Module 4 Configuring ISA Server as a Firewall





- Slides: 31

Module 4: Configuring ISA Server as a Firewall

Overview Using ISA Server as a Firewall Examining Perimeter Networks and Templates Configuring System Policies Configuring Intrusion Detection and IP Preferences

Lesson: Using ISA Server as a Firewall What Is a TCP/IP Packet? What Is Packet Filtering? What Is Stateful Filtering? What Is Application Filtering? What Is Intrusion Detection? How ISA Server 2004 Filters Network Traffic Implementing ISA Server 2004 as a Firewall

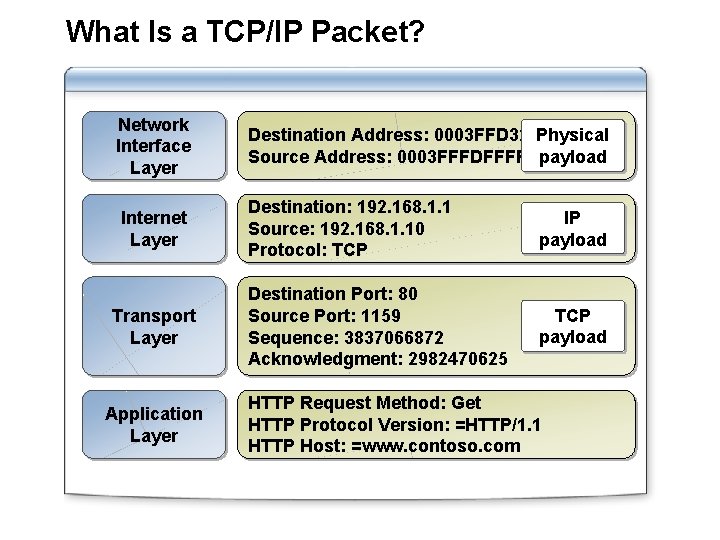
What Is a TCP/IP Packet? Network Interface Layer Destination Address: 0003 FFD 329 B 0 Physical Source Address: 0003 FFFDFFFF payload Internet Layer Destination: 192. 168. 1. 1 Source: 192. 168. 1. 10 Protocol: TCP IP payload Destination Port: 80 Source Port: 1159 Sequence: 3837066872 Acknowledgment: 2982470625 TCP payload Transport Layer Application Layer HTTP Request Method: Get HTTP Protocol Version: =HTTP/1. 1 HTTP Host: =www. contoso. com

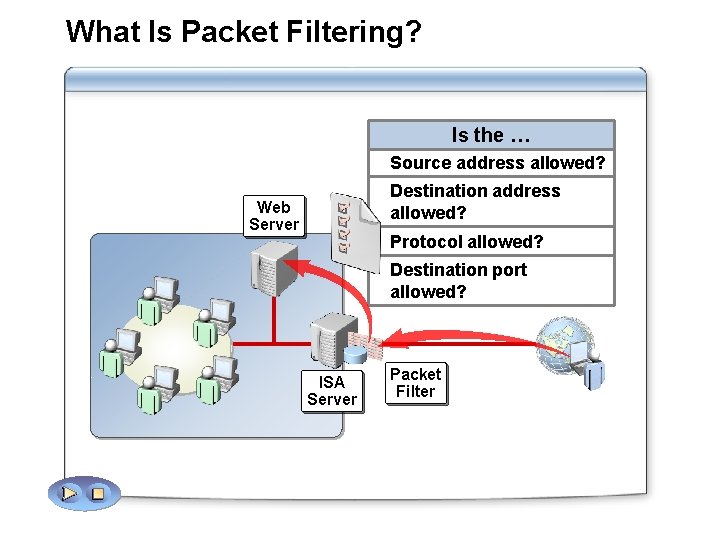
What Is Packet Filtering? Is the … Source address allowed? Destination address allowed? Web Server Protocol allowed? Destination port allowed? ISA Server Packet Filter

