Deploying and Managing Intrusion Detection Systems M 9318207

















- Slides: 28

Deploying and Managing Intrusion Detection Systems 報告人: 黃教翔 M 9318207 94/05/25

Agenda n n n Intrusion Detection Primer Deploying Network Sensors Using Response Actions Effectively

Intrusion Detection Primer


Intrusion Detection Approaches Misuse/Signature vs. Anomaly Detection Network vs. Host-Based

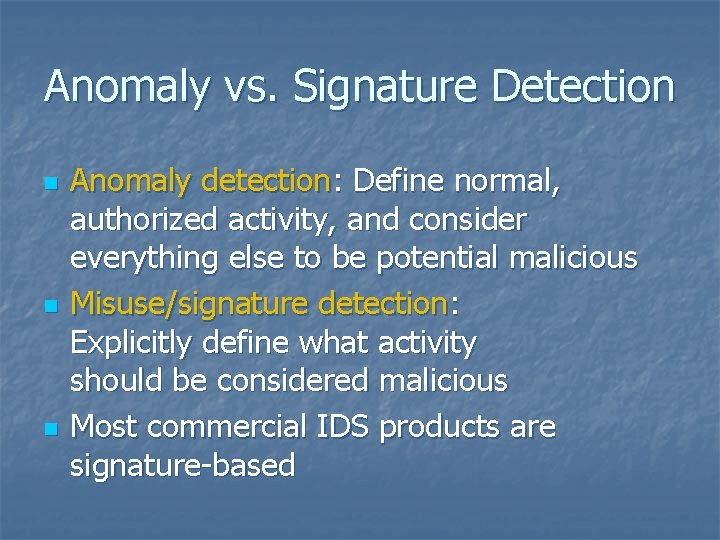
Anomaly vs. Signature Detection n Anomaly detection: Define normal, authorized activity, and consider everything else to be potential malicious Misuse/signature detection: Explicitly define what activity should be considered malicious Most commercial IDS products are signature-based

Host vs. Network-Based n n Host-based: “Agent” software monitoring activity on hosts Network-based: Collects and analyzes data from the network

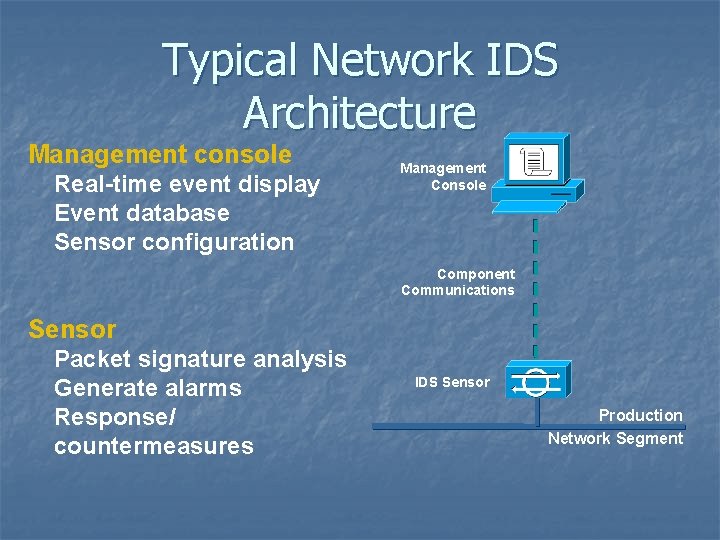
Typical Network IDS Architecture Management console Real-time event display Event database Sensor configuration Management Console Component Communications Sensor Packet signature analysis Generate alarms Response/ countermeasures IDS Sensor Production Network Segment

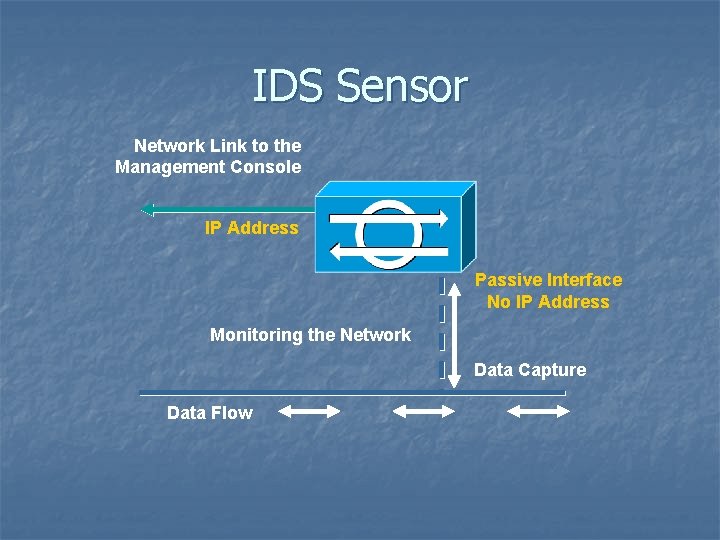
IDS Sensor Network Link to the Management Console IP Address Passive Interface No IP Address Monitoring the Network Data Capture Data Flow

