Chapter 1 Introduction Components of computer security Threats





- Slides: 11

Chapter 1: Introduction Components of computer security Threats Policies and mechanisms Operational Issues Human Issues Slide #1 -1

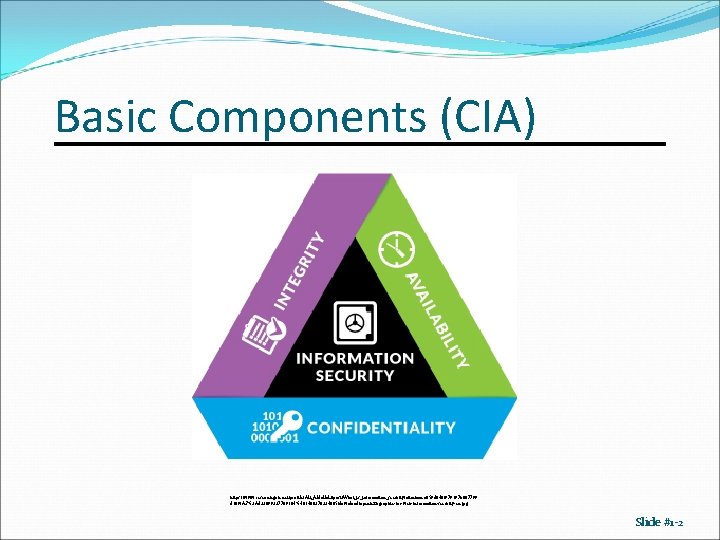
Basic Components (CIA) https: //www. researchgate. net/profile/Ali_Aldallal 2/post/What_is_information_security/attachment/59 d 640 f 979197 b 807799 d 189/AS%3 A 433099327709184%401480270334665/download/opentext-graphic-for-web-information-security-en. jpg Slide #1 -2

Integrity Data integrity (integrity, correctness) Origin integrity (authentication, trustworthiness) Slide #1 -3

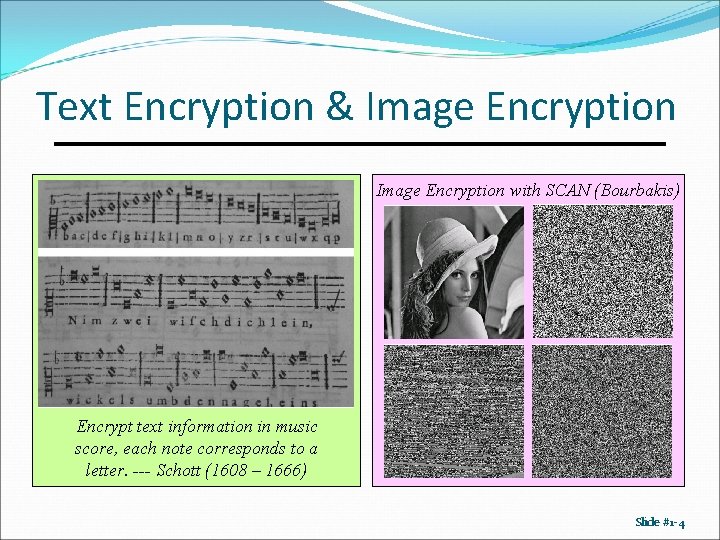
Text Encryption & Image Encryption with SCAN (Bourbakis) Encrypt text information in music score, each note corresponds to a letter. --- Schott (1608 – 1666) Slide #1 -4

Information Hiding - Examples APPARENTLY NEUTRAL’S PROTEST IS THOROUGHLY DISCOUNTED AND IGNORED. ISMAN HARD HIT. BLOCKADE ISSUE AFFECTS PRETEXT FOR EMBARGO ON BYPRODUCTS, EJECTING SUETS AND VEGETABLE OILS. A message sent by a spy in World War II. PERSHING SAILS FROM NY JUNE 1. Extract the second letter from each word. Slide #1 -5

Information Hiding - Examples (Maniccam & Bourbakis) Slide #1 -6

Classes of Threats Threat: potential violation of security; Attack: the actual violation; Attacker: people who execute the violation; http: //datasmithnetworks. com/site/wp-content/uploads/2016/06/Screen-Shot-2016 -06 -16 -at-10. 25. 22 -AM. png Slide #1 -7

Classes of Threats Disclosure: unauthorized access to information Deception: acceptance of false data Disruption: interruption or prevention of correct operation Usurpation: unauthorized control of a part of a system Slide #1 -8

Policies and Mechanisms http: //images. slideplayer. com/15/4818128/slides/slide_4. jpg Slide #1 -9

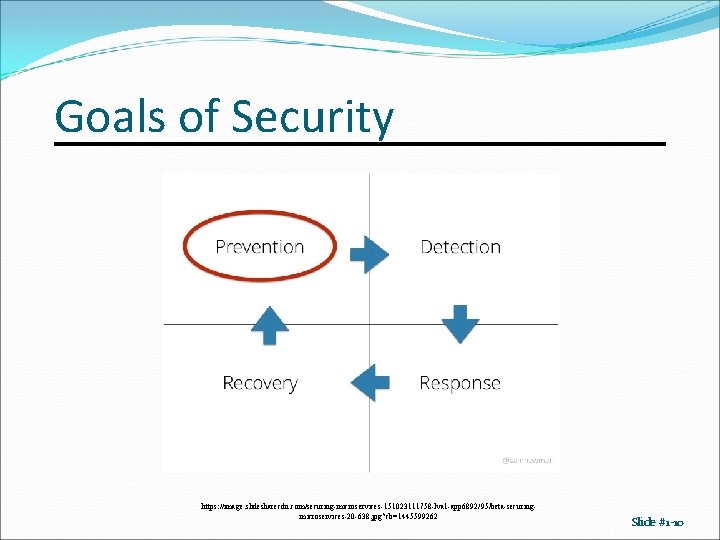
Goals of Security https: //image. slidesharecdn. com/securing-microservices-151023111758 -lva 1 -app 6892/95/beta-securingmicroservices-20 -638. jpg? cb=1445599262 Slide #1 -10

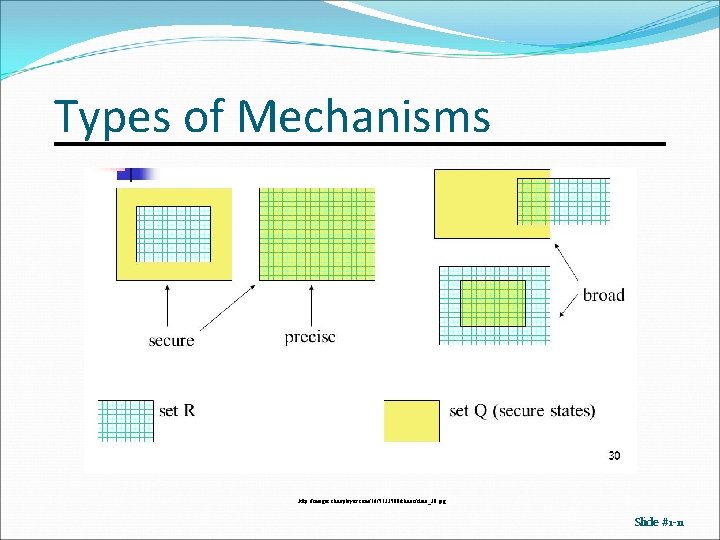
Types of Mechanisms http: //images. slideplayer. com/16/5133500/slides/slide_30. jpg Slide #1 -11