Security Guide to Network Security Fundamentals Fifth Edition




















- Slides: 72

Security+ Guide to Network Security Fundamentals, Fifth Edition Chapter 7 Network Security Fundamentals

Objectives • List the different types of network security devices and explain how they can be used • Explain how network technologies can enhance security • Describe secure network design elements Security+ Guide to Network Security Fundamentals, Fifth Edition 2

Network Security Fundamentals • Once information security and network security were virtually synonymous • The network was viewed as the protecting wall around which client computers could be kept safe • But this approach is untenable: too many entry points that circumvent the network and allow malware to enter: – Infected USB flash drive – Malware take advantage of common network protocols (HTTP), and could not always be detected or blocked by network security devices Security+ Guide to Network Security Fundamentals, Fifth Edition 3

Network Security Posture • Yet having secure network is essential to comprehensive information security posture: – Not all applications are designed and written with security and reliability in mind, so falls to network to provide protection – Network-delivered services can scale better for larger environments and can complement server and application functionality – Attacker who can successfully penetrate computer network may have access to thousands of desktop systems, servers, and storage devices Security+ Guide to Network Security Fundamentals, Fifth Edition 4

Network Security Strategy • Secure network defense still remains critical element in any organization’s security plan • Organizations should make network defenses one of first priorities in protecting information • Network security strategy: – Network devices – Network technologies – Design of the network Security+ Guide to Network Security Fundamentals, Fifth Edition 5

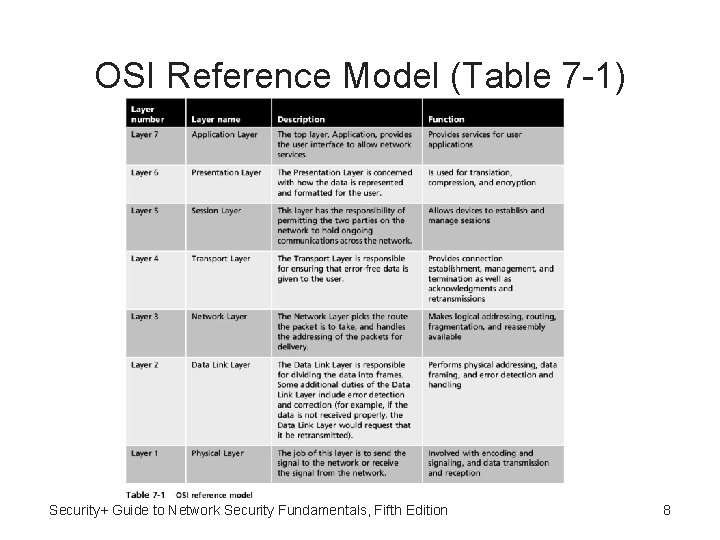
Standard Network Devices • Security functions of standard network devices can be used to provide degree of network security • Network devices can be classified based on function in Open systems interconnection (OSI) model – Standards released in 1978, revised in 1983, still used today – Illustrates: • How network device prepares data for delivery • How data is handled once received Security+ Guide to Network Security Fundamentals, Fifth Edition 6

OSI Layers • OSI model breaks networking steps into seven layers – Each layer has different networking tasks – Each layer cooperates with adjacent layers Security+ Guide to Network Security Fundamentals, Fifth Edition 7

OSI Reference Model (Table 7 -1) Security+ Guide to Network Security Fundamentals, Fifth Edition 8

Hubs • Hubs – Used by early LANs to connect multiple Ethernet devices together to function as single network segment • Work at Layer 1 of the OSI model • Did not read data passing through them so ignorant of data source and destination • Essentially multiport repeater • Protocol analyzer - Captures packets to decode and analyze their contents; facilitated by hub • Hubs rarely used today due to security vulnerability and increased network traffic Security+ Guide to Network Security Fundamentals, Fifth Edition 9

Switches • • Switch – Device that connects network devices Operate at Data Link Layer (Layer 2) Determine which device is connected to each port Can forward frames sent to that specific device or broadcast to all devices • Use MAC address to identify devices • Provide better security than hubs by limiting distribution of frames Security+ Guide to Network Security Fundamentals, Fifth Edition 10

