Introduction Components of computer security Threats Policies and












- Slides: 23

Introduction Components of computer security Threats Policies and mechanisms Operational Issues Human Issues

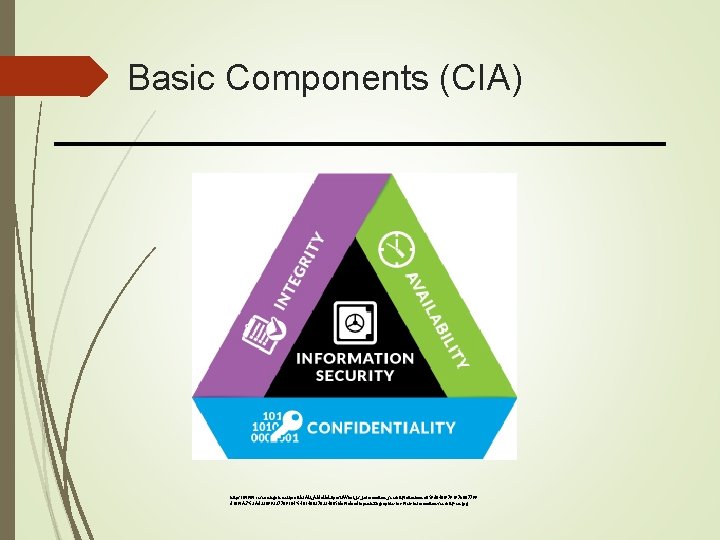
Basic Components (CIA) https: //www. researchgate. net/profile/Ali_Aldallal 2/post/What_is_information_security/attachment/59 d 640 f 979197 b 807799 d 189/AS%3 A 433099327709184%401480270334665/download/opentext-graphic-for-web-information-security-en. jpg

CONFIDENTIALITY https: //encrypted-tbn 0. gstatic. com/images? q=tbn: ANd 9 Gc. QMry 15 l. Pb 2 Qs. US 1 e. PX-y 3 b 7 VD 4 k 0 Bxyc. ODp. K 8 oxg 2 Ln 8_I 7 k. W 1

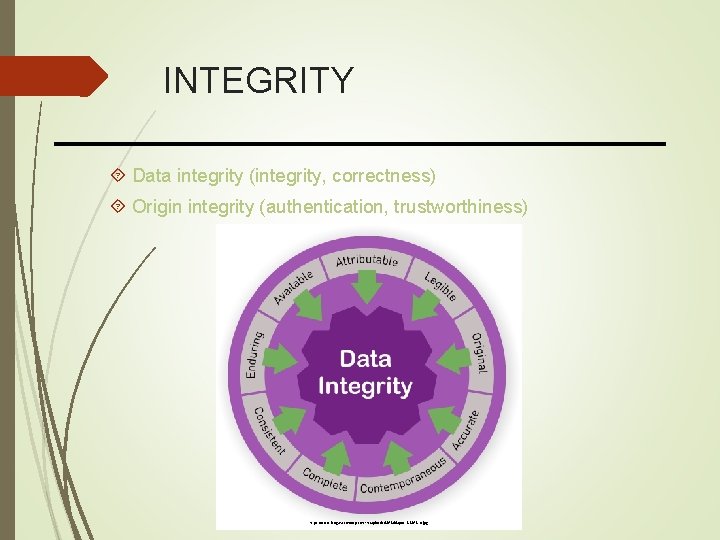
INTEGRITY Data integrity (integrity, correctness) Origin integrity (authentication, trustworthiness) https: //www. labguru. com/wp-content/uploads/2018/08/post-8 -2018 -b. jpg

DATA INTEGRITY Data integrity (integrity, correctness) https: //images-na. ssl-images-amazon. com/images/I/81 d. Cr. Vjgrb. L. _SL 1500_. jpg

ORIGIN INTEGRITY Origin integrity (authentication, trustworthiness)

AVAILABILITY https: //www. blackmoreops. com/wp-content/uploads/2015/10/Free-DOS-Attack-Tools-Do. S-attack-black. MORE-Ops. jpg

