Computer Networks Chapter 10 Error Detection and Correction









- Slides: 35

Computer Networks Chapter 10 – Error Detection and Correction

Errors § The physical link is always subject to imperfections § Noise/interference § Limited bandwidth § Distortion § Errors – a consequence of imperfecton § Some bits send at the sender are received with different value at the receiver Sender Receiver Value 0 ----- 1 Value sent Spring 2006 1 -----0 received Computer Networks 2

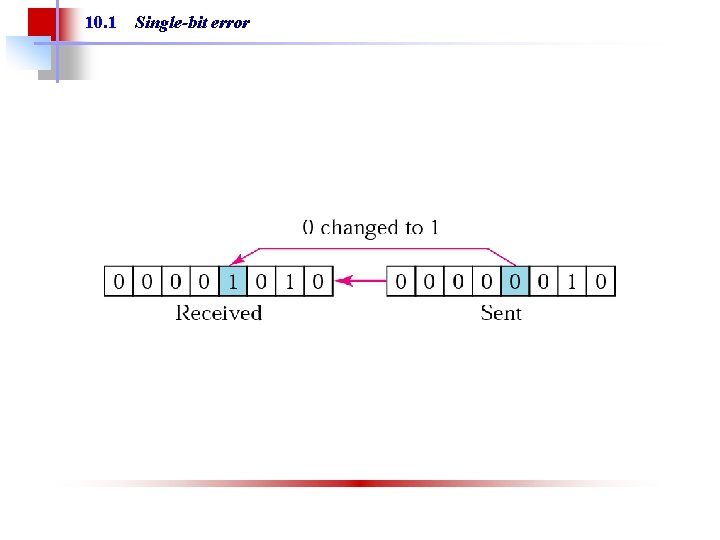
Note: In a single-bit error, only one bit in the data unit has changed.

10. 1 Single-bit error

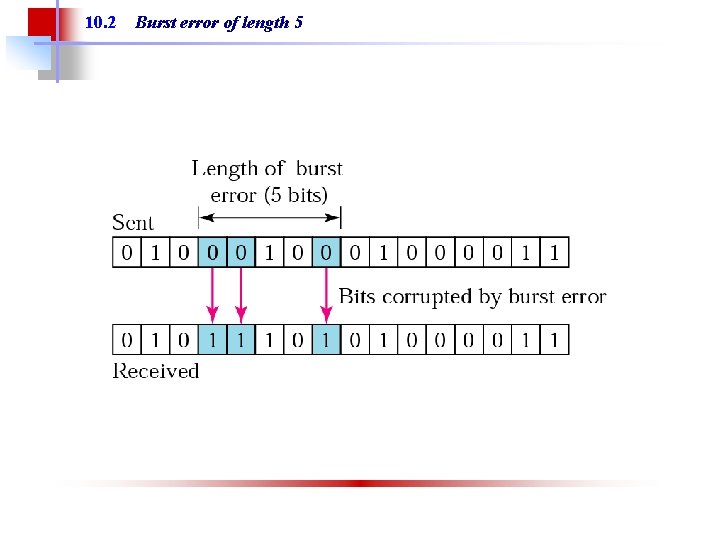
Note: A burst error means that 2 or more bits in the data unit have changed.

10. 2 Burst error of length 5

Types of Errors § Single-bit error § The value of a single bit in a data unit is changed § Does not occur very often in serial data transmission § Burst error § The value of two or more bits in the data unit is changed § Usual type of error in serial data transmission Spring 2006 Computer Networks 7

Errors and Error Effect Original Waterfall Image: Spring 2006 Computer Networks 8

Errors and Error Effect (Cont. ) Waterfall Image: every tenth bit in error Spring 2006 Computer Networks 9

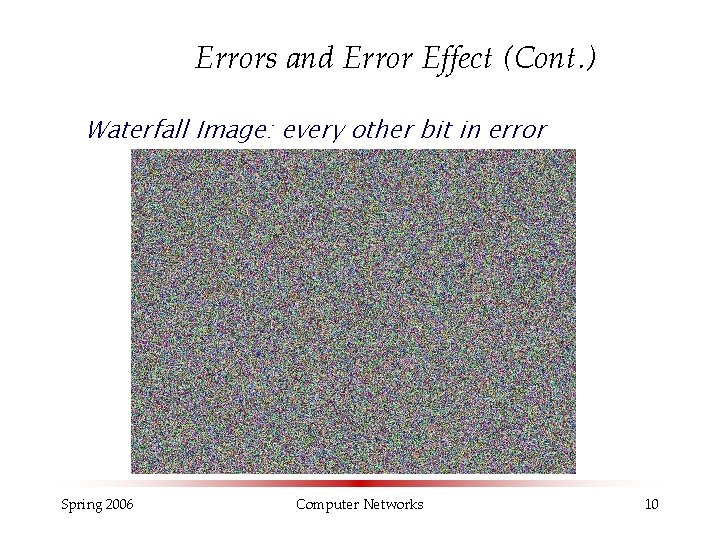
Errors and Error Effect (Cont. ) Waterfall Image: every other bit in error Spring 2006 Computer Networks 10