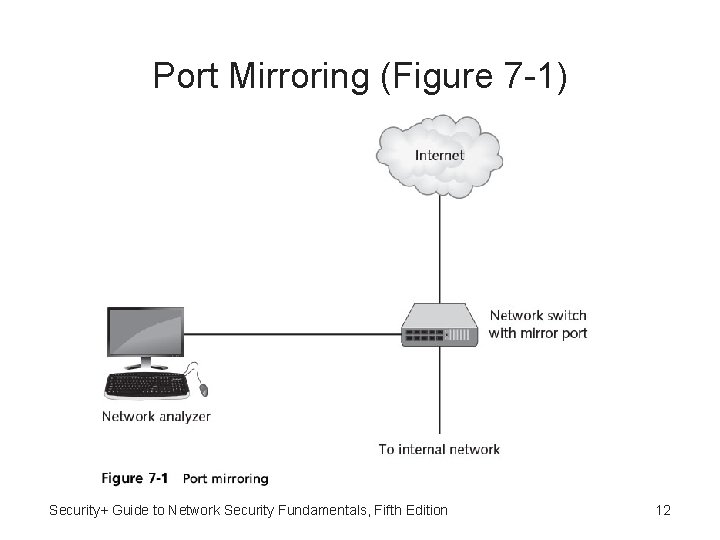
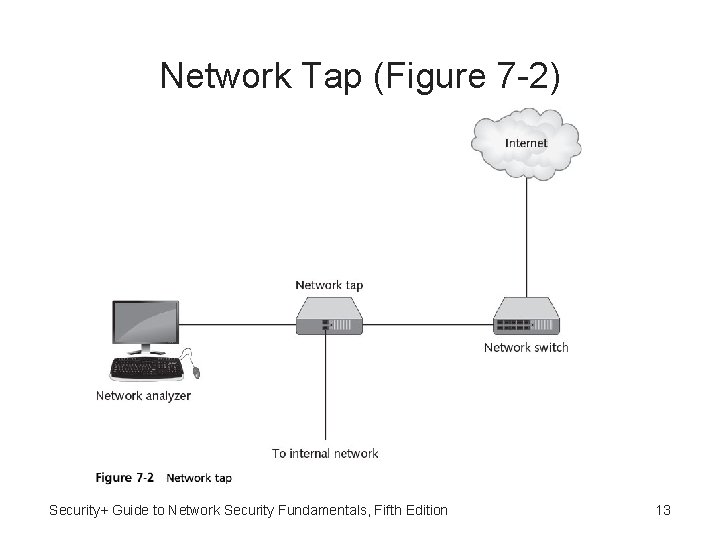
Traffic Monitoring • Network administrator monitors network traffic to help identify and troubleshoot network problems • Traffic monitoring methods: – Port mirroring - Allows administrator to configure switch to copy traffic that occurs on some or all ports to designated monitoring port on switch – Network tap (test access point) - Separate device installed on network Security+ Guide to Network Security Fundamentals, Fifth Edition 11

Port Mirroring (Figure 7 -1) Security+ Guide to Network Security Fundamentals, Fifth Edition 12

Network Tap (Figure 7 -2) Security+ Guide to Network Security Fundamentals, Fifth Edition 13

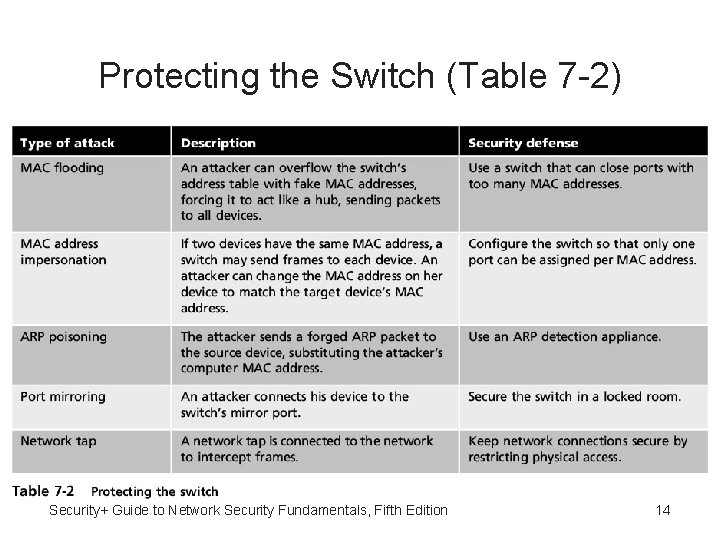
Protecting the Switch (Table 7 -2) Security+ Guide to Network Security Fundamentals, Fifth Edition 14

Routers • Router – Network device that forward packets across computer networks • Operate at Network Layer (Layer 3) • Can be set to filter out specific types of network traffic Security+ Guide to Network Security Fundamentals, Fifth Edition 15

Load Balancing • Load balancing – Technology to help evenly distribute work across network • Allocate requests among multiple devices • Advantages of load-balancing technology – Reduces probability of overloading a single server – Optimizes bandwidth of network computers – Reduces network downtime • Load balancing achieved through software or hardware device Security+ Guide to Network Security Fundamentals, Fifth Edition 16

Load Balancers • Load balancer - Dedicated hardware device • Often grouped into two categories: – Layer 4 load balancers - Act upon data found in Network and Transport layer protocols such as Internet Protocol (IP), Transmission Control Protocol (TCP), File Transfer Protocol (FTP), and User Datagram Protocol (UDP) – Layer 7 load balancers - Distribute requests based on data found in Application layer protocols such as HTTP Security+ Guide to Network Security Fundamentals, Fifth Edition 17

Load Balancer Techniques • Layer 4 and Layer 7 load balancers can distribute work in different ways: – Based on a “round-robin” rotation to all devices equally – To devices that have the least number of connections • Layer 7 load balancers also can use HTTP headers, cookies, or data within application message itself to make decision on distribution Security+ Guide to Network Security Fundamentals, Fifth Edition 18

Load Balancers Security • Load balancer has security advantages • Because load balancers generally are located between routers and servers, can detect and stop attacks directed at a server or application • Load balancer can be used detect and prevent denial-of-service (Do. S) and protocol attacks that could cripple a single server • Some load balancers can hide HTTP error pages or remove server identification headers from HTTP responses, denying attackers additional information about the internal network Security+ Guide to Network Security Fundamentals, Fifth Edition 19

