HONEYPOTS An Intrusion Detection System Index Intrusion Detection








- Slides: 17

HONEYPOTS An Intrusion Detection System

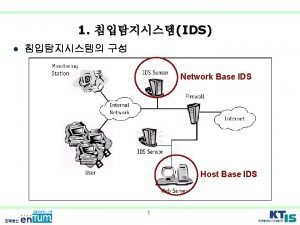
Index • Intrusion Detection System • Host bases Intrusion Detection System • Network Based Intrusion Detection System • Honeypot • Motivation behind Honeypot • Working and Configuration • Advantages of Honeypots • Feasibility • Conclusion

Intrusion Detection System • What is IDS? • History • Hey wait a minute doesn’t Firewall do the same thing? • Types of IDS

Host based intrusion Detection System • Monitoring the System • Techniques • How to fool HIDS?

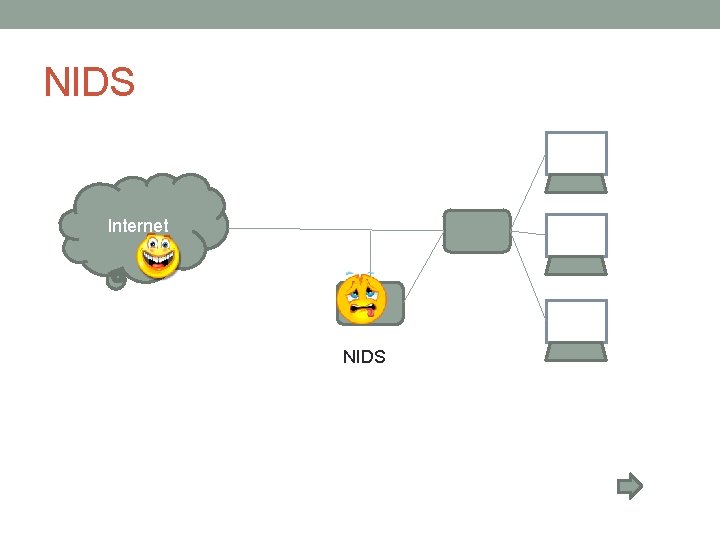
Network Based Intrusion Detection System • Monitoring the Network -> • How to fool NIDS?

NIDS Internet NIDS

Why do we need Honeypots? • The Magic word that solves most of the worlds problems : “INFORMATION” • Doesn't HIDS and NIDS do the same thing, then why Honeypot? -> • OH!, That is why we need Honeypots ->

What are the problems in other IDS • Large Dataset problem • Not all attacks are detected • False positive and false negative problem • Time factor <-

So what is Honeypot? • A honeypot is an information system resource whose value lies in unauthorized or illicit use of that resource. • Basic Idea ->

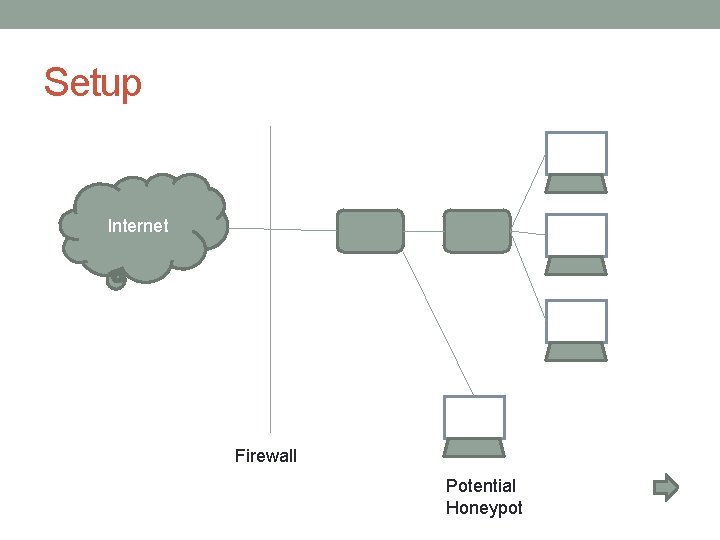
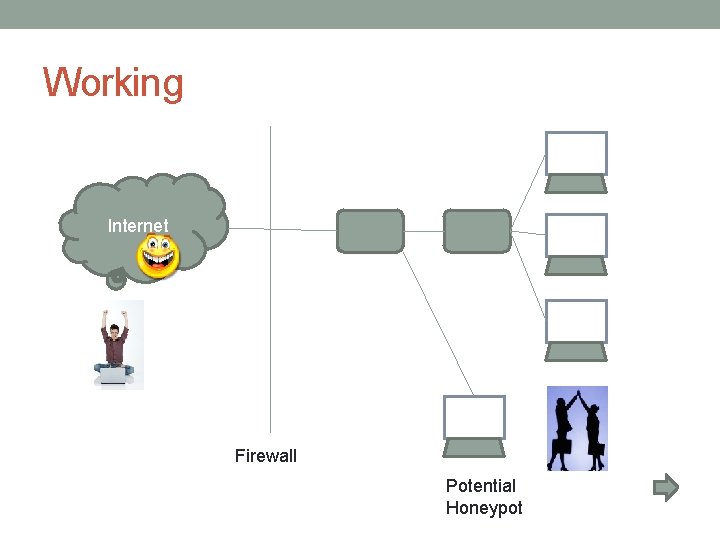
Basic Idea • Setup -> • Working ->

Setup Internet Firewall Potential Honeypot

Working Internet Firewall Potential Honeypot

Working and Configuration • Rerouting System log files • Dummy log files • Network packet sniffing • Monitoring system binaries

Advantages and Disadvantages • Advantages: • easily determine exploit being used • allows administrators to patch systems accordingly • protect production systems from attacks • Disadvantages: • Extra overhead costs • Extra hardware/man hours • Legal issues

Well known packages used to create Honeypot • Commercial honeypots • Cyber. Cop Sting • Man. Trap • Deception Tool Kit • Other Packages • Tripwire • INTACT • INTEGRIT • SAMHAIN • SIDEKICK

Feasibility • With proper knowledge, not too difficult to set up • Does require some extra hardware • Does require some extra man hours to monitor system

Conclusion • Honeypots are a good option for network security • More overhead cost and work to maintain • The future of Honeypots
 Honeypots and honeynets
Honeypots and honeynets Nids open source
Nids open source Bro ids hardware requirements
Bro ids hardware requirements Common intrusion detection framework
Common intrusion detection framework L
L Firewalls and intrusion detection systems
Firewalls and intrusion detection systems Fiber optic perimeter intrusion detection systems
Fiber optic perimeter intrusion detection systems Infrasonic intrusion detection
Infrasonic intrusion detection Wireless intrusion prevention system
Wireless intrusion prevention system Configure ios intrusion prevention system (ips) using cli
Configure ios intrusion prevention system (ips) using cli Ips intrusion
Ips intrusion Diff between step index and graded index fiber
Diff between step index and graded index fiber Dense secondary index
Dense secondary index Lepromin test ppt
Lepromin test ppt Limitations of pqli
Limitations of pqli Mode theory of circular waveguide
Mode theory of circular waveguide Simpsons evenness
Simpsons evenness Consistency limits and indices
Consistency limits and indices