Integrating ISA Server and Exchange Server 1 How







- Slides: 34

Integrating ISA Server and Exchange Server 1

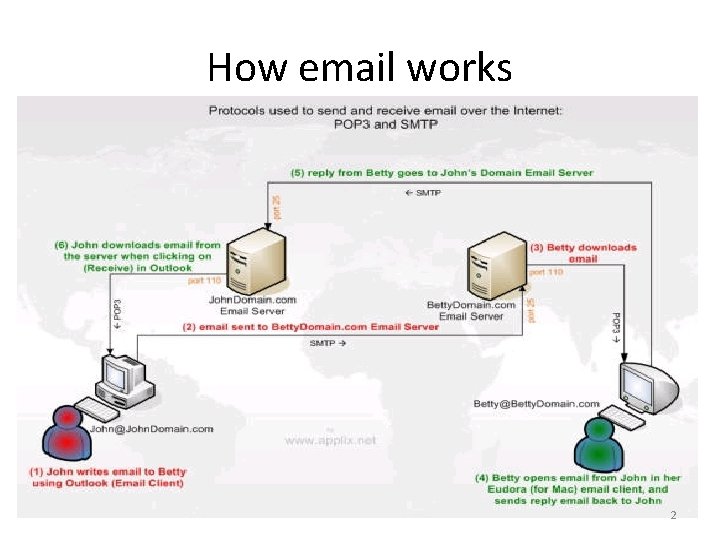
How email works 2

Mail server • An mail server is typically a combination of processes running on a server with a large storage capacity – a list of users and rules, and the capability to receive, send and store emails and attachments • Mail server software: Mdeamon, Exchange server 2003, … 3

Why use Exchange 2003 • • • Backup and restore High availability Help migrating from older systems Security improvements Protection of e-mail 4

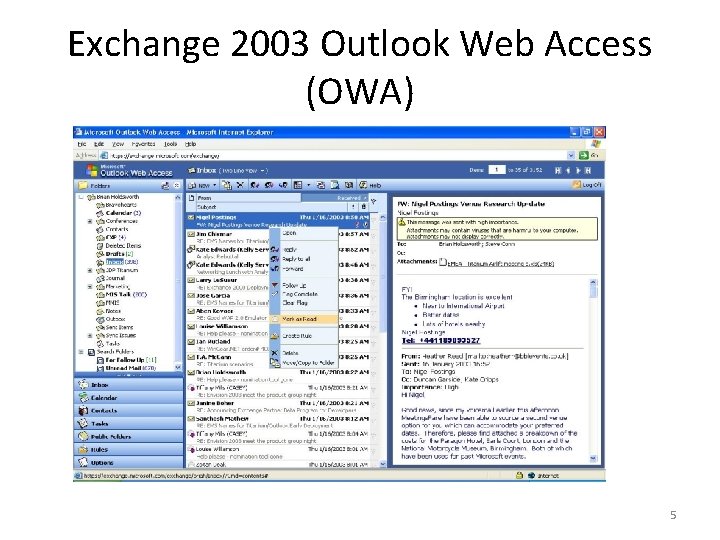
Exchange 2003 Outlook Web Access (OWA) 5