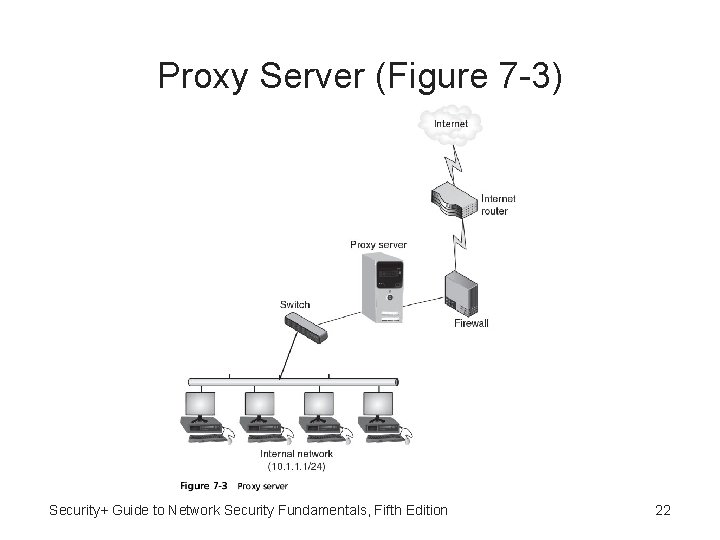
Proxies • Proxy – Person who authorized to act as substitute or agent on behalf of another human • Proxy server - Computer or application that intercepts and processes user requests: – If previous request has been fulfilled a copy of Web page may reside in proxy server’s cache – If not, proxy server requests item from external Web server using its own IP address Security+ Guide to Network Security Fundamentals, Fifth Edition 20

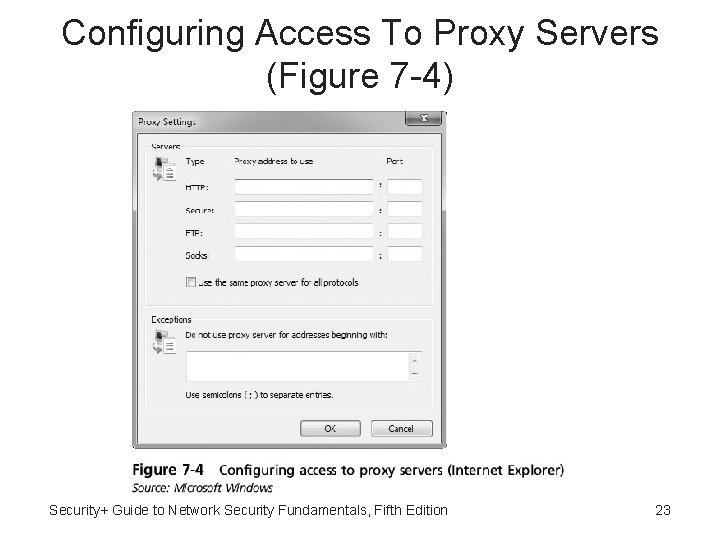
Application-Aware Proxies • When proxy server receives requested item from web server, item is then forwarded to the client • Access to proxy servers is configured in user’s web browser • Application-aware proxy - Special proxy server that “knows” the application protocols that it supports (FTP proxy server implements the protocol FTP) Security+ Guide to Network Security Fundamentals, Fifth Edition 21

Proxy Server (Figure 7 -3) Security+ Guide to Network Security Fundamentals, Fifth Edition 22

Configuring Access To Proxy Servers (Figure 7 -4) Security+ Guide to Network Security Fundamentals, Fifth Edition 23

Proxy Advantages • Proxy server advantages: – Increased speed (requests served from the cache) – Reduced costs (cache reduces bandwidth required) – Improved management - Block specific Web pages or sites – Stronger security: • Intercept malware • Hide client system’s IP address from the open Internet Security+ Guide to Network Security Fundamentals, Fifth Edition 24

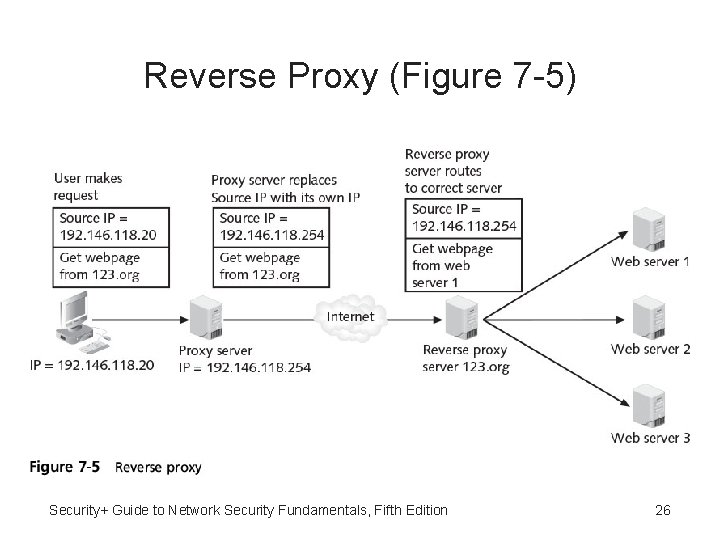
Reverse Proxies • Reverse proxy - Does not serve clients but routes incoming requests to correct server • Reverse proxy’s IP address visible to outside users • Internal server’s IP address hidden Security+ Guide to Network Security Fundamentals, Fifth Edition 25

Reverse Proxy (Figure 7 -5) Security+ Guide to Network Security Fundamentals, Fifth Edition 26

Network Security Hardware • Specifically designed security hardware devices • Greater protection than standard networking devices • Devices include network firewalls, spam filters, virtual private network concentrators, Internet content filters, Web security gateways, intrusion detection and prevention systems, and Unified Threat Management appliances Security+ Guide to Network Security Fundamentals, Fifth Edition 27

