Overview q Important components of computer security o

















- Slides: 56

Overview q Important components of computer security: o User authentication – determine the identity of an individual accessing the system o Access control policies – stipulate what actions a given user is allowed to perform on the system o Access control mechanisms – enforce the system’s access control policy Chapter 7 Computer Security 1

The Reference Monitor q Computer systems are comprised of many diverse objects that can be employed by users to accomplish tasks o Examples: CPU, memory segments, files, printers, etc. q q It is the job of a reference monitor to control access to system objects The reference monitor must: o Operate correctly o Always be invoked o Be tamper-proof Decisions on whether or not to allow an action are based on the identity of the user performing the action Chapter 7 Computer Security 2 q

Authorization q q Authorization entails determining whether or not the protection policy permits a given user to perform a given action Example: o Badges at a military installation q Many operating systems base authorization decisions on a user’s unique user identifier (or uid): o User is authenticated during log on and given an appropriate uid § Must enter valid username and password o The uid is used to determine which actions are authorized Chapter 7 Computer Security 3

User Authentication q Three basic approaches: o Knowledge-based – users prove their identity through something that they know § Example: passwords o Token-based – users prove their identity through something they possess § Example: passport o Biometric – users prove their identity through a unique physiological characteristic § Example: fingerprint Chapter 7 Computer Security 4

Passwords are widely-used for user authentication q Advantages: q o Easy to use, understood by most users o Require no special equipment o Offer an adequate degree of security in many environments q Disadvantages: o Users tend to choose passwords that are easy to guess o Many password-cracking tools are available Chapter 7 Computer Security 5

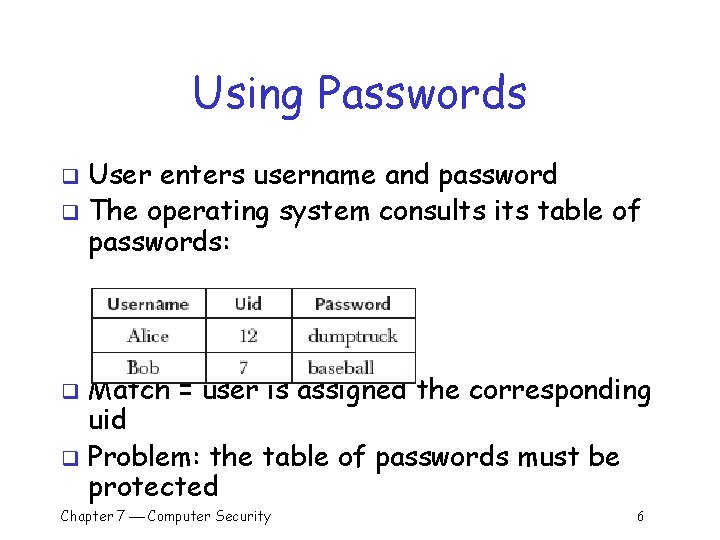
Using Passwords User enters username and password q The operating system consults its table of passwords: q Match = user is assigned the corresponding uid q Problem: the table of passwords must be protected q Chapter 7 Computer Security 6

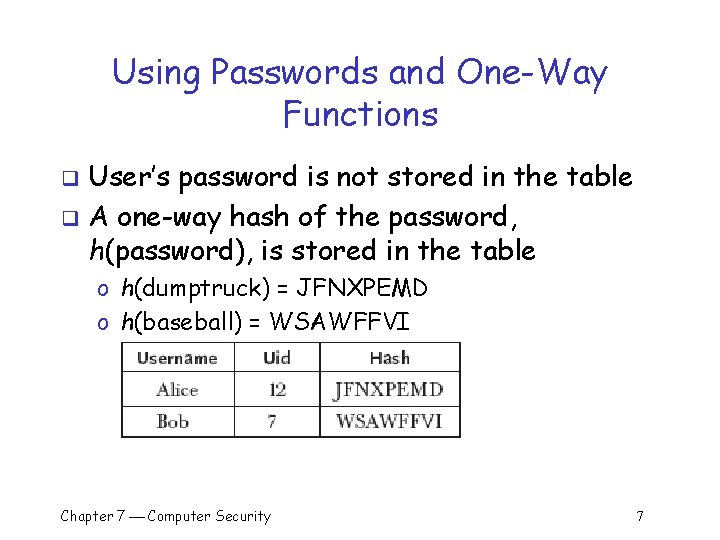
Using Passwords and One-Way Functions User’s password is not stored in the table q A one-way hash of the password, h(password), is stored in the table q o h(dumptruck) = JFNXPEMD o h(baseball) = WSAWFFVI Chapter 7 Computer Security 7

Using Passwords and One-Way Functions (cont) User enters username and password q The operating system hashes the password q The operating system compares the result to the entry in the table q Match = user is assigned the corresponding uid q Advantage: password table does not have to be protected q Disadvantage: dictionary attack q Chapter 7 Computer Security 8

A Dictionary Attack q q An attacker can compile a dictionary of several thousand common words and compute the hash for each one: Look for matches between the dictionary and the password table o Example: WSAWFFVI tells us Bob’s password is baseball Chapter 7 Computer Security 9

Dictionary Attacks (cont) q Dictionary attacks are a serious problem: o Costs an intruder very little to send tens of thousands of common words through the one-way function and check for matches o Between 20 and 40 percent of the passwords on a typical system can be cracked in this way q Solution #1: don’t allow users to select their own passwords o System generates a random password for each user o Drawback: § Many people find system-assigned passwords hard to remember and write them down Ø Example: L 8 f#n!. 5 r. H’ Chapter 7 Computer Security 10

Combating Dictionary Attacks q Solution #2: password checking o Allow users to choose their own passwords o Do not allow them to use passwords that are in a common dictionary q Solution #3: salt the password table o A salt is a random string that is concatenated with a password before sending it through the one-way hash function § Random salt value chosen by system Ø Example: plre § Password chosen by user Ø Example: baseball Chapter 7 Computer Security 11

