Visit for more Learning Resources Chapter 1 22















































































- Slides: 104

Visit for more Learning Resources

Chapter 1 (22 M) Introduction to computer security and security trends

Computer Security • Computer security is designed to protect your computer and everything associated with it the workstations and printers, cabling, and disks and other storage media. Most importantly, computer security protects the information stored in your system. • Computer security deals with prevention and detention of unauthorized actions of user at computer system. • It involves security majors such as a Data encryption, passwords, antivirus, firewalls etc.

Need /Model / CIA model of Security • The need of computer security has been threefold: confidentiality, integrity, and availability—the “CIA” of security. 1. Confidentiality: 2. Integrity: 3. Availability/Authentication


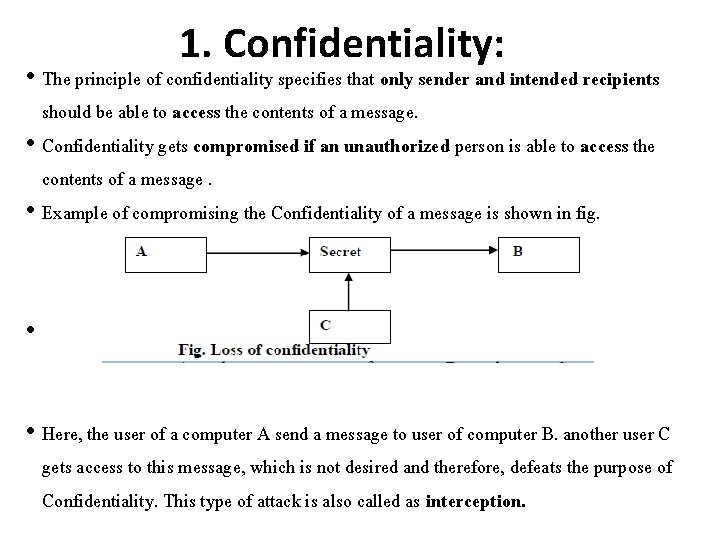
1. Confidentiality: • The principle of confidentiality specifies that only sender and intended recipients should be able to access the contents of a message. • Confidentiality gets compromised if an unauthorized person is able to access the contents of a message. • Example of compromising the Confidentiality of a message is shown in fig. • • Here, the user of a computer A send a message to user of computer B. another user C gets access to this message, which is not desired and therefore, defeats the purpose of Confidentiality. This type of attack is also called as interception.

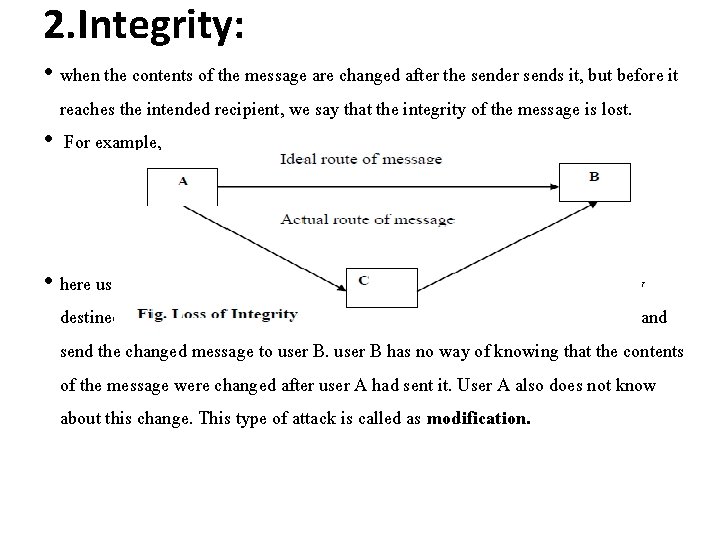
2. Integrity: • when the contents of the message are changed after the sender sends it, but before it reaches the intended recipient, we say that the integrity of the message is lost. • For example, • here user C tampers with a message originally sent by user A, which is actually destined for user B. user C somehow manages to access it, change its contents and send the changed message to user B has no way of knowing that the contents of the message were changed after user A had sent it. User A also does not know about this change. This type of attack is called as modification.

