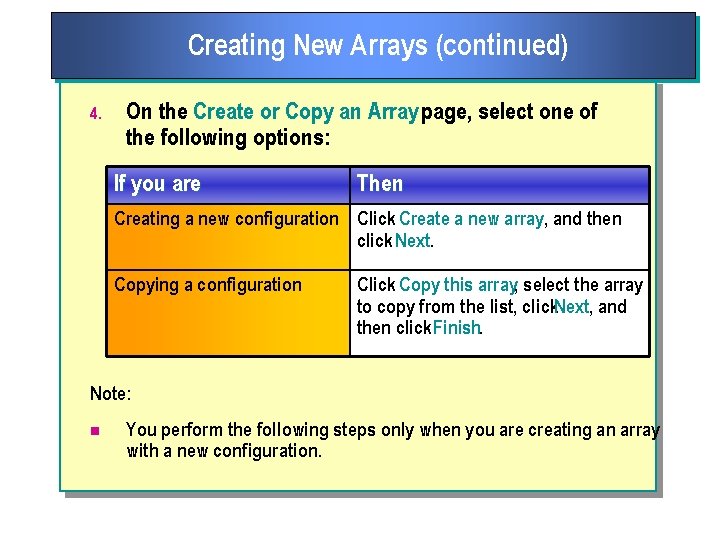
Creating New Arrays (continued) 4. On the Create or Copy an Array page, select one of the following options: If you are Then Creating a new configuration Click Create a new array, and then click Next. Copying a configuration Click Copy this array, select the array to copy from the list, click. Next, and then click Finish. Note: n You perform the following steps only when you are creating an array with a new configuration.

Creating New Arrays (continued) 5. On the Enterprise policy settingspage, select one of the following options, and then click. Next: l Do not use enterprise policy. l Use default enterprise policy settings. l Use custom enterprise policy settings. Use this option to specify an enterprise policy. You can also select the Allow array policy check box.

Creating New Arrays (continued) 6. On the Array type page, select one of the following options, and then click. Next: l Cache only l Firewall only l Integrated

Creating New Arrays (continued) 7. 8. On the Array Global Policy Optionspage, select one or both of the following options, and then click Next: l Allow publishing rules to be created on the array l Force packet filtering on the array On the Completing the New Array Wizardpage, review your choices, and then click. Finish.

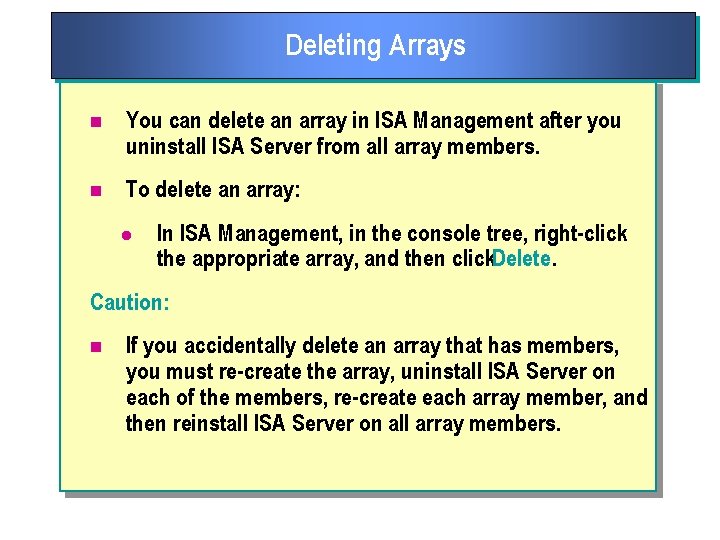
Deleting Arrays n You can delete an array in ISA Management after you uninstall ISA Server from all array members. n To delete an array: l In ISA Management, in the console tree, right click the appropriate array, and then click. Delete. Caution: n If you accidentally delete an array that has members, you must re create the array, uninstall ISA Server on each of the members, re create each array member, and then reinstall ISA Server on all array members.

Promoting a Stand Alone Server n Migrating Policy Settings n Promoting a Stand Alone Server

n After you initialize the enterprise, you can promote stand alone servers to array members. After promoting a stand alone server to an array, by default, the name of the array is the same as the name of the server. You can rename the array in ISA Management. Note: n You can promote stand alone servers that belong to a Windows 2000 domain only. You cannot reverse the promotion without uninstalling ISA Server.

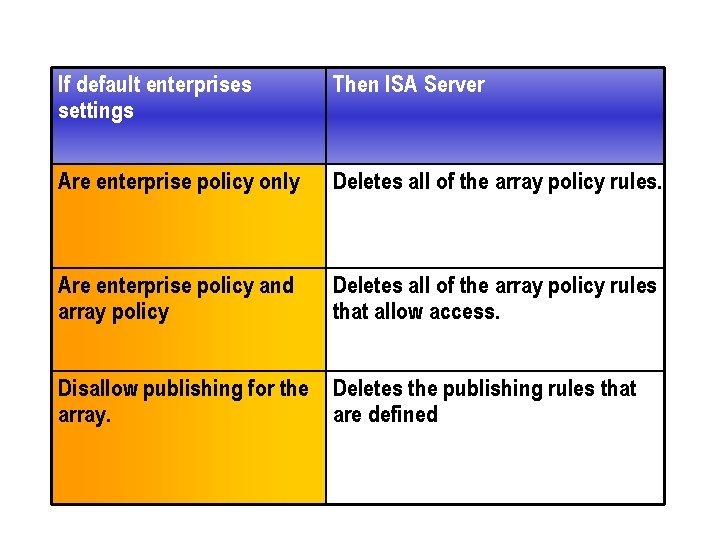
Migrating Policy Settings n When you promote a stand alone server to an array, the new array adopts the default enterprise policy settings or another enterprise policy that you select. Because array policies cannot be more permissive than enterprise policies, depending on the default enterprise policy settings, ISA Server may delete some of the existing array policy rules as follows.

If default enterprises settings Then ISA Server Are enterprise policy only Deletes all of the array policy rules. Are enterprise policy and array policy Deletes all of the array policy rules that allow access. Disallow publishing for the Deletes the publishing rules that array. are defined

Promoting a Stand Alone Server n To promote a stand alone server: 1. In ISA Management, in the console tree, right click the server, and then click. Promote. 2. Click Yes to verify that you want the ISA Server to become an array member. 3. If you are not a member of the Enterprise. Admins group, click. Yes to confirm that the default enterprise policy will be applied to the array. or n If you are a member of the Enterprise. Admins group, in the Set Global Policy dialog box, select the appropriate policy options and settings, and then click. OK.

Maintaining Enterprise Configurations ISA Management Action View Tree Internet Security and Acceleration Server Set Defaults… Back Up… Restore… View Refresh Export List… Properties Help Configure enterprise You can create one or more enterprise policies that can be applied to arrays. At the enterprise level, you control whether additional rules can be created at the array level. Use this taskpad to configure how the enterprise policy affects the array policy. Servers and Arrays: Array LONDON PERTH VANCOUVER Description Backup Type. Configuration Mode Enterprise Store Array Integratedin backup. Array configuration this Created 1/4/2001 7: 19… 1/4/2001 7: 52… 1/4/2001 7: 33… location: Applied Enterprise Policy 1 Browse… Comment: Configure Enterprise Policies Restore Enterprise Configuration Welcome Configure Enterprise Set Enterprise Policy for Policy Default Settings the Selected Array Servers and Arrays Enterprise Monitoring Help OK Restore configuration from the following backup (. BEF) file: Browse… OK Backup Cancel

n You can back up the enterprise configuration information and then store it locally in a file. The backup process saves all of the enterprise specific information, including the enterprise policies and the enterprise policy elements. The backup process also saves information about the enterprise policies that the arrays are using.

Important: n Because restoring an enterprise configuration may affect arrays that use enterprise policies, it is recommended that you back up an array configuration after you back up the enterprise configuration. When you restore the enterprise configuration, you can also restore all of the array configurations. For information about backing up and restoring arrays, see Module 2, "Installing and Maintaining ISA Server, " in Course 2159 A, Deploying and Managing Microsoft Internet Security and Acceleration Server 2000.

Backing Up an Enterprise Configuration n To back up an enterprise configuration: 1. In ISA Management, in the console tree, right click Enterprise, and then click. Back Up. 2. In the Store backup configuration in this locationbox, type the name of the folder in which to store the backup data, and then click OK.

Restoring an Enterprise Configuration n To restore an enterprise configuration: 1. In ISA Management, in the console tree, right click Enterprise, click Restore, and then click Yes to overwrite the existing enterprise configuration with the backup configuration. 2. In the Restore configuration from the following backup (. bef) file box, type the path of the backup folder and the name of the backup file.

u. Using Enterprise Policies and Array Policies n Configuring an Enterprise Policy n Configuring an Array Policy n Combining Enterprise Policies and Array Policies

n You use enterprise and array policies to specify rules for controlling how an internal network communicates with the Internet. You use enterprise policies to apply a centralized set of rules to all of the arrays in the enterprise. You use array policies to apply a unique set of rules to each array in the enterprise. You can also combine enterprise policies and array policies.

Configuring an Enterprise Policy n Using Enterprise Policy Elements n Setting a Default Enterprise Policy n Changing Default Settings for the Enterprise Policy n Applying an Enterprise Policy to Selected Arrays

n An enterprise policy consists of site and content rules, protocol rules, and policy elements. When you set a default enterprise policy, ISA Server applies the rules of the default enterprise policy to all of the new arrays that you create, unless you specify a different policy. If required, you can configure the default enterprise policy to apply to only selected arrays. Note: n For more information about site and content rules, protocol rules, and policy elements, see Module 3, "Enabling Secure Internet Access" in Course 2159 A, Deploying and Managing Microsoft Internet Security and Acceleration Server 2000.

n By default, only members of the Enterprise. Admins group can create, configure, and apply enterprise policies and can create and configure enterprise wide policy elements.

Using Enterprise Policy Elements n When you create policy elements for an enterprise, these policy elements are available to all of the arrays in the enterprise. You can use these policy elements in enterprise policies and in array policies.

Setting a Default Enterprise Policy n To set a default enterprise policy: l In ISA Management, in the console tree, expand Enterprise, expand Policies, right-click the specified enterprise policy, and then click Set as Default Policy.

Changing Default Settings for the Enterprise Policy n After initializing ISA Server for the enterprise, you can change the default policies that ISA Server applies when you create a new array. n To change the default policies: 1. In ISA Management, in the console tree, right click Enterprise, and then click Set Defaults. 2. In the Set Default Policy dialog box, select the applicable policy and settings, and then click. OK.

Applying an Enterprise Policy to Selected Arrays n To apply an enterprise policy to selected arrays: 1. In ISA Management, in the console tree, expand Enterprise, expand Policies, right click the default enterprise policy, and then click. Properties. 2. In the Enterprise Policy Propertiesdialog box, click the Arrays tab, select the names of the arrays to which you want to apply the enterprise policy, and then click. OK. n Caution: When you apply an enterprise policy to an array, ISA Server deletes all of the previously defined array level site and content rules and protocol rules that allow access.

