ecs 236 Winter 2007 Computer Security Intrusion Detection






![Anti-Spam sfelixwu@gmail. com l subject: [0 x 9876543210 ABCDEF]… l l 0 x 9876543210 Anti-Spam sfelixwu@gmail. com l subject: [0 x 9876543210 ABCDEF]… l l 0 x 9876543210](https://slidetodoc.com/presentation_image_h2/642da41757f87ee4aa310bd25e066051/image-27.jpg)








![b int bar(int a, int b) { int i, j; char buf[9]; } a b int bar(int a, int b) { int i, j; char buf[9]; } a](https://slidetodoc.com/presentation_image_h2/642da41757f87ee4aa310bd25e066051/image-63.jpg)
![“NOP Sled” Engineering Attack Code Exploit (Return. Addr) code[] = “xebx 2 ax 5 “NOP Sled” Engineering Attack Code Exploit (Return. Addr) code[] = “xebx 2 ax 5](https://slidetodoc.com/presentation_image_h2/642da41757f87ee4aa310bd25e066051/image-72.jpg)












- Slides: 121

ecs 236 Winter 2007: Computer Security: Intrusion Detection Based Approach #1: Vulnerability Dr. S. Felix Wu Computer Science Department University of California, Davis http: //www. cs. ucdavis. edu/~wu/ sfelixwu@gmail. com 01/04/2007 ecs 236 winter 2007 1

Intrusion Prevention l Prevention: This should/must never be broken in! – “This” means a perfectly designed, implemented, and managed/configured secure system! 01/04/2007 ecs 236 winter 2007 2

Intrusion Detection Prevention: This should/must never be broken in! l Detection: l – The IDS (Intrusion Detection System) approach has been taken as the “Second Line of Defense” and “Short Term Solutions”. 01/04/2007 ecs 236 winter 2007 3

Examples Application/service issues Firewalls l Email spam/vo. IP spit Spam Filters l Phishing detectors l The list goes on… l 01/04/2007 ecs 236 winter 2007 4

Examples Application/service issues Firewalls l Email spam/vo. IP spit Spam Filters l Phishing detectors l It is NOT whether we need the “detection approach” l It is whether it can be effective. l 01/04/2007 ecs 236 winter 2007 5

Intrusion Detection Prevention: This should/must never be broken in! l Detection: “This” will need to face the reality check! l – We had, have, will have so many “expected” unexpected. – Industry never really serious about cyber security – profit/market-driven 01/04/2007 ecs 236 winter 2007 6

We accept it as a fact… 01/04/2007 ecs 236 winter 2007 7

And, we have to have… 01/04/2007 ecs 236 winter 2007 8

Intrusion Detection Prevention: This should/must never be broken in! l Detection: “This” will need to face the reality check! l – We had, have, will have so many “expected” unexpected. – We had, have, will have even more “unexpected” unexpected!! 01/04/2007 ecs 236 winter 2007 9

To: All Faculty, Staff and Students On Tuesday, January 03, 2006, UC Davis implemented temporary measures to prevent the exploitation of a serious new computer vulnerability for which no patch is yet available. This vulnerability affects Windows 2000, Windows XP, Windows Server 2003, Windows 98 and ME systems and may be exploited when infected email file attachments or infected Web pages are viewed. Once a computer is infected, data may be permanently lost and/or a remote attacker could gain control of the computer. After extensive consultation with the campus leadership, the decision has been made to temporarily block wmf image attachments. These files can have a number of different extensions, but most commonly will have. wmf and. jpg extensions. 01/04/2007 ecs 236 winter 2007 10

Max-Sequence # Attack l Block LSA updates for one hour by injecting one bad LSA. – You can hit it once and come back in an hour. l Implementation Bug! – Two independently developed OSPF packages. – Max. Seq# LSA Purging has not been implemented correctly!! l Announced in May, 1997. 01/04/2007 ecs 236 winter 2007 11

What is Intrusion Detection? 01/04/2007 ecs 236 winter 2007 12

Intrusion Detection l Detecting intrusions such as – Viruses, Worms, Spywares, Phishing, Spamming, Insider, Un-authorized activities, faults/failures, among many others l Detecting and Managing anything “unexpected” – Anomalies l Question: “Detecting what? ? ” 01/04/2007 ecs 236 winter 2007 13

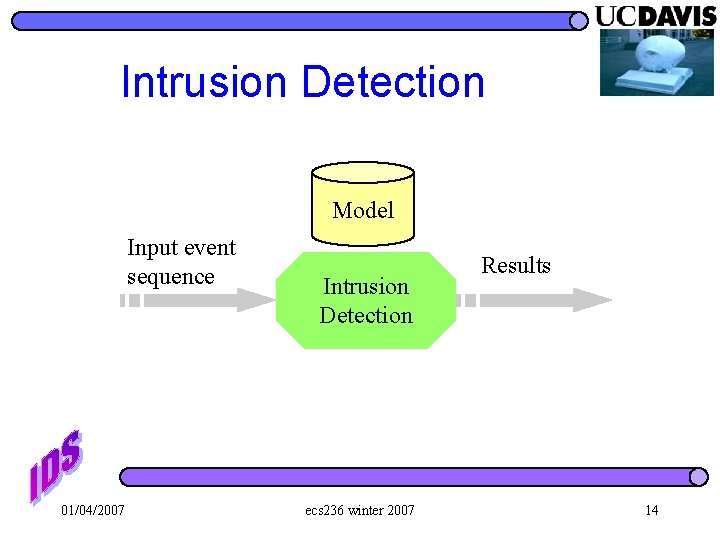
Intrusion Detection Model Input event sequence 01/04/2007 Intrusion Detection ecs 236 winter 2007 Results 14

Results? ? This email contains virus XYZ l This email might be a spam with 80% probability l This email is somewhat trusted based on your social network l This email might be malicious for reasons ABC and DEF. l 01/04/2007 ecs 236 winter 2007 15

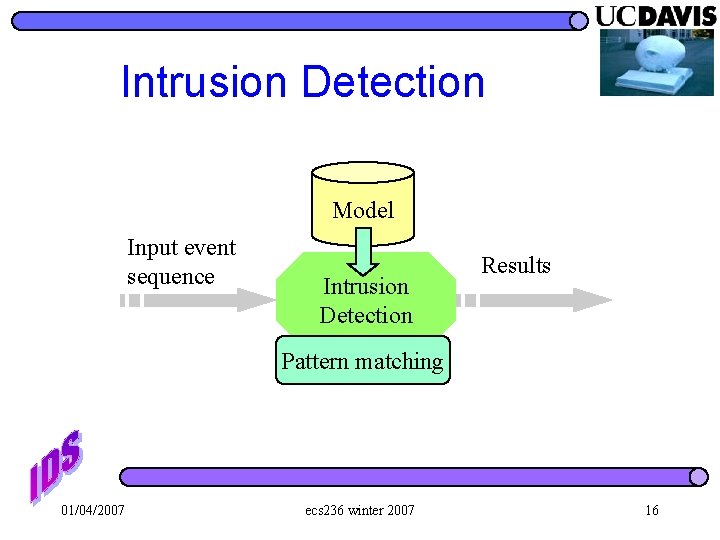
Intrusion Detection Model Input event sequence Intrusion Detection Results Pattern matching 01/04/2007 ecs 236 winter 2007 16

IDS Events TCPdump traces l OS kernel and Host-level information l BGP traces l Application Logs l Many others… l 01/04/2007 ecs 236 winter 2007 17

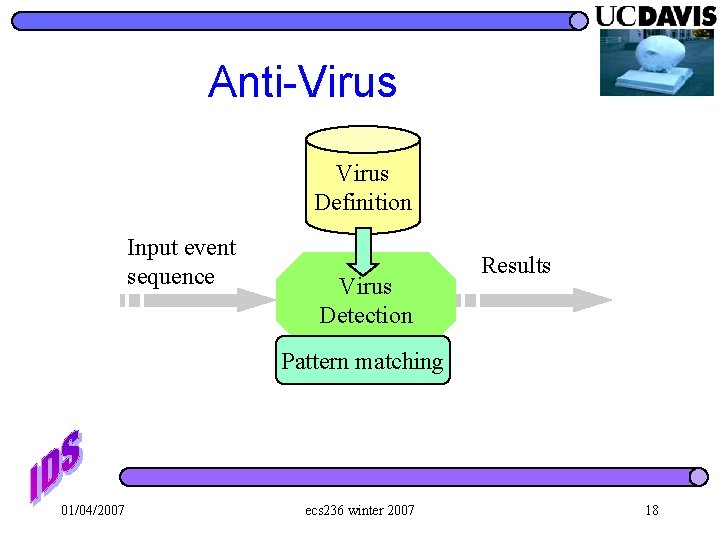
Anti-Virus Definition Input event sequence Virus Detection Results Pattern matching 01/04/2007 ecs 236 winter 2007 18

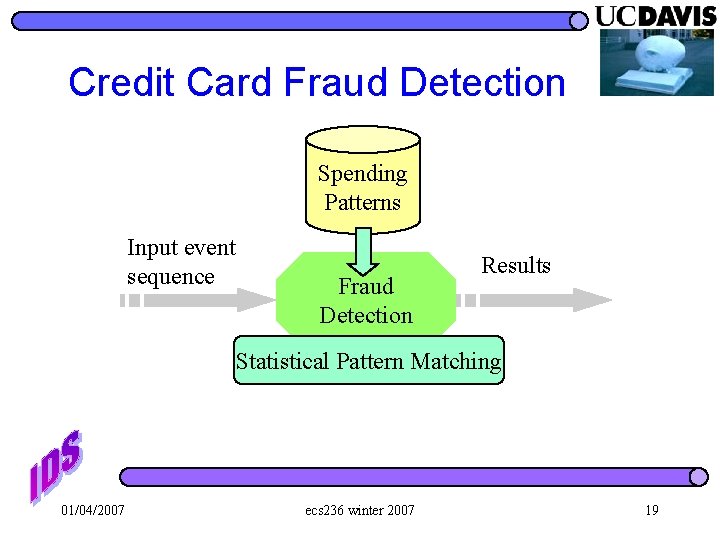
Credit Card Fraud Detection Spending Patterns Input event sequence Fraud Detection Results Statistical Pattern Matching 01/04/2007 ecs 236 winter 2007 19

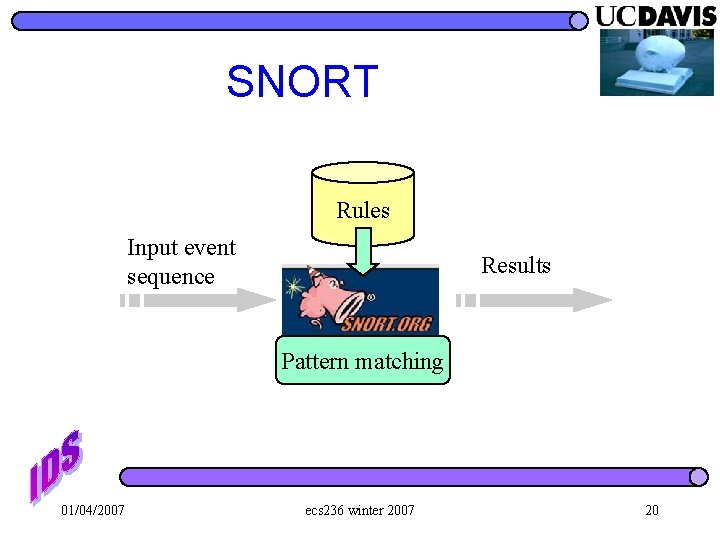
SNORT Rules Input event sequence Results Pattern matching 01/04/2007 ecs 236 winter 2007 20

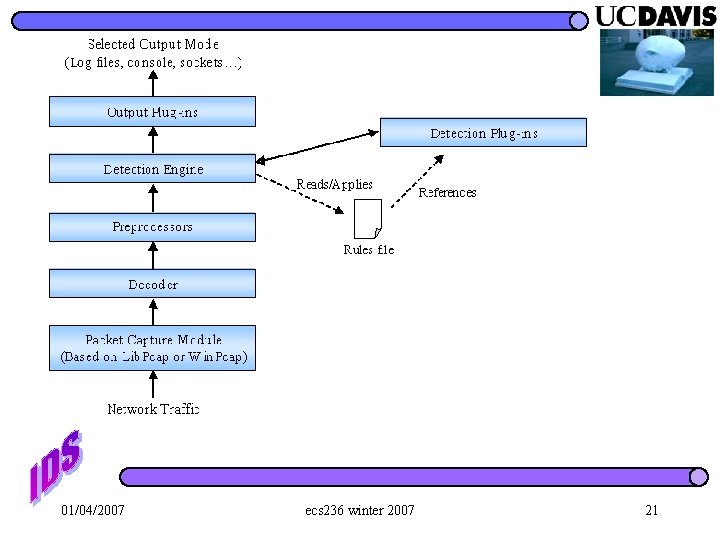
01/04/2007 ecs 236 winter 2007 21

About the Instructor l S. Felix Wu – sfelixwu@gmail. com – sfwu@ucdavis. edu – sfelixwu@yahoo. com l l l Office: 3057 Engineering II Phone: 530 -754 -7070 Office Hours: – 10 -11 a. m. on Monday and Friday – by appointment 01/04/2007 ecs 236 winter 2007 22