Deploying Network Sensors

IDS Sensors n n Must see all of the monitored traffic Must be able to keep up with monitored traffic Normally not pass-through devices Normally limited to monitoring LAN media segments

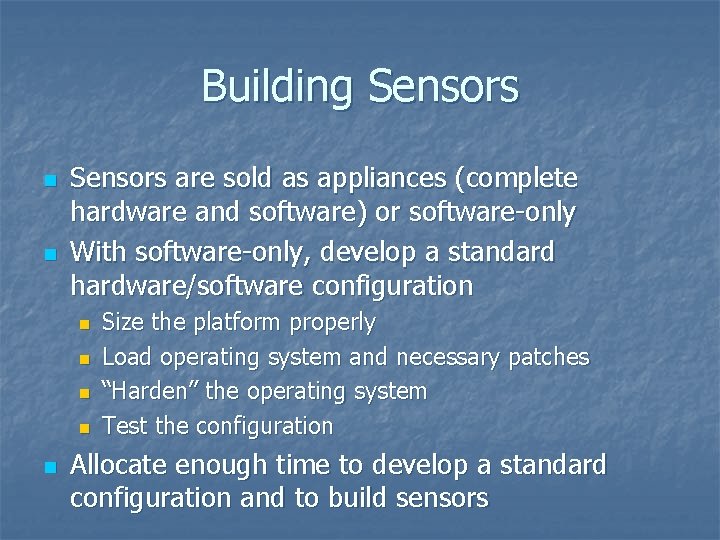
Building Sensors n n Sensors are sold as appliances (complete hardware and software) or software-only With software-only, develop a standard hardware/software configuration n n Size the platform properly Load operating system and necessary patches “Harden” the operating system Test the configuration Allocate enough time to develop a standard configuration and to build sensors

Typical Sensor Placement Critical Servers and Resources Remote/Branch Offices Data Center Corporate Network Internet Workgroup Server Cluster Remote Access Systems Business Partner Access DMZ Servers Internet Connections Extranet Connections

Why at Internet Connections? n n Firewalls usually don’t protect against data driven attacks Consider scenario where you have Web servers on DMZ n n n A number of Web server vulnerabilities discovered during the past year Patches available from vendors, but… Can be exploited to deny service and/or access the server

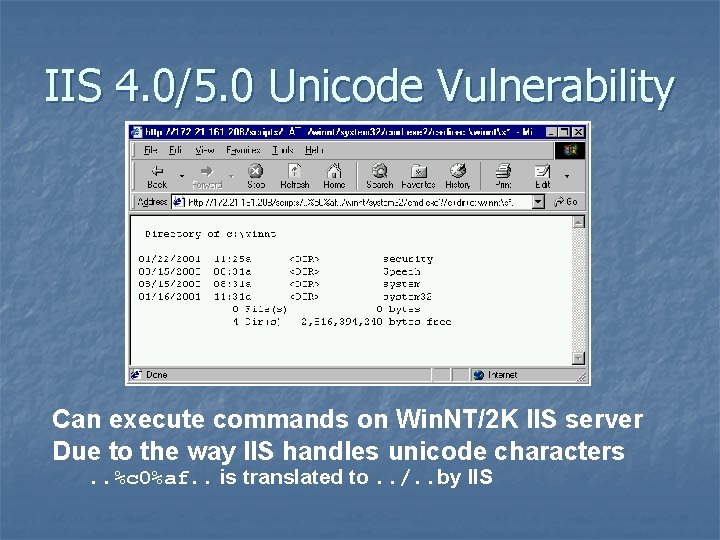
IIS 4. 0/5. 0 Unicode Vulnerability Can execute commands on Win. NT/2 K IIS server Due to the way IIS handles unicode characters. . %c 0%af. . is translated to. . /. . by IIS