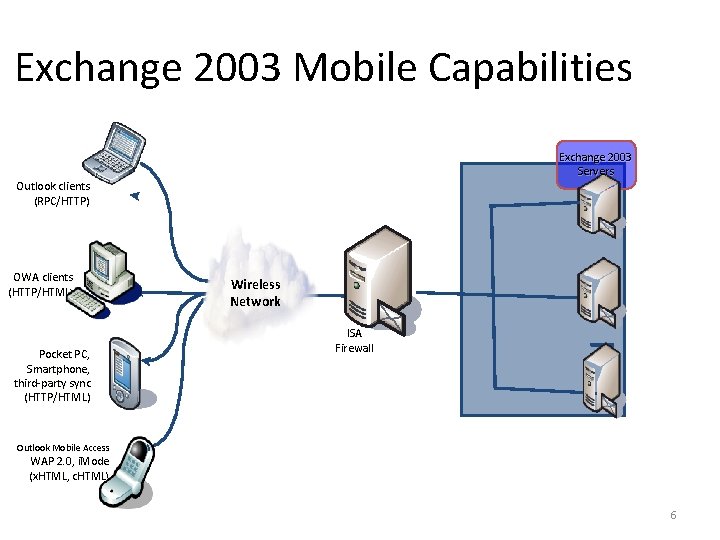
Exchange 2003 Mobile Capabilities Exchange 2003 Servers Outlook clients (RPC/HTTP) OWA clients (HTTP/HTML) Pocket PC, Smartphone, third-party sync (HTTP/HTML) Wireless Network ISA Firewall Outlook Mobile Access WAP 2. 0, i. Mode (x. HTML, c. HTML) 6

The goal of attack • • Steal data Blackmail Launch bed for others attack Bragging rights Vandalism Demonstrate vulnerability/satisfy curiosity Damage company reputation Others? 7

Exchange 2003 and ISA 2006 Securing SMTP Traffic: • SMTP-based attacks: – Invalid, overly long, or unusual SMTP commands to attack a mail server or to gather recipient information – Attacks against recipients by including malicious content, such as worms • ISA Server protects mail servers by: – Enforcing compliance of SMTP commands with standards – Blocking disallowed SMTP commands – Blocking messages with disallowed attachment types, content, recipient or sender • ISA Server can stop attacks before they reach your mail servers!! 8

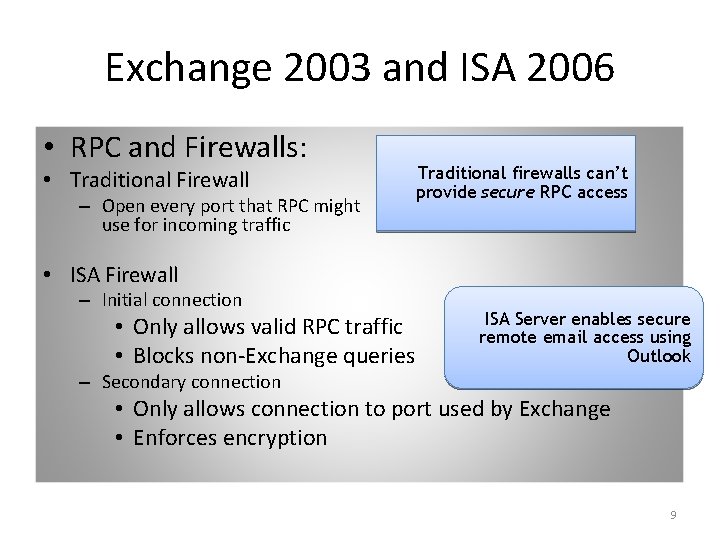
Exchange 2003 and ISA 2006 • RPC and Firewalls: • Traditional Firewall – Open every port that RPC might use for incoming traffic Traditional firewalls can’t provide secure RPC access • ISA Firewall – Initial connection • Only allows valid RPC traffic • Blocks non-Exchange queries ISA Server enables secure remote email access using Outlook – Secondary connection • Only allows connection to port used by Exchange • Enforces encryption 9

