Computer and Network Security John Kristoff jtkdepaul edu




































- Slides: 66

Computer and Network Security John Kristoff jtk@depaul. edu +1 312 362 -5878 De. Paul University Chicago, IL 60604 IPD - November 3, 2001 John Kristoff - De. Paul University 1

What are you trying to secure? � Confidentiality � Avoid � Authentication snooping � Encryption? that you? � Nonrepudiation � Integrity � No � Deletes, changes � Backups � Access control off! � Reputation attacks IPD - November 3, 2001 denying it � Hands � Availability � (D)Do. S � Is � Name John Kristoff - De. Paul University = MUD 2

Internet security really bites � LOTS � Bad of hosts are hard to secure default configurations � Poor software implementations � Fixes/patches � Average � It rarely applied user/admin is security clueless is difficult to coordinate among sites � Any weak link can break the security chain IPD - November 3, 2001 John Kristoff - De. Paul University 3

Why doesn't telco security bite? Telco Internet � Central authority � Network � Billing intelligence records per call � Legalese understood � Wiretapping � Circuit laws connections IPD - November 3, 2001 � No central authority � End � No host intelligence packet accounting � Legalese � Privacy � Ease John Kristoff - De. Paul University fuzzy issues of anonymity 4

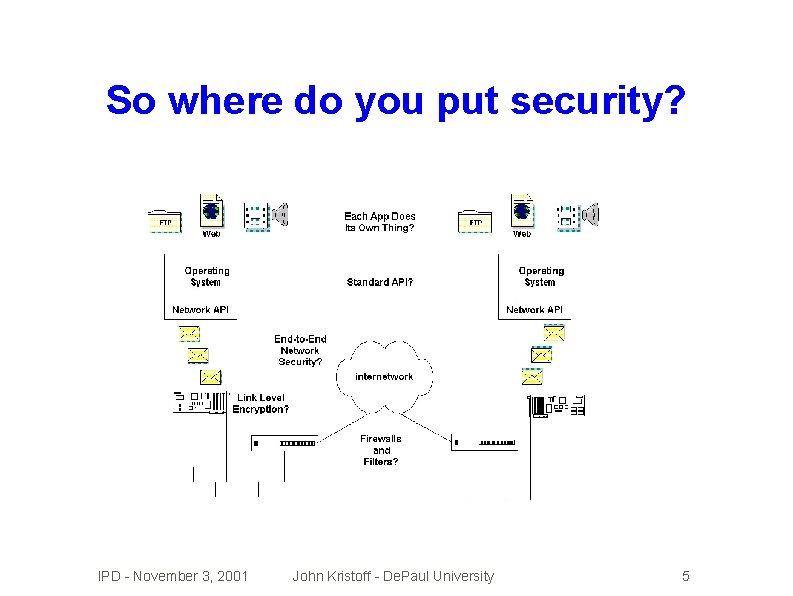
So where do you put security? IPD - November 3, 2001 John Kristoff - De. Paul University 5

Physical security � Trash bins � Social engineering � It's easier to trust a face/voice than a packet � Protect from the whoops! � Don't trip over the power cord � Don't spill your coffee � Hit the right switch � Software really can kill hardware IPD - November 3, 2001 John Kristoff - De. Paul University 6

End host security � The end-to-end argument � This is usually where the problem is � But, ultimately you want to protect data � End hosts are in control of data � Users are in control of hosts � Users often don't secure hosts sufficiently � There are LOT of hosts and LOTS of users IPD - November 3, 2001 John Kristoff - De. Paul University 7

Network security � Inspect � Boy, and act on packets as they go this is really hard! � Evasive tactics like tunneling get through � Uh-oh. . . encryption � What � Can � This am I breaking? I relay, inspect and act fast enough? might help, but its not a panacea IPD - November 3, 2001 John Kristoff - De. Paul University 8

Probably need layered defenses � The belt and suspenders approach � Attackers � Multiple � Use � If might hit a layer they can't break layers tend to slow attacks down the laws of statistics defense A stops 90% of all attacks, � And if defense B stops 90% of all attacks, � Then combined they may stop 99% of all attacks �(1 -. 9)*(1 -. 9) IPD - November 3, 2001 =. 01, 1 -. 01 =. 99 or 99% John Kristoff - De. Paul University 9

The network is just a highway � How do you secure the highway � Police � Toll patrol booths � Licensed � Vehicle � Rules � Are drivers inspections and standards of the road the highways completely safe now? IPD - November 3, 2001 John Kristoff - De. Paul University 10

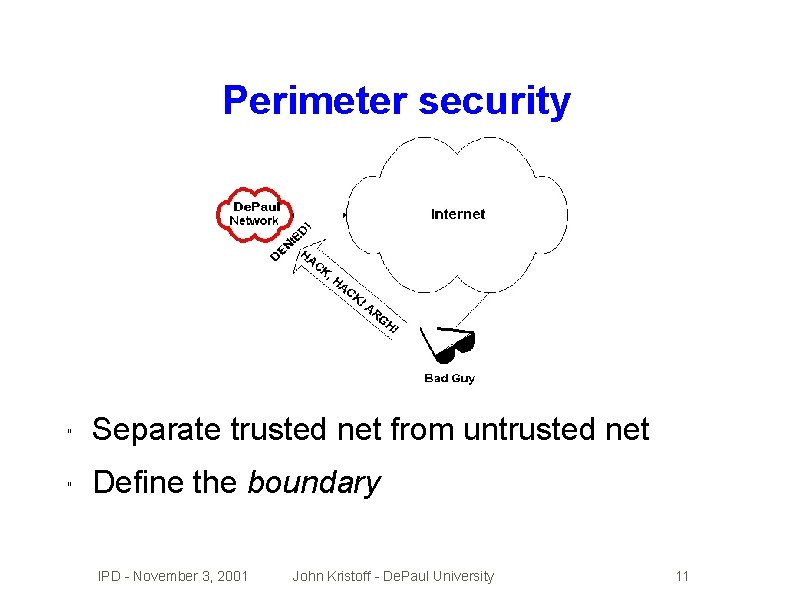
Perimeter security " Separate trusted net from untrusted net " Define the boundary IPD - November 3, 2001 John Kristoff - De. Paul University 11

