Chapter One Introduction to Pipelined Processors Pipeline Hazards











- Slides: 17

Chapter One Introduction to Pipelined Processors

Pipeline Hazards • A pipeline hazard occurs when the pipeline must stall because some conditions do not permit continued execution. • It is also referred to as a pipeline bubble. • There are three types of hazards: resource, data and control.

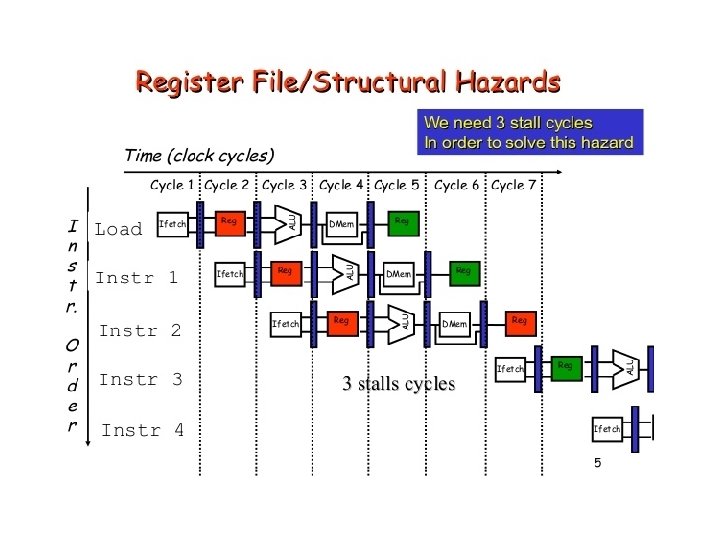
Resource Hazard • A resource hazard occurs when two or more instructions in the pipeline need the same resource.


Data Hazards • A data hazard occurs when there is a conflict in the access of an operand location. • Hazards are caused by resource usage conflicts among various instructions • They are triggered by inter-instruction dependencies

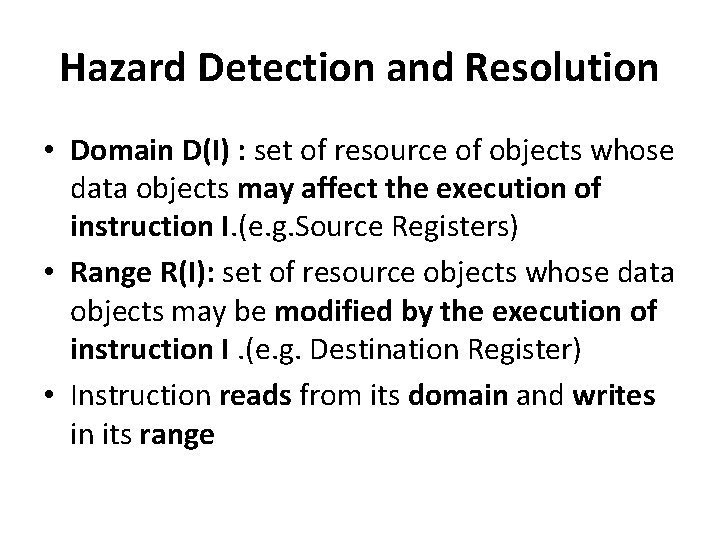
Hazard Detection and Resolution Terminologies: • Resource Objects: set of working registers, memory locations and special flags • Data Objects: Content of resource objects • Each Instruction can be considered as a mapping from a set of data objects to a set of data objects.

Hazard Detection and Resolution • Domain D(I) : set of resource of objects whose data objects may affect the execution of instruction I. (e. g. Source Registers) • Range R(I): set of resource objects whose data objects may be modified by the execution of instruction I. (e. g. Destination Register) • Instruction reads from its domain and writes in its range

Hazard Detection and Resolution • Consider execution of instructions I and J, and J appears immediately after I. • There are 3 types of data dependent hazards: 1. RAW (Read After Write) 2. WAW(Write After Write) 3. WAR (Write After Read)

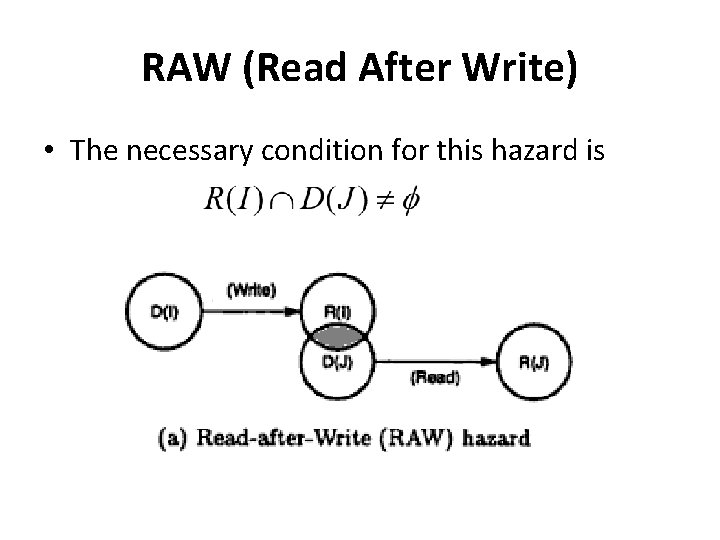
RAW (Read After Write) • The necessary condition for this hazard is