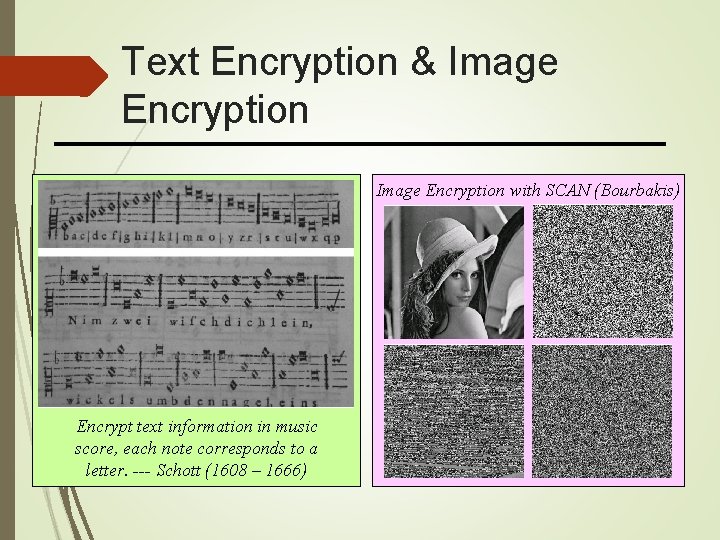
Text Encryption & Image Encryption with SCAN (Bourbakis) Encrypt text information in music score, each note corresponds to a letter. --- Schott (1608 – 1666)

Information Hiding - Examples APPARENTLY NEUTRAL’S PROTEST IS THOROUGHLY DISCOUNTED AND IGNORED. ISMAN HARD HIT. BLOCKADE ISSUE AFFECTS PRETEXT FOR EMBARGO ON BY-PRODUCTS, EJECTING SUETS AND VEGETABLE OILS. A message sent by a spy in World War II. PERSHING SAILS FROM NY JUNE 1. Extract the second letter from each word.

Information Hiding - Examples (Maniccam & Bourbakis)

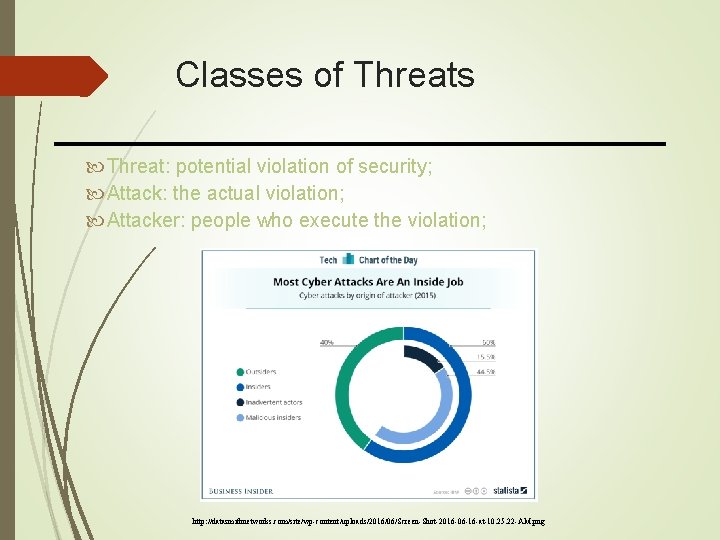
Classes of Threats Threat: potential violation of security; Attack: the actual violation; Attacker: people who execute the violation; http: //datasmithnetworks. com/site/wp-content/uploads/2016/06/Screen-Shot-2016 -06 -16 -at-10. 25. 22 -AM. png

Classes of Threats Disclosure Deception Disruption Usurpation

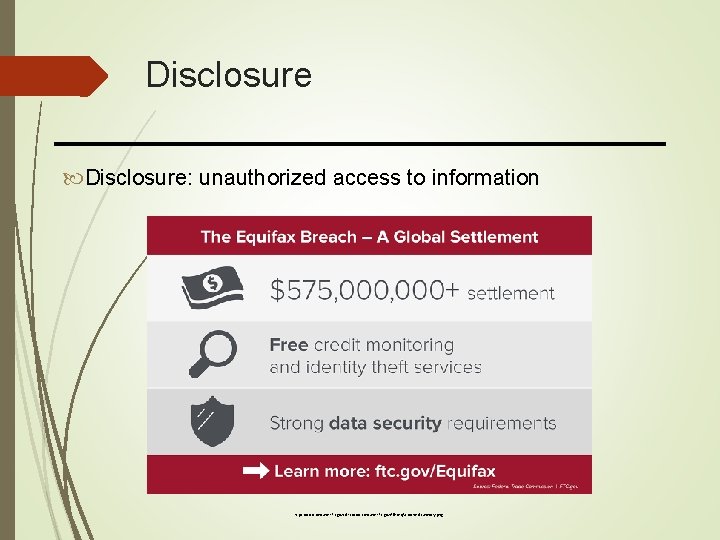
Disclosure: unauthorized access to information https: //www. consumer. ftc. gov/sites/www. consumer. ftc. gov/files/eqfx-socmed-summary. png

