Risk Management for Technology Exposures National Charter Schools



























































































- Slides: 128

Risk Management for Technology Exposures National Charter Schools Text Pete Reilly preilly@edtechjourneys. com http: //edtechjourneys. pbwiki. com Sponsored by NYSIR copyright 2008 Ed Tech Journeys

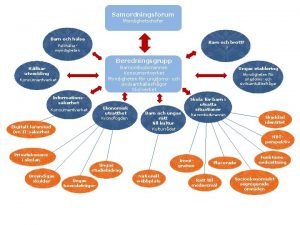
Agenda Student Security Network/Data Security Employee Issues Foil/E-Discovery/Audits Physical Security Audit Case Study copyright 2008 Ed Tech Journeys CWG Survey Results Security Vulnerability Survey

Student Security Cyberbullying Student Safety Web 2. 0 RSS Blogs The Facts About Online Sexual Abuse Enforcement and Strategies copyright 2008 Ed Tech Journeys

Employee Issues Personal Use Advertising Privacy Politics Improper Access Fundraising Harassment Teacher Web Sites Copyright Teacher Links Confidentiality copyright 2008 Ed Tech Journeys

Common Security Risks Prevention Applications Servers Network WAN Desktops Policies Forensics Recovery Internal Hacks Denial of Service Phishing BOTs Spyware Spam Trojan Web 2. 0

Managing Internet Risks Educational Forum Disclosure and disclaimers Enforcement Educational Restrictions District Strategies The Facts About Internet Sexual Abuse copyright 2008 Ed Tech Journeys

Managing Security Risks Firewalls Applications Servers & Network Policies Desktops User Awareness Initial & Annual Security Audit copyright 2008 Ed Tech Journeys

FOIL & E-Discovery FOIL & E-Document Policy E- Discovery Open Meetings Software Audits Domain Names CIPA & E-Rate Comptrollers Audits copyright 2008 Ed Tech Journeys

Spyware Three Shocking Statistics on Spyware! 1. 8 out of 10 PC’s are infected with some sort of Spyware, with an average of 24. 4 spies per PC scanned. 2. Microsoft estimates that 50% of all PC crashes are due to spyware. 3. Dell reports that 20% of all technical support calls involve spyware. copyright 2008 Ed Tech Journeys

Spyware * Severe Threat – 15% of spyware threats send private information gathered from the end user currently logged on to the infected system: logging the user's keystrokes, logged-on user name, hash of administrator passwords, email addresses, contacts, instant messengers login and usage, and more. * Moderate Threat – 25% percent of spyware sends information gathered from the victim's operating system, including the computer (host) name, domain name, logs of all processes running in memory, installed programs, security applications, client's internal IP address, OS version, the existence and versions of service packs and security updates, TCP ports the spyware is listening to, Computer Security Identifier (SID) , default browser's homepage, browser plug-ins, etc. * Minor Threat – 60% of spyware transmits gathered commercial-value information about the end user's browsing habits. This includes keywords used in search engines, browsing habits and ratings of frequently visited websites, shopping reports etc.

Spam = 40%-70% of all e-mail Spam floods overloading servers and acting like Do. S copyright 2008 Ed Tech Journeys

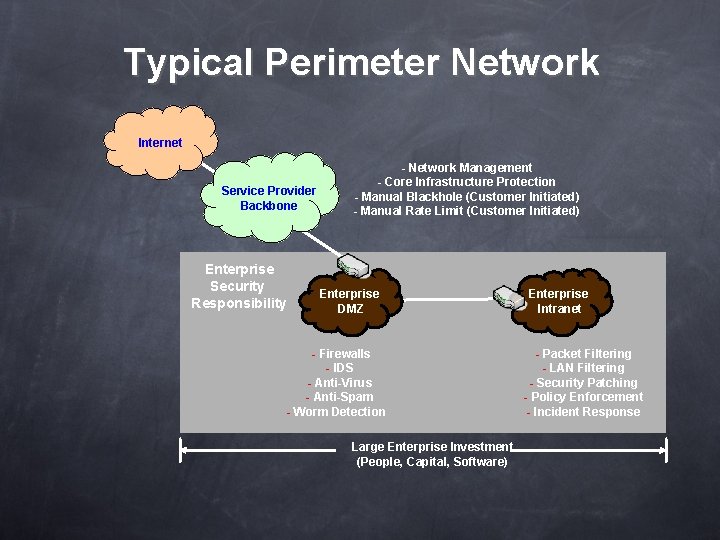
Typical Perimeter Network Internet Service Provider Backbone Enterprise Security Responsibility - Network Management - Core Infrastructure Protection - Manual Blackhole (Customer Initiated) - Manual Rate Limit (Customer Initiated) Enterprise DMZ - Firewalls - IDS - Anti-Virus - Anti-Spam - Worm Detection Large Enterprise Investment (People, Capital, Software) Enterprise Intranet - Packet Filtering - LAN Filtering - Security Patching - Policy Enforcement - Incident Response

Prevention - Firewalls Intrusion Detection Software 5, 000 port scans per day Apply update and patches immediately Review Firewall policies annually Hole opened for server install - not closed Server decommissioned - hole not closed copyright 2008 Ed Tech Journeys

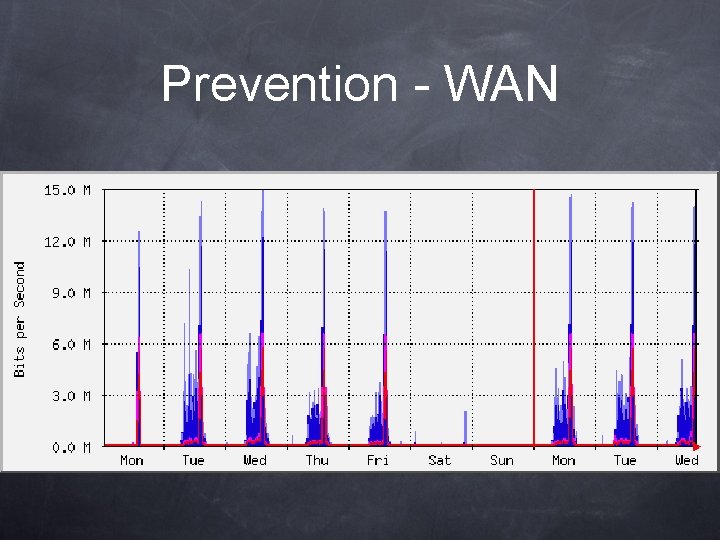
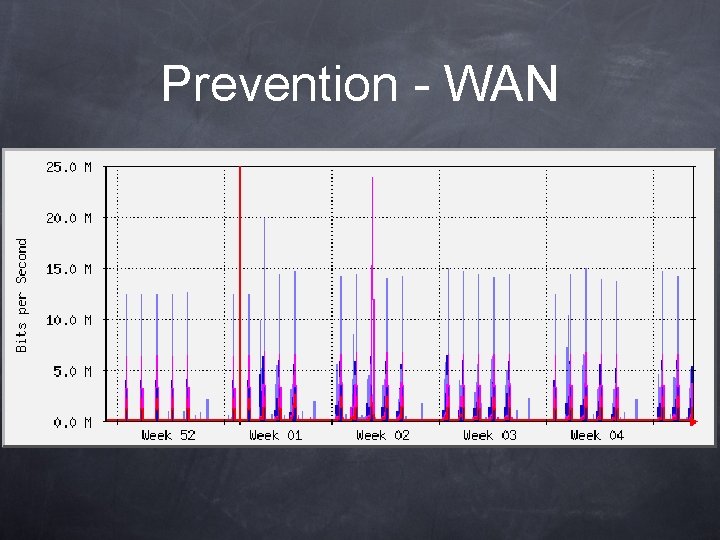
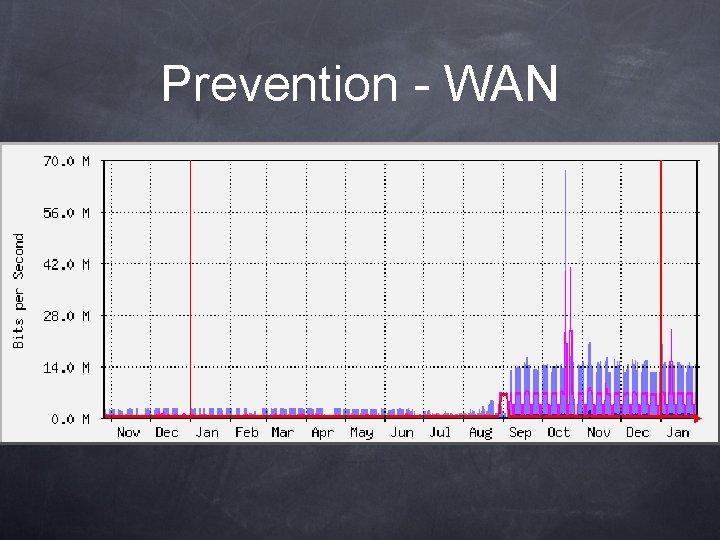
Prevention - WAN Periodic Network Traffic Analysis

Prevention - WAN

Prevention - WAN

Prevention - WAN

Prevention - WAN Configure your routers with access lists Check hubs, switches and routers for web management modules and change default passwords Use security on your wireless networks copyright 2008 Ed Tech Journeys

Prevention - Servers Server maintenance and security patches immediately Remove all generic and guest defaults after install Check for inactive web modules copyright 2008 Ed Tech Journeys

Prevention - Network Use Virtual Private Networks (VPNs) Require specific logons Lab aid giving generic logons so students could bypass filter Pornography found on C: drive in teachers’ room copyright 2008 Ed Tech Journeys

Prevention - Network Periodic network and server scans Consultant with website on school server Secure remote access to network Maintenance done by third parties copyright 2008 Ed Tech Journeys

Prevention - Desktops A: drive Vulnerable to infected floppy disks, flash drives, and other non-authorized files and applications C: drive Vulnerable to configuration changes, and access to restricted resources (students hide Internet access) FTP Vulnerable to downloads of infected files or other non-authorized files and applications