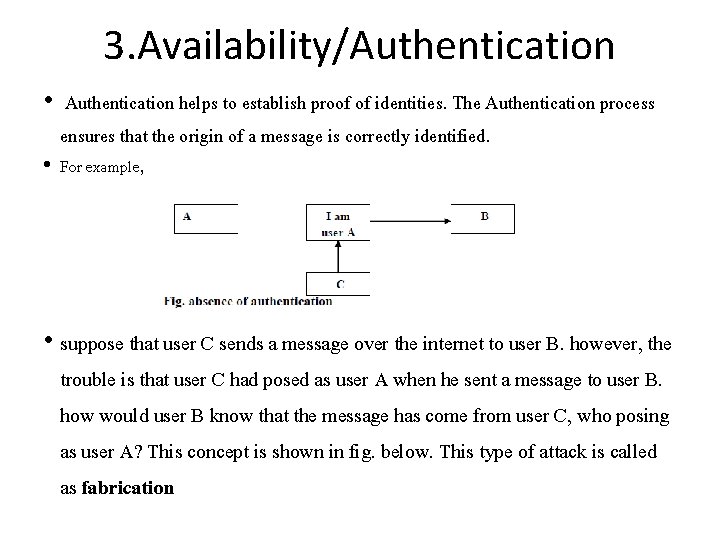
3. Availability/Authentication • Authentication helps to establish proof of identities. The Authentication process ensures that the origin of a message is correctly identified. • For example, • suppose that user C sends a message over the internet to user B. however, the trouble is that user C had posed as user A when he sent a message to user B. how would user B know that the message has come from user C, who posing as user A? This concept is shown in fig. below. This type of attack is called as fabrication

Key Principles of Security • Confidentiality • Integrity • Availability • Authentication • Non repudiation • Access Control

Authentication • It determines the identity of user or other entity. • Authentication methods are as follows: 1. Password Based Authentication(Something user knows) 2. Devise Based Authentication (Something user has) 3. Biometric Authentication(Something about user)

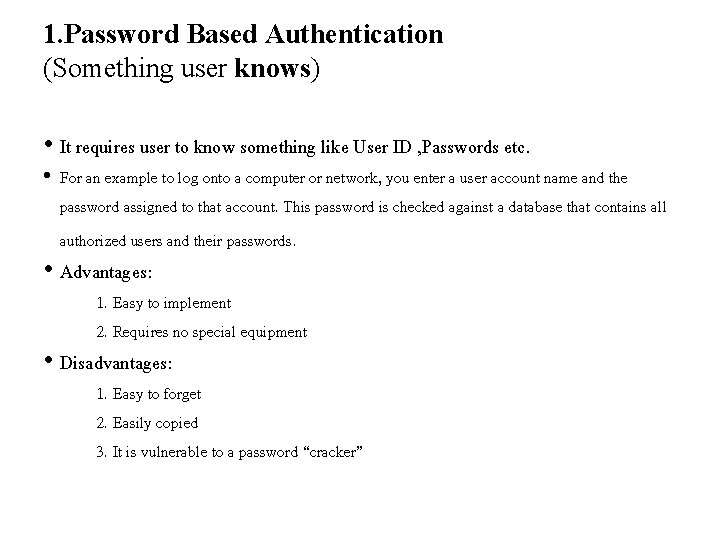
1. Password Based Authentication (Something user knows) • It requires user to know something like User ID , Passwords etc. • For an example to log onto a computer or network, you enter a user account name and the password assigned to that account. This password is checked against a database that contains all authorized users and their passwords. • Advantages: 1. Easy to implement 2. Requires no special equipment • Disadvantages: 1. Easy to forget 2. Easily copied 3. It is vulnerable to a password “cracker”

2. Devise Based Authentication (Something user has) • It requires the user to pass some items such as a key , map strip, card etc. • Advantages: 1. It is difficult to copy 2. User can’t forget a password • Disadvantages: 1. Easy target for theft 2. User has to carry it every time

3. Biometric Authentication (Something about user) • It identifies some physical characteristics of user that can’t be separated from their body like voice , fingerprint , retina etc. • Advantages: 1. User don’t need to carry anything 2. User don’t need to remember passwords • Disadvantages: 1. Complex implementation 2. High Cost

• Availability: – It ensures that data or system itself is available for user when user wants it. • Non repudiation: – It is a way to guarantee that the sender of a message can’t later deny having sent the message and that the receiver can’t deny having received the message • Access Control: – It gives organization the ability to control , restrict , monitor and protect resource availability , integrity , confidentiality

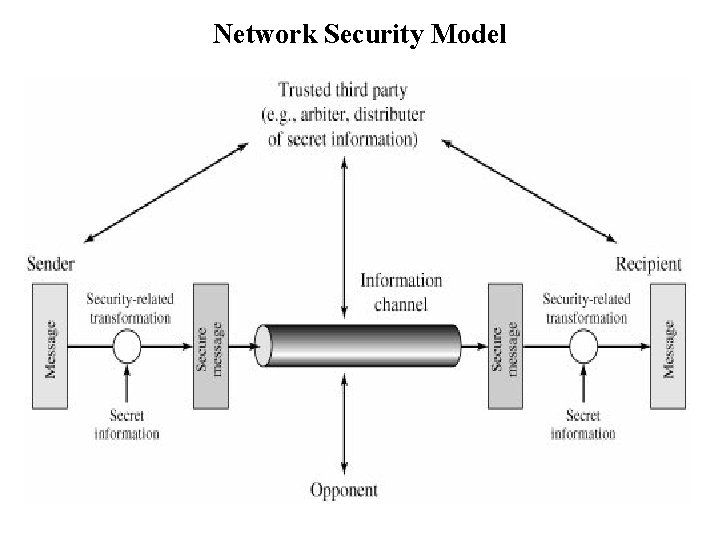
Network Security Model

Working of Network Security Model 1. Sender: it sends a message in a network in encrypted format. 2. Trusted 3 rd party: It provides encryption key to sender. 3. Information Channel: Message is transferred through the information channel. 4. Opponent: It hacks the secret message to capture information but it is useless because message is in encrypted format so it is not readable for opponent. 5. Trusted 3 rd party: It provides a key to receiver for decryption of message. 6. Recipient : when receiver receives a key then original message is display or read by receiver.