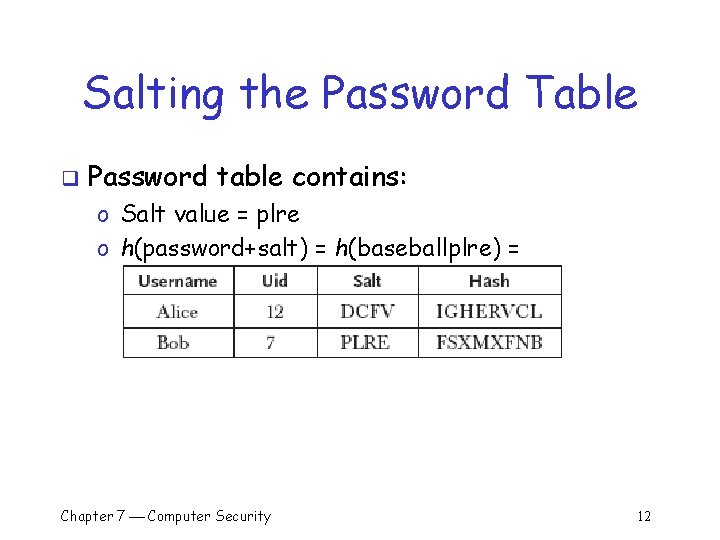
Salting the Password Table q Password table contains: o Salt value = plre o h(password+salt) = h(baseballplre) = FSXMXFNB Chapter 7 Computer Security 12

Salting the Password Table (cont) User enters username and password q The operating system combines the password and the salt and hashes the result q The operating system compares the result to the entry in the table q Match = user is assigned the corresponding uid q Advantages: q o Password table does not have to be protected o 7 Dictionary attacks are much harder Chapter Computer Security 13

A Dictionary Attack q Attacker must now expand the dictionary to contain every possible salt with each possible password: o baseballaaaa o baseballaaab o baseballaaac …. o baseballaaaz o baseballaaba o baseballaabb …. q 264 (about half a million) times more work to check each word in the dictionary (for 4 -letter salts) Chapter 7 Computer Security 14

Access Control Policies q Once a user has logged in the system must decide which actions he can and cannot perform o Examples: § Bob may be allowed to read files that Alice cannot § Alice may be permitted to use a printer that Bob cannot q In general, we view the system as a collection of: o Subjects (users) o Objects (resources) q An 7 access control Chapter Computer Security policy specifies how 15

The Access Control Matrix Suggested by Butler Lampson q Forms the basis of protection in many real operating systems q o Resources to be protected are called objects o Every object is within one or more protection domain o A domain specifies what operations are permitted on the objects it contains o Authorization to perform an operation on an object in a domain is called an access right Chapter 7 Computer Security 16

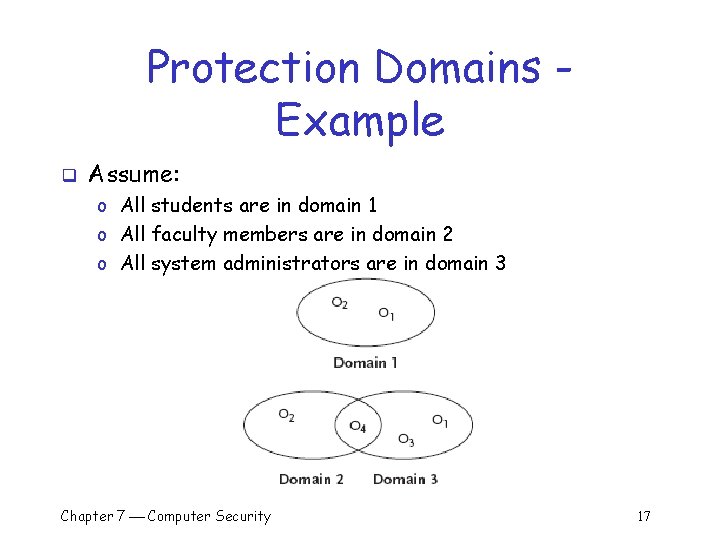
Protection Domains Example q Assume: o All students are in domain 1 o All faculty members are in domain 2 o All system administrators are in domain 3 Chapter 7 Computer Security 17

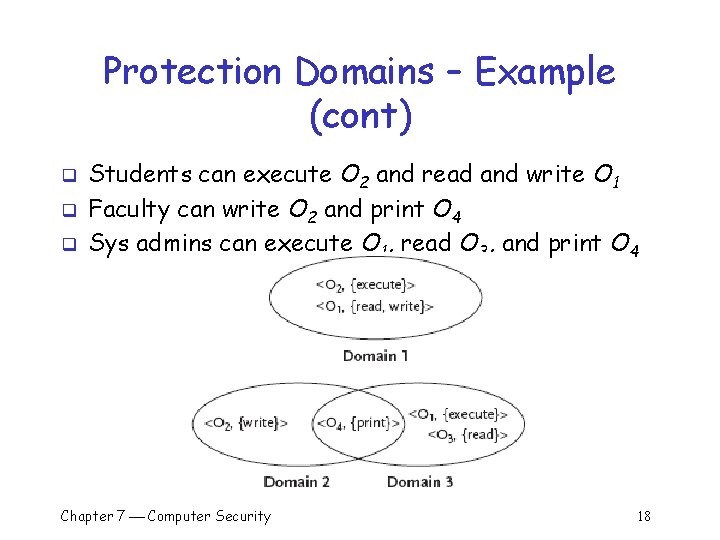
Protection Domains – Example (cont) q q q Students can execute O 2 and read and write O 1 Faculty can write O 2 and print O 4 Sys admins can execute O 1, read O 3, and print O 4 Chapter 7 Computer Security 18

Protection Domains (cont) q A user can only be in one protection domain at any given time o Static: a user always operates in the same domain § Simple § Inflexible o Dynamic: a user can switch from one domain to another § Complex § More flexible The domain in which a user is operating determines what actions are and are not Chapter 7 Computer Security permitted q 19

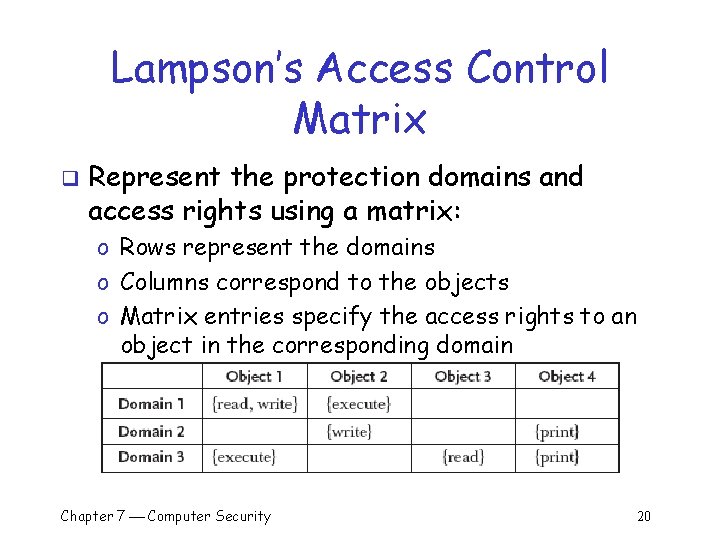
Lampson’s Access Control Matrix q Represent the protection domains and access rights using a matrix: o Rows represent the domains o Columns correspond to the objects o Matrix entries specify the access rights to an object in the corresponding domain Chapter 7 Computer Security 20