Why 3 email addresses? – sfelixwu@gmail. com – sfwu@ucdavis. edu – sfelixwu@yahoo. com 01/04/2007 ecs 236 winter 2007 23

Why 3 email addresses? – sfelixwu@gmail. com – sfwu@ucdavis. edu – My main email contact for everything all the time. – sfelixwu@yahoo. com 01/04/2007 ecs 236 winter 2007 24

Why 3 email addresses? – sfelixwu@gmail. com – sfwu@ucdavis. edu – My main email contact for everything all the time. – sfelixwu@yahoo. com – Read only once in the past three months… 01/04/2007 ecs 236 winter 2007 25

Why 3 email addresses? – sfelixwu@gmail. com read/response during the quarters, especially before the homework deadlines. – sfwu@ucdavis. edu – My main email contact for everything all the time. – sfelixwu@yahoo. com – Read only once in the past three months… 01/04/2007 ecs 236 winter 2007 26
![AntiSpam sfelixwugmail com l subject 0 x 9876543210 ABCDEF l l 0 x 9876543210 Anti-Spam sfelixwu@gmail. com l subject: [0 x 9876543210 ABCDEF]… l l 0 x 9876543210](https://slidetodoc.com/presentation_image_h2/642da41757f87ee4aa310bd25e066051/image-27.jpg)
Anti-Spam sfelixwu@gmail. com l subject: [0 x 9876543210 ABCDEF]… l l 0 x 9876543210 ABCDEF is the cyber social link between the instructor and the students in ecs 236, Winter 2007. 01/04/2007 ecs 236 winter 2007 27

Intrusion Detection l Practical Engineering – Performance, Accuracy, Scalability, CPU/Memory, Correlation, Deployment. l Theoretical Foundation – Detectability/Limitation, Dimensionality, Entropy, False Negative and Positive, Evaluation 01/04/2007 ecs 236 winter 2007 28

In this quarter… l The architecture of ID and IDS – Stateful versus stateless A balance between – Signature, specification, anomaly ØEngineering a Highl Analysis of ID Results Performance IDS system – Explanation and Analysis ØFundamentally understand our – Event Correlation limitations l IDS Evaluation or Attacking IDS – Attack Polymorphism and IDS Evasion l IDS Fundamental Principles 01/04/2007 ecs 236 winter 2007 29

Syllabus IDS architecture l Anomaly-based Approach l Event Correlation and Analysis l IDS Evaluation l Advanced Research Topics l 01/04/2007 ecs 236 winter 2007 30

Course Requirements l Teamwork or individual – Discussion with others is highly encouraged! l 50%: 5 Homework Assignments – 10% each (read 1~2 IDS papers and answer a few questions) 10%: l 40%: l 01/04/2007 Proposal Final Project ecs 236 winter 2007 31

l www. cs. ucdavis. edu/~wu/ecs 236/ 01/04/2007 ecs 236 winter 2007 32

Final Projects IDS Architecture l Network versus Host l Anomaly Detection l IDS Evaluation and Evasion l Alert correlation and explanation l 01/04/2007 ecs 236 winter 2007 33

More… Polymorphic/metamorphic worms l Spam/Spit, Phishing, Spyware, … l P 2 P issues (e. g. , Bittorrent) l Botnet. . l 01/04/2007 ecs 236 winter 2007 34

Even more… Fundamental… l “Why will we have DDo. S and Spam in the first place? ? ” l 01/04/2007 ecs 236 winter 2007 35

about Web site http: //www. cs. ucdavis. edu/~wu/ecs 236/ l all lectures, notes, announcements, homework assignments, tools, papers will be there. l 01/04/2007 ecs 236 winter 2007 36

First Paper: BUTTERCUP http: //www. cs. ucdavis. edu/~wu/ecs 236/pap ers/Buttercup_NOMS 2004. pdf l Question: “How would you attack the Buttercup mechanism mentioned in the paper? ” l 01/04/2007 ecs 236 winter 2007 37

Internet Infrastructure l It enables many cool applications. – Email, Web+, IM, Skype, Google, Bittorrent, Infospace, Linked. In, . . . l We are connected, at least in the “IP address” sense!! 01/04/2007 ecs 236 winter 2007 38

Internet Infrastructure l It enables many cool applications. – Email, Web+, IM, Skype, Google, Bittorrent, Infospace, Linked. In, . . . We are connected, at least in the “IP address” sense!! l Many other forms of connections: l – Peer 2 Peer, Friend 2 Friend, community 01/04/2007 ecs 236 winter 2007 39

Internet Infrastructure It enables many cool applications. l It enables many cool attacks. l 01/04/2007 ecs 236 winter 2007 40

Internet Infrastructure It enables many cool applications. l It enables many cool attacks. l – David Clark on Morris Worms to DARPA in 1988 01/04/2007 ecs 236 winter 2007 41

Internet Infrastructure It enables many cool applications. l It enables many cool attacks. l – David Clark on Morris Worms to DARPA in 1988 “Internet is doing exactly what it supposed to do” 01/04/2007 ecs 236 winter 2007 42

It enables many cool applications. l It enables many cool attacks. l – Worm, DDo. S, spamming, phishing, … (the list is still growing) 01/04/2007 ecs 236 winter 2007 43

We can not blame everything to Microsoft! It enables many cool applications. l It enables many cool attacks. l – Worm, DDo. S, spamming, phishing, … (the list is still growing) Related to our Inter-domain routing today… 01/04/2007 ecs 236 winter 2007 44

WORM l Since November 2 nd of 1988… – Robert T. Morris, Code Red, Nimda, Slammer, Blaster, and many others… l inject infect spread 01/04/2007 ecs 236 winter 2007 45

WORM l Since November 2 nd of 1988… – Robert T. Morris, Code Red, Nimda, Slammer, Blaster, and many others… l inject infect spread l WORM is causing Internet-wide instability. 01/04/2007 ecs 236 winter 2007 46

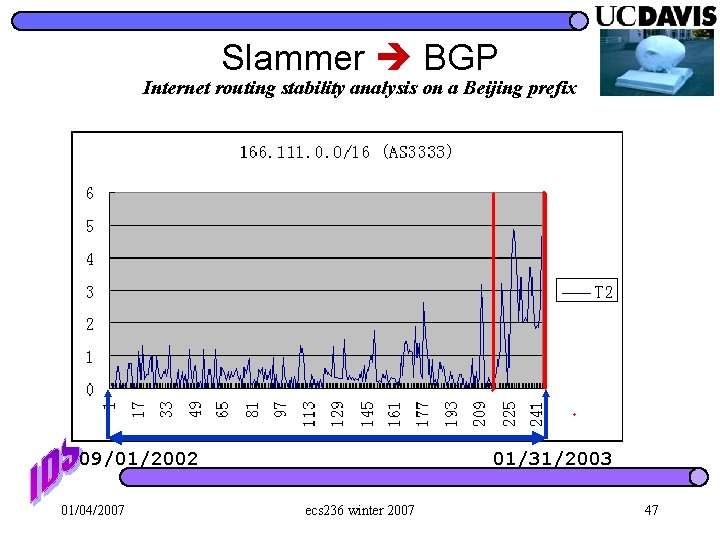
Slammer BGP Internet routing stability analysis on a Beijing prefix 09/01/2002 01/04/2007 01/31/2003 ecs 236 winter 2007 47

Network meets Software An interesting interaction among the Internet, the software on the hosts, and the worms themselves. l The “short-term” Reality: l – Estimated 40~50% of Internet hosts are still vulnerable to Code. Red. 01/04/2007 ecs 236 winter 2007 48

WORM l Since November 2 nd of 1988… – Robert T. Morris, Code Red, Nimda, Slammer, Blaster, and many others… inject infect spread l WORM is causing Internet-wide instability. l WORM is a critical first step for the attacker to quickly build the large-scale attacking infrastructure. l 01/04/2007 ecs 236 winter 2007 49

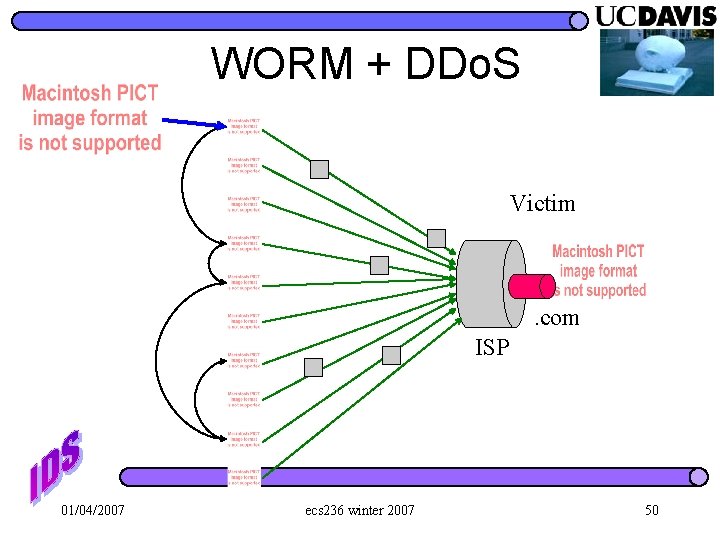
WORM + DDo. S Victim . com ISP 01/04/2007 ecs 236 winter 2007 50

They are getting better… l The rapid evolution of the “attacker’s community” 01/04/2007 ecs 236 winter 2007 51

They are getting better… l The rapid evolution of the “attacker’s community” l And, many thanks to our rapid growing software industry in the past “N” years as well… 01/04/2007 ecs 236 winter 2007 52

Software Vulnerability l Software vulnerabilities are weaknesses, being introduced during the “software engineering” process, that can potentially be exploited by attackers. – OS kernels, device drivers, applications… l There are other types of vulnerabilities in our software systems that can be exploited. 01/04/2007 ecs 236 winter 2007 53

Software Vulnerability l Difficulties in security management – we don’t know how attackers are going to attack us, – And, we don’t know which vulnerabilities can/will be exploited, either. 01/04/2007 ecs 236 winter 2007 54

Software Vulnerability Focus on Software Vulnerabilities l Two approaches l – better software engineering – better vulnerabilities understanding 01/04/2007 ecs 236 winter 2007 55

Software Vulnerability Focus on Software Vulnerabilities l Two approaches l – better software engineering – better vulnerabilities understanding Practically, around the Internet, we currently have and will still have a large number of legacy software systems around for “quite a while. ” 01/04/2007 ecs 236 winter 2007 56

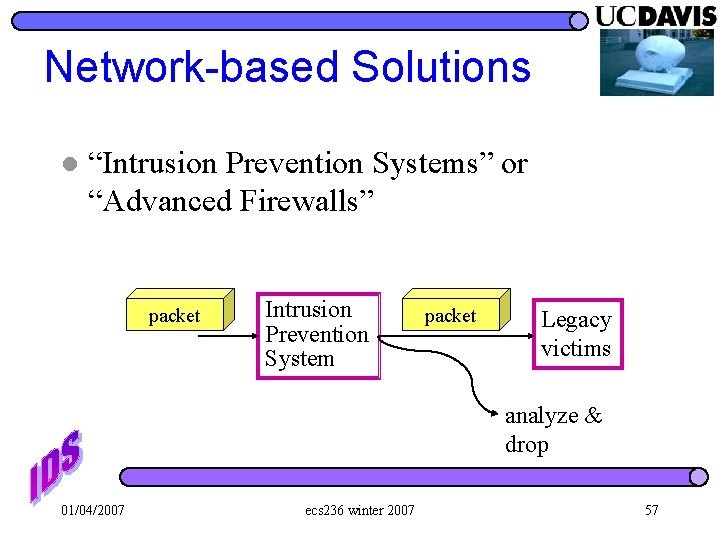
Network-based Solutions l “Intrusion Prevention Systems” or “Advanced Firewalls” packet Intrusion Prevention System packet Legacy victims analyze & drop 01/04/2007 ecs 236 winter 2007 57

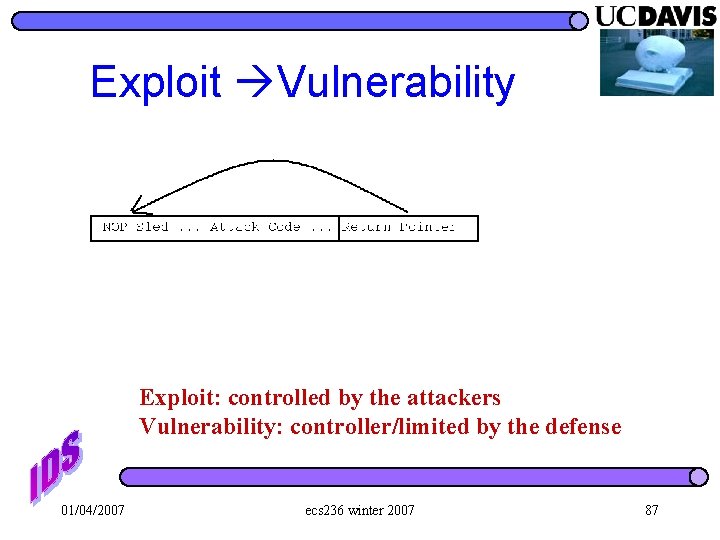
Vulnerability vs. Exploit l Vulnerability – the “weak” points in the software – applications or even the kernel itself – “control flow hijack” based on buffer overflow. l Exploit – the attack code utilizing one or more vulnerabilities 01/04/2007 ecs 236 winter 2007 58