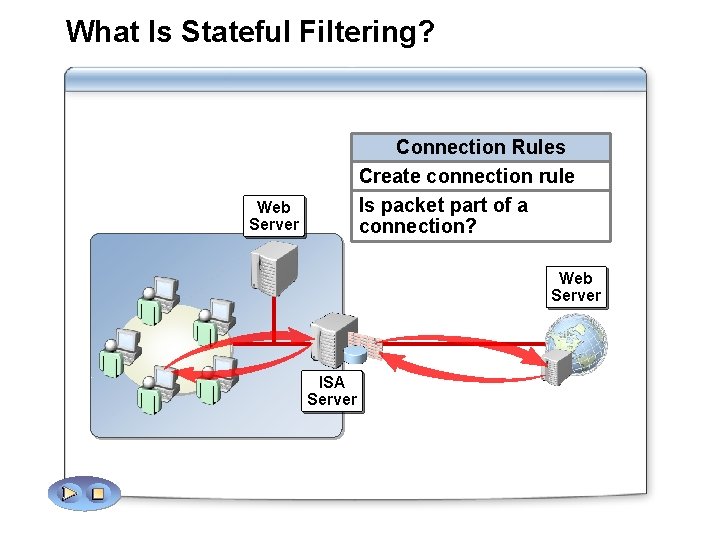
What Is Stateful Filtering? Connection Rules Create connection rule Is packet part of a connection? Web Server ISA Server

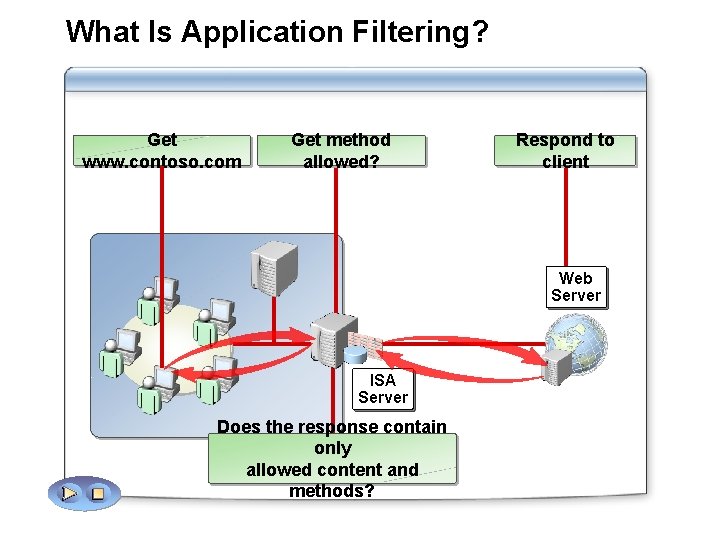
What Is Application Filtering? Get www. contoso. com Get method allowed? Respond to client Web Server ISA Server Does the response contain only allowed content and methods?

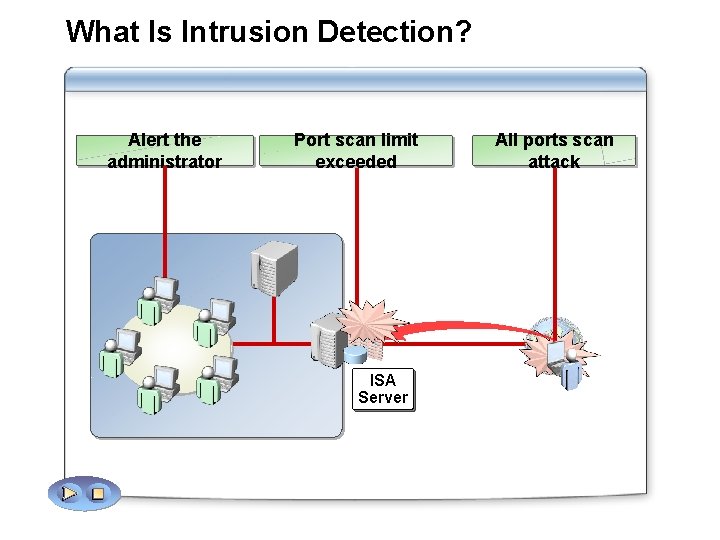
What Is Intrusion Detection? Alert the administrator Port scan limit exceeded ISA Server All ports scan attack