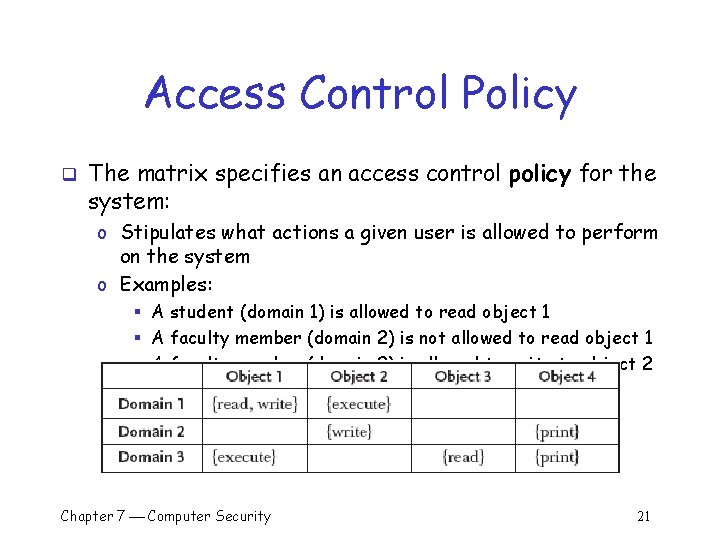
Access Control Policy q The matrix specifies an access control policy for the system: o Stipulates what actions a given user is allowed to perform on the system o Examples: § A student (domain 1) is allowed to read object 1 § A faculty member (domain 2) is not allowed to read object 1 § A faculty member (domain 2) is allowed to write to object 2 Chapter 7 Computer Security 21

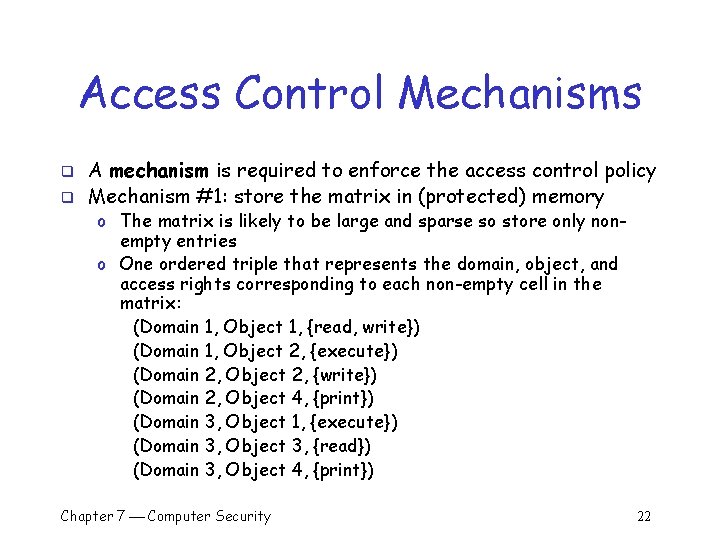
Access Control Mechanisms q q A mechanism is required to enforce the access control policy Mechanism #1: store the matrix in (protected) memory o The matrix is likely to be large and sparse so store only nonempty entries o One ordered triple that represents the domain, object, and access rights corresponding to each non-empty cell in the matrix: (Domain 1, Object 1, {read, write}) (Domain 1, Object 2, {execute}) (Domain 2, Object 2, {write}) (Domain 2, Object 4, {print}) (Domain 3, Object 1, {execute}) (Domain 3, Object 3, {read}) (Domain 3, Object 4, {print}) Chapter 7 Computer Security 22

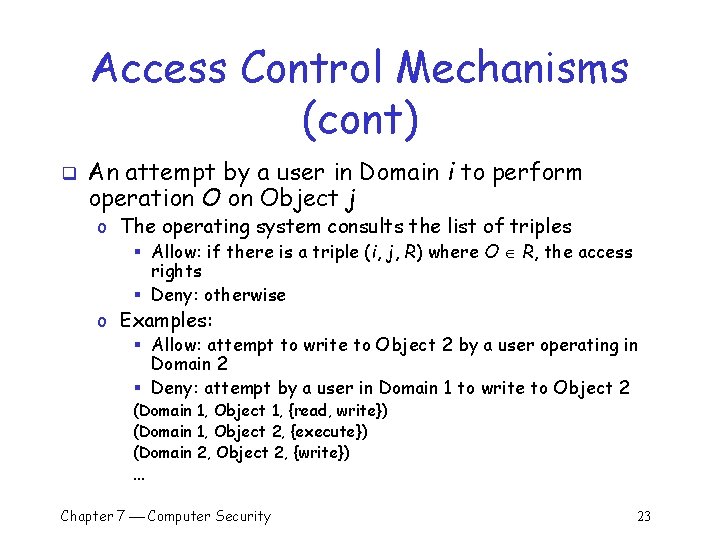
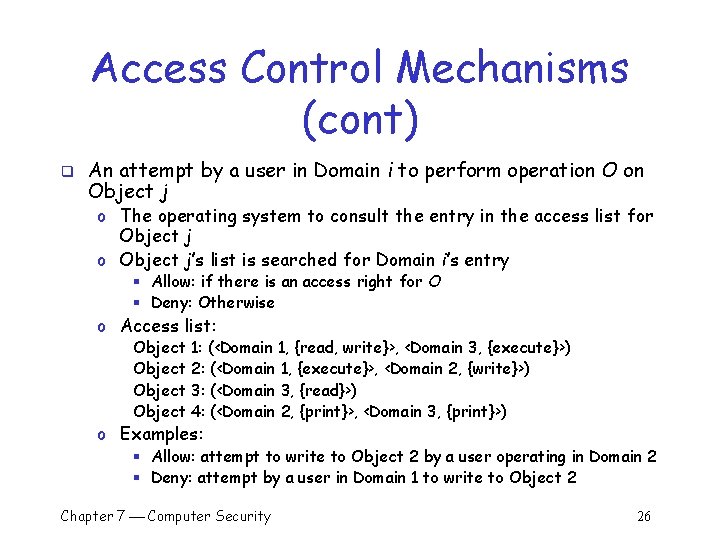
Access Control Mechanisms (cont) q An attempt by a user in Domain i to perform operation Object j o The operating system consults the list of triples § Allow: if there is a triple (i, j, R) where O R, the access rights § Deny: otherwise o Examples: § Allow: attempt to write to Object 2 by a user operating in Domain 2 § Deny: attempt by a user in Domain 1 to write to Object 2 (Domain 1, Object 1, {read, write}) (Domain 1, Object 2, {execute}) (Domain 2, Object 2, {write}) … Chapter 7 Computer Security 23

