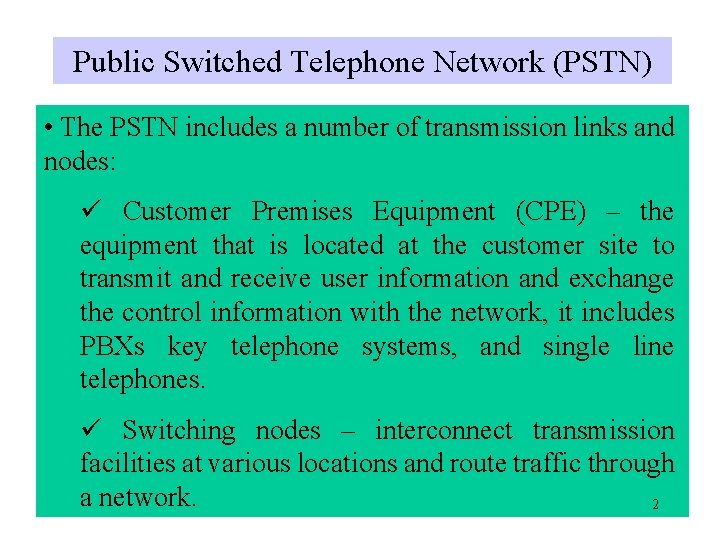
Reference Models THE OSI TCPIP REFERENCE MODELS 1



















- Slides: 96

Reference Models THE OSI & TCP/IP REFERENCE MODELS 1

Public Switched Telephone Network (PSTN) • The PSTN includes a number of transmission links and nodes: ü Customer Premises Equipment (CPE) – the equipment that is located at the customer site to transmit and receive user information and exchange the control information with the network, it includes PBXs key telephone systems, and single line telephones. ü Switching nodes – interconnect transmission facilities at various locations and route traffic through a network. 2

Public Switched Telephone Network (PSTN) (Continued. . ) üTransmission nodes – provide communication paths that carry user traffic and network control information between the nodes in the network, include the transmission media, transport equipment, amplifiers and/or repeaters, multiplexers and… ü Service nodes – handle signaling, which is the transmission of information to control the setup, holding, charging, and releasing of connections, as well as the transmission of information to control network operations and billing (SS 7) 3

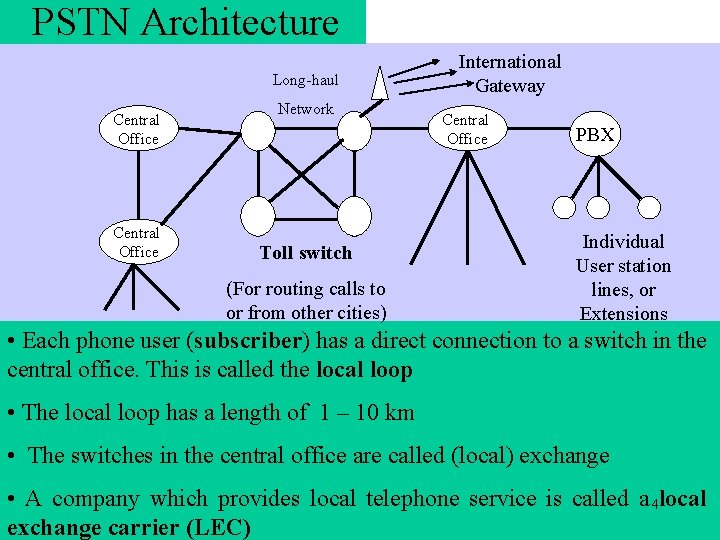
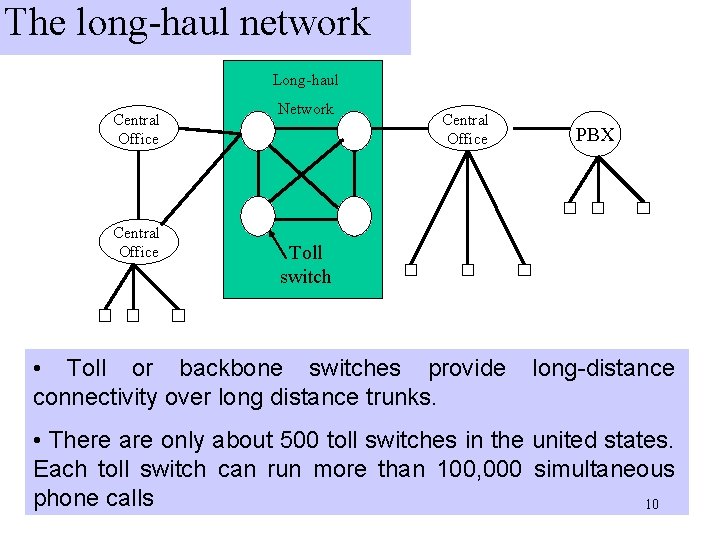
PSTN Architecture Long-haul Central Office Network Toll switch (For routing calls to or from other cities) International Gateway Central Office PBX Individual User station lines, or Extensions • Each phone user (subscriber) has a direct connection to a switch in the central office. This is called the local loop • The local loop has a length of 1 – 10 km • The switches in the central office are called (local) exchange • A company which provides local telephone service is called a 4 local exchange carrier (LEC)

How is voice transmitted? • Voice can be transmitted in two ways: – Analog voice transmission: each voice channel is allocated a bandwidth of 3. 5 k. Hz – Digital voice transmission: analog voice stream is converted in a digital stream: • Standard scheme for voice call: Obtain 8000 samples per second, each with length 8 bit 5

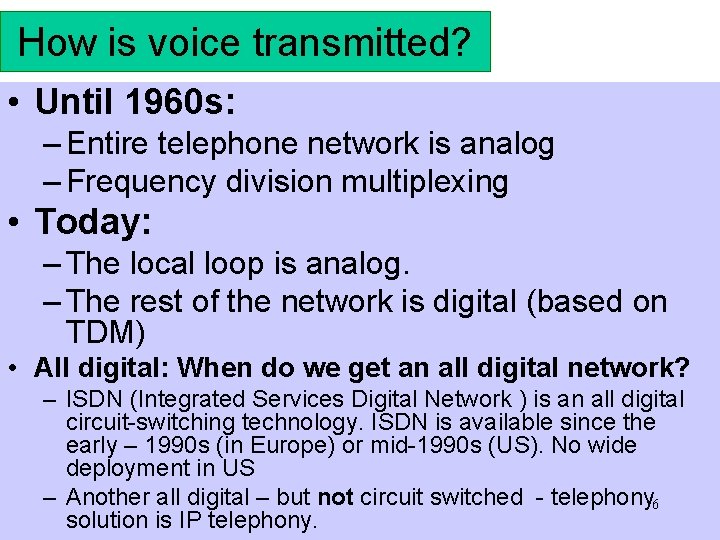
How is voice transmitted? • Until 1960 s: – Entire telephone network is analog – Frequency division multiplexing • Today: – The local loop is analog. – The rest of the network is digital (based on TDM) • All digital: When do we get an all digital network? – ISDN (Integrated Services Digital Network ) is an all digital circuit-switching technology. ISDN is available since the early – 1990 s (in Europe) or mid-1990 s (US). No wide deployment in US – Another all digital – but not circuit switched - telephony 6 solution is IP telephony.

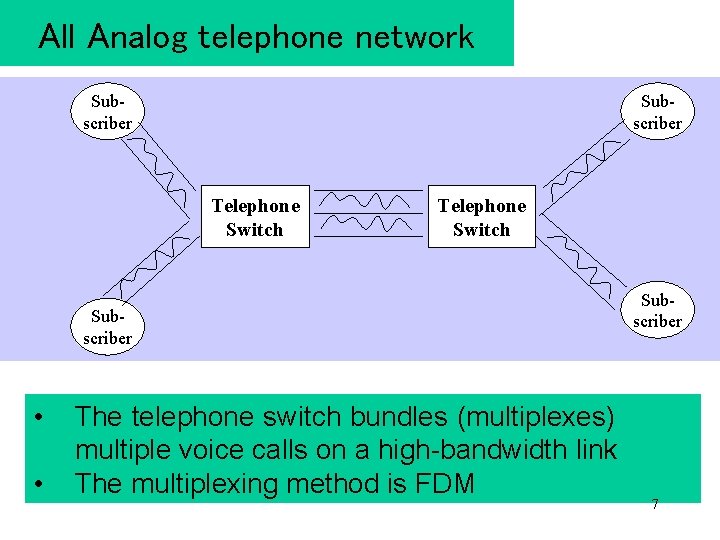
All Analog telephone network Subscriber Telephone Switch Subscriber • • The telephone switch bundles (multiplexes) multiple voice calls on a high-bandwidth link The multiplexing method is FDM Subscriber 7

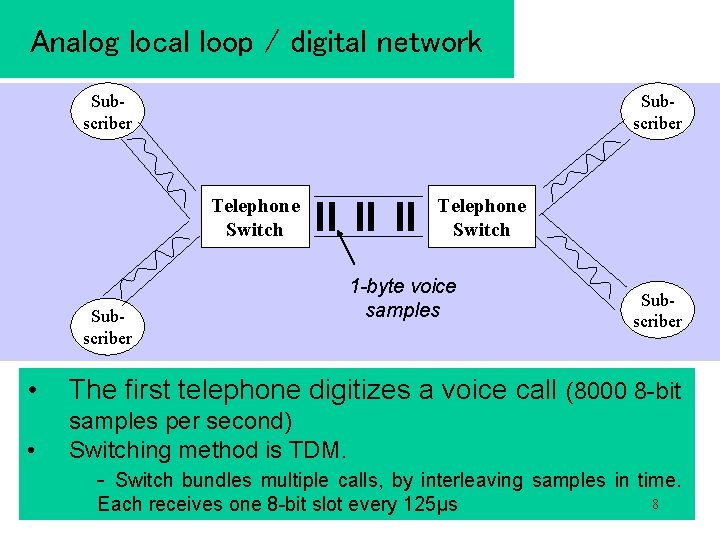
Analog local loop / digital network Subscriber Telephone Switch 1 -byte voice samples Subscriber • The first telephone digitizes a voice call (8000 8 -bit • samples per second) Switching method is TDM. - Switch bundles multiple calls, by interleaving samples in time. Each receives one 8 -bit slot every 125μs 8

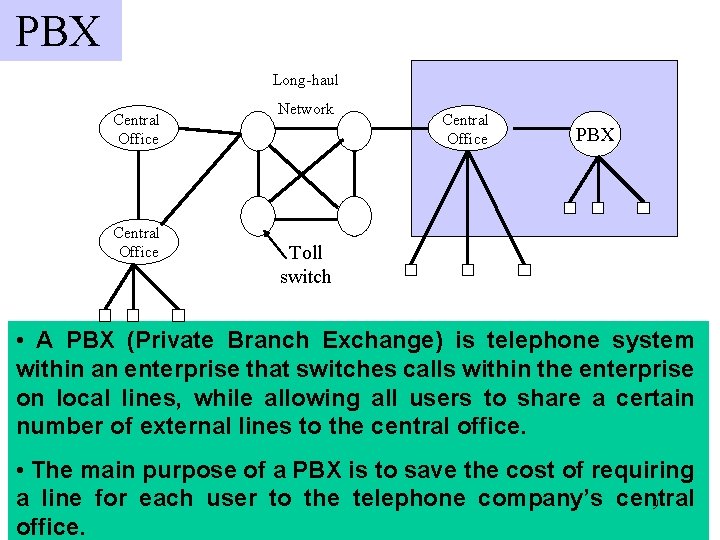
PBX Long-haul Central Office Network Central Office PBX Toll switch • A PBX (Private Branch Exchange) is telephone system within an enterprise that switches calls within the enterprise on local lines, while allowing all users to share a certain number of external lines to the central office. • The main purpose of a PBX is to save the cost of requiring a line for each user to the telephone company’s central 9 office.