Prevention - Desktops Windows Explorer Students see all network resources Right Click Students can cut, paste, and delete important files including system configuration copyright 2008 Ed Tech Journeys

Prevention - Applications themselves have security. Are these security elements fully utilized? Programming courses such as C++ and Visual Basic copyright 2008 Ed Tech Journeys

Strong Passwords At least: 7 characters, 1 letter, 1 digit, 1 uppercase, 1 lowercase, 1 special character Not based on user’s name or login ID Not based on a dictionary word in any language Not contain more than 2 paired letters -abbcdde is valid but abbbcdd is not copyright 2008 Ed Tech Journeys

Prevention - Policies. exe files Slow Internet and/or network performance Overwhelmed hard drives and network servers Disks from home Technical vulnerabilities Copyright vulnerabilities copyright 2008 Ed Tech Journeys

Prevention - Policies Loading software locally Technical issues – not in “Ghost image” Printing and application support issues Copyright issues Accidentally “blow out” system Docking home computers Students running “cracking” programs and access SASI passwords Keychain hardrives copyright 2008 Ed Tech Journeys

Prevention - Policies Removal of access when someone leaves E-mail, Calendar, network logon, etc. Early notification of problems such as viruses What process in place to notify users of new viruses, etc. More than one person with key knowledge and access. Network backdoors setup Secret backups and password changes done before termination

Prevention – Policies Log-off apps, log-off network Students doing “high level” maintenance May compromise security intentionally or unintentionally Enforcement of Policies If practice doesn’t follow policy than policies are not valid. copyright 2008 Ed Tech Journeys

Forensics Log files: Intrusion detection logs Firewall logs Router logs Server logs Application logs copyright 2008 Ed Tech Journeys

Forensics Unique log-ins Isolate systems Notify authorities Print screens (IM’ing, chat, e-mail, etc. ) Terror threat to local HS Hard Dive recovery copyright 2008 Ed Tech Journeys

Recovery Save to the network Saving to the C: drive means no backups Verify that backups are complete Who is responsible? Who is their backup? External backups vs internal Proper tape rotation - off site storage Off-site storage Periodic backup check before and emergency copyright 2008 Ed Tech Journeys

Recovery Damaged servers & switches RAID drives UPS on all servers and switches Maintenance 24 x 7 x 7 contracts or spares Mirrored or backup servers Routers, switches, hubs Maintenance 24 x 7 x 7 contract or replacements copyright 2008 Ed Tech Journeys

Recovery Formalize a Hot Spot Partnership Applications media archived Escalation procedure to move to recovery quicker and to limit damages Must notify if privacy is compromised May need to isolate problem May need to change passwords copyright 2008 Ed Tech Journeys

Internal Hacks

Internal Hacks

Internal Hacks

Internal Hacks 60%-80% of hacks are internal -FBI Bypassing the filter - IP address (ping) You. Tube UK Superintendent’s private files Employee w Backdoor access copyright 2008 Ed Tech Journeys

Internal Hacks Anonymous surfing - Port 443 Inadvertent damage Loading software from home Deleting important configuration files Attempting to help wiping our systems copyright 2008 Ed Tech Journeys

Denial of Service In this type of attack, the attacker begins the process of establishing a connection to the victim machine, but does it in such a way as to prevent the ultimate completion of the connection. In the meantime, the victim machine has reserved one of a limited number of data structures required to complete the impending connection. The result is that legitimate connections are denied while the victim machine is waiting to complete bogus "half-open" connections.



BOT

Phishing

Trojan

Improper Access to Obscene and Inappropriate Material from the School’s System Inadvertent Access to Pornography Julie Amero Story: 4 felony counts, firewall license expired, virus protection lapsed, no spyware defense, on an old Win 98 system obscene popup. “It was an innocent search” Domain name spoofs Hate Sites …How to Build a Bomb. . . Doom & Duke Nukem copyright 2008 Ed Tech Journeys

What Is Web 2. 0? Refers to the most recent generation of web technologies and products including: u • Blogs • Podcasts • Wikis • RSS Newsfeeds • Social networking (My. Space, Friendster) • Web applications with rich, interactive interfaces u User created content copyright 2008 Ed Tech Journeys

What Is RSS? RSS stands for Really Simple Syndication or RDF Site Summary. Is based on XML and is simple to learn. Used by blogs, websites, browsers and applications to deliver content to subscribers. copyright 2008 Ed Tech Journeys

RSS in Plain English

Security Problems of RSS As an avenue for automated delivery of web-based content, can be easily used as a delivery method for spam and phishing. Popularity of RSS syndication aggregators can make it easier to subvert feeds and redirect them from originators. But the biggest problem is the RSS enclosure capability, which is the feature of RSS which enables things like podcasting. Nothing in the specification which limits this to MP 3 files. Can also be used to deliver anything from Flash to executables. In most cases downloads happen automatically. copyright 2008 Ed Tech Journeys

How To Secure RSS Verify accurate address of content delivery from your RSS feeds. u Block downloads of executables and other high-risk content at the gateway u copyright 2008 Ed Tech Journeys

The Security Problems of Blogs As a complex web application, blogs have the same potential problems as most web applications, such as bugs and security holes which require patching, and susceptibility to classic web hacking techniques. However, interactivity of blogs provides some unique areas of attack, specifically in the typical ability for any reader to be able to comment within a blog. At the lowest level this makes blogs susceptible to spam but also opens up more dangerous exploits. copyright 2008 Ed Tech Journeys

Example: The Storm Worm Variant New Storm Worm Spreading Via Blog Posts A Storm worm variant using both e-mail and Web sites to infect Windows-based PCs is injecting itself into the responses people are leaving on blogs. When infected systems visited blogs, worm inserted script into the blog comments that linked to malware. u copyright 2008 Ed Tech Journeys

How To Secure Your Blogging Infrastructure • Keep your blogging platform software fully patched and up-to-date • Don’t allow unmoderated comments • Configure blog to only allow straight text in blog comments • Use software designed to block or limit what is know as “comment spam”. Examples of these include Bad Behaviour and Akismet copyright 2008 Ed Tech Journeys






Cyberbullying Statistics 90% of MS students have had their feelings hurt online 42% have been bullied online copyright 2008 Ed Tech Journeys

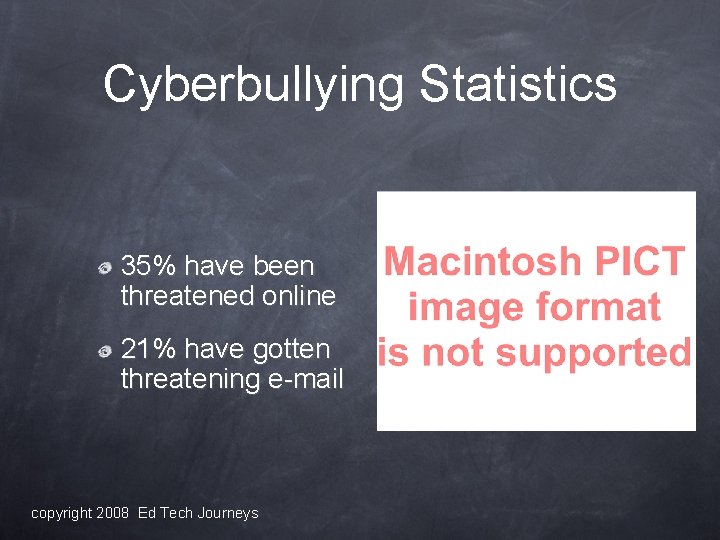
Cyberbullying Statistics 35% have been threatened online 21% have gotten threatening e-mail copyright 2008 Ed Tech Journeys

Cyberbullying Statistics 53% have said something mean or hurtful online 58% have not told their parents about bullying incidents copyright 2008 Ed Tech Journeys

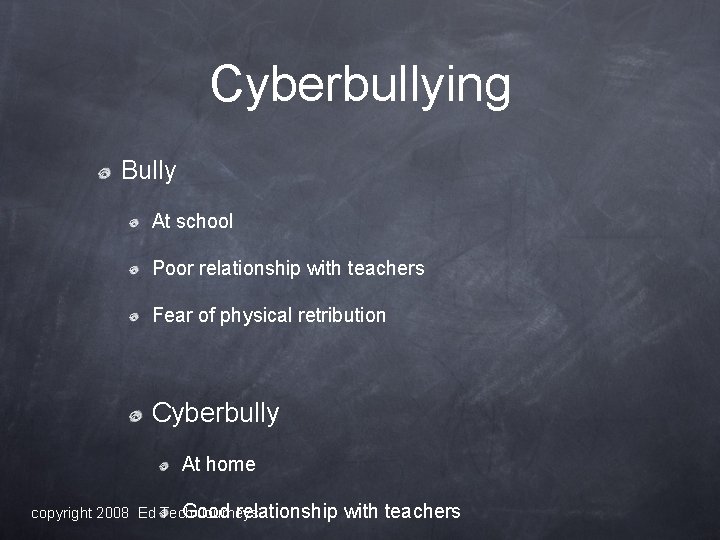
Cyberbullying Bully At school Poor relationship with teachers Fear of physical retribution Cyberbully At home Good relationship copyright 2008 Ed Tech Journeys with teachers


Copyright Infringement Everything on the Internet is protected by Copyright If employer has the right & ability to supervise the actions of the employee & has a financial interest in exploitation…even if the employer didn’t know…he may be liable SIA lawsuits, Record industry lawsuits copyright 2008 Ed Tech Journeys

Copyright Infringement Students cutting and pasting parts of Web pages onto their own Improper use of student material copyright 2008 Ed Tech Journeys

District Strategies Supervise! Educate staff, students, and parents Develop a site limitation strategy Develop a solid AUP Keep policy decisions at the highest level copyright 2008 Ed Tech Journeys

Establish an Educational Forum Insure that policy and practice are aligned Insure that AUP is signed - affirmative consent You can allow limited “self-discovery” copyright 2008 Ed Tech Journeys

Enforcement - Due If it is educational, access can’t be Process denied, restricted or suspended without due process. Notice to student of alleged violation Opportunity for student to respond to allegation No denial of an account in advance of a hearing Missouri suit Arkansas suit Ohio suit copyright 2008 Ed Tech Journeys Pennsylvania expulsion upheld

Court to school district: You can't stop a kid from creating a personal web site critical of your schools: Missouri school district becomes the latest to learn the hard way From e. School News staff and wire service reports Sending a clear signal to educators everywhere, a federal judge ruled Dec. 28 that Woodland School District in Marble Hill, Mo. , violated a high school student's free speech rights when it suspended him for posting a personal web page criticizing his school. The ruling makes clear that schools have no jurisdiction over what their students do in cyberspace, provided it's done on their own time and from their own computers. U. S. District Court Judge Rodney Sippel issued a preliminary injunction that prohibits the district from using the suspension against student Brandon Beussink in grade and attendance calculations. It also bars the district from punishing Beussink or restricting his ability to post his home page on the internet. "Dislike or being upset by the content of a student's speech is not an acceptable justification for limiting student speech, " Sippel wrote in his opinion.

