The open source network intrusion detection system Secure












- Slides: 27

The open source network intrusion detection system. Secure System Administration & Certification Ravindra Pendyala

The main distribution site for Snort is http: //www. snort. org v IDS & History of Snort v What is Snort? v Features of Snort v Snort Modes v Compiling & Installing Snort v Snort Rules v Snort in different Modes v Using Snort v Third Party Enhancements v Conclusion

Intrusion: An intrusion is somebody (A. K. A. "hacker" or "cracker") attempting to break into or misuse your system. NIDS: network intrusion detection systems (NIDS) monitors packets on the network wire and attempts to discover if a hacker/cracker is attempting to break into a system (or cause a denial of service attack).

Martin Roesch is the founder and CTO of Sourcefire, Inc. NIDS & History of Snort. . . Snort was a true case of a programmer scratching his own itch. Here was Marty Roesch with his home network, wanting to see who, if anyone, was trying to penetrate it. This was a small and simple detection system for home use Initial Release on Dec 22 1998 - snort-0. 96. tar. gz Latest Release on Oct 3 - snort-1. 9. 0. tar. gz

Snort does NOT block intruders. Assumes a human is watching!!! What is Snort? Snort is a lightweight network intrusion detection system, capable of performing real-time traffic analysis and packet logging on IP networks. It can perform protocol analysis, content searching/matching and can be used to detect a variety of attacks and probes, such as buffer overflows, stealth port scans, CGI attacks, SMB probes, OS fingerprinting attempts, and much more. Snort uses a flexible rules language to describe traffic that it should collect or pass, as well as a detection engine that utilizes a modular plugin architecture. Snort has a real-time alerting capability as well, incorporating alerting mechanisms for syslog, a user specified file, a UNIX socket, or Win. Popup messages to Windows clients using Samba's smbclient.

Snort in simple words … • Automated tool to detect intrusions • Works locally (reactionary) or network wide (preemptive) • Preemptive IDS can use traffic monitoring or content monitoring • Does NOT block intruders. Assumes a human is watching!!!

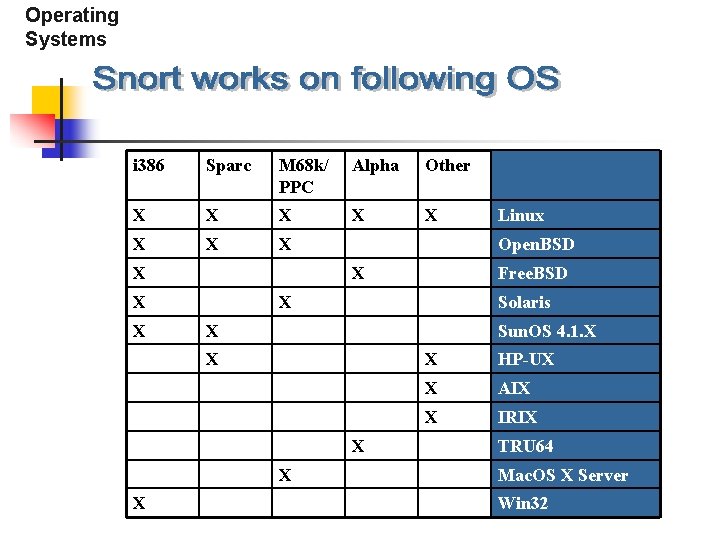
Operating Systems i 386 Sparc M 68 k/ PPC Alpha Other X X X X X Open. BSD X X Free. BSD X Solaris X Sun. OS 4. 1. X X X Linux X HP-UX X AIX X IRIX TRU 64 Mac. OS X Server Win 32

• “Lightweight” • Free • Portable • Runs on HP-UX, Linux, AIX, Irix, *BSD, Solaris, Win 2 K • Configurable with easy setup