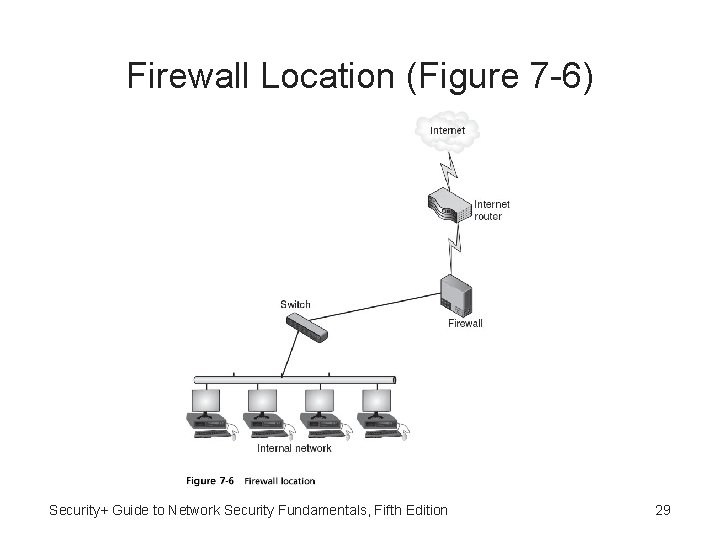
Network Firewalls • Host-based application software firewall runs as program on one client • Hardware-based network firewall designed to protected an entire network • Both essentially same: to inspect packets and either accept or deny entry • Hardware firewalls usually located outside network security perimeter as first line of defense Security+ Guide to Network Security Fundamentals, Fifth Edition 28

Firewall Location (Figure 7 -6) Security+ Guide to Network Security Fundamentals, Fifth Edition 29

Network Firewall Filtering • Methods of firewall packet filtering: – Stateless packet filtering - Inspects incoming packet and permits or denies based on conditions set by administrator – Stateful packet filtering - Keeps record of state of connection and makes decisions based on connection and conditions Security+ Guide to Network Security Fundamentals, Fifth Edition 30

Network Firewall Actions • Firewall actions: – Allow - Let packet pass through and continue on its journey – Drop - Prevent packet from passing into network and send no response to sender – Reject - Prevent packet from passing into network but send a message to sender that the destination cannot be reached – Ask - Inquire what action to take Security+ Guide to Network Security Fundamentals, Fifth Edition 31

Rule-Based Firewalls • Rule-based firewall uses set of individual instructions to control actions (firewall rules) • Each firewall rule is separate instruction processed in sequence • Rules stored together in one or more text files that read when firewall starts • Rule-based are static in nature and cannot do anything other than what have been expressly configured to do Security+ Guide to Network Security Fundamentals, Fifth Edition 32

Application-Aware Firewalls • Application-aware firewall (next-generation firewall or NGFW) - More “intelligent” firewall operates at higher level • Identifies applications that send packets through firewall and then make decisions about application (vs. granular rule settings like destination port or protocol) • Web application firewall - Special type of application-aware that looks at applications using HTTP Security+ Guide to Network Security Fundamentals, Fifth Edition 33

Spam Filters • Spam filters - Enterprise-wide spam filters block spam before it reaches the host • Email systems use two protocols: – Simple Mail Transfer Protocol (SMTP) - Handles outgoing mail – Post Office Protocol (POP) - Handles incoming mail Security+ Guide to Network Security Fundamentals, Fifth Edition 34

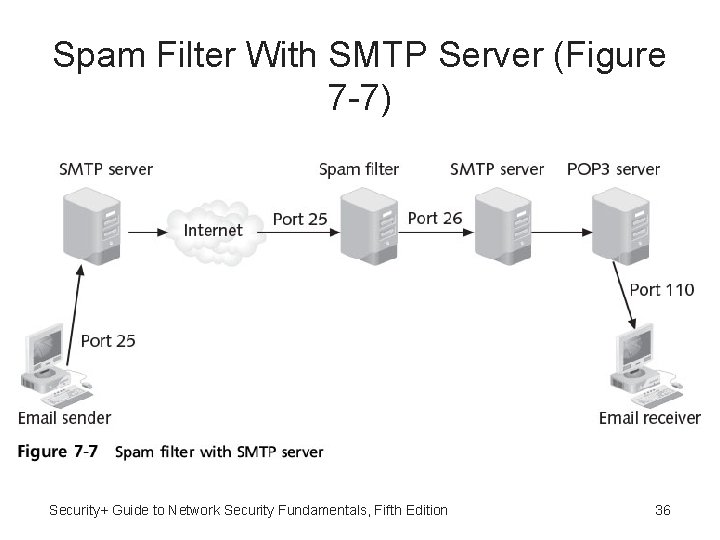
Spam Filters On SMTP Server • Spam filters installed with SMTP server – Filter configured to listen on port 25 – Pass non-spam e-mail to SMTP server listening on another port – Method prevents SMTP server from notifying spammer of failed message delivery Security+ Guide to Network Security Fundamentals, Fifth Edition 35

Spam Filter With SMTP Server (Figure 7 -7) Security+ Guide to Network Security Fundamentals, Fifth Edition 36