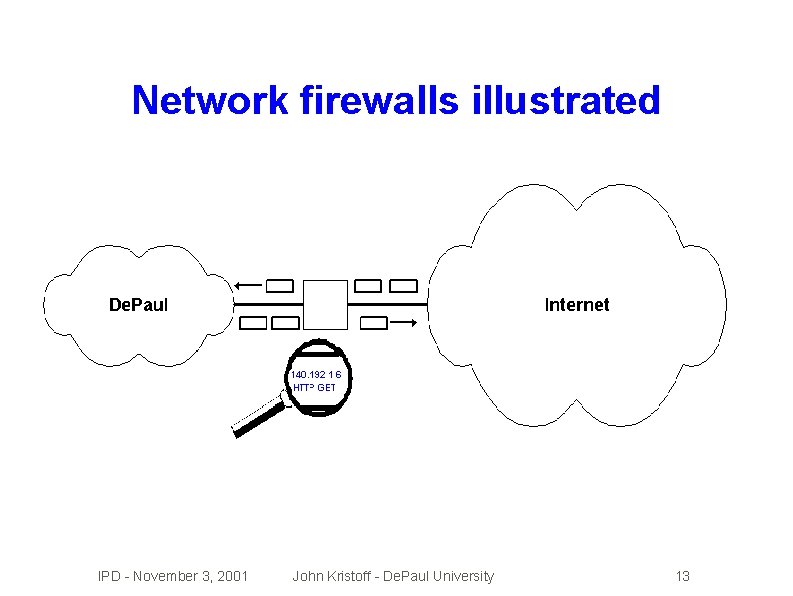
What network firewalls do � Define untrusted and trusted boundaries � Inspect traffic traversing firewall boundary � Limit communication traversing boundary � Help shield insecure hosts IPD - November 3, 2001 John Kristoff - De. Paul University 12

Network firewalls illustrated IPD - November 3, 2001 John Kristoff - De. Paul University 13

Key ideas �Firewalls �They're �They a network solution to a host problem don't solve the real problem and. . . �. . make it hard/impossible to do certain things �Ultimate control of hosts is out of our hands �Securing �But. . should be unnecessary a LOT of hosts is hard! network solutions are *sigh* necessary IPD - November 3, 2001 John Kristoff - De. Paul University 14

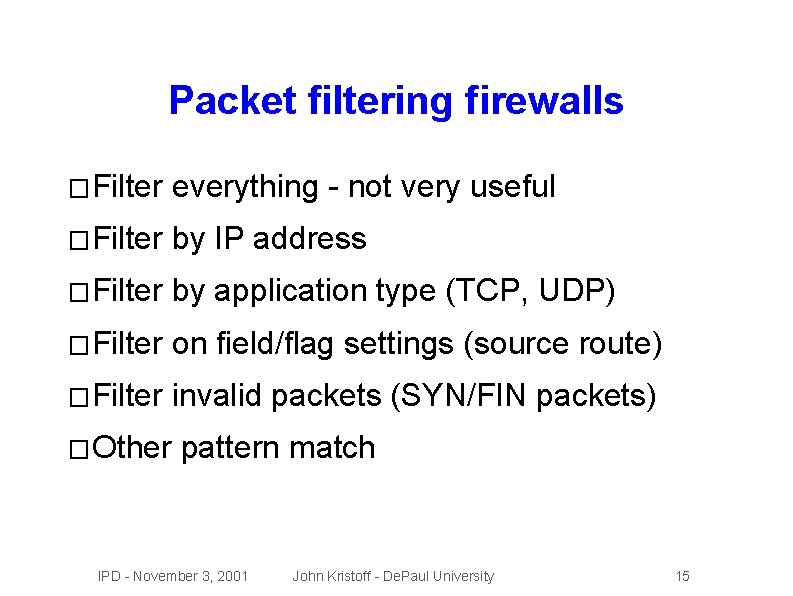
Packet filtering firewalls � Filter everything - not very useful � Filter by IP address � Filter by application type (TCP, UDP) � Filter on field/flag settings (source route) � Filter invalid packets (SYN/FIN packets) � Other pattern match IPD - November 3, 2001 John Kristoff - De. Paul University 15

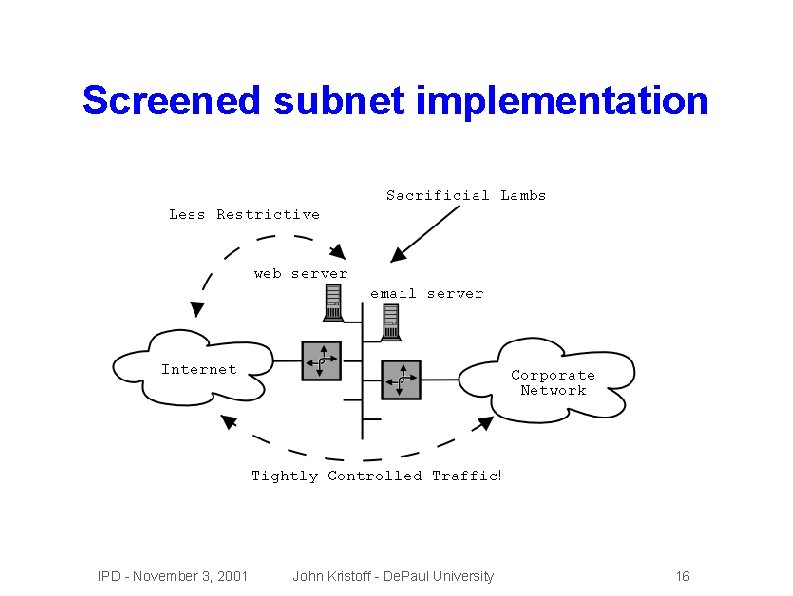
Screened subnet implementation IPD - November 3, 2001 John Kristoff - De. Paul University 16

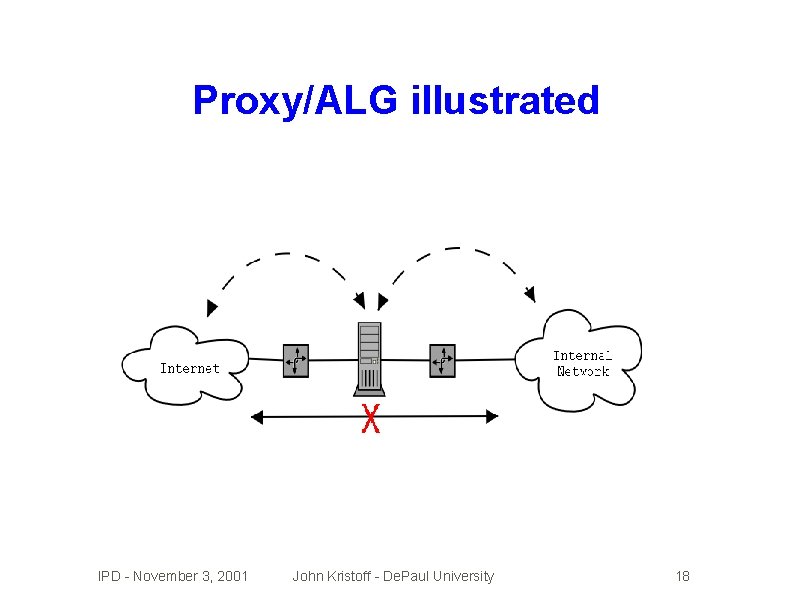
Application Layer Gateway (ALG) � Also commonly called a proxy firewall � These permit no direct communication � Firewall � Very intercepts all traffic in each direction intelligent device. . . �. . . must understand what a user is doing � Difficult to install if it doesn't currently exist IPD - November 3, 2001 John Kristoff - De. Paul University 17