Deception: acceptance of false data https: //www. naturalnews. com/wp-content/uploads/sites/91/2018/12/Fake-News-Fact-Truth-Myth-Rumor-Fiction. jpg

Disruption: interruption or prevention of correct operation https: //static 01. nyt. com/images/2017/12/18/us/18 xp-airport 4 -article. Large. jpg? quality=75&auto=webp&disable=upscale

Usurpation: unauthorized control of a part of a system http: //creditfraudalert. org/wp-content/id-theft-protection/2019/05/usurpation-didentite. png

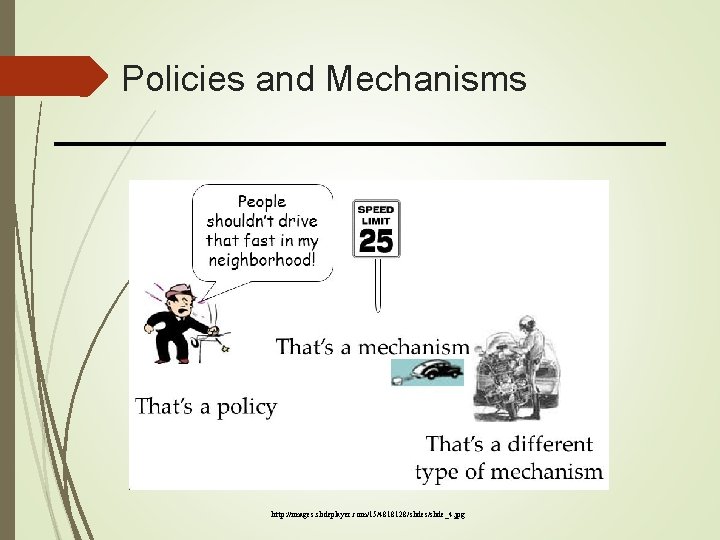
Policies and Mechanisms http: //images. slideplayer. com/15/4818128/slides/slide_4. jpg

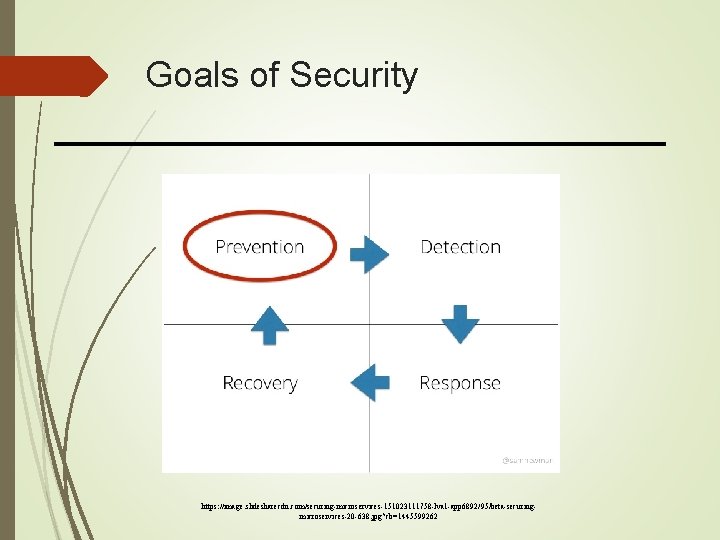
Goals of Security https: //image. slidesharecdn. com/securing-microservices-151023111758 -lva 1 -app 6892/95/beta-securingmicroservices-20 -638. jpg? cb=1445599262