Two Strategies for Error Control § Error detection and correction § Enough redundancy (extra bits) is incorporated, so that at the reciever the errors can be not only detected, but also corrected § Not applicable to data communication, because too much redundancy is needed § Error detection and retransmission § There is enough redundancy only to detect the error in a data unit. If an error is descovered the sender is automaticly required to retransmit the data unit § Applicabbble to data communication Spring 2006 Computer Networks 11

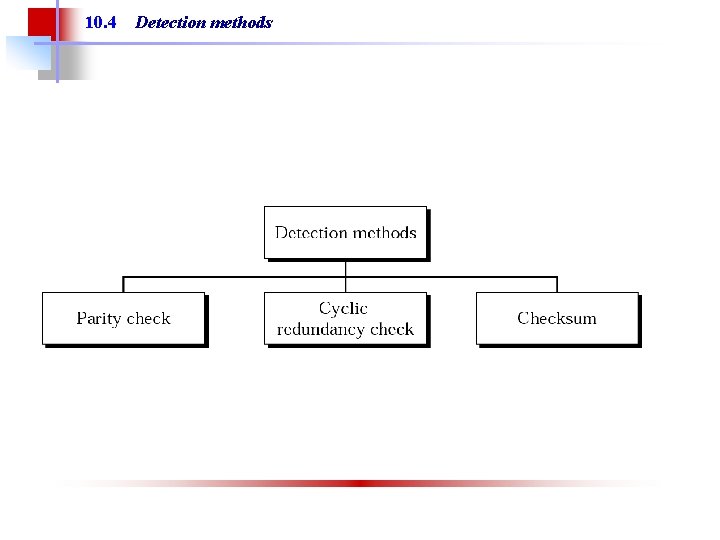
Error Detection Methods § Each method involves adding extra bits (redundant bits) to the data unit § Three most common methods are § Parity checking § Cyclic Redundancy Check (CRC) § Checksum Spring 2006 Computer Networks 12

Note: Error detection uses the concept of redundancy, which means adding extra bits for detecting errors at the destination.

10. 4 Detection methods

Parity Checking § The sender and the receiver agree in advance whether the data units will have even or odd number of 1 s. § The sender adds extra bits to create the data units according to the agreement § The receiver checks the parity of the 1 s according to the agreement. § If the data unit received has a number of 1 s according to the agreement, it is accepted as correct; otherwise it is rejected as “in error”. Spring 2006 Computer Networks 15

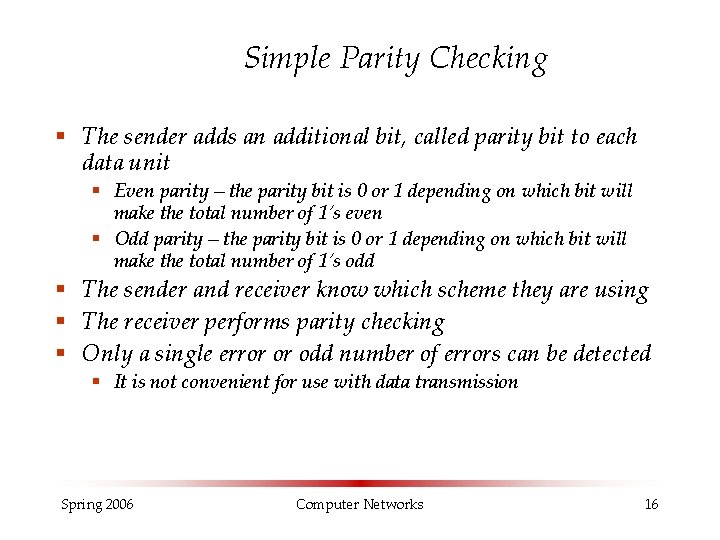
Simple Parity Checking § The sender adds an additional bit, called parity bit to each data unit § Even parity – the parity bit is 0 or 1 depending on which bit will make the total number of 1’s even § Odd parity – the parity bit is 0 or 1 depending on which bit will make the total number of 1’s odd § The sender and receiver know which scheme they are using § The receiver performs parity checking § Only a single error or odd number of errors can be detected § It is not convenient for use with data transmission Spring 2006 Computer Networks 16