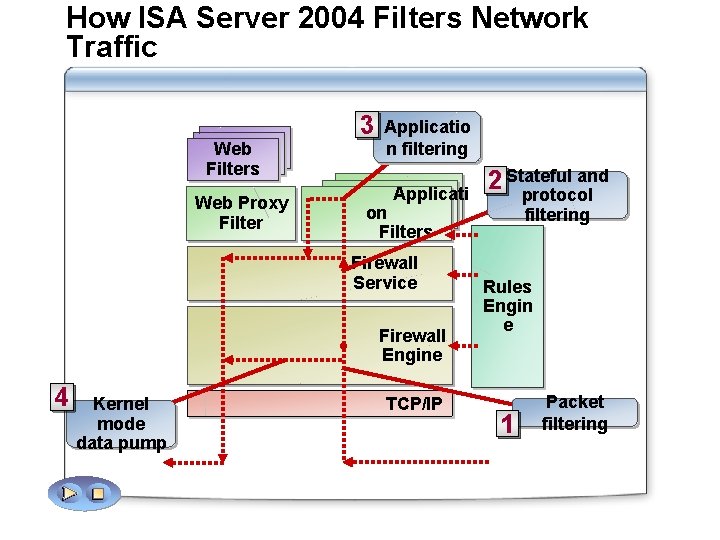
How ISA Server 2004 Filters Network Traffic Web Filters Web Proxy Filter 3 Applicatio n filtering Applicati on Filters Firewall Service Firewall Engine 4 Kernel mode data pump TCP/IP and 2 Stateful protocol filtering Rules Engin e 1 Packet filtering

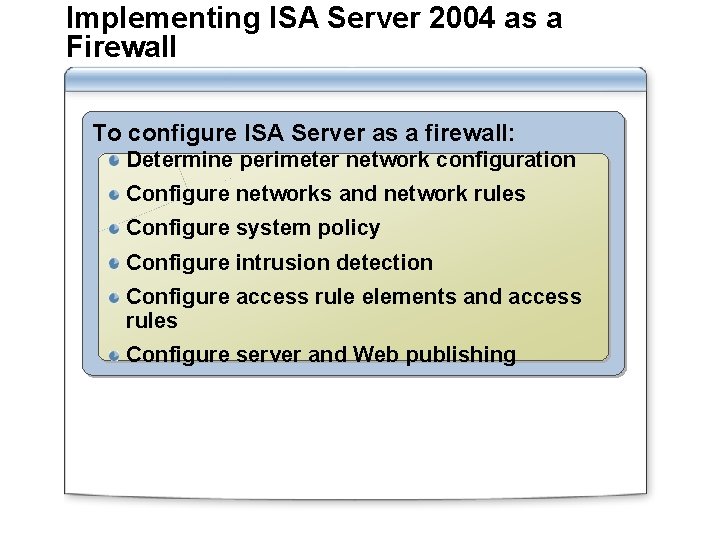
Implementing ISA Server 2004 as a Firewall To configure ISA Server as a firewall: Determine perimeter network configuration Configure networks and network rules Configure system policy Configure intrusion detection Configure access rule elements and access rules Configure server and Web publishing

Practice: Applying Firewall Concepts In this practice, you will analyze three scenarios describing an organization’s network security requirements and determine what firewall functionality is required in each scenario

Lesson: Examining Perimeter Networks and Templates What Is a Perimeter Network? Why Use a Perimeter Network? Network Perimeter Configurations About Network Templates How to Use the Network Template Wizard Modifying Rules Applied by Network Templates

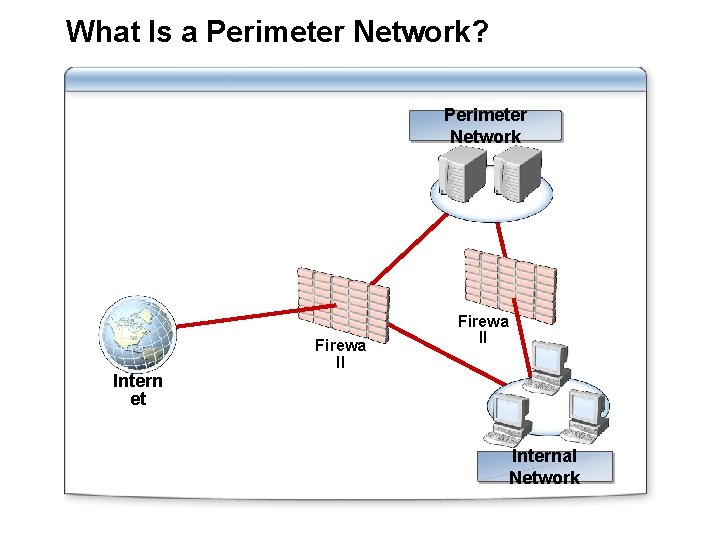
What Is a Perimeter Network? Perimeter Network Intern et Firewa ll Internal Network