Threats to Security 1. Virus 2. Worms 3. Intruder 4. Insiders 5. Criminal Organizations 6. Terrorists 7. Information Warfare


What is a Virus? Computer virus is a software program written with malicious intentions. Computer virus is a harmful software program written intentionally to enter a computer without the user's permission or knowledge. It has the ability to replicate itself, thus continuing to spread.

Phases(Life Cycle) of Virus 1) Dormant Phase Here, the virus remains idle and gets activated based on a certain action or event(for example, a user pressing a key or on a certain date and time etc) 2)Propagation Phase The virus starts propagating, that is multiplying itself. A piece of code copies itself and each copy starts copying more copies of self, thus propagating.

Phases(Life Cycle) of Virus 3)Triggering Phase A Dormant virus moves into this phase when it gets activated, that is, the event it was waiting for gets initialised. 4)Execution Phase The function of virus is performed. It can be destructive(deleting files on disk) or harmless(popping messages on screen).

Types of Computer Viruses Parasitic viruses Memory Resident virus Non-Resident virus Boot Sector virus Overwriting virus Stealth virus Macro virus Polymorphic virus Email viruses Metamorphic virus

Parasitic viruses A parasitic virus attaches itself to a file in order to propagate. . COM and EXE files are easiest to infect, as they are simply loaded directly into memory and execution always starts at the first instruction.

Memory Resident Virus These viruses fix themselves in the computer memory and get activated whenever the OS runs and infects all the files that are then opened. This type of virus hides in the RAM and stays there even after the malicious code is executed.

Non-Resident virus A Non-Resident Computer Virus is a computer virus that is not stored on the hard drive of the computer that is impacted. Rather, the virus is housed in an executable file that infects a computer each time it is accessed and run.

Boot Sector Virus This type of virus affects the boot sector of a hard disk. . It hides in the memory until DOS accesses the floppy disk, and whichever boot data is accessed, the virus infects it.

Overwrite Viruses The virus replaces the file content. However, it does not change the file size.

Stealth virus A stealth virus is complex malware that hides itself after infecting a computer. Stealth viruses hide in files, partitions and boot sectors. It uses various mechanisms to avoid detection by antivirus software.

Macro Virus Macro viruses infect files that are created using certain applications or programs that contain macros, like. doc, . xls, . pps, . mdb, etc. These are not executable viruses. These hide in documents that are shared via e-mail or networks. Examples: Relax, Melissa. A, Bablas, O 97 M/Y 2 K

Polymorphic Virus Polymorphic viruses encrypt or encode themselves in a different way (using different algorithms and encryption keys) every time they infect a system. This makes it impossible for antivirus software to find them.

Companion Viruses This is the virus which creates a new program instead of modifying an existing file. These generally use the same filename and create a different extension of it. For example: If there is a file "Me. exe", the virus creates another file named "Me. com" and hides in the new file. When the system calls the filename "Me", the ". com" file gets executed (as ". com" has higher priority than ". exe"), thus infecting the system.

Email viruses An e-mail virus is computer code sent to you as an e-mail note attachment which, if activated, will cause some unexpected and usually harmful effect, such as destroying certain files on your hard disk and causing the attachment to be re mailed to everyone in your address book.

Metamorphic virus This type of virus keeps rewriting itself every time. It may change their behavior as well as appearance.

Computer Anti-Virus Antivirus software is a computer program that detects, prevents, and takes action to disarm or remove malicious software programs, such as viruses and worms. There are certain types of anti-viruses.

Worms • Definition – Piece of code that automatically reproduces itself over the network. It doesn’t need the user intervention to propagate (autonomous). • Infection – Via buffer overflow, file sharing, configuration errors and other vulnerabilities.