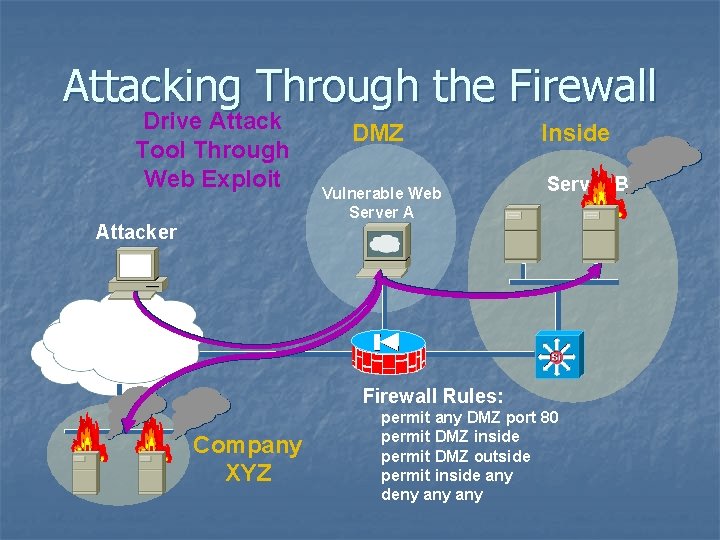
Attacking Through the Firewall Drive Attack Tool Through Web Exploit Attacker DMZ Vulnerable Web Server A Inside Server B Internet Firewall Rules: Company XYZ permit any DMZ port 80 permit DMZ inside permit DMZ outside permit inside any deny any

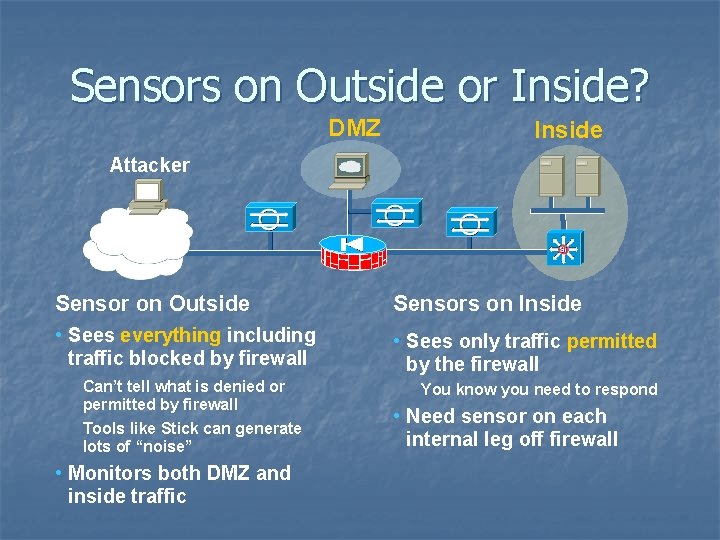
Sensors on Outside or Inside? DMZ Inside Attacker Internet Sensor on Outside Sensors on Inside • Sees everything including traffic blocked by firewall • Sees only traffic permitted by the firewall Can’t tell what is denied or permitted by firewall Tools like Stick can generate lots of “noise” • Monitors both DMZ and inside traffic You know you need to respond • Need sensor on each internal leg off firewall

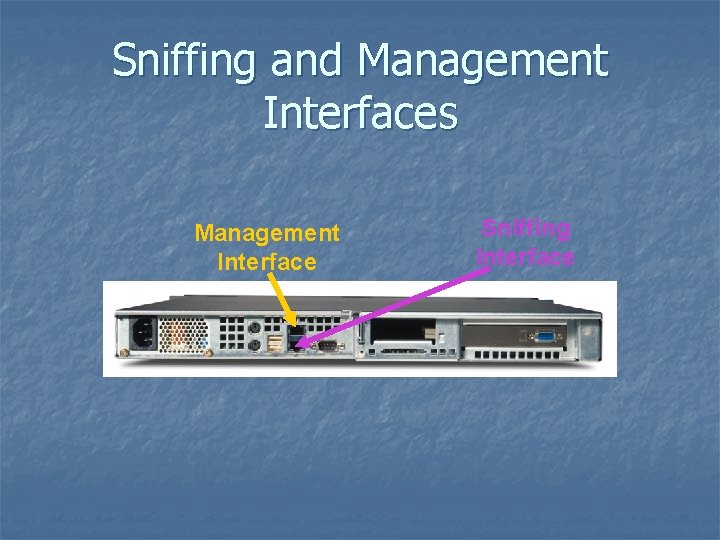
Sniffing and Management Interfaces Management Interface Sniffing Interface