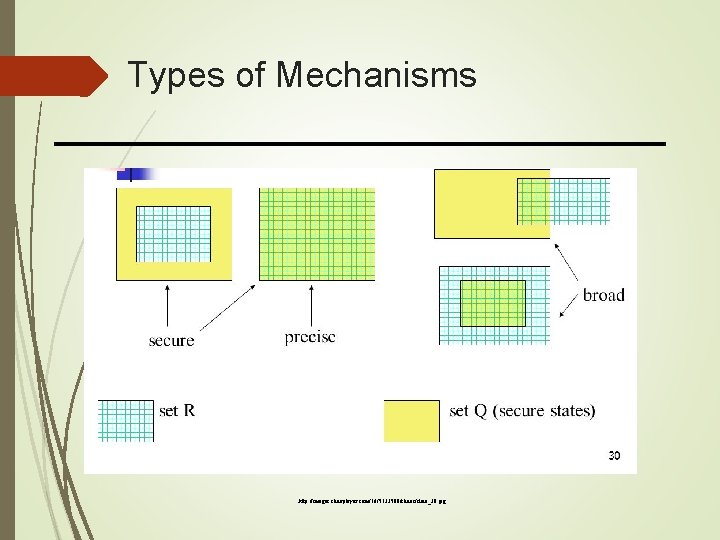
Types of Mechanisms http: //images. slideplayer. com/16/5133500/slides/slide_30. jpg

Assurance Assurance: the basis for specifying how much one can trust a system; it includes specification, design, and implementation; Specification Formal statement of desired functionality Requirements analysis Design Translates specifications into components that will implement them; How system will meet specification Implementation Create a system that satisfies the design; Programs/systems that carry out design;

Operational Issues Cost-Benefit Analysis Is it cheaper to prevent or recover? Risk Analysis Should we protect something? How much should we protect this thing? The level of protection is a function of the probability of an attack occurring and the effects of the attack should it succeed; Laws and Customs Are desired security measures illegal? Will people do them?

Human Issues Organizational Problems Security provides no direct financial rewards to the user; Responsibility without power causes problems; Lack of trained people or lack of resource; Financial benefits of security is not much; People problems Insiders could be more dangerous than an outsider; Untrained personnel could cause problems;

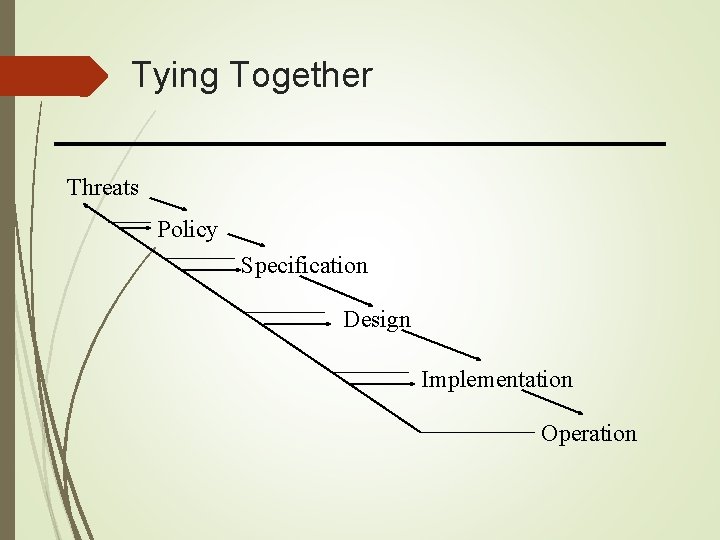
Tying Together Threats Policy Specification Design Implementation Operation
 Most common computer security threats
Most common computer security threats Wireless security threats and vulnerabilities
Wireless security threats and vulnerabilities Cyber security threats and countermeasures
Cyber security threats and countermeasures Security program and policies principles and practices
Security program and policies principles and practices Security program and policies principles and practices
Security program and policies principles and practices Security program and policies principles and practices
Security program and policies principles and practices Security program and policies principles and practices
Security program and policies principles and practices Security program and policies principles and practices
Security program and policies principles and practices Ccna security chapter 1
Ccna security chapter 1 Ecommerce security threats
Ecommerce security threats Wireless security threats
Wireless security threats Security security security
Security security security Components of computer security
Components of computer security Components of computer security
Components of computer security Components of computer security
Components of computer security Components of computer security
Components of computer security Basic components of computer security
Basic components of computer security Components of computer security
Components of computer security Components of computer security
Components of computer security Components of computer security
Components of computer security Components of computer security
Components of computer security Database security policy
Database security policy Types of security policies
Types of security policies Introduction to computer security
Introduction to computer security