The long-haul network Long-haul Central Office Network Central Office PBX Toll switch • Toll or backbone switches provide connectivity over long distance trunks. long-distance • There are only about 500 toll switches in the united states. Each toll switch can run more than 100, 000 simultaneous phone calls 10

Signaling Ø Signaling: exchange of messages among network entities to enable (provide service) to connection / call Ø Or the communication necessary to set up a call from one subscriber to another q Before, during, after connection/call o call setup and tear down o call maintenance o measurement, billing q Between: o end – user <-> network o network element <-> network element o end – user <-> end – user 11

Telephone network: services Ø point-to-point POTS calls Ø special telephone numbers: o 800 (888) number service: free call to customer o numbers for life Ø caller ID Ø calling card / third part charging Ø call routing (to end user): prespecified, by time-of-day Ø “follow me” service – allows you to select a temporary alternate phone on campus to receive your forwarded calls. Ø incoming/outgoing call restrictions Ø support for cellular roaming: “home” number routed to 12 current cell location

Intelligence in the network Ø Telephone companies are looking for providing intelligent services to their subscribers: forward, block, reverse the call charges and record messages. Ø Network programmability. Ø Competence by delivering value-added services Ø This competence led to the standardization of intelligent network architecture. Ø SS 7 – Metanetwork for signaling. 13

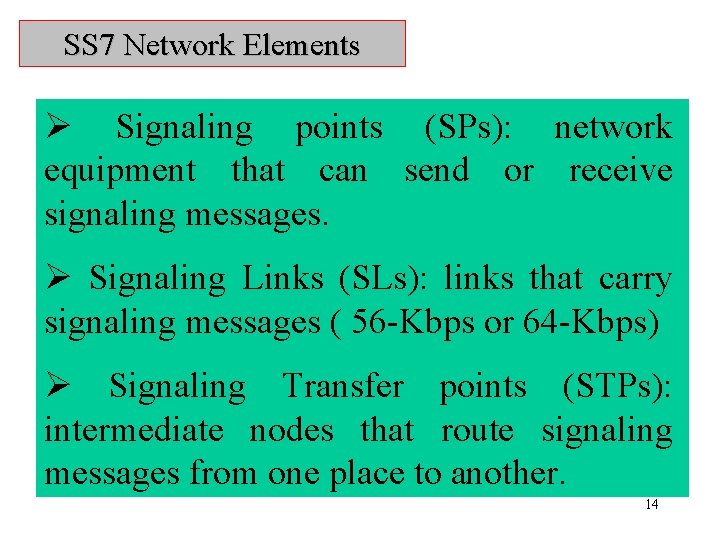
SS 7 Network Elements Ø Signaling points (SPs): network equipment that can send or receive signaling messages. Ø Signaling Links (SLs): links that carry signaling messages ( 56 -Kbps or 64 -Kbps) Ø Signaling Transfer points (STPs): intermediate nodes that route signaling messages from one place to another. 14

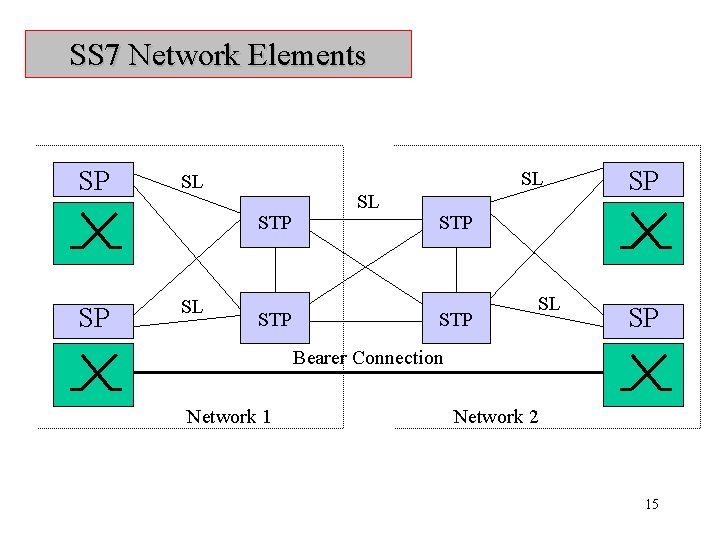
SS 7 Network Elements SP SL SL STP SP SL STP SL SP Bearer Connection Network 1 Network 2 15

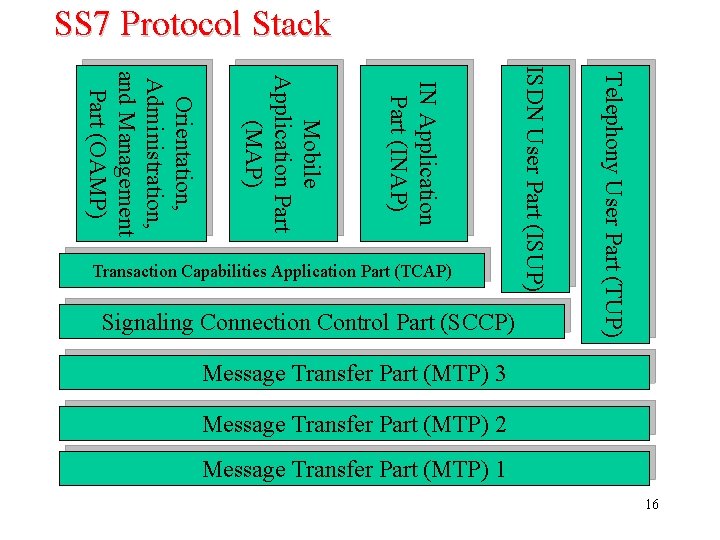
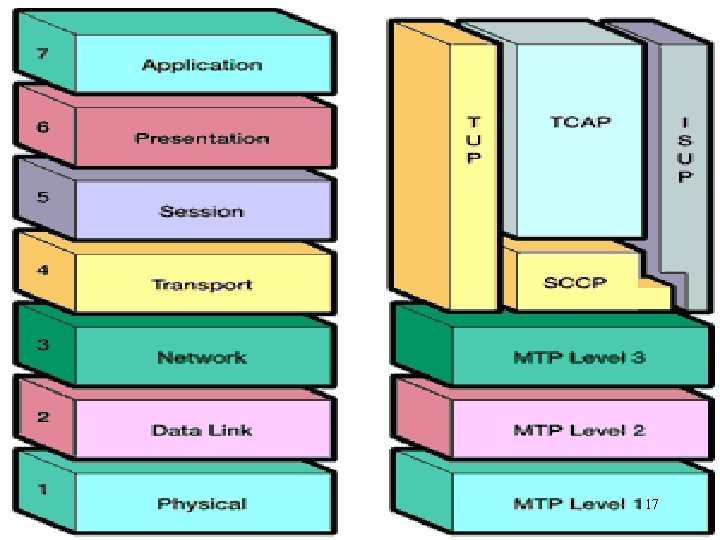
SS 7 Protocol Stack Telephony User Part (TUP) Signaling Connection Control Part (SCCP) ISDN User Part (ISUP) IN Application Part (INAP) Mobile Application Part (MAP) Orientation, Administration, and Management Part (OAMP) Transaction Capabilities Application Part (TCAP) Message Transfer Part (MTP) 3 Message Transfer Part (MTP) 2 Message Transfer Part (MTP) 1 16

17

SS 7 Protocol Stack (Cont. ) Ø Message Transfer Part 1 (MTP 1): Contains hardware and firmware resources (Network Cards, Transceivers, and Cables). Ø Message Transfer Part 2 (MTP 2): Responsible for secure transaction of messages between two signaling points. Ø Message Transfer Part 3 (MTP 3): Responsible for routing (Through STP). Ø Telephony User Part (TUP): Describes the signaling messages for the setup of calls and connections in analog telephony networks. Ø ISDN User Part (ISUP): Describes the signaling messages for the setup of calls and connections in Digital networks. 18

SS 7 Protocol Stack (Cont. ) Ø Signaling Connection Control Part (SCCP): Sets up and manages signaling connections, using MTP 3 to route messages reliably from one node to another. ü Supports both Connection-Oriented and Connectionless signaling contexts. ü Carries the information that STPs need to perform global title translation. (800 numbers, and number portability) Ø Transaction Capabilities Application Part (TCAP): allows signaling nodes to do transactions. (e. g. Database access). It contains two types of information: 1. Transaction Portion (starting and ending transactions & maintains the state of the dialog). 2. Component portion (carries the actual protocol queries 19 and responses).

SS 7 Protocol Stack (Cont. ) ØA TCAP message can carry the signaling message of other protocols in the component portion: Ø Operation, Administration, and Management Part (OAMP): verification network routing Database and diagnosing link problems. Ø Mobile Application Part (MAP): Responsible for Mobility management, GSM networks. Ø IN Application Part (INAP). 20

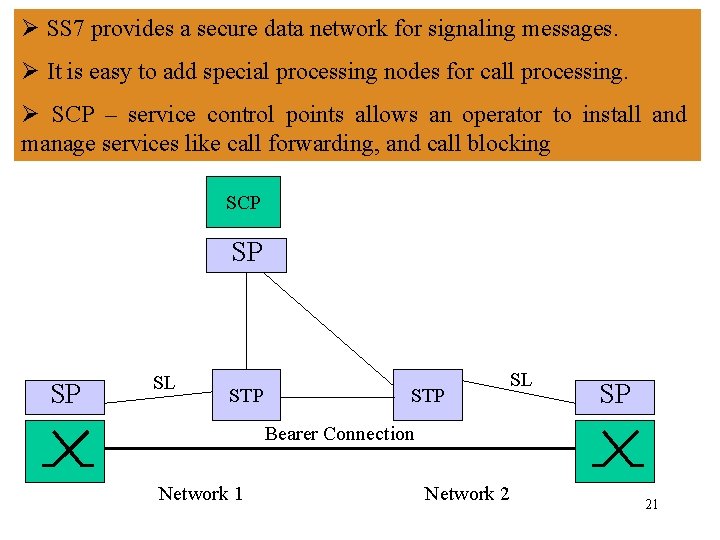
Ø SS 7 provides a secure data network for signaling messages. Ø It is easy to add special processing nodes for call processing. Ø SCP – service control points allows an operator to install and manage services like call forwarding, and call blocking SCP SP SP SL STP SL SP Bearer Connection Network 1 Network 2 21

IN Standardization & Implementation Problems: 1. Framework expanding all the time by nature. 2. Telephony switches offer more and more features with every release and new network. 3. Technology such as GSM and the Internet are constantly changing the environment that IN operates in. Assumptions: Ø Upward compatibility Ø IN – collection of dedicated computers that perform special control functions. Ø IN – software architecture that runs services. Ø IN – set of nodes as it is a software framework. 22

