Network Fundamentals Generalized network training starting with the



























- Slides: 109

Network Fundamentals Generalized network training starting with the very basic and moving into complex concepts and configurations. Presented by @alt_bier aka Richard Gowen Solution Architect, Pepsi. Co Global Network Engineering Co-Founder of the Plano Hacker Space The. Lab. ms Document Title Goes Here 1

What is a “Network”? The basic definition of a network is a way to get ‘stuff’ between two or more ‘things’ using a defined transport model. Examples: Postal System, Phone System, Railroads, Highways/Roads. A computer network fits this definition as it allows computers to transmit information between each other using a defined transport model. In fact, correlations have been made between computer networks and Highways given the similarities of the two (e. g. “The Information Super-Highway”). 2

Computer Networking Models, also called protocol stacks, are represented in layers to help us understand where things happen and where they might go wrong. There are several models that have been used over the years (e. g. DOD 3 -layer, Simplified 4 -layer). However, the OSI 7 layer model is the current standard that is used to describe computer networks. The OSI (Open Systems Interconnection) model defines seven layers / protocols that are used in computer networking. Each layer is dependent upon the layer below it and thus all layers are stacked to provide information transport. 3

Protocol Concepts Protocols are sets of rules that define how to perform various tasks. • What do you want to do? (Application) • How do you need it displayed? (Presentation) • How important is it? (Prioritization) • Where are you going? (Addressing) • How do you get there? (Media types, Routes) • Did you get there? (Acknowledgments, Error checking) 4

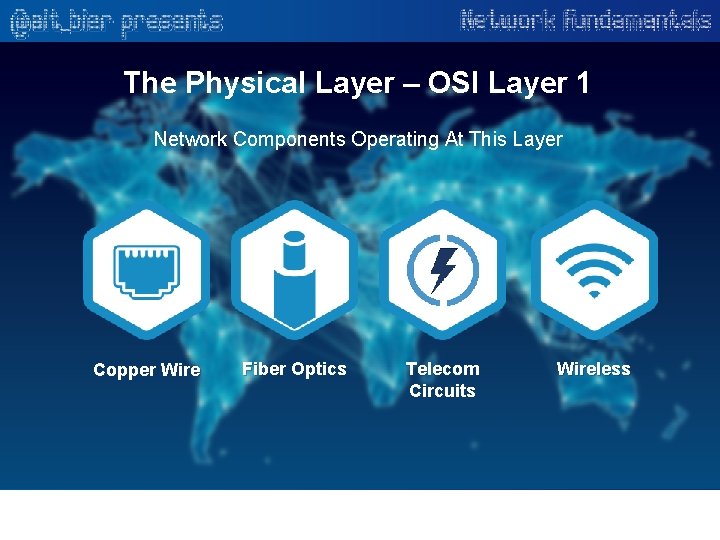
The Physical Layer – OSI Layer 1 Network Components Operating At This Layer Copper Wire Fiber Optics Telecom Circuits Wireless

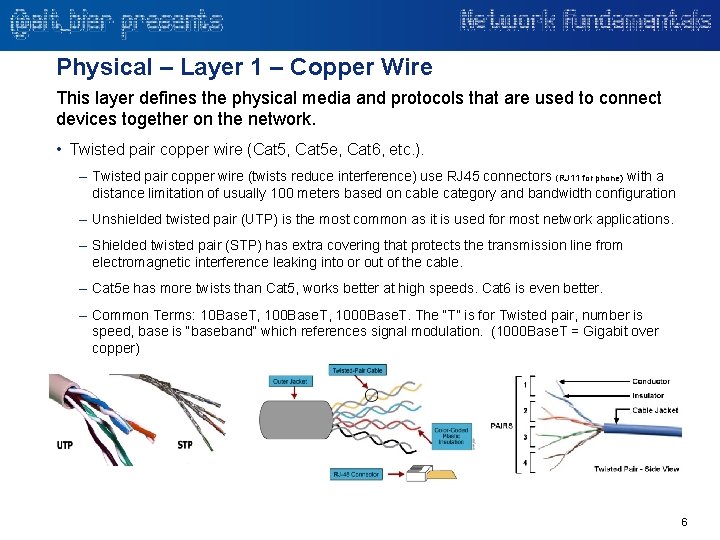
Physical – Layer 1 – Copper Wire This layer defines the physical media and protocols that are used to connect devices together on the network. • Twisted pair copper wire (Cat 5, Cat 5 e, Cat 6, etc. ). – Twisted pair copper wire (twists reduce interference) use RJ 45 connectors (RJ 11 for phone) with a distance limitation of usually 100 meters based on cable category and bandwidth configuration – Unshielded twisted pair (UTP) is the most common as it is used for most network applications. – Shielded twisted pair (STP) has extra covering that protects the transmission line from electromagnetic interference leaking into or out of the cable. – Cat 5 e has more twists than Cat 5, works better at high speeds. Cat 6 is even better. – Common Terms: 10 Base. T, 1000 Base. T. The “T” is for Twisted pair, number is speed, base is “baseband” which references signal modulation. (1000 Base. T = Gigabit over copper) 6

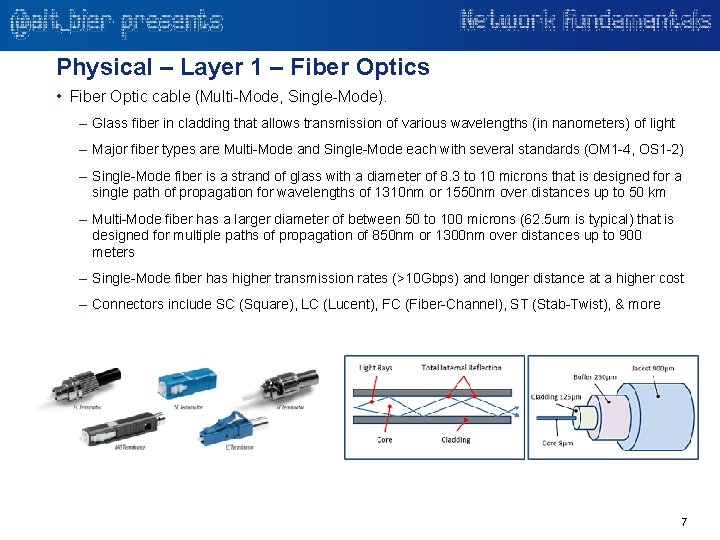
Physical – Layer 1 – Fiber Optics • Fiber Optic cable (Multi-Mode, Single-Mode). – Glass fiber in cladding that allows transmission of various wavelengths (in nanometers) of light – Major fiber types are Multi-Mode and Single-Mode each with several standards (OM 1 -4, OS 1 -2) – Single-Mode fiber is a strand of glass with a diameter of 8. 3 to 10 microns that is designed for a single path of propagation for wavelengths of 1310 nm or 1550 nm over distances up to 50 km – Multi-Mode fiber has a larger diameter of between 50 to 100 microns (62. 5 um is typical) that is designed for multiple paths of propagation of 850 nm or 1300 nm over distances up to 900 meters – Single-Mode fiber has higher transmission rates (>10 Gbps) and longer distance at a higher cost – Connectors include SC (Square), LC (Lucent), FC (Fiber-Channel), ST (Stab-Twist), & more 7

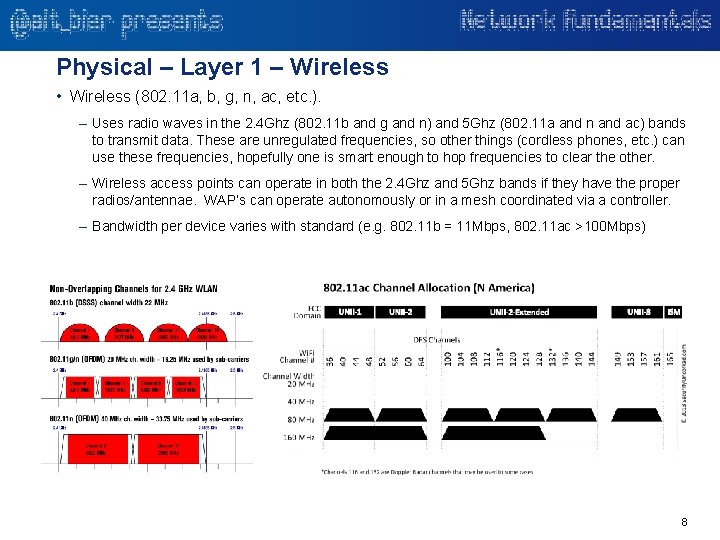
Physical – Layer 1 – Wireless • Wireless (802. 11 a, b, g, n, ac, etc. ). – Uses radio waves in the 2. 4 Ghz (802. 11 b and g and n) and 5 Ghz (802. 11 a and n and ac) bands to transmit data. These are unregulated frequencies, so other things (cordless phones, etc. ) can use these frequencies, hopefully one is smart enough to hop frequencies to clear the other. – Wireless access points can operate in both the 2. 4 Ghz and 5 Ghz bands if they have the proper radios/antennae. WAP’s can operate autonomously or in a mesh coordinated via a controller. – Bandwidth per device varies with standard (e. g. 802. 11 b = 11 Mbps, 802. 11 ac >100 Mbps) 8

Physical – Layer 1 – Carrier Circuits • Telecommunication Carrier Circuits (ISDN, SMDS, DSL, SONET, Metro. E, MPLS, etc. ). – Leased lines from telecommunication carriers vary in type, protocol, and bandwidth. – Integrated Services Digital Network (ISDN) - Separate signal D channel (delta@16 kbps) from data B channels (bearer@64 kbps) provisioned as Basic Rate Interface (2 B+1 D) or Primary Rate Interface (23 B+1 D) – Switched Multimegabit Data Service (SMDS) - Switched digital service from carrier with multiple speeds: T 1 (1. 544 Mbps), T 3 (44. 736 Mbps), etc. – Digital Subscriber Line (DSL) – Deliver digitized signals over telephone lines. Higher data speeds available than ISDN and SMDS. Two types: Symmetric / Asymmetric (SDSL / ADSL) – Synchronous optical network (SONET) – High bandwidth optical service from carrier w/ multiple speeds: OC 1 (51. 48 Mbps), OC 3 (155. 52 Mbps), OC 12 (622. 08 Mbps), etc. – Metro-Ethernet (Metro. E) – Carrier provided Ethernet service using Metropolitan Area Network (MAN) technology available in 10 Mbps, 100 Mbps, and 1000 Mbps port speeds with fractional data rates optional – Multi-Protocol Label Switching (MPLS) – A data-carrying technique for high-performance networks that can utilize a number of existing carrier services such as SMDS, SONET, and Metro Ethernet. While not a physical media type on its own, it is often called out as such based on marketing terms. 9