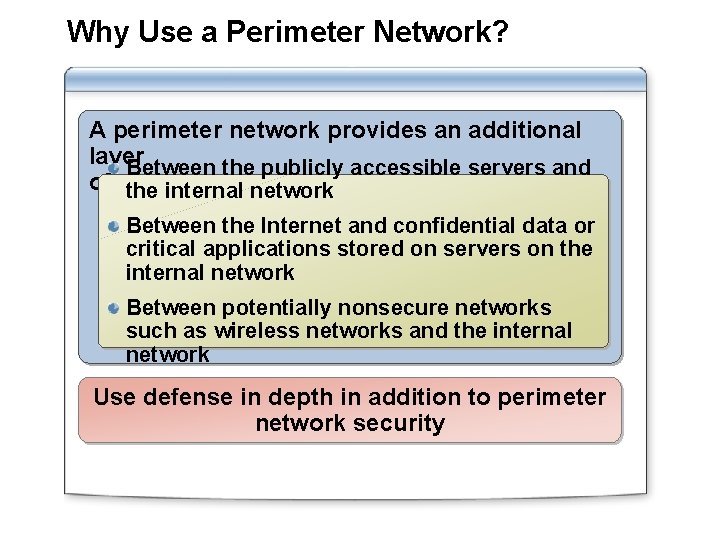
Why Use a Perimeter Network? A perimeter network provides an additional layer Between the publicly accessible servers and of security: the internal network Between the Internet and confidential data or critical applications stored on servers on the internal network Between potentially nonsecure networks such as wireless networks and the internal network Use defense in depth in addition to perimeter network security

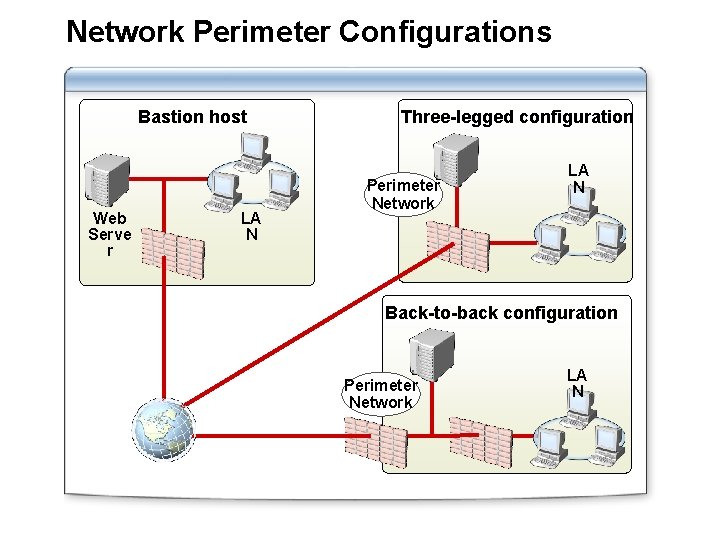
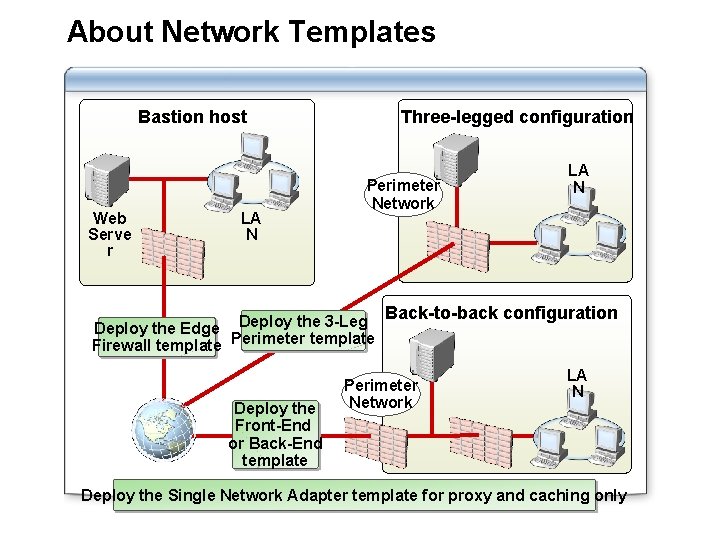
Network Perimeter Configurations Bastion host Web Serve r LA N Three-legged configuration Perimeter Network LA N Back-to-back configuration Perimeter Network LA N

