Firewall Exercise Firewall Exercise In this exercise you




- Slides: 6

Firewall Exercise

Firewall Exercise • In this exercise, you are given a set-up scenario from which you must determine how firewall rules would be written • The scenario describes the pertinent details of a small network, including specific addresses and port numbers • Your task is to determine if the inbound firewall rules on the last slide of this presentation are correct as written, or if they need to be changed in order to be correct • If they need to be changed, please note the change you would make to correct the rule

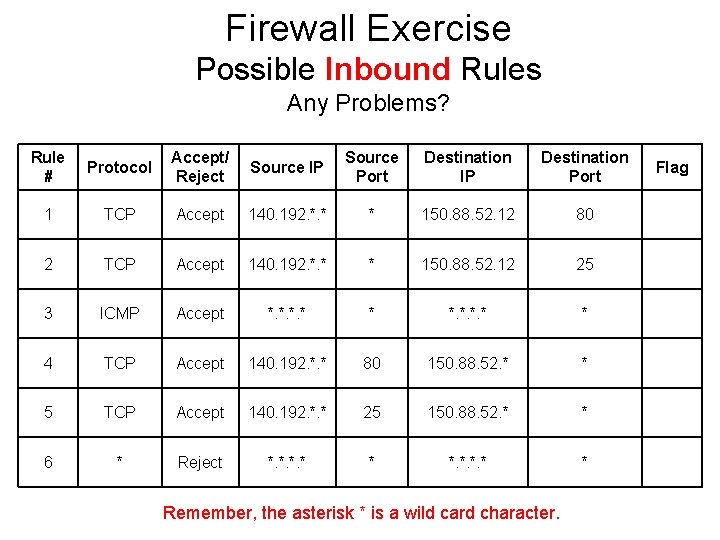
Firewall Exercise • Assume you have a small network at 150. 88. 52. 0/24 subnet • Your web/e-mail server is at address 150. 88. 52. 12 • You want only http: (port 80) and e-mail (port 25) requests from De. Paul clients to come into your site • You want your internal users to be able to access http: and email services from De. Paul servers only • You want to allow ICMP “pings” • Given this scenario, take a look at the next slide and tell me which of the inbound rules shown there are okay, and which are not • For the ones that are NOT okay, what would you do to fix them? • Remember, you want rules that allow the above criteria, and nothing else!

Firewall Exercise Possible Inbound Rules Any Problems? Rule # Protocol Accept/ Reject Source IP Source Port Destination IP Destination Port 1 TCP Accept 140. 192. *. * * 150. 88. 52. 12 80 2 TCP Accept 140. 192. *. * * 150. 88. 52. 12 25 3 ICMP Accept *. * * 4 TCP Accept 140. 192. *. * 80 150. 88. 52. * * 5 TCP Accept 140. 192. *. * 25 150. 88. 52. * * 6 * Reject *. * * Remember, the asterisk * is a wild card character. Flag

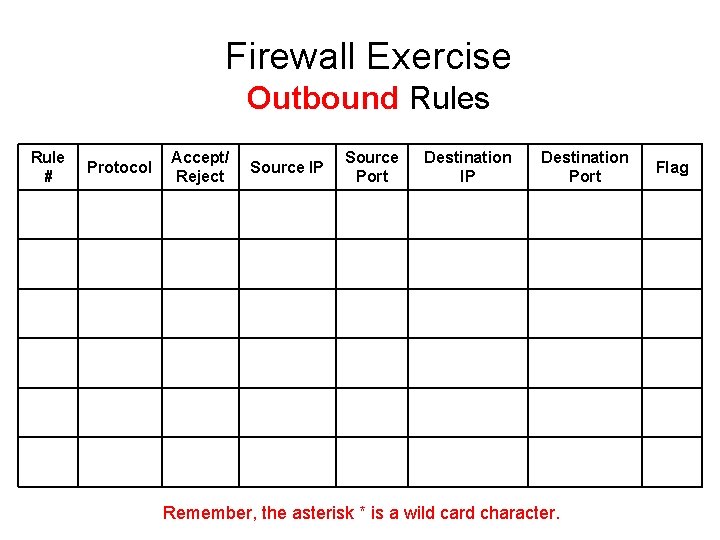
Firewall Exercise • Time to try writing firewall rules of your own! • Outbound rules explicitly allow, or explicitly block, network traffic originating from the computer that matches the criteria in the rule. For example, you can configure a rule to explicitly block outbound traffic to a computer (by IP address) through the firewall, but allow the same traffic for other computers. Because outbound traffic is allowed by default, you typically use outbound rules to block network traffic that you do not want. • Using the blank template on the last slide of this presentation, please write OUTBOUND firewall rules for the following: • Assume you have a small network at 169. 64. 98. 0/48 subnet • Your web/e-mail server is at address 169. 64. 98. 12 • You don’t want anyone on your network to access Facebook at all • You want to allow all ICMP messages sent out by your network • You want the computer at subnet 40 to be blocked from the Internet entirely • You don’t want anyone on your network to be able to send any messages to De. Paul

Firewall Exercise Outbound Rules Rule # Protocol Accept/ Reject Source IP Source Port Destination IP Destination Port Remember, the asterisk * is a wild card character. Flag