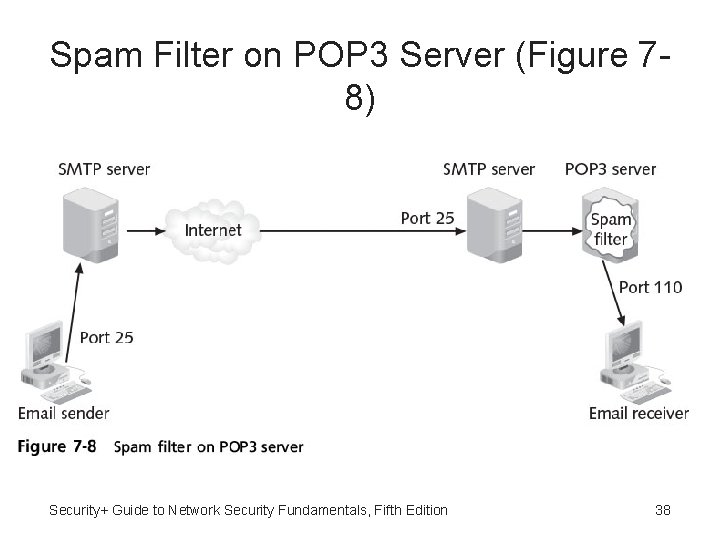
Spam Filters On POP 3 Server • Spam filters installed on POP 3 server – All spam must first pass through SMTP server and be delivered to user’s mailbox – Can result in increased costs of storage, transmission, backup, deletion • Third-party entity contracted to filter spam – All email directed to third-party’s remote spam filter – Email cleansed before being redirected to organization Security+ Guide to Network Security Fundamentals, Fifth Edition 37

Spam Filter on POP 3 Server (Figure 78) Security+ Guide to Network Security Fundamentals, Fifth Edition 38

Virtual Private Network Concentrators • Virtual private network (VPN) - Uses unsecured network as if were secure • All data transmitted between remote device and network is encrypted • Types of VPNs: – Remote-access VPN - User to LAN connection – Site-to-site VPN - Multiple sites can connect to other sites over the Internet Security+ Guide to Network Security Fundamentals, Fifth Edition 39

VPN Endpoints • Endpoints – End of tunnel between VPN devices: – May be software on local computer – May be VPN concentrator (hardware device) – May be integrated into another networking device • VPNs can be software-based or hardware-based – Hardware-based generally have better security – Software-based have more flexibility in managing network traffic Security+ Guide to Network Security Fundamentals, Fifth Edition 40

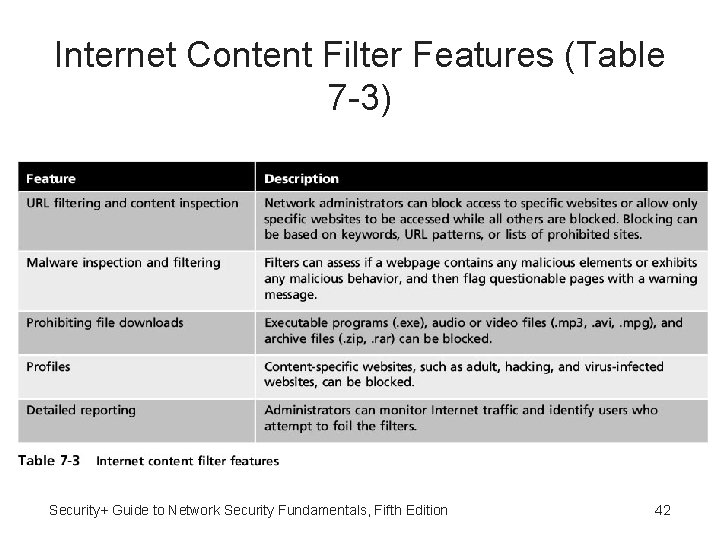
Internet Content Filters • Internet content filters - Monitor Internet traffic and block access to preselected Web sites and files • Unapproved sites can be restricted based on: – Uniform Resource Locator (URL filtering) – Searching for and matching keywords such as sex or hate (content inspection) – Looking for malware (malware inspection) Security+ Guide to Network Security Fundamentals, Fifth Edition 41

Internet Content Filter Features (Table 7 -3) Security+ Guide to Network Security Fundamentals, Fifth Edition 42

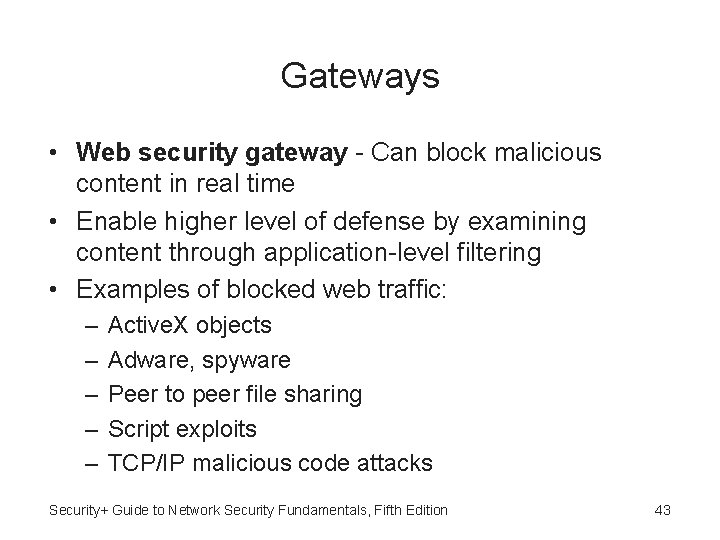
Gateways • Web security gateway - Can block malicious content in real time • Enable higher level of defense by examining content through application-level filtering • Examples of blocked web traffic: – – – Active. X objects Adware, spyware Peer to peer file sharing Script exploits TCP/IP malicious code attacks Security+ Guide to Network Security Fundamentals, Fifth Edition 43