About Network Templates Bastion host Web Serve r LA N Three-legged configuration Perimeter Network Deploy the Edge Deploy the 3 -Leg Firewall template Perimeter template Deploy the Front-End or Back-End template LA N Back-to-back configuration Perimeter Network LA N Deploy the Single Network Adapter template for proxy and caching only

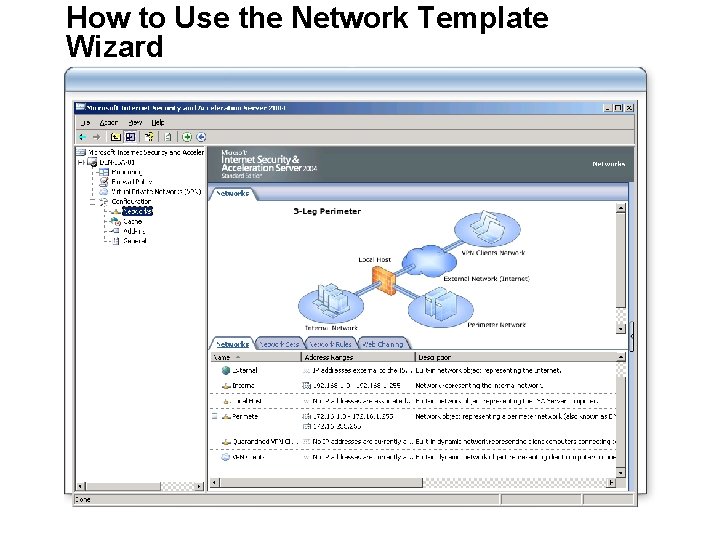
How to Use the Network Template Wizard

Modifying Rules Applied by Network Templates You may need to modify the rules applied by a network template to: Modify Internet access based on user or computer sets Modify Internet access based on protocols Modify network rules to change network relationships You can either change the properties of one of the rules configured by the network template, or you can create a new access rule to apply a specific setting

Practice: Implementing Network Templates Applying the 3 -Legged Network Template Reviewing the Access Rules Created by the 3 -Legged Network Template Testing Internet Access Den-ISA-01 Den-Clt-01 Den-DC-01 Gen-Web-01 Internet

Lesson: Configuring System Policies What Is System Policy? System Policy Settings How to Modify System Policy Settings

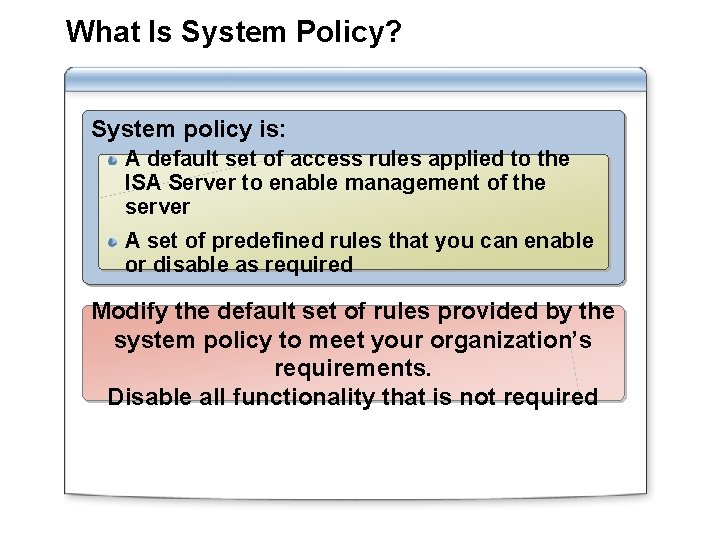
What Is System Policy? System policy is: A default set of access rules applied to the ISA Server to enable management of the server A set of predefined rules that you can enable or disable as required Modify the default set of rules provided by the system policy to meet your organization’s requirements. Disable all functionality that is not required