Newslines--Arkansas district settles lawsuit over student’s sexually explicit web page e. School News staff and wire service reports Arkansas’ Valley View School District has settled a lawsuit involving a student’s internet site so it could begin the school year without the distractions of a court hearing, a school district attorney said Aug. 18. Dan Bufford said the court case was causing too much disruption. “We were looking at sending six to eight teachers, seven to eight students, and three sets of parents from Jonesboro to Little Rock to testify, ” Bufford said. “The distractions and the expense of that was just too much. ” The American Civil Liberties Union sued the school district, contending the district wrongly suspended Justin Redman for 10 days. He was suspended for producing a web site that mirrored the school’s official web site, but included sexually explicit photos and text, some of which named other students and administrators. John Burnett, the ACLU’s state legal director, said the settlement doesn’t mean the organization agrees with the district’s actions. “Every school board and every school board attorney in the state is going to know about this case, ” he said. “The schools are going to have to come to realization that, just as they cannot visit discipline on students for something they said at a weekend party, they cannot do it because of something a student said on the world wide web. ”

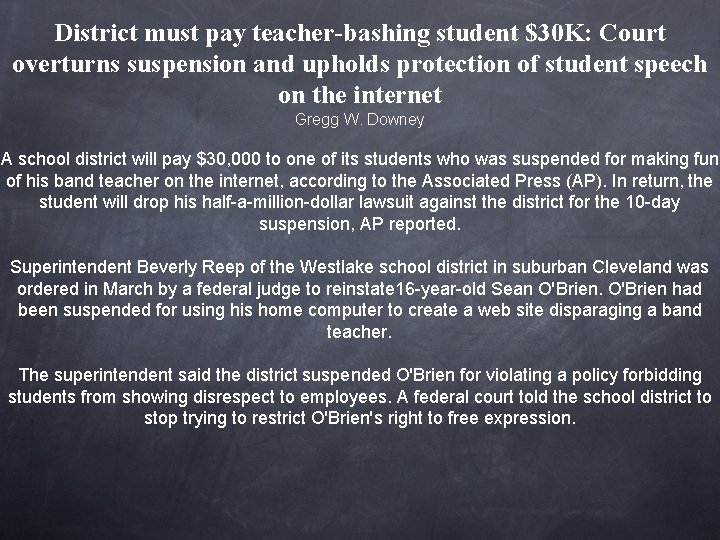
District must pay teacher-bashing student $30 K: Court overturns suspension and upholds protection of student speech on the internet Gregg W. Downey A school district will pay $30, 000 to one of its students who was suspended for making fun of his band teacher on the internet, according to the Associated Press (AP). In return, the student will drop his half-a-million-dollar lawsuit against the district for the 10 -day suspension, AP reported. Superintendent Beverly Reep of the Westlake school district in suburban Cleveland was ordered in March by a federal judge to reinstate 16 -year-old Sean O'Brien had been suspended for using his home computer to create a web site disparaging a band teacher. The superintendent said the district suspended O'Brien for violating a policy forbidding students from showing disrespect to employees. A federal court told the school district to stop trying to restrict O'Brien's right to free expression.

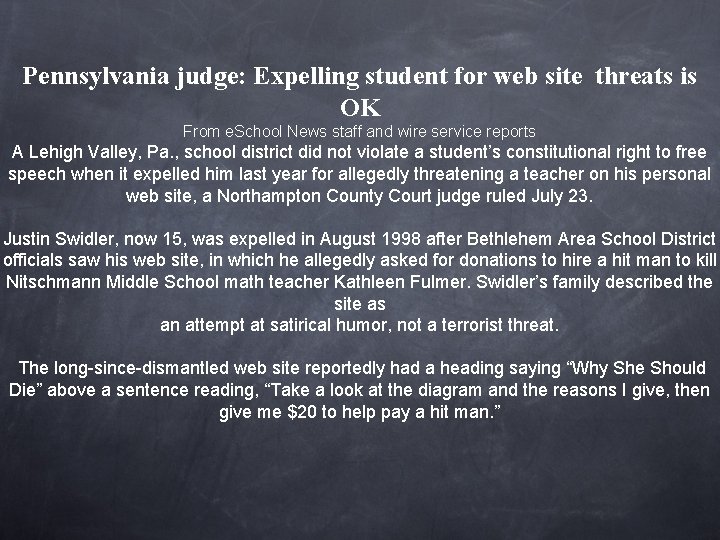
Pennsylvania judge: Expelling student for web site threats is OK From e. School News staff and wire service reports A Lehigh Valley, Pa. , school district did not violate a student’s constitutional right to free speech when it expelled him last year for allegedly threatening a teacher on his personal web site, a Northampton County Court judge ruled July 23. Justin Swidler, now 15, was expelled in August 1998 after Bethlehem Area School District officials saw his web site, in which he allegedly asked for donations to hire a hit man to kill Nitschmann Middle School math teacher Kathleen Fulmer. Swidler’s family described the site as an attempt at satirical humor, not a terrorist threat. The long-since-dismantled web site reportedly had a heading saying “Why She Should Die” above a sentence reading, “Take a look at the diagram and the reasons I give, then give me $20 to help pay a hit man. ”

Enforcement Consistency Schools have double standard for computer vandalism and crime “It was just a joke. ” Nerd discipline School yanks Internet access Legal punishments Incident policy $10, 000 damage award copyright 2008 Ed Tech Journeys

The Evolution of 'Nerd Discipline' As with most schools, our overall experience with computer technology, classroom applications, networks, and controlled internet access has been positive and productive. There is, however, a small, smart, and venturesome segment of our student population whose actions sometimes make it otherwise. These are individuals who use school computers--occasionally in conjunction with computers at home--to test every rule, procedure, and established guideline. . . and thus challenge us to devise new and different ways of dealing fairly and effectively with a whole new category of "electronic" infractions. The infractions can range in severity from downloading objectionable material to exchanging passwords, and from intentionally deleting student files to planting software devices designed to disable one or more targeted workstations, a whole department, or the school's entire network. Through constant monitoring and review of policies and rules, we can make every school's experience with computer technology as positive and productive as it can and should be. Jeannine Clark is an assistant principal at Clarkstown High School North in New City, N. Y. , and the school's building coordinator for the district's technology initiative.

School yanks student internet access By Rebecca Flowers A school in Cloverdale, Calif. , is being criticized for its decision to shut down student access to the internet after two local teens were accused of hacking Pentagon computers. Some charge the school overreacted in issuing the internet ban, but school officials disagree. The two students, sophomores at Cloverdale High School, have not been charged with any crimes, and investigators are certain the school's computer network was not used during any of the attacks. But the fear of sabotage or retaliation compelled school officials to close down access to the internet for all students at the school on March 5 Although the FBI had not contacted the school, John Hudspeth, the boys' computer science teacher, disabled the hackers' network accounts and froze their personal directories. "We had tried to limit the privileges of only the two hacking students, to allow the rest of the student body and faculty to enjoy continued online services, " said Bill Cox, president of the board of education. "But either other students were helping our hackers out of friendship or because they saw hacking as 'cool’ or our hackers had captured other account passwords and were using those accounts in direct violation of our Acceptable Use Contract that all network users sign. " Threats of further retaliation in the Wired article coupled with attacks on one of the ISPs were enough to convinced Cox that strong action was necessary. "Do we just wait around for our high school server to be trashed? " he said. School officials said the temporary suspension was needed to allow them to regroup and learn more about security. Cox also felt that the student body needed to think about the hacking issues in a more reasoned light.

Enforcement Who do I call? When should I escalate How do I secure the evidence? How do I limit the damage? Do I have to notify users of the breach? What long term actions are needed? copyright 2008 Ed Tech Journeys

Personal Use “School computers, networks, and Internet access are provided to support the educational mission of the school. They are to be used primarily for school-related purposes. Incidental personal use must not interfere with the employee’s job performance, must not violate any of the rules contained in this policy or the student AUP, and must not damage the school’s hardware, software, or communications systems. ” • NSBA Legal Issues and Education Technology copyright 2008 Ed Tech Journeys

Privacy Parents & Public can access Web Logs Exeter Schools Indiana Superintendents E-Mail and all electronic data is discoverable in litigation Utah lawsuit School Board’s e-communications may be in violation of state’s Sunshine Laws South Carolina, Pennsylvania, copyright 2008 Ed Tech Journeys

Improper Access Images from web pages are stored in cache and can be accessed from hard drive even without Internet access Physics Teacher fired Dean of Harvard Divinity School Amero Tragedy copyright 2008 Ed Tech Journeys

N. J. district sues teacher for allegedly viewing web porn From e. School News staff and wire service reports The Bergenfield, N. J. , board of education is suing a physics teacher to recoup wages it paid him while he allegedly viewed computer pornography during school hours. The viewing took place in a school physics room and included times when students were in the room, school officials said. According to the Associated Press, Alan Ross, who taught 11 th- and 12 th-grade chemistry, physics, and earth science before being suspended without pay last year, also has a tenure challenge pending. If Ross is found guilty, he would lose tenure and the board would be allowed to fire him. A report on computer-stored information viewed from Nov. 3 through Dec. 19, 1997 showed visits to about 2, 900 sites, more than half of which were categorized as adult or personal. All of the online visits occurred during school time--and about 55 percent while students were present in the physics room, school officials said. No sites were visited on the three days Ross was absent during that period, they said.