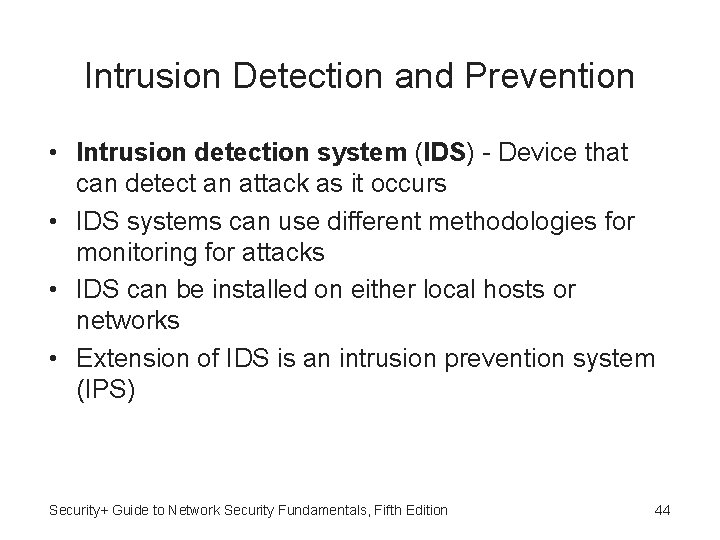
Intrusion Detection and Prevention • Intrusion detection system (IDS) - Device that can detect an attack as it occurs • IDS systems can use different methodologies for monitoring for attacks • IDS can be installed on either local hosts or networks • Extension of IDS is an intrusion prevention system (IPS) Security+ Guide to Network Security Fundamentals, Fifth Edition 44

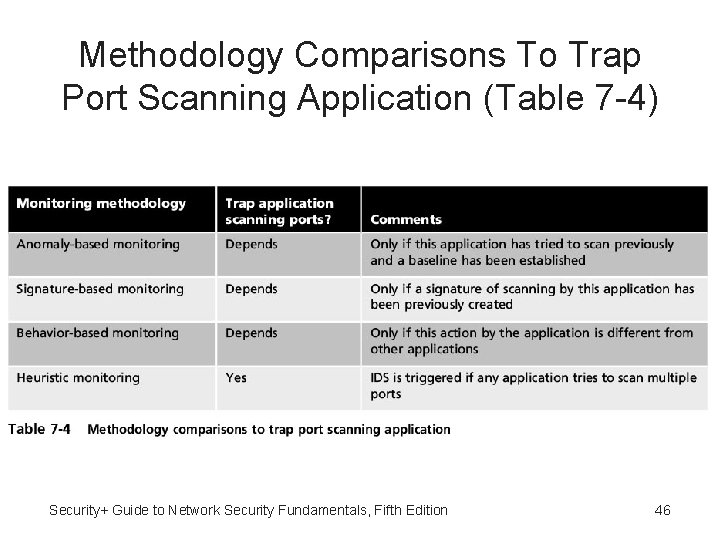
Monitoring Methodologies • Anomaly-based monitoring - Compares current detected behavior with baseline • Signature-based monitoring - Looks for wellknown attack signature patterns • Behavior-based monitoring - Detects abnormal actions by processes or programs and alerts user who decides whether to allow or block activity • Heuristic monitoring - Uses experience-based techniques Security+ Guide to Network Security Fundamentals, Fifth Edition 45

Methodology Comparisons To Trap Port Scanning Application (Table 7 -4) Security+ Guide to Network Security Fundamentals, Fifth Edition 46

Host-Based Intrusion Detection System (HIDS) • Host-based intrusion detection system (HIDS) Software-based application that runs on local host computer that can detect an attack as occurs • HIDS relies on agents installed directly on system being protected • Monitors: – – System calls File system access System registry settings Host input/output Security+ Guide to Network Security Fundamentals, Fifth Edition 47

HIDS Disadvantages • Disadvantages of HIDS: – Cannot monitor network traffic that does not reach local system – All log data is stored locally – Resource-intensive and can slow system Security+ Guide to Network Security Fundamentals, Fifth Edition 48

Network Intrusion Detection System (NIDS) • Network intrusion detection system (NIDS) Watches for attacks on network. • NIDS sensors installed on firewalls and routers to gather information and report back to central device • May use one or more of the evaluation techniques Security+ Guide to Network Security Fundamentals, Fifth Edition 49

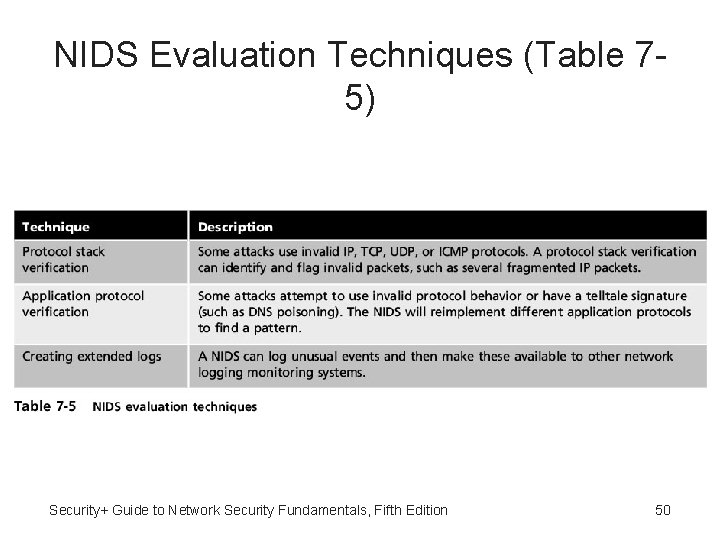
NIDS Evaluation Techniques (Table 75) Security+ Guide to Network Security Fundamentals, Fifth Edition 50