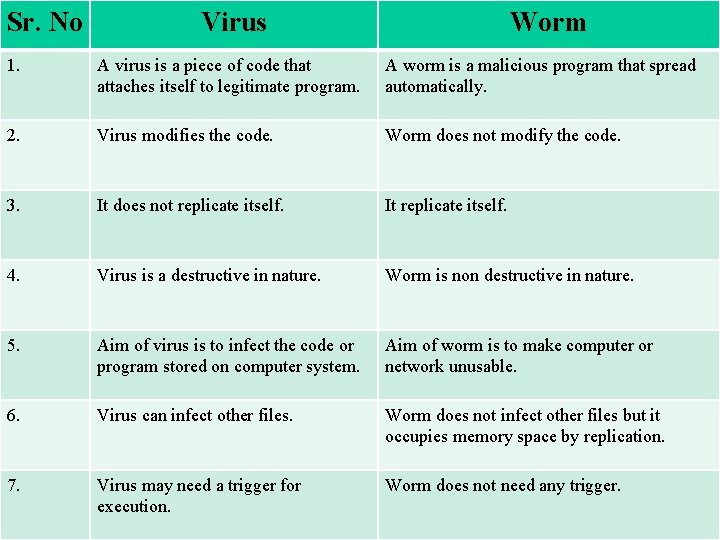
Sr. No Virus Worm 1. A virus is a piece of code that attaches itself to legitimate program. A worm is a malicious program that spread automatically. 2. Virus modifies the code. Worm does not modify the code. 3. It does not replicate itself. It replicate itself. 4. Virus is a destructive in nature. Worm is non destructive in nature. 5. Aim of virus is to infect the code or program stored on computer system. Aim of worm is to make computer or network unusable. 6. Virus can infect other files. Worm does not infect other files but it occupies memory space by replication. 7. Virus may need a trigger for execution. Worm does not need any trigger.

Intruder • An intruder is a person that enters territory that does not belong to that person. • Intruders are said to be of three types, as below: 1. Masquerader: 2. Misfeasor: 3. Clandestine user:

1. Masquerader: A user who does not have the authority to use a computer, but penetrates into a system to access a legitimate user‘s account is called a masquerader. ii. It is generally an external user. iii. It pretend to be someone which is not. i. 2. Misfeasor: There are two possible cases for an internal user to be called as a misfeasor: i) A legitimate user, who does not have access to some applications, data or resources, accesses them. ii) A legitimate user, who has access to some applications, data or resources, misuses these privileges.

• 3. Clandestine user: 1. An individual who seizes supervisory control of the system and uses this control to evade auditing and access controls to suppress the audit collection. 2. An internal or external user who tries to work using the privileges of a supervisor user to avoid auditing information being captured and recorded is called as a clandestine user. 3. It can be insider or outsider.

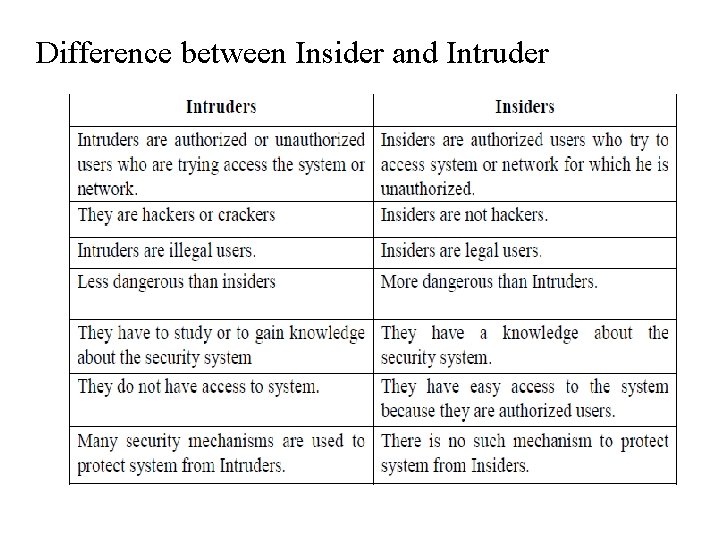
Insiders • Insiders are authorized users who try to access system or network for which he is unauthorized. • Insiders are legal users. • They have easy access to the system because they are authorized users.

Why insiders are more dangerous than intruder? – More dangerous than Intruders as they have knowledge about the security system. – They have easy access to the system because they are authorized users. – There is no security mechanism to protect system from Insiders are more dangerous than intruders because: – The insiders have the access and necessary knowledge to cause immediate damage to an organization. . – So they can have all the access to carry out criminal activity like fraud. – They have knowledge of the security systems and will be better able to avoid detection

Difference between Insider and Intruder

Risk and Threat Analysis: • • Assets: Vulnerability : Threats: Counter measures: Risks = Assets * Vulnerability * Threats

