Introduction to Network Security 1 Outline Attacks services




























- Slides: 38

Introduction to Network Security 1

Outline • • 해킹 동향 사이버 윤리 Attacks, services and mechanisms Security attacks Security services Methods of Defense A model for Internetwork Security Internet standards and RFCs 2





Virus and Worm • What is Virus? – Self-replicating code – Inserts itself into other executable code – Contains a malicious function, called payload (can be empty) – Native code which infects executable files – Distribution by Email and File sharing – Often requires a trigger from a user • e. g. execute infected application – Virus is often used as a collective term for malware 7

Trojan Horse • A destructive program that masquerades as a benign application. Unlike viruses, Trojan horses do not replicate themselves but they can be just as destructive. – A Trojan horse can be deliberately attached to otherwise useful software by a cracker, or it can be spread by tricking users into believing that it is a useful program. • The term comes from the a Greek story of the Trojan War 8

Virus and Worm • What is Worm? – First Internet worm in 1988 – Different to a virus • • Stand-alone program Does not infect an application Spreads itself through the network automatically Usually spread much faster than viruses – Worms often use exploits to propagate • SQL Slammer – MS SQL Server • Slapper - Apache/Mod-SSL • Code Red – MS Internet Information Server 9






Hacking • 해킹 기법의 변화 • 2000년대 – 분산 서비스 거부 공격(Distribute Denial Of Service) – 분산 반사 서비스 거부 공격(Distributed Reflected Denial Of Service) – 웹 해킹 15






Attacks, Services and Mechanisms • Security Attack: Any action that compromises the security of information. • Security Mechanism: A mechanism that is designed to detect, prevent, or recover from a security attack. • Security Service: A service that enhances the security of data processing systems and information transfers. A security service makes use of one or more security mechanisms. 21

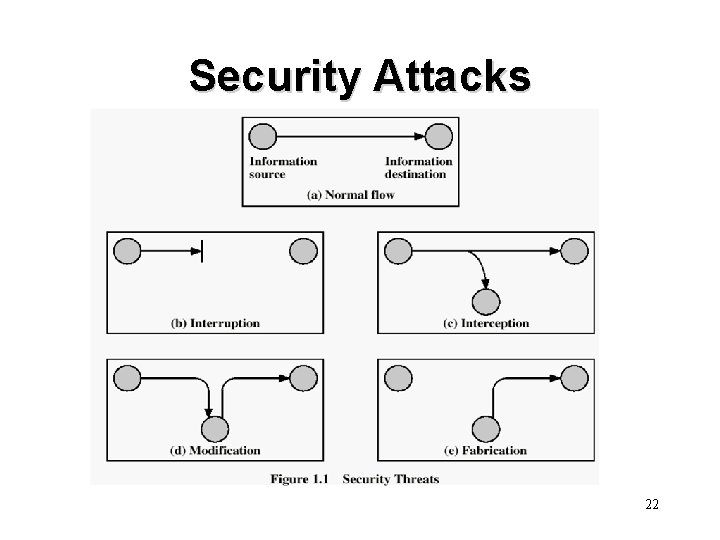
Security Attacks 22

Security Attacks • Interruption: This is an attack on availability • Interception: This is an attack on confidentiality • Modification: This is an attack on integrity • Fabrication: This is an attack on authenticity 23

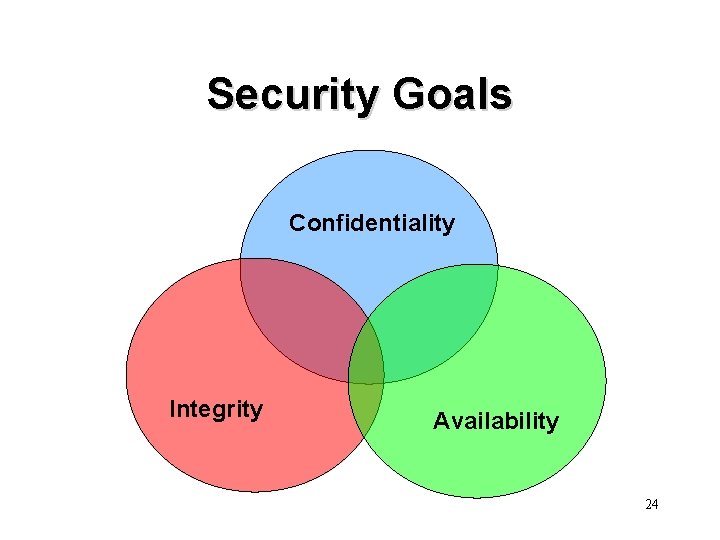
Security Goals Confidentiality Integrity Availability 24