Application-Aware IDS • Once attack detected NIDS can perform different actions to sound an alarm and log event • Application-aware IDS - Specialized IDS capable of using “contextual knowledge” in real time • Can know the version of the operating system or which application is running as well as what vulnerabilities are present in the systems being protected • Improves the speed and accuracy of IDS decisions and reduces the risk of false positives Security+ Guide to Network Security Fundamentals, Fifth Edition 51

Intrusion Prevention System (IPS) • Intrusion prevention system (IPS) - Monitors to detect malicious activities like IDS does but also attempts to prevent them by stopping attack • Network intrusion prevention system (NIPS) Similar to active NIDS that monitors network traffic to immediately react to malicious attack Security+ Guide to Network Security Fundamentals, Fifth Edition 52

NIDS vs. NIPS • Major differences between a NIDS and a NIPS is location: – NIDS has sensors that monitor traffic entering and leaving firewall, and reports back to central device for analysis – NIPS would be located “in line” on firewall itself to allow NIPS to more quickly take action to block attack • Application-aware IPS - Knows information like applications and operating systems so that can provide higher degree of accuracy Security+ Guide to Network Security Fundamentals, Fifth Edition 53

Unified Threat Management (UTM) Security Appliances • Because different types of network security hardware each provide a different defense, network may require multiple devices for comprehensive protection • Makes cumbersome to manage multiple devices • Unified Threat Management (UTM) - Security product that combines several security functions Security+ Guide to Network Security Fundamentals, Fifth Edition 54

UTM Functions • UTM functions: – – – – – Antispam and antiphishing Antivirus and antispyware Bandwidth optimization Content filtering Encryption Firewall Instant messaging control Intrusion protection Web filtering Security+ Guide to Network Security Fundamentals, Fifth Edition 55

Security Through Network Technologies • Network technologies can also help to secure network • Two technologies: • Network address translation • Network access control Security+ Guide to Network Security Fundamentals, Fifth Edition 56

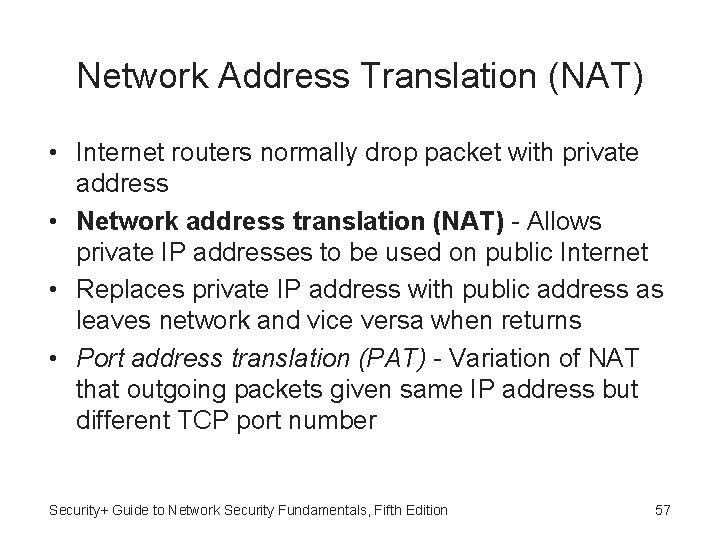
Network Address Translation (NAT) • Internet routers normally drop packet with private address • Network address translation (NAT) - Allows private IP addresses to be used on public Internet • Replaces private IP address with public address as leaves network and vice versa when returns • Port address translation (PAT) - Variation of NAT that outgoing packets given same IP address but different TCP port number Security+ Guide to Network Security Fundamentals, Fifth Edition 57

Network Address Translation (Figure 7 -9) Security+ Guide to Network Security Fundamentals, Fifth Edition 58

NAT Advantages • Advantages of NAT: – Masks IP addresses of internal devices – Allows multiple devices to share smaller number of public IP addresses Security+ Guide to Network Security Fundamentals, Fifth Edition 59

Network Access Control (NAC) • Network access control (NAC) - Examines current state of system or network device before allowing network connection • Device must meet set of criteria • If not met, NAC allows connection to quarantine network until deficiencies corrected Security+ Guide to Network Security Fundamentals, Fifth Edition 60

Network Access Control (NAC) Framework (Figure 7 -10) Security+ Guide to Network Security Fundamentals, Fifth Edition 61

Security Through Network Design Elements • Elements of a secure network design – – Demilitarized zones Subnetting Virtual LANs Remote access Security+ Guide to Network Security Fundamentals, Fifth Edition 62