Using Response Actions Effectively

Typical Response Actions TCP resets n IP session logging n “Shunning/blocking” n

TCP Resets n n Resets sent from “sniffing” interface Spoofs source and destination MAC and IP addresses n n Must guess correct TCP sequence number n n Spoofing MAC can confuse switch if using SPAN Makes TCP Resets inherently unreliable especially with a lot of traffic between source and destination Certain applications will automatically reconnect and resend (e. g. , SMTP)

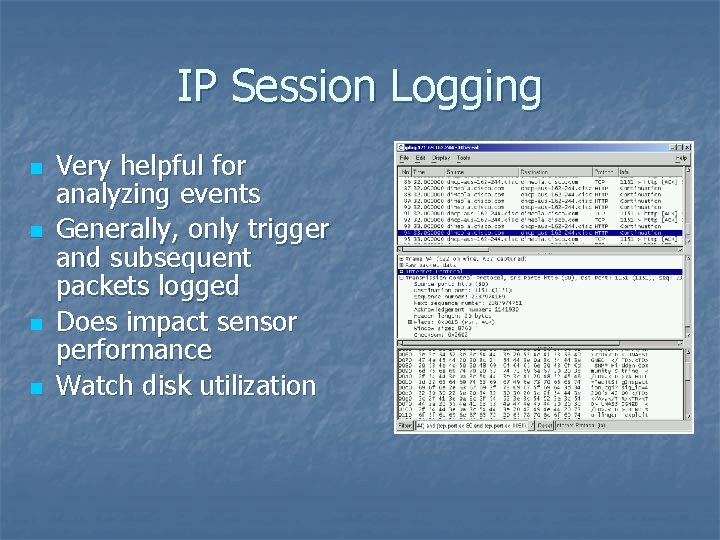
IP Session Logging n n Very helpful for analyzing events Generally, only trigger and subsequent packets logged Does impact sensor performance Watch disk utilization

Shunning/Blocking n Sensor connects to firewall and/or router from management interface n n n Need to configure authentication credentials for router/firewall When signature fires, sensor tells firewall/ router to deny subsequent traffic from that source IP address Note that initial trigger packet will make it to its destination

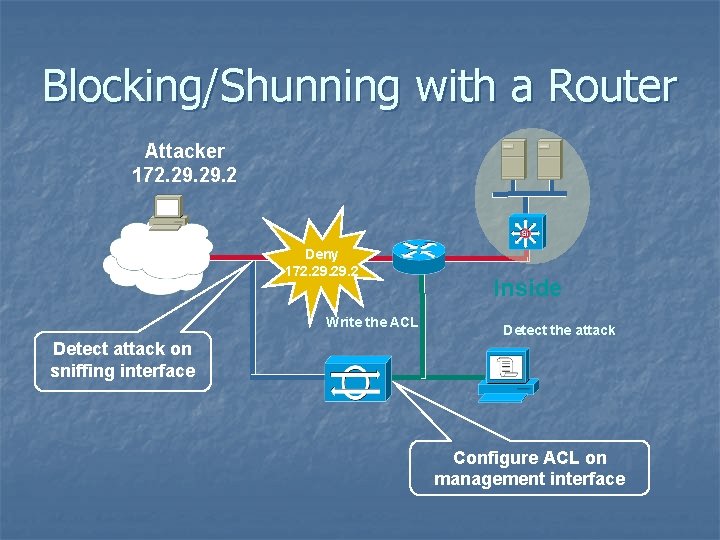
Blocking/Shunning with a Router Attacker 172. 29. 2 Internet Deny 172. 29. 2 Write the ACL Inside Detect the attack Detect attack on sniffing interface Configure ACL on management interface

Where to Apply ACLs n n n Remember that the sensor controls the ACL You configure interface and direction to apply ACL External interface—Apply on inbound direction n n Denies traffic before it enters the router Internal interface—Apply on outbound direction n Doesn’t protect the router Untrusted network External interfaces Inbound ACL Internal interfaces Outbound ACL Protected network


END

Q&A