Access Control Mechanisms (cont) q q Mechanism #1: store the matrix in (protected) memory Drawbacks: o The matrix must be protected against unauthorized modification o Searching may be slow (if there are many entries) o Cannot take advantage of special groupings of objects § Example: the system clock Ø Ø Can be read by all users Matrix requires an entry in every domain specifying that the clock is readable Chapter 7 Computer Security 24

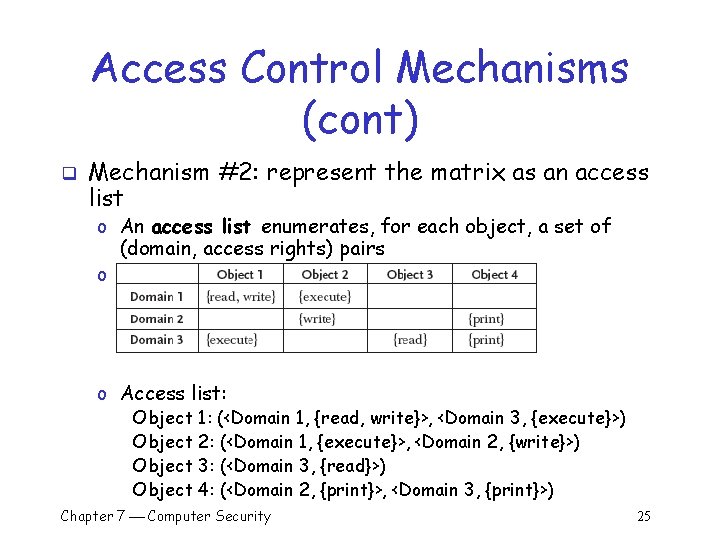
Access Control Mechanisms (cont) q Mechanism #2: represent the matrix as an access list o An access list enumerates, for each object, a set of (domain, access rights) pairs o Matrix: o Access list: Object 1: (<Domain 1, {read, write}>, <Domain 3, {execute}>) Object 2: (<Domain 1, {execute}>, <Domain 2, {write}>) Object 3: (<Domain 3, {read}>) Object 4: (<Domain 2, {print}>, <Domain 3, {print}>) Chapter 7 Computer Security 25

Access Control Mechanisms (cont) q An attempt by a user in Domain i to perform operation Object j o The operating system to consult the entry in the access list for Object j o Object j’s list is searched for Domain i’s entry § Allow: if there is an access right for O § Deny: Otherwise o Access list: Object 1: (<Domain 1, {read, write}>, <Domain 3, {execute}>) Object 2: (<Domain 1, {execute}>, <Domain 2, {write}>) Object 3: (<Domain 3, {read}>) Object 4: (<Domain 2, {print}>, <Domain 3, {print}>) o Examples: § Allow: attempt to write to Object 2 by a user operating in Domain 2 § Deny: attempt by a user in Domain 1 to write to Object 2 Chapter 7 Computer Security 26

Access Control Mechanisms (cont) q q Access lists also allow a default set of rights to be specified for each object Example: make Object 2 readable in every domain: Object 2: (<Default, {read}>, <Domain 1, {execute}>, <Domain 2, {write}>) q Advantages: o Can specify rights available in every domain in a single entry § Reduces the total amount of storage space required § Increases efficiency (for default rights) q Disadvantages: o Must be stored in memory, protected, and searched Chapter 7 Computer Security 27

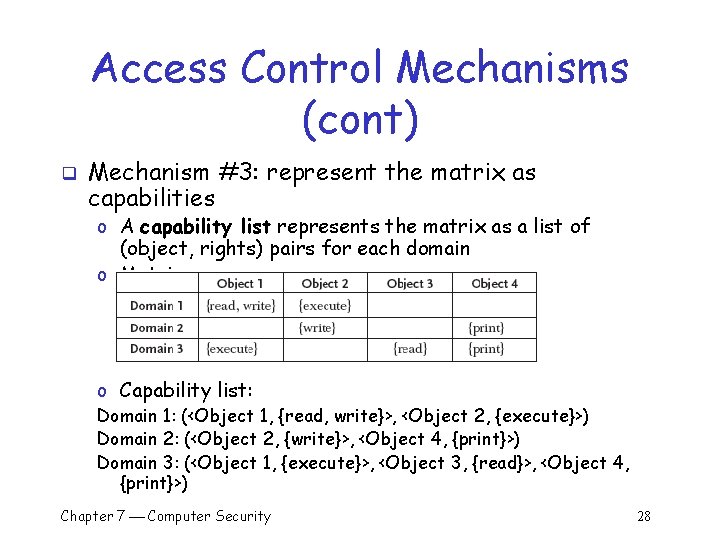
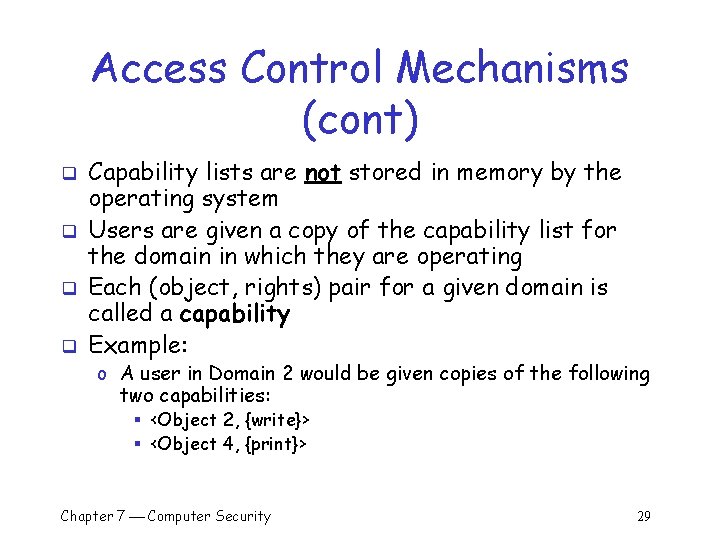
Access Control Mechanisms (cont) q Mechanism #3: represent the matrix as capabilities o A capability list represents the matrix as a list of (object, rights) pairs for each domain o Matrix: o Capability list: Domain 1: (<Object 1, {read, write}>, <Object 2, {execute}>) Domain 2: (<Object 2, {write}>, <Object 4, {print}>) Domain 3: (<Object 1, {execute}>, <Object 3, {read}>, <Object 4, {print}>) Chapter 7 Computer Security 28