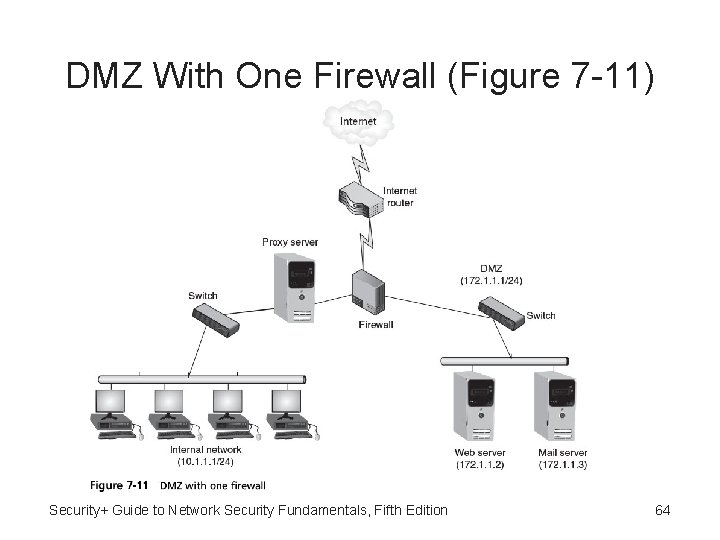
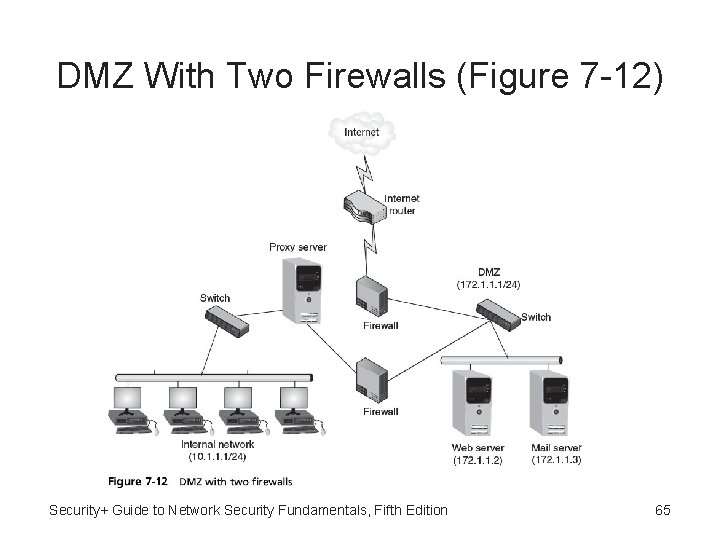
Demilitarized Zone (DMZ) • Demilitarized zone (DMZ) - Separate network located outside secure network perimeter • Untrusted outside users can access DMZ but not secure network • Most secure approach is have two firewalls Security+ Guide to Network Security Fundamentals, Fifth Edition 63

DMZ With One Firewall (Figure 7 -11) Security+ Guide to Network Security Fundamentals, Fifth Edition 64

DMZ With Two Firewalls (Figure 7 -12) Security+ Guide to Network Security Fundamentals, Fifth Edition 65

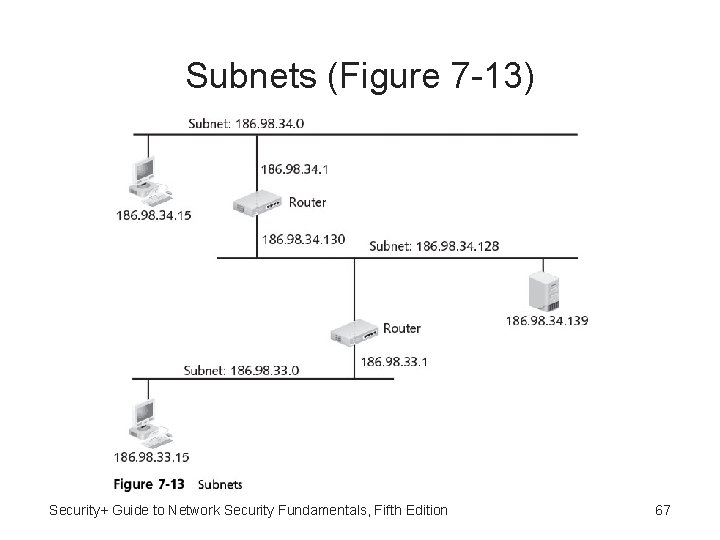
Subnetting • IP addresses are 32 -bit (4 -byte) addresses with network address and host address • Classful addressing - Split between the network and host portions on the boundaries between the bytes • Subnetting or subnet addressing - IP address split anywhere within its 32 bits • Instead of just having networks and hosts networks essentially can be divided into three parts: network, subnet, and host Security+ Guide to Network Security Fundamentals, Fifth Edition 66

Subnets (Figure 7 -13) Security+ Guide to Network Security Fundamentals, Fifth Edition 67

Subnetting Security • Each network can contain several subnets, and each subnet connected through different routers can contain multiple hosts • Subnets also can improve network security: – Single network into multiple smaller subnets in order to isolate groups of hosts – Allows network administrators to hide the internal network layout Security+ Guide to Network Security Fundamentals, Fifth Edition 68

Virtual LANs (VLAN) • Virtual LAN (VLAN) - Segment network by separating devices into logical groups • VLAN allows scattered users to be logically grouped together even though physically attached to different switches • Can reduce network traffic and provide a degree of security similar to subnetting • VLANs can be isolated so sensitive data is transported only to members of the VLAN • Switch or tagging protocol can be used Security+ Guide to Network Security Fundamentals, Fifth Edition 69

Remote Workers • Working away from the office commonplace today: – Telecommuters – Traveling sales representatives – Traveling workers • Strong security for remote workers must be maintained • Transmissions are routed through networks not managed by the organization Security+ Guide to Network Security Fundamentals, Fifth Edition 70

Remote Access • Remote access - Any combination of hardware and software that enables remote users to access local internal network • Remote access provides remote users with same access and functionality as local users through VPN or dial-up connection • Service includes support for remote connection and logon and then displays the same network interface as the normal network Security+ Guide to Network Security Fundamentals, Fifth Edition 71

Security+ Guide to Network Security Fundamentals, Fifth Edition Chapter 7 Network Security Fundamentals