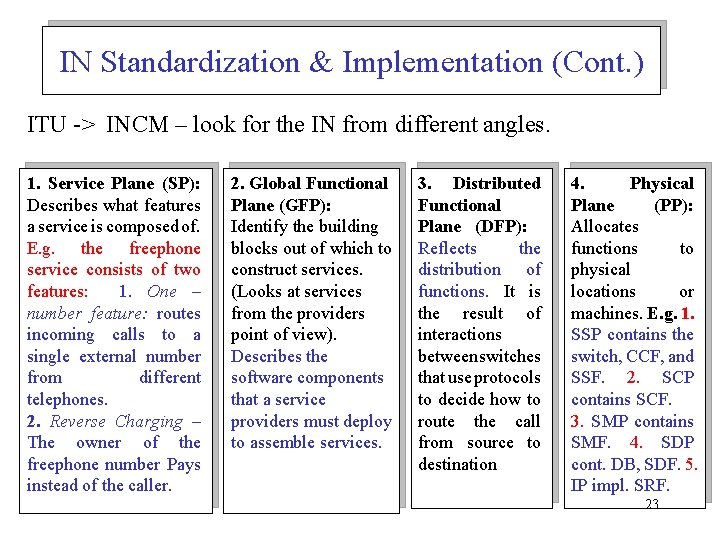
IN Standardization & Implementation (Cont. ) ITU -> INCM – look for the IN from different angles. 1. Service Plane (SP): Describes what features a service is composed of. E. g. the freephone service consists of two features: 1. One – number feature: routes incoming calls to a single external number from different telephones. 2. Reverse Charging – The owner of the freephone number Pays instead of the caller. 2. Global Functional Plane (GFP): Identify the building blocks out of which to construct services. (Looks at services from the providers point of view). Describes the software components that a service providers must deploy to assemble services. 3. Distributed Functional Plane (DFP): Reflects the distribution of functions. It is the result of interactions between switches that use protocols to decide how to route the call from source to destination 4. Physical Plane (PP): Allocates functions to physical locations or machines. E. g. 1. SSP contains the switch, CCF, and SSF. 2. SCP contains SCF. 3. SMP contains SMF. 4. SDP cont. DB, SDF. 5. IP impl. SRF. 23

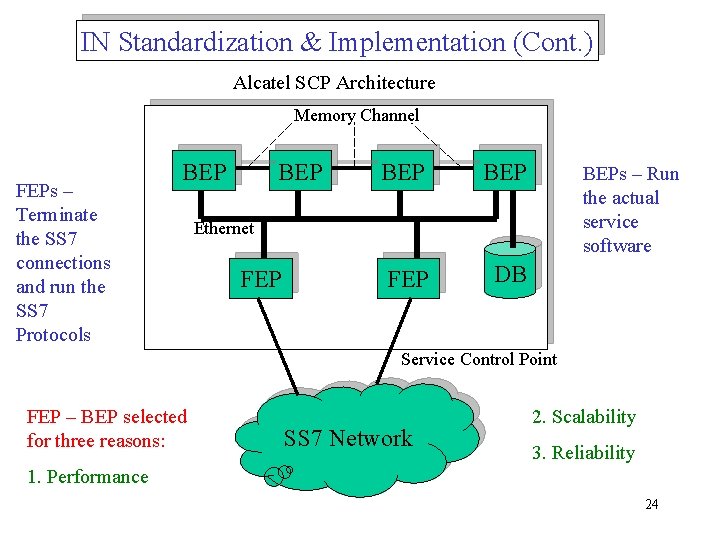
IN Standardization & Implementation (Cont. ) Alcatel SCP Architecture Memory Channel FEPs – Terminate the SS 7 connections and run the SS 7 Protocols BEP BEP FEP DB BEPs – Run the actual service software Ethernet FEP Service Control Point FEP – BEP selected for three reasons: SS 7 Network 2. Scalability 3. Reliability 1. Performance 24

IN and the Internet Ø Many operators and manufacturers already started making their IN platforms Internet ready with proprietary solutions. 1. IP, the Internet, and the Web 2. Routers and Gateways: hubs, bridges, routers, gateways, firewalls. 3. Connecting to the Internet using modems via an ISPs. 4. ISDN 5. ADSL, VDSL, and DHN 6. Satellite Networks, LEO 7. Cellular Networks: GSM, GPRS 25

Intelligence on the Internet IN and The Internet Ø The internet is a network of networks. Ø Not administered by a central operator Ø Invented for data communication not for voice communication Ø Communications achieved by the routing packets of data Ø IP addresses and telephone numbers are differ on format, scope, and the way that they are assigned. IP Networks have almost the intelligence on the application layer Ø The Features in IN are centralized and controlled from the SCF. In the Internet they are completely distributed through the network. Ø Some IN features do not make sense in the Internet: freephone, calling card calls Ø All of this changes when we use the Internet Infrastructure for telephony. 26

Intelligence on the Internet IN and The Internet Voice, Video, and Multimedia over the Internet Ø TCP/IP – Designed for communicating data (files, e-mail, web pages) between servers and clients. It breaks the data up into packets and routs them to their destination, where they are reassembled and passed to the receiving application. Ø Voice and video could be translated into bits using codecs, IP routers should be able to deal with it as they do the routing of a file or a web page. Ø H 323 is the standard for providing Voice and Multimedia services over packet networks. Can involve the following components: Gateways, Gatekeepers (address translation, call authorization, accounting and billing, call management), Multipoint Control Units. 27

The Mobile Dimension Three types of mobility in telecommunications: 1. Terminal mobility: the terminal is connected to the network via radio interface and can move around freely (e. g. cordless and cellular phones) 2. User mobility: the user can move from one terminal to another and register for incoming and outgoing calls to be made to and from this terminal. (e. g. calling cards) 3. Service mobility: the portfolio of services that a user has subscribed to follows the user as he or she roams to different networks (the concept of exporting content and service to visited location) 28

Cellular Networks The Mobile Dimension Types of Terminal Mobility Networks: • Cordless: DECT, CT 2, … • Cellular: GSM, DAMPS, … • Satellite: LEO – EUTELSAT, … GEO – SKYBRIDGE, … A cellular network employs many radio cells of limited coverage to cover a large area that gives the following advantages: 1. A mobile phone is always close to a network transceiver, needs less transmission power. 2. channels can be reused in different cells, the capacity of 29 network increases as the cell size shrinks.

Cellular Networks Generations The Mobile Dimension First Generation (1 G): 1980 – analog cellular networks (e. g. AMPS – USA, NMT – Scandinavia, C-450 – Germany, RTMS - France). Second Generation (2 G): 1990 – digital transmission, higher capacity, Better standardization (e. g. GSM, DAMPS, IS-95, PDC). Third Generation (3 G): 2000 – Multimedia communications, Mobile Internet, Capacity & services (e. g. GPRS, UMTS) 30

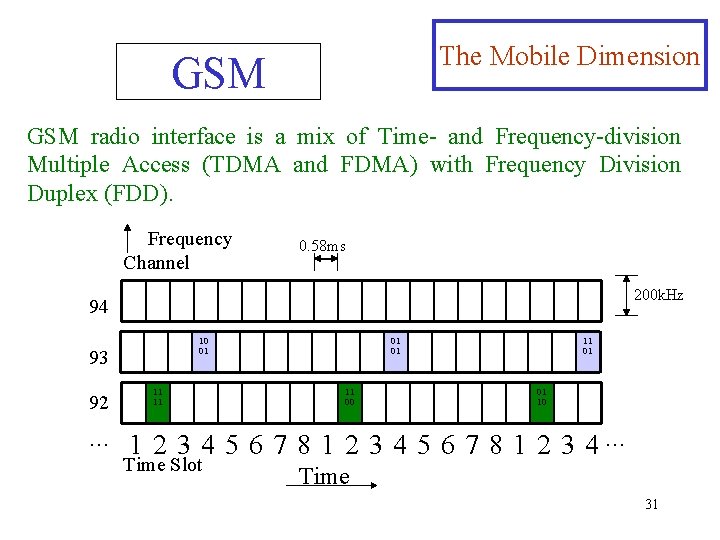
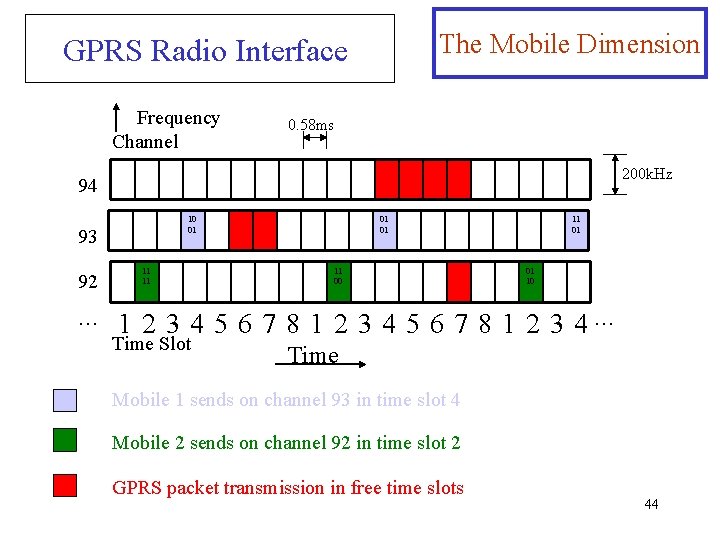
The Mobile Dimension GSM radio interface is a mix of Time- and Frequency-division Multiple Access (TDMA and FDMA) with Frequency Division Duplex (FDD). Frequency Channel 0. 58 ms 200 k. Hz 94 10 01 93 92 … 11 11 01 01 11 00 11 01 01 10 1 2 3 4 5 6 7 8 1 2 3 4… Time Slot Time 31

GSM Architecture The Mobile Dimension A GSM network consists of three components: 1. Mobile Station (MS): GSM network terminals, they connect to the network through a radio interface and require processing power. 2. Base Station Subsystem (BSS): consists of a base station controller (BSC) and base transceiver stations (BTS). 3. Network Switching Subsystem (NSS): the core network part of the GSM, the key component in NSS is the Mobile Switch Center (MSC); A Visited Location Register database (VLR) – holds the subscriber data for visiting subscribers; A home Location Register database (HLR) – holds the essential subscriber information including information about the VLR to which a 32 subscriber is currently attached.

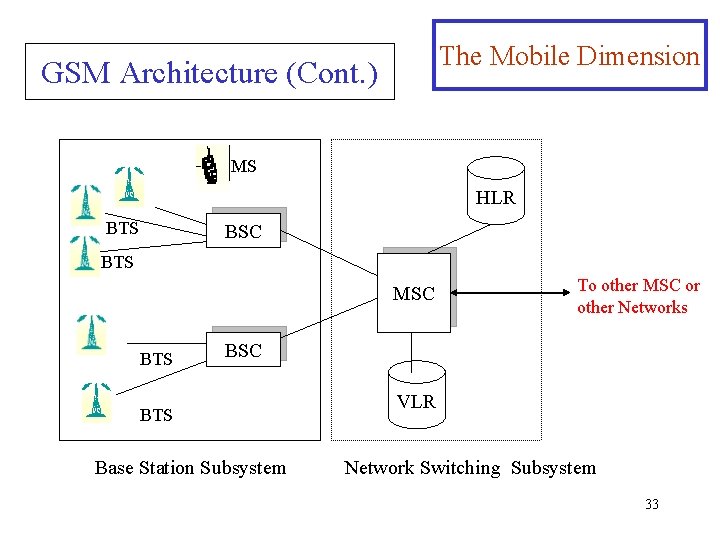
The Mobile Dimension GSM Architecture (Cont. ) MS HLR BTS BSC BTS MSC BTS To other MSC or other Networks BSC BTS Base Station Subsystem VLR Network Switching Subsystem 33

Mobility Management and Handover The Mobile Dimension Ø Procedures that enable mobile terminal when a call arrives. Ø GSM is divided into location areas, each area covers several radio cells and has a unique identifier transmitted on a special channel in all the cells it contains. Ø Each mobile monitors this channel. When it detects a change in the broadcast location area identifier (LAI), the mobile terminal knows it has crossed into another location area’s radio cell. at that time it requests a 34 location update from the network.