Harassment Off color and potentially offensive Internet jokes and e-mails circulating among staff may create a “hostile” environment Teacher suspended Harassment rules apply equally to electronic communications Report abuse Take immediate steps copyright 2008 Ed Tech Journeys

Newslines--Judge upholds teacher’s suspension over sexually explicit e. Mail e. School News staff and wire service reports A judge has upheld the three-week suspension without pay of a Scottsbluff, Neb. , middle school teacher accused of repeatedly sending sexually explicit materials on the school district’s e. Mail system. Gerald Schmeckpeper was suspended in December for insubordination when he disobeyed repeated requests to stop his e. Mail practice. The school board upheld the suspension in January. Schmeckpeper argued that he was told only to use caution when opening e. Mail. But District Judge Robert Hippe on July 13 said there was sufficient evidence to suspend Schmeckpepper. Schmeckpeper was receiving and sending e. Mail with crude jokes and cartoons and had several sexually explicit pictures stored electronically, Hippe said.

Copyright LA Schools sued for $4. 8 million in copyright abuse case LA Schools settle copyright suit Fair Use suit could influence what schools can publish on the web copyright 2008 Ed Tech Journeys

Alleged software piracy could cost LA schools $4. 8 million e. School News Staff Reports A coalition of software makers that includes Microsoft Corp. has targeted the Los Angeles Unified School District (LAUSD), alleging its teachers and other employees have illegally copied software programs. The charges of piracy could cost the nation's second-largest school district (after New York City) nearly $5 million over the next three years. Under a proposed settlement, the district would pay $300, 000 to the Business Software Alliance (BSA), a trade group based in Washington State that was formed by Microsoft and other software producers to protect their copyrights. But the real cost of the settlement, which at press time was still subject to board approval, is the estimated $4. 5 million the district would be forced to spend to replace the unlicensed software that allegedly has spread throughout its classrooms.

Newslines--LAUSD school board settles software piracy charge e. School News Staff and Wire Reports The Los Angeles Unified School District (LAUSD) will pay a computer trade group $300, 000 to settle a lawsuit alleging that copyrighted computer programs were being unlawfully duplicated for use in schools. The settlement, approved Feb. 9 by the LAUSD school board, also requires the district to spend $1. 5 million over the next three years on an eight-member team to find and eliminate any unauthorized software and to train staff and students on district policy prohibiting the unlawful duplication of computer programs. The Business Software Alliance, an organization formed by Microsoft Corp. , Novell Inc. , and other computer software companies, alleged that the West Valley Occupational Center in Woodland Hills used unauthorized copies of numerous types of software, including Microsoft Word and Adobe Photoshop. The group said it had found at least 1, 399 copies of software that it contended were being used without authorization and asked for more than $562, 000 in compensation. LAUSD officials admitted no wrongdoing, but their legal counsel recommended settling to avoid an even more costly court battle.

Newspaper 'fair use' challenge could limit what schools and others post on the web: LA Times and Washington Post sue web site for copyright infringement From e. School News staff and wire reports In a case with broad implications about what you can post on your schools' web sites, the Los Angeles Times and the Washington Post have filed a copyright-infringement lawsuit against the operator of a site that posts their stories without permission. The lawsuit, filed Oct. 1 in a federal court in Los Angeles, accuses the Free Republic site of using hundreds of stories from the two newspapers, violating their copyrights and diverting users and potential revenue from their own sites. Rex Heinke, an attorney for the newspapers, said the Free Republic site has been posting the stories "on a very large scale for a very long time. ” Reproducing the stories without the publishers' consent is financially detrimental to the newspaper companies, Heinke said. The newspapers rely on hits to their own web sites to generate advertising sales, he said. The Free Republic site, based in Fresno, Calif. , posts the stories and allows users to write comments about them. The site's operator, Jim Robinson, said he has ignored warnings from the newspapers because the practice is protected by the First Amendment and the "fair use" doctrine of copyright law.

Teacher Web Sites created by teachers for their students that are not hosted on the school’s computer system may expose the teacher to risk. Whenever possible migrate the teacher’s site to the school system where he/she is protected by the schools AUP, and computer use policies copyright 2008 Ed Tech Journeys

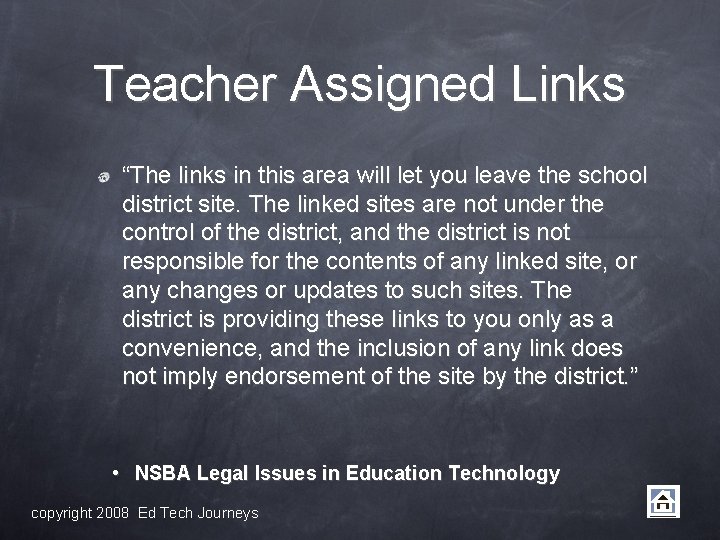
Teacher Assigned Links “The links in this area will let you leave the school district site. The linked sites are not under the control of the district, and the district is not responsible for the contents of any linked site, or any changes or updates to such sites. The district is providing these links to you only as a convenience, and the inclusion of any link does not imply endorsement of the site by the district. ” • NSBA Legal Issues in Education Technology copyright 2008 Ed Tech Journeys

Confidentiality The Family Education Rights and Privacy Act (FERPA) requires schools to have a policy that grants parents the rights to inspect and review the educational records of their children within 45 days of a request. FERPA also requires a parent’s written consent before disclosing personally identifiable information about a student.

Advertising School employees are often involved in outside businesses and they may find it tempting to advertise or solicit using the school’s e-mail. Prohibition should include sending messages from home or other outside computer to school district e-mail users. copyright 2008 Ed Tech Journeys

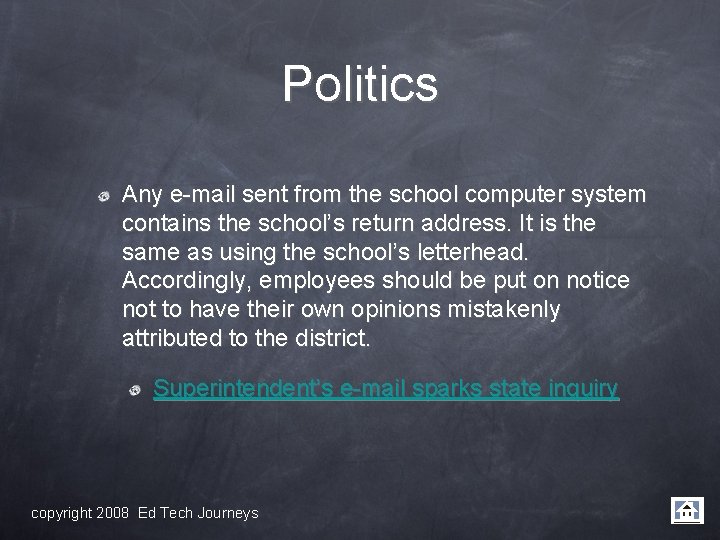
Politics Any e-mail sent from the school computer system contains the school’s return address. It is the same as using the school’s letterhead. Accordingly, employees should be put on notice not to have their own opinions mistakenly attributed to the district. Superintendent’s e-mail sparks state inquiry copyright 2008 Ed Tech Journeys

Newslines--Middle school principal suspended for e. Mail violation e. School News Staff and wire service reports A Massachusetts middle school principal was suspended for 10 days because she sent an e. Mai message to her staff urging them to vote for a political candidate. Mary A. Toomey, principal of the South Lawrence East School, might also have violated state ethics laws. “As a result of the investigation, I determined that Mary Toomey exercised poor judgment, ” said Lawrence Public Schools Superintendent Mae E. Gaskins. Toomey e. Mailed the school’s staff soliciting their votes for Nancy J. Kennedy, who was running a sticker campaign for school committee. She sent the e. Mail the day before the Oct. 5 primary election. The e. Mail said Kennedy needed voters to place stickers printed with her name directly on the ballot. The stickers would be available at the school’s front office, according to the e. Mail message. Kennedy received the votes she needed and went on to win a spot on the committee. School committee spokeswoman Martha E. Previte said Toomey should have received a harshe punishment.

Fundraising Schools may decide to permit fundraising with prior approval or they will prohibit it. If they permit fundraising activity they must be careful not to discriminate and bar any speakers based on the message. copyright 2008 Ed Tech Journeys

FOIL Are e-mail, web logs, spreadsheets & word processing documents considered records under FOIL? Web site logs Policy directives Correspondence and memos related to business Work schedules and assignments Agendas and minutes of meetings Drafts of documents circulated for comment Any document that initiates, authorizes or completes a business transaction

FOIL Parents & Public can access Web Logs Exeter Schools Indiana Superintendents E-Mail, IM, Voice Mail, etc. is discoverable in litigation Utah lawsuit copyright 2008 Ed Tech Journeys

FOIL Administrators must plan for and design a filing structure that can adequately support operational needs and record keeping requirements. You will have to retrieve everything - no matter where it is stored in mandatory Discovery. If you keep everything it’s a problem If you delete everything it’s a problem Generally, records transmitted through email and electronic systems will have the same retention periods as records in other copyright 2008 Ed Tech Journeys formats.