Configuring an Array Policy n Configuring the Cache for an Array n Forcing Packet Filtering for an Array n Allowing Publishing Rules in an Array n Configuring Server Specific Settings in ISA Server

n Configuring an array policy is similar to configuring a policy for a stand alone server. However, there are some important differences that you must keep in mind when configuring and using an array policy. n An array policy includes site and content rules, protocol rules, IP packet filters, and the associated policy elements. When you configure an array policy, ISA Server applies the rules of the array policy to all of the ISA Server computers in the array. You can also set an enterprise policy to require packet filtering at the array level. Note: n For more information about site and content rules, protocol rules, and policy elements, see Module 3, "Enabling Secure Internet Access, " in Course 2159 A, Deploying and Managing Microsoft Internet Security and Acceleration Server 2000.

Configuring the Cache for an Array n All of the cache configuration properties are the same for all of the servers in an array. These properties include the HTTP caching properties, the FTP caching properties, and most of the CARP properties. However, ISA Server separately allocates disk space for the cache on each server according to the amount that you specify when you install or reconfigure the cache on each server.

Forcing Packet Filtering for an Array n You cannot enable packet filtering at the enterprise level. However, an enterprise administrator can specify that packet filtering can be forced at the array level. If you are a member of the Enterprise. Admins group, ISA Server prompts you about whether you want to force the array to use packet filtering when you create a new array. You can also change this setting after you create an array. Enforce packet filtering to prevent an array administrator from configuring ISA Server in an insecure manner.

Forcing Packet Filtering for an Array (continued) n To force packet filtering for an array: 1. In ISA Management, in the console tree, expand Servers and Arrays, right click the applicable array, and then click Properties. 2. On the Policies tab, verify that Use custom enterprise policy settingsis selected, select the Force packet filtering on the arraycheck box, and then click. OK.

Allowing Publishing Rules in an Array n You cannot create publishing rules at the enterprise level. However, an enterprise administrator can specify whether an array is allowed to publish servers by creating Web publishing rules or server publishing rules. If you are a member of the Enterprise. Admins group, ISA Server prompts you about whether you want to allow publishing rules in the array when you create a new array. You can also change this setting after you have created an array.

Allowing Publishing Rules in an Array (continued) n To allow publishing rules for an array: 1. In ISA Management, in the console tree, expand Servers and Arrays, right click the applicable array, and then click Properties. 2. On the Policies tab, verify that. Use custom enterprise policy settingsis selected, select the Allow publishing rules check box, and then click. OK.

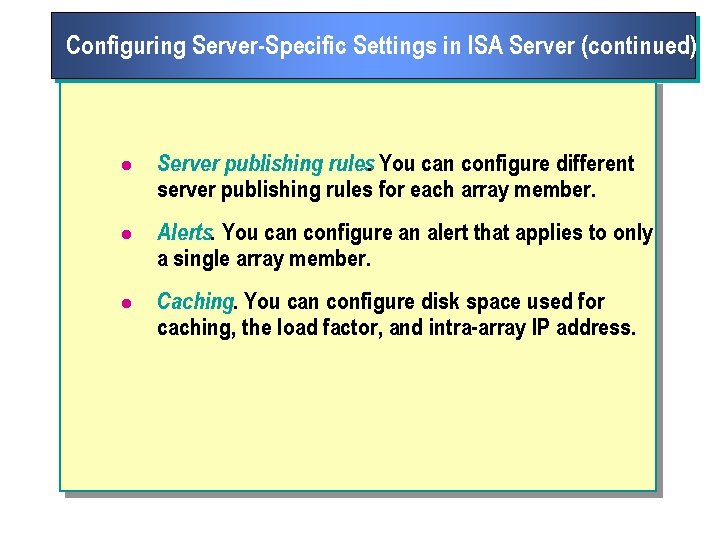
Configuring Server Specific Settings in ISA Server n Most of the settings in ISA Server apply to the entire array. However, some settings are specific to each array member. These settings include: l Listeners for outgoing and incoming Web requests. You can set up listeners to be active on only a single network interface. You can also configure a separate listener for each network interface on each ISA Server computer. l Packet filters. You can configure a packet filter to apply to only a single array member.

Configuring Server Specific Settings in ISA Server (continued) l Server publishing rules. You can configure different server publishing rules for each array member. l Alerts. You can configure an alert that applies to only a single array member. l Caching. You can configure disk space used for caching, the load factor, and intra array IP address.

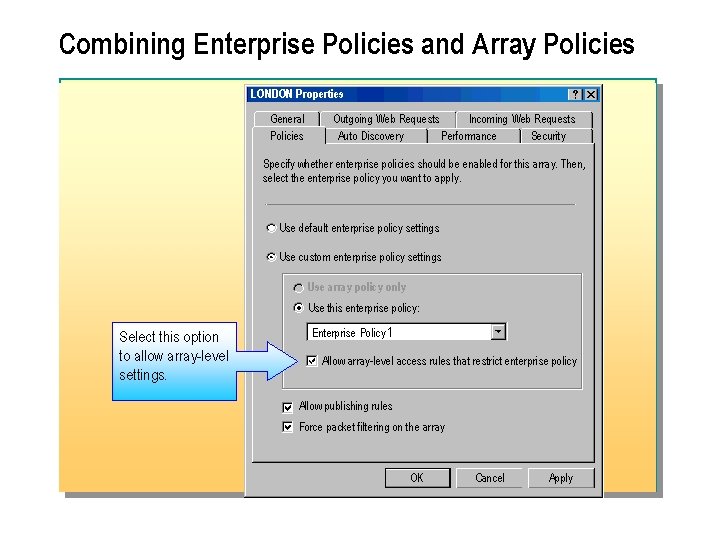
Combining Enterprise Policies and Array Policies LONDON Properties General Policies Outgoing Web Requests Incoming Web Requests Auto Discovery Performance Security Specify whether enterprise policies should be enabled for this array. Then, select the enterprise policy you want to apply. Use default enterprise policy settings Use custom enterprise policy settings Use array policy only Use this enterprise policy: Select this option to allow array-level settings. Enterprise Policy 1 Allow array-level access rules that restrict enterprise policy Allow publishing rules Force packet filtering on the array OK Cancel Apply

n You can configure enterprise policy settings so that an administrator can configure rules for an array policy to refine the enterprise policy. For example, you can create an access policy for an array to deny access to additional users, sites, content, or protocols.

n When you apply an enterprise policy to an array, you can no longer create site and content rules and protocol rules for the array that allows access. You can create site and content rules and protocol rules for only the array that denies access. Because ISA Server combines enterprise polices and array policies, you should define all of the rules that allow access in an enterprise policy and then create an array policy to further restrict the access granted by the enterprise policy. Note: n Only enterprise administrators can specify whether enterprise policies will allow array level rules.

n To configure an enterprise policy to allow array level settings: 1. In ISA Management, in the console tree, right click the applicable array, and then click. Properties. 2. On the Policies tab, select the Use custom enterprise policy settingscheck box, select the. Allow array level access rules that restrict enterprise policycheck box, and then click OK.

u. Managing Network Connections n Routing Overview n Configuring Routing for Web Proxy Client Requests n Configuring Routing for Firewall Client and. Secure. NAT Client Requests n Automatic Discovery Overview n Configuring Automatic Discovery n Configuring Clients for Automatic Discovery n Customizing Client Discovery Information

n You can manage network connections by configuring routing rules to direct Web requests. You can also use the automatic discovery feature to make the configuration of clients easier. By enabling automatic discovery, Web Proxy clients and Firewall clients will automatically discover the appropriate ISA Server computer. Important: n You can use ISA Server Standard Edition or ISA Server Enterprise Edition to manage network connections for ISA Server. However, customizing network connections yields the most benefits in an enterprise wide installation.

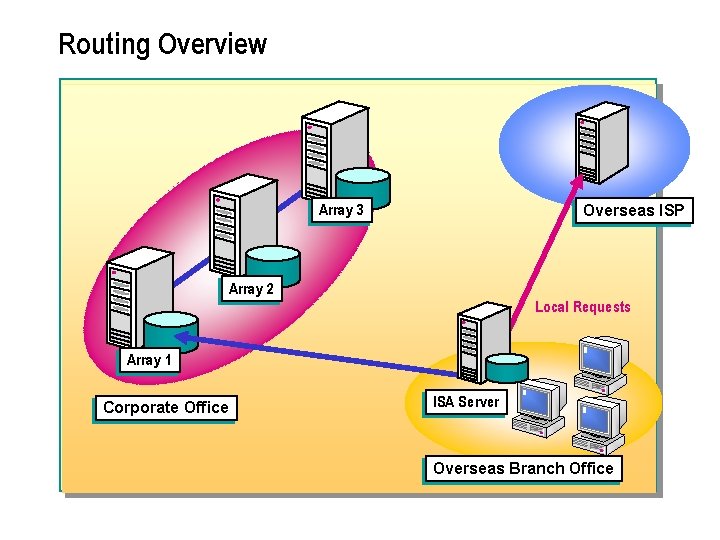
Routing Overview Array 3 Overseas ISP Array 2 Local Requests Array 1 Corporate Office ISA Server Overseas Branch Office

n Routing is the process of sending Web requests from an ISA Server computer to a specified destination. You can create routing rules to determine whether a Web Proxy client request is: l Retrieved directly from the specified destination. l Sent to an upstream server. l Redirected to an alternate site.

n You can also create routing rules to conditionally route requests, depending on the destination. For example, an organization with an overseas branch office could set up an ISA Server computer at the branch office that is connected to both the corporate office and an Internet service provider (ISP) that is local to the branch office. A routing rule on the ISA Server computer at the branch office could direct requests for local destinations to the ISP and direct all other requests to the ISA Server array at the corporate office. The ISA Server computer at the overseas branch office benefits from the ISA Server cache at the corporate office, and it is able to cache local objects retrieved from the ISP.