RAW (Read After Write) • Example: I 1 : LOAD r 1, a I 2 : ADD r 2, r 1 • I 2 cannot be correctly executed until r 1 is loaded • Thus I 2 is RAW dependent on I 1

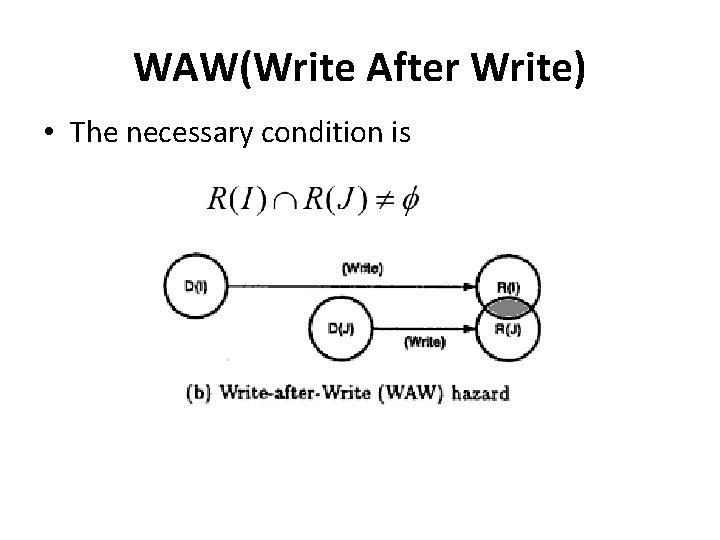
WAW(Write After Write) • The necessary condition is

WAW(Write After Write) • Example I 1 : MUL r 1, r 2 I 2 : ADD r 1, r 4 • Here I 1 and I 2 writes to same destination and hence they are said to be WAW dependent.

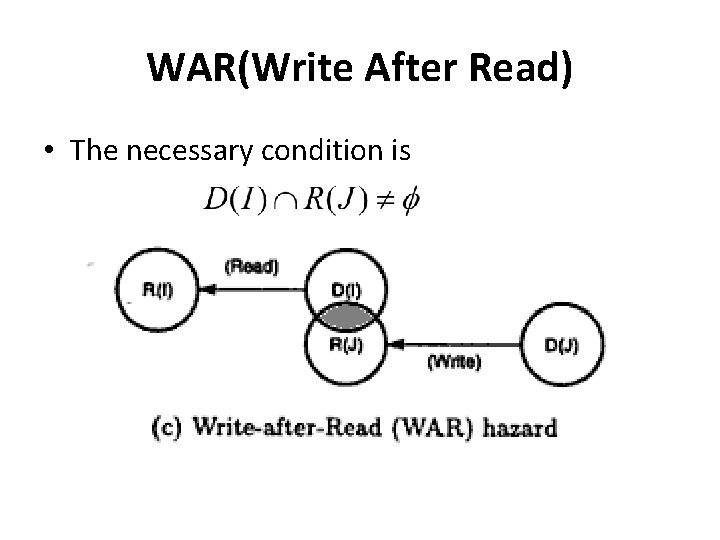
WAR(Write After Read) • The necessary condition is

WAR(Write After Read) • • Example: I 1 : MUL r 1, r 2 I 2 : ADD r 2, r 3 Here I 2 has r 2 as destination while I 1 uses it as source and hence they are WAR dependent

Hazard Detection and Resolution • Hazards can be detected in fetch stage by comparing domain and range. • Once detected, there are two methods: 1. Generate a warning signal to prevent hazard 2. Allow incoming instruction through pipe and distribute detection to all pipeline stages.

Control Hazards • Instructions that disrupt the sequential flow of control present problems for pipelines. • The following types of instructions can introduce control hazards: – Unconditional branches. – Conditional branches. – Indirect branches. – Procedure calls. – Procedure returns.

Solutions for Control Hazards • The following are solutions that have been proposed for mitigating control hazards: – Pipeline stall cycles: Freeze the pipeline until the branch outcome and target are known, then proceed with fetch. – Branch delay slots: The compiler must fill these branch delay slots with useful instructions or NOPs – Branch prediction.