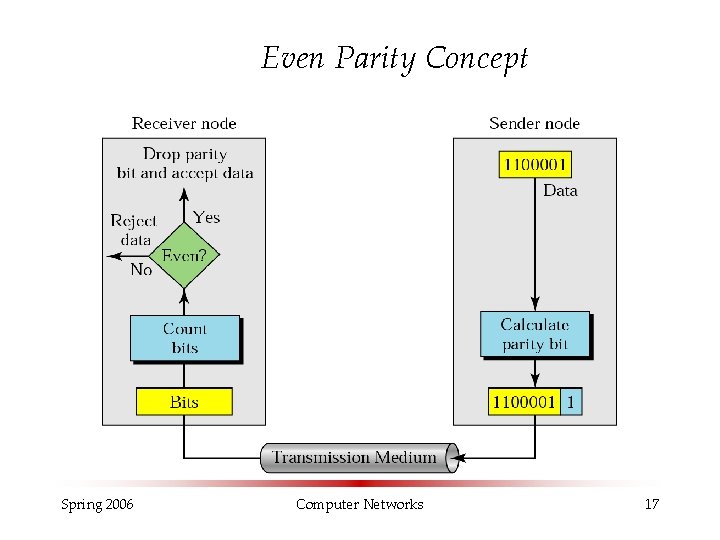
Even Parity Concept Spring 2006 Computer Networks 17

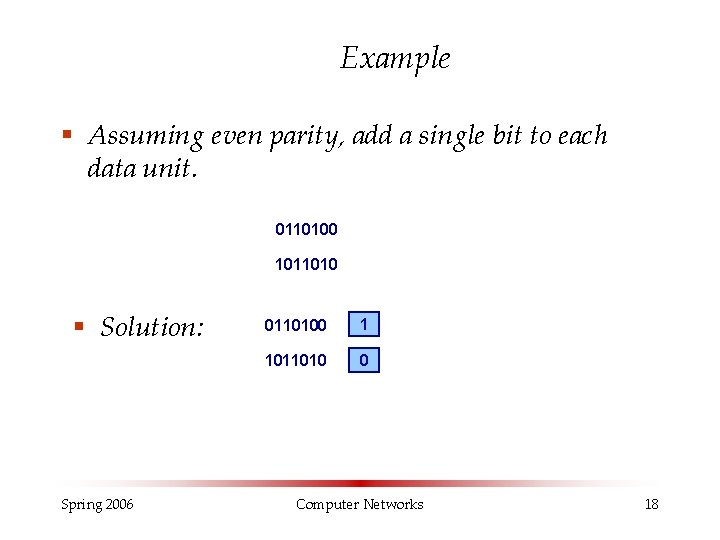
Example § Assuming even parity, add a single bit to each data unit. 0110100 1011010 § Solution: Spring 2006 0110100 1 1011010 0 Computer Networks 18

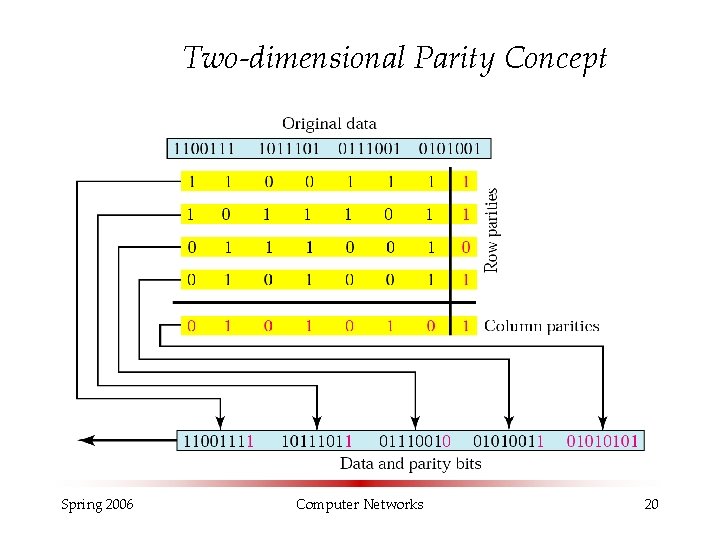
Two-dimensional Parity Check § Data units are arranged in two-dimensional array § Parity bit is added to the rows (each data unit) and to the columns (an extra data unit is created) § The receiver checks the parity in the rows and in the columns § Improved performance compared to single-parity checking § Still not very often used with data transmission Spring 2006 Computer Networks 19