Access Control Mechanisms (cont) q q Capability lists are not stored in memory by the operating system Users are given a copy of the capability list for the domain in which they are operating Each (object, rights) pair for a given domain is called a capability Example: o A user in Domain 2 would be given copies of the following two capabilities: § <Object 2, {write}> § <Object 4, {print}> Chapter 7 Computer Security 29

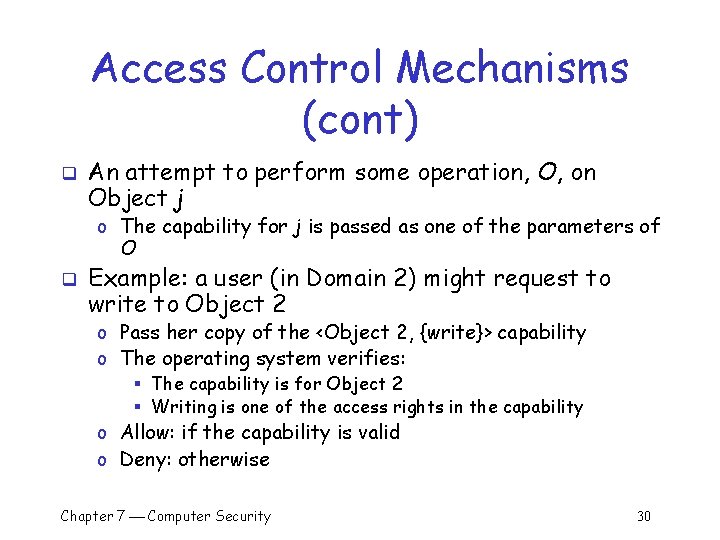
Access Control Mechanisms (cont) q An attempt to perform some operation, O, on Object j o The capability for j is passed as one of the parameters of O q Example: a user (in Domain 2) might request to write to Object 2 o Pass her copy of the <Object 2, {write}> capability o The operating system verifies: § The capability is for Object 2 § Writing is one of the access rights in the capability o Allow: if the capability is valid o Deny: otherwise Chapter 7 Computer Security 30

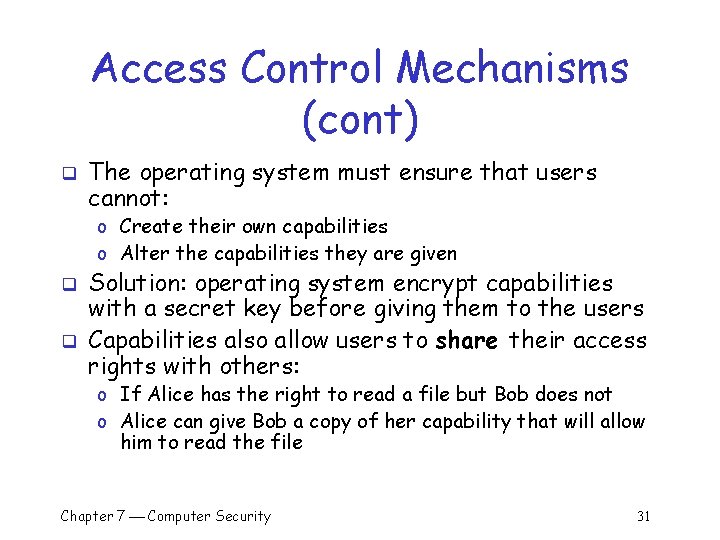
Access Control Mechanisms (cont) q The operating system must ensure that users cannot: o Create their own capabilities o Alter the capabilities they are given q q Solution: operating system encrypt capabilities with a secret key before giving them to the users Capabilities also allow users to share their access rights with others: o If Alice has the right to read a file but Bob does not o Alice can give Bob a copy of her capability that will allow him to read the file Chapter 7 Computer Security 31

Access Control Mechanisms (cont) q q Mechanism #3: represent the matrix as capabilities Advantages: o OS need not store all the access-control information § Capabilities are given to users and stored by them o Access control decisions require no searching of a list § Capabilities need to be checked o Allow users to share their capabilities with others q Disadvantages: o Capabilities must be protected (encrypted) o Sharing and revoking capabilities is complex Chapter 7 Computer Security 32

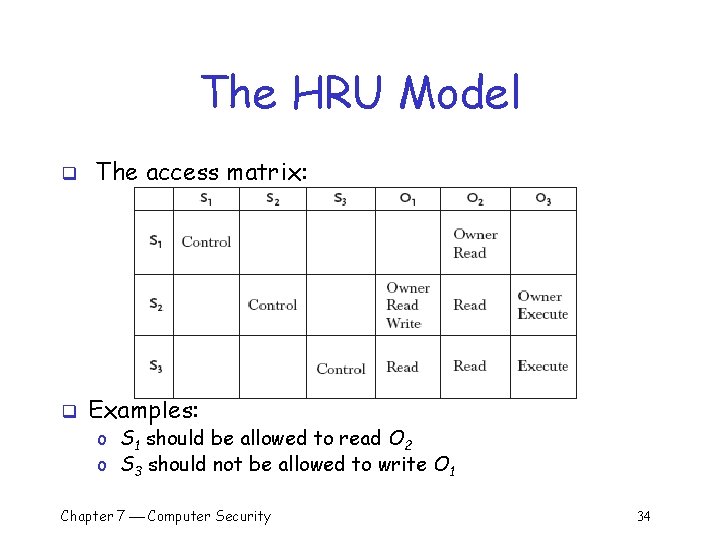
Other Access Control Policies q The HRU model o Named for its inventors, Harrison, Ruzzo, Ullman o Describes a protection system using an access matrix § Rows: the subjects in the system (S 1, S 2, and S 3) § Columns: the objects in the system (S 1, S 2, S 3, O 1, O 2, and O 3) § Note: the subjects are considered objects in the system o A subject is allowed to perform an operation on an object only if it has an access right Chapter 7 Computer Security 33

The HRU Model q q The access matrix: Examples: o S 1 should be allowed to read O 2 o S 3 should not be allowed to write O 1 Chapter 7 Computer Security 34