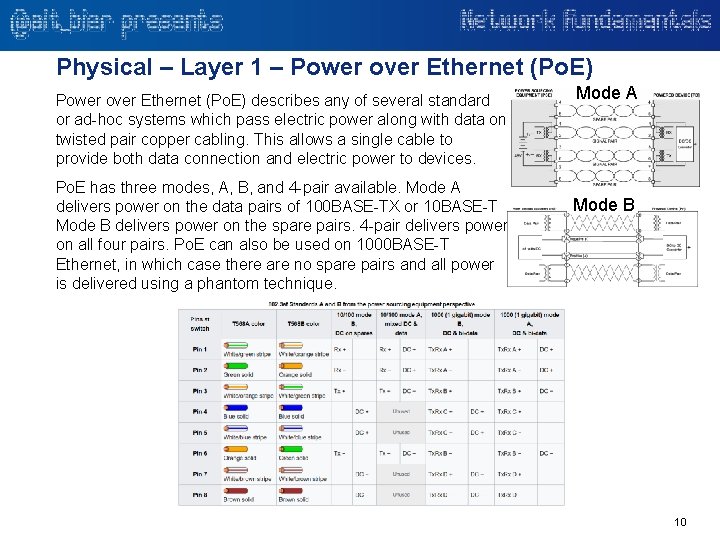
Physical – Layer 1 – Power over Ethernet (Po. E) describes any of several standard or ad-hoc systems which pass electric power along with data on twisted pair copper cabling. This allows a single cable to provide both data connection and electric power to devices. Po. E has three modes, A, B, and 4 -pair available. Mode A delivers power on the data pairs of 100 BASE-TX or 10 BASE-T Mode B delivers power on the spare pairs. 4 -pair delivers power on all four pairs. Po. E can also be used on 1000 BASE-T Ethernet, in which case there are no spare pairs and all power is delivered using a phantom technique. Mode A Mode B 10

Physical – Layer 1 – Bandwidth and Latency Two common network terms at the physical layer that are often confused are bandwidth and latency. Bandwidth is a measure of the amount of traffic that can travel on a given network medium. This can be compared to the number of lanes on a highway. More bandwidth/lanes means more traffic can use the network/highway before it becomes congested. Latency is a measure of the time it takes to get from one place to another on a network. Certain things like congestion can affect latency but there will always be a minimum latency based on the distance. For example, if it takes 15 hours to drive from Chicago to Dallas congestion may increase this to 17 hours. However, adding more lanes to the highway does not reduce this time below 15 hours. The speed of light is the determining factor for theoretical minimum latency for a specified distance. 11

The Data Link Layer – OSI Layer 2 Network Components Operating At This Layer Host Network Interface Card Modem / Repeater Switch Hub (deprecated) Network Access Control Bridge (deprecated) Wireless Access Point

Data Link – Layer 2 The data link layer takes the 1’s and 0’s handed it by the Network layer and turns them into some kind of signal that can go over the Physical layer (electrical current, light pulses, microwaves, etc. ) It also takes this signal and turns it back into 1’s and 0’s to pass up the stack on the receiving end. These transmissions are sent in a unit of data called a “Frame” which varies in size based on the protocol used (e. g. ATM = 53 Bytes, Ethernet = 1522 Bytes). Frames can only be sent between devices on the same local layer 2 network which is also known as a broadcast domain (since broadcast frames are not forwarded by bridges or switches). This was the original meaning of the term Local Area Network (LAN). Although in modern network terminology LAN refers to all layer 2 and layer 3 networks in a specific location (office, data center, etc. ). Older hubs and switches were limited to hosting a single layer 2 network on them. While modern day switches use a feature called the Virtual Local Area Network (VLAN) to host multiple layer 2 networks on a single device. Data link protocols: Token Ring, FDDI, ATM, and the most common of all the data link protocols: Ethernet (standard IEEE 802. 3). 13

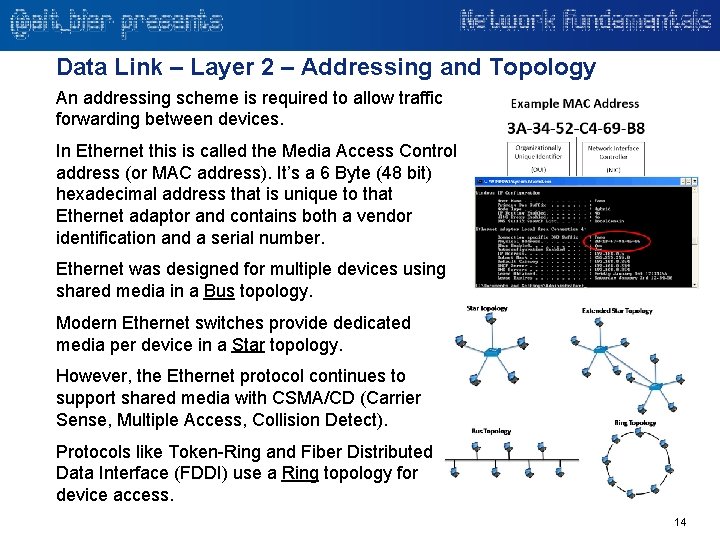
Data Link – Layer 2 – Addressing and Topology An addressing scheme is required to allow traffic forwarding between devices. In Ethernet this is called the Media Access Control address (or MAC address). It’s a 6 Byte (48 bit) hexadecimal address that is unique to that Ethernet adaptor and contains both a vendor identification and a serial number. Ethernet was designed for multiple devices using shared media in a Bus topology. Modern Ethernet switches provide dedicated media per device in a Star topology. However, the Ethernet protocol continues to support shared media with CSMA/CD (Carrier Sense, Multiple Access, Collision Detect). Protocols like Token-Ring and Fiber Distributed Data Interface (FDDI) use a Ring topology for device access. 14

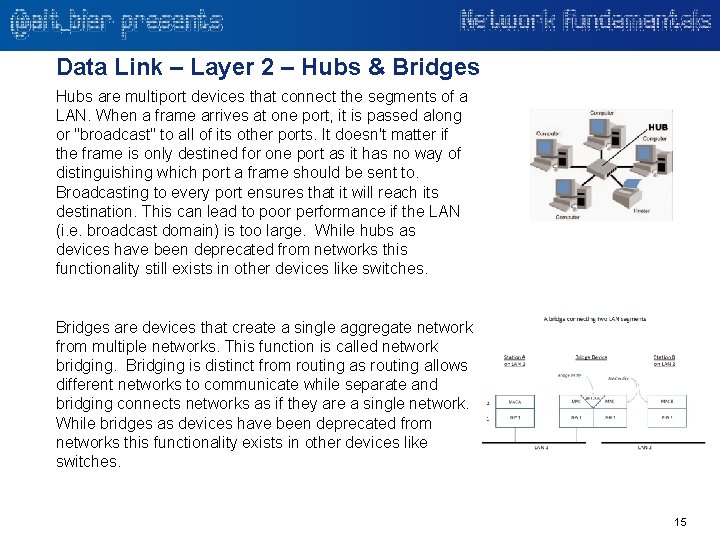
Data Link – Layer 2 – Hubs & Bridges Hubs are multiport devices that connect the segments of a LAN. When a frame arrives at one port, it is passed along or "broadcast" to all of its other ports. It doesn't matter if the frame is only destined for one port as it has no way of distinguishing which port a frame should be sent to. Broadcasting to every port ensures that it will reach its destination. This can lead to poor performance if the LAN (i. e. broadcast domain) is too large. While hubs as devices have been deprecated from networks this functionality still exists in other devices like switches. Bridges are devices that create a single aggregate network from multiple networks. This function is called network bridging. Bridging is distinct from routing as routing allows different networks to communicate while separate and bridging connects networks as if they are a single network. While bridges as devices have been deprecated from networks this functionality exists in other devices like switches. 15

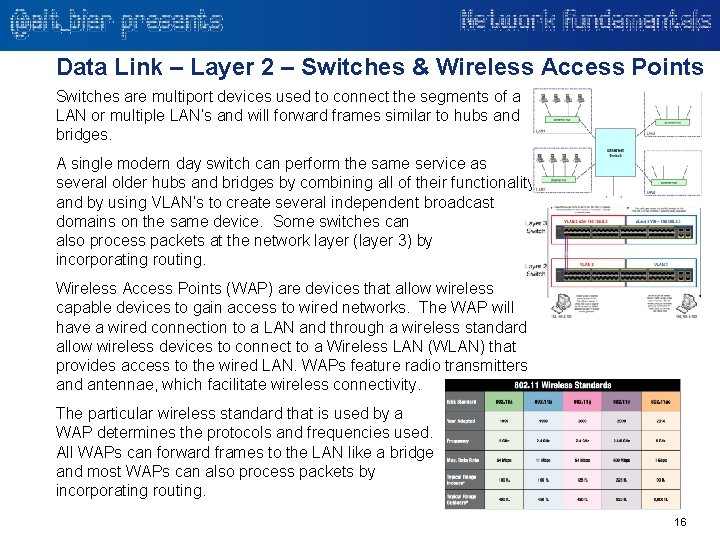
Data Link – Layer 2 – Switches & Wireless Access Points Switches are multiport devices used to connect the segments of a LAN or multiple LAN’s and will forward frames similar to hubs and bridges. A single modern day switch can perform the same service as several older hubs and bridges by combining all of their functionality and by using VLAN’s to create several independent broadcast domains on the same device. Some switches can also process packets at the network layer (layer 3) by incorporating routing. Wireless Access Points (WAP) are devices that allow wireless capable devices to gain access to wired networks. The WAP will have a wired connection to a LAN and through a wireless standard allow wireless devices to connect to a Wireless LAN (WLAN) that provides access to the wired LAN. WAPs feature radio transmitters and antennae, which facilitate wireless connectivity. The particular wireless standard that is used by a WAP determines the protocols and frequencies used. All WAPs can forward frames to the LAN like a bridge and most WAPs can also process packets by incorporating routing. 16