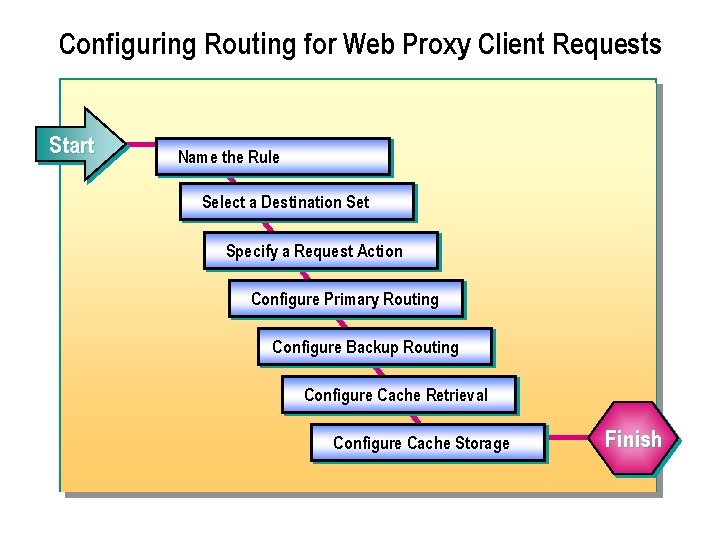
Configuring Routing for Web Proxy Client Requests Start Name the Rule Select a Destination Set Specify a Request Action Configure Primary Routing Configure Backup Routing Configure Cache Retrieval Configure Cache Storage Finish

n You can configure ISA Server to route requests from Web Proxy clients to a specific upstream ISA Server computer, a Microsoft Proxy Server 2. 0 computer, or a third party proxy server. You can specify a backup route if the primary route is unavailable. You can also configure when objects should be retrieved from the cache. You use routing rules to configure routes and cache retrieval options for Web Proxy client requests. You can also use routing rules to redirect requests to another site. For example, you can redirect internal requests for your public Web site to an internal replica of the Web site so that employees can access the site more efficiently and securely.

n To configure a routing rule: 1. In ISA Management, in the console tree, expand Servers and Arrays, expand the server or array, and then click Network Configuration. 2. In the details pane, click. Create a Routing Rule. 3. In the New Routing Rule Wizard, in the. Routing rule name box, type a name for the rule, and then click. Next. 4. On the Destination Sets page, specify the destinations, and then click. Next. 5. On the Request Action page, specify an action, and then click Next.

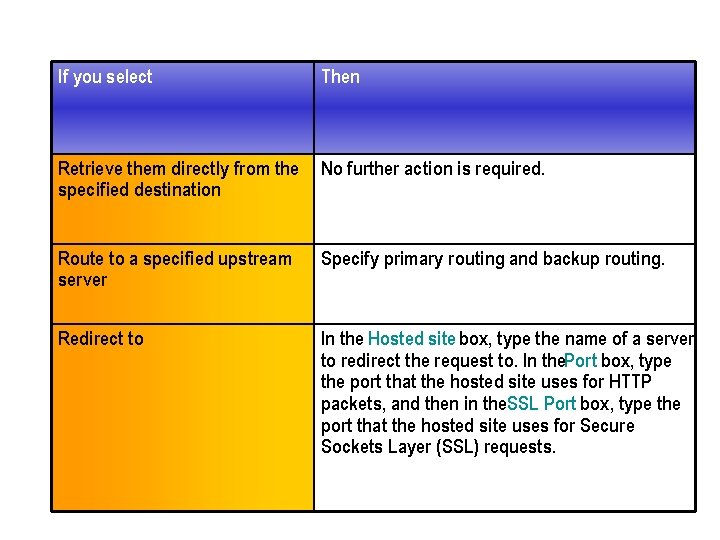
If you select Then Retrieve them directly from the specified destination No further action is required. Route to a specified upstream server Specify primary routing and backup routing. Redirect to In the Hosted site box, type the name of a server to redirect the request to. In the. Port box, type the port that the hosted site uses for HTTP packets, and then in the. SSL Port box, type the port that the hosted site uses for Secure Sockets Layer (SSL) requests.

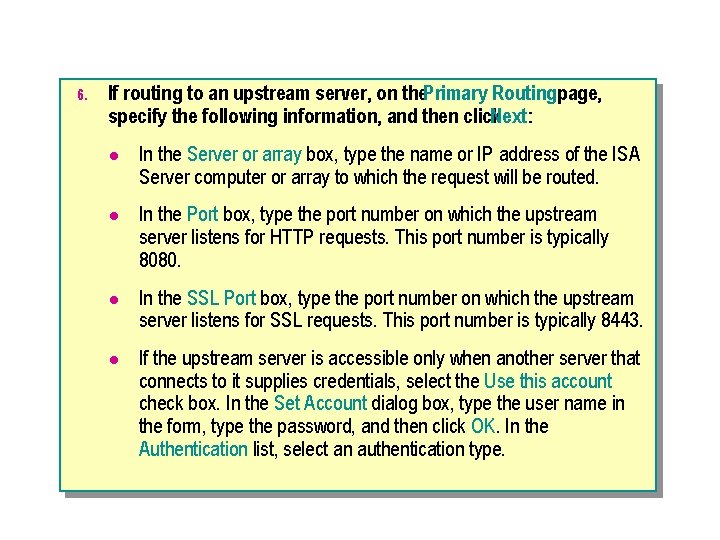
6. If routing to an upstream server, on the. Primary Routingpage, specify the following information, and then click Next: l In the Server or array box, type the name or IP address of the ISA Server computer or array to which the request will be routed. l In the Port box, type the port number on which the upstream server listens for HTTP requests. This port number is typically 8080. l In the SSL Port box, type the port number on which the upstream server listens for SSL requests. This port number is typically 8443. l If the upstream server is accessible only when another server that connects to it supplies credentials, select the Use this account check box. In the Set Account dialog box, type the user name in the form, type the password, and then click OK. In the Authentication list, select an authentication type.

7. n If routing to an upstream server, on the. Backup Routing page, select one of the following actions for cases in which the primary route is unavailable, and then click Next: l Ignore requests. Ignores the request and displays an error message in the Web Proxy client. l Retrieve the requests directly from specified destination. Bypasses ISA Server and attempts to retrieve the request directly. l Route requests to an upstream server. Note: If you route request to an upstream server, you must also configure the properties of an upstream ISA Server computer or array on the. Backup Routingpage.

8. On the Cache Retrieval Configurationpage, select an option for retrieving the object and routing the request, and then click. Next. 9. On the Cache Content Configurationpage, select an option for storing objects, and then click. Next. 10. On the Completing the New Routing Rule Wizard page, review your choices, and then click. Finish.

Applying Web Routing Rules n ISA Server applies routing rules in the order in which they are listed when you click. Routing under Network Configurationin the console tree. n To change the order in which rules are applied, right click a rule, and then click. Move Up or Move Down. The built in Default rule retrieves requests directly from the specified destination. You can edit but you cannot delete the default routing rule.

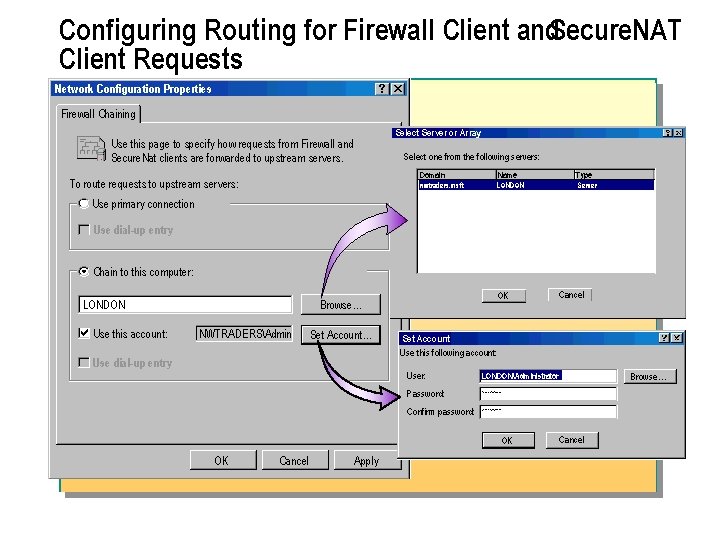
Configuring Routing for Firewall Client and. Secure. NAT Client Requests Network Configuration Properties Firewall Chaining Use this page to specify how requests from Firewall and Secure. Nat clients are forwarded to upstream servers. To route requests to upstream servers: Select Server or Array Select one from the following servers: Domain Name Type nwtraders. msft LONDON Server Use primary connection Use dial up entry Chain to this computer: LONDON Use this account: OK Browse… NWTRADERSAdmin Set Account… Use dial up entry Cancel Set Account Use this following account: User: Browse… LONDONAdministrator Password: Confirm password: OK OK Cancel Apply Cancel

n You can route requests from Firewall and. Secure. NAT clients by using firewall chaining. Firewall chainingrefers to a hierarchical connection between individual ISA Server computers or arrays of ISA Server computers. Firewall chaining enables requests from Firewall clients and Secure. NAT clients to be routed to upstream servers. For example, in an enterprise, you might configure ISA Server to forward all. Secure. NAT and Firewall client requests to an ISA Server computer at a central office, which then forwards the requests to the Internet.

n To configure firewall chaining: 1. In ISA Management, in the console tree, expand Servers and Arrays, expand your array, right click Network Configuration, and then click Properties. 2. On the Firewall Chaining tab, click Chain to this computer, and then type the name of the computer in the box. 3. If the server that you are chaining to is accessible only by using user account credentials, click the. Use this account check box, and then click. Set Account. In the Set Account dialog box, type the user name, type the password twice, and then click. OK twice.

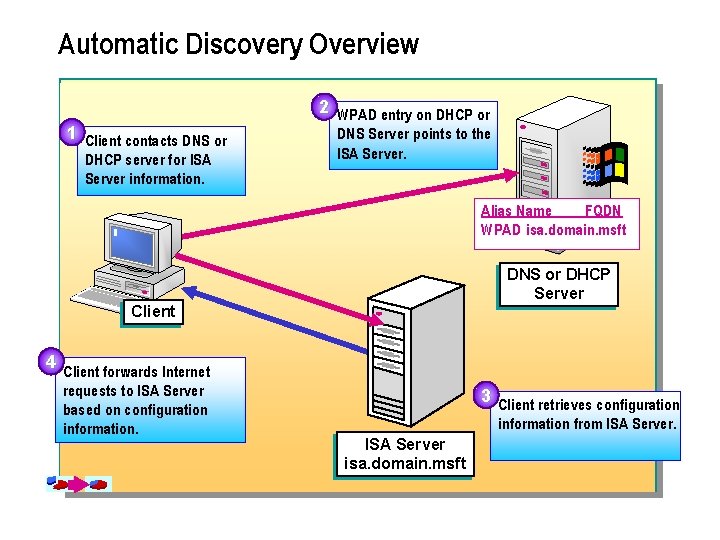
Automatic Discovery Overview 1 Client contacts DNS or DHCP server for ISA Server information. 2 WPAD entry on DHCP or DNS Server points to the ISA Server. Alias Name FQDN WPAD isa. domain. msft DNS or DHCP Server Client 4 Client forwards Internet requests to ISA Server based on configuration information. 3 Client retrieves configuration information from ISA Server isa. domain. msft

n For a Web Proxy client or a Firewall client to connect to an ISA Server computer, you must configure the browser or Firewall client to forward Internet requests to a specific ISA Server computer. If the ISA Server computer becomes unavailable or you want to use a different ISA Server computer, you must change this configuration. When you enable automatic discovery, Firewall clients and Web Proxy clients can automatically find an ISA Server computer on the network. Using automatic discovery can help you to minimize the time spent troubleshooting connection problems on client computers.

n Web Proxy clients enable automatic discovery by using Web Proxy Auto. Discovery. Protocol (WPAD) information. Firewall clients use the Winsock Proxy Auto. Detect Protocol (WSPAD). Both clients connect to an ISA Server computer and request configuration information after locating the ISA Server computer by using a WPAD entry on the Dynamic Host Configuration Protocol (DHCP) server or the Domain Name System (DNS) server.

n Automatic discovery is especially useful when you move your computer from one network to another. For example, if you use a laptop computer at home and at work, both the Firewall client and Microsoft Internet Explorer use ISA Server when you are connected to the corporate network, but you can gain access to the Internet directly when you are working at home.

n The automatic discovery process works as follows: 1. A client connects to a DNS or DHCP server for the ISA Server location information. 2. The client uses a WPAD entry to locate an ISA Server computer. 3. The client connects to the ISA Server computer specified in the WPAD entry to retrieve configuration information by using the WPAD protocol or the WSPAD protocol. 4. The client configures itself by using the configuration information that it retrieved.