Mobility Management and Handover (Continued) The Mobile Dimension Two ways that a location update can take place: 1. If the new location area is served by the same MSC and VLR, then the VLR registers the move. 2. If the new location area is served by the another MSC and VLR, then the mobile subscriber information is moved from the old to the new VLR. The HLR is also updated so that it can rout all incoming calls to the new MSC and VLR as follows: 35

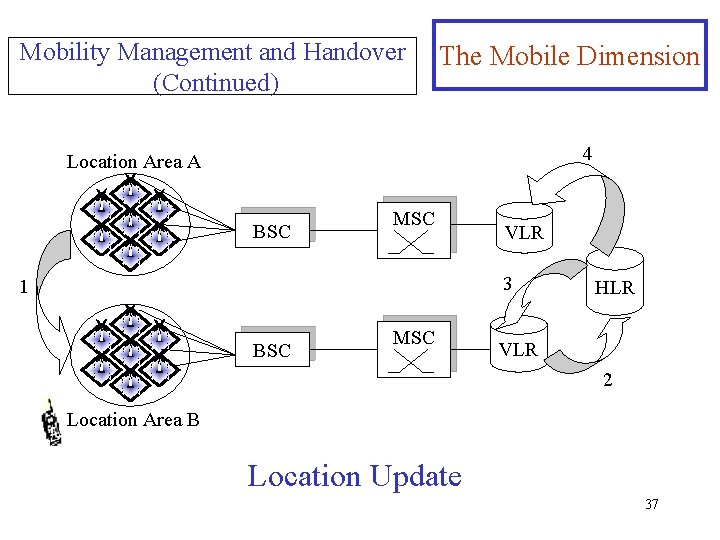
Mobility Management and Handover (Continued) The Mobile Dimension 1. The mobile terminal moves into a new cell, notice that the location identifier for this cell is different, and requests a location update. 2. The VLR requests the subscriber information from the HLR. 3. The HLR sends the subscriber information to the VLR and registers that the subscriber is now attached to the new VLR. 4. The HLR informs the old network of the move and orders the old VLR to remove the record for this 36 subscriber.

Mobility Management and Handover (Continued) The Mobile Dimension 4 Location Area A BSC MSC VLR 3 1 BSC MSC HLR VLR 2 Location Area B Location Update 37

Mobility Management and Handover (Continued) The Mobile Dimension Handover: When the network and the mobile terminal perceive a decline in quality of the current connection, the network will look for a better channel in a neighboring cell. The mobile terminal must be detached in real time from the radio channel of the old cell and attached to the new channel in the new cell. 38

GSM Security The Mobile Dimension Ø A subscriber identity module (SIM) stores the GSM subscription. Ø Each subscription has a unique identifier, the international mobile subscriber identity (IMSI). Ø The dialed number is called the mobile station ISDN number (MS-ISDN). Ø The HLR stores the mapping from MS-ISDN to IMSI. Ø The network authenticates the SIM in the mobile terminal using a secret key algorithm. The visited network will request a location update by sending the mobile station 39 roaming number (MSRN) to the HLR.

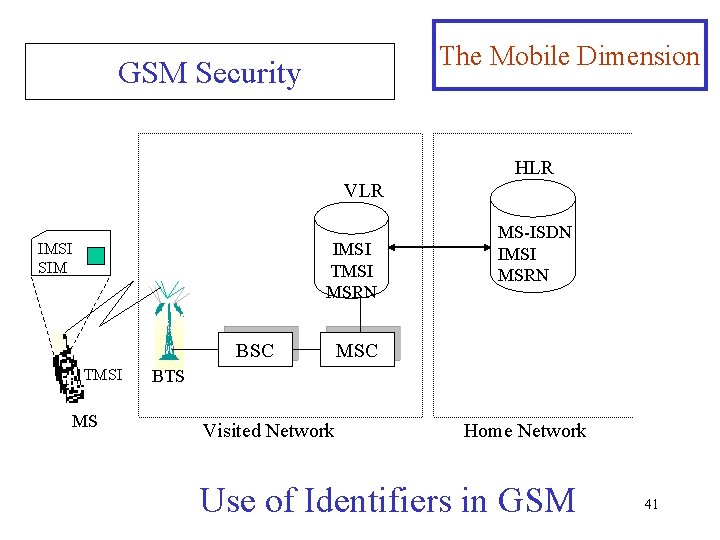
GSM Security (Continued) The Mobile Dimension Ø The MSRN is an identifier composed of the IMSI and the LAI of the cell where the mobile terminal is located. Ø The VLR assigns a temporary identifier for the mobile terminal that is locally unique, the temporary mobile station identifier (TMSI). It is much shorter than IMSI and prevents the IMSI from being sent over the air frequently. Ø The VLR stores the relationship between IMSI and TMSI, and also keep track of the location area of the mobile terminal in the form of the MSRN Ø when the call is established, the exchange of the digital voice is encrypted using the same secret key as for 40 authentication, but using a different algorithm.

The Mobile Dimension GSM Security HLR VLR IMSI TMSI MSRN IMSI SIM BSC TMSI MS MS-ISDN IMSI MSRN MSC BTS Visited Network Home Network Use of Identifiers in GSM 41

GSM Connection Services The Mobile Dimension GSM provides the following services: 1. Basic voice (using 13 kbps codec) 2. Half - rate voice (using 6. 5 kbps codecs) 3. Circuit Switched data connection (9. 6 kbps) 4. SMS (Store-and-forward Messages of 160 characters) 5. Cell broadcast (93 characters) 6. USSD – transfer of service data between mobile terminal and HLR. 42

General Packet Radio Service (GPRS) The Mobile Dimension Ø GPRS deployed by operators that already have a GSM network; it is implemented as an extension of the existing GSM infrastructure. GPRS Radio Interface Ø GPRS occupies free time slots only when a packet is sent or received in a dynamic way. Ø The maximum number of time slots that a terminal can handle is called mutlislot class of the terminal. It depends on the processing power and radio interface hardware in 43 the terminal.

The Mobile Dimension GPRS Radio Interface Frequency Channel 0. 58 ms 200 k. Hz 94 10 01 93 92 … 11 11 01 01 11 00 11 01 01 10 1 2 3 4 5 6 7 8 1 2 3 4… Time Slot Time Mobile 1 sends on channel 93 in time slot 4 Mobile 2 sends on channel 92 in time slot 2 GPRS packet transmission in free time slots 44

GPRS Radio Interface (continued) The Mobile Dimension Ø Many terminals support more slots for the downlink than for the uplink. Ø Most terminal multislot classes commercially available are 4+1, 3+1, …, and 2+2. Ø The data rate depends on the number of slots and the coding scheme employed to map the data packets on the channel bit stream. Ø The most frequently used scheme offers 13. 4 kbps per time slot. 45

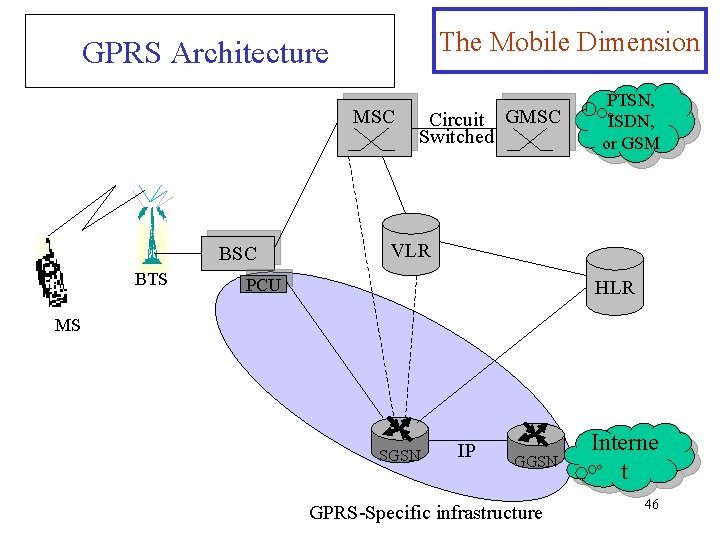
The Mobile Dimension GPRS Architecture MSC BTS Circuit GMSC Switched PTSN, ISDN, or GSM VLR PCU HLR MS SGSN IP GGSN GPRS-Specific infrastructure Interne t 46

GPRS Architecture The Mobile Dimension Ø Installing GPRS requires software updates in the BTS, MSC, VLR, and HLR. Ø The BSC needs to extend with a Packet Control Unit (PCU), which inserts the packet data traffic into the GSM channel structure. Ø GPRS core network contains: 1. The serving GPRS support node (SGSN), which routs the packets to and from the mobile terminals. 2. The Gateway GPRS support node (GGSN), which acts as the gateway to the external packet 47 network.

GPRS Mobility Management The Mobile Dimension Ø The GPRS network is divided into routing areas, to find a compromise between notifying the network of each cell change and the broadcasting of packets for each subscriber to the whole network. Ø The routing area is the same as, or a subset of , a location area. This gives the following advantages to the GSM-GPRS subscribers: 1. GSM updates automatically imply routing area updates. 2. An incoming GSM call can be paged in the GPRS routing area. Which is smaller than a location area that means less use of radio resources for paging. 48

GPRS Mobility Management The Mobile Dimension ATTACHMENT AND DETACHMENT PROCEDURE Ø Before a mobile station can use GPRS services, it must register with an SGSN of the GPRS network. The network checks if the user is authorized, copies the user profile from the HLR to the SGSN, and assigns a packet temporary mobile subscriber identity (P-TMSI) to the user. This procedure is called GPRS attach. Ø For mobile stations using both circuit switched and packet switched services it is possible to perform combined GPRS/IMSI attach procedures. The disconnection from the GPRS network is called GPRS detach. It can be initiated by the mobile station or by the network (SGSN or HLR). 49

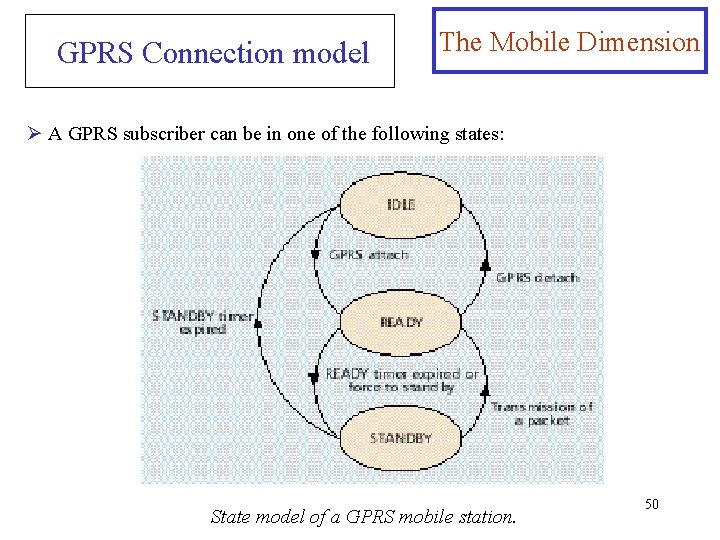
GPRS Connection model The Mobile Dimension Ø A GPRS subscriber can be in one of the following states: State model of a GPRS mobile station. 50