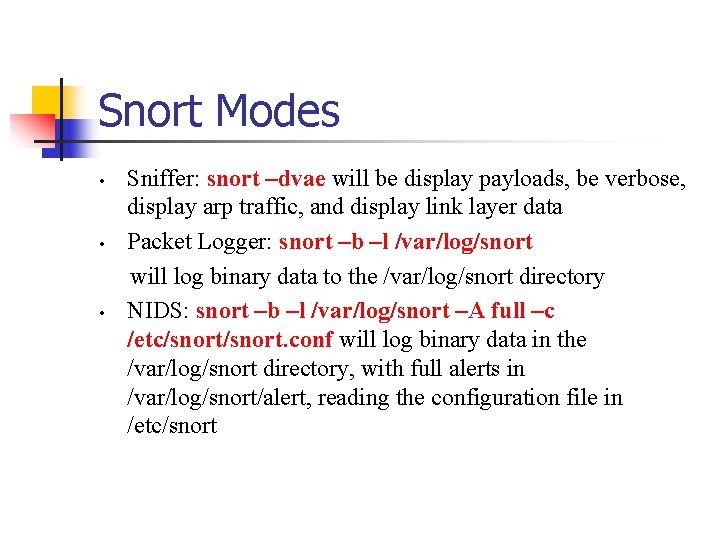
Snort Modes • Packet sniffer • Packet Logger • Preemptive IDS - Actively monitors network traffic in real time to match intrusion signatures and send alerts

On Red Hat Linux 7. 2, as root: • Download and install libpcap • Download and install these three. rpm: libnet-1. 0. 2 a-1 snort. i 386. rpm snort-1. 8. 4 -1 snort. i 386. rpm snort-postgresql+flexresp-1. 8. 4 -1 snort. i 386. rpm Create /var/log/snort directory

Files installed: • /etc/snort contains conf and rule files • /var/log/snort will contain logs • /usr/sbin/snort contains snort binary • For a quick test, execute this command within the /etc/snort directory: snort –A console • From a separate machine, use nmap to generate events for Snort to detect: nmap –s. P <snort_machine_IP_address>

Installing on Windows 2000 • Download and install winpcap • Download & execute Snort 184 Win 32. exe, select “typical” installation • mkdir “c: Program FilesSourcefireSnortlog” Files installed in c: Program FilesSourcefireSnort: • snort. conf • rules directory contains rules • Snort. executable

Installing Snort To test, execute this command FilesSourcefireSnort directory: within the c: Program • snort –A console From a separate machine, use nmap to generate events for Snort to detect: • nmap –s. P <snort_machine_IP_address> You should see an alert like this: 03/27 -15: 18: 06. 911226 [**] [1: 469: 1] ICMP PING NMAP [**] [Classification: Attempted Information Leak] [Priority: 2] {ICMP} 129. 244. 70. 17 -> 129. 244. 70. 237

Snort rules are extremely flexible and are easy to modify, unlike many commercial NIDS • Sample rule alert udp $EXTERNAL_NET 53 -> $HOME_NET : 1024 (msg: "MISC source port 53 to <1024"; ) Rule alerts that anything from the external network coming in from port 53 and going to port 1024 should be flagged

• Elements before parentheses comprise ‘rule header’ • Elements in parentheses are ‘rule options’ • Rules can: Alert, Log, or Pass • Used for IP, UDP, ICMP • Source address / port • Destination address / port • Additional options - This is where content matching can take place