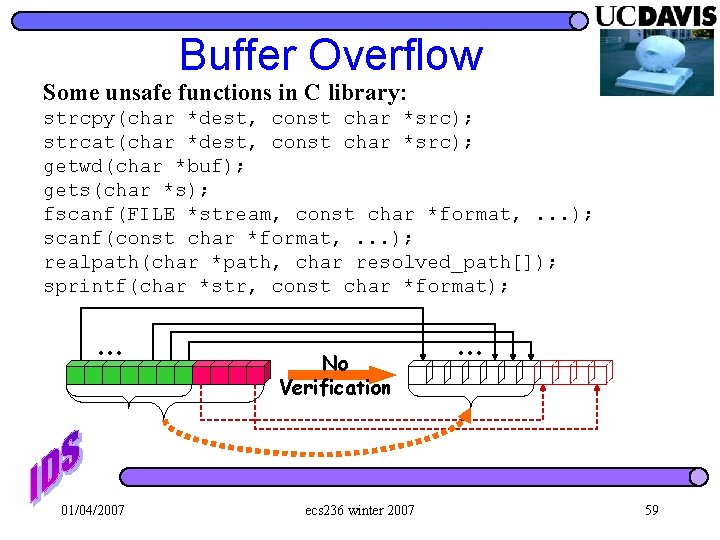
Buffer Overflow Some unsafe functions in C library: strcpy(char *dest, const char *src); strcat(char *dest, const char *src); getwd(char *buf); gets(char *s); fscanf(FILE *stream, const char *format, . . . ); scanf(const char *format, . . . ); realpath(char *path, char resolved_path[]); sprintf(char *str, const char *format); … 01/04/2007 No Verification ecs 236 winter 2007 … 59

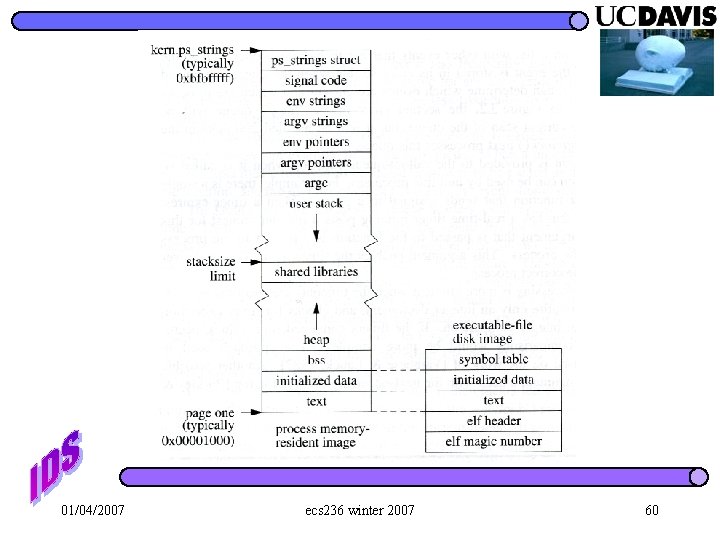
01/04/2007 ecs 236 winter 2007 60

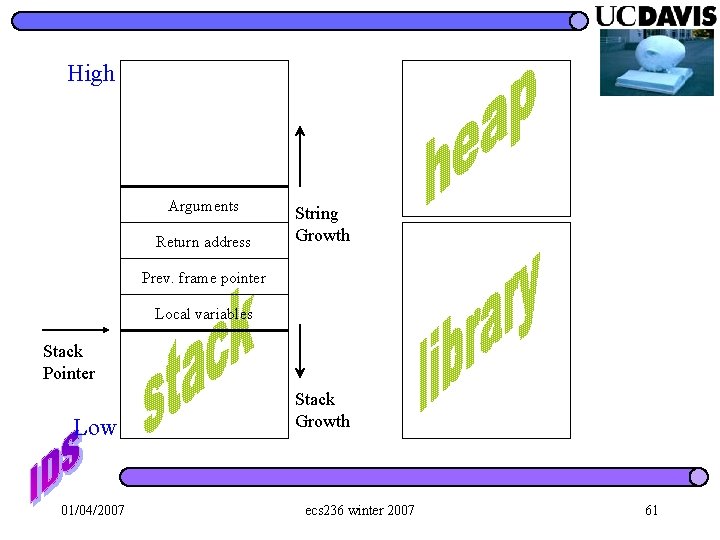
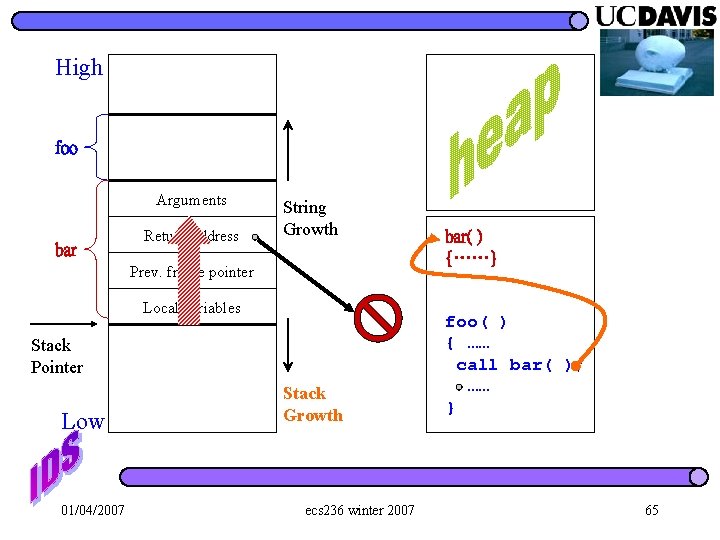
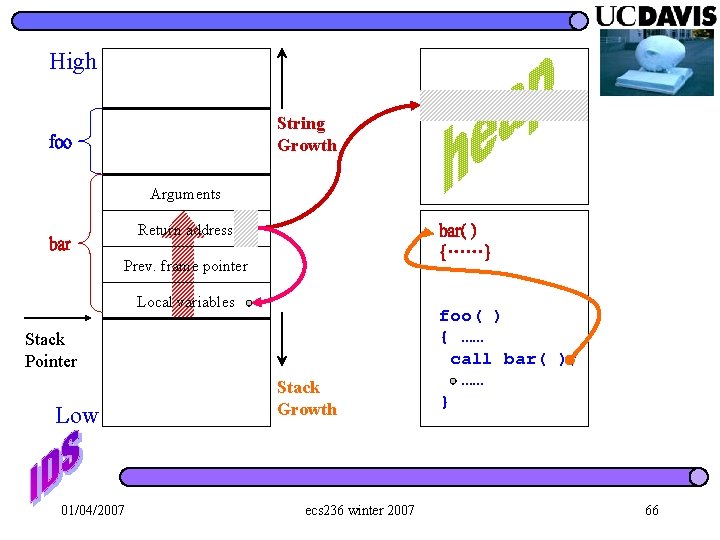
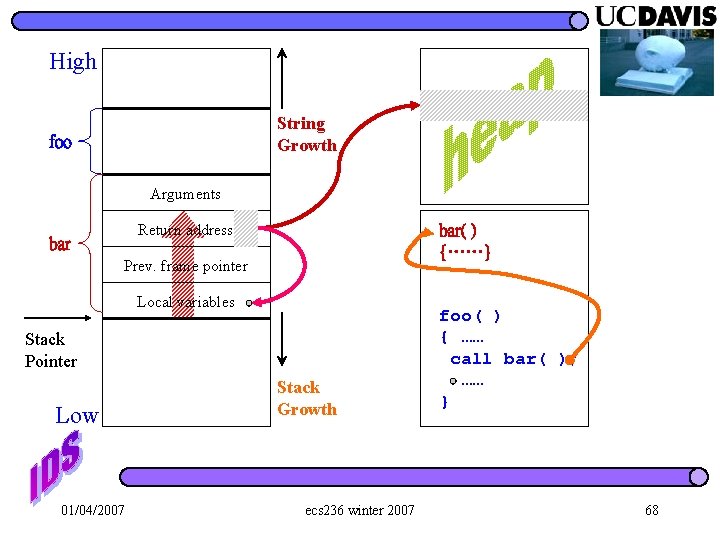
High Arguments Return address String Growth Prev. frame pointer Local variables Stack Pointer Low 01/04/2007 Stack Growth ecs 236 winter 2007 61

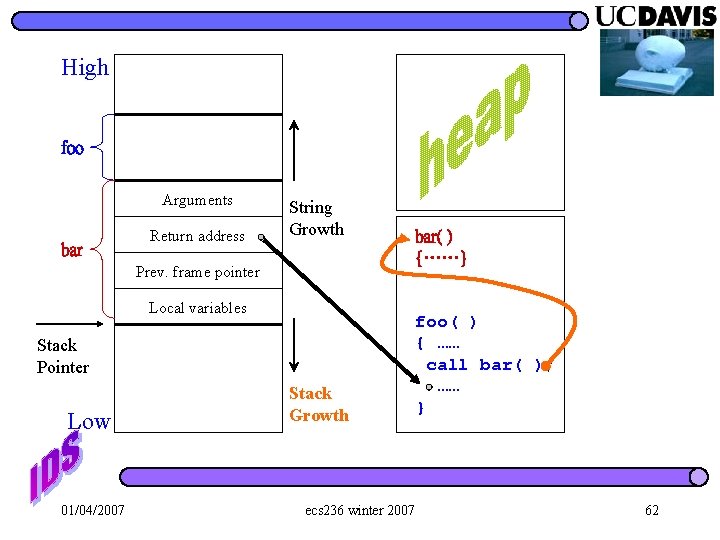
High foo Arguments bar Return address String Growth Prev. frame pointer Local variables Stack Pointer Low 01/04/2007 Stack Growth ecs 236 winter 2007 bar( ) {……} foo( ) { …… call bar( ); …… } 62
![b int barint a int b int i j char buf9 a b int bar(int a, int b) { int i, j; char buf[9]; } a](https://slidetodoc.com/presentation_image_h2/642da41757f87ee4aa310bd25e066051/image-63.jpg)
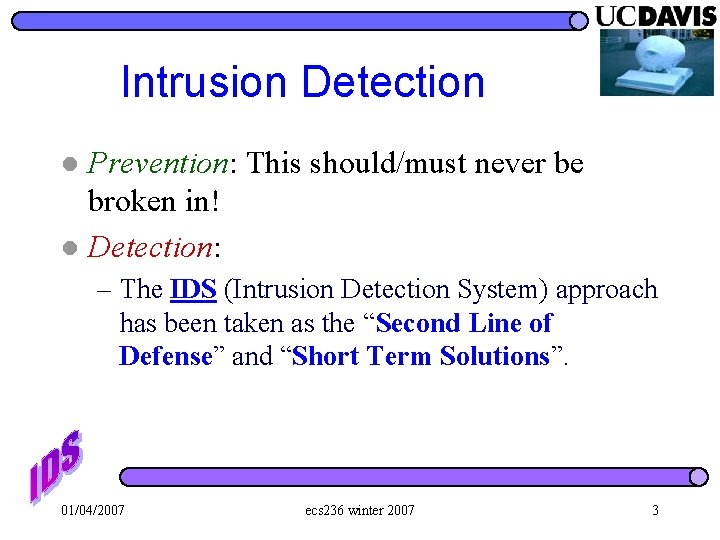
b int bar(int a, int b) { int i, j; char buf[9]; } a ret address SFP i = 5; j = 123; strcpy(buf, “securephdbcde”); Buffer Overflow 01/04/2007 high ecs 236 winter 2007 05 00 00 e 00 00 00 65 d 62 b 63 c 64 d 64 r 65 e 70 p 68 h 72 s 65 e 63 c 75 u 73 low 63

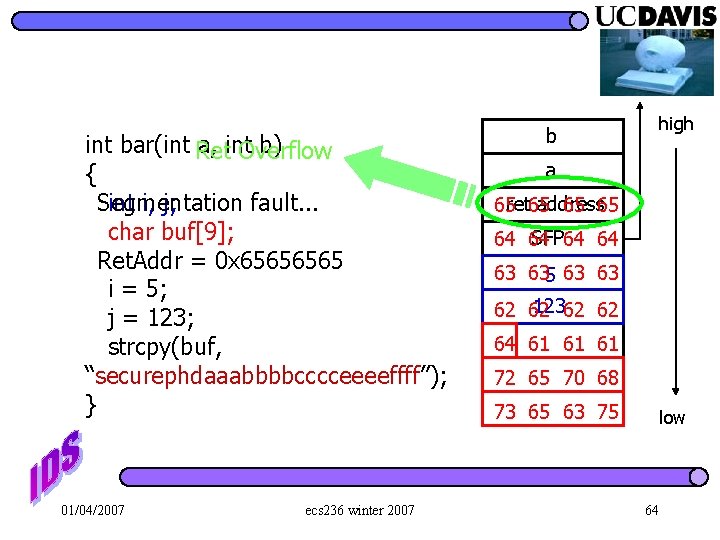
int bar(int Ret a, int b) Overflow { int i, j; Segmentation fault. . . char buf[9]; Ret. Addr = 0 x 6565 i = 5; j = 123; strcpy(buf, “securephdaaabbbbcccceeeeffff”); } 01/04/2007 ecs 236 winter 2007 high b a address 65 ret 65 65 65 SFP 64 64 63 635 63 63 12362 62 64 61 61 61 72 65 70 68 73 65 63 75 low 64