GPRS Connection model (Continued) The Mobile Dimension Ø In IDLE state the MS is not reachable. Performing a GPRS attach, the MS gets into READY state. With a GPRS detach it may disconnect from the network and fall back to IDLE state. All PDP contexts will be deleted. Ø The STANDBY state will be reached when an MS does not send any packets for a longer period of time, and therefore the READY timer (which was started at GPRS attach) expires. Ø An MS in READY state informs its SGSN of every movement to a new cell. 51

GPRS Connection model (Continued) The Mobile Dimension Ø For the location management of an MS in STANDBY state, a GSM location area (LA) is divided into several routing areas (RA). In general, an RA consists of several cells. The SGSN will only be informed when an MS moves to a new RA; cell changes will not be disclosed. To find out the current cell of an MS in STANDBY state, paging of the MS within a certain RA must be performed. 52

GPRS Connection model (Continued) The Mobile Dimension Ø For MSs in READY state, no paging is necessary. Whenever an MS moves to a new RA, it sends a “routing area update request” to its assigned SGSN. The message contains the routing area identity (RAI) of its old RA. The base station subsystem (BSS) adds the cell identifier (CI) of the new cell, from which the SGSN can derive the new RAI. 53

GPRS Connection model (Continued) The Mobile Dimension To exchange data packets with external PDNs after a successful GPRS attach, a mobile station must apply for one or more addresses used in the PDN, e. g. , for an IP address in case the PDN is an IP network. This address is called PDP address (Packet Data Protocol address). For each session, a so-called PDP context is created, which describes the characteristics of the session. It contains the PDP type (e. g. , IPv 4), the PDP address assigned to the mobile station (e. g. , 129. 187. 222. 10), the requested Qo. S, and the address of a GGSN that serves as the access point to the PDN. This context is stored in the MS, the SGSN, and the GGSN. With an active PDP context, the mobile station is “visible” for the external PDN and is able to send and receive data packets. The mapping between the two addresses, PDP and IMSI, enables the GGSN to transfer data packets between PDN and MS. A user may have several simultaneous PDP contexts 54 active at a given time.

Parlay & OSA Distributed Intelligence Ø Intelligent networks were originally designed for telephony networks. Ø Services are controlled and managed centrally by the network operator. Ø The IN model doesn’t seem prepared to deliver value -added services in an environment that is becoming heterogeneous and competitive. Ø Several industry initiatives sought to develop more state-of-the art software architectures for service deployment and operation. 55

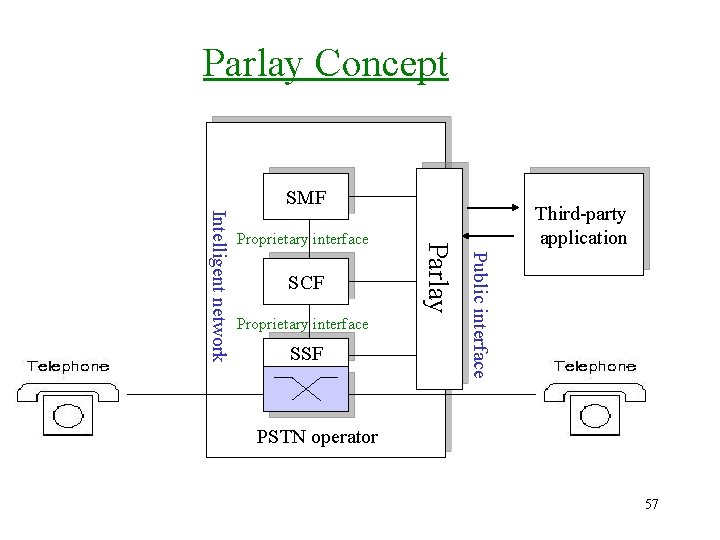
Parlay & OSA (cont. ) Distributed Intelligence Ø Parlay & OSA appear to be the technologies that are leading the way in the evolution of IN – the key concept in both is the distribution of service control. Parlay Concept Ø The network provider is responsible for deploying, operating, and managing services. Ø The idea of Parlay is to open this interface to third parties, so that others beside the network operator can create and deploy services. 56

Parlay Concept SMF Proprietary interface SSF Public interface SCF Parlay Intelligent network Proprietary interface Third-party application PSTN operator 57

Parlay Concept (cont. ) Distributed Intelligence Ø The Parlay interface also allows access to other network functionalities, such as messaging, charging, Qo. S negotiation, and mobility management. Ø Network access to third-party applications is subject to authentication and authorization. Ø Parlay allow the network provider to set different privilege levels (e. g. some third-party applications can be allowed to receive only notifications from the network while others can control calls and connections) Ø Parlay also provides facilities for nonrepudiation. 58

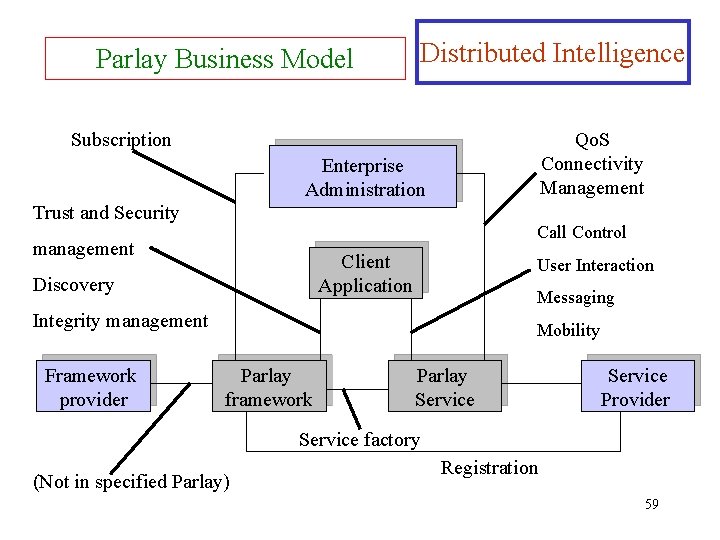
Parlay Business Model Distributed Intelligence Subscription Qo. S Connectivity Management Enterprise Administration Trust and Security Call Control management Client Application Discovery User Interaction Messaging Integrity management Framework provider Mobility Parlay framework Parlay Service Provider Service factory (Not in specified Parlay) Registration 59

Parlay Business Model Distributed Intelligence Ø Client Application: the third-party application that accesses network features through Parlay interface. (deployed and operated by the enterprise administration) Ø Framework Interfaces: offer all support functions for Parlay, in particular security and management features (administered by the service provider) Ø Service Interfaces: offer access to network features, such as call control, messaging, and mobility management (administered by the service provider) 60

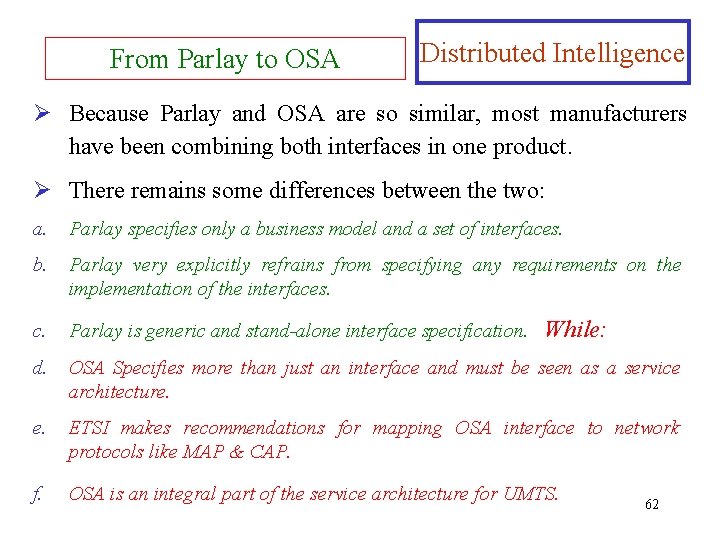
Parlay Business Model Distributed Intelligence Ø Parlay wanted to ensure complete flexibility in mapping Parlay business roles into real-world physical entities. Ø Parlay allows the provider of the framework interface to be different from the provider of the service interface. From Parlay to OSA Ø At the same time that Parlay began gaining momentum, 3 GPP and ETSI were working on the OSA interfaces for UMTS. 61

From Parlay to OSA Distributed Intelligence Ø Because Parlay and OSA are so similar, most manufacturers have been combining both interfaces in one product. Ø There remains some differences between the two: a. Parlay specifies only a business model and a set of interfaces. b. Parlay very explicitly refrains from specifying any requirements on the implementation of the interfaces. c. Parlay is generic and stand-alone interface specification. d. OSA Specifies more than just an interface and must be seen as a service architecture. ETSI makes recommendations for mapping OSA interface to network protocols like MAP & CAP. f. OSA is an integral part of the service architecture for UMTS. While: 62

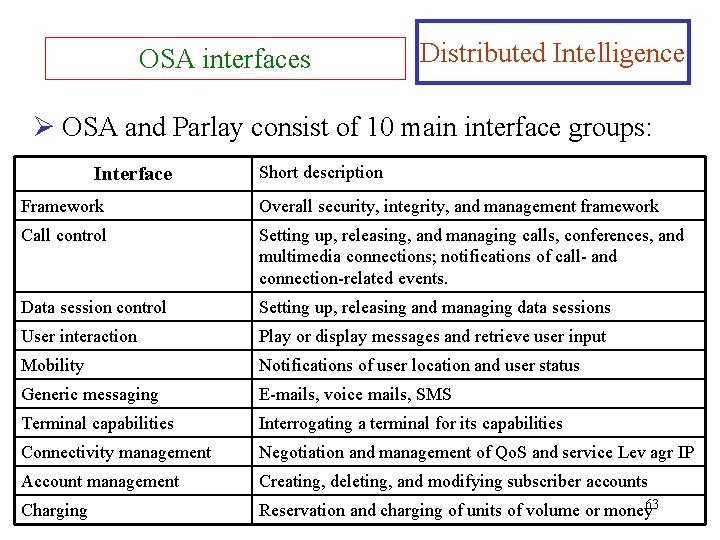
OSA interfaces Distributed Intelligence Ø OSA and Parlay consist of 10 main interface groups: Interface Short description Framework Overall security, integrity, and management framework Call control Setting up, releasing, and managing calls, conferences, and multimedia connections; notifications of call- and connection-related events. Data session control Setting up, releasing and managing data sessions User interaction Play or display messages and retrieve user input Mobility Notifications of user location and user status Generic messaging E-mails, voice mails, SMS Terminal capabilities Interrogating a terminal for its capabilities Connectivity management Negotiation and management of Qo. S and service Lev agr IP Account management Creating, deleting, and modifying subscriber accounts Charging Reservation and charging of units of volume or money 63