Proxy/ALG illustrated IPD - November 3, 2001 John Kristoff - De. Paul University 18

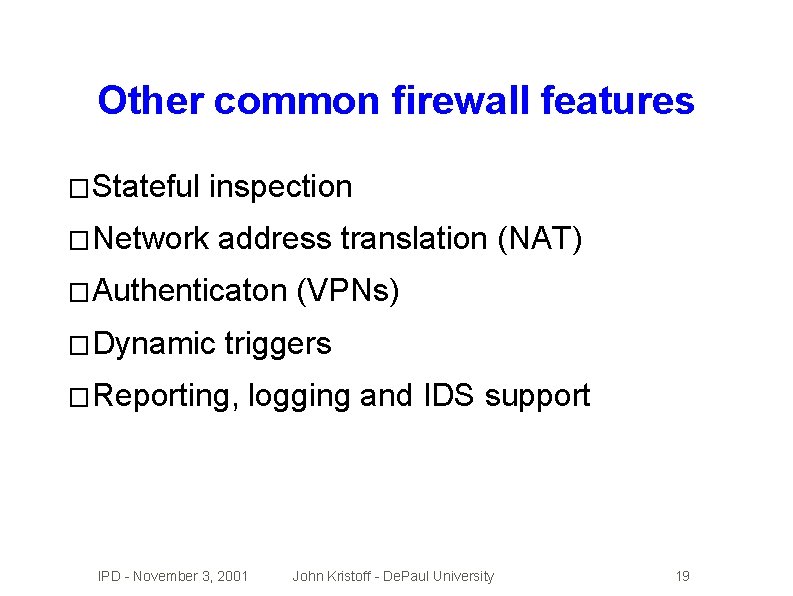
Other common firewall features � Stateful inspection � Network address translation (NAT) � Authenticaton � Dynamic (VPNs) triggers � Reporting, logging and IDS support IPD - November 3, 2001 John Kristoff - De. Paul University 19

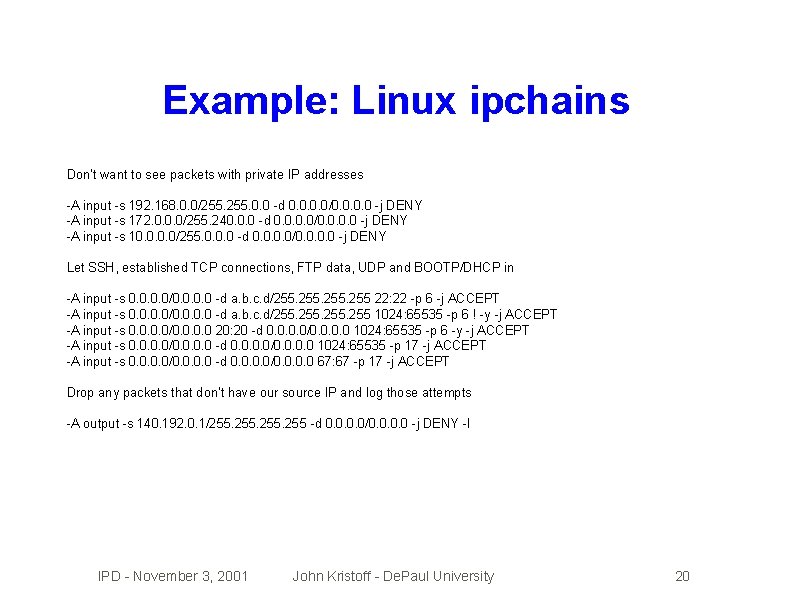
Example: Linux ipchains Don't want to see packets with private IP addresses -A input -s 192. 168. 0. 0/255. 0. 0 -d 0. 0/0. 0 -j DENY -A input -s 172. 0. 0. 0/255. 240. 0. 0 -d 0. 0/0. 0 -j DENY -A input -s 10. 0/255. 0. 0. 0 -d 0. 0/0. 0 -j DENY Let SSH, established TCP connections, FTP data, UDP and BOOTP/DHCP in -A input -s 0. 0/0. 0 -d a. b. c. d/255. 255 22: 22 -p 6 -j ACCEPT -A input -s 0. 0/0. 0 -d a. b. c. d/255. 255 1024: 65535 -p 6 ! -y -j ACCEPT -A input -s 0. 0/0. 0 20: 20 -d 0. 0/0. 0 1024: 65535 -p 6 -y -j ACCEPT -A input -s 0. 0/0. 0 -d 0. 0/0. 0 1024: 65535 -p 17 -j ACCEPT -A input -s 0. 0/0. 0 -d 0. 0/0. 0 67: 67 -p 17 -j ACCEPT Drop any packets that don't have our source IP and log those attempts -A output -s 140. 192. 0. 1/255. 255 -d 0. 0/0. 0 -j DENY -l IPD - November 3, 2001 John Kristoff - De. Paul University 20

Example: Cisco ACL Block private IP addresses access-list 100 deny ip 192. 168. 0. 0. 255 any access-list 100 deny ip 172. 0. 0. 0 0. 15. 255 any access-list 100 deny ip 10. 0 0. 255 any Block reserved, loopback and Class E IP addresses access-list 100 deny ip 0. 0 0. 255 any access-list 100 deny ip 127. 0. 0. 0 0. 255 any access-list 100 deny ip 224. 0. 0. 0 31. 255 any Block source port of 111 from going anywhere access-list 100 deny tcp any eq sunrpc any access-list 100 deny udp any eq sunrpc any Allow DNS and TELNET (log it) to 1. 2. 3. 4, deny everything else access-list 100 permit tcp any host 1. 2. 3. 4 eq domain access-list 100 permit tcp any host 1. 2. 3. 5 eq telnet log IPD - November 3, 2001 access-list 100 deny ip any. John Kristoff - De. Paul University 21

What can't a network firewall stop? � Bad packets that look good � Denial � Well, � But of service (Do. S) attacks they can stop them at the firewall then the firewall has just been Do. S'd � Stupid user tricks � Things that go around the firewall � Things that don't cross the firewall boundary IPD - November 3, 2001 John Kristoff - De. Paul University 22

So you're saying. . . ? �It would be nice if all hosts could be secured �Network solutions can help �Malicious �A insiders can get by anything you got holistic approach is needed. Including: � Audits, detection and response � Education � Standards IPD - November 3, 2001 and best practices John Kristoff - De. Paul University 23