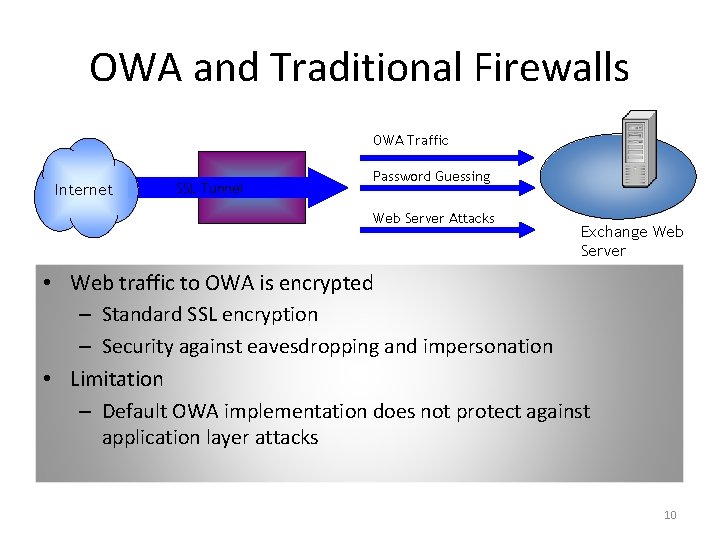
OWA and Traditional Firewalls OWA Traffic Internet SSL Tunnel Password Guessing Web Server Attacks Exchange Web Server • Web traffic to OWA is encrypted – Standard SSL encryption – Security against eavesdropping and impersonation • Limitation – Default OWA implementation does not protect against application layer attacks 10

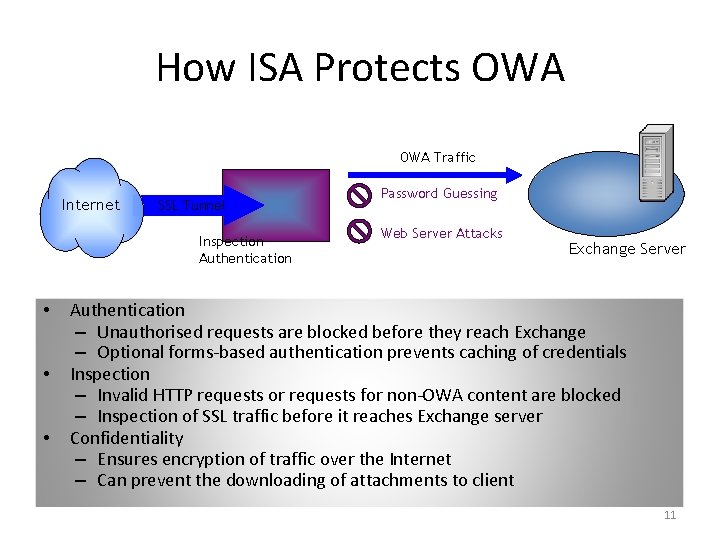
How ISA Protects OWA Traffic Internet SSL Tunnel Inspection Authentication • • • Password Guessing Web Server Attacks Exchange Server Authentication – Unauthorised requests are blocked before they reach Exchange – Optional forms-based authentication prevents caching of credentials Inspection – Invalid HTTP requests or requests for non-OWA content are blocked – Inspection of SSL traffic before it reaches Exchange server Confidentiality – Ensures encryption of traffic over the Internet – Can prevent the downloading of attachments to client 11

Publishing Exchange Server with ISA 2006 12

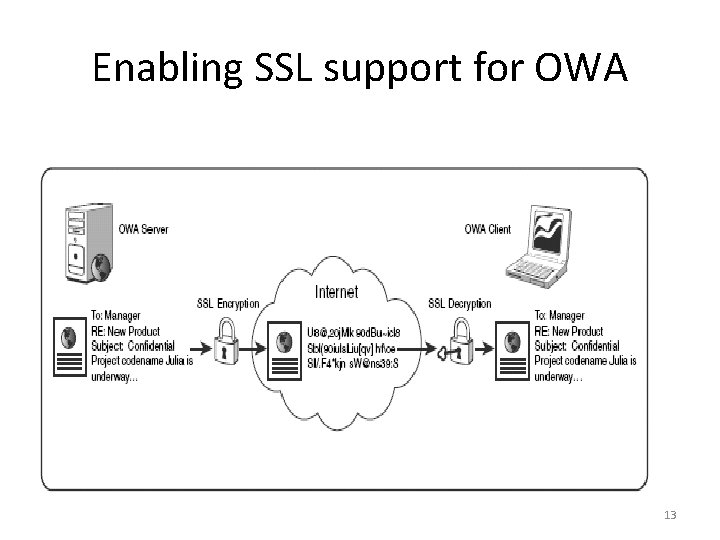
Enabling SSL support for OWA 13

Understanding the Need for Third. Party CAs • can buy a certificate from a third-party certificate authority such as Verisign, Thawte, or one of many other enterprise certificate authorities • validate that their customers are really who they say they are, and to generate the digital certificates that validate this for digital communications • that require encryption, such as SSL 14