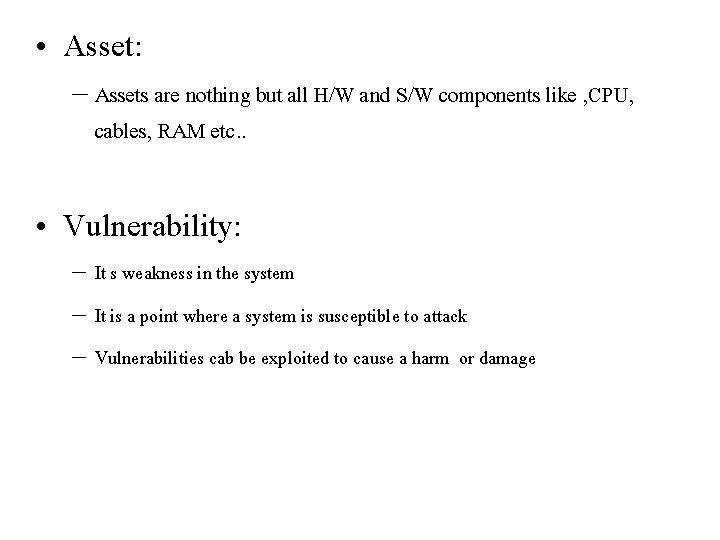
• Asset: – Assets are nothing but all H/W and S/W components like , CPU, cables, RAM etc. . • Vulnerability: – It s weakness in the system – It is a point where a system is susceptible to attack – Vulnerabilities cab be exploited to cause a harm or damage

• Threat : – It is a set of circumstances that has potential to cause loss or harm. – is a possible danger to the system – The danger might be a person (a system cracker or a spy), a thing (a faulty piece of equipment), or an event (a fire or a flood) that might exploit a vulnerability of the system

• Countermeasures: – These are actions, device, procedures or techniques for protecting your system.

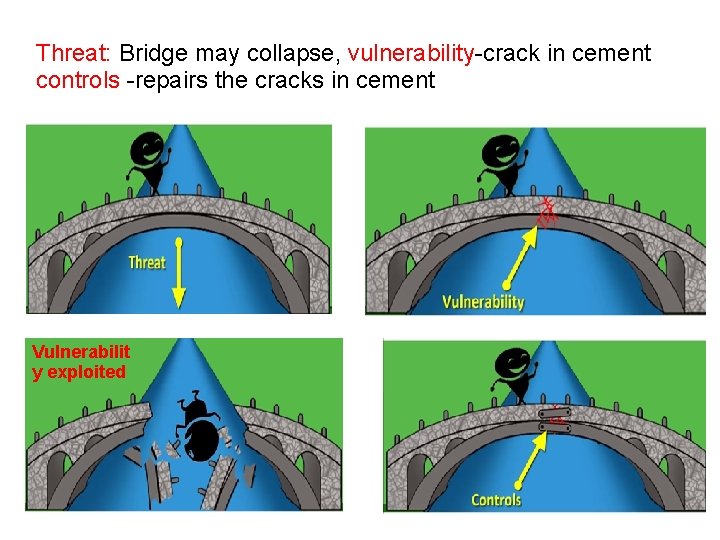
Threat: Bridge may collapse, vulnerability-crack in cement controls -repairs the cracks in cement Vulnerabilit y exploited








Attack An attack is any attempt to destroy, expose, alter, disable, steal or gain unauthorized access to or make unauthorized use of an asset. An attack occurs when an individual or a group of individuals attempts to access, modify, or damage your systems or environment.

Steps in Attacks 1 Step 1: Reconnaissance/Planning/Investigation Step 2: Scanning Step 3: Gaining access Step 4: Maintaining access Step 5: Covering tracks

Step 1: Reconnaissance/Planning/Investigation In this attacker will need to collect more information about organization that will helf later to gain unauthorized access to computer system. Attacker can use “Software Engineering” and “Dumpster Diving” to find sensitive information Attackker can also install virus, worms, spywares softwares to gain informations.

Step 2: Scanning Once an attacker gets a sensitive information attacker starts scanning to find entry points such as backdoors, trapdoors or finding vulnerabilities of syatem.

Step 3: Gaining access Once attacker gains access he take over a system that exploit a vulnerabilities of system by installing “Trojan Horse” or automatic “Bot” that allow an attacker to send a command from internet.

Step 4: Maintaining access Once an attacker gains full access to system they will reconfigure a system. They also install software patches to close previous security vulnerabilities just to keep hackers out.

Step 5: Covering tracks Attacker must stay hidden to maintain control and gather more intelligence to maximize the damage.

Steps in Attacks 2 Step 1: Interception: Step 2: Fabrication: Step 3: Modification: Step 4: Interruption:

Step 1: Interception: It is related concept of confidentiality. Here an unauthorized party has gained access to a resource, it can be person, program, or computer based system. i. e. copying of data or programs, listening to network traffic.

Step 2: Fabrication concept of authorization, It involves the creation of illegal objects on a computer system. i. e. attacker adds fake records to data base.

Step 3: Modification Its under Integrity, Here attacker may modify the values in the database.