Configuring Automatic Discovery n Configuring ISA Server for Automatic Discovery n Configuring a DNS Server for Automatic Discovery n Configuring a DHCP Server for Automatic Discovery

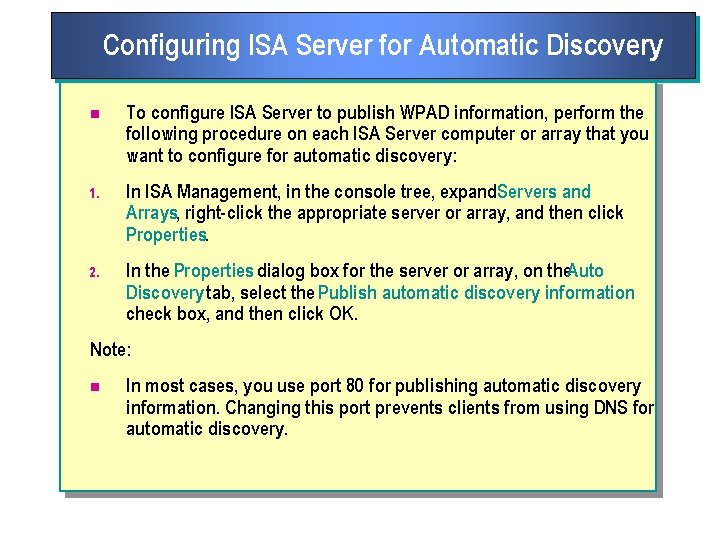
n The automatic discovery feature of ISA Server enables clients to automatically detect the appropriate ISA Server computer. To allow automatic discovery, you must first configure ISA Server to publish WPAD information. You can configure automatic discovery for clients running Windows 2000, Microsoft Windows 98, and Microsoft Windows Millennium Edition that use DHCP or DNS.

Configuring ISA Server for Automatic Discovery n To configure ISA Server to publish WPAD information, perform the following procedure on each ISA Server computer or array that you want to configure for automatic discovery: 1. In ISA Management, in the console tree, expand. Servers and Arrays, right click the appropriate server or array, and then click Properties. 2. In the Properties dialog box for the server or array, on the. Auto Discovery tab, select the Publish automatic discovery information check box, and then click OK. Note: n In most cases, you use port 80 for publishing automatic discovery information. Changing this port prevents clients from using DNS for automatic discovery.

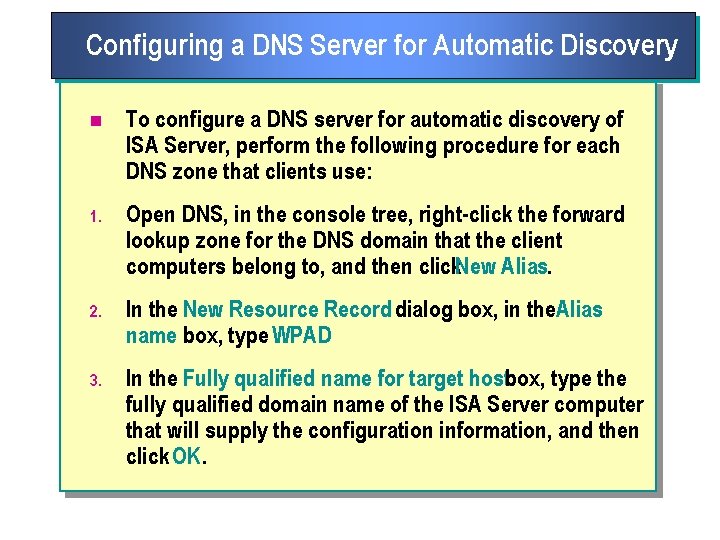
Configuring a DNS Server for Automatic Discovery n To configure a DNS server for automatic discovery of ISA Server, perform the following procedure for each DNS zone that clients use: 1. Open DNS, in the console tree, right click the forward lookup zone for the DNS domain that the client computers belong to, and then click. New Alias. 2. In the New Resource Record dialog box, in the. Alias name box, type WPAD 3. In the Fully qualified name for target hostbox, type the fully qualified domain name of the ISA Server computer that will supply the configuration information, and then click OK.

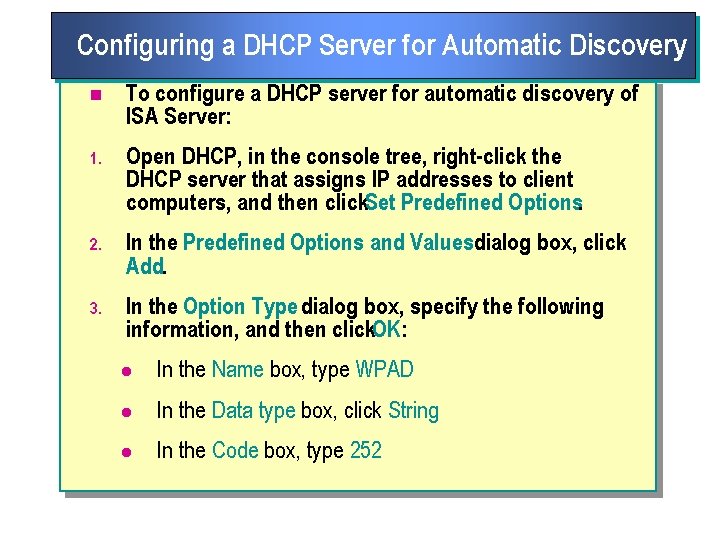
Configuring a DHCP Server for Automatic Discovery n To configure a DHCP server for automatic discovery of ISA Server: 1. Open DHCP, in the console tree, right click the DHCP server that assigns IP addresses to client computers, and then click. Set Predefined Options. 2. In the Predefined Options and Valuesdialog box, click Add. 3. In the Option Type dialog box, specify the following information, and then click. OK: l In the Name box, type WPAD l In the Data type box, click String l In the Code box, type 252

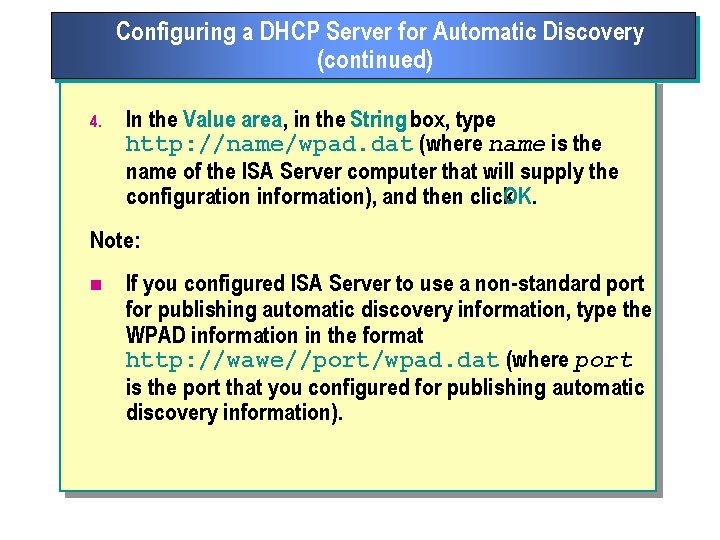
Configuring a DHCP Server for Automatic Discovery (continued) 4. In the Value area, in the String box, type http: //name/wpad. dat (where name is the name of the ISA Server computer that will supply the configuration information), and then click. OK. Note: n If you configured ISA Server to use a non standard port for publishing automatic discovery information, type the WPAD information in the format http: //wawe//port/wpad. dat (where port is the port that you configured for publishing automatic discovery information).

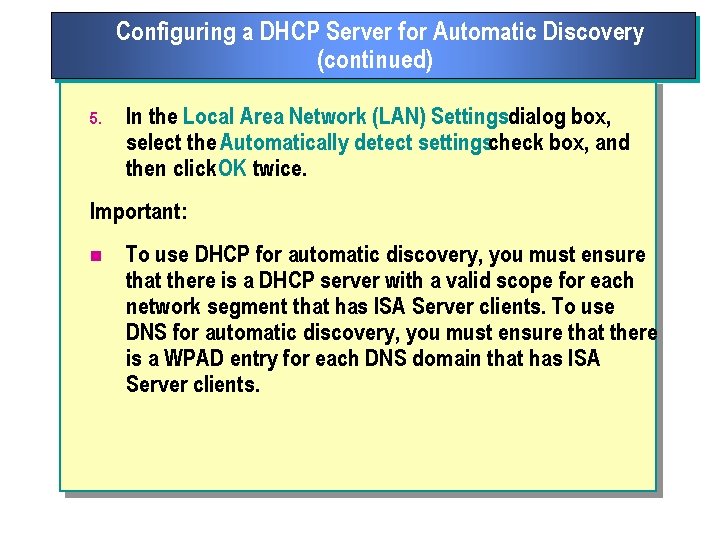
Configuring a DHCP Server for Automatic Discovery (continued) 5. In the Local Area Network (LAN) Settingsdialog box, select the Automatically detect settingscheck box, and then click OK twice. Important: n To use DHCP for automatic discovery, you must ensure that there is a DHCP server with a valid scope for each network segment that has ISA Server clients. To use DNS for automatic discovery, you must ensure that there is a WPAD entry for each DNS domain that has ISA Server clients.

Configuring Clients for Automatic Discovery n Setting Automatic Discovery for Firewall Clients n Setting Automatic Discovery for Internet Explorer

n Before clients can use automatic discovery, you must enable the Firewall Client and Internet Explorer to automatically detect ISA Server.

Setting Automatic Discovery for Firewall Clients n To set automatic discovery for Firewall Clients: 1. On the client computer, open Control Panel, and then double click. Firewall Client. 2. In the Firewall Client Optionsdialog box, select the Automatically detect ISA Servercheck box, and then click OK.

Setting Automatic Discovery for Internet Explorer n To set automatic discovery for Internet Explorer: 1. In Internet Explorer, on the. Tools menu, click Internet Options. 2. On the Connections tab, click LAN settings. 3. In the Local Area Network (LAN) Settingsdialog box, select the Automatically detect settingscheck box, and then click OK twice.