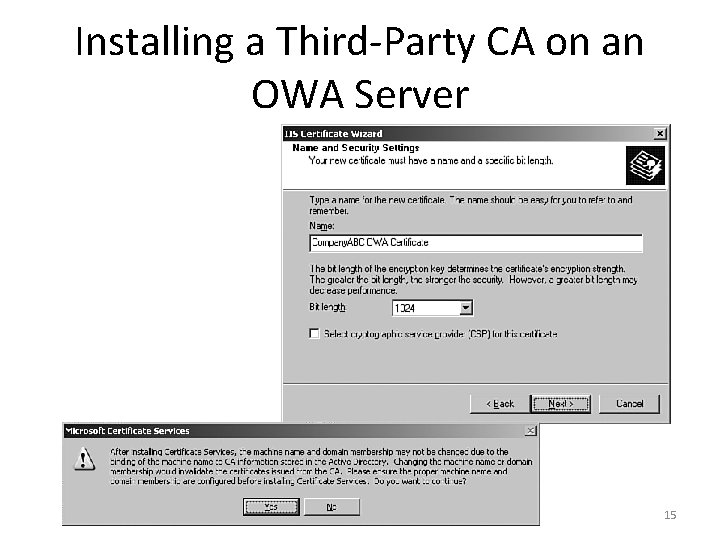
Installing a Third-Party CA on an OWA Server 15

Type of CA • Enterprise root CA: highest-level certificate authority for an organization • Enterprise subordinate CA: subordinate to an existing enterprise root CA, and must receive a certificate from that root CA to work properly • Stand-alone root CA: similar to an enterprise CA, in that it provides for its own unique identity and can be uniquely configured 16