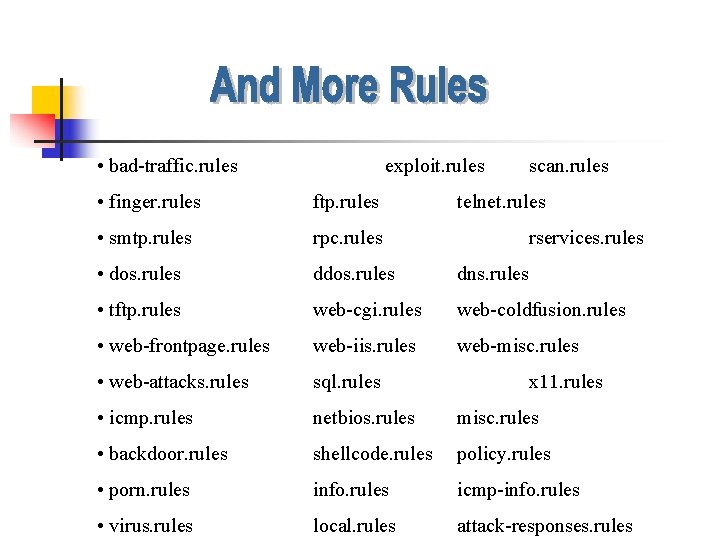
• bad-traffic. rules exploit. rules scan. rules • finger. rules ftp. rules • smtp. rules rpc. rules • dos. rules dns. rules • tftp. rules web-cgi. rules web-coldfusion. rules • web-frontpage. rules web-iis. rules web-misc. rules • web-attacks. rules sql. rules • icmp. rules netbios. rules misc. rules • backdoor. rules shellcode. rules policy. rules • porn. rules info. rules icmp-info. rules • virus. rules local. rules attack-responses. rules telnet. rules rservices. rules x 11. rules

Luckily you probably won’t have to write rules!

Snort Modes • • • Sniffer: snort –dvae will be display payloads, be verbose, display arp traffic, and display link layer data Packet Logger: snort –b –l /var/log/snort will log binary data to the /var/log/snort directory NIDS: snort –b –l /var/log/snort –A full –c /etc/snort. conf will log binary data in the /var/log/snort directory, with full alerts in /var/log/snort/alert, reading the configuration file in /etc/snort

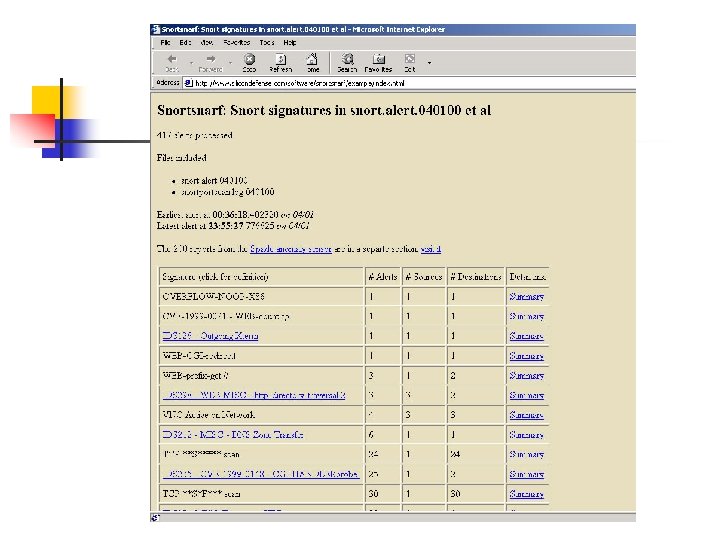
Snort. Snarf www. silicondefense. com/software/snortsnarf/ • Snort. Snarf is a Perl program to take files of alerts from the Snort to produce HTML reports • Output intended for diagnostic inspection • Silicon Defense also supplies sensors with commercial support • Description and screenshot taken from Snort. Snarf web