Customizing Client Discovery Information n Customizing Settings for Web Proxy Clients n Customizing Settings for Firewall Clients

n You can customize the information that Firewall clients receive when they retrieve configuration information from ISA Server. You can also customize the client discovery information for Web Proxy clients.

Customizing Settings for Web Proxy Clients n You can customize the Web Proxy configuration settings that ISA Server applies to a computer when you install the Firewall Client on that computer. n To customize settings for Web Proxy clients: 1. In ISA Management, in the console tree, expand Servers and Arrays, expand your array or server, and then click Client Configuration. 2. In the details pane, right click. Web Browser, and then click Properties.

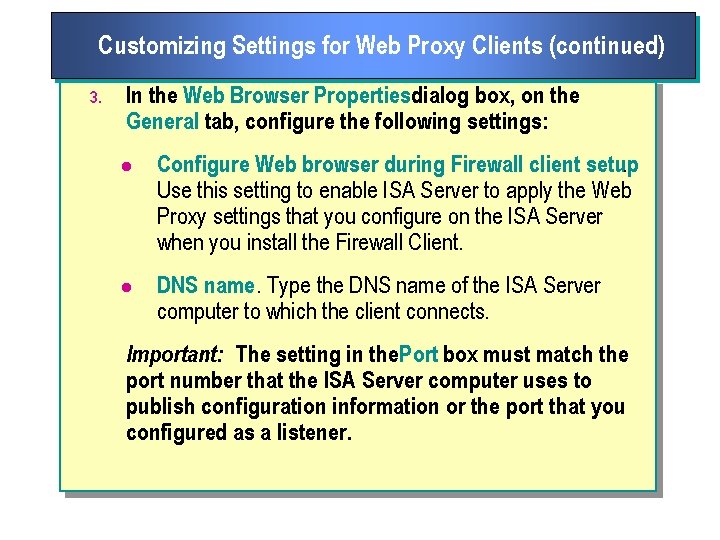
Customizing Settings for Web Proxy Clients (continued) 3. In the Web Browser Propertiesdialog box, on the General tab, configure the following settings: l Configure Web browser during Firewall client setup. Use this setting to enable ISA Server to apply the Web Proxy settings that you configure on the ISA Server when you install the Firewall Client. l DNS name. Type the DNS name of the ISA Server computer to which the client connects. Important: The setting in the Port box must match the port number that the ISA Server computer uses to publish configuration information or the port that you configured as a listener.

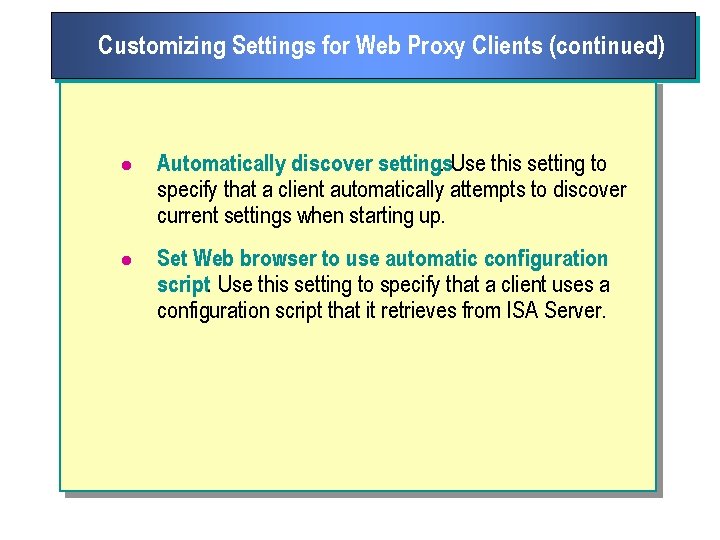
Customizing Settings for Web Proxy Clients (continued) l Automatically discover settings. Use this setting to specify that a client automatically attempts to discover current settings when starting up. l Set Web browser to use automatic configuration script. Use this setting to specify that a client uses a configuration script that it retrieves from ISA Server.

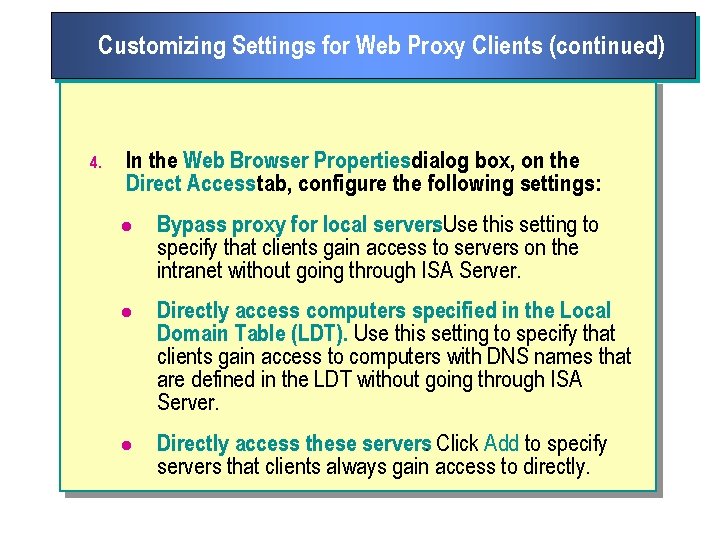
Customizing Settings for Web Proxy Clients (continued) 4. In the Web Browser Propertiesdialog box, on the Direct Access tab, configure the following settings: l Bypass proxy for local servers. Use this setting to specify that clients gain access to servers on the intranet without going through ISA Server. l Directly access computers specified in the Local Domain Table (LDT). Use this setting to specify that clients gain access to computers with DNS names that are defined in the LDT without going through ISA Server. l Directly access these servers. Click Add to specify servers that clients always gain access to directly.

Customizing Settings for Web Proxy Clients (continued) 5. In the Web Browser Propertiesdialog box, on the Backup Route tab, configure the following setting, and then click OK: l If ISA Server is unavailable, use this backup route to connect to the Internet. Use this setting to provide an alternate route for clients to connect to the Internet when the ISA Server computer is not available.

Customizing Settings for Firewall Clients n To customize settings for Firewall Clients: 1. In ISA Management, in the console tree, expand Servers and Arrays, expand your array or server, and then click Client Configuration. 2. In the details pane, right click. Firewall Client, and then click Properties.

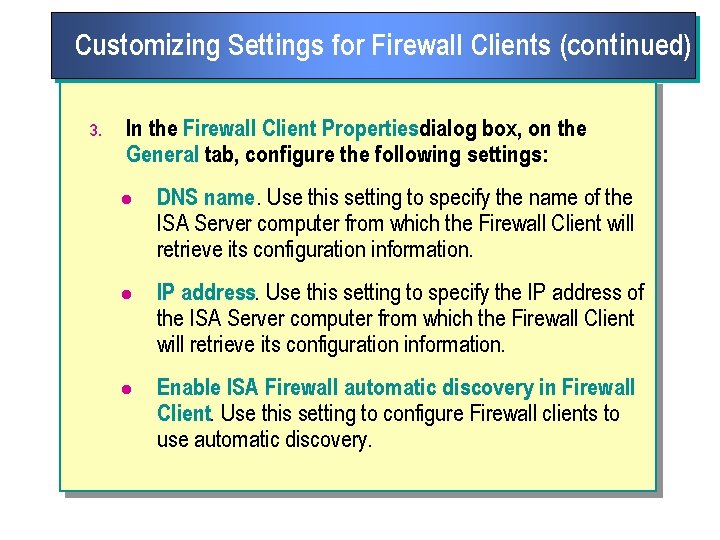
Customizing Settings for Firewall Clients (continued) 3. In the Firewall Client Propertiesdialog box, on the General tab, configure the following settings: l DNS name. Use this setting to specify the name of the ISA Server computer from which the Firewall Client will retrieve its configuration information. l IP address. Use this setting to specify the IP address of the ISA Server computer from which the Firewall Client will retrieve its configuration information. l Enable ISA Firewall automatic discovery in Firewall Client. Use this setting to configure Firewall clients to use automatic discovery.

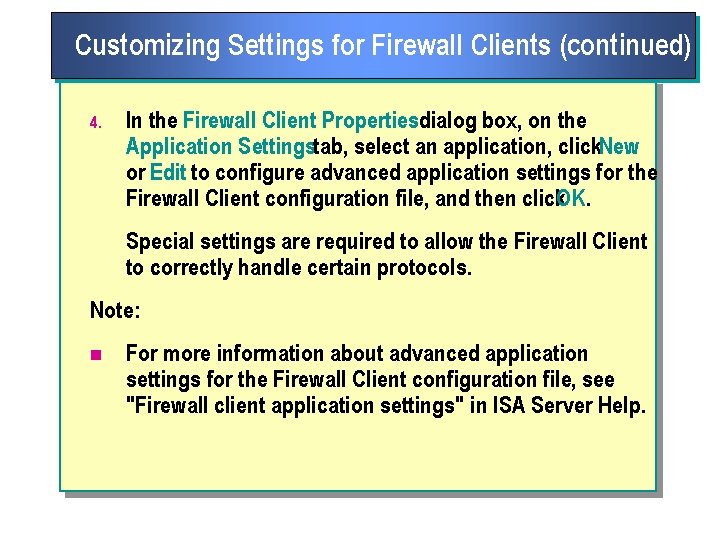
Customizing Settings for Firewall Clients (continued) 4. In the Firewall Client Propertiesdialog box, on the Application Settingstab, select an application, click. New or Edit to configure advanced application settings for the Firewall Client configuration file, and then click. OK. Special settings are required to allow the Firewall Client to correctly handle certain protocols. Note: n For more information about advanced application settings for the Firewall Client configuration file, see "Firewall client application settings" in ISA Server Help.

u. Scaling ISA Server n Understanding CARP n Configuring CARP n Understanding Network Load Balancing

n When you set up an array of ISA Server computers, you can increase performance and availability by distributing caching and using Network Load Balancing. n ISA Server uses the CARP protocol to enable multiple ISA Server computers in an array to distribute the cache between them. You can enable CARP for both outgoing and incoming requests. You can also configure array members so that different servers have different cache loads.

n For Secure. NAT clients, fault tolerance can be achieved when two or more ISA Server computers are used together with Windows 2000 Advanced Server Network Load Balancing. Also, by combining the resources of two or more computers running Windows 2000 Advanced Server into a single Network Load Balancing cluster, Network Load Balancing can increase reliability and performance for servers that you publish by using ISA Server. Important: n To use CARP and to use Network Load Balancing efficiently, you must use ISA Server Enterprise Edition.