Step 4: Interruption It‘s related to availability, Here Resources become unavailable, Lost or unusable, i. e. denial of service, problem causing to a hardware device, erasing program, data, or operating system components. For more detail contact us

Security Attacks 1. Active & passive attacks 2. Denial of service attack 3. Backdoors & trapdoors 4. Sniffing 5. Spoofing 6. Man-in Middle attack 7. TCP/IP Hacking 8. Replay attack 9. Encryption attack. 10. Malware- Virus, Worms

1. Active Attacks 1. In active attacks, the contents of the original message are modified in some way. 2. The active attacks can not be prevented easily. 3. These types of attacks are subdivided into four categories : a. Masquerade b. Replay c. Modification of Message d. Denial of service

2. Passive Attacks 1. Passive attacks are those, where attacker aims to obtain information that is in transit. 2. In passive attack, attacker does not involve any modifications to the contents of an original message. 3. They are hard to detect. 4. There are two types of passive attacks: a. Release of Message contents b. Traffic Analysis

3. Denial Of Service Attack. 1. Denial of service (DOS) attack scan exploits a known vulnerability in a specific application or operating system, or they may attack features (or weaknesses) in specific protocols or services. 2. In this form of attack, the attacker is attempting to deny authorized users access either to specific information or to the computer system or network itself. 3. The purpose of such an attack can be simply to prevent access to the target system, or the attack can be used in conjunction with other actions in order to gain unauthorized access to a computer or network. 4. Examples: a. SYN Flood 1. Types: a. POD (ping-of-death) b. DDOS (Distributed Denial of Service attack)

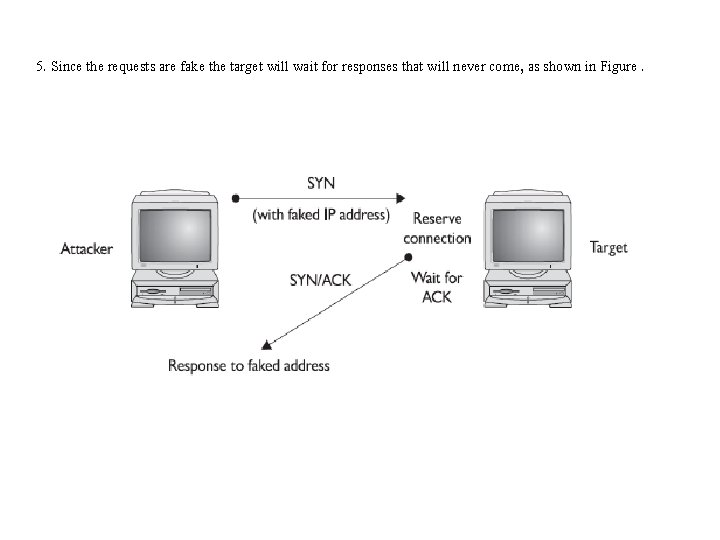
4. SYN flooding Attack 1. SYN flooding is an example of a DOS attack that takes advantage of the way TCP/IP networks were designed to function, and it can be used to illustrate the basic principles of any DOS attack. 2. SYN flooding utilizes the TCP three-way handshake that is used to establish a connection between two systems. 3. In a SYN flooding attack, the attacker sends fake communication requests to the targeted system. 4. Each of these requests will be answered by the target system, which then waits for the third part of the handshake.

5. Since the requests are fake the target will wait for responses that will never come, as shown in Figure.

6. The target system will drop these connections after a specific time-out period, but if the attacker sends requests faster than the time-out period eliminates them, the system will quickly be filled with requests. 7. The number of connections a system can support is finite, so when more requests come in than can be processed, the system will soon be reserving all its connections for fake requests. 8. At this point, any further requests are simply dropped (ignored), and legitimate users who want to connect to the target system will not be able to. 9. Use of the system has thus been denied to them.

POD (ping-of-death) 1. In the POD attack, the attacker sends an Internet Control Message Protocol (ICMP) ―ping‖ packet equal to, or exceeding 64 KB (which is to say, greater than 64 * 1024 = 65, 536 bytes). 2. This type of packet should not occur naturally (there is no reason for a ping packet to be larger than 64 KB). 3. Certain systems were not able to handle this size of packet, and the system would hang or crash.

DDOS (Distributed Denial of Service attack) 1. These types of attacks are difficult to prevent because the behavior of whole networks needs to be analyzed, not only the behavior of small piece of code. 2. A denial of service attack employing multiple attacking systems is known as a distributed denial of service (DDOS) attack. 3. The goal of a DDOS attack is the same: to deny the use of or access to a specific service or system. 4. In a DDOS attack, the method used to deny service is simply to flood the target with traffic from many different systems.

5. A network of attack agents (sometimes called zombies) is created by the attacker, and upon receiving the attack command from the attacker, the attack agents commence sending a specific type of traffic against the target. 6. If the attack network is large enough, even ordinary web traffic can quickly overwhelm the largest of sites, such as the ones targeted in 2000. ed attacks on e. Bay, CNN, Amazon, and Yahoo.


3. Backdoor/Trapdoor attack i. ii. iv. v. These are the methods used by software developers to make sure that they can gain access to an application even if something were to happen in future to prevent normal access methods. It allows to gain access without going through the usual security access procedures. These attacks are initiated by gaining access to network and inserting a program that creates a backdoor for an attacker. Net. Bus and Back Orifice are common backdoors that allows attacker to remotely access the system and perform various operations on it. It is often only known by the programmer. A backdoor is a potential security risk.

