Configuring ISA Server as a Firewall 1 Understanding





- Slides: 26

Configuring ISA Server as a Firewall 1

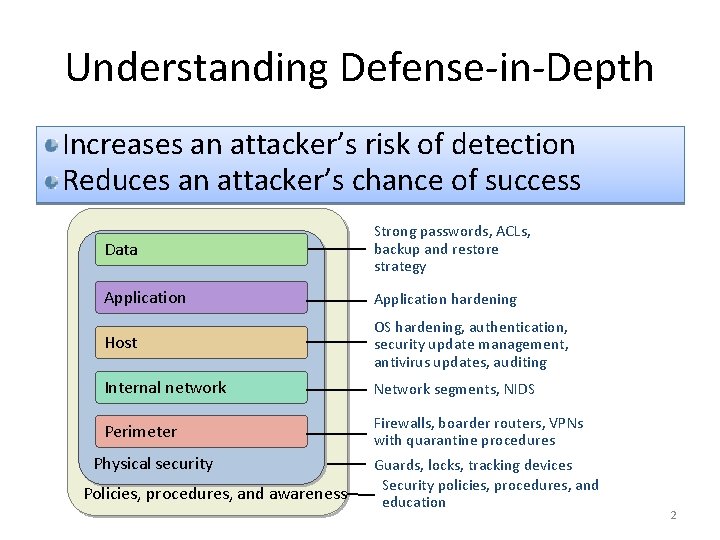
Understanding Defense-in-Depth Increases an attacker’s risk of detection Reduces an attacker’s chance of success Data Strong passwords, ACLs, backup and restore strategy Application hardening Host OS hardening, authentication, security update management, antivirus updates, auditing Internal network Network segments, NIDS Perimeter Firewalls, boarder routers, VPNs with quarantine procedures Physical security Policies, procedures, and awareness Guards, locks, tracking devices Security policies, procedures, and education 2

Firewall 3

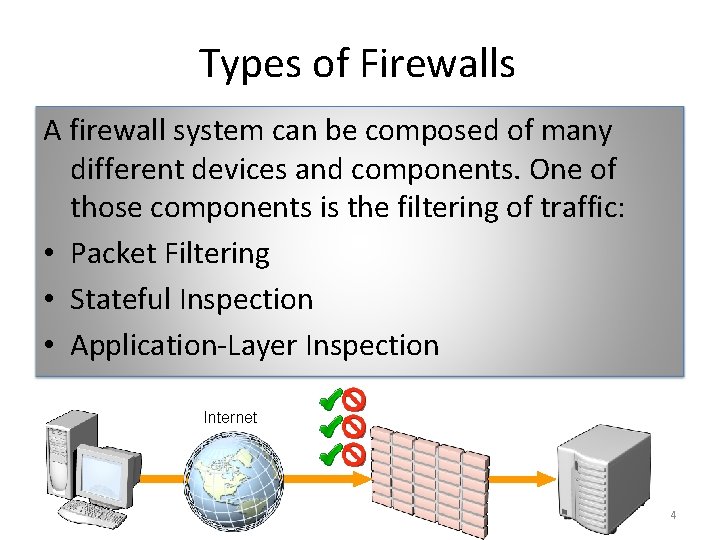
Types of Firewalls A firewall system can be composed of many different devices and components. One of those components is the filtering of traffic: • Packet Filtering • Stateful Inspection • Application-Layer Inspection Internet 4

Packet Filtering • Control access to the network at the network layer by inspecting and allowing or denying the Internet Protocol (IP) packets • Examine only information in the network and transport layer headers 5