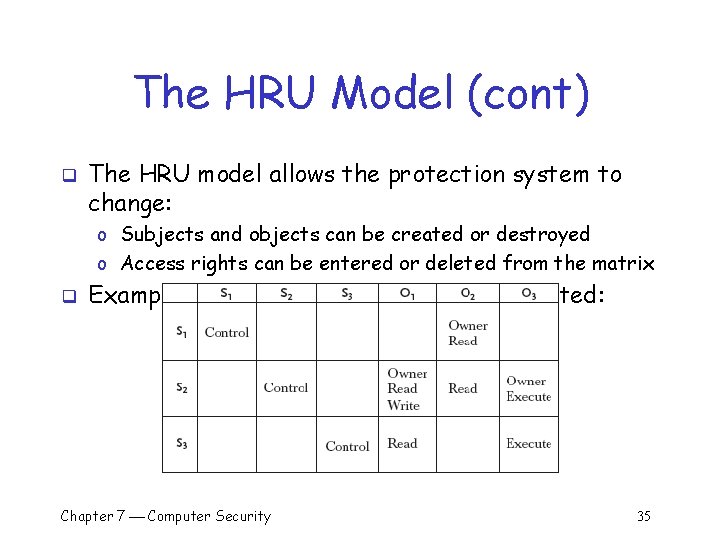
The HRU Model (cont) q The HRU model allows the protection system to change: o Subjects and objects can be created or destroyed o Access rights can be entered or deleted from the matrix q Example: S 3’s right to read O 2 can be deleted: Chapter 7 Computer Security 35

The HRU Model (cont) q The matrix can be changed by a well-defined set of commands that consist of: o A list of conditions that must be satisfied o A list of primitive operations that modify the matrix § Add/delete a subject to the matrix § Add/delete an object to the matrix § Add/delete a right to the matrix q Example: the command used to delete S 3’s right to read O 2 o If a subject is the owner of an object o The subject can perform the delete operation on a right in the matrix Chapter 7 Computer Security 36

The HRU Model (cont) q A right, r, is said to leak if: o The execution of some set of commands causes r to be entered into a cell that did not previously contain r A state where r has leaked is called unsafe q If, starting from an initial state unsafe states are unreachable: q o The matrix is said to be safe for r, since r cannot be leaked Chapter 7 Computer Security 37

The HRU Model (cont) The HRU model was designed to be general enough to represent most real protection systems q Main result: Harrison, Ruzzo, Ullman proved that: q o Determining whether or not unsafe states are reachable from a given initial state is not possible for an arbitrary set of commands o Safety is decidable in some restricted cases: § No command contains an operation that add subjects or objects § Mono-operational systems: every command performs Chapter 7 Computer Securityprimitive operation 38 only a single

The HRU Model (cont) q The HRU model demonstrates that for most useful access control policies: o Substantial restrictions must be placed on the policy to facilitate analysis o Even with restrictions analysis is likely to be difficult o If the policy is proven safe, we still need to show that the system properly implements the policy Chapter 7 Computer Security 39

Other Access Control Policies (cont) q The take-grant model: o More restricted than the HRU model § Not powerful enough to represent an arbitrary protection policy o Designed to be both useful and efficiently analyzable o An unlimited number of subjects and objects can be created o Four primitive operations: § Take § Grant § Create § Computer Revoke. Security Chapter 7 40

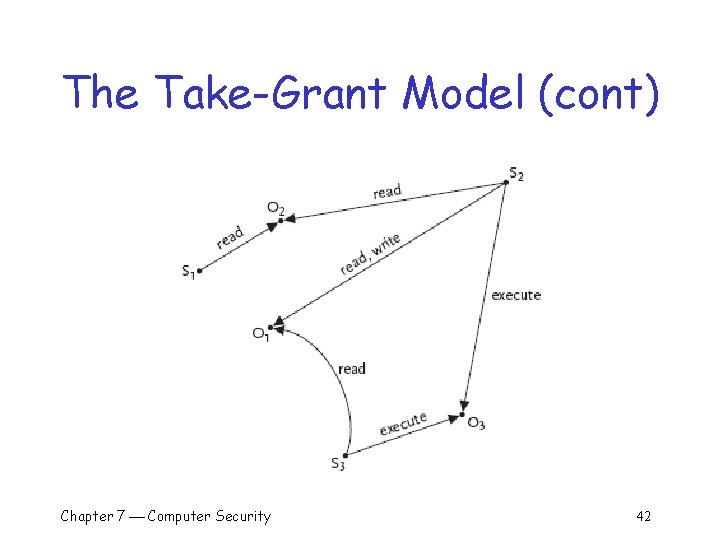
The Take-Grant Model q q A policy is not represented as a matrix A policy is represented as a directed graph o Nodes represent subjects and objects § Unlike the HRU model, subjects are not themselves objects o Edges represent access rights q Safety question: o Can a subject gain a given access right to a given object? Chapter 7 Computer Security 41

The Take-Grant Model (cont) Chapter 7 Computer Security 42

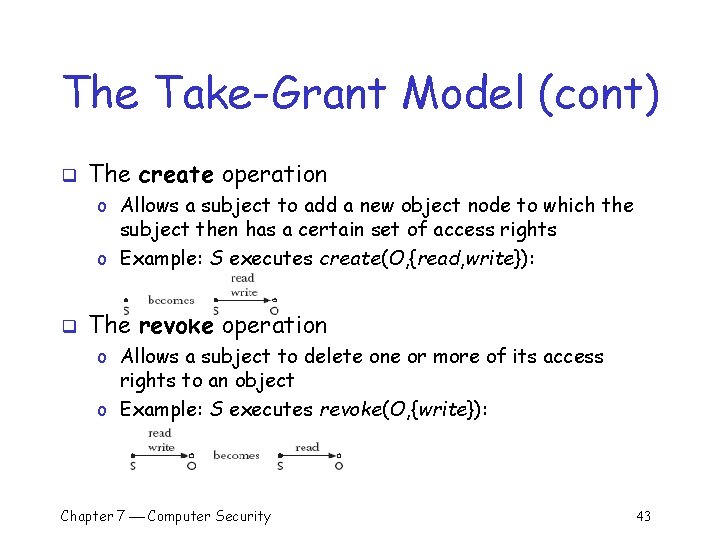
The Take-Grant Model (cont) q The create operation o Allows a subject to add a new object node to which the subject then has a certain set of access rights o Example: S executes create(O, {read, write}): q The revoke operation o Allows a subject to delete one or more of its access rights to an object o Example: S executes revoke(O, {write}): Chapter 7 Computer Security 43