4. Sniffing Attack sniffers is a software or hardware device that is used to observe traffic as it passes through a network on shared broadcast media. The device can be used to views all traffic or it can target a specific protocol, service, or even string of characters. Objective of sniffing is to steal: • Password • Email text • Files in transfer

5. Spoofing • In the context of network security, a spoofing attack is a situation in which one person or program successfully masquerades as another by falsifying data and thereby gaining an illegitimate advantage. • An attacker alters his identity so that some one thinks he is some one else

Types of Spoofing • IP Spoofing • • URL spoofing Referrer spoofing Caller ID spoofing E-mail Address Spoofing

IP Spoofing Definition: Attacker spoofs the address of another machine and inserts itself between the attacked machine and the spoofed machine to intercept replies From Address: 10. 20. 30 To Address: 10. 5. 5 Attacker intercepts packets as they go to 10. 20. 30 Replies sent back to 10. 20. 30 Attacker 10. 50. 50 John 10. 5. 5 • thus gaining access to all messages in both directions without the trouble of any cryptanalytic effort. The attacker must monitor the packets sent from Alice to Bob and then guess the sequence number of the packets. Then the attacker knocks out Alice and injects his own packets, claiming to have the address of Alice.

URL Spoofing and Phishing • Another kind of spoofing is "webpage spoofing, " also known as phishing. In this attack, a legitimate web page such as a bank's site is reproduced in "look and feel" on another server under control of the attacker. The main intent is to fool the users into thinking that they are connected to a trusted site, for instance to harvest user names and passwords. • This attack is often performed with the aid of URL spoofing, which exploits web browser bugs in order to display incorrect URLs in the browsers location bar; in order to direct the user away from the legitimate site and to the fake one. Once the user puts in their password, the attackcode reports a password error, then redirects the user back to the legitimate site.




Referrer Spoofing • Referrer spoofing or ref tar spoofing is the sending of incorrect referrer information in an HTTP request, sometimes with the aim of gaining unauthorized access to a web site. It is also used to improve the privacy of an individual using a web browser to view World Wide Web sites, by replacing valid referrer data with incorrect data, though most users simply suppress their web browser from sending referrer data, and may also modify other HTTP headers.

Caller ID Spoofing • In public telephone networks, it has for a long while been possible to find out who is calling you by looking at the Caller ID information that is transmitted with the call. There are technologies that transmit this information on landlines, on cell phones and also with Vo. IP. Unfortunately, there are now technologies (especially associated with Vo. IP) that allow callers to lie about their identity, and present false names and numbers, which could of course be used as a tool to defraud or harass. Because there are services and gateways that interconnect Vo. IP with other public phone networks, these false Caller IDs can be transmitted to any phone on the planet, which makes the whole Caller ID information now next to useless

That’s easy. You can use a spoof card. A Caller ID Spoofer and Voice Changer is a calling card you can use to make a call to anyone and hide or mask your caller ID. http: //www. spoofcard. com/? utm_source=pj&utm _medium=Affiliate&source=pjn&subid=7504

E-mail Address Spoofing • The sender information shown in e-mails (the "From" field) can be spoofed easily. This technique is commonly used by spammers to hide the origin of their e-mails and leads to problems such as misdirected bounces (i. e. e-mail spam backscatter). • E-mail spoofing is a term used to describe (usually fraudulent) e-mail activity in which the sender address and other parts of the e-mail header are altered to appear as though the e-mail originated from a different source. • By changing certain properties of the e-mail, such as the From, Return. Path and Reply-To fields (which can be found in the message header), illintentioned users can make the e-mail appear to be from someone other than the actual sender. The result is that, although the e-mail appears to come from the address indicated in the From field (found in the e-mail headers), it actually comes from another source.



6. Man in the middle attack. 1. A man in the middle attack occurs when attackers are able to place themselves in the middle of two other hosts that are communicating in order to view or modify the traffic. 2. This is done by making sure that all communication going to or from the target host is routed through the attacker‘s host. 3. Then the attacker is able to observe all traffic before transmitting it and can actually modify or block traffic. 4. To the target host, communication is occurring normally, since all expected replies are received. 5. Prevention: – To prevent this attack both sender and receiver must authenticate each other.