Court: Schools must let parents view internet-use logs From e. School News staff and wire service reports In a decision with broad implications for schools nationwide, a New Hampshire judge has ruled that the Exeter school district must make public copies of its internet history logs so a father can check whether officials are doing enough to keep pupils away from the web’s seedy side. James Knight, a father of four whose children attended district schools until recently, filed a lawsuit asking a judge to force the district to hand over its internet logs after educators decided not to use filtering programs on computers children use. The programs, which have been criticized for their accuracy, block access to objectionable internet sites. The district decided to use supervision and spot checks by teachers instead

Superintendents’ use of school computers questioned From e. School News staff and wire service reports An investigation of computer records from 49 Indiana school districts by the Indianapolis Star has raised questions about what constitutes appropriate use of computers by administrators. In a Feb. 18 story, the Star reported that superintendents who are in charge of enforcing their districts’ web-surfing policies often violate their own rules. While many school internet policies say web surfing should be for educational use only, some Indiana superintendents are shopping for cars, planning trips, and looking for other jobs on their district-issued computers, the Star reported. In fact, one superintendent’s internet records reportedly included two sites with pornographic material—an apparent violation of common school district internet policies, and one that cost former Hamilton Southeastern Superintendent Robert Herrold his job in September. It was Herrold’s example that prompted the Star’s investigation. The Star’s review of 6, 691 web sites on superintendents’ computers showed that half of the sites clearly were education pages. But 3, 000 other sites—some of which also could have been viewed for educational purposes—ranged from the popular Amazon. com shopping site to more obscure sites.

DA eyes agency's failure to release school internet logs: Utah Education Network faces sanctions for overwriting data it was ordered to disclose Failure to hand over certain logs that track the wanderings of school computer users on the world wide web--including records showing attempts to visit sexually oriented or other banned sites--could result in a criminal investigation by a county district attorney in Utah. The target of the probe: the Utah Education Network (UEN), a public/private consortium that provides internet service to Utah's K-12 schools districts. In April, Michael Sims, an anti-censorship internet activist, filed for access to the school computer logs under Utah's sunshine law. He wanted to check what web sites were being blocked by internet content filters used by Utah schools. At first, UEN officials refused Sims' request, claiming they didn't own the logs. They said those records belonged to the individual school districts. Sims appealed that denial to the State Records Committee. At a hearing last month, the committee agreed with Sims and ordered that the computer logs, purged of any confidential material, be released.

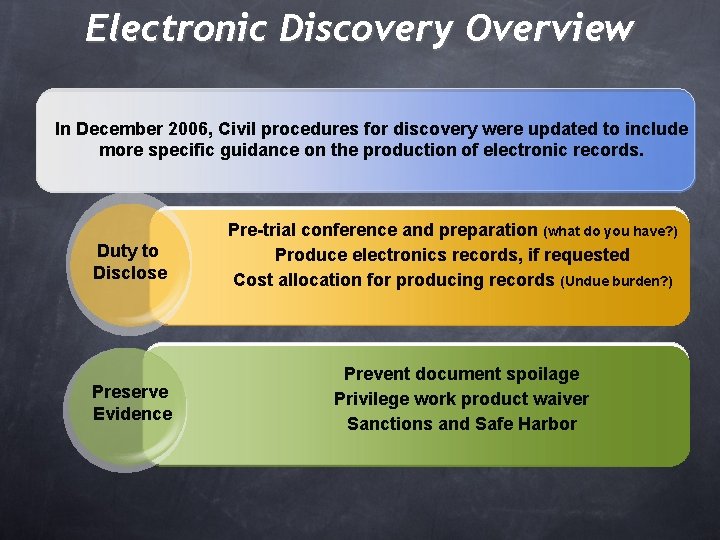
Electronic Discovery Overview In December 2006, Civil procedures for discovery were updated to include more specific guidance on the production of electronic records. Duty to Disclose Preserve Evidence Pre-trial conference and preparation (what do you have? ) Produce electronics records, if requested Cost allocation for producing records (Undue burden? ) Prevent document spoilage Privilege work product waiver Sanctions and Safe Harbor

E-Discovery Create an enforce an e-Document policy that minimizes the time Non-FOILable information is kept. Create a litigation response that preserves data at the outset of litigation. Educate employees on the need for a business approach to e-documents. NSBA Legal Issues and Ed Tech copyright 2008 Ed Tech Journeys

Duty to Disclose • Define the environment and data controls • Restrict data storage locations o. Email & Voice mail o. Shared folders and files o. Database • Data classification, handling and disposal policy • Document Retention Schedules (especially email) • User training • Audit and assessment to validate controls • Forensic Analysis capabilities o. Internal discovery o. Opposing counsel - "come and get it. "

Preserve Evidence • Records Management System o. Enterprise wide o. Litigation support only • System controls • Encryption • Backup Records • Notice to stop operations or restrict data disposal

Open Meeting & Sunshine Laws The use of e-mail and conferencing tools have raised questions. If one Board member e-mails another about school board business is that a violation of the state’s sunshine laws? How about when board members use the telephone, e-mail, or faxes to poll one another about board business? copyright 2008 What about soliciting feedback from the public ? Edelectronically Tech Journeys

Open Meetings Law Electronic distribution of Board packets: OK E-mail between members considered a written memo and is discoverable. Interaction via e-mail, bulletin board, chat, instant messaging, or video conference most likely constitutes a meeting and is in violation. copyright 2008 Ed Tech Journeys

Open Meetings Law Resource: Robert Freeman Committee on Open Government www. dos. state. ny. us. coogwww. html opengov@dos. state. ny. us copyright 2008 Ed Tech Journeys

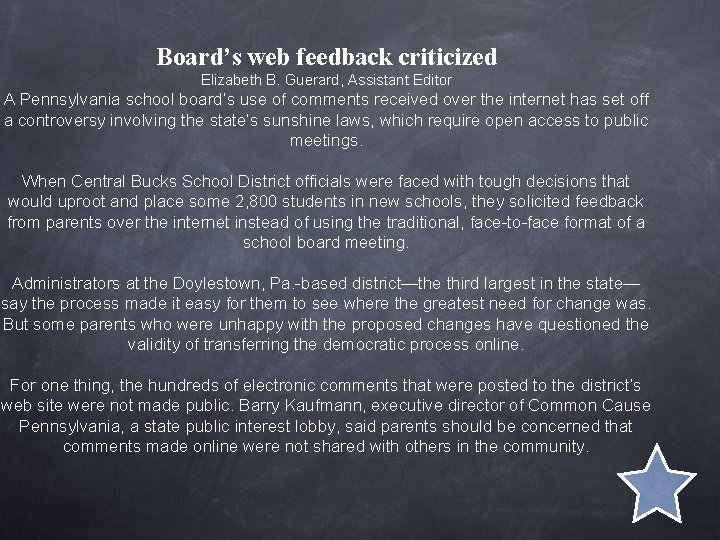
Board’s web feedback criticized Elizabeth B. Guerard, Assistant Editor A Pennsylvania school board’s use of comments received over the internet has set off a controversy involving the state’s sunshine laws, which require open access to public meetings. When Central Bucks School District officials were faced with tough decisions that would uproot and place some 2, 800 students in new schools, they solicited feedback from parents over the internet instead of using the traditional, face-to-face format of a school board meeting. Administrators at the Doylestown, Pa. -based district—the third largest in the state— say the process made it easy for them to see where the greatest need for change was. But some parents who were unhappy with the proposed changes have questioned the validity of transferring the democratic process online. For one thing, the hundreds of electronic comments that were posted to the district’s web site were not made public. Barry Kaufmann, executive director of Common Cause Pennsylvania, a state public interest lobby, said parents should be concerned that comments made online were not shared with others in the community.

Private web forum snags school board e. School News staff and wire service reports Members of the Beaufort County (South Carolina) School Board and district Superintendent Herman Gaither have come under fire for using a private internet bulletin board to discuss school district matters. The private electronic forum might constitute a violation of the state’s freedom of information laws, a South Carolina media attorney says. The issue raises questions about how existing laws meant to ensure the open exchange of public information should be applied to modern technologies such as e. Mail and the internet. Gaither said he set up the bulletin board so he could share information with board members on “sensitive or semiprivate information. ” Only Gaither and board members had access to the site, which let them read and respond to internal messages. Jay Bender, the attorney for the South Carolina Press Association, said the state’s Freedom of Information Act prohibits public agencies from using technology to conduct their business in private and that the bulletin board might violate the law.