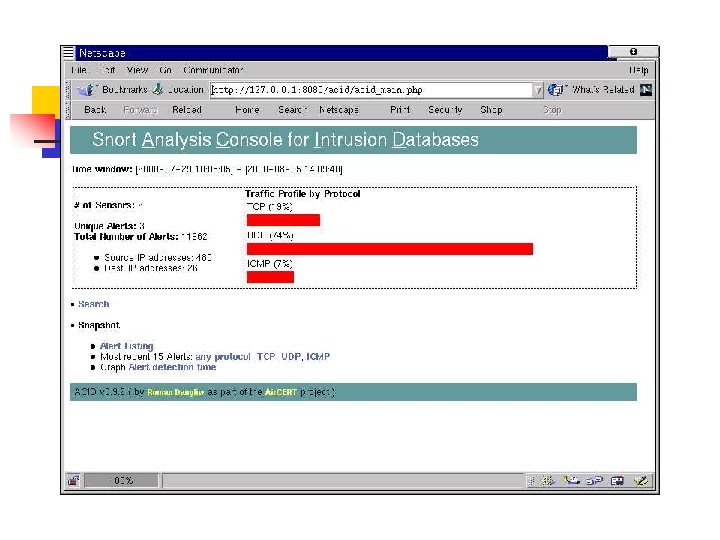
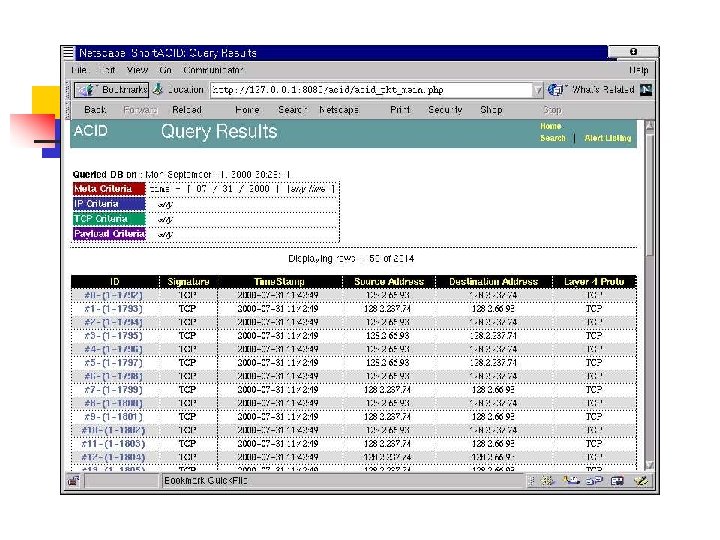
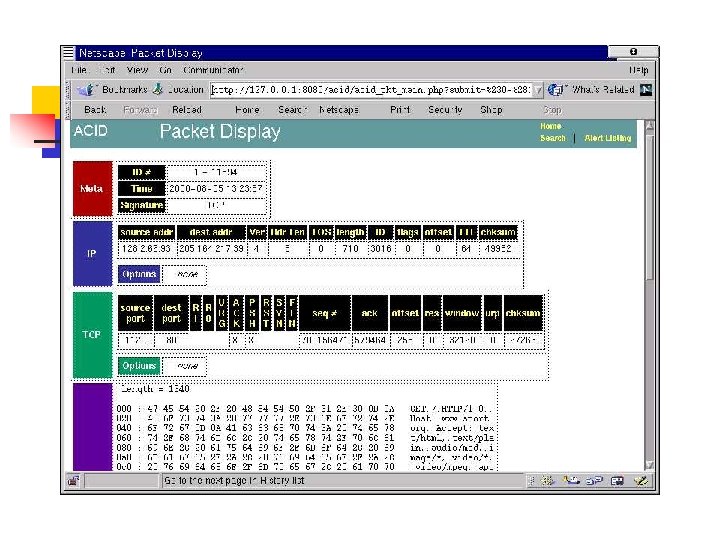
Analysis Console for Intrusion Databases (ACID) • acidlab. sourceforge. net/ • PHP-based analysis engine to search and process a database of security events generated by various IDSes, firewalls, and network monitoring tools • Query-builder and search interface, packet viewer (decoder), alert management, chart and statistics generation. • Description and screenshots taken from ACID web




Conclusions n n Snort is a powerful tool, but maximizing its usefulness requires a trained operator Snort is considered a superior NIDS when compared to most commercial systems Snort is a wonderful low to no cost solution for businesses. Snort, written in C, can compile and run on variety of different Operating Systems.

Snort. org Securityfocus. com Whitehats. com

Questions?