System Policy Settings System policy settings include: Network Services Authentication Services Remote Management Firewall Client Diagnostic Services Logging and Monitoring SMTP Scheduled Download Jobs Allowed Sites

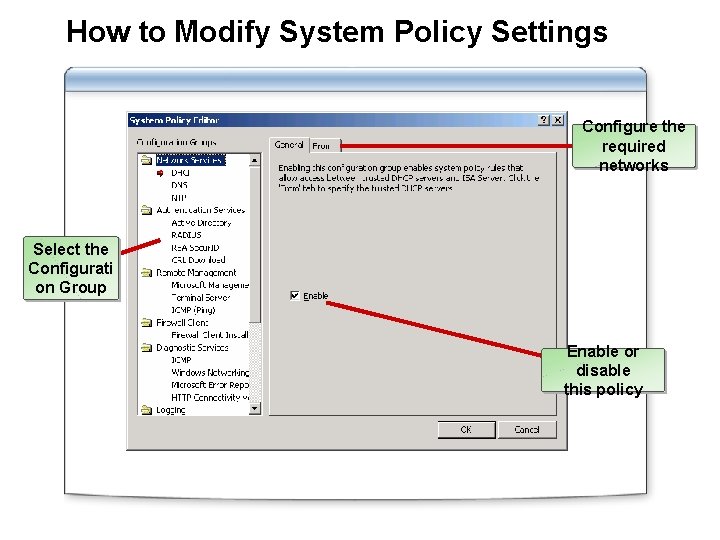
How to Modify System Policy Settings Configure the required networks Select the Configurati on Group Enable or disable this policy

Practice: Modifying System Policy Examining and modifying the default system policy Testing the modified system policy Den-ISA-01 Den-Clt-01 Den-DC-01 Internet

Lesson: Configuring Intrusion Detection and IP Preferences About Intrusion Detection Configuration Options How to Configure Intrusion Detection About IP Preferences Configuration Options How to Configure IP Preferences

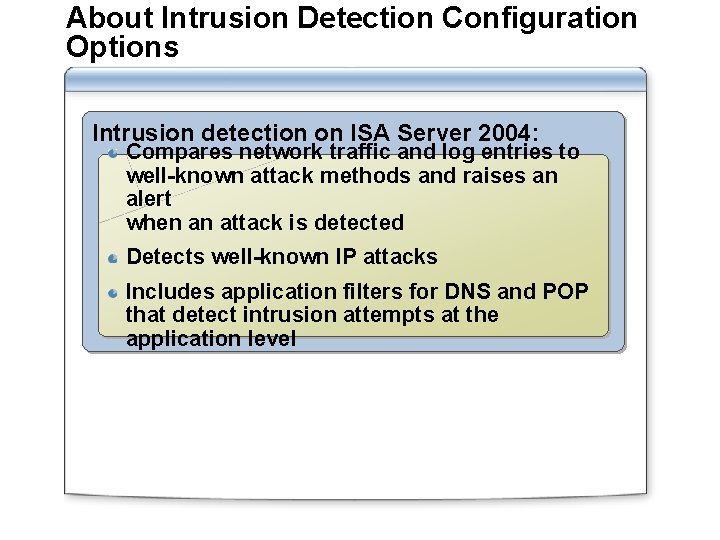
About Intrusion Detection Configuration Options Intrusion detection on ISA Server 2004: Compares network traffic and log entries to well-known attack methods and raises an alert when an attack is detected Detects well-known IP attacks Includes application filters for DNS and POP that detect intrusion attempts at the application level