High foo Arguments bar Return address String Growth Prev. frame pointer Local variables Stack Pointer Low 01/04/2007 Stack Growth ecs 236 winter 2007 bar( ) {……} foo( ) { …… call bar( ); …… } 65

High String Growth foo Arguments Return address bar( ) {……} Prev. frame pointer Local variables Stack Pointer Low 01/04/2007 Stack Growth ecs 236 winter 2007 foo( ) { …… call bar( ); …… } 66

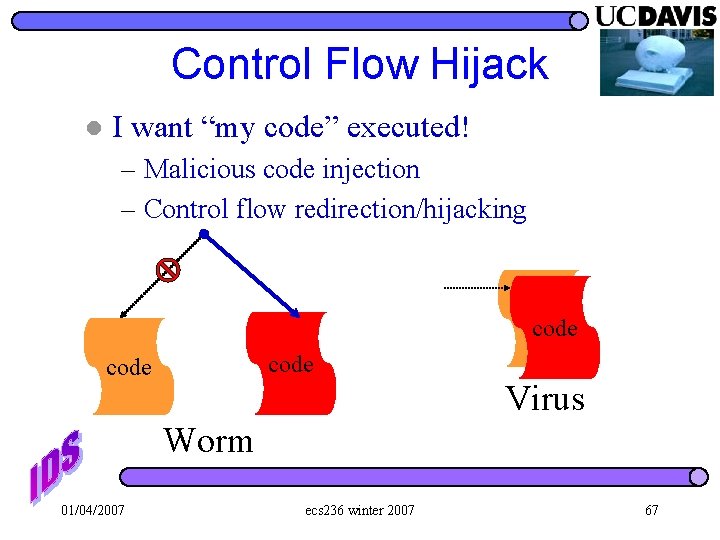
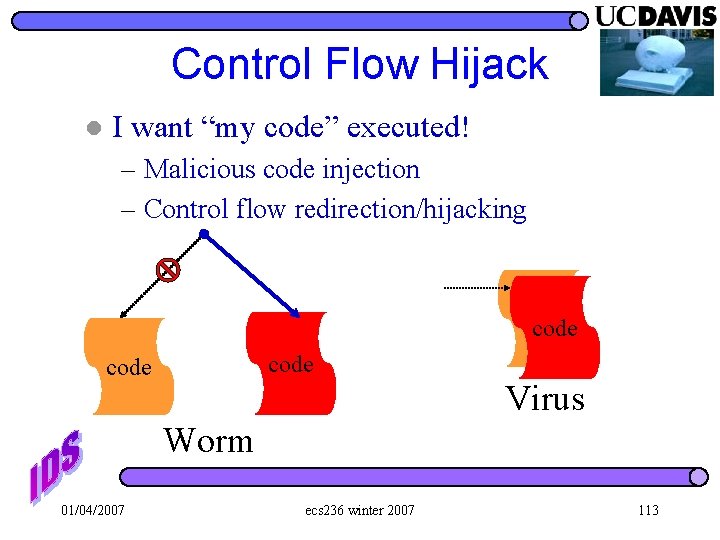
Control Flow Hijack l I want “my code” executed! – Malicious code injection – Control flow redirection/hijacking code Virus Worm 01/04/2007 ecs 236 winter 2007 67

High String Growth foo Arguments Return address bar( ) {……} Prev. frame pointer Local variables Stack Pointer Low 01/04/2007 Stack Growth ecs 236 winter 2007 foo( ) { …… call bar( ); …… } 68

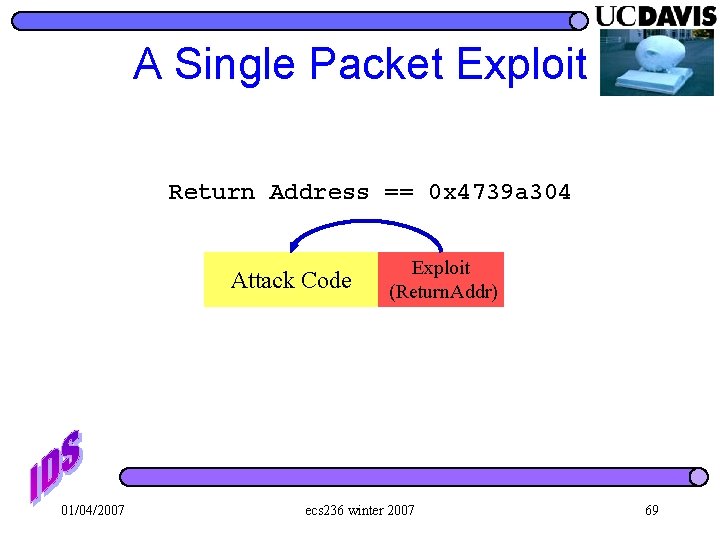
A Single Packet Exploit Return Address == 0 x 4739 a 304 Attack Code 01/04/2007 Exploit (Return. Addr) ecs 236 winter 2007 69

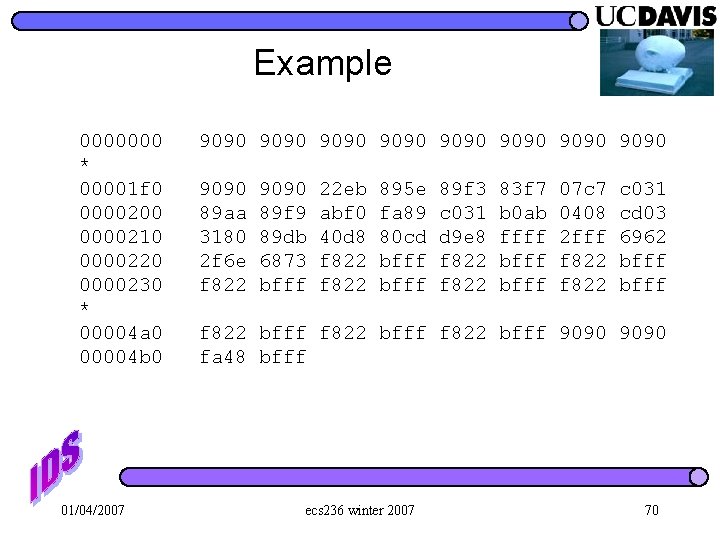
Example 0000000 * 00001 f 0 0000200 0000210 0000220 0000230 * 00004 a 0 00004 b 0 01/04/2007 9090 9090 9090 89 aa 3180 2 f 6 e f 822 9090 89 f 9 89 db 6873 bfff 22 eb abf 0 40 d 8 f 822 895 e fa 89 80 cd bfff 89 f 3 c 031 d 9 e 8 f 822 83 f 7 b 0 ab ffff bfff 07 c 7 0408 2 fff f 822 c 031 cd 03 6962 bfff f 822 bfff 9090 fa 48 bfff ecs 236 winter 2007 70

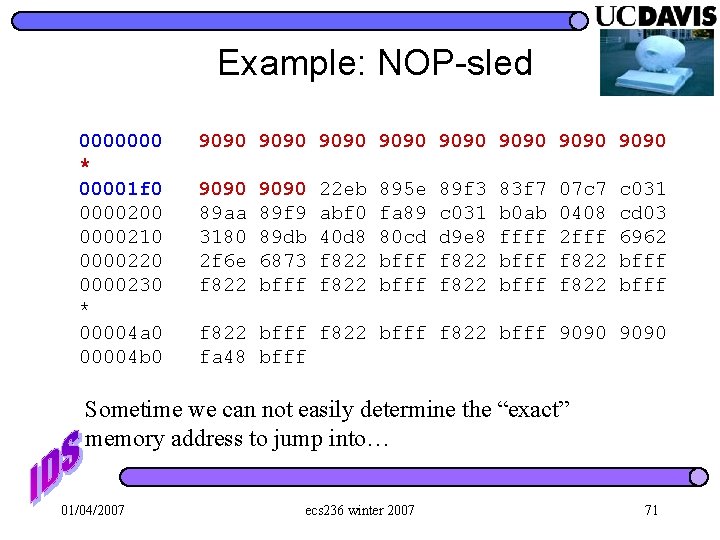
Example: NOP-sled 0000000 * 00001 f 0 0000200 0000210 0000220 0000230 * 00004 a 0 00004 b 0 9090 9090 9090 89 aa 3180 2 f 6 e f 822 9090 89 f 9 89 db 6873 bfff 22 eb abf 0 40 d 8 f 822 895 e fa 89 80 cd bfff 89 f 3 c 031 d 9 e 8 f 822 83 f 7 b 0 ab ffff bfff 07 c 7 0408 2 fff f 822 c 031 cd 03 6962 bfff f 822 bfff 9090 fa 48 bfff Sometime we can not easily determine the “exact” memory address to jump into… 01/04/2007 ecs 236 winter 2007 71
![NOP Sled Engineering Attack Code Exploit Return Addr code xebx 2 ax 5 “NOP Sled” Engineering Attack Code Exploit (Return. Addr) code[] = “xebx 2 ax 5](https://slidetodoc.com/presentation_image_h2/642da41757f87ee4aa310bd25e066051/image-72.jpg)
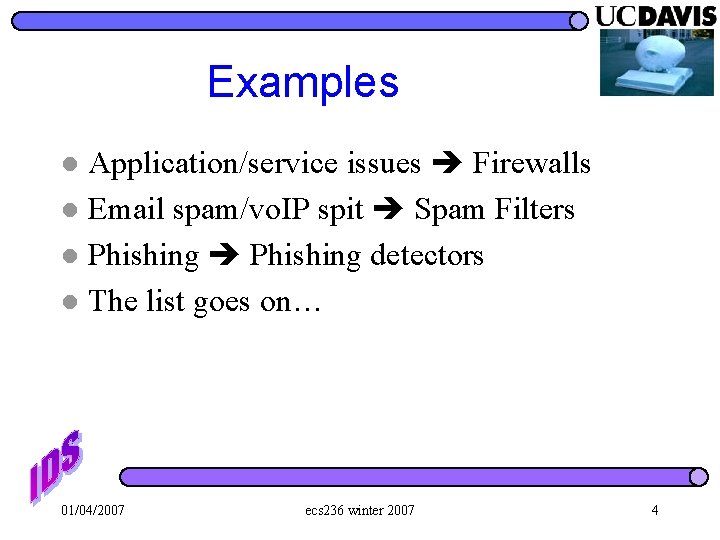
“NOP Sled” Engineering Attack Code Exploit (Return. Addr) code[] = “xebx 2 ax 5 fxc 6x 47x 00x 89x 7 fx 08xc 7x 47”; strcpy(buf, code); buf = “xebx 2 ax 5 fxc 6x 47x 07” NOP NOP Attack Code Exploit (Return. Addr) And, sometimes, we simply want to find a way to avoid “x 00”. 01/04/2007 ecs 236 winter 2007 72

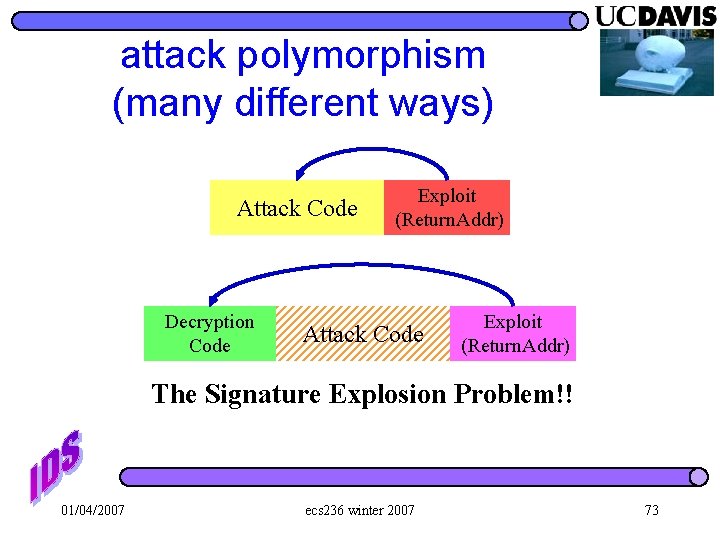
attack polymorphism (many different ways) Attack Code Decryption Code Exploit (Return. Addr) Attack Code Exploit (Return. Addr) The Signature Explosion Problem!! 01/04/2007 ecs 236 winter 2007 73

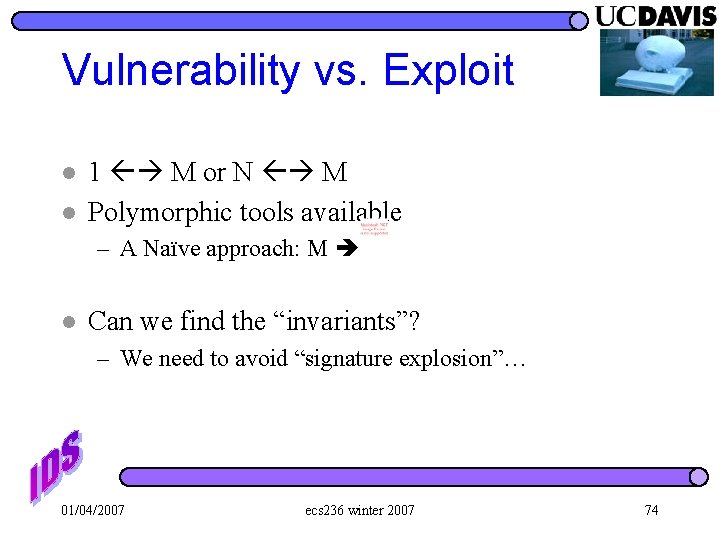
Vulnerability vs. Exploit l l 1 M or N M Polymorphic tools available – A Naïve approach: M l Can we find the “invariants”? – We need to avoid “signature explosion”… 01/04/2007 ecs 236 winter 2007 74