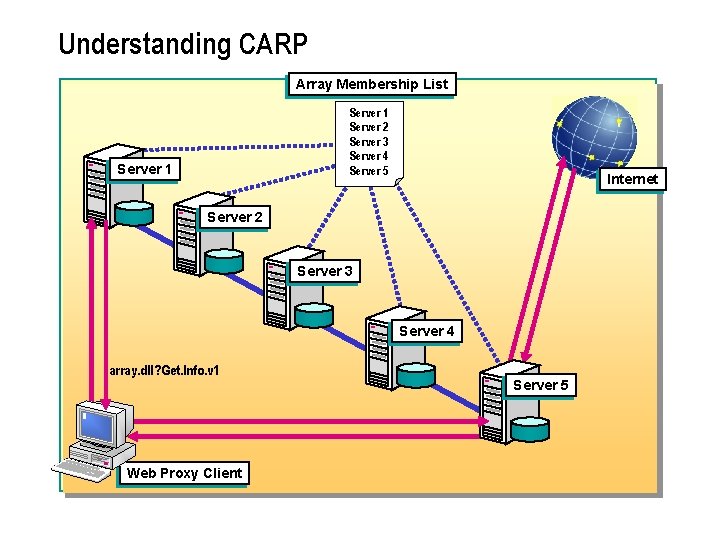
Understanding CARP Array Membership List Server 1 Server 2 Server 3 Server 4 Server 5 Server 1 Internet Server 2 Server 3 Server 4 array. dll? Get. Info. v 1 Web Proxy Client Server 5

n ISA Server computers in an array use CARP to create a single logical cache. CARP is a routing algorithm that provides efficiency and prevents the duplication of cache content. CARP uses hash based routing to determine the best path through an array to resolve a request. By using CARP, Web Proxy clients and downstream servers are able to determine the most efficient way to route a request. In addition, by using hash based routing instead of queries to determine the location of cached information, CARP becomes faster and more efficient as more member servers are added to the array.

ISA Server uses CARP to provide efficient routing for Web requests as follows: n An array membership list, which is maintained in Active Directory, tracks the servers in the array. Array members are notified when servers are added or removed from the array. n Periodically, Web Proxy clients and downstream servers poll the array membership list and, if necessary, update it. l Web Proxy clients send an array. dll? Get. Routing. Script request to the member server. l Downstream servers send an array. d. Il? Get. Info. v 1 request to the member server.

n When requesting an object, the Web Proxy client or the downstream server uses the array membership list and the hash function to determine which server should resolve the request. The request is then routed to the server that has the hash with the highest value. n The server receiving the request checks if it should handle the request. If so, it sends the request to the Internet host. If not, it sends the request to another array member. Forwarding to another array member transparently allows clients that cannot use CARP to get the benefits of distributed caching.

Note: n The hash is a value that is derived from the URL of the Web request and the server properties. ISA Server uses this value to determine which ISA Server computer caches a given URL. Similarly, Web Proxy clients that support CARP use the same formula to determine which ISA Server computer in an array may hold a cached copy of the object. Because both the client computer and the array members use the same formula to determine the hash value for a given URL, there is a high likelihood that the ISA Server computer that the client contacts does indeed cache that URL. Using this mechanism instead of a central directory causes less network traffic and processor usage for both the Web Proxy clients and ISA Server computers. For more information about CARP, see the white paper "Cache Array Routing Protocol and Microsoft Proxy Server 2. 0" under. Additional Readingon the Student Materials compact disc. The implementation of CARP in ISA Server is identical to the implementation in Proxy Server 2. 0.

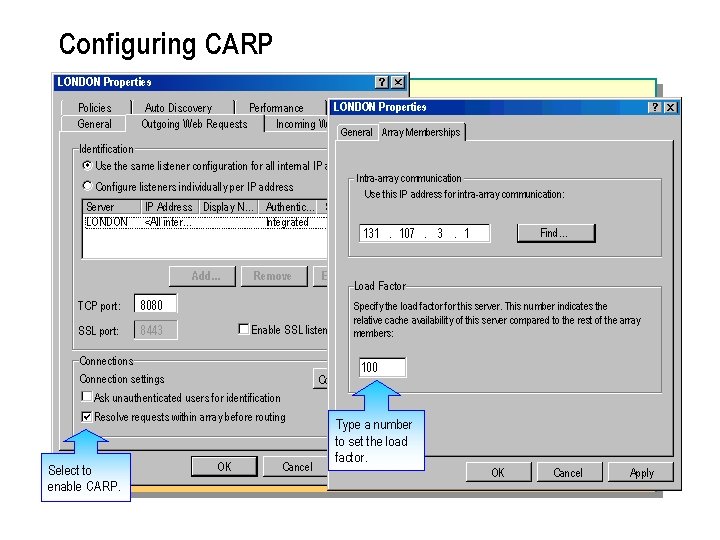
Configuring CARP LONDON Properties Policies General LONDON Auto Discovery Performance Security Properties Outgoing Web Requests Incoming Web Requests General Array Memberships Identification Use the same listener configuration for all internal IP addresses. Intra-array communication Use this IP address for intra-array communication: Configure listeners individually per IP address Server LONDON IP Address Display N… Authentic… Server C… <All inter… Integrated 131. 107. 3. 1 Add… TCP port: 8080 SSL port: 8443 Remove Edit… Enable SSL listeners Connection settings Find… Load Factor Specify the load factor for this server. This number indicates the relative cache availability of this server compared to the rest of the array members: 100 Configure… Ask unauthenticated users for identification Resolve requests within array before routing Select to enable CARP. OK Cancel Type a number to set the load factor. Apply OK Cancel Apply

n You can enable CARP separately for incoming and outgoing Web requests. By default, ISA Server enables CARP for outgoing Web requests and disables CARP for all incoming Web requests. You can also distribute the cache load by configuring the load factor for any ISA Server computer in an array. For example, if a server has a larger disk or a fast processor, you can configure that server to receive more of the cache load by increasing its load factor.

Enabling CARP n To enable CARP: 1. In ISA Management, in the console tree, right click the applicable array, and then click. Properties. 2. On the Incoming Web requeststab or on the Outgoing Web requests tab, select the Resolve requests within array before routingcheck box, and then click. OK.

Configuring the Load Factor n The load factor for an ISA Sever computer indicates the share of caching based on the total of the load factors of all servers in the array. n To configure the load factor: 1. In ISA Management, in the console tree, click. Computers. 2. In the details pane, right click the applicable computer, and then click Properties. 3. On the Array Membership tab, under Load factor, type theload factor, and then click OK. Important: n When a member server of an array sends a request to another member server, it uses the intra array IP address of a server. This address must be an internal IP address.

Understanding Network Load Balancing ISA Server Array Internet Cache Published Server

n You can use the Network Load Balancing component of Windows 2000 Advanced Server to share the publishing of internal servers between multiple ISA Server computers. Important: n Network Load Balancing is available with only Windows 2000 Advanced Server.

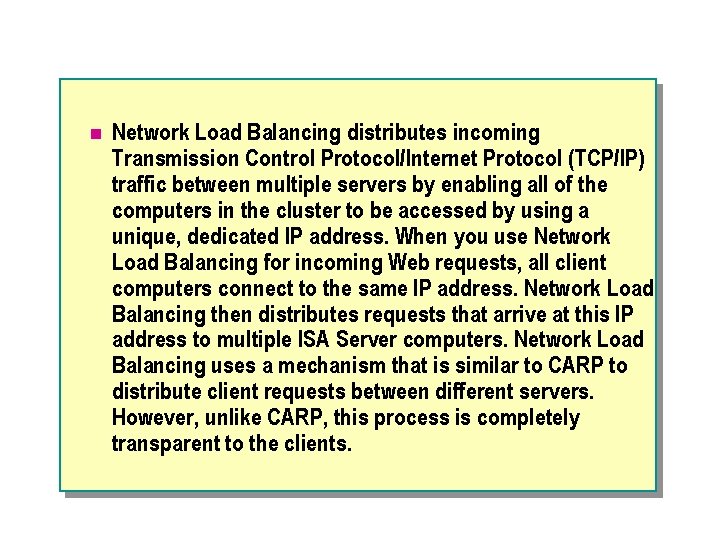
n Network Load Balancing distributes incoming Transmission Control Protocol/Internet Protocol (TCP/IP) traffic between multiple servers by enabling all of the computers in the cluster to be accessed by using a unique, dedicated IP address. When you use Network Load Balancing for incoming Web requests, all client computers connect to the same IP address. Network Load Balancing then distributes requests that arrive at this IP address to multiple ISA Server computers. Network Load Balancing uses a mechanism that is similar to CARP to distribute client requests between different servers. However, unlike CARP, this process is completely transparent to the clients.

Note: n You can also achieve load balancing by configuring DNS for round robin lookups. Configuring DNS for round robin lookups is easier than configuring Network Load Balancing, but Network Load Balancing provides more efficient load balancing and fault tolerance.

n For best performance and for ease of administration, ensure that all members of the Network Load Balancing cluster are members of the same ISA Server array. Note: n For more information about Network Load Balancing, see "Using Network Load Balancing" in ISA Server Help, the white paper entitled "Network Load Balancing Technical Overview" under Additional Reading on the Student Materials compact disc, and "Network Load Balancing" in the Windows 2000 Server Resource Kit.

u. Extending and Automating ISA Server Functionality n Automating Administration Tasks n Extending Functionality By Using Filters

n Security policies, network traffic, and content formats vary from organization to organization. To meet the unique security and performance needs of a large organization, ISA Server is extensible. Several third party vendors offer compatible and complementary solutions that extend and integrate with ISA Server. You can also automate many ISA Server administration tasks by using scripts.

Important: n You can gain benefits from using ISA Server's extensibility and automation features whether you use the Standard Edition or the Enterprise Edition. Note: n The ISA Server Software Development Kit (SDK) is included on the ISA Server compact disc. For more information about third party offerings, see the Microsoft ISA Server Web site at http: //www. microsoft. com/isaserver/

Automating Administration Tasks n Using the ISA Server SDK n Extending ISA Management n Managing Cache Content n Adding Custom Events and Alerts

n You can use scripting to automate many of the administration tasks of ISA Server. Scripting allows you to use ISA administration objects to gain access to and control policies and configuration settings for an enterprise, an ISA Server array, or a stand alone server. You can use the same script multiple times to automate repetitive tasks or to apply the same configuration settings to multiple stand alone servers or arrays. n Note Scripting requires some basic familiarity with a scripting language, such as Microsoft Visual Basic® Scripting Edition (VBScript) or Microsoft Jscript®, or a programming language, such as Microsoft Visual C++® or Microsoft Visual Basic.

Using the ISA Server SDK n Documentation for creating administration scripts is included in the ISA Server SDK, which you can install from the sdk directory on the ISA Server compact disc. The SDK also contains required run time libraries, sample scripts and applications, and information about ISA Server architecture and internals.