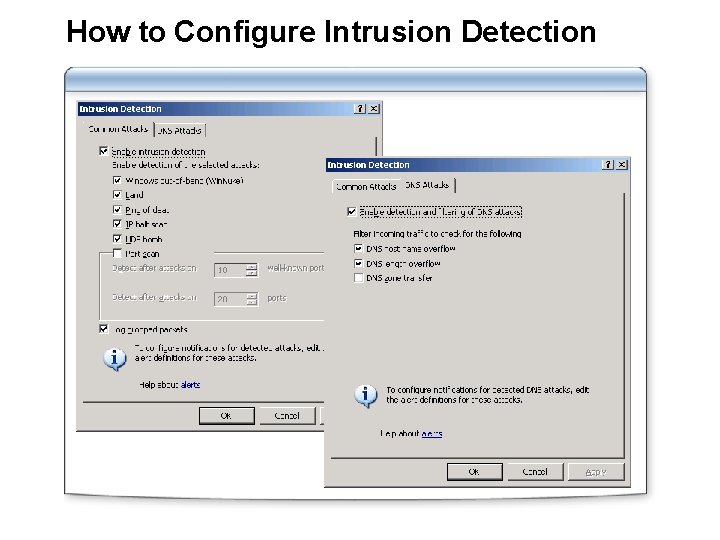
How to Configure Intrusion Detection

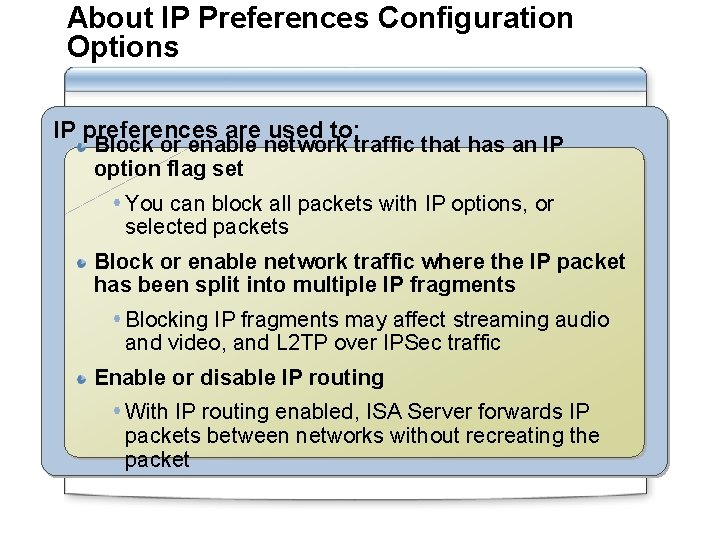
About IP Preferences Configuration Options IP preferences are used to: Block or enable network traffic that has an IP option flag set You can block all packets with IP options, or selected packets Block or enable network traffic where the IP packet has been split into multiple IP fragments Blocking IP fragments may affect streaming audio and video, and L 2 TP over IPSec traffic Enable or disable IP routing With IP routing enabled, ISA Server forwards IP packets between networks without recreating the packet

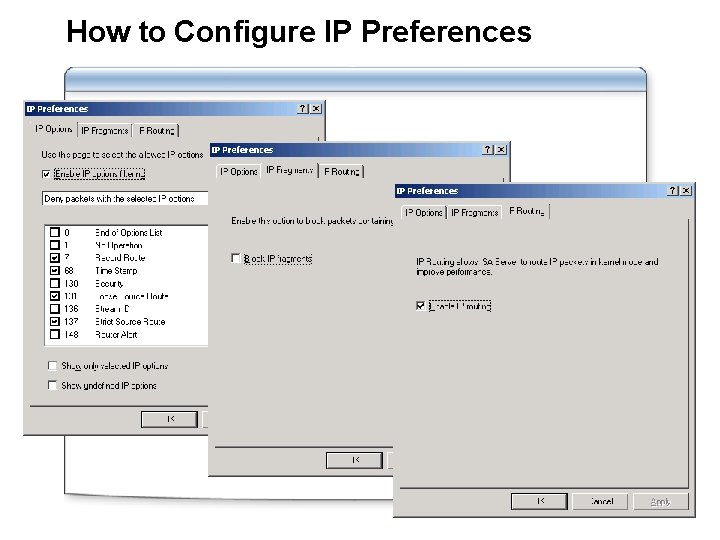
How to Configure IP Preferences

Practice: Configuring Intrusion Detection Modify the default intrusion detection configuration Test intrusion detection Gen-Web-01 Den-ISA-01 Internet Den-Clt-01 Den-DC-01

Lab: Configuring ISA Server as a Firewall Exercise 1: Restoring Firewall Access Rules Exercise 2: Modifying the ISA Server System Policy Exercise 3: Testing the Policy Modifications Den-ISA-01 Den-DC-01 Internet Den-ISA-02