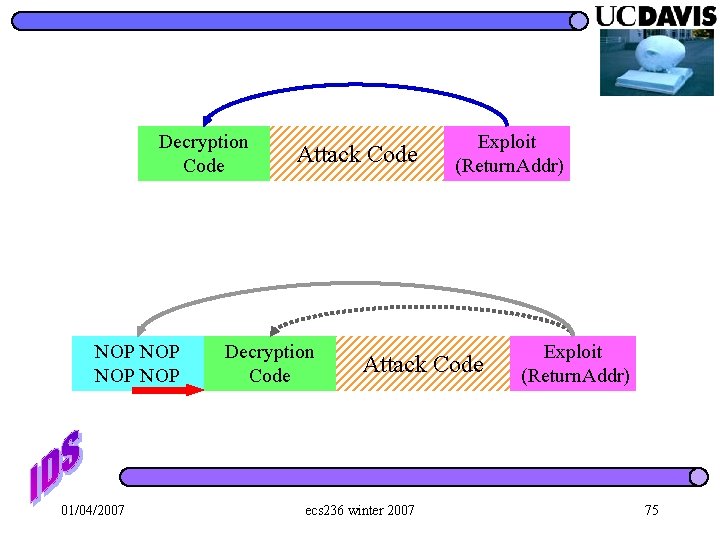
Decryption Code NOP NOP 01/04/2007 Attack Code Decryption Code Exploit (Return. Addr) Attack Code ecs 236 winter 2007 Exploit (Return. Addr) 75

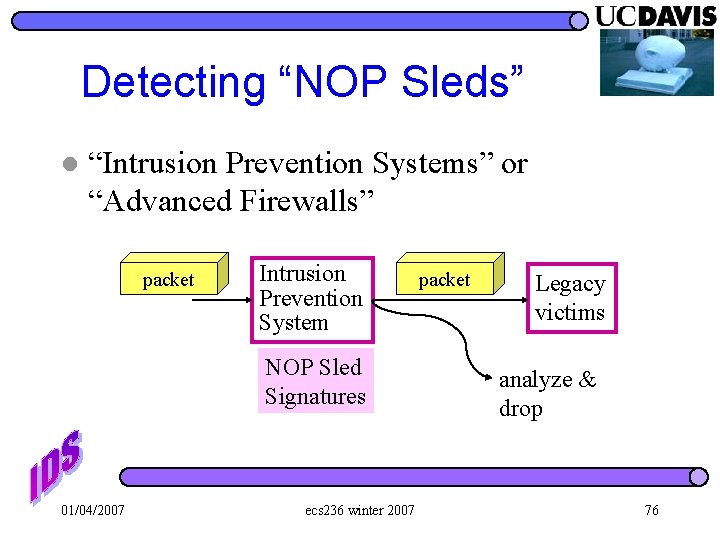
Detecting “NOP Sleds” l “Intrusion Prevention Systems” or “Advanced Firewalls” packet Intrusion Prevention System NOP Sled Signatures 01/04/2007 ecs 236 winter 2007 packet Legacy victims analyze & drop 76

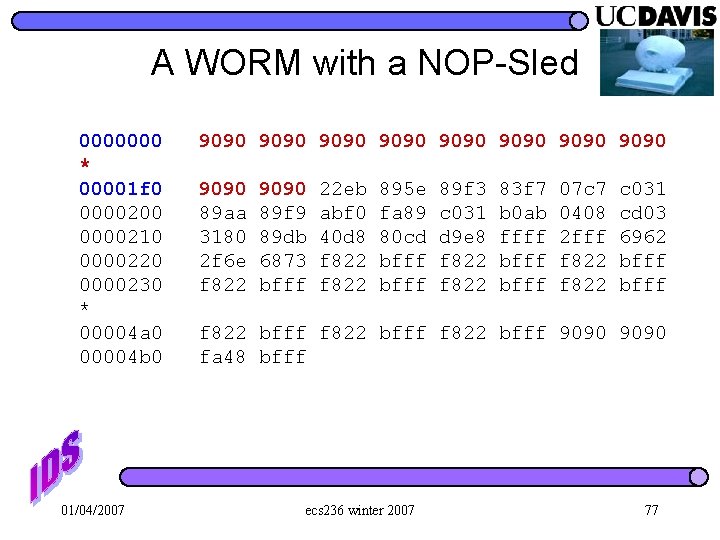
A WORM with a NOP-Sled 0000000 * 00001 f 0 0000200 0000210 0000220 0000230 * 00004 a 0 00004 b 0 01/04/2007 9090 9090 9090 89 aa 3180 2 f 6 e f 822 9090 89 f 9 89 db 6873 bfff 22 eb abf 0 40 d 8 f 822 895 e fa 89 80 cd bfff 89 f 3 c 031 d 9 e 8 f 822 83 f 7 b 0 ab ffff bfff 07 c 7 0408 2 fff f 822 c 031 cd 03 6962 bfff f 822 bfff 9090 fa 48 bfff ecs 236 winter 2007 77

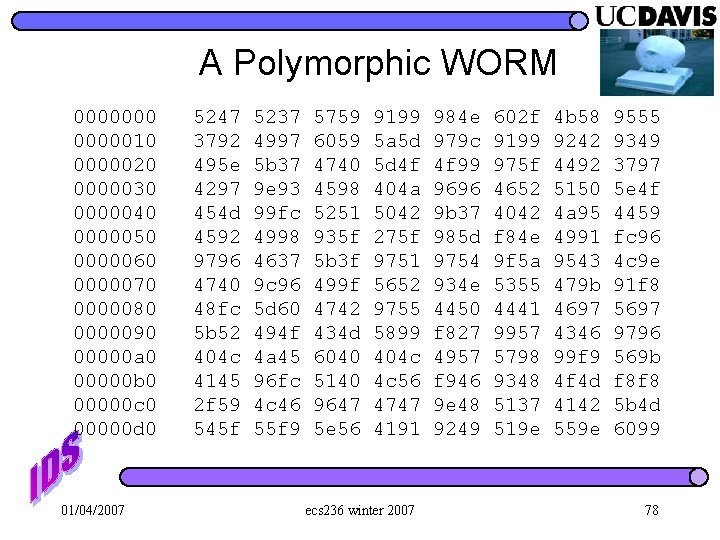
A Polymorphic WORM 000000010 0000020 0000030 0000040 0000050 0000060 0000070 0000080 0000090 00000 a 0 00000 b 0 00000 c 0 00000 d 0 01/04/2007 5247 3792 495 e 4297 454 d 4592 9796 4740 48 fc 5 b 52 404 c 4145 2 f 59 545 f 5237 4997 5 b 37 9 e 93 99 fc 4998 4637 9 c 96 5 d 60 494 f 4 a 45 96 fc 4 c 46 55 f 9 5759 6059 4740 4598 5251 935 f 5 b 3 f 499 f 4742 434 d 6040 5140 9647 5 e 56 9199 5 a 5 d 5 d 4 f 404 a 5042 275 f 9751 5652 9755 5899 404 c 4 c 56 4747 4191 ecs 236 winter 2007 984 e 979 c 4 f 99 9696 9 b 37 985 d 9754 934 e 4450 f 827 4957 f 946 9 e 48 9249 602 f 9199 975 f 4652 4042 f 84 e 9 f 5 a 5355 4441 9957 5798 9348 5137 519 e 4 b 58 9242 4492 5150 4 a 95 4991 9543 479 b 4697 4346 99 f 9 4 f 4 d 4142 559 e 9555 9349 3797 5 e 4 f 4459 fc 96 4 c 9 e 91 f 8 5697 9796 569 b f 8 f 8 5 b 4 d 6099 78

NOP sleds l “NOP sled” can/will NOT be a useful signature in detecting future WORMs… l 80~90% of the WORMs today don’t really need “NOP sleds” but, historically, they are still “left” there. 01/04/2007 ecs 236 winter 2007 79

BUTTERCUP l Ideas: – Given a software exploit, the hacker can encrypt the malicious code but not the “hijacking” entry point (e. g. , return address). – The hacker can twist the “return address” but practically not infinitely a range of memory addresses. 01/04/2007 ecs 236 winter 2007 80

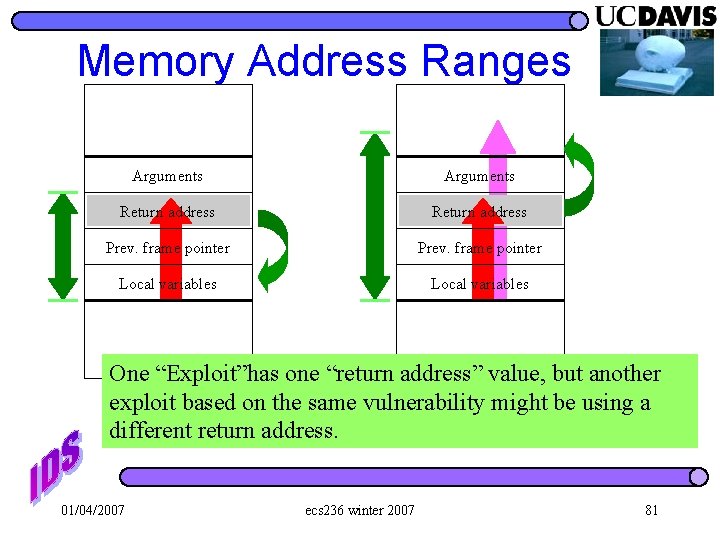
Memory Address Ranges Arguments Return address Prev. frame pointer Local variables One “Exploit”has one “return address” value, but another exploit based on the same vulnerability might be using a different return address. 01/04/2007 ecs 236 winter 2007 81

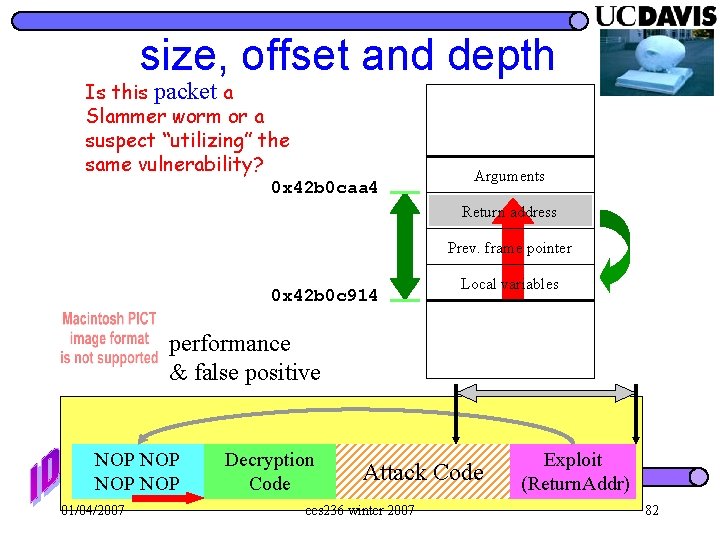
size, offset and depth Is this packet a Slammer worm or a suspect “utilizing” the same vulnerability? 0 x 42 b 0 caa 4 Arguments Return address Prev. frame pointer 0 x 42 b 0 c 914 Local variables performance & false positive NOP NOP 01/04/2007 Decryption Code Attack Code ecs 236 winter 2007 Exploit (Return. Addr) 82