Intrusion Detection Systems � Interesting, � Provides but immature technology lots of data/information � Generally doesn't interfere with communications � Anything that improves security. . . IPD - November 3, 2001 John Kristoff - De. Paul University 24

What is IDS? � Ideally, immediately identifies successful attacks � Should have a immediate notification system � Out-of-band � Probably from the attack if possible can also monitor attack attempts too � Might have attack diagnosis, recommendation and/or automated attack mitigation response � Lofty goals: � 0% false positive rate � 0% false negative rate IPD - November 3, 2001 John Kristoff - De. Paul University 25

Privacy issues � Does � Are � Is an IDS violate privacy? packet headers (protocols) private? identification (an address) private? � Are packet contents private (payload)? � Are communications (flows/sessions) private? � Where is the IDS? � Who manages the IDS? � How is the IDS data handled and managed? IPD - November 3, 2001 John Kristoff - De. Paul University 26

Storage, mining and presentation � IDSs can collect LOTS of information � What is useful data? � What are you looking for? � Data correlation within/outside of the IDS? � What does the admin see? � Where � How and for how long do you keep data? do you secure access to IDS data? IPD - November 3, 2001 John Kristoff - De. Paul University 27

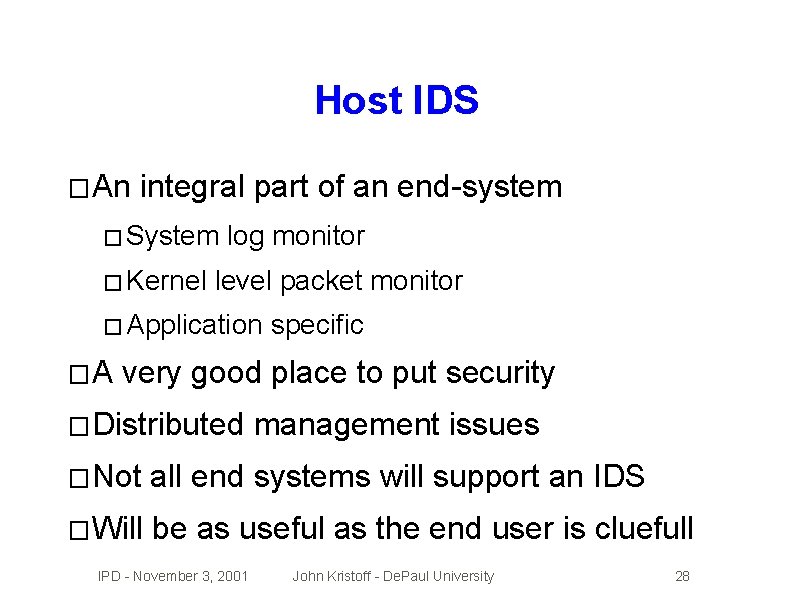
Host IDS � An integral part of an end-system � System � Kernel log monitor level packet monitor � Application �A specific very good place to put security � Distributed management issues � Not all end systems will support an IDS � Will be as useful as the end user is cluefull IPD - November 3, 2001 John Kristoff - De. Paul University 28

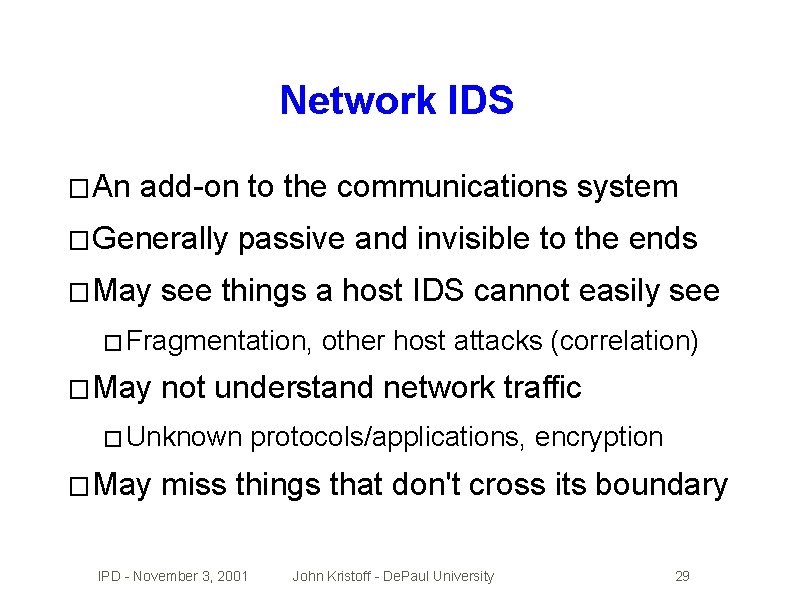
Network IDS � An add-on to the communications system � Generally � May passive and invisible to the ends see things a host IDS cannot easily see � Fragmentation, � May not understand network traffic � Unknown � May other host attacks (correlation) protocols/applications, encryption miss things that don't cross its boundary IPD - November 3, 2001 John Kristoff - De. Paul University 29

Anomaly detection �A form of artificial intelligence � Learn � If what is normal for a network/system an event is not normal, generate alert � May � For catch new attacks not seen before a simple, but effective example see: � Detecting Backdoors, Y. Zhang and V. Paxson, 9 th USENIX Security Symposium � An area of active research IPD - November 3, 2001 John Kristoff - De. Paul University 30

Signature matching � Know what an attack looks like and look for it � Very easy to implement � Low false positive rate � Most current IDSs are of this type � Easy to fool � Signatures IPD - November 3, 2001 must be added/updated regularly John Kristoff - De. Paul University 31

Honeypots �A system that welcomes attacks � Unbeknownst to the attacker generally � The system is very closely monitored � Can be used to test new technology/systems � Generally � Helpful � Be educational in nature as trend monitor for that system type careful honeypot doesn't become liability IPD - November 3, 2001 John Kristoff - De. Paul University 32

Possible IDS failure modes � Fragmentation, � Requires � Inability state and high-speeds lots of CPU, memory and bandwidth to decode message/transaction � t^Hrr^Hm 56^H^H � Background //^H -u^Hrf noise � Tunnelling/encryption � IDS path evasion � Stupid user tricks IPD - November 3, 2001 John Kristoff - De. Paul University 33

The poor man's Network IDS � Setup a router subnet and unix host � Block all outgoing/incoming packets � access-list 100 deny ip any log � Log packets (filter matches) with syslog � Use perl/grep/uniq/. . . to build simple reports � Total violations: 468 � Top source host: badguy. org � Top dest. TCP port: 21 (ftp) IPD - November 3, 2001 John Kristoff - De. Paul University 34

The poor man's host IDS � Use � Turn snort (http: //www. snort. org) or. . . on all logging and do log reporting � Install fake service and monitor � tcp_wrappers, � Use diff (or equivalent), monitor file changes � Keep � Use back officer friendly copies of data/configs elsewhere Tripwire or equivalent IPD - November 3, 2001 John Kristoff - De. Paul University 35