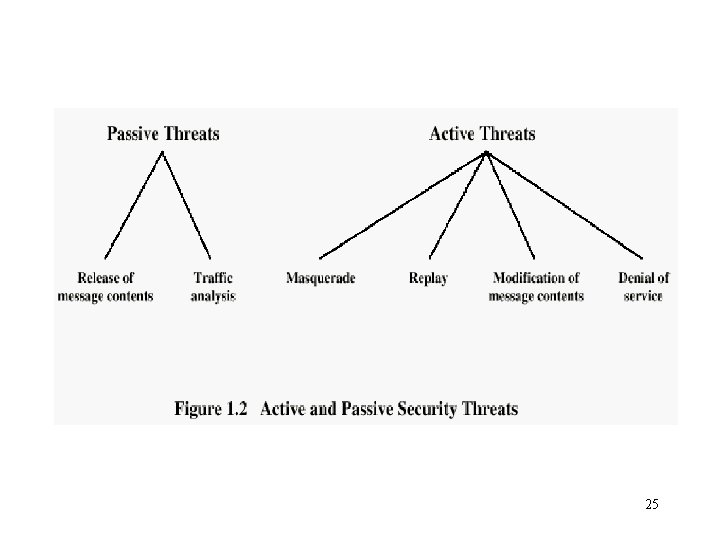
25

Passive Attacks (threats) - Release of message contents 26

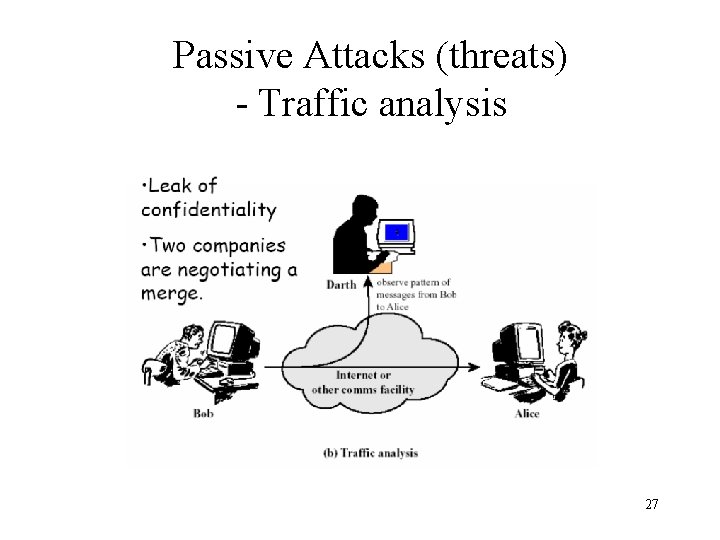
Passive Attacks (threats) - Traffic analysis 27