Domain Names Norwichschools. org vs Norwichschools. com Purchase all available names Maintain all school domain names rigorously Porno site appears under school name High cost of re-purchase Legitimate third parties have put up school web sites that many parents believe is the “official” school site. Irate e-mails that school didn’t respond copyright 2008 Ed Tech Journeys

CIPA & E-Rate Must certify that all users are protected from inappropriate materials Must have public meeting Must have AUP copyright 2008 Ed Tech Journeys


Software Audits LA Schools RICs/Schools/BOCES P. O. ’s, Licenses, Hard drive snapshots copyright 2008 Ed Tech Journeys

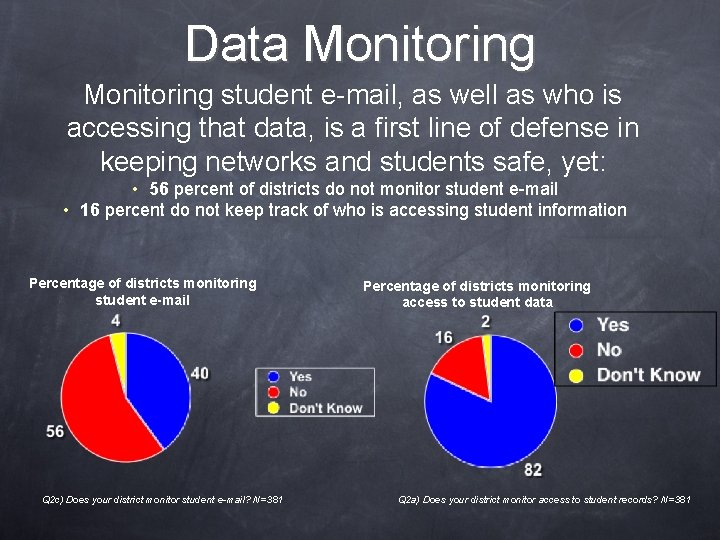
Data Monitoring student e-mail, as well as who is accessing that data, is a first line of defense in keeping networks and students safe, yet: • 56 percent of districts do not monitor student e-mail • 16 percent do not keep track of who is accessing student information Percentage of districts monitoring student e-mail Q 2 c) Does your district monitor student e-mail? N=381 Percentage of districts monitoring access to student data Q 2 a) Does your district monitor access to student records? N=381

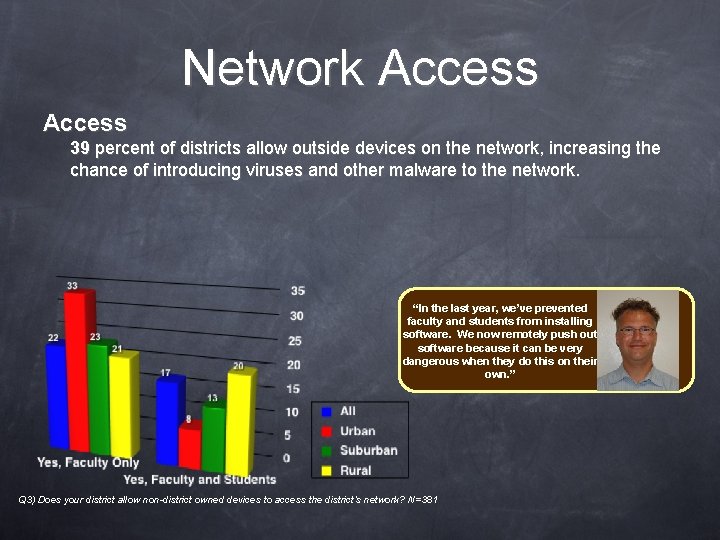
Network Access 39 percent of districts allow outside devices on the network, increasing the chance of introducing viruses and other malware to the network. “In the last year, we’ve prevented faculty and students from installing software. We now remotely push out software because it can be very dangerous when they do this on their own. ” Q 3) Does your district allow non-district owned devices to access the district’s network? N=381

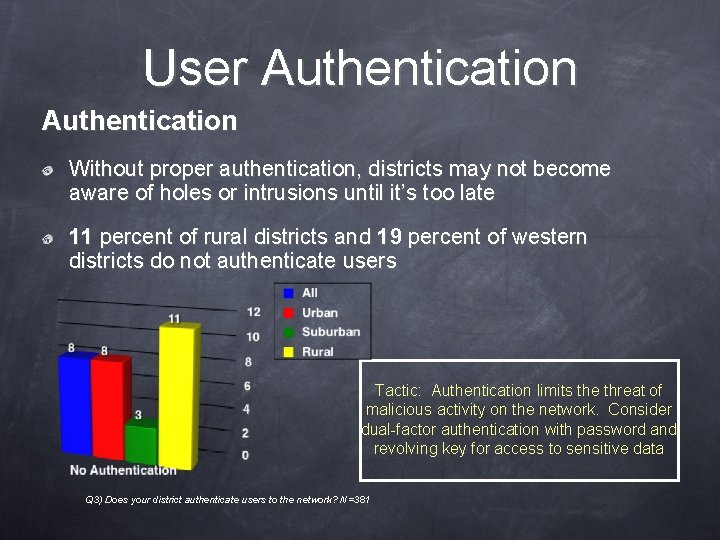
User Authentication Without proper authentication, districts may not become aware of holes or intrusions until it’s too late 11 percent of rural districts and 19 percent of western districts do not authenticate users Tactic: Authentication limits the threat of malicious activity on the network. Consider dual-factor authentication with password and revolving key for access to sensitive data Q 3) Does your district authenticate users to the network? N=381

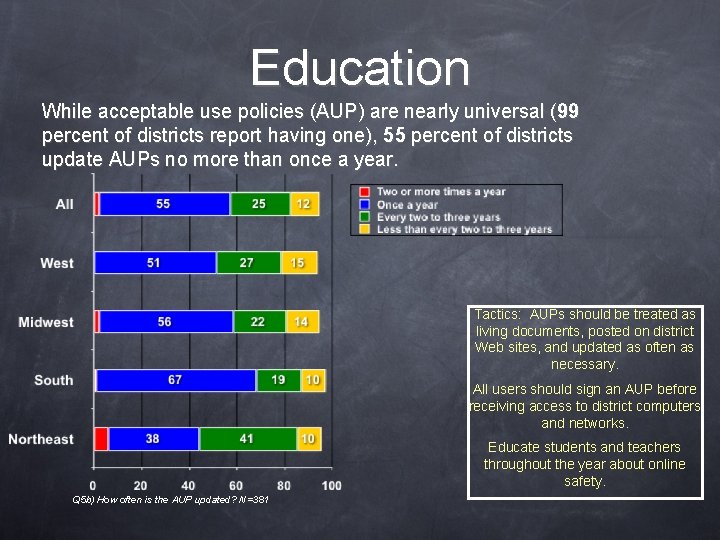
Education While acceptable use policies (AUP) are nearly universal (99 percent of districts report having one), 55 percent of districts update AUPs no more than once a year. Tactics: AUPs should be treated as living documents, posted on district Web sites, and updated as often as necessary. All users should sign an AUP before receiving access to district computers and networks. Educate students and teachers throughout the year about online safety. Q 5 b) How often is the AUP updated? N=381

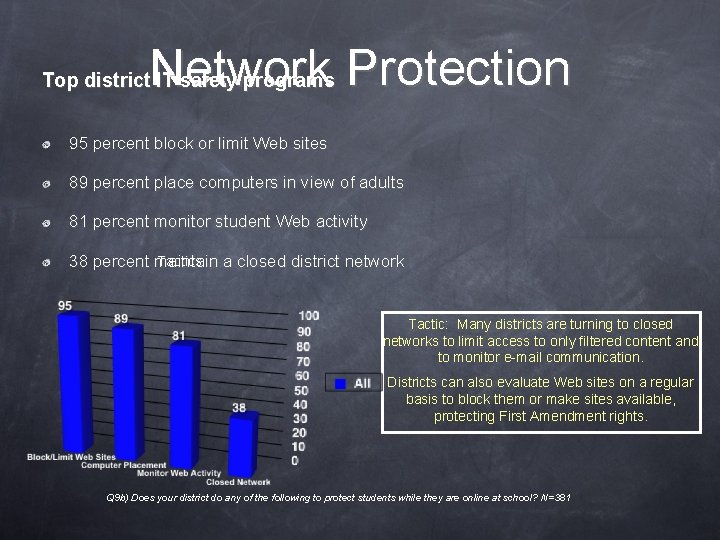
Network Protection Top district IT safety programs 95 percent block or limit Web sites 89 percent place computers in view of adults 81 percent monitor student Web activity Tactics 38 percent maintain a closed district network Tactic: Many districts are turning to closed networks to limit access to only filtered content and to monitor e-mail communication. Districts can also evaluate Web sites on a regular basis to block them or make sites available, protecting First Amendment rights. Q 9 b) Does your district do any of the following to protect students while they are online at school? N=381

Network Protection Districts rely on filtering software as a primary defense method. More districts could benefit from using safety education as a tool to improve security. IT Security Defenses Tactic: Filtering software is not a substitute for educating students, parents and staff about the dangers of the Internet. Districts need to engage the entire community in the IT security process. “I would say that we’re constantly looking for ways to improve. At a minimum, [these new technologies] take a lot of management. What we’re looking for as technology evolves are new ways to defend. ” Q 10) What are some additional ways your district protects students while they are online? N=375

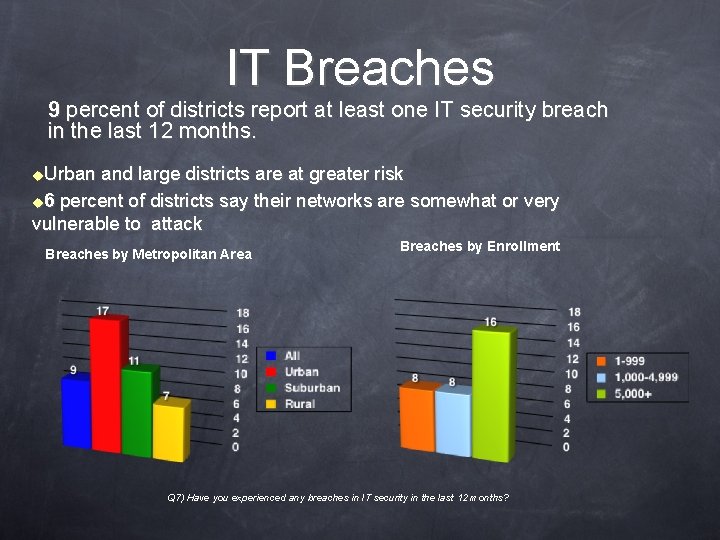
IT Breaches 9 percent of districts report at least one IT security breach in the last 12 months. u. Urban and large districts are at greater risk u 6 percent of districts say their networks are somewhat or very vulnerable to attack Breaches by Metropolitan Area Breaches by Enrollment Q 7) Have you experienced any breaches in IT security in the last 12 months?