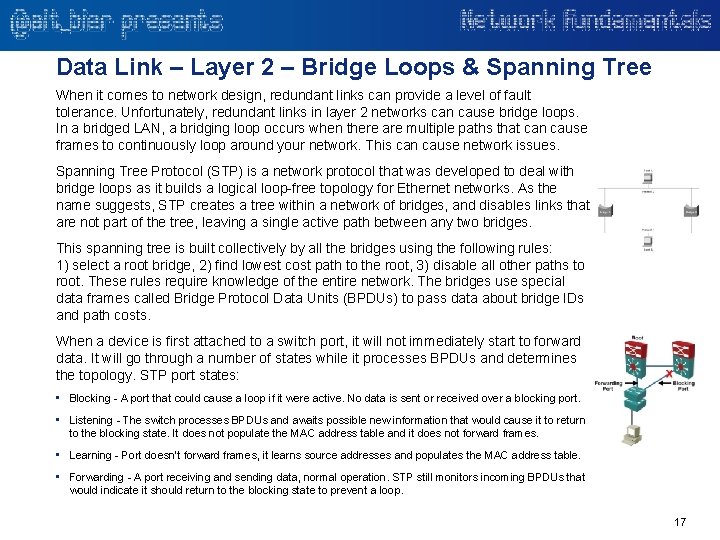
Data Link – Layer 2 – Bridge Loops & Spanning Tree When it comes to network design, redundant links can provide a level of fault tolerance. Unfortunately, redundant links in layer 2 networks can cause bridge loops. In a bridged LAN, a bridging loop occurs when there are multiple paths that can cause frames to continuously loop around your network. This can cause network issues. Spanning Tree Protocol (STP) is a network protocol that was developed to deal with bridge loops as it builds a logical loop-free topology for Ethernet networks. As the name suggests, STP creates a tree within a network of bridges, and disables links that are not part of the tree, leaving a single active path between any two bridges. This spanning tree is built collectively by all the bridges using the following rules: 1) select a root bridge, 2) find lowest cost path to the root, 3) disable all other paths to root. These rules require knowledge of the entire network. The bridges use special data frames called Bridge Protocol Data Units (BPDUs) to pass data about bridge IDs and path costs. When a device is first attached to a switch port, it will not immediately start to forward data. It will go through a number of states while it processes BPDUs and determines the topology. STP port states: • Blocking - A port that could cause a loop if it were active. No data is sent or received over a blocking port. • Listening - The switch processes BPDUs and awaits possible new information that would cause it to return to the blocking state. It does not populate the MAC address table and it does not forward frames. • Learning - Port doesn’t forward frames, it learns source addresses and populates the MAC address table. • Forwarding - A port receiving and sending data, normal operation. STP still monitors incoming BPDUs that would indicate it should return to the blocking state to prevent a loop. 17

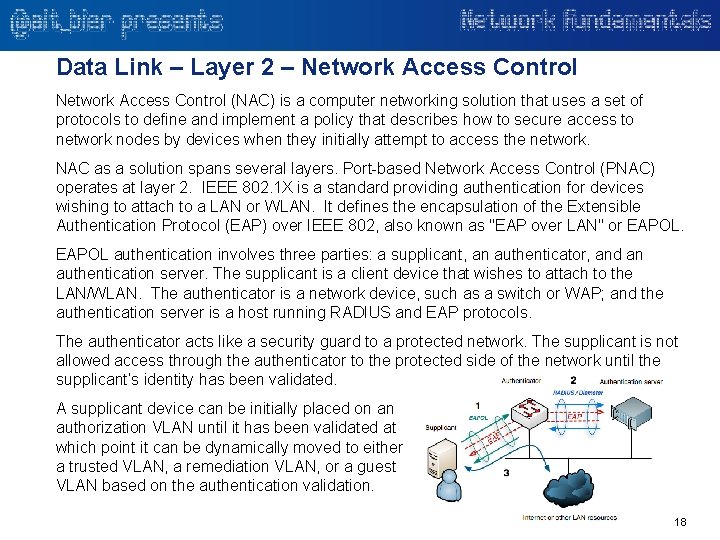
Data Link – Layer 2 – Network Access Control (NAC) is a computer networking solution that uses a set of protocols to define and implement a policy that describes how to secure access to network nodes by devices when they initially attempt to access the network. NAC as a solution spans several layers. Port-based Network Access Control (PNAC) operates at layer 2. IEEE 802. 1 X is a standard providing authentication for devices wishing to attach to a LAN or WLAN. It defines the encapsulation of the Extensible Authentication Protocol (EAP) over IEEE 802, also known as "EAP over LAN" or EAPOL authentication involves three parties: a supplicant, an authenticator, and an authentication server. The supplicant is a client device that wishes to attach to the LAN/WLAN. The authenticator is a network device, such as a switch or WAP; and the authentication server is a host running RADIUS and EAP protocols. The authenticator acts like a security guard to a protected network. The supplicant is not allowed access through the authenticator to the protected side of the network until the supplicant’s identity has been validated. A supplicant device can be initially placed on an authorization VLAN until it has been validated at which point it can be dynamically moved to either a trusted VLAN, a remediation VLAN, or a guest VLAN based on the authentication validation. 18

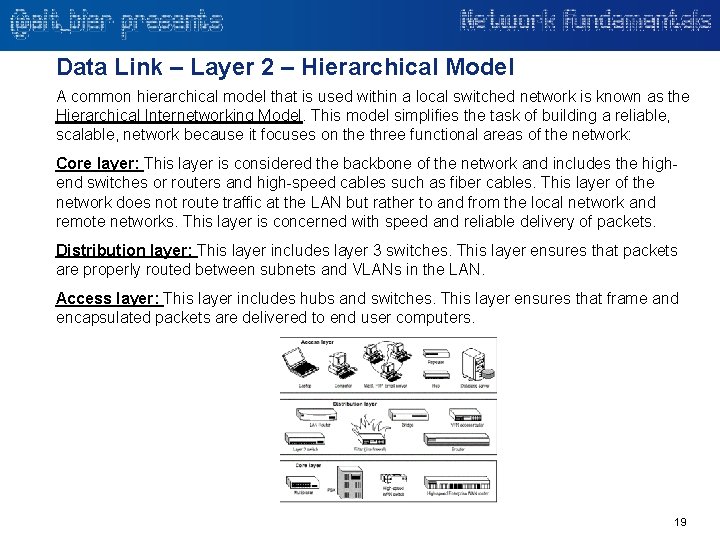
Data Link – Layer 2 – Hierarchical Model A common hierarchical model that is used within a local switched network is known as the Hierarchical Internetworking Model. This model simplifies the task of building a reliable, scalable, network because it focuses on the three functional areas of the network: Core layer: This layer is considered the backbone of the network and includes the highend switches or routers and high-speed cables such as fiber cables. This layer of the network does not route traffic at the LAN but rather to and from the local network and remote networks. This layer is concerned with speed and reliable delivery of packets. Distribution layer: This layer includes layer 3 switches. This layer ensures that packets are properly routed between subnets and VLANs in the LAN. Access layer: This layer includes hubs and switches. This layer ensures that frame and encapsulated packets are delivered to end user computers. 19

The Network Layer – OSI Layer 3 Network Components Operating At This Layer Router Layer-3 Switch Multi-Service Switch Firewall Intrusion Detection & Prevention Network Access Control Load Balancer Voice / Video Gateway Wireless Access Point Wireless Controller

Network – Layer 3 When you link computers up, via layers 1 and 2 you get a local network. When you link networks up, you get an internetwork. You need the Network layer (layer 3) to get data between all the local networks of your internetwork. One internetwork’s so well known, it drops the “work” and gets a capital “I. ” Network Layer transmissions are sent in a unit of data called a “Packet”. Network packets can be routed unlike data link frames. This means they can be passed from one local network to another. A device can only get data link layer frames on its local network interface. So, network layer packets have to be stuffed inside the data link layer frames. This is called “encapsulation” and is why a layered model is handy for reference. Network Layer Protocols: Internet Protocol (IP), Internet Control Message Protocol (ICMP), and several others, some that aren’t used much any more (Apple. Talk, Netware IPX, etc. ). Internet Protocol (IP) is used on the Internet as well as most other networks. It was designed for huge, ever-expanding networks of networks. 21

Network – Layer 3 – IP Version 4 Internet Protocol Version 4 (IPv 4) is the original basis for the Internet and is still the majority network protocol used even with the launch of IPv 6 in 2009. Every connected host has a four octet address expressed in dotted decimal format: [0 -255] (e. g. 192. 168. 10. 1) Hosts send packets to IP addresses that are routed to those destinations. Classful addressing: In IPv 4 the class of a network can be A, B, or C and this affects how the network is sub-netted. In a Class A network the first octet is reserved for network addresses and the remaining 3 octets are for host addresses. In a Class B network 2 octets are network and 2 are host. In a Class C network 3 octets are network and 1 is for hosts. In all classes the lowest host address is reserved for network identification and the highest host address is reserved for broadcast. (e. g. Class C network 192. 168. 10. 0 has 254 host addresses from 1 -254 and a broadcast address of 192. 168. 10. 255) The broadcast address is intended for sending traffic to every host on that network. Variable-length subnet masking (VLSM) and Classless Inter-Domain Routing (CIDR): These provide methods of carving up subnets beyond the classful boundaries by using a subnet mask to identify how many bits of an IP address reference network vs hosts. (e. g. network 192. 168. 10. 0/25 has 126 hosts 1 -126 with broadcast 192. 168. 10. 127) 22

Network – Layer 3 – IP Version 6 Internet Protocol Version 6 (IPv 6) is a new version of IP that was officially launched in 2012 and is recently starting to gain adoption as the IPv 4 address space is exhausted. IPv 6 expands addressing beyond the IPv 4 32 -bit value to a 128 -bit value address. Given this larger address space a new way to express these addresses was developed An IPv 6 address is represented as eight groups of four hexadecimal digits, each group representing 16 bits (two octets, a group sometimes also called a hextet). The groups are separated by colons (: ). An example of an IPv 6 address is: 2001: 0 db 8: 85 a 3: 0000: 8 a 2 e: 0370: 7334 Leading zeroes in a group may be omitted, but each group must retain at least one hexadecimal digit. Thus, the example address may be written as: 2001: db 8: 85 a 3: 0: 0: 8 a 2 e: 370: 7334 One or more consecutive groups of zero value may be replaced with two consecutive colons (: : ) Thus, the example address can be further simplified: 2001: db 8: 85 a 3: : 8 a 2 e: 370: 7334 Network address ranges are written in CIDR notation. A network is denoted by the first address in the block (ending in all zeroes), a slash (/), and a decimal value equal to the size in bits of the prefix. For example, the network written as 2001: db 8: 1234: : /48 starts at address 2001: db 8: 1234: 0: 0: 0 and ends at 2001: db 8: 1234: ffff: ffff. IPv 6 functions similar to IPv 4 in most respects and serves the same purpose of allowing networks to be interconnected and packets to be routed to IP addresses. 23

Network – Layer 3 – Private Network Address Space In the Internet addressing architecture, a private network is a network that uses private IP address space, following the standards set by RFC 1918 for IPv 4, and RFC 4193 for IPv 6. These addresses are commonly used for home, office, and enterprise local area networks. Addresses in the private space are not allocated to any specific organization and anyone may use these addresses without approval from a regional Internet registry. However, IP packets addressed from them cannot be transmitted through the public Internet. So if such a private network needs to connect to the Internet, it must do so via a network address translator (NAT) gateway, or a proxy. Private IPv 4 address spaces shown as largest CIDR block (subnet mask): – 10. 0/8 (255. 0. 0. 0) – 172. 16. 0. 0/12 (255. 240. 0. 0) – 192. 168. 0. 0/16 (255. 0. 0) Private IPv 6 address spaces shown as largest CIDR block: – fd 00: : /8 Another type of private networking is the link-local address range used in autoconfiguration. – In IPv 4, link-local addresses are codified in RFC 6890 and RFC 3927. The block 169. 254. 0. 0/16 is reserved for this purpose, with the exception of the first and the last /24 subnets in the range. – In IPv 6, link-local addresses are codified in RFC 4862. Their use is mandatory, and an integral part of the IPv 6 standard. The RFC 4291 sets aside the block fe 80: : /10 for IP address autoconfiguration. The local loopback mechanism uses private networks as well. In IPv 4 the address block 127. 0. 0. 0/8 is reserved for loopback. In IPv 6 there is just a single address reserved which is : : 1. 24