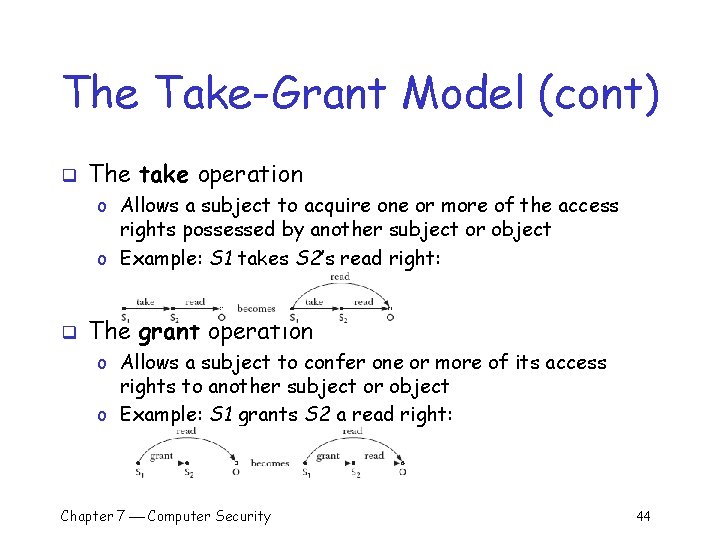
The Take-Grant Model (cont) q The take operation o Allows a subject to acquire one or more of the access rights possessed by another subject or object o Example: S 1 takes S 2’s read right: q The grant operation o Allows a subject to confer one or more of its access rights to another subject or object o Example: S 1 grants S 2 a read right: Chapter 7 Computer Security 44

The Take-Grant Model (cont) q More restricted than the HRU model o Not powerful enough to represent an arbitrary protection policy q Designed to be both useful and efficiently analyzable o There is an efficient algorithm for determining whether or not a particular subject can acquire a specific right to an object q Work has been done to define useful protection systems based on the takegrant model Chapter 7 Computer Security 45

Discretionary Vs. Mandatory Access Control q All the access control policies and mechanisms discussed so far have been discretionary o The owner of an object fully controls what users have what access rights q Mandatory access control policies and mechanisms o Control over what users have what access rights resides with the system and not the object’s owner q Examples: Bob creates a file o Discretionary: Bob can give Alice read access to the file if he wishes o Mandatory: The system may deny Alice read access to Bob’s file regardless of Bob’s wishes Chapter 7 Computer Security 46

Information Flow Policies q An important class of mandatory access control policies are information flow policies o Control both direct and indirect paths through which information can flow q Example: o Alice does not have permission to read a file but Bob does o Alice convince Bob to read the file and transmit its contents to her q Result: Alice has gained unauthorized access to the file’s contents o Discretionary access-control policies cannot prevent this breach o 7 Information flow policies can prevent this breach Chapter Computer Security 47

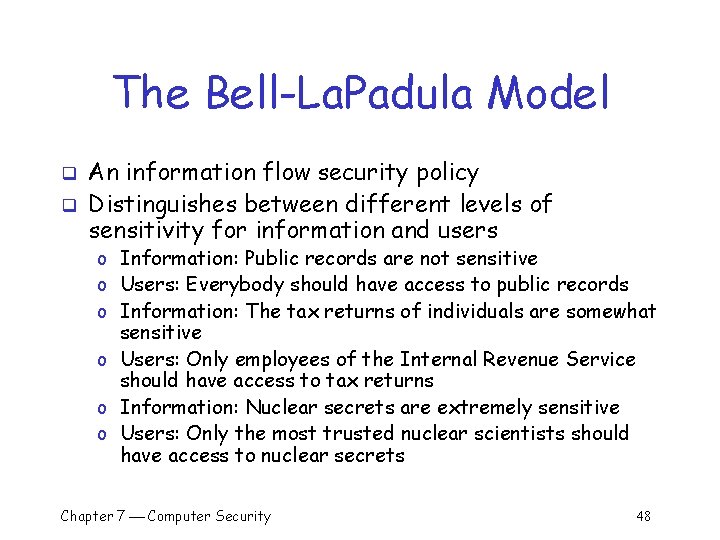
The Bell-La. Padula Model q q An information flow security policy Distinguishes between different levels of sensitivity for information and users o Information: Public records are not sensitive o Users: Everybody should have access to public records o Information: The tax returns of individuals are somewhat sensitive o Users: Only employees of the Internal Revenue Service should have access to tax returns o Information: Nuclear secrets are extremely sensitive o Users: Only the most trusted nuclear scientists should have access to nuclear secrets Chapter 7 Computer Security 48

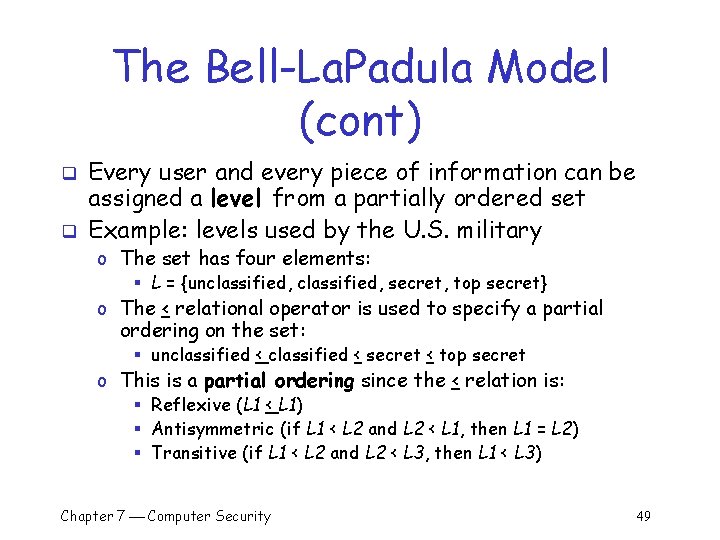
The Bell-La. Padula Model (cont) q q Every user and every piece of information can be assigned a level from a partially ordered set Example: levels used by the U. S. military o The set has four elements: § L = {unclassified, secret, top secret} o The < relational operator is used to specify a partial ordering on the set: § unclassified < secret < top secret o This is a partial ordering since the < relation is: § Reflexive (L 1 < L 1) § Antisymmetric (if L 1 < L 2 and L 2 < L 1, then L 1 = L 2) § Transitive (if L 1 < L 2 and L 2 < L 3, then L 1 < L 3) Chapter 7 Computer Security 49

The Bell-La. Padula Model (cont) Every subject and object in the system is assigned a security level from L q Example: q o o o Alice might be assigned the level secret Bob might be unclassified Carol might be classified The file memo 1 might be classified The file memo 2 might be top secret Chapter 7 Computer Security 50