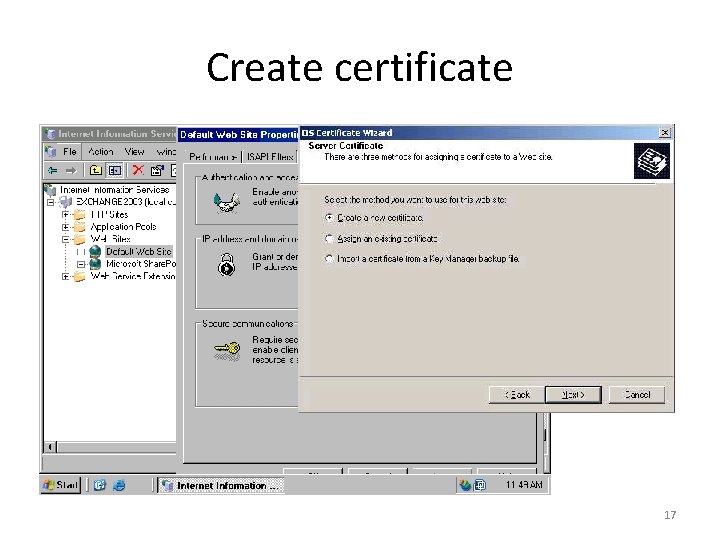
Create certificate 17

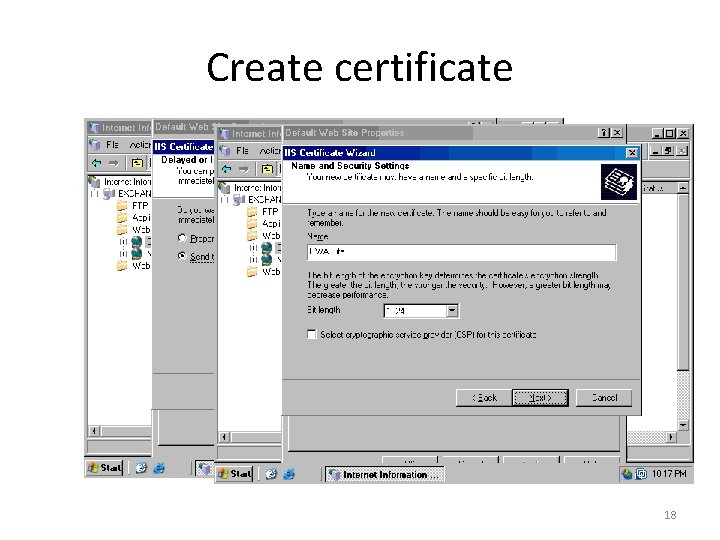
Create certificate 18

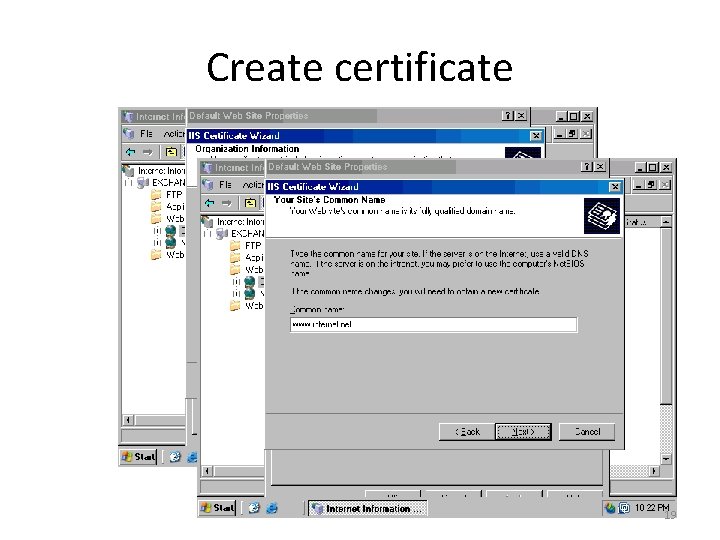
Create certificate 19

Create certificate 20

Create certificate 21

Exporting and Importing the OWA Certificate to the ISA Server On OWA server 22

Exporting and Importing the OWA Certificate to the ISA Server On ISA server, open MMC console 23