Encryption or Fodszqujpo �Try to make something readable, unreadable �Usually math intensive �Plain text to cipher text to plain text �Need strong algorithms and secure keys � Public � How � Key versus private keys do you exchange keys securely? escrow, recovery and trusted 3 rd parties IPD - November 3, 2001 John Kristoff - De. Paul University 36

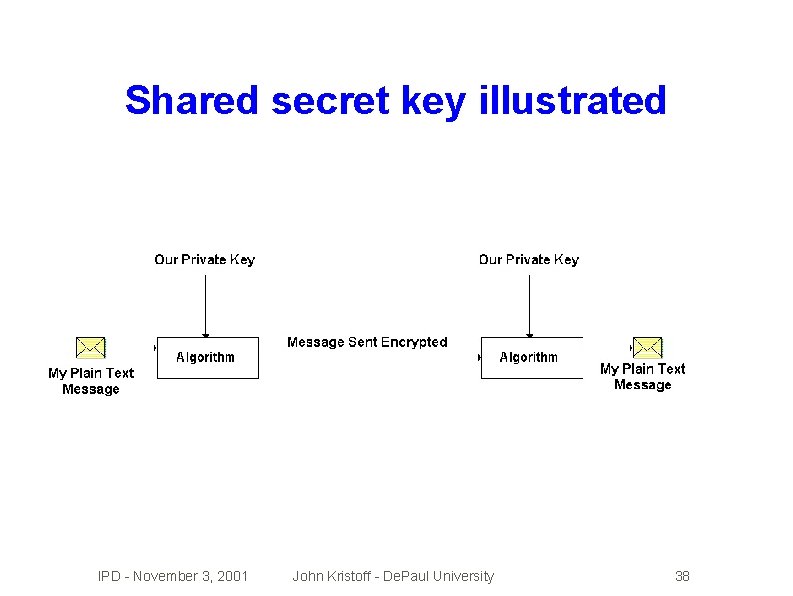
Shared secret key �Each �The party knows the secret key decrypts the cipher text � Book = Ulysses � Key = 7, 23, 4 �. . . or page 7, line 23, word 4 �Ulysses �How is the secret key, don't tell anyone! do the trusted parties learn the key? IPD - November 3, 2001 John Kristoff - De. Paul University 37

Shared secret key illustrated IPD - November 3, 2001 John Kristoff - De. Paul University 38

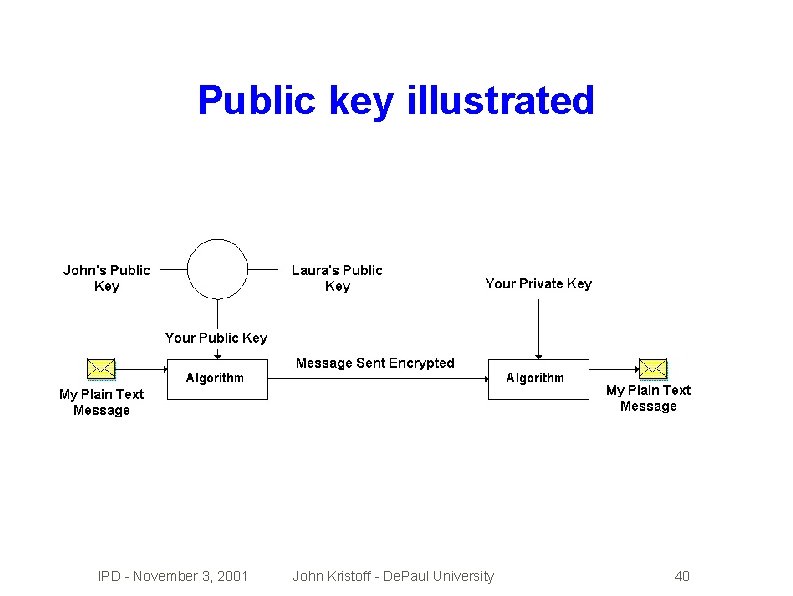
Public key cryptography �Advertise your well known public key � Everyone � Once �Private � Only uses it to encrypt messages to you encrypted, no one can decrypt it key you have the private key � Private �Keyrings key decrypts the public key encryption and secure public key distribution IPD - November 3, 2001 John Kristoff - De. Paul University 39

Public key illustrated IPD - November 3, 2001 John Kristoff - De. Paul University 40

Pretty Good Privacy (PGP) �Crypto �Uses software for mail, files and disks public (and private) key technology �Supports �Public �Free digital signatures key servers maintain public keys for non-commercial use �http: //web. mit. edu/network/pgp. html IPD - November 3, 2001 John Kristoff - De. Paul University 41

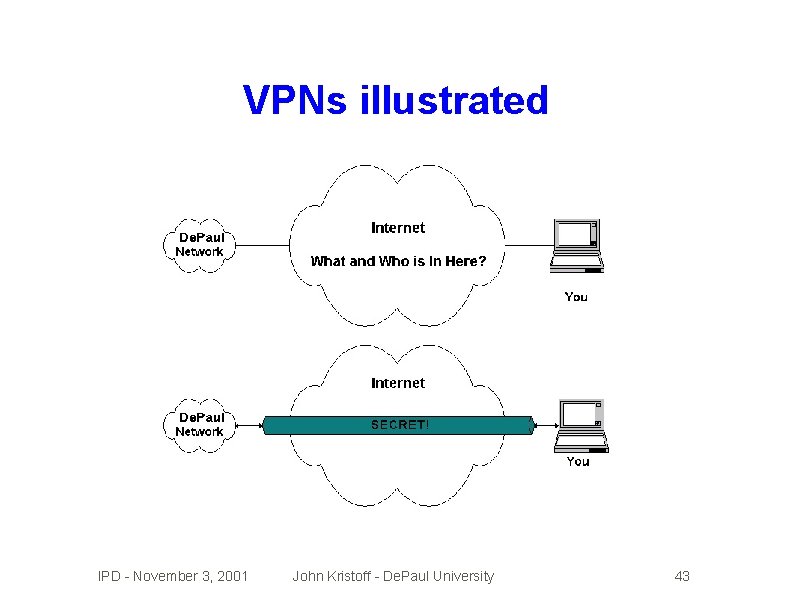
Virtual Private Networks (VPNs) �Make �Use an insecure public network secure Internet instead of building your own net �Secure/encrypted �Endpoints �Sound �Many tunnels between endpoints must be secure like a host security problem? Yep. challenges and trade-offs IPD - November 3, 2001 John Kristoff - De. Paul University 42