Network – Layer 3 – Network Address Translation Network address translation (NAT) is a method of remapping one IP address space into another by modifying network address information in IP packet headers while they are in transit across a routing device. This was originally used for ease of rerouting traffic in IP networks without readdressing every host. In more advanced NAT implementations featuring IP masquerading, it has become a popular and essential tool in conserving global address space allocations in face of IPv 4 address exhaustion by sharing one Internet-routable IP address of a NAT gateway for an entire private network. IP masquerading is a technique that hides an IP address space, usually of private IP addresses, behind a single IP address in another, usually public address space. The address to be hidden is changed into a single (public) IP address as "new" source address of the outgoing packet so it appears as originating from the routing device itself. Because of the popularity of this technique to conserve IPv 4 address space, the term NAT has become virtually synonymous with IP masquerading. The simplest type of NAT provides a one-to-one translation of IP addresses. In this type of NAT, only the IP addresses, IP header checksum and any higher level checksums that include the IP address are changed. Basic NATs can be used to interconnect two IP networks that have incompatible addressing. The majority of NATs map multiple private hosts to one publicly exposed IP address. In a typical configuration, a local network uses a designated "private" IP address subnet. 25

Network – Layer 3 – IP Address Resolution As indicated earlier our machines do not communicate directly at the Network layer but rather encapsulate these packets into Data Link layer frames. So, how do we determine what MAC address at Layer 2 to send an IP address at Layer 3 to? This process is called address resolution where destination Layer 3 IP addresses are resolved to a destination Layer 2 MAC address. In IPv 4 the protocol that provides this service is the Address Resolution Protocol (ARP) An ARP request is made asking who has an IP address. The reply will contain the IP address of the router that replied and also the MAC address of the local device that sent that reply. This is saved in an ARP table so future traffic to that destination will not require an ARP request. ARP tables age out to allow for changes in the network. In IPv 6 this same ARP functionality is included in the Neighbor Discovery Protocol (NDP) which handles this as well as a number of other auto-discovery tasks for IPv 6. While it is possible to use IP addresses natively in higher layers, it can be inconvenient. This is where the concept of names arise as it is easier to type google. com in a browser than 172. 217. 12. 78 or 2607: f 8 b 0: 4000: 813: : 200 e The Domain Name Service (DNS) and the Windows Internet Name Service (WINS) provide this type of address resolution by taking a name request and replying with the associated IP address. To use DNS or WINS a device must be configured to point to DNS and/or WINS servers that will provide this resolution. 26

Network – Layer 3 – IP Host Configuration Unlike a MAC address which is physically assigned to a network interface, an IP network must be configured on a host for it to communicate at Layer 3. The minimum configuration would include the hosts specific IP address, the subnet mask, and the gateway IP address (this is the IP of a host that knows how to route to other IP networks also known as a router) Additional configurable items include DNS server IP addresses, WINS server IP addresses, a host name, a domain name, NTP Time server IP addresses, and more. IP host configuration can be done manually or can be auto-configured using the Dynamic Host Configuration Protocol (DHCP). In IPv 4 a DHCP server enables computers to request their IP addresses and all other networking parameters. In IPv 6 networks stateless autoconfiguration is provided by the Neighbor Discovery Protocol which give a host its IP address. However, if other information is required the DHCPv 6 protocol provides this. 27

Network – Layer 3 – Addressing Methods IP Addressing Methods: Who do we want to talk to? In networking there are several ways that one device can address its traffic to send to one or many devices on the network. We previously discussed broadcast in the data link layer and this concept carries forward to the network layer. However, there are more ways to address traffic being sent on a network. Unicast addressing uses a one-to-one association between a sender and destination: each destination address uniquely identifies a single receiver endpoint. Broadcast addressing uses a one-to-all association; a single packet from one sender is routed to all of the possibly multiple endpoints associated with the broadcast address. The network automatically replicates packets as needed to reach all the recipients within the scope of the broadcast (usually a subnet). Multicast addressing uses a one-to-many-of-many or many-to-many-of-many association; packets are routed simultaneously in a single transmission to many recipients. It differs from broadcast in that the destination address designates a subset, not necessarily all, of the accessible nodes. Anycast addressing is a one-to-one-of-many association where packets are routed to any single member of a group of potential receivers that are all identified by the same destination address. The routing algorithm selects the single receiver from the group based on which is the nearest according to some distance measure. 28

Network – Layer 3 – IP Routing: How do we get packets from here to there? Every IP address that is not on your local IP network (as determined by your subnet mask) will not be accessible for you to communicate directly with. But a router that is on your local network should be able to take that packet and pass it along for you, routing the traffic from your local IP network to a remote IP network. By default every host on an IP network is configured with a gateway IP address that is a router which will allow it to communicate to non-local IP addresses. Routers keep tables of networks, often large tables. These tables can be configured beyond the routers connected network routes manually with static routes or dynamically using routing protocols. Most routers also have a gateway IP address similar to a hosts that is called a default route for any traffic not in it’s tables. In this way routers can pass IP packets along from router to router until it reaches a router that is directly connected to the destination IP network and the packet is delivered to the destination host. Ping and Traceroute are two basic useful tools in identifying routing issues on a network. Ping will send a small packet to a destination IP address to determine if it is reachable and how long in milliseconds it took to get a reply. Traceroute asks all the routers along the path between source and destination for a reply and times the responses and records the path of routers taken to get to the destination. 29

Network – Layer 3 – Routers are network devices that forward network packets between networks. A Router can be a dedicated network device or a function added to a multi-purpose network device such as a Layer-3 Switch. A router is connected to two or more networks. When a packet comes in on one of its network interfaces, the router reads the network address in the packet to determine the ultimate destination. Then, using its routing table, it forwards the packet to the next router on its journey or to its destination (if connected to the destination network). Routers allow for network communication beyond the limits of a single location. This wider expanse of internetwork communication is called a Wide Area Network (WAN) A Layer 3 router topology which is called the logical topology, is similar to but independent of the layer 1/2 aka. physical topology. You may see a mesh topology of routers at layer 3 that sit upon star topology layer 1/2 network. Network layer topologies include Bus, Star, Ring, Linear, Tree, and Mesh (partial & full). Routing protocols specify how routers distribute information that enables them to select which routes to send traffic. Routing algorithms determine the specific choice of route. Each router has knowledge only of networks attached to it directly. A routing protocol shares this information throughout the network. This way, routers gain knowledge of the topology of the network. 30

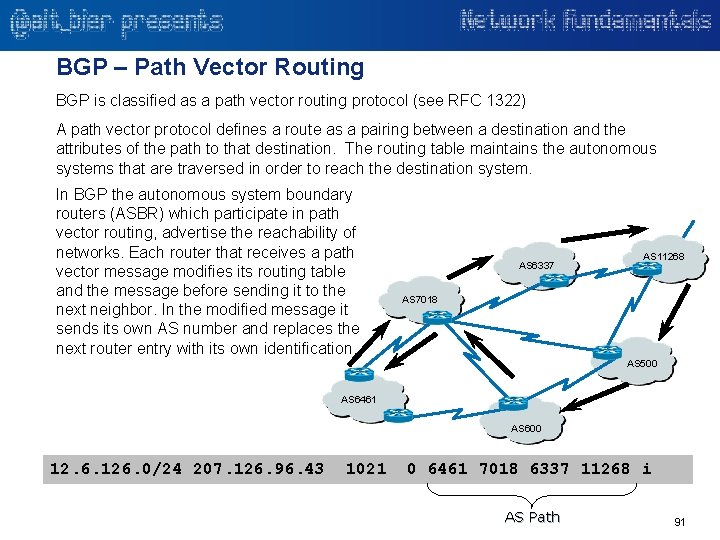
Network – Layer 3 – Routing Protocols There are three major classes of routing protocols in widespread use on IP networks: • Interior gateway protocols type 1, link-state routing protocols • Examples: Open Shortest Path First (OSPF) and Intermediate System to Intermediate System (IS-IS) • The concept of link-state routing is that every node constructs a map of connectivity, in the form of a graph, showing which nodes are connected to which other nodes. Each node calculates the next best logical path from it to every possible destination in the network • Interior gateway protocols type 2, distance-vector routing protocols • Examples: Routing Information Protocol (RIP), RIPv 2, Interior Gateway Routing Protocol (IGRP) and Enhanced Interior Gateway Routing Protocol (EIGRP). • A distance-vector routing protocol requires routers inform its neighbors of topology changes periodically. The term distance vector refers to the fact that it manipulates vectors (arrays) of distances to other nodes in the network. • Exterior gateway protocols, path-vector routing protocols Path Vector Routing Example • While Interior Gateway Protocols (IGP’s) route within an autonomous system, routing protocols that route between autonomous systems are referred to as Exterior Gateway Protocols (EGP’s) • Example: Border Gateway Protocol (BGP), which is the most widely used EGP is a path vector routing protocol. (Not all EGP’s use path-vector routing) • Path vector routing maintains path information that is updated dynamically. It is different from the distance vector routing and link state routing as each entry in the routing table contains the destination network, the next router and the path to reach the destination. 31

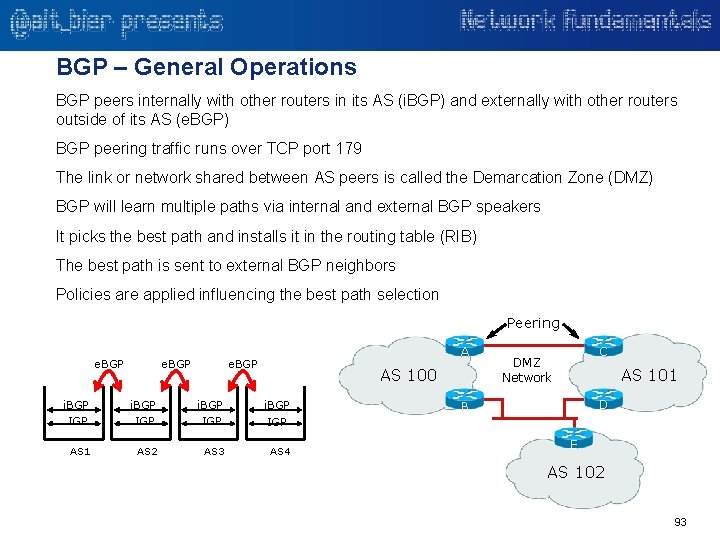
Network – Layer 3 – Routing Over Redundant Paths If there was only one road leading to a destination and there was an accident on that road you would be forced to wait for it to clear to proceed. However, most destinations have more than one way to get to them. The same is true with routed networks. While a redundant path may exist it may not be the preferred method of getting to your destination. If your primary path is a highway and your redundant path is along surface streets with several stops lights, you would usually prefer the primary highway path. This redundant surface street path would be available in the case of an accident on the primary path. It may not be the preferred path, but it is better than no path. The network equivalent of this example would be a site with a private circuit and an internet circuit both of which can connect a remote site to a data center. The private circuit would be preferred unless there was a problem with it in which case the internet circuit can be used. This concept of primary and secondary but less preferred network connections is often called an active-passive design. In an activepassive design the redundant path would only be used in the case of a failure on the primary path. If both paths were equally preferred they could both be used in an active-active design. 32