Exporting and Importing the OWA Certificate to the ISA Server 24

Exporting and Importing the OWA Certificate to the ISA Server 25

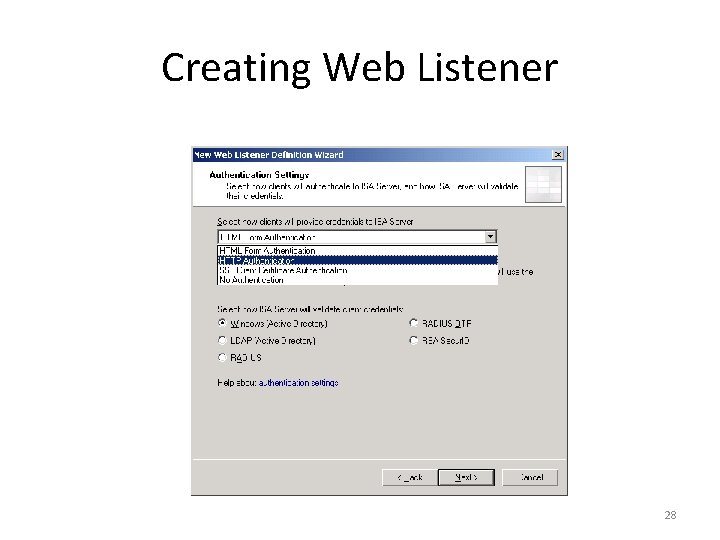
Creating Web Listener 26

Creating Web Listener 27

Creating Web Listener 28

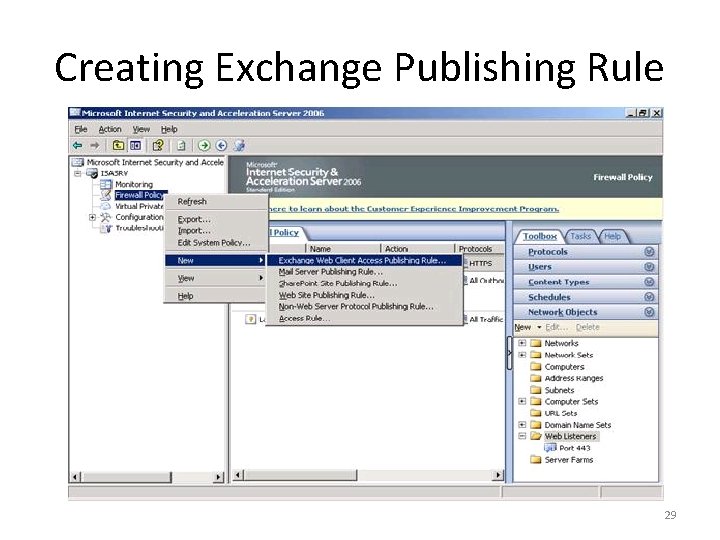
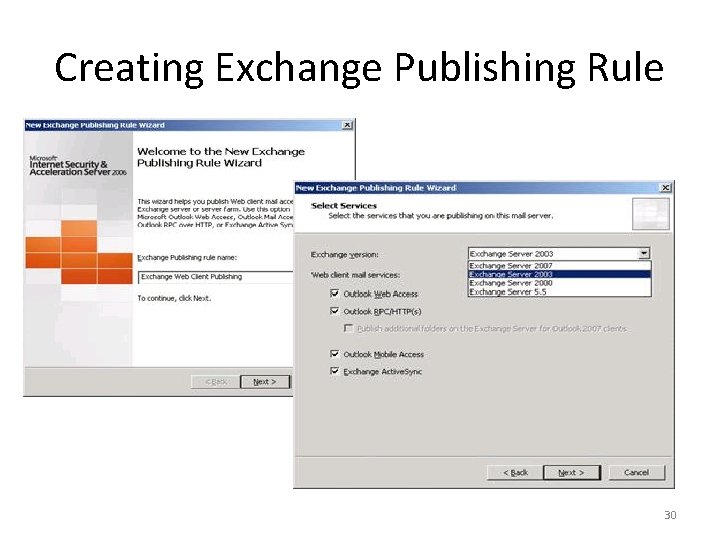
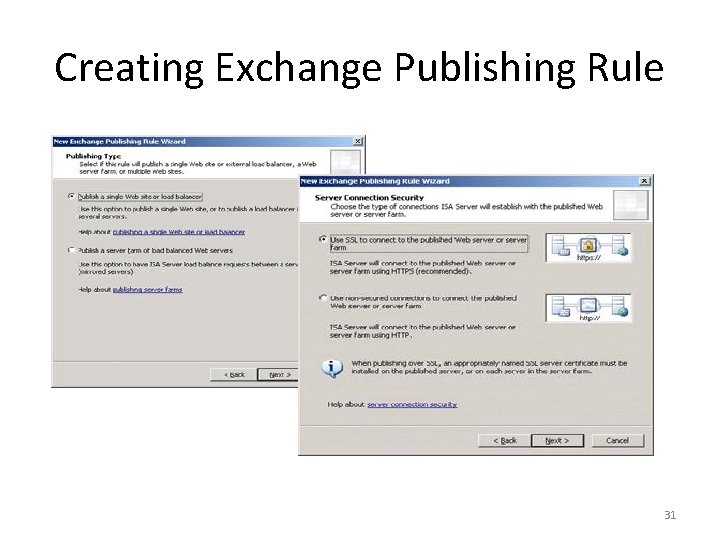
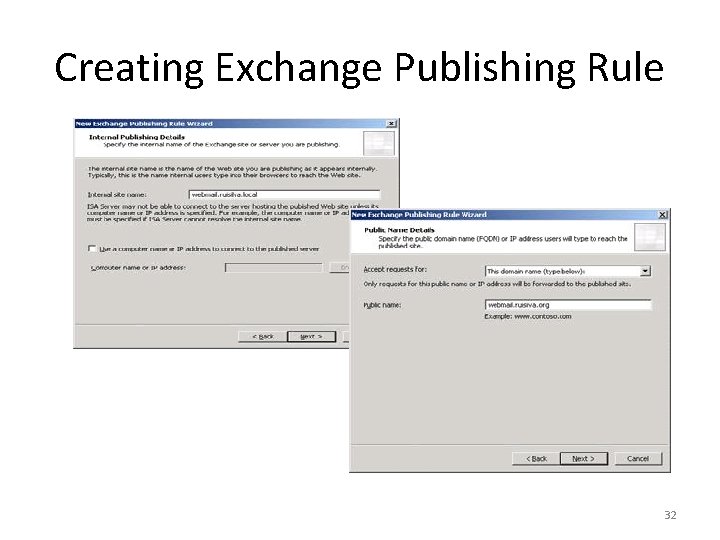
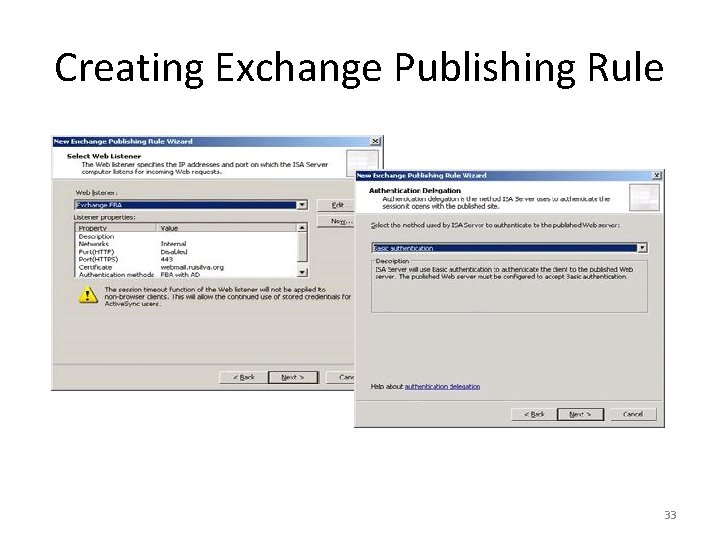
Creating Exchange Publishing Rule 29