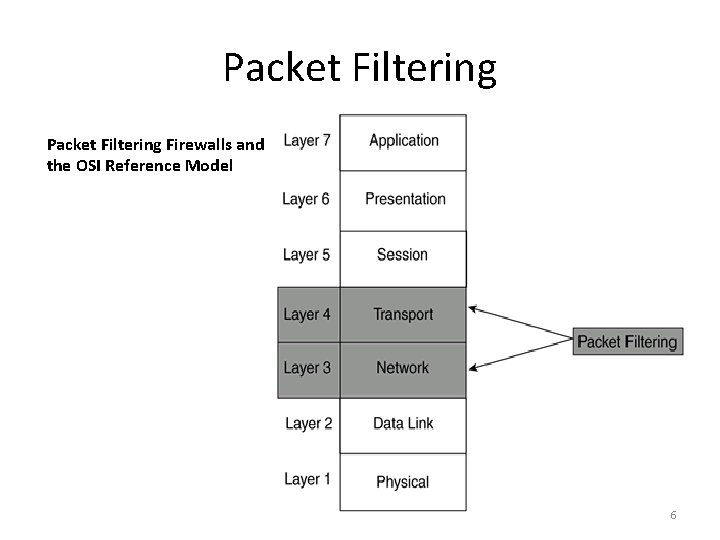
Packet Filtering Firewalls and the OSI Reference Model 6

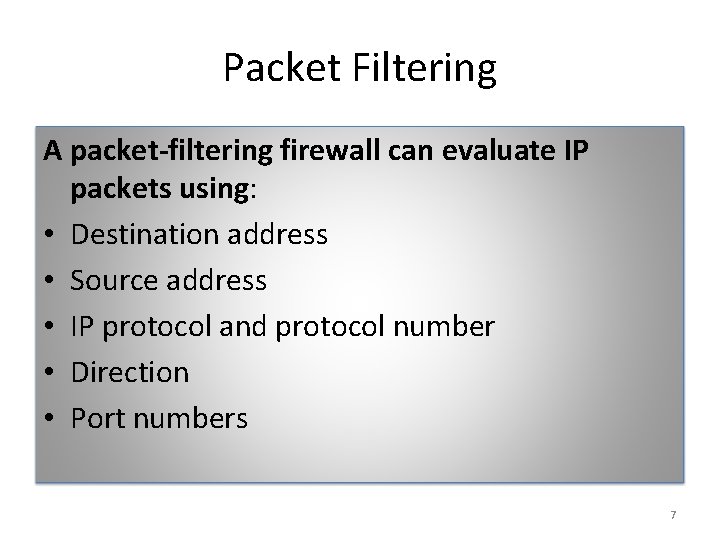
Packet Filtering A packet-filtering firewall can evaluate IP packets using: • Destination address • Source address • IP protocol and protocol number • Direction • Port numbers 7

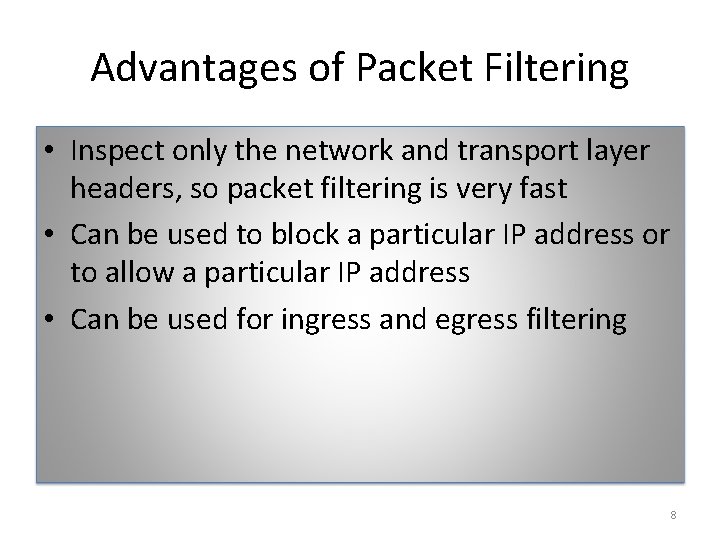
Advantages of Packet Filtering • Inspect only the network and transport layer headers, so packet filtering is very fast • Can be used to block a particular IP address or to allow a particular IP address • Can be used for ingress and egress filtering 8

Disadvantages of Packet Filtering • Packet filters cannot prevent IP address spoofing or source-routing attacks • Packet filters cannot prevent IP-fragment attacks • Packet filters are not application-aware 9