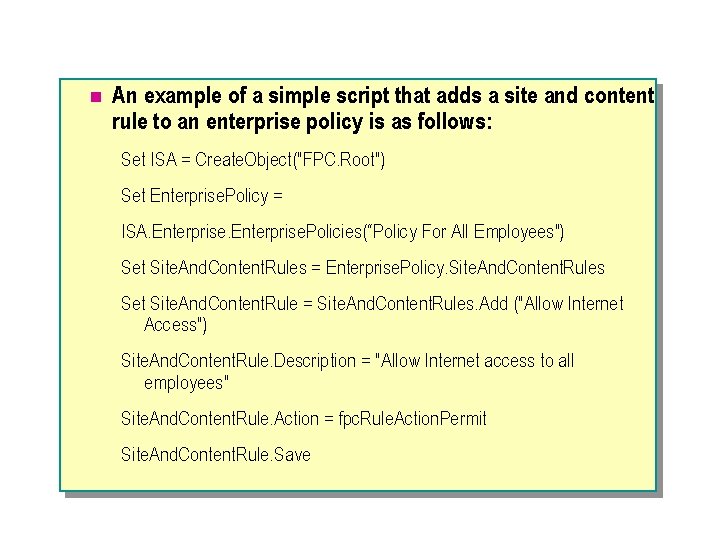
n An example of a simple script that adds a site and content rule to an enterprise policy is as follows: Set ISA = Create. Object("FPC. Root") Set Enterprise. Policy = ISA. Enterprise. Policies(“Policy For All Employees") Set Site. And. Content. Rules = Enterprise. Policy. Site. And. Content. Rules Set Site. And. Content. Rule = Site. And. Content. Rules. Add ("Allow Internet Access") Site. And. Content. Rule. Description = "Allow Internet access to all employees" Site. And. Content. Rule. Action = fpc. Rule. Action. Permit Site. And. Content. Rule. Save

Extending ISA Management n You can extend ISA Management by creating context sensitive menu extensions, adding extension snap ins to ISA Management, and adding tasks to ISA Management Taskpads. Note: n For more information about how to perform these tasks, see "Extending ISA Management" in the ISA Server SDK documentation.

Managing Cache Content n You can manage all of the cache content in ISA Server programmatically. For example, you could create an application that places objects into the cache from storage media, such as a CD ROM. By using storage media, you can pre load the cache to give users access to data even when no connection to the Internet is available for extended periods or where preloading the cache from the Internet would create unacceptable amounts of network traffic.

Adding Custom Events and Alerts n You can create custom events and alerts by using scripts. For example, you can create an alert that is triggered when a specific connection sequence occurs that indicates an intrusion attempt. n You can also create a custom alert. For example, you could create an alert that signals a specialized application to send a pre recorded telephone message to administrators.

Extending Functionality By Using Filters n Creating Application Filters n Creating Web Filters

n You can enhance ISA Server functionality by installing filters developed by third party vendors. You can also create your own filters. The ISA Server SDK contains information about how to do this and contains several samples of how to create filters. Finally, by using the programming interfaces of ISA Server, you can customize many built in features of ISA Server. To create application filters or Web filters, use Visual C++. Visual Basic, Java, and scripting languages are not suitable for creating such filters. Note: n For more information about how to perform these tasks, see the ISA Server SDK.

Creating Application Filters 2. Application filters work with the Microsoft Firewall service of ISA Server to intercept and process data. Application filters can gain access to the data stream or specific datagrams that are associated with a session in the Firewall service. An application filter can perform protocol specific tasks or system specific tasks, such as authentication and checking for viruses. For example, the SDK contains an application filter sample that blocks the transmission of program files by using the FTP protocol.

Creating Web Filters n Web filters work with the Microsoft Web Proxy service to perform tasks on Web objects that the Web Proxy service processes. You can create Web filters to perform tasks such as: l Scanning and modifying Web requests or responses. l Implementing custom authentication schemes. l Encrypting data. l Logging data. l Performing traffic analysis or other analysis tasks.

n For example, you can create a Web filter that blocks access to Web pages that contain specific words. n ISA Server implements Web filters as Internet Server Application Programming Interface (IS API) applications. If you use IS API programming to create ISAPI applications for Internet Information Services (IIS), you will be able to use these same skills to create Web filters for ISA Server.

Lab A: Configuring ISA Server for the Enterprise

Exercise 1: Configuring Auto Discovery n In this exercise, you will configure DNS and DHCP to enable Auto Discovery for ISA Server clients.

Exercise 1: Scenario n When you installed ISA Server, you configured the client computers to use the ISA Server computer for Internet access. This configuration works well most of the time, but it takes much of your time to configure new client computers and troubleshoot connection problems with existing clients. To reduce the time that it takes to support ISA Server clients, you decide to configure ISA Server Auto Discovery.

Exercise 2: Installing the ISA Server Schema Update n In this exercise, you will install the ISA Server schema update.

Exercise 2: Scenario n Northwind Traders has experienced rapid growth in its network infrastructure and performance monitoring shows heavy usage of your ISA Server computer. You have decided to improve performance for Internet access by using an ISA Server array. Before you can create an ISA Server array, you must install the ISA Server Active Directory schema update.

Exercise 3: Promoting an Array n In this exercise, you will promote a stand alone ISA Server computer to an array.

Exercise 3: Scenario n After you have installed the schema update, you can create an ISA Server array for Northwind Traders. To preserve most of the configuration settings that you have performed on your stand alone ISA Server computer, you will promote the stand alone server to an array.

Exercise 4: Creating Enterprise Policies and Array Policies n In this exercise, you will create enterprise policies and array policies.

Exercise 4: Scenario n After you have promoted the stand alone ISA Server computer to an array, you must configure the rules that are required to implement the Internet access policy of Northwind Traders. The first rule is a rule that allows administrators to gain access to the Internet to test the array.

Adding an ISA Server Computer to an Array n In this exercise, you will add an ISA Server computer to an array.

Scenario n After you have configured the ISA Server array at Northwind Traders, you will add another ISA Server computer to the array to provide the scalability and fault tolerance that an array provides.

Review n Introducing ISA Server Enterprise Edition n Installing ISA Server in the Enterprise n Using Enterprise Policies and Array Policies n Managing Network Connections n Scaling ISA Server n Extending and Automating ISA Server Functionality

Appendix A: ISA Server Caching Criteria n ISA Server uses several criteria when determining which objects to cache and how to cache them. This appendix provides an overview of the caching criteria used by ISA Server.

HTTP Caching n ISA Server uses the following criteria when caching HTTP objects:

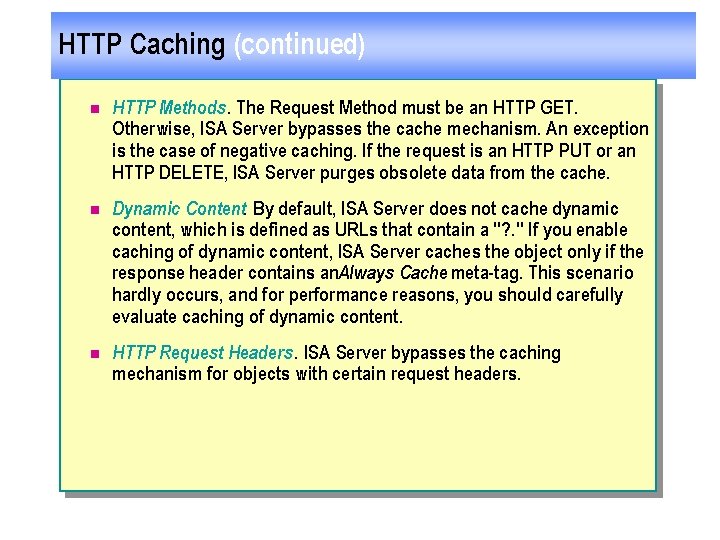
HTTP Caching (continued) n HTTP Methods. The Request Method must be an HTTP GET. Otherwise, ISA Server bypasses the cache mechanism. An exception is the case of negative caching. If the request is an HTTP PUT or an HTTP DELETE, ISA Server purges obsolete data from the cache. n Dynamic Content. By default, ISA Server does not cache dynamic content, which is defined as URLs that contain a "? . " If you enable caching of dynamic content, ISA Server caches the object only if the response header contains an. Always Cache meta tag. This scenario hardly occurs, and for performance reasons, you should carefully evaluate caching of dynamic content. n HTTP Request Headers. ISA Server bypasses the caching mechanism for objects with certain request headers.

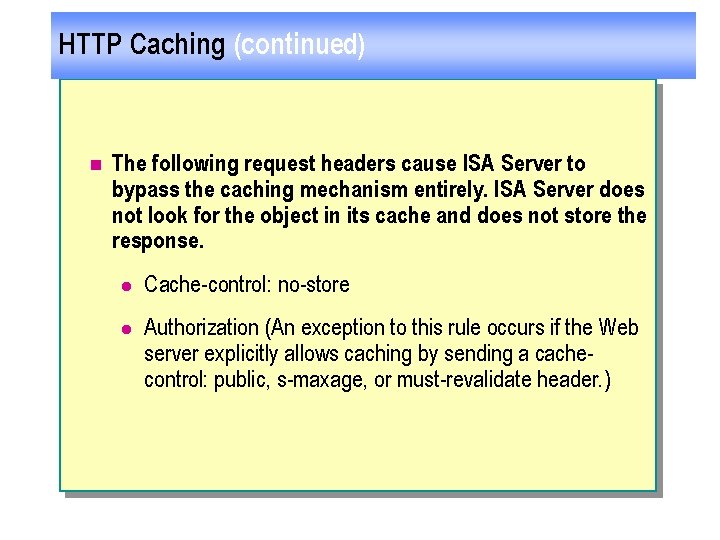
HTTP Caching (continued) n The following request headers cause ISA Server to bypass the caching mechanism entirely. ISA Server does not look for the object in its cache and does not store the response. l Cache-control: no-store l Authorization (An exception to this rule occurs if the Web server explicitly allows caching by sending a cachecontrol: public, s-maxage, or must-revalidate header. )

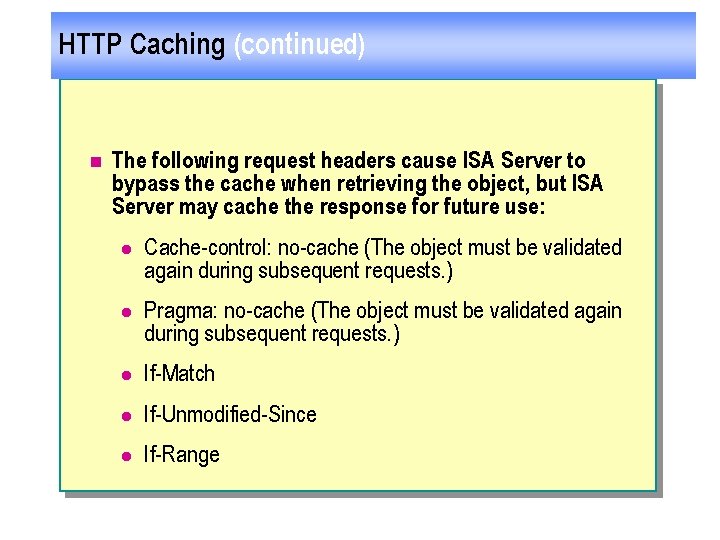
HTTP Caching (continued) n The following request headers cause ISA Server to bypass the cache when retrieving the object, but ISA Server may cache the response for future use: l Cache-control: no-cache (The object must be validated again during subsequent requests. ) l Pragma: no-cache (The object must be validated again during subsequent requests. ) l If-Match l If-Unmodified-Since l If-Range