VPNs illustrated IPD - November 3, 2001 John Kristoff - De. Paul University 43

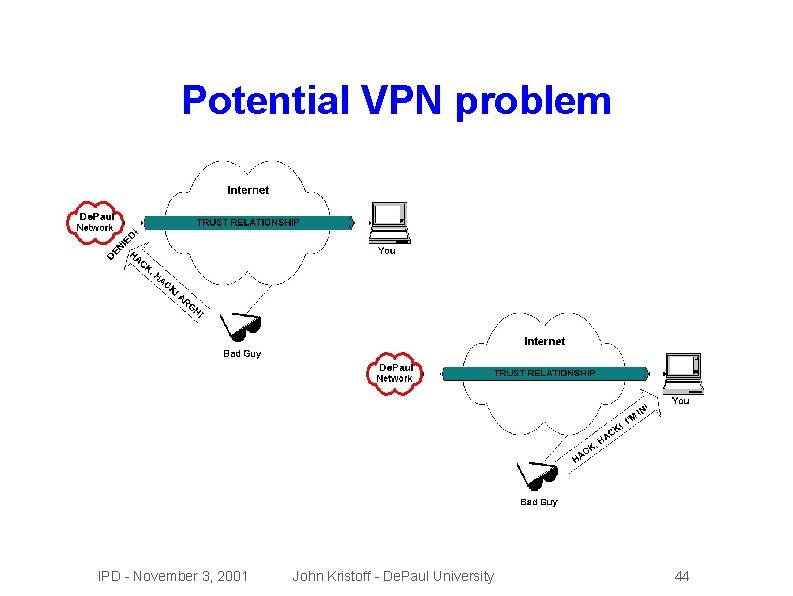
Potential VPN problem IPD - November 3, 2001 John Kristoff - De. Paul University 44

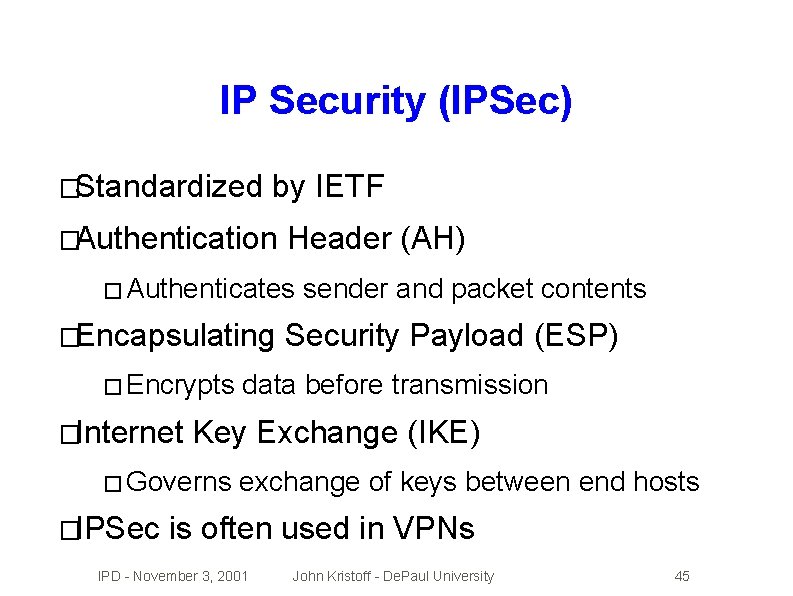
IP Security (IPSec) �Standardized by IETF �Authentication Header (AH) � Authenticates �Encapsulating � Encrypts �Internet Security Payload (ESP) data before transmission Key Exchange (IKE) � Governs �IPSec sender and packet contents exchange of keys between end hosts is often used in VPNs IPD - November 3, 2001 John Kristoff - De. Paul University 45

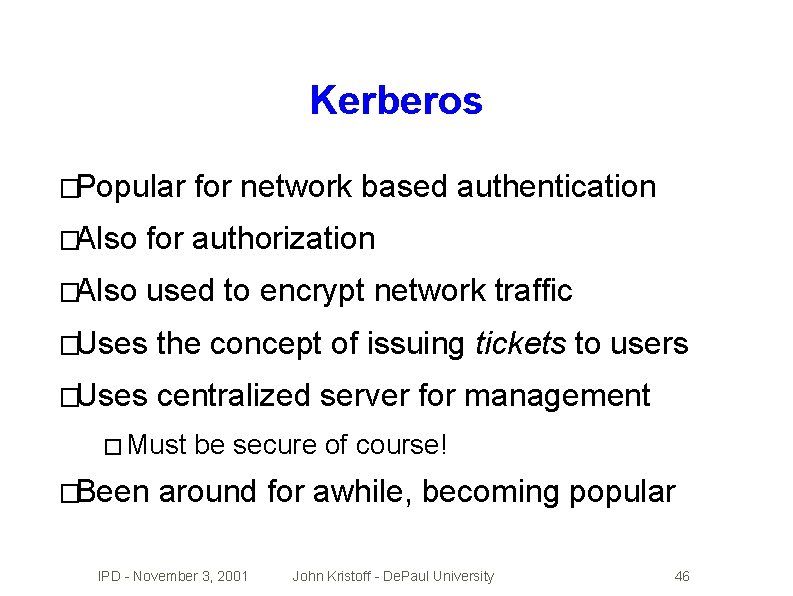
Kerberos �Popular for network based authentication �Also for authorization �Also used to encrypt network traffic �Uses the concept of issuing tickets to users �Uses centralized server for management � Must �Been be secure of course! around for awhile, becoming popular IPD - November 3, 2001 John Kristoff - De. Paul University 46

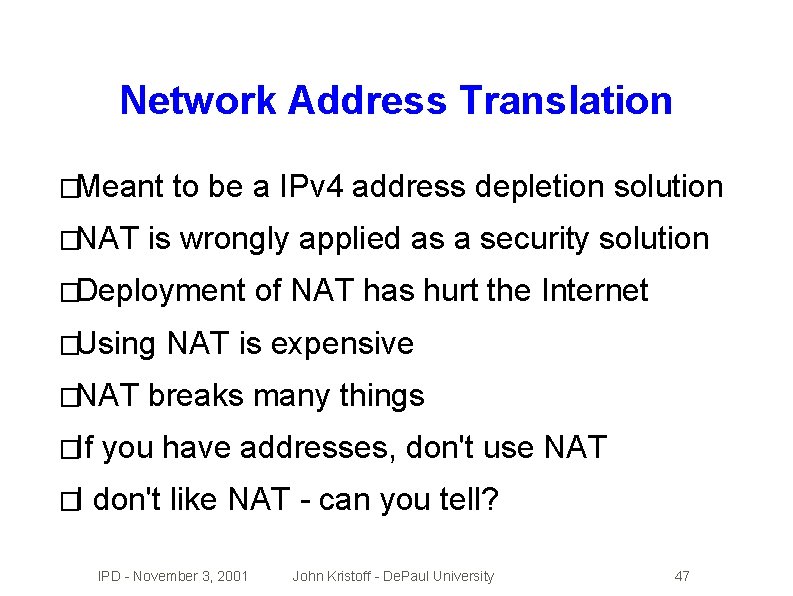
Network Address Translation �Meant �NAT to be a IPv 4 address depletion solution is wrongly applied as a security solution �Deployment �Using �NAT �If �I of NAT has hurt the Internet NAT is expensive breaks many things you have addresses, don't use NAT don't like NAT - can you tell? IPD - November 3, 2001 John Kristoff - De. Paul University 47