Network – Layer 3 – Performance Routing (Pf. R) is a network term that refers to a process that monitors the network paths and changes the way traffic routes dynamically based on the performance and policies. In short, it uses redundant paths for certain traffic when it makes sense to, not just during a failure. So just like a driver not authorized for HOV lanes on the highway may choose to take surface roads to avoid congestion, Pf. R will choose to route some traffic on a redundant circuit if the primary is congested. Quality of Service (Qo. S) would still work on an MPLS connection the way it normally would and traffic with Class of Service (Co. S) classifications higher than best effort could continue to prefer an MPLS circuit over an Internet circuit. Pf. R can help prevent congestion on the primary MPLS circuit by routing certain traffic via the redundant Internet circuit. Products like Cisco’s Intelligent Wide Area Network (IWAN) utilize Pf. R to make the best use of all the available networks. 33

Network – Layer 3 – Load Balancing Load balancing in networking is the process of distributing traffic and workload across multiple resources, such as servers, network links, or storage. Load balancing aims to optimize resource use, maximize throughput, minimize response time, and avoid overload of any single resource. Load balancers are devices that distribute network or application traffic across a number of devices. Load balancers are used to increase capacity and reliability of services. Simple load balancing operates at layer 3 where traffic destined to a single specific IP address can be forwarded by the load balancer to multiple separate IP addresses. There are several algorithms that can be used to load balance traffic: • Round robin • Weighted round robin • Least connections • Least response time This network layer load balancing is typically seen with network devices rather than services or applications (e. g. load balancing traffic across two redundant firewalls). Most modern load balancers operate at either layers 3 -4 (a network service load balancer) or at layers 3 -7 (an application load balancer). These more advanced load balancing features will be reviewed later in those layers. 34

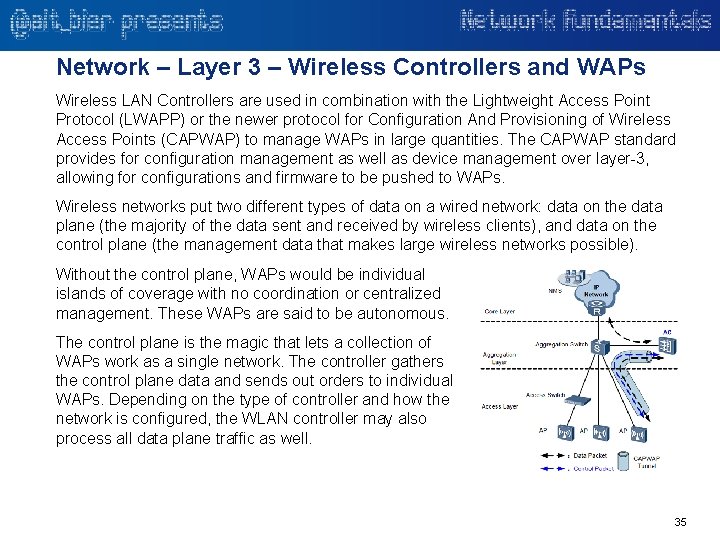
Network – Layer 3 – Wireless Controllers and WAPs Wireless LAN Controllers are used in combination with the Lightweight Access Point Protocol (LWAPP) or the newer protocol for Configuration And Provisioning of Wireless Access Points (CAPWAP) to manage WAPs in large quantities. The CAPWAP standard provides for configuration management as well as device management over layer-3, allowing for configurations and firmware to be pushed to WAPs. Wireless networks put two different types of data on a wired network: data on the data plane (the majority of the data sent and received by wireless clients), and data on the control plane (the management data that makes large wireless networks possible). Without the control plane, WAPs would be individual islands of coverage with no coordination or centralized management. These WAPs are said to be autonomous. The control plane is the magic that lets a collection of WAPs work as a single network. The controller gathers the control plane data and sends out orders to individual WAPs. Depending on the type of controller and how the network is configured, the WLAN controller may also process all data plane traffic as well. 35

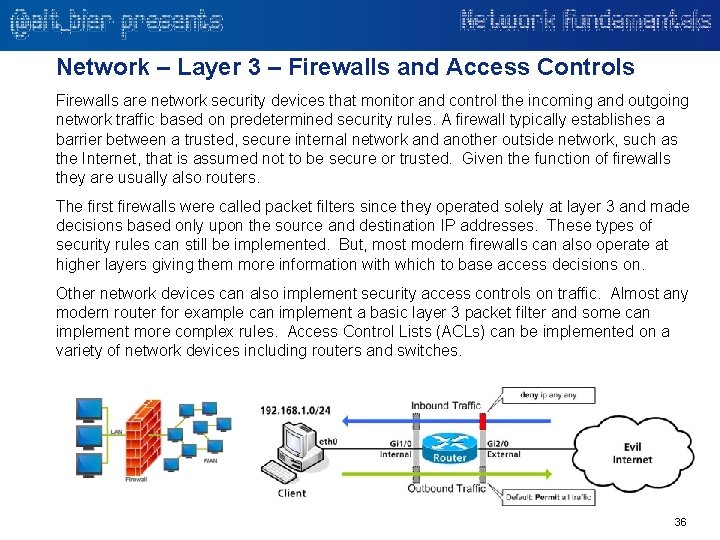
Network – Layer 3 – Firewalls and Access Controls Firewalls are network security devices that monitor and control the incoming and outgoing network traffic based on predetermined security rules. A firewall typically establishes a barrier between a trusted, secure internal network and another outside network, such as the Internet, that is assumed not to be secure or trusted. Given the function of firewalls they are usually also routers. The first firewalls were called packet filters since they operated solely at layer 3 and made decisions based only upon the source and destination IP addresses. These types of security rules can still be implemented. But, most modern firewalls can also operate at higher layers giving them more information with which to base access decisions on. Other network devices can also implement security access controls on traffic. Almost any modern router for example can implement a basic layer 3 packet filter and some can implement more complex rules. Access Control Lists (ACLs) can be implemented on a variety of network devices including routers and switches. 36

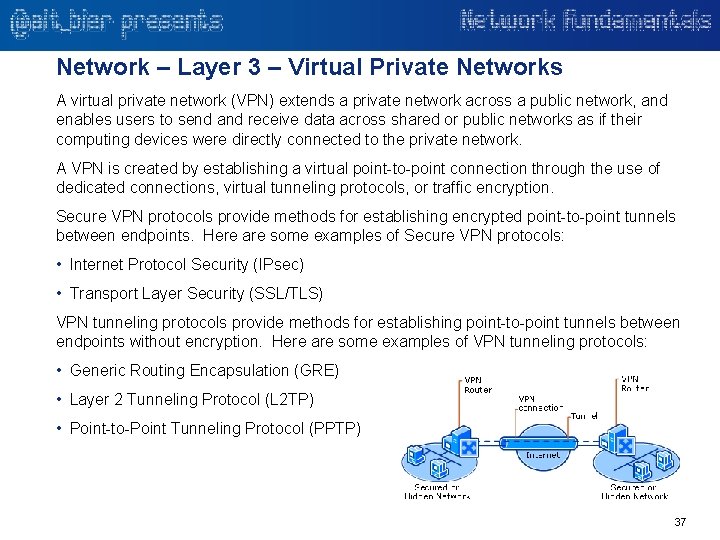
Network – Layer 3 – Virtual Private Networks A virtual private network (VPN) extends a private network across a public network, and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. A VPN is created by establishing a virtual point-to-point connection through the use of dedicated connections, virtual tunneling protocols, or traffic encryption. Secure VPN protocols provide methods for establishing encrypted point-to-point tunnels between endpoints. Here are some examples of Secure VPN protocols: • Internet Protocol Security (IPsec) • Transport Layer Security (SSL/TLS) VPN tunneling protocols provide methods for establishing point-to-point tunnels between endpoints without encryption. Here are some examples of VPN tunneling protocols: • Generic Routing Encapsulation (GRE) • Layer 2 Tunneling Protocol (L 2 TP) • Point-to-Point Tunneling Protocol (PPTP) 37

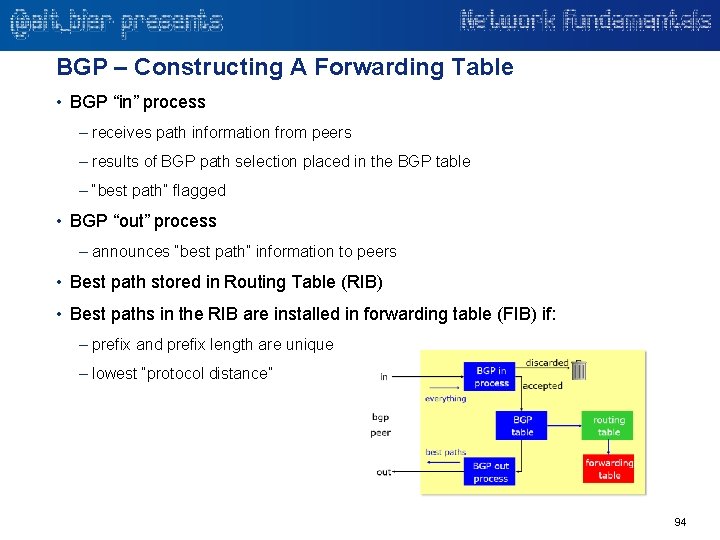
The Transport Layer – OSI Layer 4 Network Components Operating At This Layer Firewall Intrusion Detection & Prevention Load Balancer Multi-Service Switch Network Flow Monitor Proxy