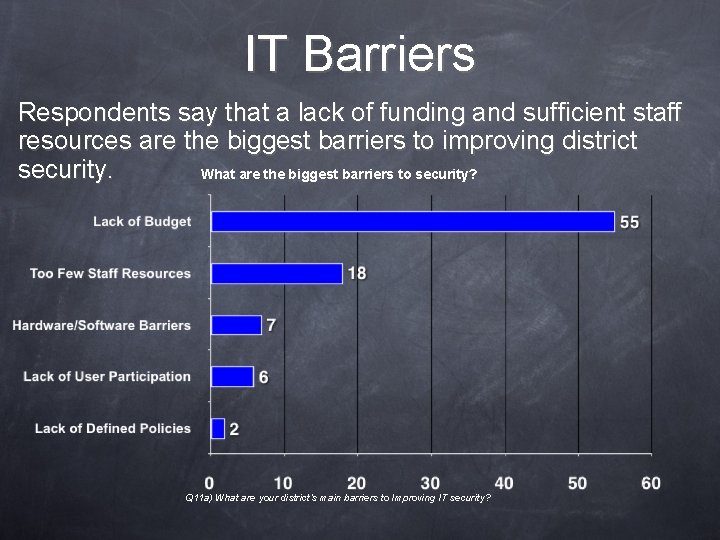
IT Barriers Respondents say that a lack of funding and sufficient staff resources are the biggest barriers to improving district security. What are the biggest barriers to security? Q 11 a) What are your district’s main barriers to Improving IT security?

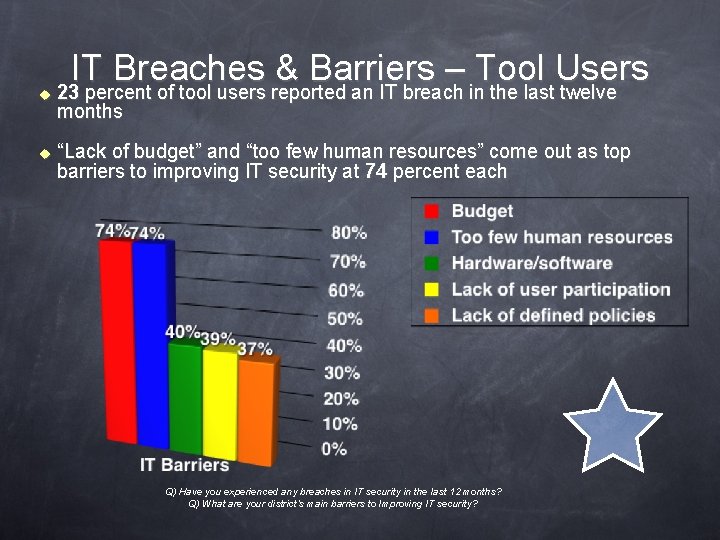
u u IT Breaches & Barriers – Tool Users 23 percent of tool users reported an IT breach in the last twelve months “Lack of budget” and “too few human resources” come out as top barriers to improving IT security at 74 percent each Q) Have you experienced any breaches in IT security in the last 12 months? Q) What are your district’s main barriers to Improving IT security?

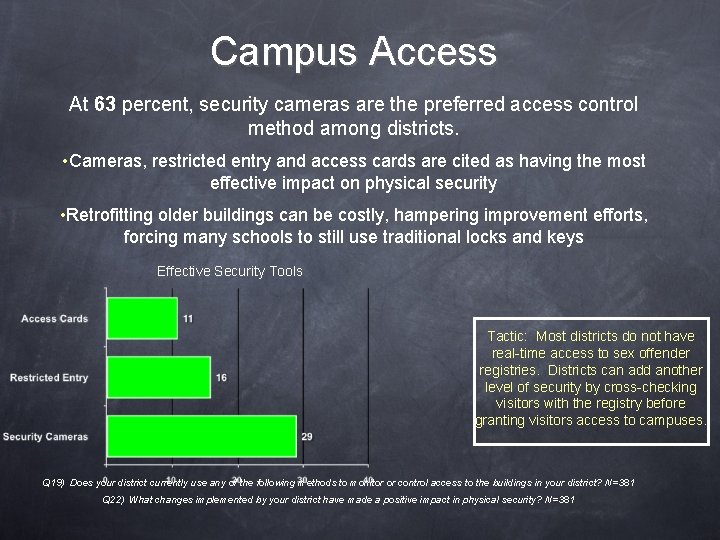
Campus Access At 63 percent, security cameras are the preferred access control method among districts. • Cameras, restricted entry and access cards are cited as having the most effective impact on physical security • Retrofitting older buildings can be costly, hampering improvement efforts, forcing many schools to still use traditional locks and keys Effective Security Tools Tactic: Most districts do not have real-time access to sex offender registries. Districts can add another level of security by cross-checking visitors with the registry before granting visitors access to campuses. Q 19) Does your district currently use any of the following methods to monitor or control access to the buildings in your district? N=381 Q 22) What changes implemented by your district have made a positive impact in physical security? N=381

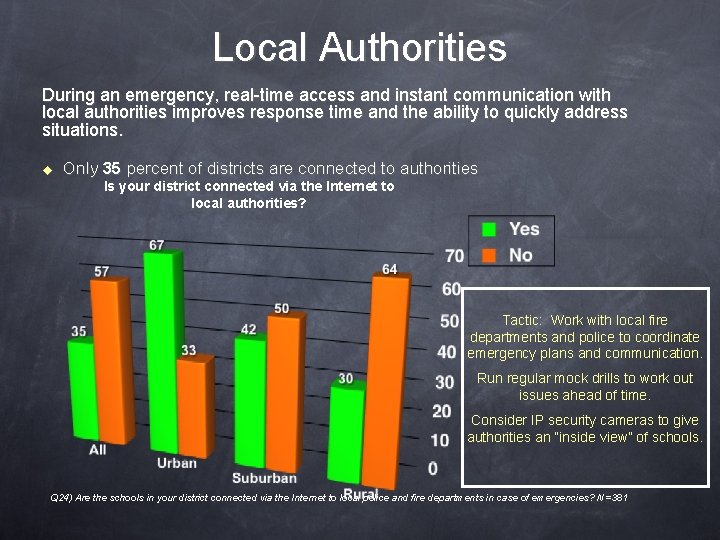
Local Authorities During an emergency, real-time access and instant communication with local authorities improves response time and the ability to quickly address situations. u Only 35 percent of districts are connected to authorities Is your district connected via the Internet to local authorities? Tactic: Work with local fire departments and police to coordinate emergency plans and communication. Run regular mock drills to work out issues ahead of time. Consider IP security cameras to give authorities an “inside view” of schools. Q 24) Are the schools in your district connected via the Internet to local police and fire departments in case of emergencies? N=381

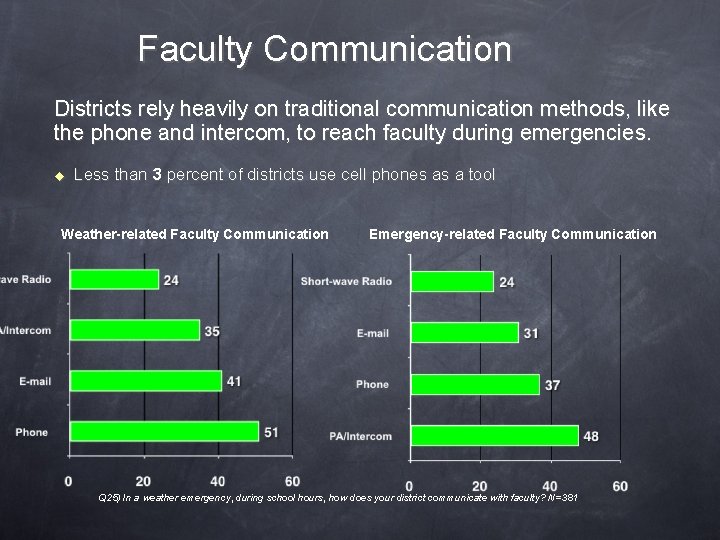
Faculty Communication Districts rely heavily on traditional communication methods, like the phone and intercom, to reach faculty during emergencies. u Less than 3 percent of districts use cell phones as a tool Weather-related Faculty Communication Emergency-related Faculty Communication Q 25) In a weather emergency, during school hours, how does your district communicate with faculty? N=381

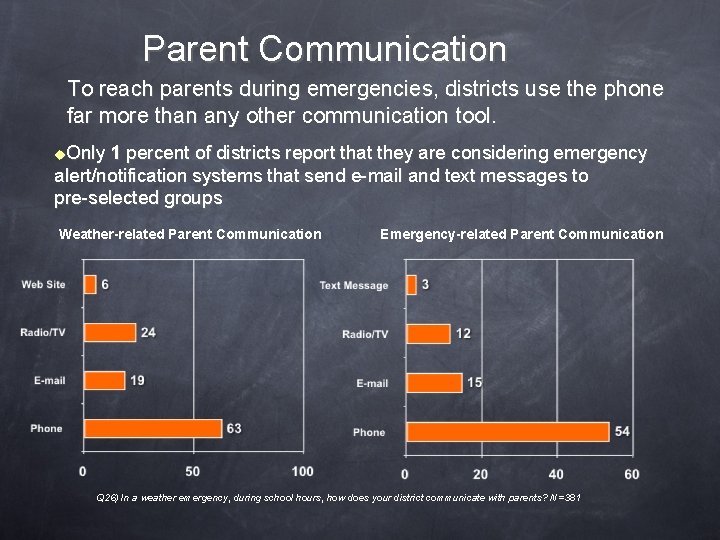
Parent Communication To reach parents during emergencies, districts use the phone far more than any other communication tool. u. Only 1 percent of districts report that they are considering emergency alert/notification systems that send e-mail and text messages to pre-selected groups Weather-related Parent Communication Emergency-related Parent Communication Q 26) In a weather emergency, during school hours, how does your district communicate with parents? N=381