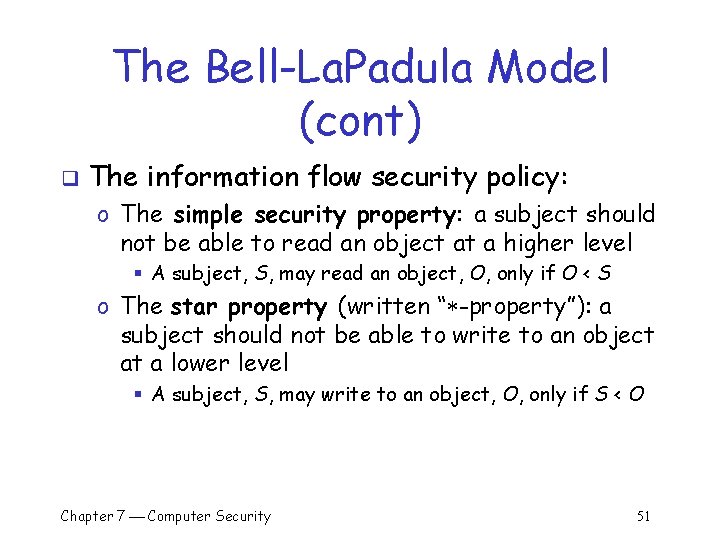
The Bell-La. Padula Model (cont) q The information flow security policy: o The simple security property: a subject should not be able to read an object at a higher level § A subject, S, may read an object, O, only if O < S o The star property (written “ -property”): a subject should not be able to write to an object at a lower level § A subject, S, may write to an object, O, only if S < O Chapter 7 Computer Security 51

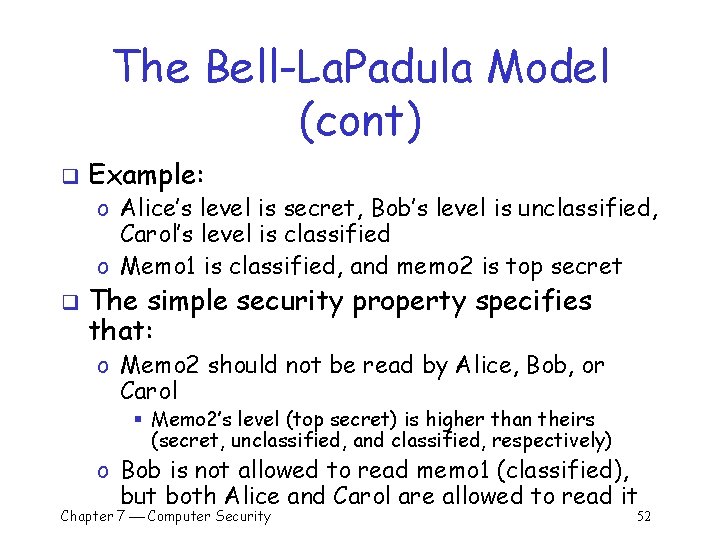
The Bell-La. Padula Model (cont) q Example: o Alice’s level is secret, Bob’s level is unclassified, Carol’s level is classified o Memo 1 is classified, and memo 2 is top secret q The simple security property specifies that: o Memo 2 should not be read by Alice, Bob, or Carol § Memo 2’s level (top secret) is higher than theirs (secret, unclassified, and classified, respectively) o Bob is not allowed to read memo 1 (classified), but both Alice and Carol are allowed to read it Chapter 7 Computer Security 52

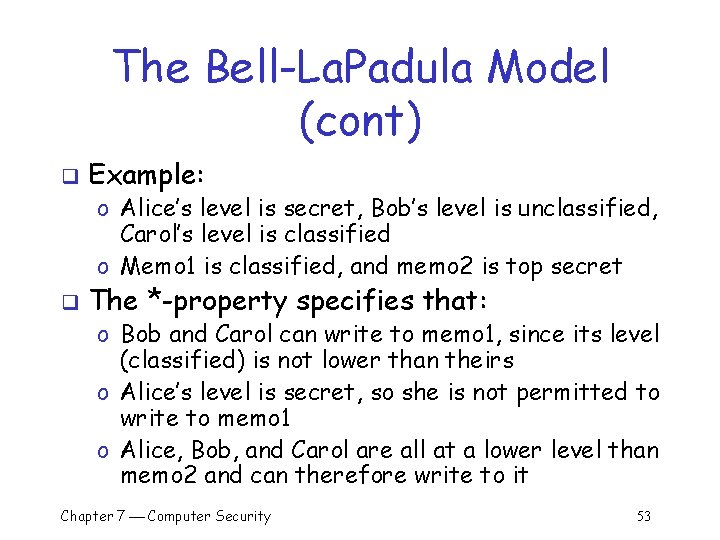
The Bell-La. Padula Model (cont) q Example: o Alice’s level is secret, Bob’s level is unclassified, Carol’s level is classified o Memo 1 is classified, and memo 2 is top secret q The *-property specifies that: o Bob and Carol can write to memo 1, since its level (classified) is not lower than theirs o Alice’s level is secret, so she is not permitted to write to memo 1 o Alice, Bob, and Carol are all at a lower level than memo 2 and can therefore write to it Chapter 7 Computer Security 53

The Bell-La. Padula Model (cont) q q This information flow policy controls both direct and indirect paths through which information can flow Example: Bob cannot learn the contents of memo 1 o Bob (unclassified) is not allowed to read memo 1 (classified) himself o Alice (secret) is allowed to read memo 1 (classified) § Alice is not allowed to write anything but secret or top secret documents which Bob cannot read § Bob cannot read anything that Alice writes so Alice cannot tell Bob the contents of memo 1 § Problem: Alice may be able to communicate with Bob without writing any files Chapter 7 Computer Security 54

The Bell-La. Padula Model (cont) q q q Suppose that Bob can observe some aspect of the system that Alice can control Example: Bob can determine whether or not Alice is logged in to the system Bob and Alice agree that: o Every minute Alice spends logged in will represent a 1 o Every minute Alice spends logged out will represent a 0 q Alice could read memo 1 and then begin transmitting it, one bit every minute, to Bob using their covert channel o There are many other covert channels available on most time-sharing systems o Eliminating all possible covert channels can be challenging Chapter 7 Computer Security 55

Summary q Important components of computer security: o User authentication – determine the identity of an individual accessing the system § Knowledge-based, token-based, and biometrics o Access control policies – stipulate what actions a given user is allowed to perform on the system § Discretionary: access control matrix § Mandatory: the Bell-La. Padula model o Access control mechanisms – enforce the system’s policy § Discretionary: access lists, capabilities Chapter 7 Computer Security 56