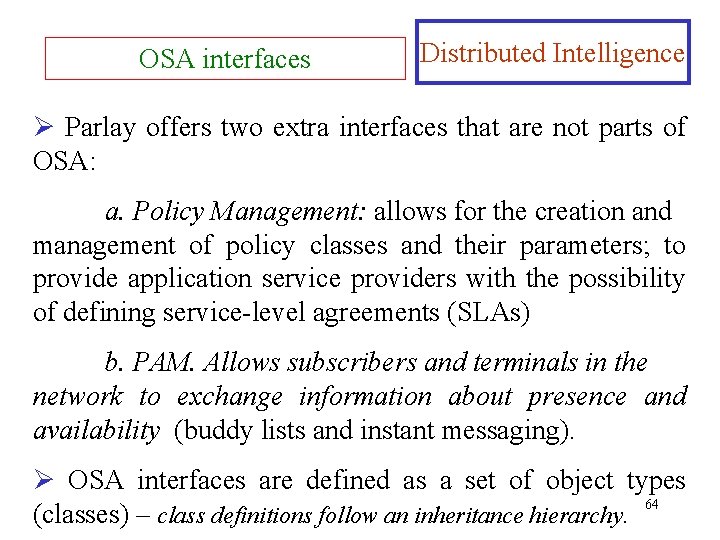
OSA interfaces Distributed Intelligence Ø Parlay offers two extra interfaces that are not parts of OSA: a. Policy Management: allows for the creation and management of policy classes and their parameters; to provide application service providers with the possibility of defining service-level agreements (SLAs) b. PAM. Allows subscribers and terminals in the network to exchange information about presence and availability (buddy lists and instant messaging). Ø OSA interfaces are defined as a set of object types (classes) – class definitions follow an inheritance hierarchy. 64

OSA interfaces Distributed Intelligence Ø Each of the OSA interfaces is specified (in UML and IDL) in four parts: 1. Class diagrams. Provide an overview of the inheritance structure of the interface, its classes and operations. 2. Sequence diagrams. Show key examples of use of the interface in the form of UML message sequence charts. 3. Interface specifications. Provide the formal definition of the interface 4. Data definitions. Provide formal data-type definition in IDL. 65

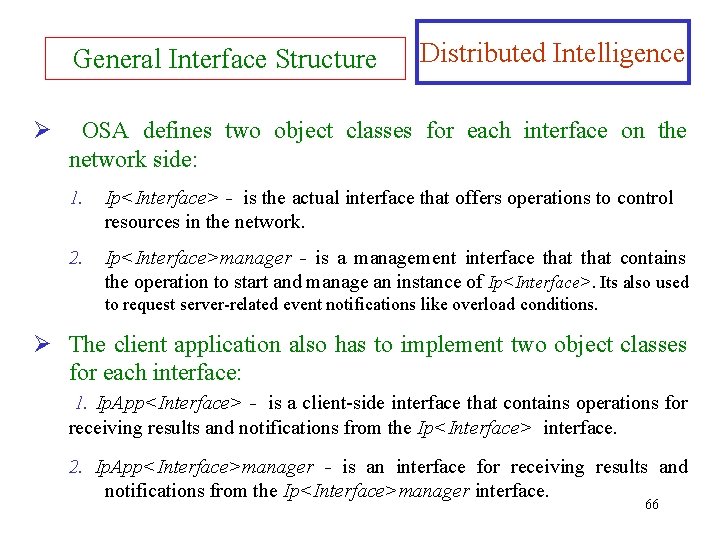
General Interface Structure Ø Distributed Intelligence OSA defines two object classes for each interface on the network side: 1. Ip<Interface> - is the actual interface that offers operations to control resources in the network. 2. Ip<Interface>manager - is a management interface that contains the operation to start and manage an instance of Ip<Interface>. Its also used to request server-related event notifications like overload conditions. Ø The client application also has to implement two object classes for each interface: 1. Ip. App<Interface> - is a client-side interface that contains operations for receiving results and notifications from the Ip<Interface> interface. 2. Ip. App<Interface>manager - is an interface for receiving results and notifications from the Ip<Interface>manager interface. 66

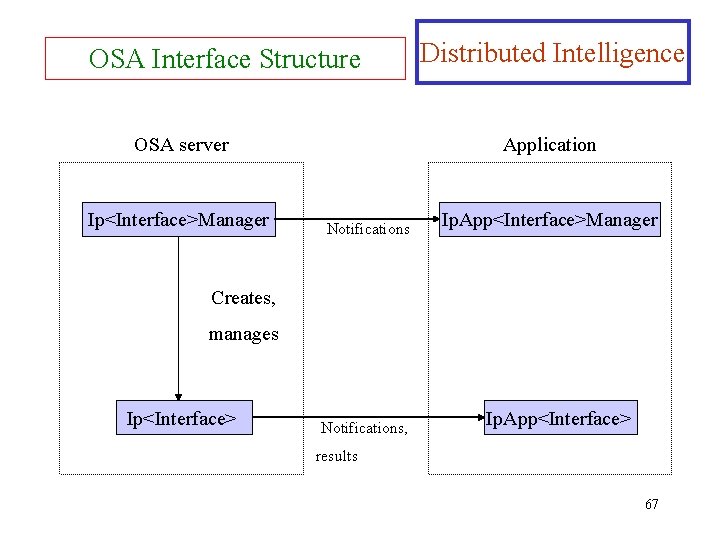
OSA Interface Structure OSA server Ip<Interface>Manager Distributed Intelligence Application Notifications Ip. App<Interface>Manager Creates, manages Ip<Interface> Notifications, Ip. App<Interface> results 67

General Interface Structure Distributed Intelligence Ø These client-side interfaces are often called callback interfaces – they are just like procedure calls in programming languages such as Pascal, operations on objects are synchronous: a client application that requests an operation on an object has to wait for this operation to finish and send back the result. Ø By putting a callback interface on the client it is possible to decouple the delivery of the result from the request. Ø Callbacks are used to allow asynchronous communication with synchronous operations. 68

OSA call-control interface Distributed Intelligence Ø OSA offers several interfaces for call control, some of these interfaces consist of several classes with an inheritance relation. Ø The figure below shows the inheritance structure (the main classes defined at the server side) Ø A new object class is defined in a terms of an existing one by inheriting and extending the operations of the parent class 69

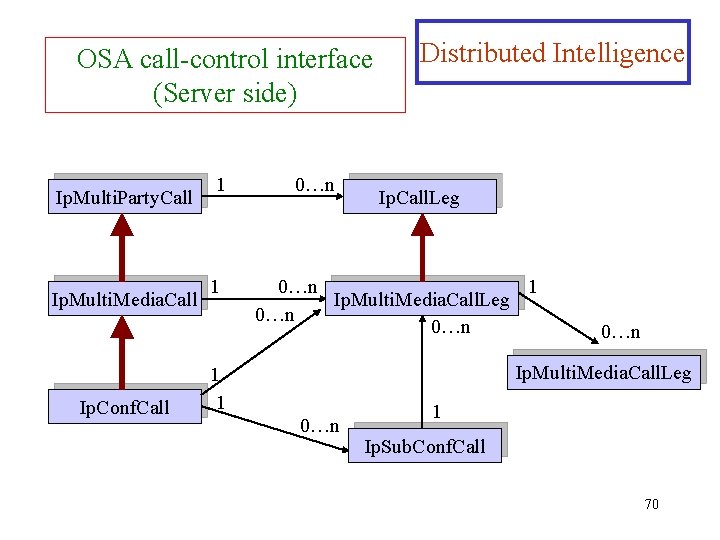
OSA call-control interface (Server side) Ip. Multi. Party. Call Ip. Multi. Media. Call Ip. Conf. Call 1 1 0…n Distributed Intelligence Ip. Call. Leg 0…n 1 Ip. Multi. Media. Call. Leg 0…n 0…n Ip. Multi. Media. Call. Leg 1 1 0…n 1 Ip. Sub. Conf. Call 70

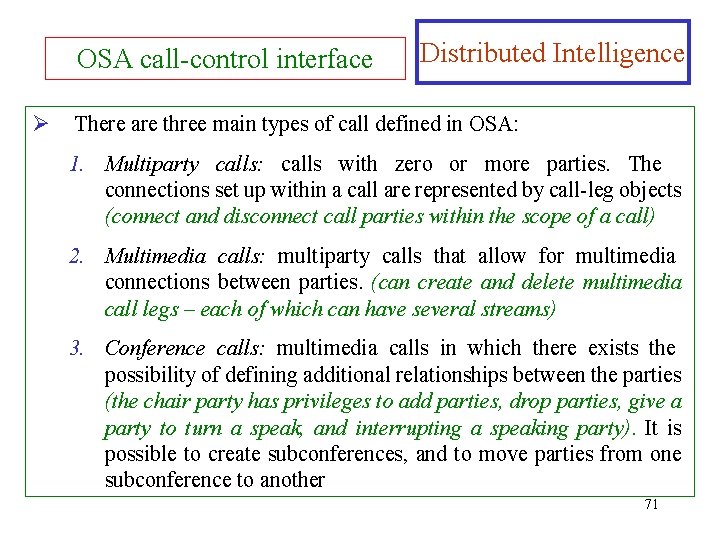
OSA call-control interface Ø Distributed Intelligence There are three main types of call defined in OSA: 1. Multiparty calls: calls with zero or more parties. The connections set up within a call are represented by call-leg objects (connect and disconnect call parties within the scope of a call) 2. Multimedia calls: multiparty calls that allow for multimedia connections between parties. (can create and delete multimedia call legs – each of which can have several streams) 3. Conference calls: multimedia calls in which there exists the possibility of defining additional relationships between the parties (the chair party has privileges to add parties, drop parties, give a party to turn a speak, and interrupting a speaking party). It is possible to create subconferences, and to move parties from one subconference to another 71

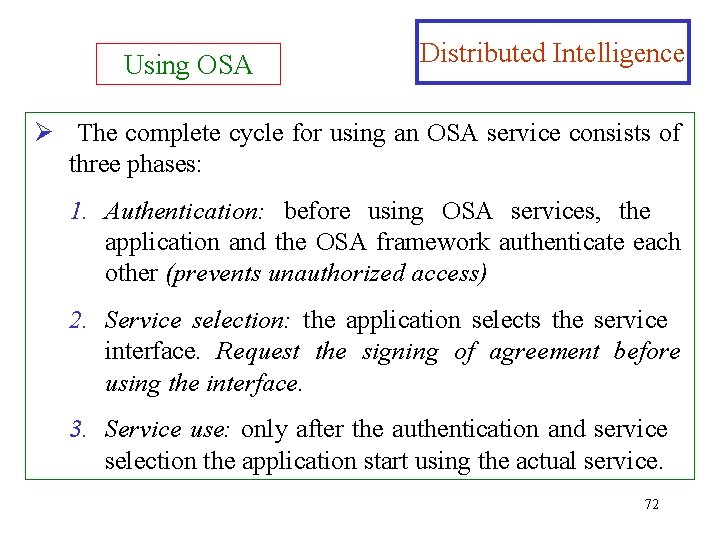
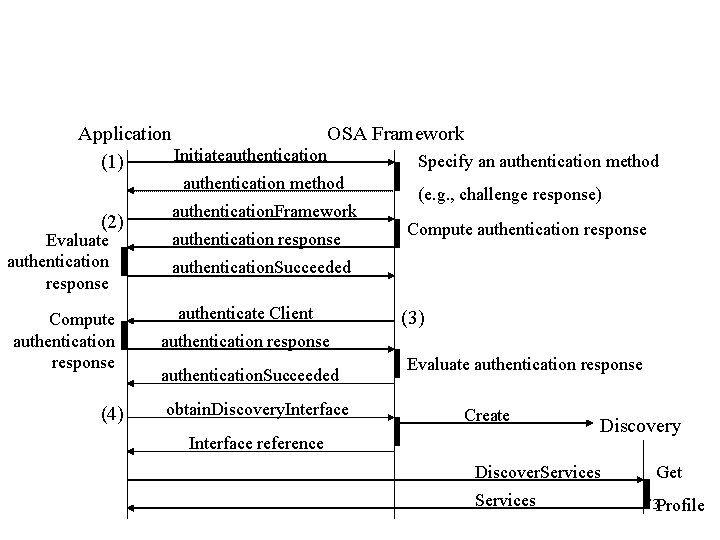
Using OSA Distributed Intelligence Ø The complete cycle for using an OSA service consists of three phases: 1. Authentication: before using OSA services, the application and the OSA framework authenticate each other (prevents unauthorized access) 2. Service selection: the application selects the service interface. Request the signing of agreement before using the interface. 3. Service use: only after the authentication and service selection the application start using the actual service. 72