Active Attacks (threats) - Modification of message contents 28

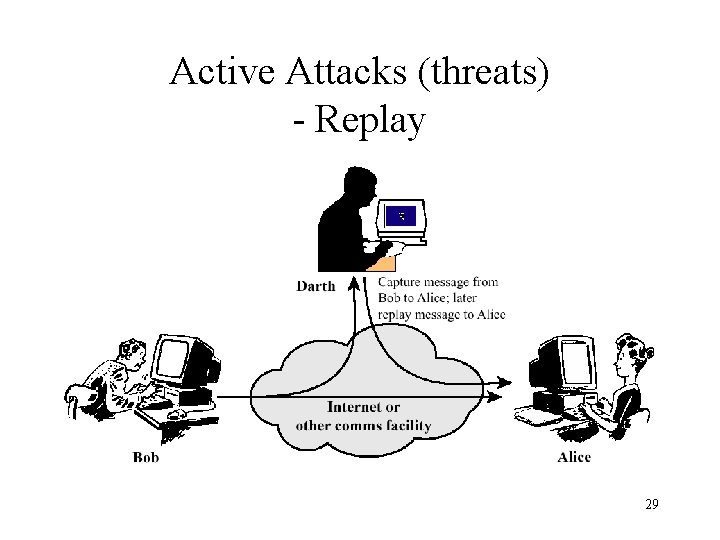
Active Attacks (threats) - Replay 29

Active Attacks (threats) - Masquerade 30

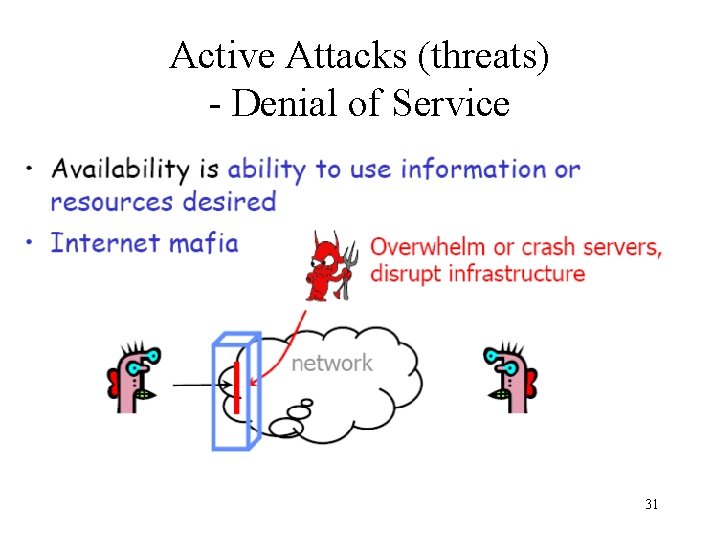
Active Attacks (threats) - Denial of Service 31

Security Services • Confidentiality (privacy) • Authentication (who created or sent the data) • Integrity (has not been altered) • Non-repudiation (the order is final) • Access control (prevent misuse of resources) • Availability (permanence, non-erasure) – Denial of Service Attacks – Virus that deletes files 32

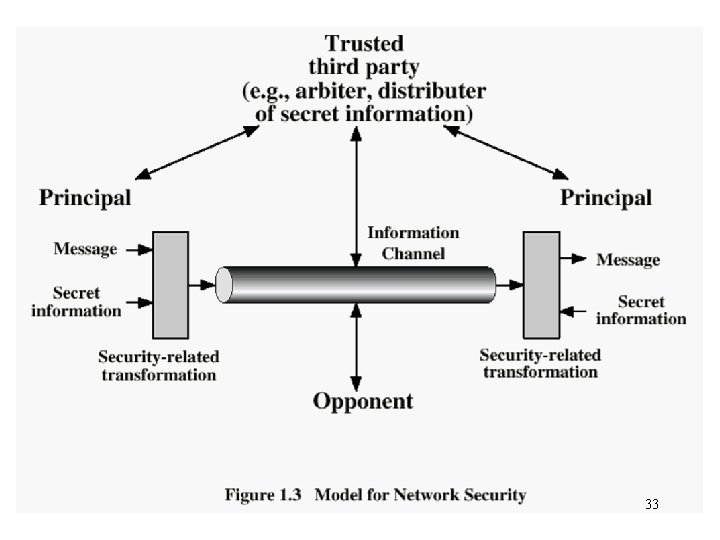
33

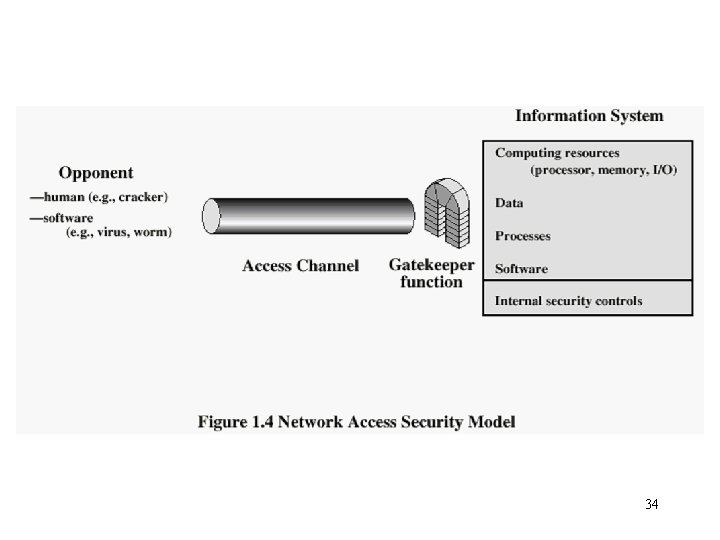
34

Methods of Defense • Encryption • Software Controls (access limitations in a data base, in operating system protect each user from other users) • Hardware Controls (smartcard) • Policies (frequent changes of passwords) • Physical Controls 35

Internet standards and RFCs • The Internet society – Internet Architecture Board (IAB) – Internet Engineering Task Force (IETF) – Internet Engineering Steering Group (IESG) 36

Internet RFC Publication Process 37

Recommended Reading • Pfleeger, C. Security in Computing. Prentice Hall, 1997. • Mel, H. X. Baker, D. Cryptography Decrypted. Addison Wesley, 2001. 38