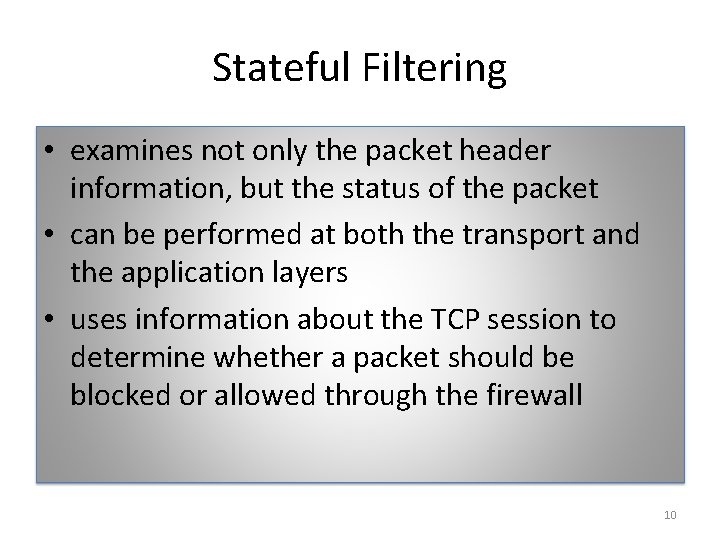
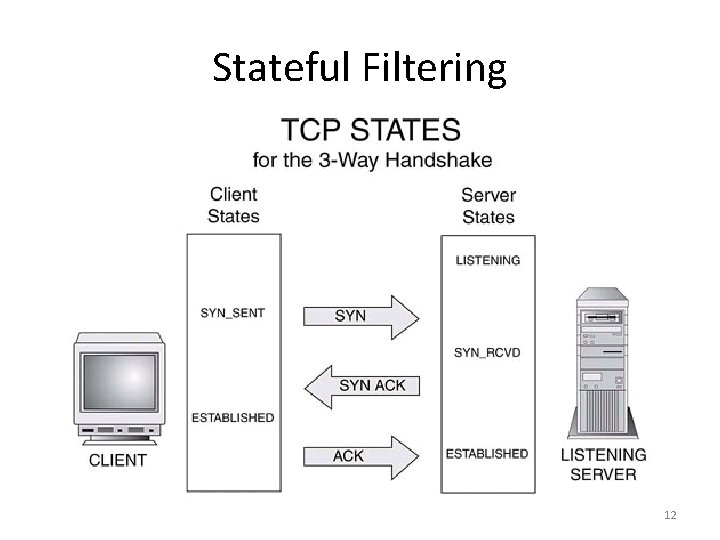
Stateful Filtering • examines not only the packet header information, but the status of the packet • can be performed at both the transport and the application layers • uses information about the TCP session to determine whether a packet should be blocked or allowed through the firewall 10

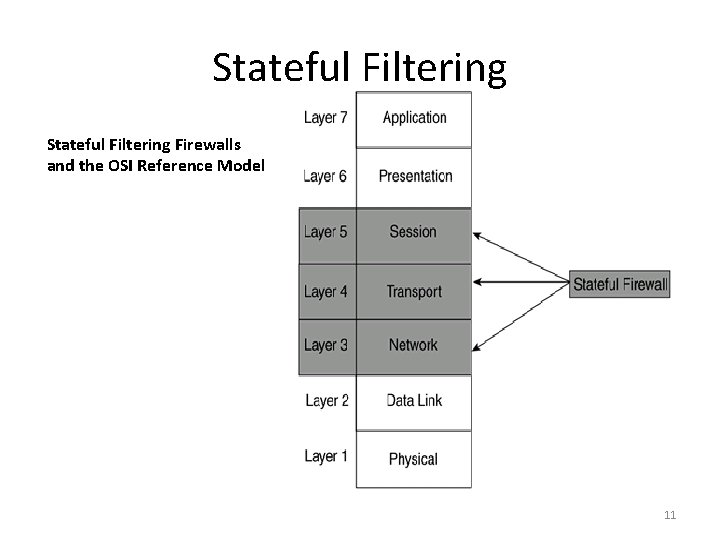
Stateful Filtering Firewalls and the OSI Reference Model 11