Application OSA Framework Initiateauthentication Specify an authentication method (1) authentication method (2) Evaluate authentication response Compute authentication response (4) authentication. Framework authentication response (e. g. , challenge response) Compute authentication response authentication. Succeeded authenticate Client (3) authentication response authentication. Succeeded obtain. Discovery. Interface Evaluate authentication response Create Interface reference Discovery Discover. Services Get 73 Profile

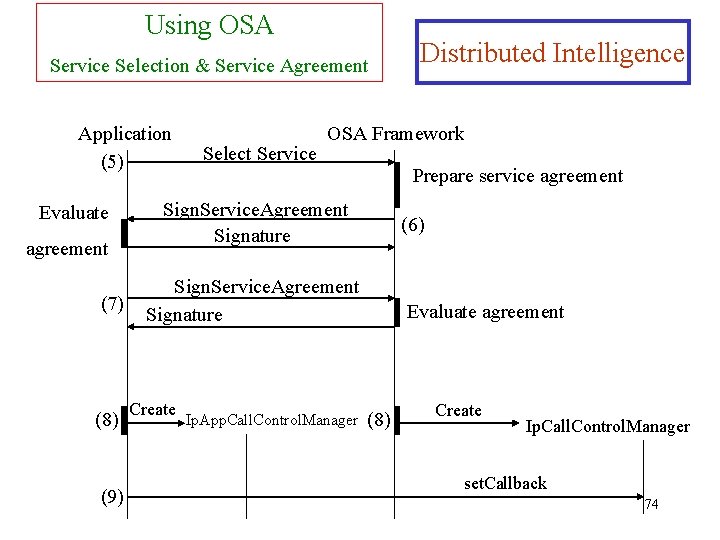
Using OSA Service Selection & Service Agreement Application (5) Evaluate agreement (7) (8) (9) Select Service OSA Framework Prepare service agreement Sign. Service. Agreement Signature (6) Sign. Service. Agreement Signature Create Distributed Intelligence Ip. App. Call. Control. Manager Evaluate agreement (8) Create Ip. Call. Control. Manager set. Callback 74

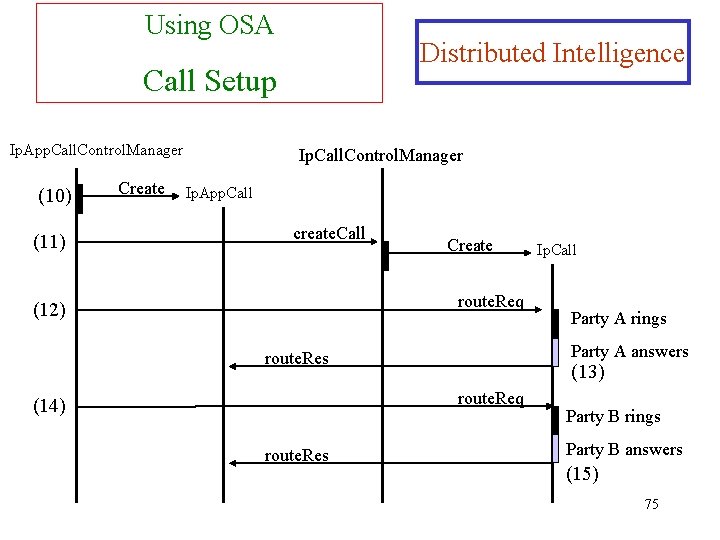
Using OSA Distributed Intelligence Call Setup Ip. App. Call. Control. Manager (10) (11) Create Ip. Call. Control. Manager Ip. App. Call create. Call Create route. Req (12) (13) route. Req route. Res Party A rings Party A answers route. Res (14) Ip. Call Party B rings Party B answers (15) 75

OSA Applications Distributed Intelligence Ø OSA can bring the following added value: 1. Third-party service control. Allow the integration of network features with applications external to the network. (OSA needed to securely access the network’s features) 2. Roaming interface. Current roaming agreements require a high level of trust between the roaming partners. OSA has a security framework, it offers roaming between parties that don’t have an established trust relationship. 76

OSA Applications Distributed Intelligence (Continue…) 3. Protocol replacement. OSA can provide a standard programming interface for these network functions; OSA also provides a framework for features that might be added in the future. 4. Content billing. The OSA charging interface can be used to dynamically establish relations between volume and value. 77

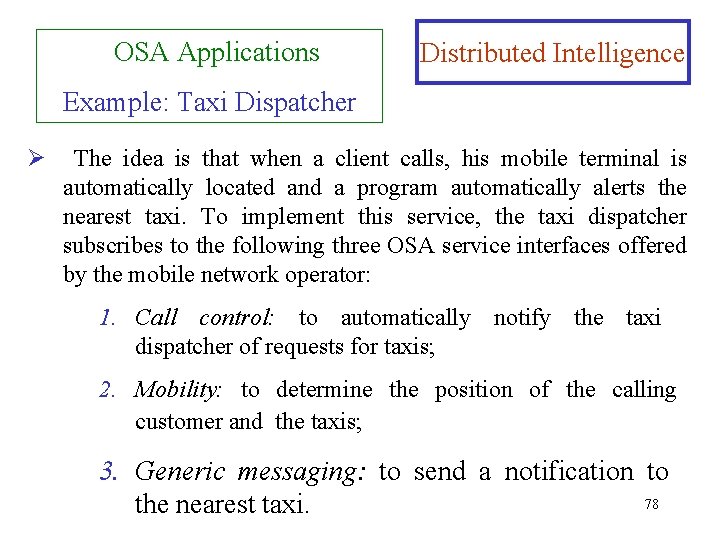
OSA Applications Distributed Intelligence Example: Taxi Dispatcher Ø The idea is that when a client calls, his mobile terminal is automatically located and a program automatically alerts the nearest taxi. To implement this service, the taxi dispatcher subscribes to the following three OSA service interfaces offered by the mobile network operator: 1. Call control: to automatically notify the taxi dispatcher of requests for taxis; 2. Mobility: to determine the position of the calling customer and the taxis; 3. Generic messaging: to send a notification to 78 the nearest taxi.

OSA Applications Distributed Intelligence Example: Taxi Dispatcher (Cont. ) Ø OSA supports two ways of locating taxis (mobile terminals): a. To ask for the position of all taxis whenever a customer calls. b. To have the network send periodic positioning information for each taxi, for example every 5 minutes. Ø The taxi dispatcher develops an application that automatically receives a notification when a customer calls, then locates the customer and finds the nearest taxi, the program send a short message to alert the taxi to pick up the client. This includes the following steps: 1. A customer dials a special number to request a taxi. 79

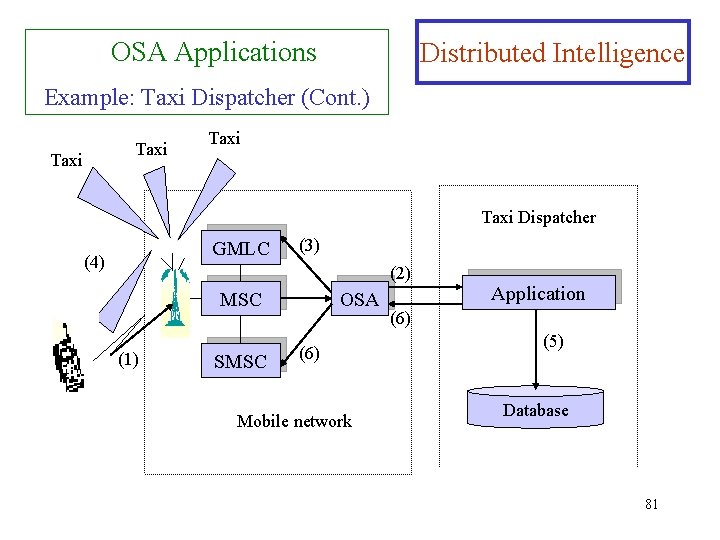
OSA Applications Distributed Intelligence Example: Taxi Dispatcher (Cont. ) 2. The OSA interface notifies the taxi dispatcher application of the customer’s call. Identifies the calling-party number. 3. The taxi dispatcher requests location of the calling party or the (taxis) through the OSA interface. Forwards it to the MLC. 4. The network locates the calling party or the taxis (this may be done periodically). 5. Receiving the caller’s coordinates, it looks up the geographic location in a database and determines the nearest taxi. 6. The application sends a short message to the nearest taxi through the OSA interface to pick up the customer at 80 the indicated location.

OSA Applications Distributed Intelligence Example: Taxi Dispatcher (Cont. ) Taxi Dispatcher GMLC (4) (3) (2) MSC (1) SMSC OSA (6) Mobile network Application (6) (5) Database 81

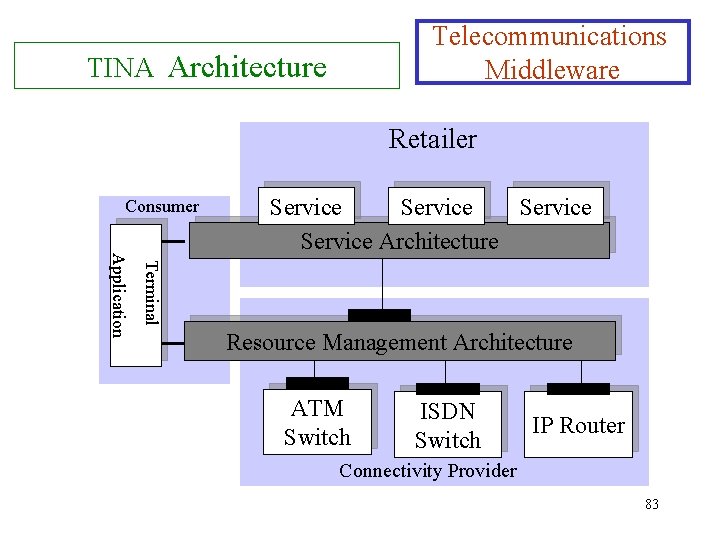
Telecommunications Information. Networking Architecture (TINA) Telecommunications Middleware Ø Middleware: is software that runs between machine’s operating system and the applications. Ø TINA Business Model Ø TINA architecture Ø Session model Ø TINA Service Architecture 1. Computational objects 2. Access session 3. Service session Ø TINA network-resource Architecture 1. Computational objects 2. Connection establishment 3. Federation 82

Telecommunications Middleware TINA Architecture Retailer Consumer Terminal Application Service Architecture Resource Management Architecture ATM Switch ISDN Switch IP Router Connectivity Provider 83

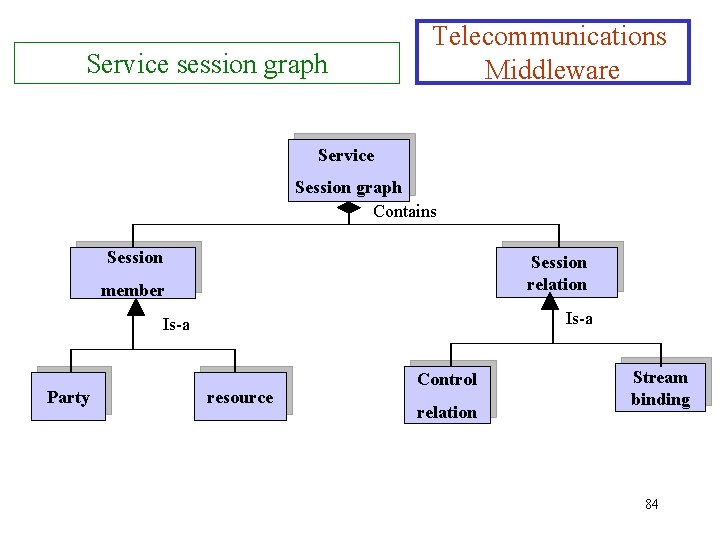
Service session graph Telecommunications Middleware Service Session graph Contains Session relation member Is-a Party resource Control relation Stream binding 84

Access session Telecommunications Middleware Ø The procedure for starting an access session: 1. When the user requests an access session, the PA (provider agent) in the terminal contacts the IA(initial agent) in the network. The address of the IA is always known to any TINA network. 2. The IA consults the subscription database, authenticates the user, and finds the UA(user agent) for this user. (UA can be in a remote network). 3. The UA activates an access session for the user. The PA in the terminal is linked to the UA for the duration of the access session and the user can start using the services. 85

Access session Ø Telecommunications Middleware Through the access session, the user can do any of the following: 1. Request a list of available services. The UA will list the services that the user is subscribed to. 2. Request the start of a service session. The access session is always the window through which services are started. 3. Receive invitations from other users to join a service session. 4. Join a service session that is already active. 5. Register remotely at terminals. A user can request to be registered on a remote terminal for incoming invitations to 86 join sessions.