Two-dimensional Parity Concept Spring 2006 Computer Networks 20

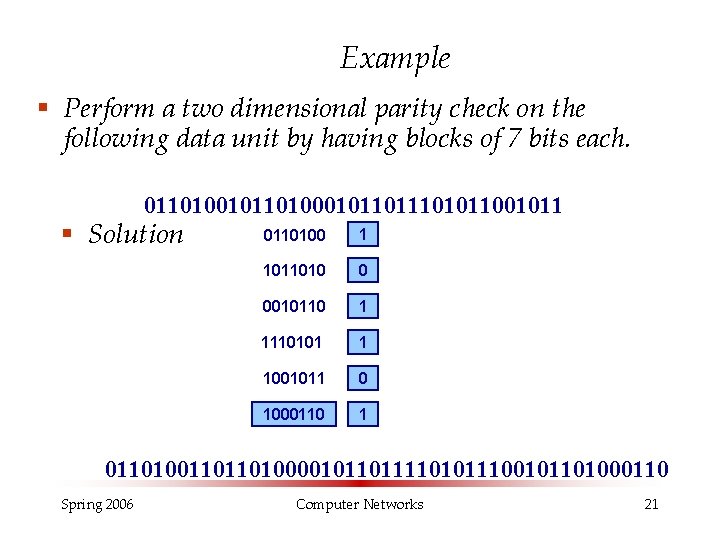
Example § Perform a two dimensional parity check on the following data unit by having blocks of 7 bits each. 0110100101101000101101011001011 § Solution 0110100 1 1011010 0 0010110 1 1110101 1 1001011 0 1000110 1 01101001101101000010110111101011100101101000110 Spring 2006 Computer Networks 21

Checksum § To compute the check sum, the sender treats the data unit as a sequence of a certain number of blocks, all with the same number of bits. § The sender and receiver agree on how long are the blocks (usually 16 bits) § The sender adds the blocks using one’s complement arithmetic and creates an additional block with the same size § The additional block is complemented and appended to the data unit as redundancy bits Spring 2006 Computer Networks 22

Checksum (Cont. ) § The receiver divides the received block into blocks with the agreed number of bits. § The blocks are added using one’s complement arithmetic § The sum is complemented § If the result is 0, the data are considered without an error, otherwise the data unit is rejected Spring 2006 Computer Networks 23

Modulo One’s Arithmetic § The addition starts at the last column from left to right § The bits are carried in the respective column before § This is repeated for each column § If the number of bits in the sum is larger then those in the blocks, they are added to the sum obtained Spring 2006 Computer Networks 24

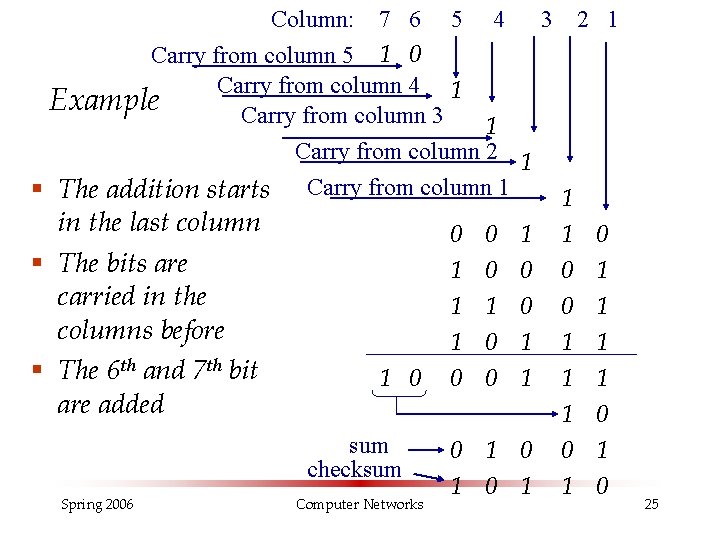
Column: 7 6 5 4 3 2 1 Carry from column 5 1 0 Carry from column 4 1 Example Carry from column 3 1 Carry from column 2 1 § The addition starts Carry from column 1 1 in the last column 0 0 1 1 0 § The bits are 1 0 0 0 1 carried in the 1 1 0 0 1 columns before 1 0 1 1 1 § The 6 th and 7 th bit 1 0 0 0 1 1 1 are added 1 0 sum 0 1 0 0 1 checksum 1 0 1 1 0 Spring 2006 Computer Networks 25