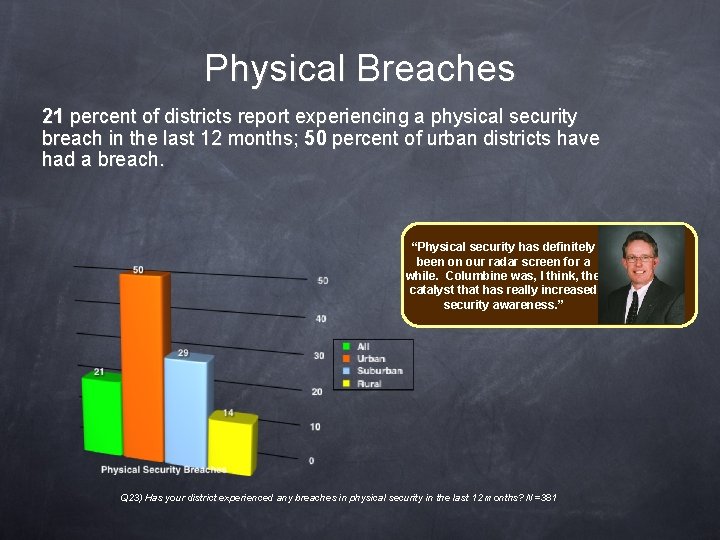
Physical Breaches 21 percent of districts report experiencing a physical security breach in the last 12 months; 50 percent of urban districts have had a breach. “Physical security has definitely been on our radar screen for a while. Columbine was, I think, the catalyst that has really increased security awareness. ” Q 23) Has your district experienced any breaches in physical security in the last 12 months? N=381

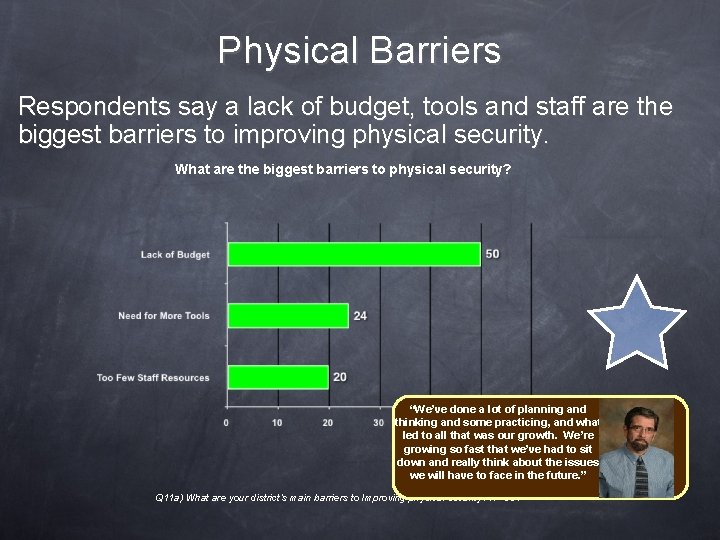
Physical Barriers Respondents say a lack of budget, tools and staff are the biggest barriers to improving physical security. What are the biggest barriers to physical security? “We’ve done a lot of planning and thinking and some practicing, and what led to all that was our growth. We’re growing so fast that we’ve had to sit down and really think about the issues we will have to face in the future. ” Q 11 a) What are your district’s main barriers to Improving physical security? N=381
 Difference between voyage charter and time charter
Difference between voyage charter and time charter Market risk credit risk operational risk
Market risk credit risk operational risk Freedom coalition for charter schools
Freedom coalition for charter schools Charter school marketing
Charter school marketing Loudoun county school board
Loudoun county school board Service delivery charter for schools
Service delivery charter for schools Ten risk management
Ten risk management How many splash exposures were reported at uf in 2020
How many splash exposures were reported at uf in 2020 Did investigator assign exposures
Did investigator assign exposures How many splash exposures were reported at uf in 2020?
How many splash exposures were reported at uf in 2020? How many splash exposures were reported at uf in 2020?
How many splash exposures were reported at uf in 2020? Types of foreign exchange exposure
Types of foreign exchange exposure Power schools huntsville city schools
Power schools huntsville city schools Safety vs target vs reach
Safety vs target vs reach National charter school resource center
National charter school resource center Key risk indicators financial risk management
Key risk indicators financial risk management Risk map
Risk map Republic act 10121
Republic act 10121 Education level primary secondary tertiary malaysia
Education level primary secondary tertiary malaysia National schools observatory
National schools observatory Uae vision 2021 education
Uae vision 2021 education Change management charter
Change management charter Charter management spain
Charter management spain Define charter party
Define charter party Kontinuitetshantering i praktiken
Kontinuitetshantering i praktiken Typiska drag för en novell
Typiska drag för en novell Tack för att ni lyssnade bild
Tack för att ni lyssnade bild Ekologiskt fotavtryck
Ekologiskt fotavtryck Shingelfrisyren
Shingelfrisyren En lathund för arbete med kontinuitetshantering
En lathund för arbete med kontinuitetshantering Personalliggare bygg undantag
Personalliggare bygg undantag Tidbok för yrkesförare
Tidbok för yrkesförare Anatomi organ reproduksi
Anatomi organ reproduksi Densitet vatten
Densitet vatten Datorkunskap för nybörjare
Datorkunskap för nybörjare Boverket ka
Boverket ka Mall för debattartikel
Mall för debattartikel För och nackdelar med firo
För och nackdelar med firo Nyckelkompetenser för livslångt lärande
Nyckelkompetenser för livslångt lärande Påbyggnader för flakfordon
Påbyggnader för flakfordon Tryck formel
Tryck formel Publik sektor
Publik sektor Kyssande vind analys
Kyssande vind analys Presentera för publik crossboss
Presentera för publik crossboss Jiddisch
Jiddisch Bat mitza
Bat mitza Treserva lathund
Treserva lathund Mjälthilus
Mjälthilus Claes martinsson
Claes martinsson Centrum för kunskap och säkerhet
Centrum för kunskap och säkerhet Programskede byggprocessen
Programskede byggprocessen Mat för idrottare
Mat för idrottare Verktyg för automatisering av utbetalningar
Verktyg för automatisering av utbetalningar Rutin för avvikelsehantering
Rutin för avvikelsehantering Smärtskolan kunskap för livet
Smärtskolan kunskap för livet Ministerstyre för och nackdelar
Ministerstyre för och nackdelar Tack för att ni har lyssnat
Tack för att ni har lyssnat Mall för referat
Mall för referat Redogör för vad psykologi är
Redogör för vad psykologi är Borstål, egenskaper
Borstål, egenskaper Atmosfr
Atmosfr Borra hål för knoppar
Borra hål för knoppar Vilken grundregel finns det för tronföljden i sverige?
Vilken grundregel finns det för tronföljden i sverige? Stickprovsvarians
Stickprovsvarians Tack för att ni har lyssnat
Tack för att ni har lyssnat Steg för steg rita
Steg för steg rita Ledningssystem för verksamhetsinformation
Ledningssystem för verksamhetsinformation Tobinskatten för och nackdelar
Tobinskatten för och nackdelar Toppslätskivling effekt
Toppslätskivling effekt Gibbs reflekterande cykel
Gibbs reflekterande cykel Egg för emanuel
Egg för emanuel Elektronik för barn
Elektronik för barn Antikt plagg
Antikt plagg Strategi för svensk viltförvaltning
Strategi för svensk viltförvaltning Kung som dog 1611
Kung som dog 1611 Ellika andolf
Ellika andolf Romarriket tidslinje
Romarriket tidslinje Tack för att ni lyssnade
Tack för att ni lyssnade Större än
Större än Haiku dikt exempel
Haiku dikt exempel Inköpsprocessen steg för steg
Inköpsprocessen steg för steg Rbk mätning
Rbk mätning Ledarskapsteorier
Ledarskapsteorier Kolposkopi, px
Kolposkopi, px Myndigheten för delaktighet
Myndigheten för delaktighet Trög för kemist
Trög för kemist Tillitsbaserad ledning
Tillitsbaserad ledning Läkarutlåtande för livränta
Läkarutlåtande för livränta Ruin karttecken
Ruin karttecken Gumman cirkel sång
Gumman cirkel sång Texter för hinduer tantra
Texter för hinduer tantra Vad är vanlig celldelning
Vad är vanlig celldelning Bris för vuxna
Bris för vuxna Bamse för de yngsta
Bamse för de yngsta Draw rmmm plan
Draw rmmm plan Risk management avoidance
Risk management avoidance Relative risk calculation
Relative risk calculation Residual risk and secondary risk pmp
Residual risk and secondary risk pmp Tracing vs vouching
Tracing vs vouching Absolute risk vs relative risk
Absolute risk vs relative risk Activity sheet 2 to risk or not to risk
Activity sheet 2 to risk or not to risk Firm risk scorecard risk classification system
Firm risk scorecard risk classification system Pembelanjaan resiko
Pembelanjaan resiko The biggest risk is not taking any risk
The biggest risk is not taking any risk Ir x cr x dr
Ir x cr x dr Business risk vs financial risk capital structure
Business risk vs financial risk capital structure Attributable risk
Attributable risk Relative risk
Relative risk Definition of technology risk
Definition of technology risk Technology and other operational risks
Technology and other operational risks National risk and resilience unit
National risk and resilience unit Ncrq diploma
Ncrq diploma National youth at risk conference
National youth at risk conference One best way
One best way Crisis management team roles
Crisis management team roles Waste management plan for schools
Waste management plan for schools Schools of management thought
Schools of management thought Unist ulsan national institute of science and technology
Unist ulsan national institute of science and technology Assistive technology implementation plan sample
Assistive technology implementation plan sample National programme on technology enhanced learning founded
National programme on technology enhanced learning founded National institute of standards and technology
National institute of standards and technology National research university of electronic technology
National research university of electronic technology Nara national college of technology
Nara national college of technology National information technology development agency
National information technology development agency National yunlin university of science and technology
National yunlin university of science and technology National institute of agricultural technology
National institute of agricultural technology Nttaa
Nttaa National unification and the national state
National unification and the national state Top management and middle management
Top management and middle management