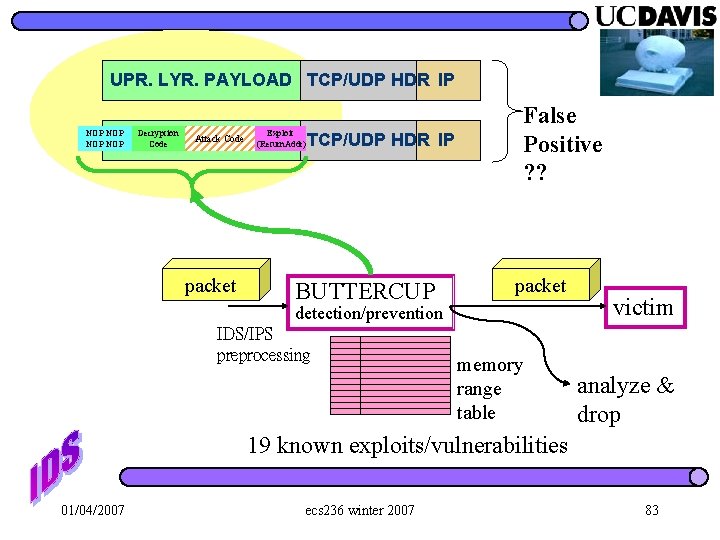
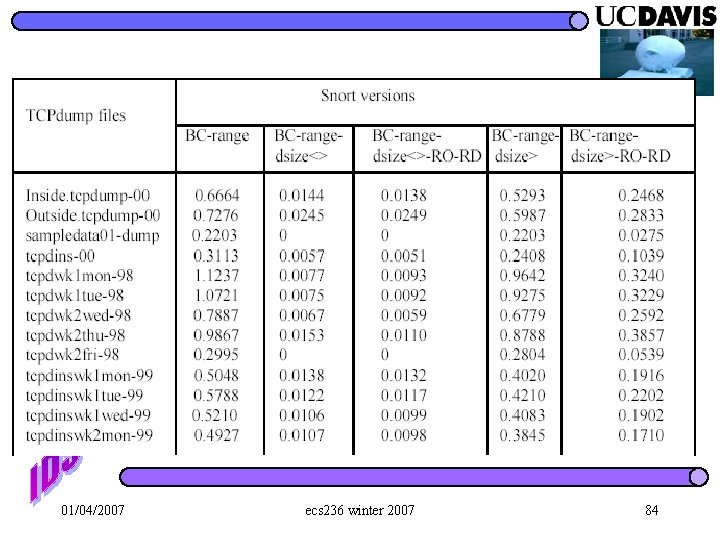
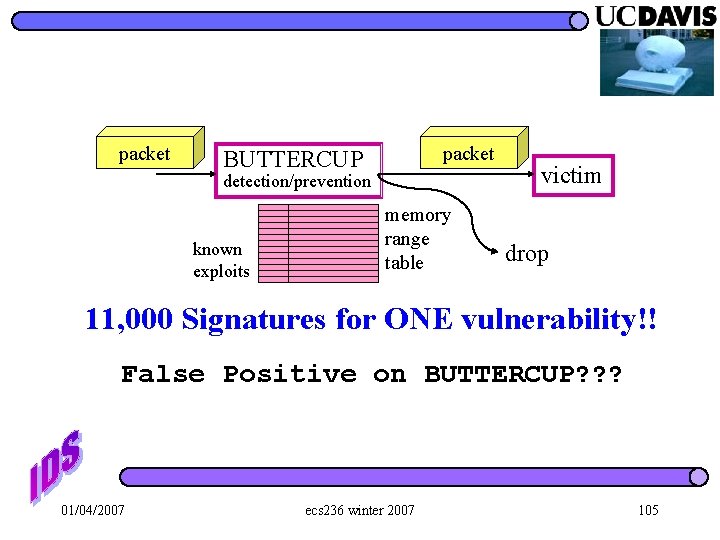
UPR. LYR. PAYLOAD TCP/UDP HDR IP NOP NOP Decryption Code Exploit (Return. Addr) Code UPR. LYR. Attack PAYLOAD TCP/UDP HDR IP packet BUTTERCUP False Positive ? ? packet detection/prevention IDS/IPS preprocessing memory range table victim analyze & drop 19 known exploits/vulnerabilities 01/04/2007 ecs 236 winter 2007 83

01/04/2007 ecs 236 winter 2007 84

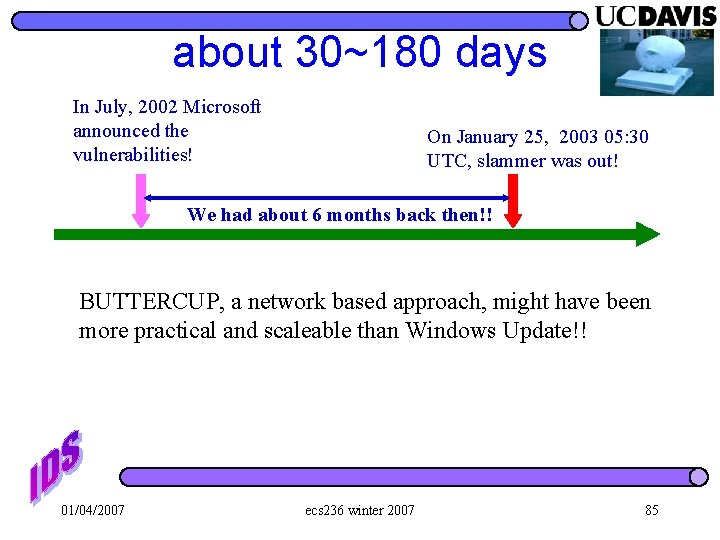
about 30~180 days In July, 2002 Microsoft announced the vulnerabilities! On January 25, 2003 05: 30 UTC, slammer was out! We had about 6 months back then!! BUTTERCUP, a network based approach, might have been more practical and scaleable than Windows Update!! 01/04/2007 ecs 236 winter 2007 85

Limitation l BUTTERCUP will only work for “known vulnerabilities”! – But, it may work for Zero-day exploits based on known vulnerabilities. 01/04/2007 ecs 236 winter 2007 86

Exploit Vulnerability Exploit: controlled by the attackers Vulnerability: controller/limited by the defense 01/04/2007 ecs 236 winter 2007 87

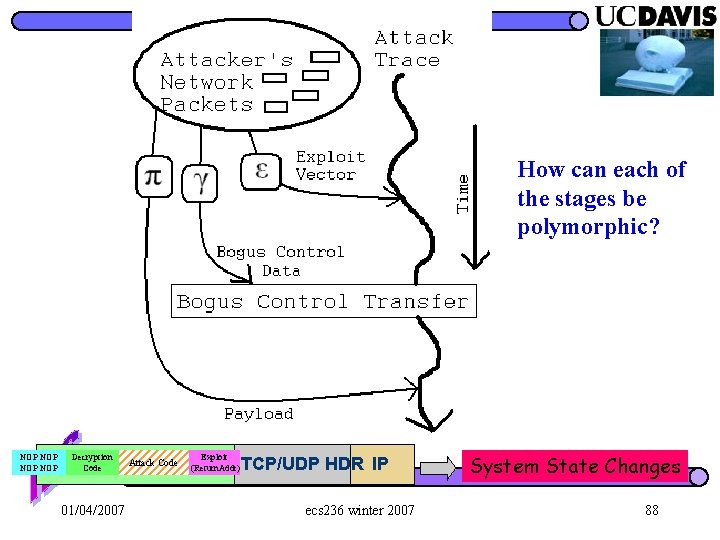
How can each of the stages be polymorphic? NOP NOP Decryption Exploit Code UPR. Code LYR. Attack PAYLOAD (Return. Addr) TCP/UDP HDR IP 01/04/2007 ecs 236 winter 2007 System State Changes 88

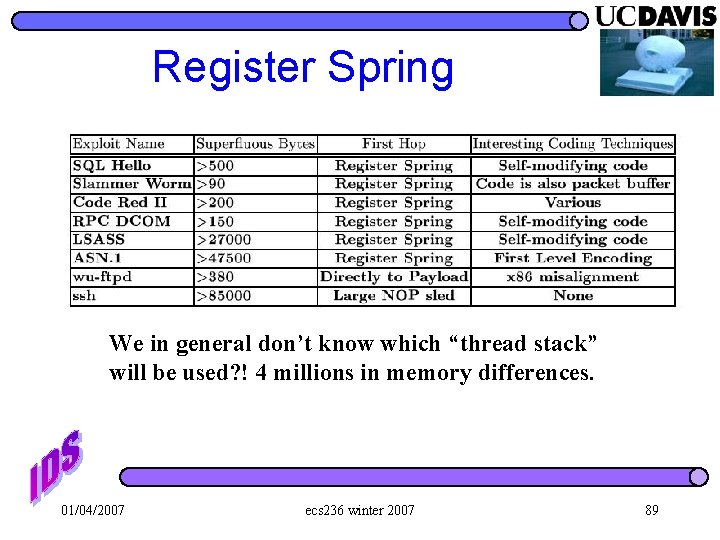
Register Spring We in general don’t know which “thread stack” will be used? ! 4 millions in memory differences. 01/04/2007 ecs 236 winter 2007 89

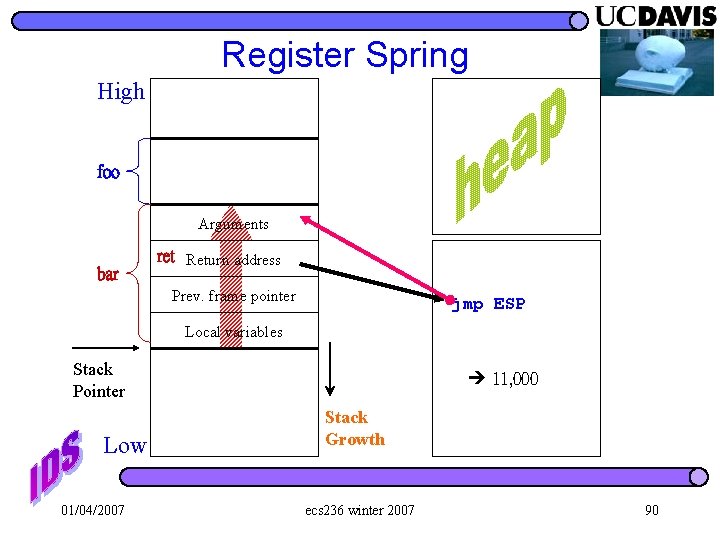
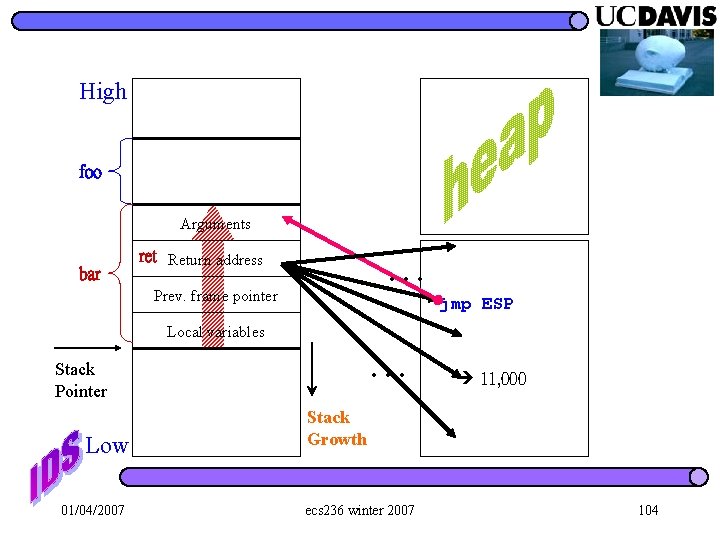
Register Spring High foo Arguments bar ret Return address Prev. frame pointer jmp ESP Local variables Stack Pointer Low 01/04/2007 11, 000 Stack Growth ecs 236 winter 2007 90

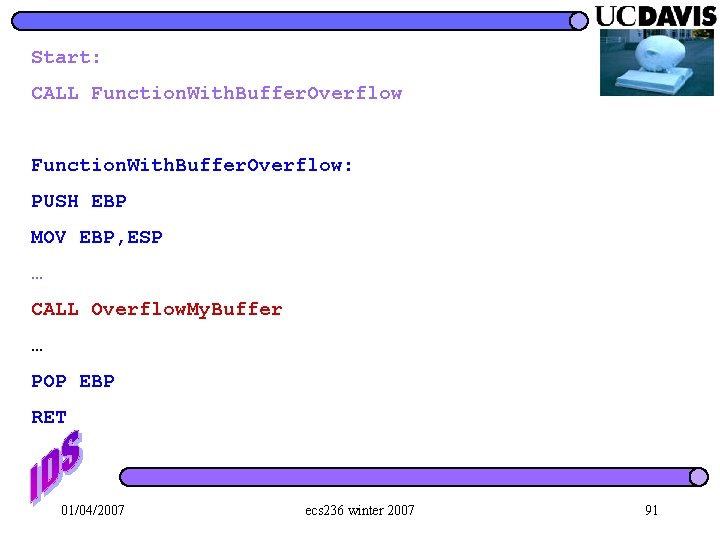
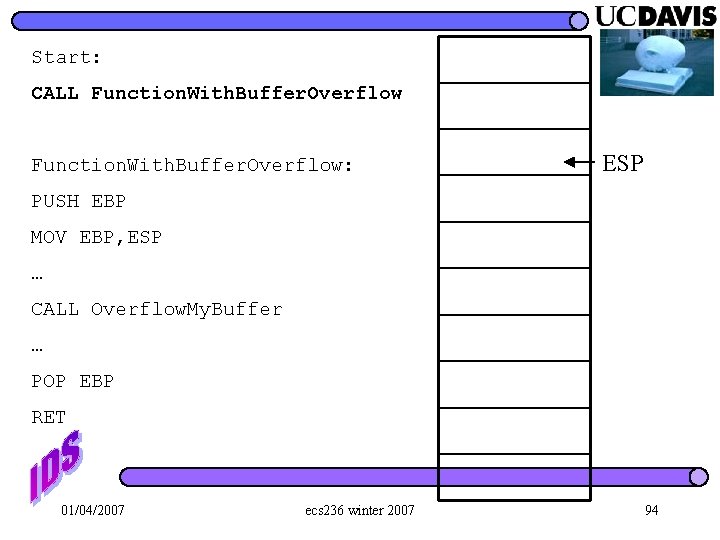
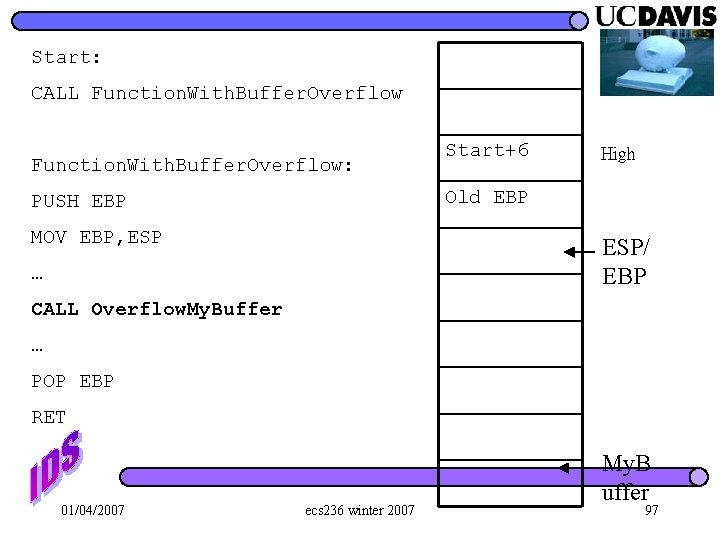
Start: CALL Function. With. Buffer. Overflow: PUSH EBP MOV EBP, ESP … CALL Overflow. My. Buffer … POP EBP RET 01/04/2007 ecs 236 winter 2007 91