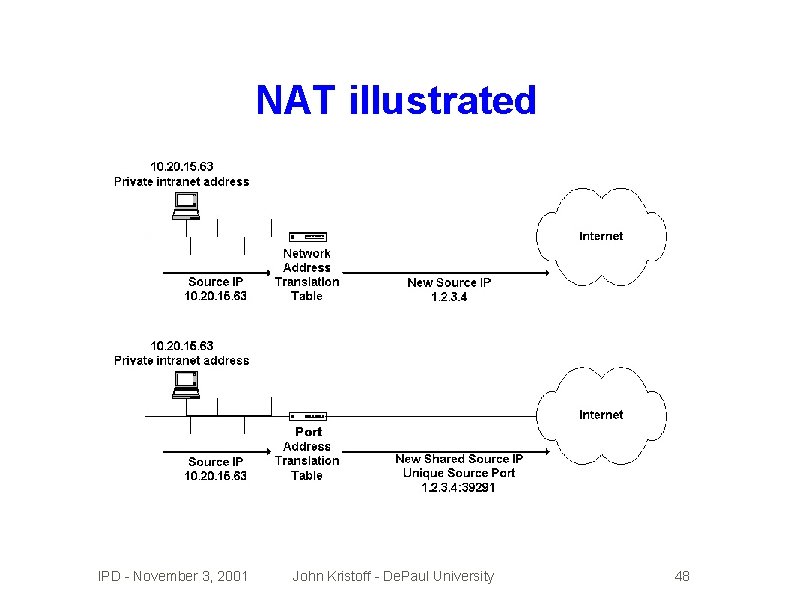
NAT illustrated IPD - November 3, 2001 John Kristoff - De. Paul University 48

Enough already, how do we hack? �We'll focus on over the network attacks �Password � Brute cracking force, keystroke capture, sniff �OS/Application � Buffer �Protocol overflows, cgi-bin attacks, email exploits abuses � Spoofs, �Denial attacks hijacks, redirects, man-in-the-middle of service attacks IPD - November 3, 2001 John Kristoff - De. Paul University 49

Anatomy of a typical compromise �Do some reconnaissance work, scan, probe �Launch the exploit �Maintain �Fix compromised access with backdoors system so no one else gets in �Use/abuse �Make system it look like you were never there �Sometimes a few of these steps are skipped IPD - November 3, 2001 John Kristoff - De. Paul University 50

Network scanning/mapping �PING, �DNS traceroute information �rpcinfo -p <hostname> �nmap �nbtstat, net use commands �Search engines, newsgroups, web sites �If you're on the Internet, you've been scanned IPD - November 3, 2001 John Kristoff - De. Paul University 51

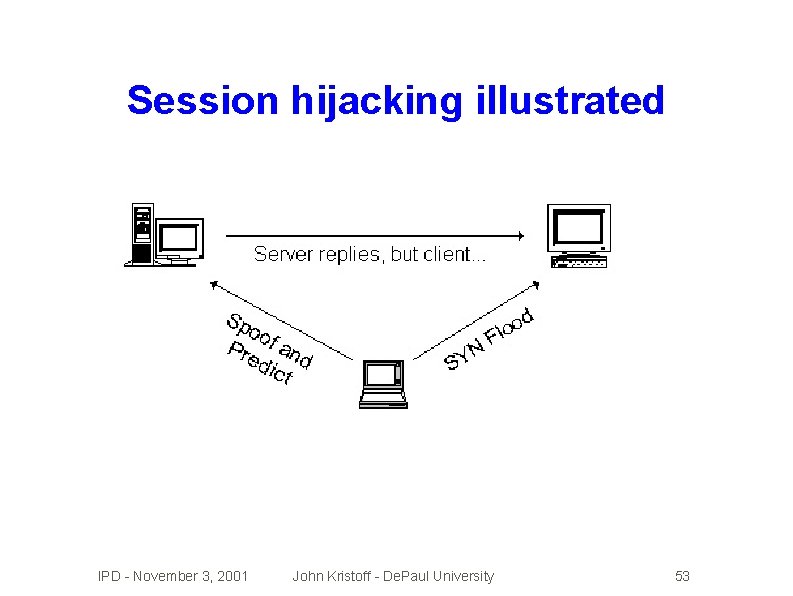
Session hijacking �Pretend �Take �You to be someone you're not over or insert commands into a session may need to � Know IP addresses � Predict � Keep � Run TCP sequence numbers one end of the real session busy blind for awhile IPD - November 3, 2001 John Kristoff - De. Paul University 52

Session hijacking illustrated IPD - November 3, 2001 John Kristoff - De. Paul University 53

Password cracking �Encrypted passwords can be broken � If nothing else, by brute force � Don't �Sending let passwords be the only line of defense logins in plain text over net is bad! � Many apps do this (e. g. FTP, TELNET) � Even HTTP! �Things like kerberos, SSL and SSH help a lot IPD - November 3, 2001 John Kristoff - De. Paul University 54

Viruses and worms �Programs whose goal is to spread �. . . and possibly cause you a great deal of grief �Worms are common (e. g. ILOVEYOU) �Viruses infect other programs �Somehow � Proves � Some � e. g. code has to be executed users are too trusting feature-full apps are becoming problems Microsoft getting burned regularly here IPD - November 3, 2001 John Kristoff - De. Paul University 55

Weak input validation �Buffer overflows and format string attacks � strcpy(destvar, �Try �If srcvar) type of stuff to get your overflowed data to execute program was running as root/Admin. . . �. . . and �It's you can successfully overflow a buffer. . . probably game over for said system. �Remote overflows are very possible/popular IPD - November 3, 2001 John Kristoff - De. Paul University 56