Stateful Filtering 12

Stateful Filtering • Stateful filtering ensures that all network traffic forwarded by the firewall is part of an existing session, or matches the rules for creating a new session. • Stateful filtering still does not provide enough protection against the threats to network security • A client computer may download malicious code in an HTTP packet that is part of a legitimate session!! 13

Application-Layer Filtering • inspect the application data in a TCP/IP packet for unacceptable commands and data • Can be used to stop attacks from sources such as viruses and worms!! 14

Intrusion Detection • Detect when an attack against a network is attempted or in progress • If you detect an intrusion attempt early enough, you may be able to prevent a successful intrusion • If an intrusion does occur, you must be alerted as soon as possible to reduce the potential impact of the intrusion and to eliminate the vulnerability in your network security. 15

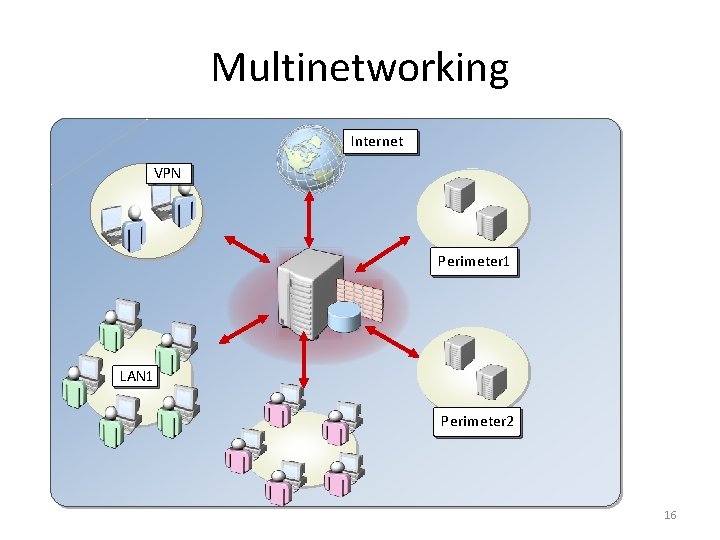
Multinetworking Internet VPN Perimeter 1 LAN 2 Perimeter 2 16

Multinetworking with ISA 2006 • Support any Number of Networks • VPN Networks Represented as Networks • Dynamic Network Membership • Per Network Rules • Per Network Policies • Network Sets 17

Network Templates • • • Edge Firewall 3 -Leg Perimeter Front Firewall Back Firewall Single Network Adapter 18

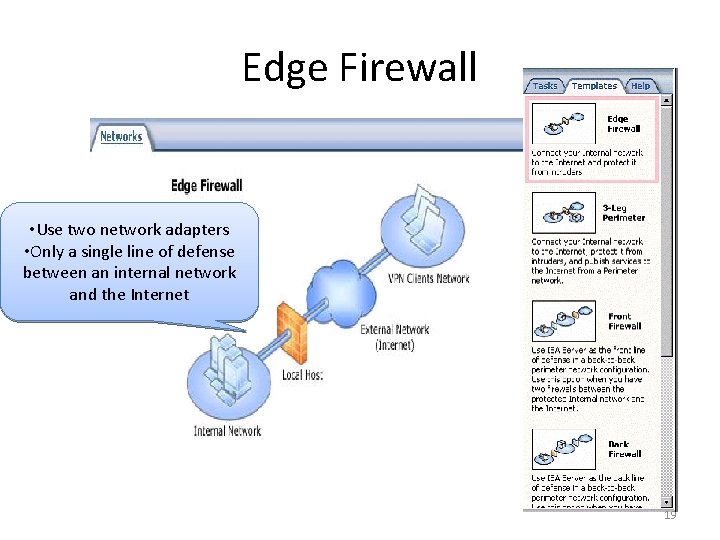
Edge Firewall • Use two network adapters • Only a single line of defense between an internal network and the Internet 19