Slammer 01/04/2007 ecs 236 winter 2007 92

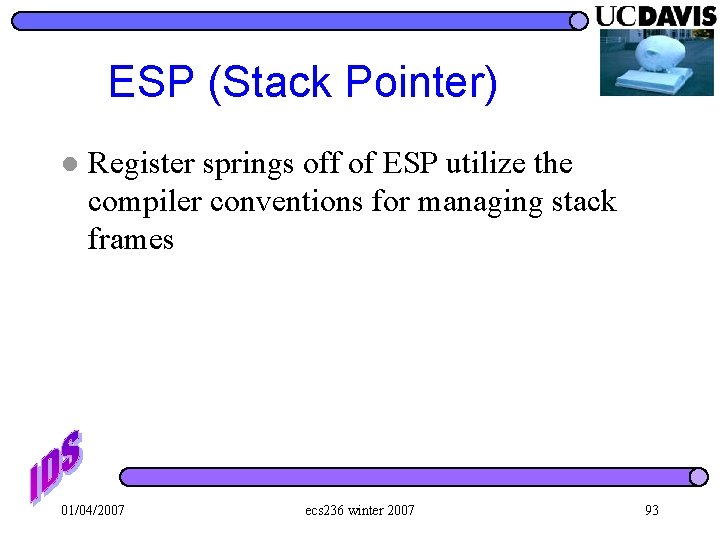
ESP (Stack Pointer) l Register springs off of ESP utilize the compiler conventions for managing stack frames 01/04/2007 ecs 236 winter 2007 93

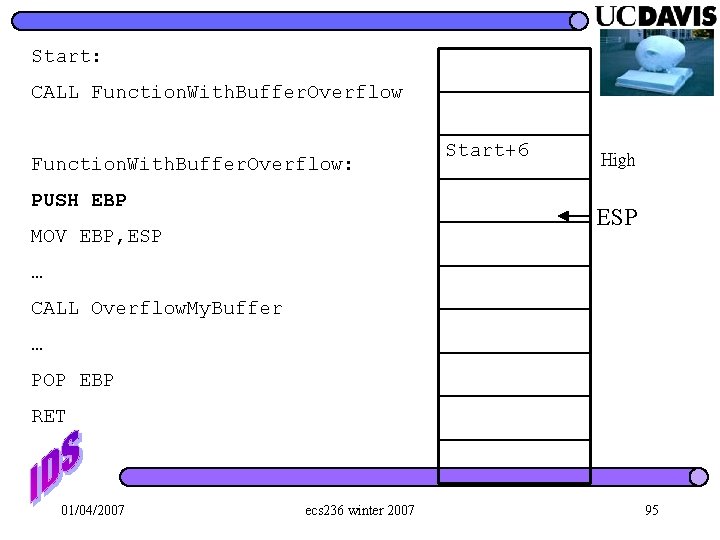
Start: CALL Function. With. Buffer. Overflow: ESP PUSH EBP MOV EBP, ESP … CALL Overflow. My. Buffer … POP EBP RET 01/04/2007 ecs 236 winter 2007 94

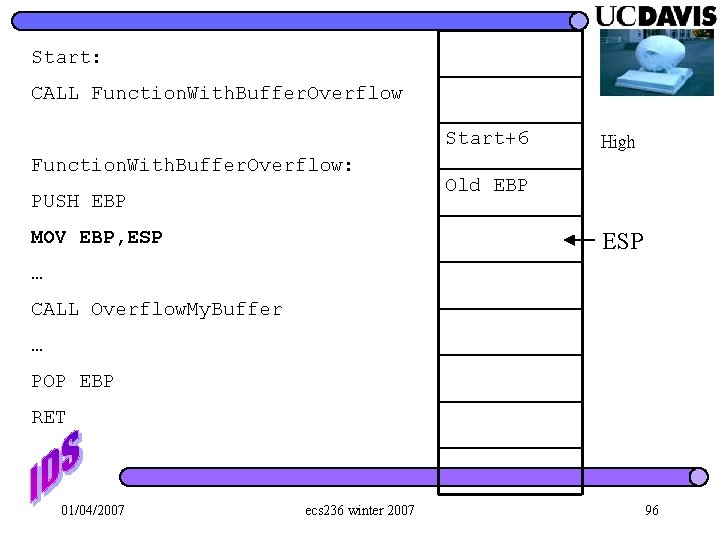
Start: CALL Function. With. Buffer. Overflow: PUSH EBP Start+6 High ESP MOV EBP, ESP … CALL Overflow. My. Buffer … POP EBP RET 01/04/2007 ecs 236 winter 2007 95

Start: CALL Function. With. Buffer. Overflow Start+6 Function. With. Buffer. Overflow: PUSH EBP MOV EBP, ESP High Old EBP ESP … CALL Overflow. My. Buffer … POP EBP RET 01/04/2007 ecs 236 winter 2007 96

Start: CALL Function. With. Buffer. Overflow: Start+6 High Old EBP PUSH EBP MOV EBP, ESP/ EBP … CALL Overflow. My. Buffer … POP EBP RET 01/04/2007 ecs 236 winter 2007 My. B uffer 97

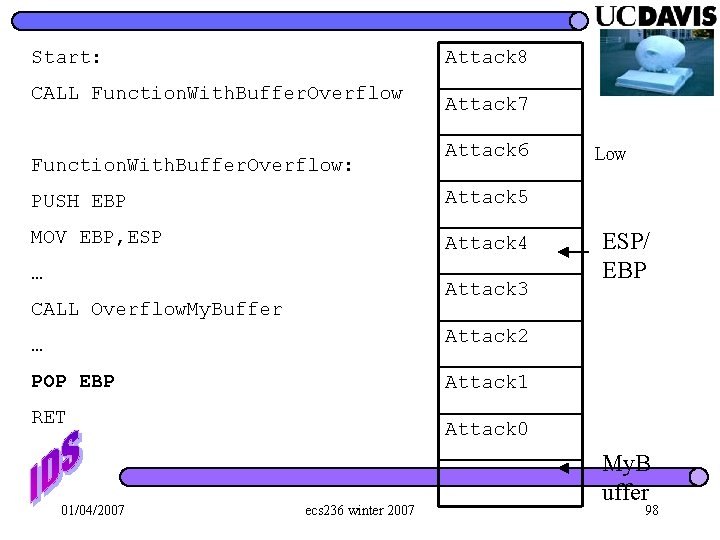
Attack 8 Start: CALL Function. With. Buffer. Overflow: Attack 7 Attack 6 PUSH EBP Attack 5 MOV EBP, ESP Attack 4 … Attack 3 CALL Overflow. My. Buffer … Attack 2 POP EBP Attack 1 RET 01/04/2007 Low ESP/ EBP Attack 0 ecs 236 winter 2007 My. B uffer 98

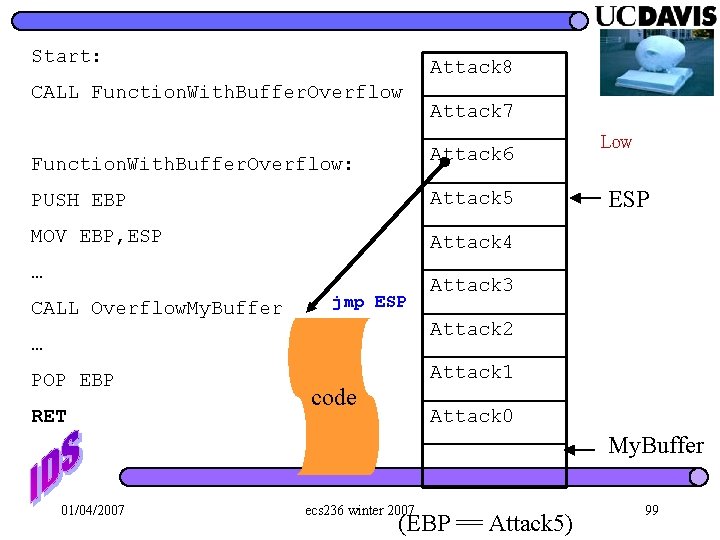
Start: Attack 8 CALL Function. With. Buffer. Overflow Attack 7 Function. With. Buffer. Overflow: Attack 6 PUSH EBP Attack 5 MOV EBP, ESP Attack 4 … CALL Overflow. My. Buffer jmp ESP RET ESP Attack 3 Attack 2 … POP EBP Low Attack 1 code Attack 0 My. Buffer 01/04/2007 ecs 236 winter 2007 (EBP == Attack 5) 99

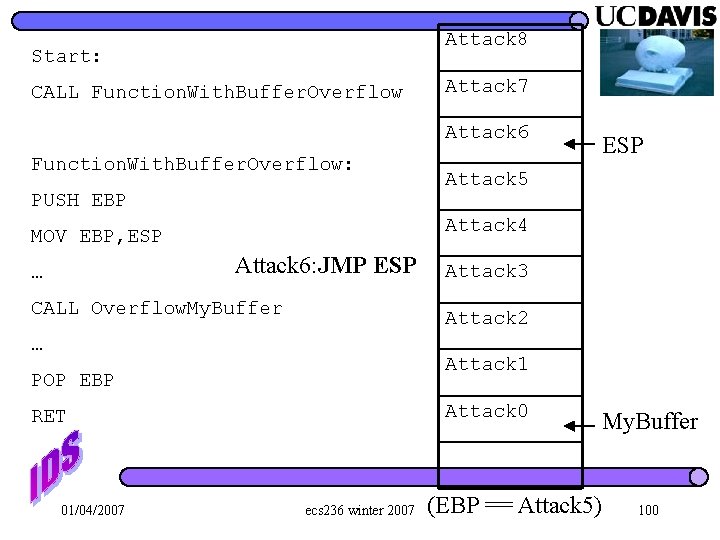
Attack 8 Start: CALL Function. With. Buffer. Overflow Attack 7 Attack 6 Function. With. Buffer. Overflow: PUSH EBP Attack 6: JMP ESP CALL Overflow. My. Buffer Attack 3 Attack 2 … Attack 1 POP EBP Attack 0 RET 01/04/2007 Attack 5 Attack 4 MOV EBP, ESP … ESP ecs 236 winter 2007 My. Buffer (EBP == Attack 5) 100

Notes This is how Slammer worked, Sasser is very similar, as are a couple of others l Bogus return pointer is Attack 6, payload starts at Attack 7 l 01/04/2007 ecs 236 winter 2007 101

Other registers Register springs off of other registers utilize the compiler conventions for managing buffers (i. e. EBX is the “base” register for indexing the base of a buffer, ESI is the “source” register for string operations, EDI is the “destination”, …) l Blaster RPC DCOM used EBX, ASN. 1 uses EDI, Code Red II used EBX l 01/04/2007 ecs 236 winter 2007 102

DCOM Exploits in svchost (Blaster) 0 xff 0 xd 3 is CALL EBX which is the one Blaster used, but JMP EBX (0 xff 0 xe 3) works just as well. l a little over 11, 000 in svchost l 0 x 0100139 d is the only one that Blaster used and is the one the publicly available DCOM exploit uses. l 01/04/2007 ecs 236 winter 2007 103

High foo Arguments bar … ret Return address Prev. frame pointer jmp ESP Local variables … Stack Pointer Low 01/04/2007 11, 000 Stack Growth ecs 236 winter 2007 104

packet BUTTERCUP detection/prevention known exploits memory range table victim drop 11, 000 Signatures for ONE vulnerability!! False Positive on BUTTERCUP? ? ? 01/04/2007 ecs 236 winter 2007 105