Complement of a Bit String § A complement of a bit string is obtained when all 0 s become 1 s and all 1 s become 0 s § Example: Given the bit string 10111001, its complement is 01000110 Spring 2006 Computer Networks 26

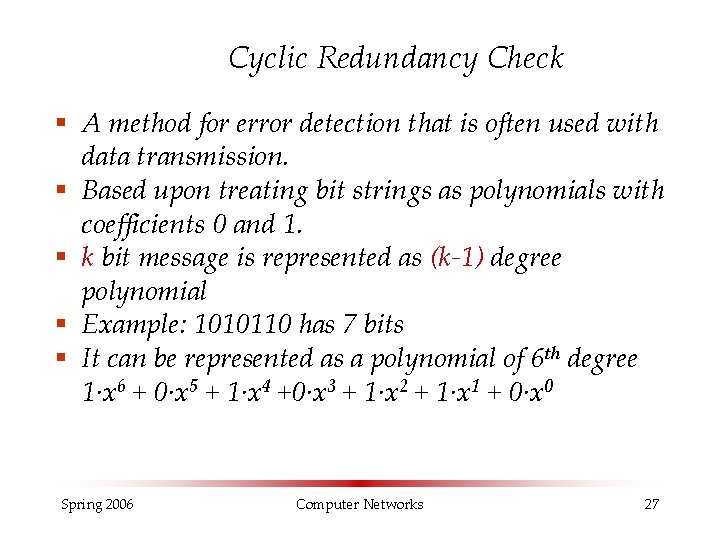
Cyclic Redundancy Check § A method for error detection that is often used with data transmission. § Based upon treating bit strings as polynomials with coefficients 0 and 1. § k bit message is represented as (k-1) degree polynomial § Example: 1010110 has 7 bits § It can be represented as a polynomial of 6 th degree 1·x 6 + 0·x 5 + 1·x 4 +0·x 3 + 1·x 2 + 1·x 1 + 0·x 0 Spring 2006 Computer Networks 27

How CRC Operates? § The sender wants to send k bits message § The sender and the receiver must agree in advance on n+1 bit string called generator polynomial (divisor), G. § G can be represented as n-degree polynomial § n redundant bits are added to the k bits message. They are called CRC bits. k bits n bits Data bits to be sent Spring 2006 CRC bits Computer Networks 28

How CRC Operates? (Cont. ) § The redundant bits are chosen in such a way that the resulting k+n bit string is exactly divisible (with a reminder=0) by G using modulo 2 arithmetic. § The receiver divides the received data together with the CRC bits by G using modulo 2 arithmetic. § If the reminder is 0, then the string is considered to be without errors § If the reminder is not 0, the data unit is with errors and it is rejected Spring 2006 Computer Networks 29

Generator Polynomial, G § For the purposes of calculating a CRC, the sender and the reciever need to agree upon a generator polynomial G in advance. § The choice of G has impact on what types of errors can be reliably detected. § There a handful generator polynomials that are very good choices for various environments and the exact choice is made as a part of protocol design Spring 2006 Computer Networks 30

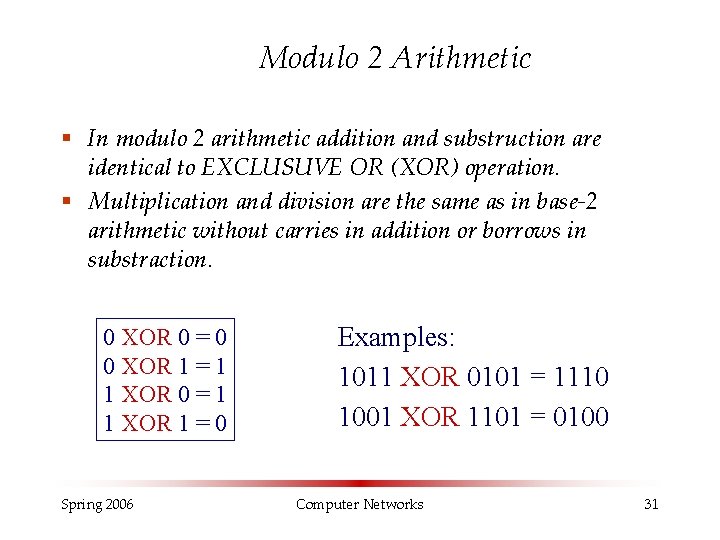
Modulo 2 Arithmetic § In modulo 2 arithmetic addition and substruction are identical to EXCLUSUVE OR (XOR) operation. § Multiplication and division are the same as in base-2 arithmetic without carries in addition or borrows in substraction. 0 XOR 0 = 0 0 XOR 1 = 1 1 XOR 0 = 1 1 XOR 1 = 0 Spring 2006 Examples: 1011 XOR 0101 = 1110 1001 XOR 1101 = 0100 Computer Networks 31