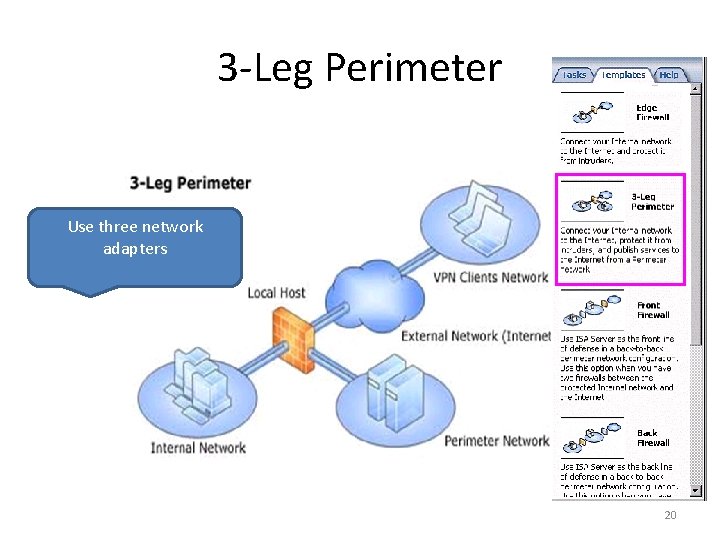
3 -Leg Perimeter Use three network adapters 20

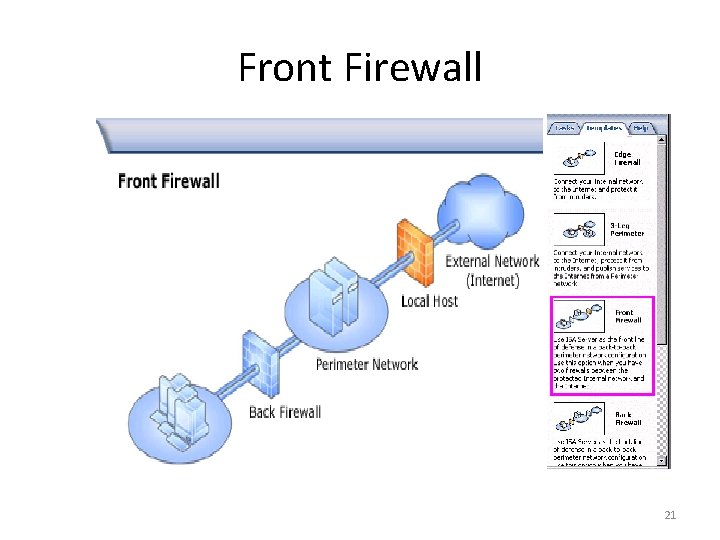
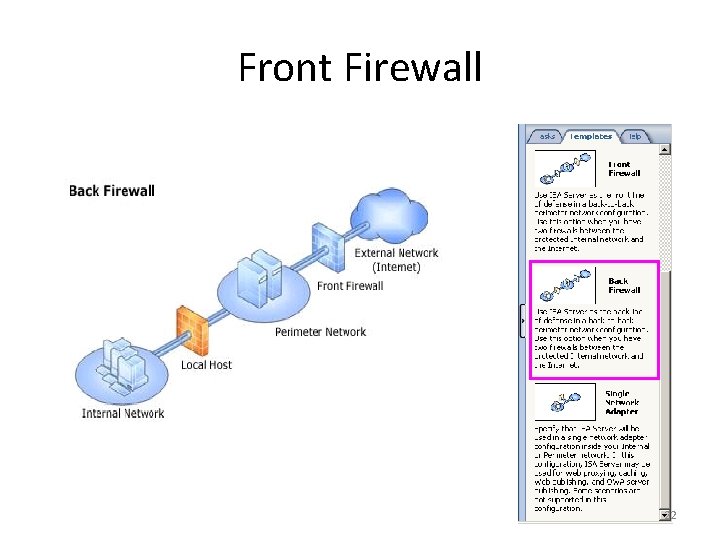
Front Firewall 21