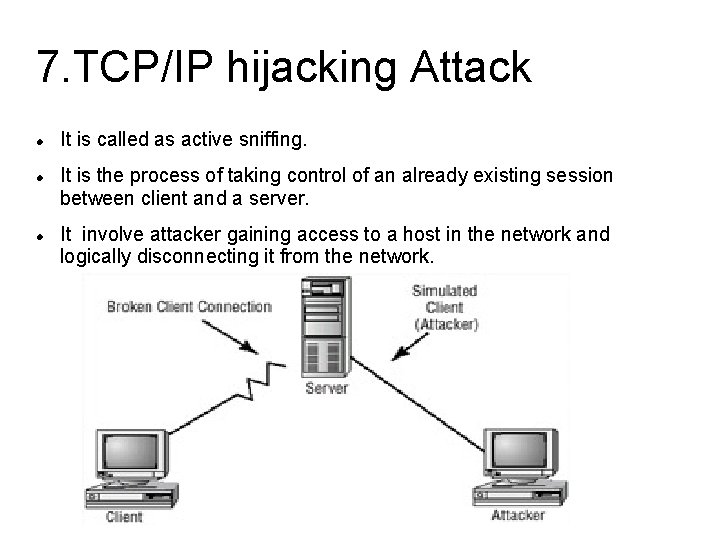
7. TCP/IP hijacking Attack It is called as active sniffing. It is the process of taking control of an already existing session between client and a server. It involve attacker gaining access to a host in the network and logically disconnecting it from the network.

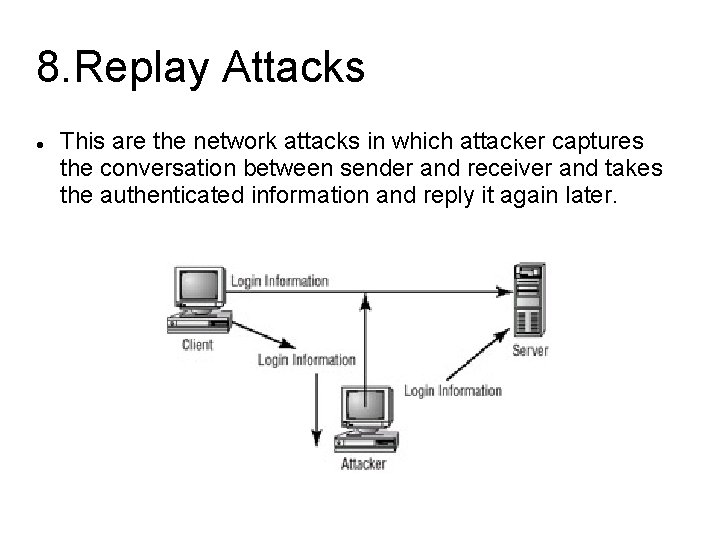
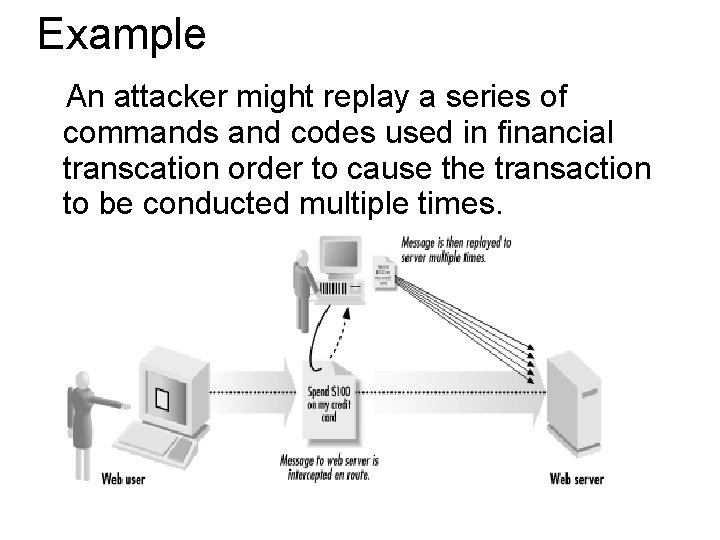
8. Replay Attacks This are the network attacks in which attacker captures the conversation between sender and receiver and takes the authenticated information and reply it again later.

Example An attacker might replay a series of commands and codes used in financial transcation order to cause the transaction to be conducted multiple times.

Prevention: 1. Encryption 2. Timestamps 3. Cryptography authentication

Trojan Horse



Logic Bomb attack: • Logic bombs are a type of malicious software that is deliberately installed, generally by an authorized user. • A logic bomb is a piece of code that sits dormant for a period of time until some event invokes its malicious payload. • An example of a logic bomb might be a program that is set to load & run automatically and that periodically checks an organization‘s payroll or personal database for a specific employee. • If the employee is not found, the malicious payload executes, deleting vital corporate files. • Logic bombs are difficult to detect because they are often installed by authorized users & by administrators.

Time bomb attack: • A time bomb refers to a computer program that has been written so that it will stop functioning after a predetermined date or time is reached. • Time bombs are commonly used in beta (pre-release) software when the manufacturer of the software does not want the beta version being used after the final release date. • Example of time bomb software would be Microsoft's Windows Vista Beta 2, which was programmed to expire on May 31, 2007. • The time limits on time bomb software not usually as heavily enforced as they are on trial software, since time bomb software does not usually implement secure clock functions.