Creating Exchange Publishing Rule 30

Creating Exchange Publishing Rule 31

Creating Exchange Publishing Rule 32

Creating Exchange Publishing Rule 33

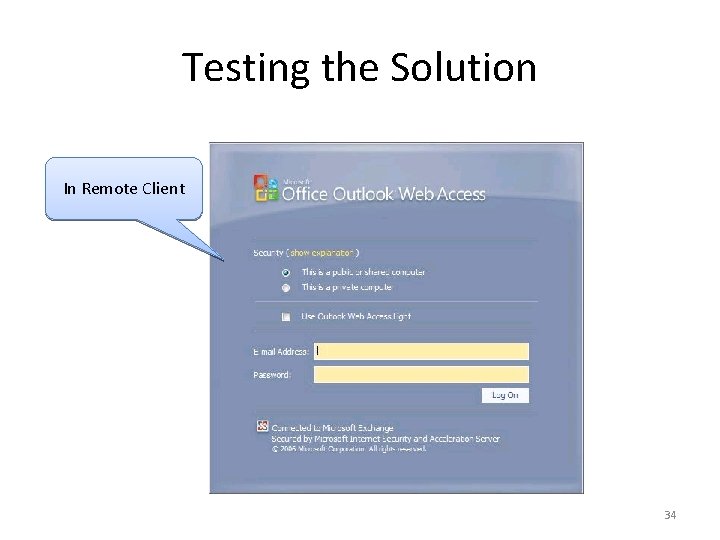
Testing the Solution In Remote Client 34