Front Firewall 22

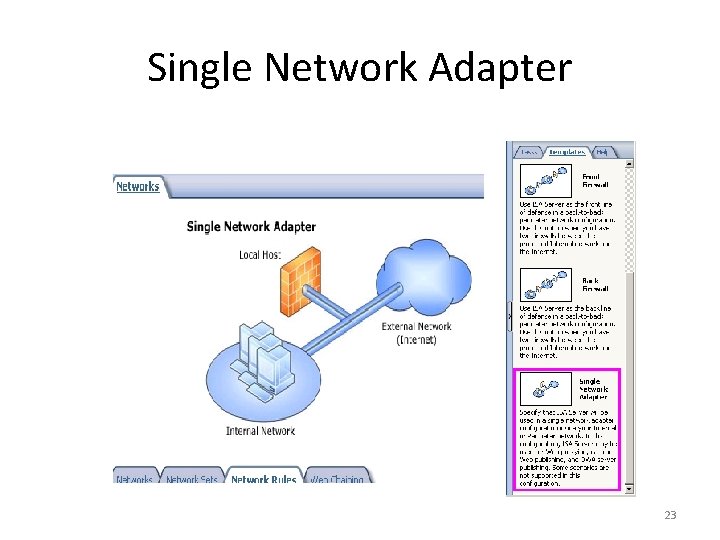
Single Network Adapter 23

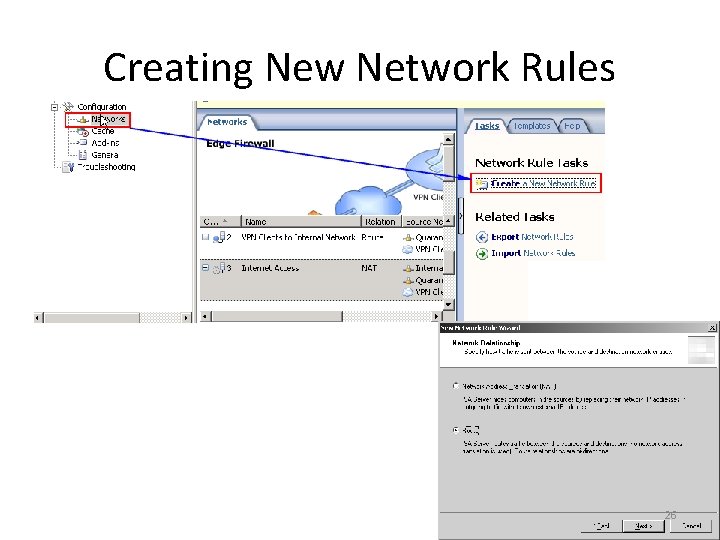
Network Rules • Define the relationships that exist between the various defined ISA networks • Two types of relationships can be defined as part of ISA network rules • The two forms of network relationships: – Network Address Translation (NAT) – Route 24

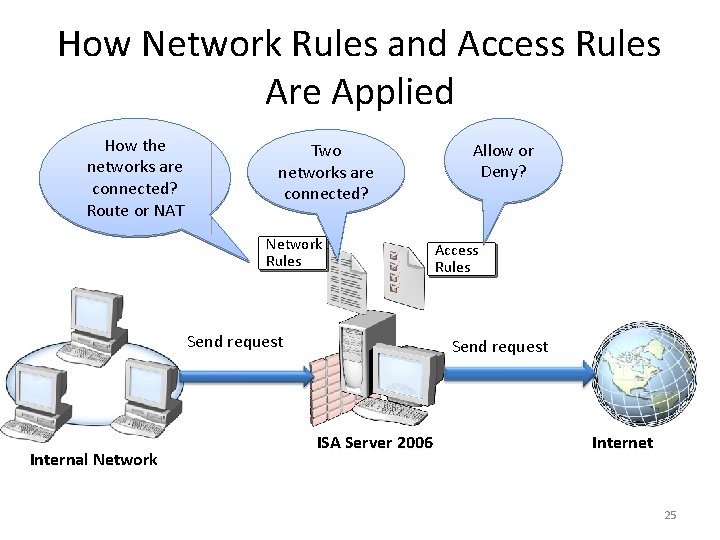
How Network Rules and Access Rules Are Applied How the networks are connected? Route or NAT Two networks are connected? Network Rules Send request Internal Network Allow or Deny? Access Rules Send request ISA Server 2006 Internet 25

Creating New Network Rules 26