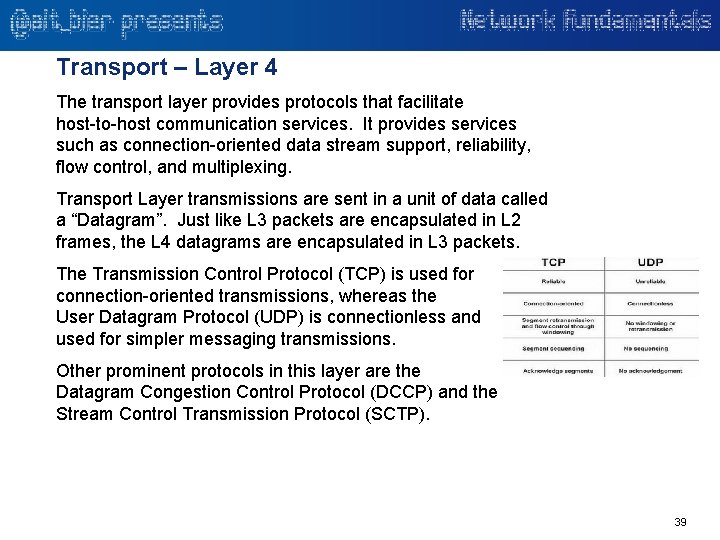
Transport – Layer 4 The transport layer provides protocols that facilitate host-to-host communication services. It provides services such as connection-oriented data stream support, reliability, flow control, and multiplexing. Transport Layer transmissions are sent in a unit of data called a “Datagram”. Just like L 3 packets are encapsulated in L 2 frames, the L 4 datagrams are encapsulated in L 3 packets. The Transmission Control Protocol (TCP) is used for connection-oriented transmissions, whereas the User Datagram Protocol (UDP) is connectionless and used for simpler messaging transmissions. Other prominent protocols in this layer are the Datagram Congestion Control Protocol (DCCP) and the Stream Control Transmission Protocol (SCTP). 39

Transport – Layer 4 – TCP is a connection-oriented protocol. It creates a virtual connection between two hosts to send data. TCP is a complex protocol, due to its stateful design incorporating reliable transmission and data stream services. TCP provides reliable, ordered, flow controlled, and error-checked delivery of a stream of octets between applications running on hosts. TCP provides host-to-host connectivity at the transport layer. An application does not need to know the mechanisms for sending data to another host, such as the required packet fragmentation on the transmission medium. The TCP protocol handles all handshaking and transmission details and presents an abstraction of the network connection to the application. TCP is used extensively by many applications available by internet, including the World Wide Web (WWW), E-mail, File Transfer Protocol, Secure Shell, peer-to-peer file sharing, and streaming media applications. TCP is optimized for accurate delivery rather than timely delivery and can incur relatively long delays while waiting for out-of-order messages or retransmissions of lost messages. Therefore, it is not particularly suitable for real -time applications such as Voice over IP. For these, protocols like the Realtime Transport Protocol (RTP) operating over UDP are recommended. 40

Transport – Layer 4 – UDP a connectionless, unreliable transport protocol. It does not add anything to the services of IP except to provide process-to-process communication instead of host-to-host communication. UDP is suitable for purposes where error checking and correction are either not necessary or are performed in the application layer. A number of UDP's attributes make it especially suited for certain applications: • It is transaction-oriented, suitable for simple query-response protocols such as the Domain Name System (DNS) or the Network Time Protocol (NTP). • It is simple, suitable for bootstrapping or other purposes without a full protocol stack, such as the DHCP and Trivial File Transfer Protocol (TFTP). • It is stateless, suitable for very large numbers of clients, such as in streaming media applications such as IPTV. • The lack of retransmission delays makes it suitable for real-time applications such as Voice over IP, online games, and many protocols built on top of the Real Time Streaming Protocol. • It works well in unidirectional communication and is suitable for broadcast information such as in many kinds of service discovery and shared information such as broadcast time or Routing Information Protocols. 41

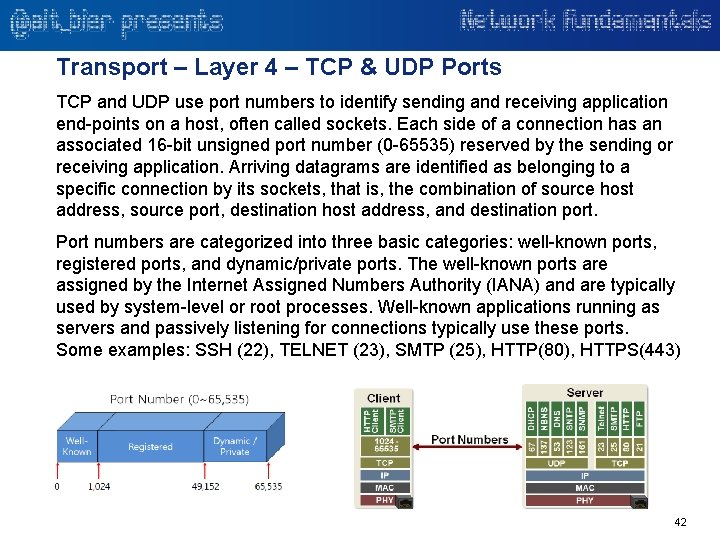
Transport – Layer 4 – TCP & UDP Ports TCP and UDP use port numbers to identify sending and receiving application end-points on a host, often called sockets. Each side of a connection has an associated 16 -bit unsigned port number (0 -65535) reserved by the sending or receiving application. Arriving datagrams are identified as belonging to a specific connection by its sockets, that is, the combination of source host address, source port, destination host address, and destination port. Port numbers are categorized into three basic categories: well-known ports, registered ports, and dynamic/private ports. The well-known ports are assigned by the Internet Assigned Numbers Authority (IANA) and are typically used by system-level or root processes. Well-known applications running as servers and passively listening for connections typically use these ports. Some examples: SSH (22), TELNET (23), SMTP (25), HTTP(80), HTTPS(443) 42

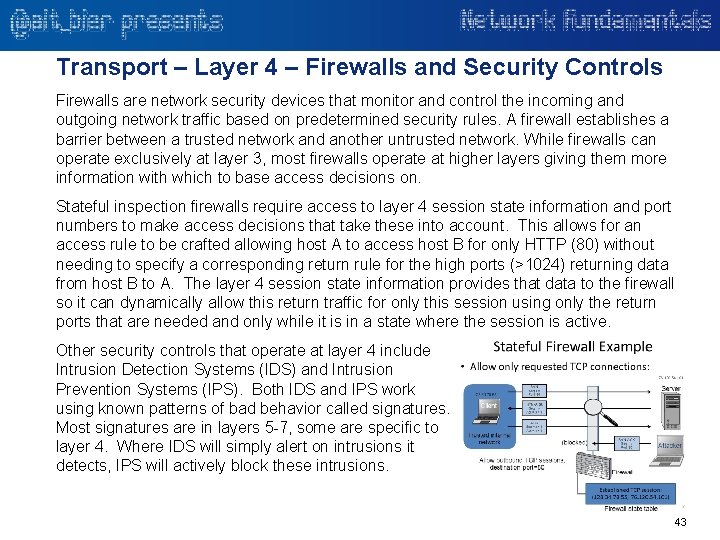
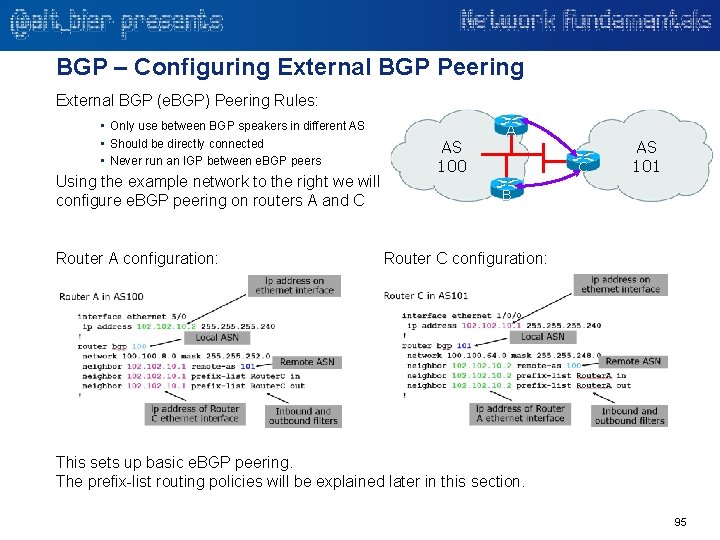
Transport – Layer 4 – Firewalls and Security Controls Firewalls are network security devices that monitor and control the incoming and outgoing network traffic based on predetermined security rules. A firewall establishes a barrier between a trusted network and another untrusted network. While firewalls can operate exclusively at layer 3, most firewalls operate at higher layers giving them more information with which to base access decisions on. Stateful inspection firewalls require access to layer 4 session state information and port numbers to make access decisions that take these into account. This allows for an access rule to be crafted allowing host A to access host B for only HTTP (80) without needing to specify a corresponding return rule for the high ports (>1024) returning data from host B to A. The layer 4 session state information provides that data to the firewall so it can dynamically allow this return traffic for only this session using only the return ports that are needed and only while it is in a state where the session is active. Other security controls that operate at layer 4 include Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS). Both IDS and IPS work using known patterns of bad behavior called signatures. Most signatures are in layers 5 -7, some are specific to layer 4. Where IDS will simply alert on intrusions it detects, IPS will actively block these intrusions. 43

Transport – Layer 4 – Firewall Rules You create firewall rules to allow this devices to send traffic to, or receive traffic from, programs, system services, computers, or users. Firewall rules can be created to take one of several actions for all connections that match the rule's criteria: • Allow the connection only if secured (IPSec) • Block the connection (normal ICMP messages) • Drop the connection (no ICMP messages sent) Rules can be created for either inbound traffic or outbound traffic. You can specify which type of network adapter the rule will be applied to: local area network (LAN), wireless, remote access, such as a virtual private network (VPN) connection, or all types. You can also configure different rules to be applied when different profiles are used. Firewall rule priority: Most firewalls apply their rules in a top down list match (called a waterfall method) where the first rule in the list that matches is applied. This allows for rules to be constructed that would look to conflict but are actually looking to catch matches at different points in the rule set. 44

Transport – Layer 4 – Load Balancers & Proxy Servers As previously discussed load balancers are devices that distribute network or application traffic across a number of devices. There are several algorithms that can be used to load balance traffic: Round robin, Weighted round robin, Least connections, Least response time, and more At layer 4 load balancers have visibility of network information such as application ports and session state. Load balancers can use this information to provide targeted application load balancing to servers that host that application. For example, a web service that is running on TCP port 80 on multiple servers. An application load balancer can perform other functions including higher layers such as a service called SSL offload. This would have a load balancer accept and terminate HTTPS connections at TCP port 443 using the TLS certificate for that web site and then it will forward these connections on to servers listening on HTTP port 80 to get the content. In this manner the load balancer is acting like a proxy for the web content and taking the load of encryption/decryption off of the web servers. Proxy servers are devices that are dedicated to this form of traffic shaping without attempting to balance loads. A proxy server can be used to proxy application traffic thru it for multiple reasons including forwarding between private and public networks without NAT, inspecting traffic heading for certain destinations, reduced complexity of firewall rules (the proxy could be the only source address in a security rule), and more. 45