Calculating the CRC Bits § Let n be the degree of G (G consists of n+1 bits). § Append n 0 s to the data unit to obtain the extended data unit. § Perform the modulo 2 division. The extended data unit is a dividend and G is a divisor. § The quotient is not used § The reminder is the CRC bits § Add the CRC bits to the data unit Spring 2006 Computer Networks 32

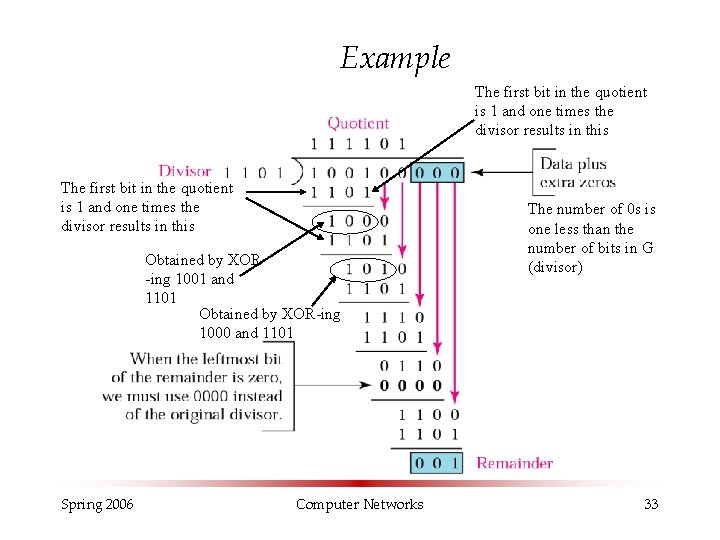
Example The first bit in the quotient is 1 and one times the divisor results in this Obtained by XOR -ing 1001 and 1101 Obtained by XOR-ing 1000 and 1101 Spring 2006 Computer Networks The number of 0 s is one less than the number of bits in G (divisor) 33

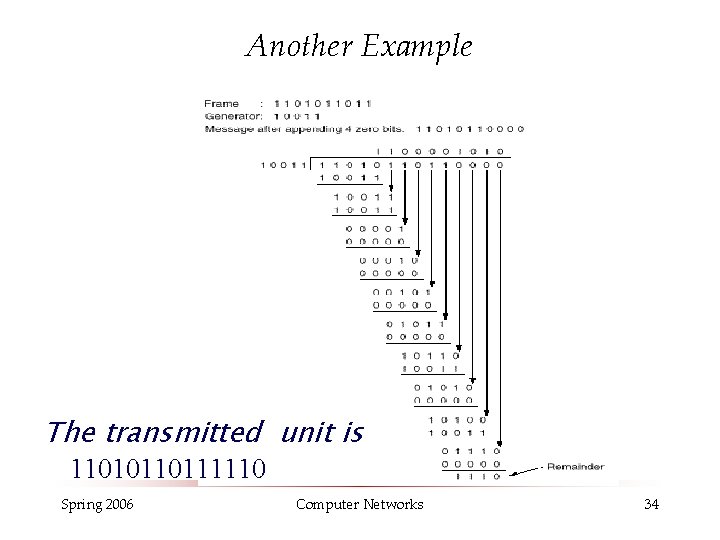
Another Example The transmitted unit is 11010110111110 Spring 2006 Computer Networks 34

CRC Performance § Assuming a good choice of the generator polynomial, G, is made, CRC method shows very good performance § Can detect all burst errors that affect odd number of bits § Can detect all burst errors of length less than or equal to G § Very high probability on detecting errors with length higher than the length of G Spring 2006 Computer Networks 35