Intrusion Detection Systems Intrusion Detection Systems 1980 Paper











- Slides: 19

Intrusion Detection Systems

Intrusion Detection Systems 1980 -Paper written detailing importance of audit data in detecting misuse + user behavior 1984 -SRI int’l develop method of tracking and analyzing of users of ARPANET, resulting 1 st IDS 1988 -Haystack project - IDS based on using defined patterns of misuse, resulting in Distributed IDS 1990 -Todd Heberlein - Network Security Monitor – 1 st network monitor, lots of interest leading to commercial development, leading to the IDS boom we see today.

What are Intrusion Detection Systems? p Not a firewall! Firewall is just that; a wall (allow/deny) p IDS is a monitoring system; it takes notes of what is going on, and reports it to someone else to deal with. p

What are Intrusion Detection Systems? Sensors -> report security events Console -> monitor events/alerts control sensors Engine -> logs events reported by sensor generate alerts based upon security rules Can have all 3 components in a single place

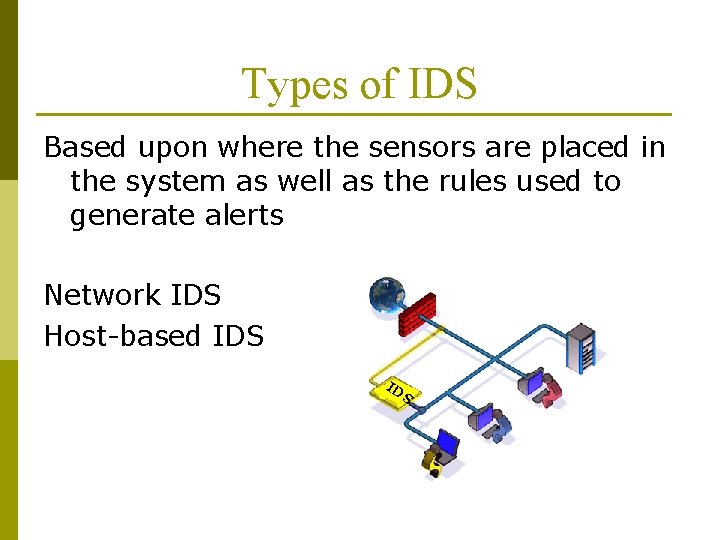
Types of IDS Based upon where the sensors are placed in the system as well as the rules used to generate alerts Network IDS Host-based IDS ID S

Network IDS p Ideally scan all, but not always practical p Examines network traffic connected to network device allowing port mirroring or network tap p Signature vs anomaly based

Network IDS Signature Based (knowledge based) most IDS are signature based p works like antivirus software – looks for attempts to exploit known vulnerabilities p This type is ineffective if an exploit type is unknown to the system p

Network IDS Anomaly based (behavior based) This type observes the deviation from “normal” behavior of the system. p Not vulnerable to new/unforeseen vulnerabilities p High “false positive” rate; requires a “learning phase” and subsequent “retraining” as network changes. p

Host based IDS p Host based Individual devices p Monitors PC – sys calls, app logs, file mods p Single device only! p Alerts user/admin if detected p

Hybrid IDS p Hybrid systems Can be combination of these systems p Such as host based + network based p n With the host reporting to the network based system for a more comprehensive protection

Passive VS Reactive IDS p Among the variety of “flavors” of IDS they can be categorized into two major groups: n Passive Systems work by simply monitoring, detecting and alerting n Reactive Systems perform any necessary action or actions to a detected threat

Passive IDS Monitors System for any suspicious or malicious intrusion p If found, evaluates it to determine whether it is a threat p If detected as so, generates and sends an I just found a alert to user threat, user p Up to the user to take action p

Reactive IDS Alerts console user and attempts to respond according to security rules/capabilities I found a threat and I’m p reprogram firewall taking care of it, oh yeah p reset connections p block IP addresses Typically called Intrusion Prevention System Essentially a firewall with network and application level filtering

IDS Evasion Techniques Closely related to network attack methods p Designed to avoid detection by the IDS p Some basic and commonly known methods to attack IDS are through: p n n n String matching weaknesses Session assembly weaknesses Denial of service techniques

String Matching Weaknesses Easiest to implement and understand p Most IDS strong dependency on string matching p Using variants, string manipulation techniques, and character substitution techniques so strings don’t match p Strings don’t match no threat is detected p

Session Assembly Weakness Works by dividing string across several packets p Data will be delivered a few bytes at the time with modified IP packets to evade string match p To defend IDS should fully understand session (difficult and processor intensive) p

Denial of Service Technique Characterized by preventing legitimate users of a service from using that service p Examples p n n n Consume device’s processing power Fill up disk space More alarms than can be handled by management systems Personnel not being able to investigate all the alarms Device lock up

Towards the Future IDS vendors and hardware will have to keep a pace with all the switched networks and traffic increases p The future of IDS lies in data correlation p n n p AI Data mining Future IDS, produce result by examining input from different sources

Conclusion Nearly every company dependent on Internet to survive, so IDS here to stay p Also as technology advances for new IDS so does the possibility of new threats p Security issues are always present p However promising future p n n Statistical Analysis Predictive AI