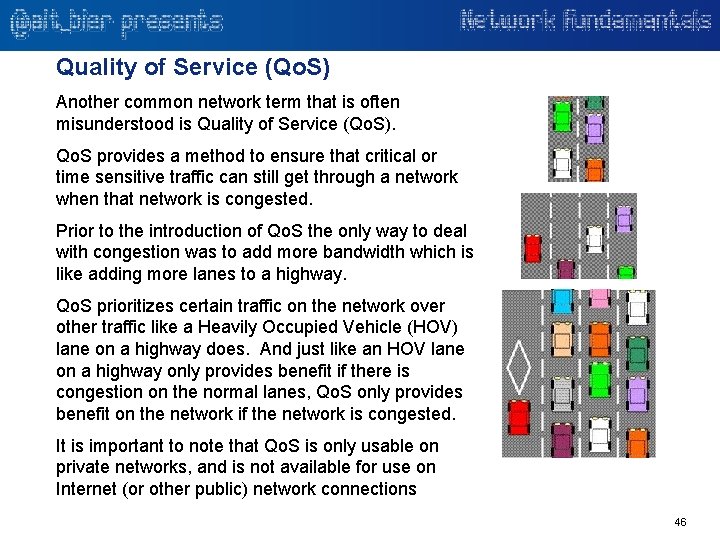
Quality of Service (Qo. S) Another common network term that is often misunderstood is Quality of Service (Qo. S). Qo. S provides a method to ensure that critical or time sensitive traffic can still get through a network when that network is congested. Prior to the introduction of Qo. S the only way to deal with congestion was to add more bandwidth which is like adding more lanes to a highway. Qo. S prioritizes certain traffic on the network over other traffic like a Heavily Occupied Vehicle (HOV) lane on a highway does. And just like an HOV lane on a highway only provides benefit if there is congestion on the normal lanes, Qo. S only provides benefit on the network if the network is congested. It is important to note that Qo. S is only usable on private networks, and is not available for use on Internet (or other public) network connections 46

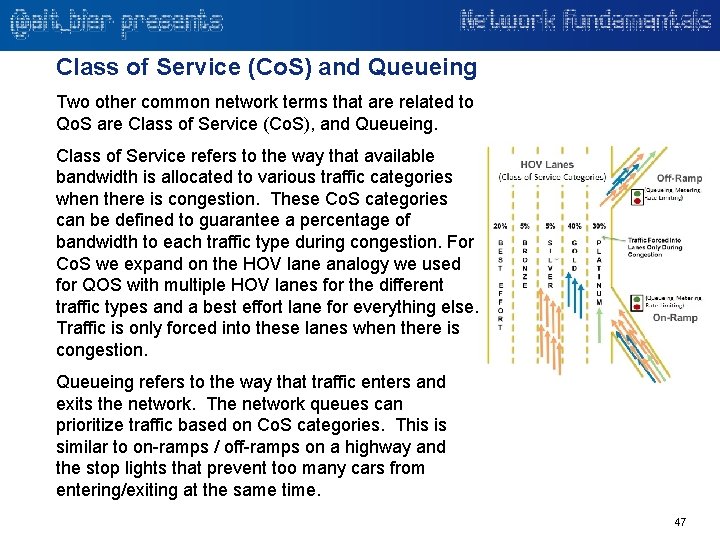
Class of Service (Co. S) and Queueing Two other common network terms that are related to Qo. S are Class of Service (Co. S), and Queueing. Class of Service refers to the way that available bandwidth is allocated to various traffic categories when there is congestion. These Co. S categories can be defined to guarantee a percentage of bandwidth to each traffic type during congestion. For Co. S we expand on the HOV lane analogy we used for QOS with multiple HOV lanes for the different traffic types and a best effort lane for everything else. Traffic is only forced into these lanes when there is congestion. Queueing refers to the way that traffic enters and exits the network. The network queues can prioritize traffic based on Co. S categories. This is similar to on-ramps / off-ramps on a highway and the stop lights that prevent too many cars from entering/exiting at the same time. 47

The Session, Presentation, and Application Layers – OSI Layers 5 -7 Network Components Operating At This Layer Firewall Intrusion Detection & Prevention Voice / Video Control Content Filters and Content Delivery Data Leakage Prevention

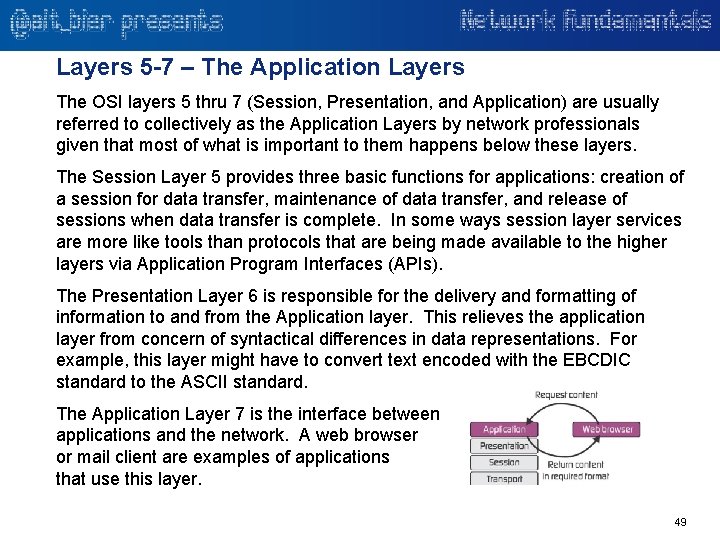
Layers 5 -7 – The Application Layers The OSI layers 5 thru 7 (Session, Presentation, and Application) are usually referred to collectively as the Application Layers by network professionals given that most of what is important to them happens below these layers. The Session Layer 5 provides three basic functions for applications: creation of a session for data transfer, maintenance of data transfer, and release of sessions when data transfer is complete. In some ways session layer services are more like tools than protocols that are being made available to the higher layers via Application Program Interfaces (APIs). The Presentation Layer 6 is responsible for the delivery and formatting of information to and from the Application layer. This relieves the application layer from concern of syntactical differences in data representations. For example, this layer might have to convert text encoded with the EBCDIC standard to the ASCII standard. The Application Layer 7 is the interface between applications and the network. A web browser or mail client are examples of applications that use this layer. 49

Layers 5 -7 – Content Filters and Content Delivery Content Filtering is the process of blocking network access to content based on rules or signatures for security or other reasons. It usually works by defining specific rules and/or signatures identifying the content that should be blocked and then when the rules are met or signatures are seen access to the specific resource is denied. An example of content filtering is on a web proxy server where certain web sites or images may need to be blocked to prevent inappropriate images or malicious files from being accessed. Content Delivery is the process of bringing content closer to the devices that will access it to increase network performance to this content. This can be localized within a network where a Content Delivery device might be placed at a remote office to pre-fetch some of the most used content from a data center to reduce WAN bandwidth and increase performance. This can also be deployed globally using an entire network of globally diverse Content Delivery devices to provide better access to a previously regional resource. This is referred to as a Content Delivery Network (CDN) and is available as a service on the Internet from several companies. 50

Layers 5 -7 – Data Loss/Leakage Prevention (DLP) is a strategy for making sure that end users do not send sensitive or business critical information outside of a secured network. DLP devices are typically placed at the exit nodes of a secured network where they can monitor traffic leaving this network and compare it to business rules that classify confidential and critical information so that users cannot accidentally or maliciously share this data. Sometimes DLP as a function is incorporated into another network device such as a proxy server or firewall. The business rules that allow DLP to work are similar to the signatures used by IPS. However, where IPS can automatically update its signatures from various 3 rd party security firms, DLP rules are specific to a business and are usually much too specific to be entirely compiled from other sources. For example, if a company stores its secret sauce recipe in a certain format it can write a DLP rule to look for any text matching that recipe format. 51

Would You Like To Know More? Lets delve into more details on some of the previous topics

Virtual Local Area Networks (VLANs) Understanding, Configuring, and Troubleshooting VLAN’s

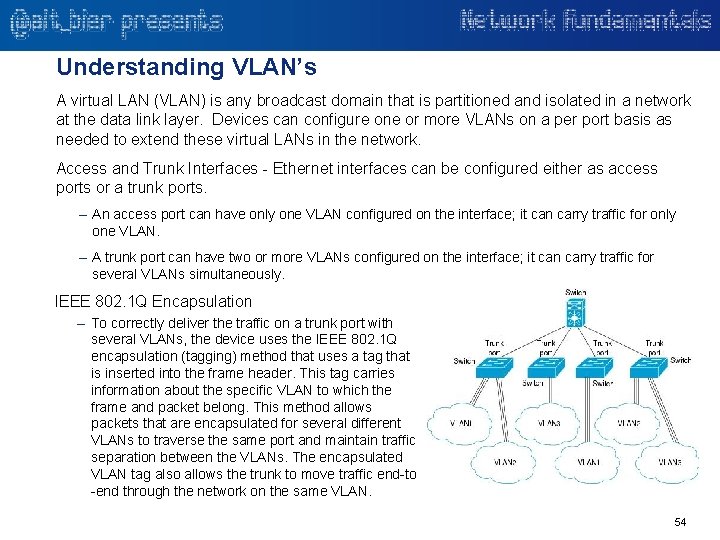
Understanding VLAN’s A virtual LAN (VLAN) is any broadcast domain that is partitioned and isolated in a network at the data link layer. Devices can configure one or more VLANs on a per port basis as needed to extend these virtual LANs in the network. Access and Trunk Interfaces - Ethernet interfaces can be configured either as access ports or a trunk ports. – An access port can have only one VLAN configured on the interface; it can carry traffic for only one VLAN. – A trunk port can have two or more VLANs configured on the interface; it can carry traffic for several VLANs simultaneously. IEEE 802. 1 Q Encapsulation – To correctly deliver the traffic on a trunk port with several VLANs, the device uses the IEEE 802. 1 Q encapsulation (tagging) method that uses a tag that is inserted into the frame header. This tag carries information about the specific VLAN to which the frame and packet belong. This method allows packets that are encapsulated for several different VLANs to traverse the same port and maintain traffic separation between the VLANs. The encapsulated VLAN tag also allows the trunk to move traffic end-to -end through the network on the same VLAN. 54

VLAN Trunking Protocol (VTP) is a Cisco proprietary protocol that propagates the definition of Virtual Local Area Networks (VLAN) on the whole local area network. To do this, VTP carries VLAN information to all the switches in a VTP domain. VTP advertisements can be sent over 802. 1 Q trunks. Using VTP, each Catalyst Family Switch advertises the following on its trunk ports: • Management domain • Configuration revision number • Known VLANs and their specific parameters There are three versions of VTP, namely version 1, version 2, version 3. The comparable IEEE standard in use by other manufacturers is GVRP or the more recent MVRP. VTP provides the following benefits: • VLAN configuration consistency across the layer 2 network • Dynamic distribution of added VLANs across the network • Plug-and-play configuration when adding new VLANs 55