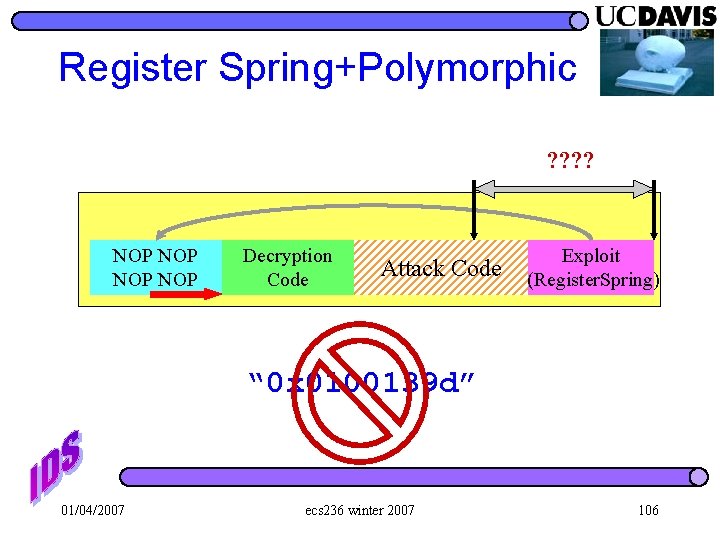
Register Spring+Polymorphic ? ? NOP NOP Decryption Code Attack Code Exploit (Register. Spring) “ 0 x 0100139 d” 01/04/2007 ecs 236 winter 2007 106

EBX-based Buttercup (a possible project idea) l Among all the memory address for call ebx (0 xff 0 xd 3 -- 11000+ of them), only four of them are around 0 x 01001***, about another 600+ are from 0 x 719555 a 4 to 0 x 71 c 637 b 3. But, the rest of them (the majority 10000+) are all from 0 x 7585149 f to 0 x 77 fbc 10 b. 0 x 0100139 d 0 x 010013 a 2 0 x 01001 c 83 0 x 01001 cc 7 0 x 719555 a 4 0 x 71 c 637 b 3 0 x 7585149 f 0 x 77 fbc 10 b 01/04/2007 ecs 236 winter 2007 107

But… l Still a lot and maybe false positive… – We don’t know – What else can we do in the network… 01/04/2007 ecs 236 winter 2007 108

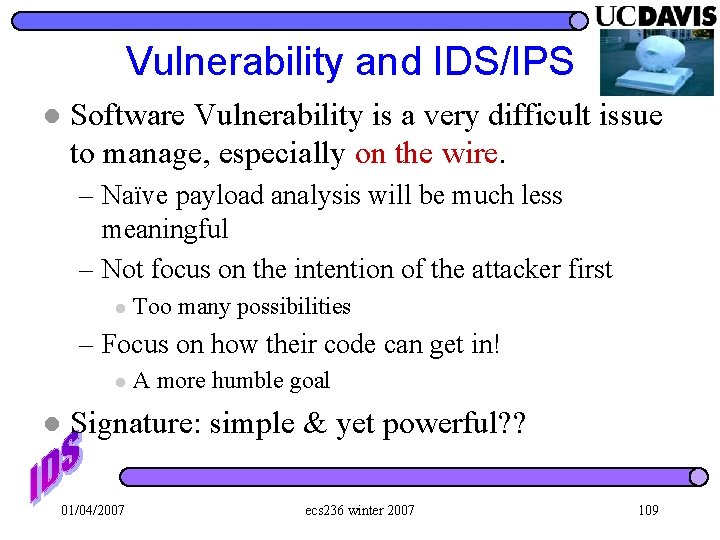
Vulnerability and IDS/IPS l Software Vulnerability is a very difficult issue to manage, especially on the wire. – Naïve payload analysis will be much less meaningful – Not focus on the intention of the attacker first l Too many possibilities – Focus on how their code can get in! l l A more humble goal Signature: simple & yet powerful? ? 01/04/2007 ecs 236 winter 2007 109

What is a “vulnerability”? l 1 Vulnerability -- N Exploits 01/04/2007 ecs 236 winter 2007 110

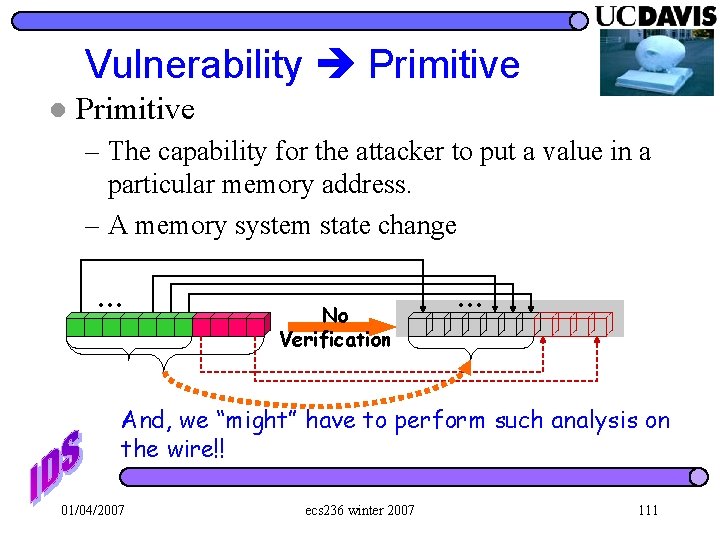
Vulnerability Primitive l Primitive – The capability for the attacker to put a value in a particular memory address. – A memory system state change … No Verification … And, we “might” have to perform such analysis on the wire!! 01/04/2007 ecs 236 winter 2007 111

Focus on “Primitives” being used in the “Epsilon” phase! Application dependent analysis NOP NOP Decryption Exploit Code UPR. Code LYR. Attack PAYLOAD (Return. Addr) TCP/UDP HDR IP 01/04/2007 ecs 236 winter 2007 System State Changes 112

Control Flow Hijack l I want “my code” executed! – Malicious code injection – Control flow redirection/hijacking code Virus Worm 01/04/2007 ecs 236 winter 2007 113

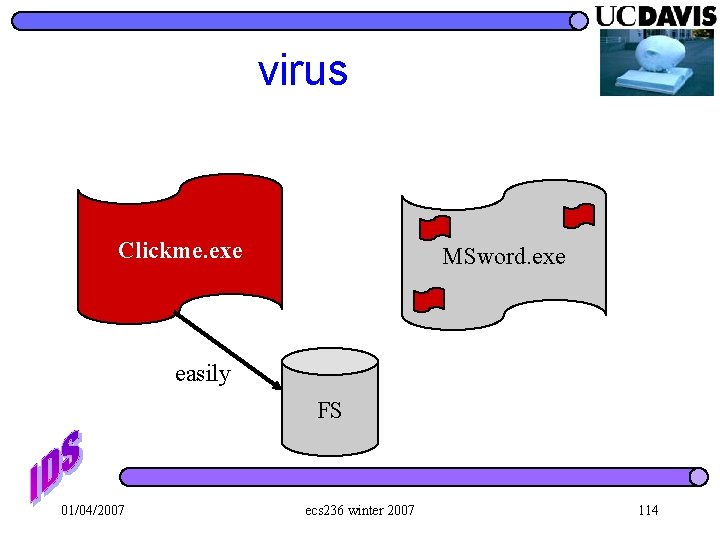
virus Clickme. exe MSword. exe easily FS 01/04/2007 ecs 236 winter 2007 114

Host-based Approach l Minos can resolve all the problems related to control-flow hijacks with zero-false positive. 01/04/2007 ecs 236 winter 2007 115

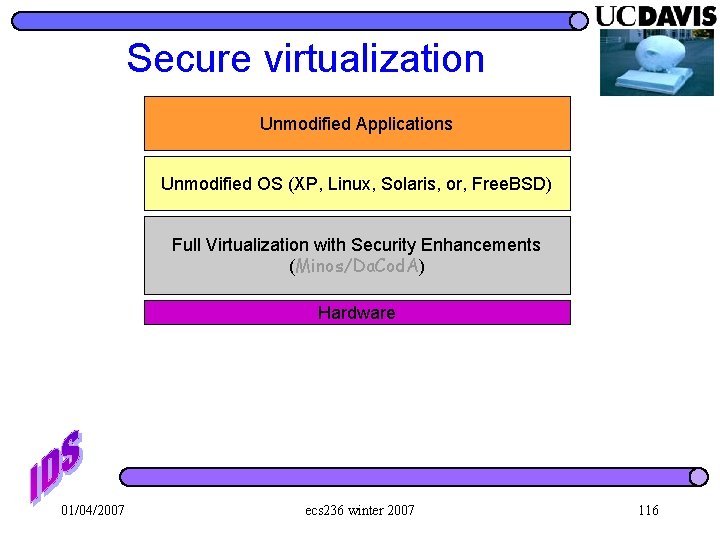
Secure virtualization Unmodified Applications Unmodified OS (XP, Linux, Solaris, or, Free. BSD) Full Virtualization with Security Enhancements (Minos/Da. Cod. A) Hardware 01/04/2007 ecs 236 winter 2007 116

Asymmetric Information l Can we fill the gap? ? 01/04/2007 ecs 236 winter 2007 117

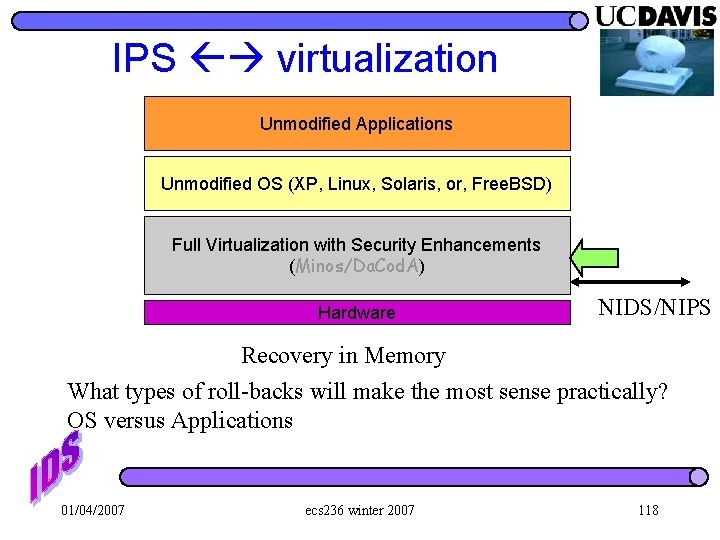
IPS virtualization Unmodified Applications Unmodified OS (XP, Linux, Solaris, or, Free. BSD) Full Virtualization with Security Enhancements (Minos/Da. Cod. A) Hardware NIDS/NIPS Recovery in Memory What types of roll-backs will make the most sense practically? OS versus Applications 01/04/2007 ecs 236 winter 2007 118

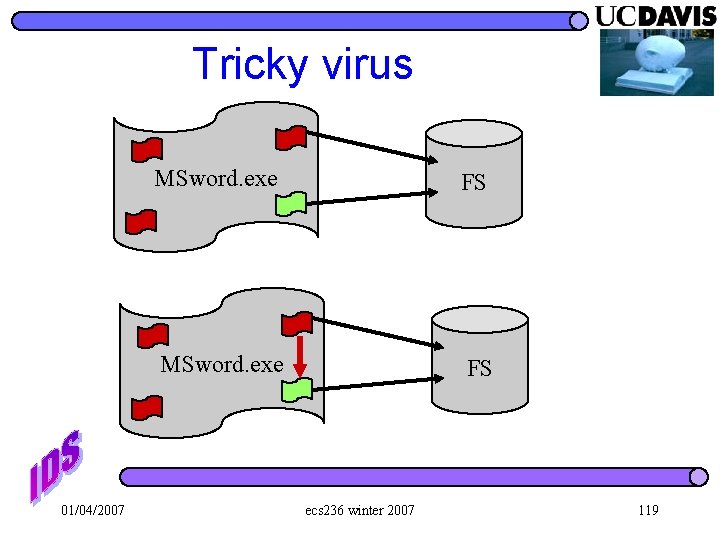
Tricky virus 01/04/2007 MSword. exe FS ecs 236 winter 2007 119

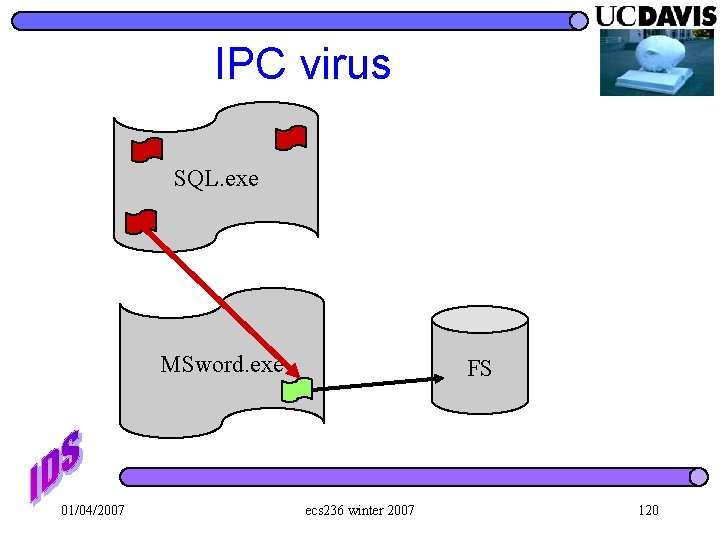
IPC virus SQL. exe MSword. exe 01/04/2007 FS ecs 236 winter 2007 120

Two definitions of Virus l A virus is a program that is able to infect other programs by modifying them to include a possibly evolved copy of itself. – Fred Cohen, early 80’s. l A computer virus is a program that recursively and explicitly copies a possibly evolved version of itself. – Peter Szor, recently. 01/04/2007 ecs 236 winter 2007 121