The OSI Security Architecture Network Security 1 The












- Slides: 17

The OSI Security Architecture Network Security 1

The OSI Security Architecture Objectives of the Topic • After completing this topic, a student will be able to – describe the OSI security architecture and its usefulness. 2

The OSI Security Architecture Figures and material in this topic have been • adapted from “Network Security Essentials: Applications and Standards”, 2014, by William Stallings. 3

The OSI Security Architecture • In an organization, the manager responsible for security has to effectively assess the security needs of an organization. • He has to evaluate and choose various security products and policies. 4

The OSI Security Architecture • Thus, the manager needs some systematic way of defining the requirements for security and characterizing the approaches to satisfying those requirements. 5

The OSI Security Architecture • This is difficult enough in a centralized data processing environment. • With the use of local and wide area networks, the problems are compounded. 6

The OSI Security Architecture • Such a systematic approach was defined by the International Telecommunication Union (ITU) Telecommunication Standardization Sector (ITU-T). 7

The OSI Security Architecture • (ITU-T) is a United Nations sponsored agency that develops standards, called Recommendations, relating to telecommunications and to open systems interconnection (OSI). 8

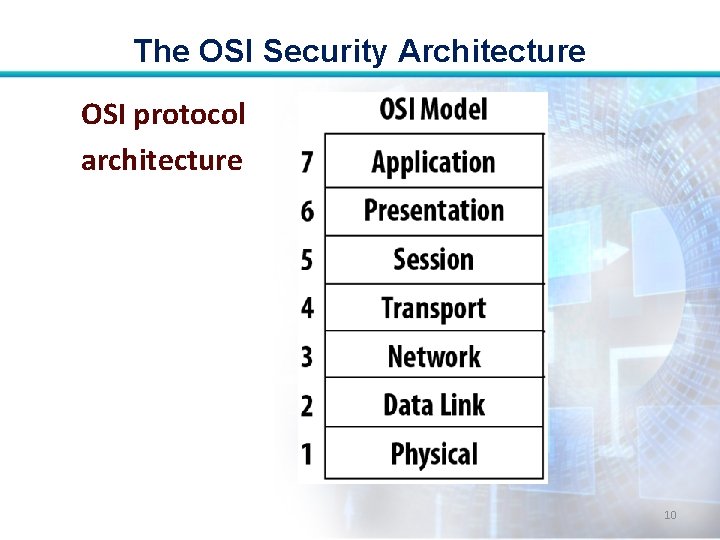
The OSI Security Architecture • Recommendation X. 800, Security Architecture for OSI. • The open systems interconnection (OSI) security architecture was developed in the context of the OSI protocol architecture. 9

The OSI Security Architecture OSI protocol architecture 10

The OSI Security Architecture • The OSI security architecture is useful to managers as a way of organizing the task of providing security. • It focuses on security attacks, mechanisms, and services. • These are defined next: 11

The OSI Security Architecture Security Attack: • Any action that compromises the security of information owned by an organization. 12

The OSI Security Architecture Security Mechanism: • A process (or a device incorporating such a process) that is designed to detect, prevent, or recover from a security attack. 13

The OSI Security Architecture Security Service: • A processing or communication service that enhances the security of the data processing systems and the information transfers of an organization. 14

The OSI Security Architecture • The services are intended to counter security attacks, and they make use of one or more security mechanisms to provide the service. 15

The OSI Security Architecture RFC 4949, Internet Security Glossary. 16

The OSI Security Architecture End • The OSI architecture is an international standard, computer and communications vendors have developed security features for their products and services that relate to this structured definition of services and mechanisms. 17