Service session graph Ø Telecommunications Middleware The TINA service session offers the following features that allow parties to modify the session graph: 1. Basic features: such as starting, stopping, and suspending a session; 2. Multiparty features: adding or dropping a party in a session; 3. Stream-binding features: adding or dropping binding to a party in the session; a stream 4. Voting features: voting among parties in the session (permission of a new party to join the session); 5. Control features: for modifying control relations between parties (transferring chairmanship of a videoconference). 87

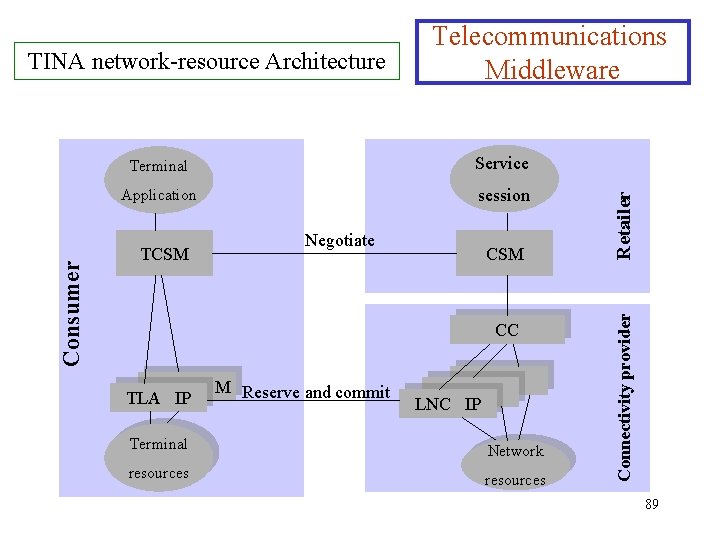
TINA network-resource Architecture Telecommunications Middleware Ø TINA sets up connections in three main steps: 1. Negotiation. The communication session queries all involved terminals and network entities for their capabilities, and selects a set of common capabilities that will allow the connection to be set up. 2. Reservation. The communication session asks all involved terminals and network entities to reserve the selected capabilities. 3. Commitment. If all involved terminals and networks confirm the reservation of the necessary resources, the communication session will then order them to commit the resources and the connection is set up. 88

Service Application session TCSM Negotiate CSM CC TLA IP M Reserve and commit LNC IP Terminal Network resources Retailer Terminal Connectivity provider Consumer TINA network-resource Architecture Telecommunications Middleware 89

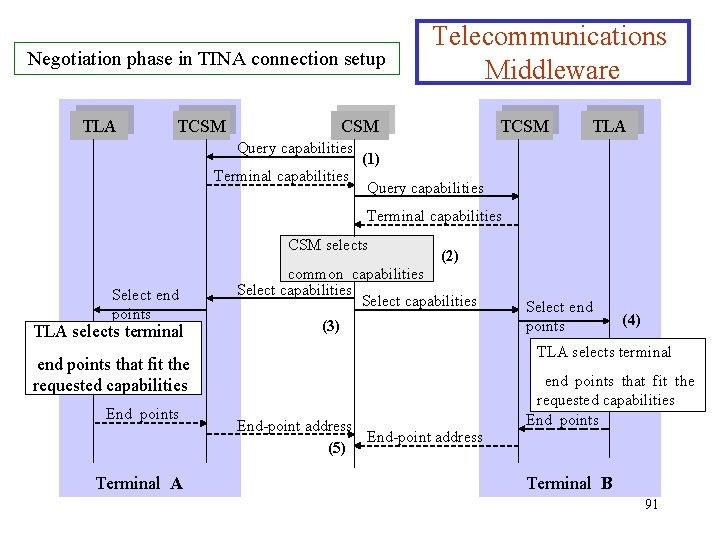
Connection Establishment Ø Telecommunications Middleware The negotiation phase consists of the following steps: 1. The CSM queries the TCSM of each terminal for the terminal capabilities. The terminals respond by giving a list of capabilities they can support (4 slot GPRS) 2. The CSM matches the terminal capabilities listed by each terminal, and defines the common set of capabilities that will allow the requested connection to be established. 3. The CSM tells the TSCM which capabilities are needed and asks the TSCM to select the necessary resources in the terminal. 4. The TCSM asks the TLA to identify the terminal end points that correspond to the requested capabilities. (GSM channels, IP addresses) 5. The selected end-point coordinates are propagated back to the 90 CSM.

Negotiation phase in TINA connection setup TLA TCSM Telecommunications Middleware CSM Query capabilities Terminal capabilities TCSM TLA (1) Query capabilities Terminal capabilities CSM selects Select end points TLA selects terminal (2) common capabilities Select capabilities (3) Terminal A (4) TLA selects terminal end points that fit the requested capabilities End points Select end points End-point address (5) end points that fit the requested capabilities End points Terminal B 91

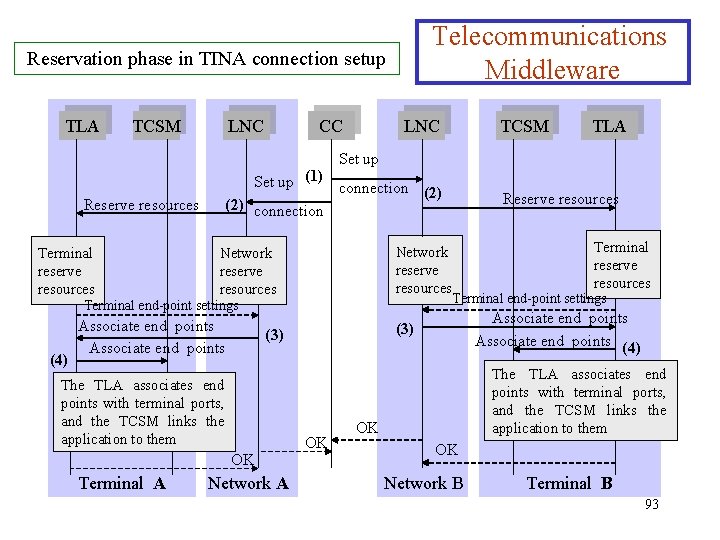
Connection Establishment Telecommunications Middleware Ø The reservation phase consists of the following steps: 1. The CC contacts the LNC for each subnetwork involved, and asks them to set up the necessary connections within their domain. 2. The LNC asks the terminal to reserve the resources negotiated in the previous steps. The LNC also reserves the necessary network resources. 3. If the selected terminal end-points are available, the LNC asks the TLA to associate them with physical resources in the terminal. 4. The TLA asks the TCSM to link the terminal applications to the physical ports in the terminal that will terminate the 92 connection.

Telecommunications Middleware Reservation phase in TINA connection setup TLA TCSM LNC CC LNC TCSM TLA Set up (1) connection (2) connection Reserve resources Terminal reserve resources Network reserve resources Terminal end-point settings (4) Associate end points OK Terminal A Network A OK Terminal reserve resources Terminal end-point settings Associate end points (4) (3) The TLA associates end points with terminal ports, and the TCSM links the application to them Reserve resources The TLA associates end points with terminal ports, and the TCSM links the application to them OK OK Network B Terminal B 93

From SIBs to Objects Service Creation Ø The key issue is how to conduct business with the new architectures. Ø Telecommunications business is determined by the services and offered and their price. Ø Service creation is all about software engineering. Ø Telecommunications software is complex, concurrent, must be reliable and deliver high performance. Ø The INCM recognizes the need for efficient creation of new services. It defines services as compositions of features, which are composed out of elementary building blocks, SIBs. Ø An IN service-creation environment allows even inexperienced service engineers to create services by clicking together elementary 94 building blocks in a plug-and-play fashion.

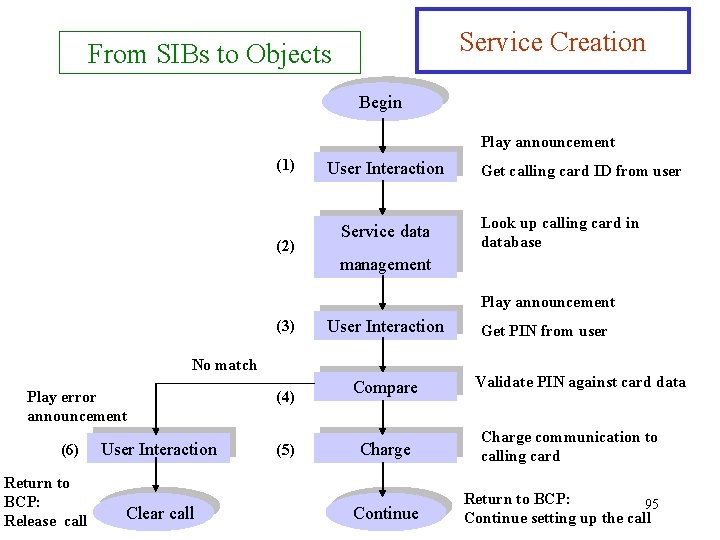
Service Creation From SIBs to Objects Begin Play announcement (1) (2) User Interaction Service data Get calling card ID from user Look up calling card in database management Play announcement (3) User Interaction No match Play error announcement (6) Return to BCP: Release call User Interaction Clear call (4) (5) Compare Charge Continue Get PIN from user Validate PIN against card data Charge communication to calling card Return to BCP: 95 Continue setting up the call

From SIBs to Objects Service Creation The calling card service shows the SIB flow and performs the following steps: 1. A message is played to the user, asking for the calling-card ID, and user input is received in the form of DTMF tones. 2. The calling card data is retrieved from the database using the calling -card ID input by the user in the previous step. 3. A message is played to the user, asking for the PIN code, and user input is received in the form of DTMF tones. 4. The PIN provided by the user is verified against the PIN on the card. 5. If the PIN is correct, the call is charged to the calling card and the call setup continues. 6. If the PIN incorrect (card number or PIN invalid), an error message is played to the user and the call is cleared. 96