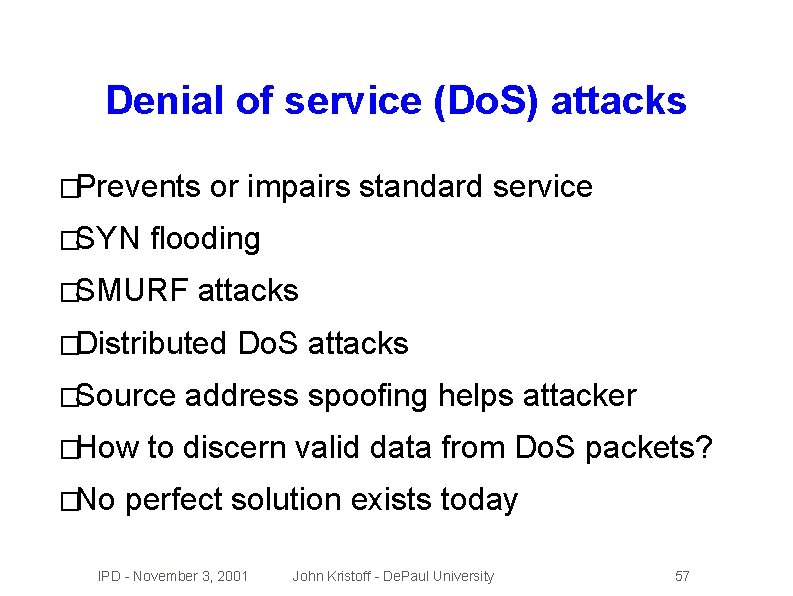
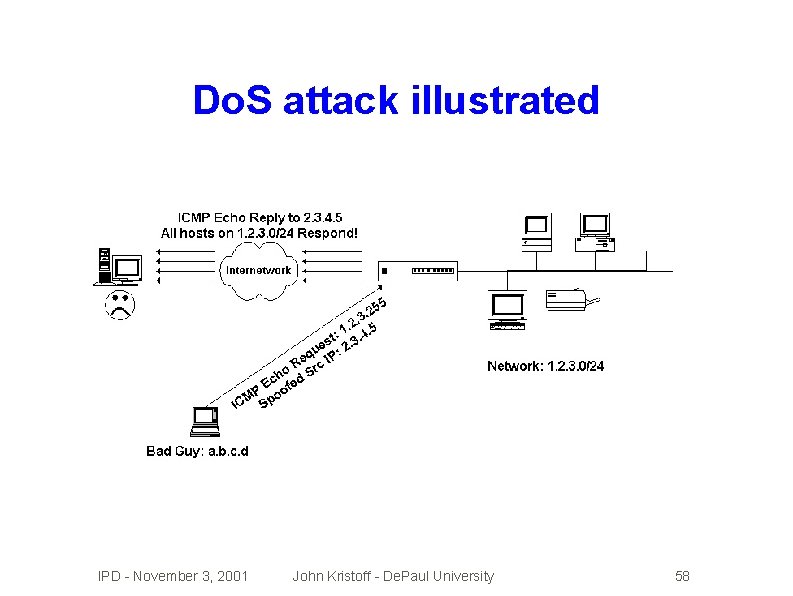
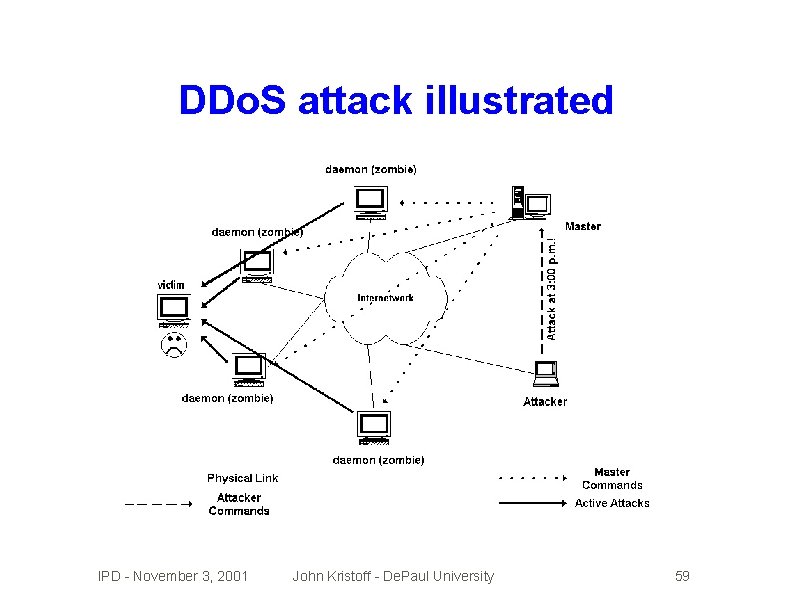
Denial of service (Do. S) attacks �Prevents �SYN or impairs standard service flooding �SMURF attacks �Distributed �Source �How �No Do. S attacks address spoofing helps attacker to discern valid data from Do. S packets? perfect solution exists today IPD - November 3, 2001 John Kristoff - De. Paul University 57

Do. S attack illustrated IPD - November 3, 2001 John Kristoff - De. Paul University 58

DDo. S attack illustrated IPD - November 3, 2001 John Kristoff - De. Paul University 59

Partial (D)Do. S solutions �Gotta find the sources - not trivial if spoofed! �Ingress/egress �ICMP traceback (itrace) �Packet �Rate marking (pushback) limiting �Shunning �Work filtering and black hole routing with upstream provider IPD - November 3, 2001 John Kristoff - De. Paul University 60

How do I secure Windows? �echo Y | del c: *. * Just kidding. . . �Keep up to date on patches � Run Windows Update �Remove unnecessary protocols like NETBIOS �Be very wary of running unknown programs �Do not use file/print sharing �Install and use virus protection, security tools IPD - November 3, 2001 John Kristoff - De. Paul University 61

How do I secure UNIX/Linux? �Remove unnecessary services � Empty � Start out inetd. conf if possible removing rc. d scripts and programs �Keep up to date on patches �Avoid RPC, wu-ftpd, BIND, sendmail � And �Use others that continue to have probs security tools IPD - November 3, 2001 John Kristoff - De. Paul University 62

How do I secure network devices? �Remove �Disable �Install �Put unnecessary services directed broadcasts spoofing filters device IP on secured management net �Secure routing protocols �Secure logs, time sync, snmp, etc. �Keep up to date on system software IPD - November 3, 2001 John Kristoff - De. Paul University 63

How do I secure. . . ? �Web servers �FTP servers �Mail (SMTP/POP/IMAP) servers �Printers, webcams, toasters �Others. . . ? IPD - November 3, 2001 John Kristoff - De. Paul University 64

Any last bit of advice? �Use the Network Time Protocol (NTP) �syslog �SSH is your friend �Learn �Find like you've never syslog'd before and make use of perl a good mailing lists/digests/URLs �Know your netstat -an |more output �Please do not attack De. Paul's network IPD - November 3, 2001 John Kristoff - De. Paul University 65

References http: //networks. depaul. edu/security/ http: //condor. depaul. edu/~jkristof/ news: //news. depaul. edu/dpu. security http: //www. cert. org http: //www. sans. org http: //www. cerias. purdue. edu http: //www. neohapsis. com http: //www. securityfocus. com IPD - November 3, 2001 John Kristoff - De. Paul University 66