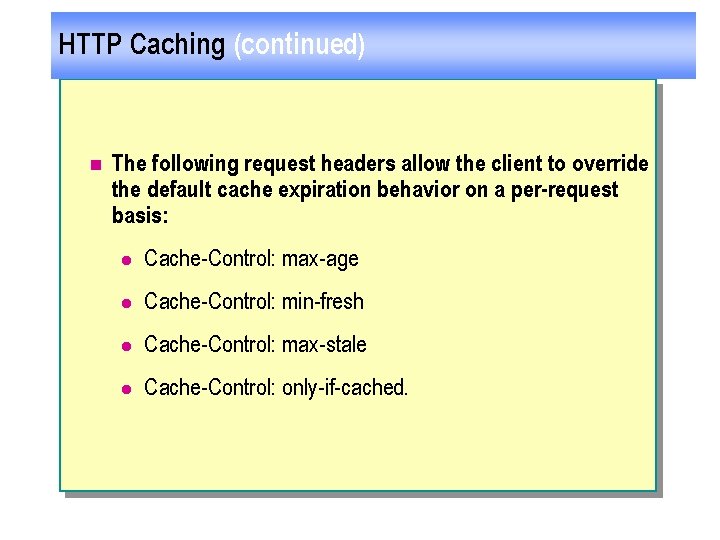
HTTP Caching (continued) n The following request headers allow the client to override the default cache expiration behavior on a per request basis: l Cache-Control: max-age l Cache-Control: min-fresh l Cache-Control: max-stale l Cache-Control: only-if-cached.

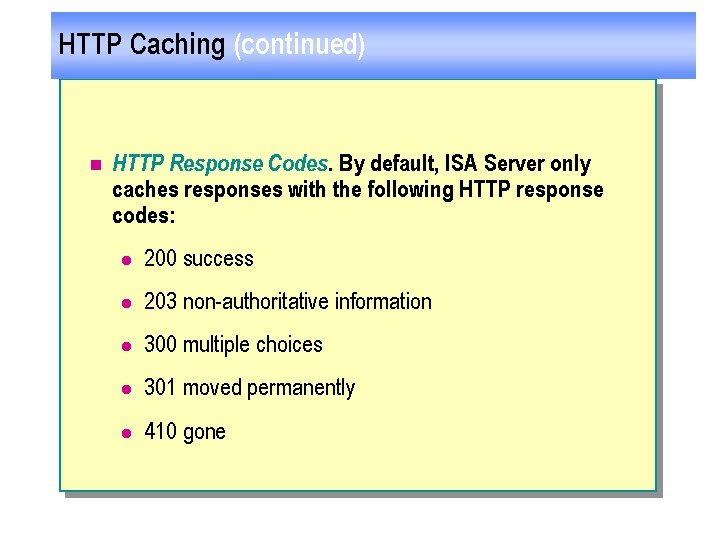
HTTP Caching (continued) n HTTP Response Codes. By default, ISA Server only caches responses with the following HTTP response codes: l 200 success l 203 non-authoritative information l 300 multiple choices l 301 moved permanently l 410 gone

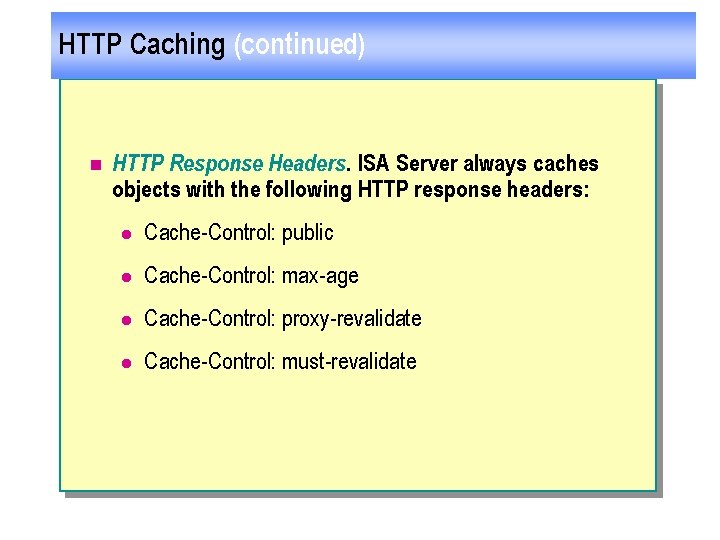
HTTP Caching (continued) n HTTP Response Headers. ISA Server always caches objects with the following HTTP response headers: l Cache-Control: public l Cache-Control: max-age l Cache-Control: proxy-revalidate l Cache-Control: must-revalidate

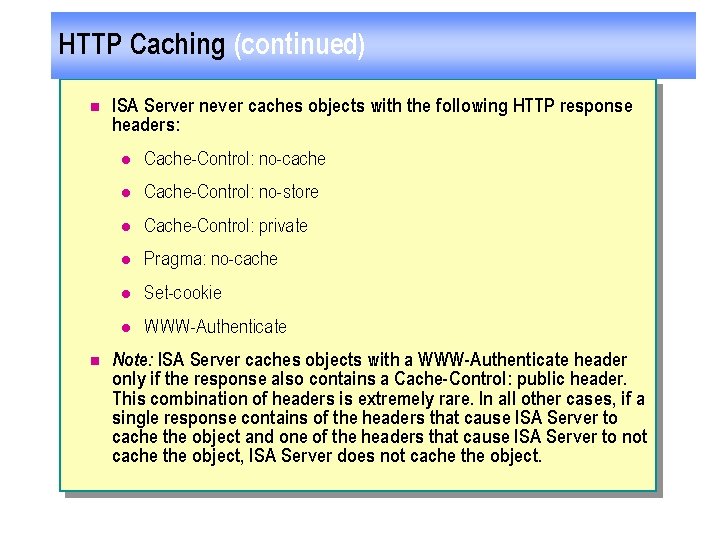
HTTP Caching (continued) n n ISA Server never caches objects with the following HTTP response headers: l Cache-Control: no-cache l Cache-Control: no-store l Cache-Control: private l Pragma: no-cache l Set-cookie l WWW-Authenticate Note: ISA Server caches objects with a WWW Authenticate header only if the response also contains a Cache Control: public header. This combination of headers is extremely rare. In all other cases, if a single response contains of the headers that cause ISA Server to cache the object and one of the headers that cause ISA Server to not cache the object, ISA Server does not cache the object.

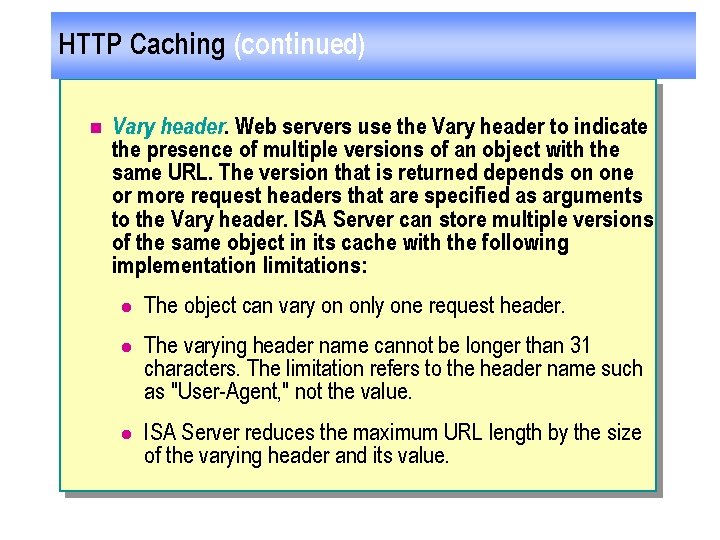
HTTP Caching (continued) n Vary header. Web servers use the Vary header to indicate the presence of multiple versions of an object with the same URL. The version that is returned depends on one or more request headers that are specified as arguments to the Vary header. ISA Server can store multiple versions of the same object in its cache with the following implementation limitations: l The object can vary on only one request header. l The varying header name cannot be longer than 31 characters. The limitation refers to the header name such as "User-Agent, " not the value. l ISA Server reduces the maximum URL length by the size of the varying header and its value.

HTTP Caching (continued) n Headers added by the ISA Server for caching, ISA Server adds the Age header to all objects served from the cache. The Age header indicates how long the object has been in the cache without ISA Server having revalidated the object. The information in the Age header can be useful when you troubleshoot reported caching problems or when you must know whether an object was cached. ISA Server also adds the Warning header on rare, appropriate occasions when required by the HTTP specifications.

HTTP Caching (continued) n Download Errors. If there is an error downloading an object that is being written to the cache, ISA Server deletes the object from the cache. Such an error can be caused by the client disconnecting before the download is complete. n Cache Filters. You can configure routing rules that disable caching for certain requests. You can use such routing rules for Web sites that users gain access to by using a fast network connection. For more information on routing rules, see Module 9, "Configuring ISA Server for an Enterprise, " in course 2159 A, Deploying and Managing Microsoft ISA Server 2000.

Caching Myths n Microsoft Product Support Services (PSS) has identified a number of common misconceptions about the caching mechanism that ISA Server uses. The following factors do not affect caching: l URLs containing the strings such as cgi or cgi-bin. l ASP pages or other content that is dynamically created on the Web server. l Responses that don't contain a Last-Modified date. ISA Server only caches responses without a Last-Modified date if you configure ISA Server to do so. l META tags within HTML. Most Web servers do not move META tags from the HTML code to the HTTP headers. l The type of object, such as if the object is a file other than a Web page.

FTP Caching n Because FTP servers do not return the helpful information that Web servers do, FTP caching is much simpler. ISA Server caches all FTP responses for a fixed period of time that you specify by using ISA Management.

Active Caching n The operations of active caching depend on three factors:

Active Caching (continued) n Time of last object access. When you configure active caching, ISA Server retrieves Web objects with a Time to Live (TTL) that is close to expiring. When you configure ISA Server to perform active caching less frequently, ISA Server actively retrieves Web objects only if a user recently requested the object. When you configure ISA Server to perform active caching more frequently, ISA Server actively retrieves Web objects even if more time has passed since a user last requested the object.

Active Caching (continued) n System load. When ISA Server determines that the number of current client sessions is low, ISA Server updates the objects that are marked for active caching as soon as 50% of the object's current TTL has expired. As the number of current client sessions approaches the maximum number of client sessions that ISA Server allows, active caching only retrieves objects that have a TTL that is close to expiring.

Active Caching (continued) n System performance. ISA Server contains several mechanisms that ensure that active caching does not place an undue burden on your computer's system performance.