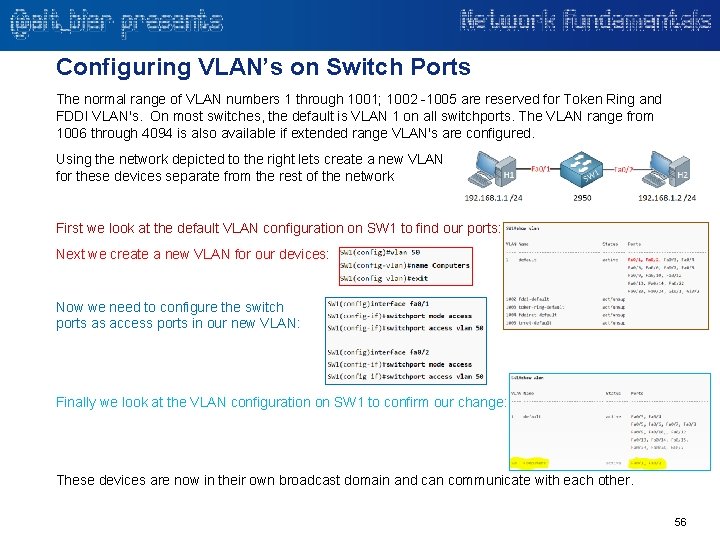
Configuring VLAN’s on Switch Ports The normal range of VLAN numbers 1 through 1001; 1002 -1005 are reserved for Token Ring and FDDI VLAN's. On most switches, the default is VLAN 1 on all switchports. The VLAN range from 1006 through 4094 is also available if extended range VLAN's are configured. Using the network depicted to the right lets create a new VLAN for these devices separate from the rest of the network First we look at the default VLAN configuration on SW 1 to find our ports: Next we create a new VLAN for our devices: Now we need to configure the switch ports as access ports in our new VLAN: Finally we look at the VLAN configuration on SW 1 to confirm our change: These devices are now in their own broadcast domain and can communicate with each other. 56

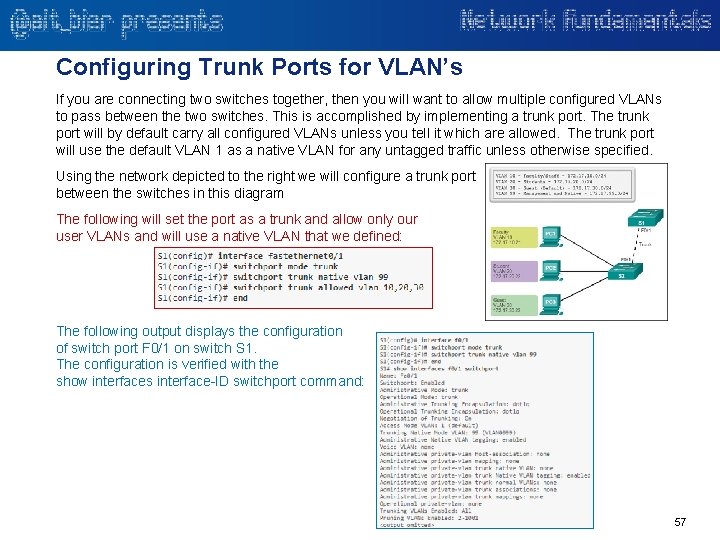
Configuring Trunk Ports for VLAN’s If you are connecting two switches together, then you will want to allow multiple configured VLANs to pass between the two switches. This is accomplished by implementing a trunk port. The trunk port will by default carry all configured VLANs unless you tell it which are allowed. The trunk port will use the default VLAN 1 as a native VLAN for any untagged traffic unless otherwise specified. Using the network depicted to the right we will configure a trunk port between the switches in this diagram The following will set the port as a trunk and allow only our user VLANs and will use a native VLAN that we defined: The following output displays the configuration of switch port F 0/1 on switch S 1. The configuration is verified with the show interfaces interface-ID switchport command: 57

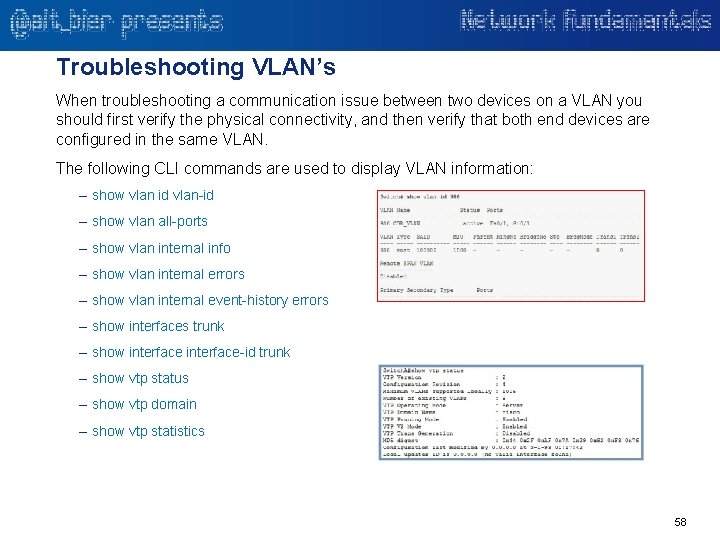
Troubleshooting VLAN’s When troubleshooting a communication issue between two devices on a VLAN you should first verify the physical connectivity, and then verify that both end devices are configured in the same VLAN. The following CLI commands are used to display VLAN information: – show vlan id vlan-id – show vlan all-ports – show vlan internal info – show vlan internal errors – show vlan internal event-history errors – show interfaces trunk – show interface-id trunk – show vtp status – show vtp domain – show vtp statistics 58

Spanning Tree Protocol (STP) Understanding, Configuring, and Monitoring STP

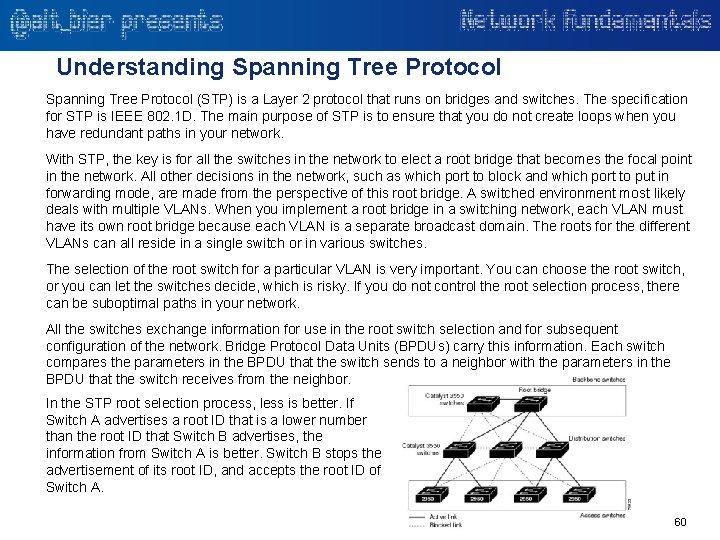
Understanding Spanning Tree Protocol (STP) is a Layer 2 protocol that runs on bridges and switches. The specification for STP is IEEE 802. 1 D. The main purpose of STP is to ensure that you do not create loops when you have redundant paths in your network. With STP, the key is for all the switches in the network to elect a root bridge that becomes the focal point in the network. All other decisions in the network, such as which port to block and which port to put in forwarding mode, are made from the perspective of this root bridge. A switched environment most likely deals with multiple VLANs. When you implement a root bridge in a switching network, each VLAN must have its own root bridge because each VLAN is a separate broadcast domain. The roots for the different VLANs can all reside in a single switch or in various switches. The selection of the root switch for a particular VLAN is very important. You can choose the root switch, or you can let the switches decide, which is risky. If you do not control the root selection process, there can be suboptimal paths in your network. All the switches exchange information for use in the root switch selection and for subsequent configuration of the network. Bridge Protocol Data Units (BPDUs) carry this information. Each switch compares the parameters in the BPDU that the switch sends to a neighbor with the parameters in the BPDU that the switch receives from the neighbor. In the STP root selection process, less is better. If Switch A advertises a root ID that is a lower number than the root ID that Switch B advertises, the information from Switch A is better. Switch B stops the advertisement of its root ID, and accepts the root ID of Switch A. 60

Understanding Spanning Tree Protocol STP Rules of Operation: These are the rules for how STP works. When the switches first come up, they start the root switch selection process. Each switch transmits a BPDU to the directly connected switch on a per-VLAN basis. As the BPDU goes out through the network, each switch compares the BPDU that the switch sends to the BPDU that the switch receives from the neighbors. The switches then agree on which switch is the root switch. The switch with the lowest bridge ID in the network wins this election process. One root switch is identified per-VLAN. After the root switch identification, the switches adhere to these rules: STP Rule 1 — All ports of the root switch must be in forwarding mode. Next, each switch determines the best path to get to the root. The switches determine this path by a comparison of the information in all the BPDUs that the switches receive on all ports. The switch uses the port with the least amount of information in the BPDU in order to get to the root switch; the port with the least amount of information in the BPDU is the root port. After a switch determines the root port, the switch proceeds to rule 2. STP Rule 2 — The root port must be set to forwarding mode. In addition, the switches on each LAN segment communicate with each other to determine which switch is best to use in order to move data from that segment to the root bridge. This switch is called the designated switch. STP Rule 3 — In a single LAN segment, the port of the designated switch that connects to that LAN segment must be placed in forwarding mode. STP Rule 4 — All the other ports in all the switches (VLAN-specific) must be placed in blocking mode. The rule only applies to ports that connect to other bridges or switches. Ports that connect to workstations or PCs remain forwarded. Note: The addition or removal of VLANs when STP runs in per-VLAN spanning tree (PVST / PVST+) mode triggers spanning tree recalculation for that VLAN instance and the traffic is disrupted only for that VLAN. The other VLAN parts of a trunk link can forward traffic normally. The addition or removal of VLANs for a Multiple Spanning Tree (MST) instance that exists triggers spanning tree recalculation for that instance and traffic is disrupted for all the VLAN parts of that MST instance which could impact an entire network. 61

Understanding Spanning Tree Protocol The Bridge ID (BID): The Bridge ID is used by STP in the root bridge election process that makes up the tree. Each VLAN on each network device has a unique 64 -bit bridge ID consisting of a bridge priority value, an extended system ID, and an STP MAC address allocation. Bridge Priority Value: The bridge priority value determines whether a given redundant link is given priority and considered part of a given span in a spanning tree. Preference is given to lower values, and if you want to manually configure a preference, assign a lower bridge priority value to a link than to its redundant possibility. Extended System ID: As networks begun to grow and become more complex, VLANs were introduced, allowing the creation of multiple logical and physical networks. It was then necessary to run multiple instances of STP in order to accommodate each network - VLAN. These multiple instances are called Multiple Spanning Tree (MST), Per-VLAN Spanning Tree (PVST) and Per-VLAN Spanning Tree Plus (PVST+). In order to accommodate the additional VLAN information, the Extended System ID field was introduced, borrowing 12 bits from the original Bridge Priority: Extended system IDs are VLAN IDs between 1025 and 4096. STP MAC Address Allocation: This is the MAC address available on the switch to support software features like STP. This MAC address is usually not tied to a specific interface of the switch. 62

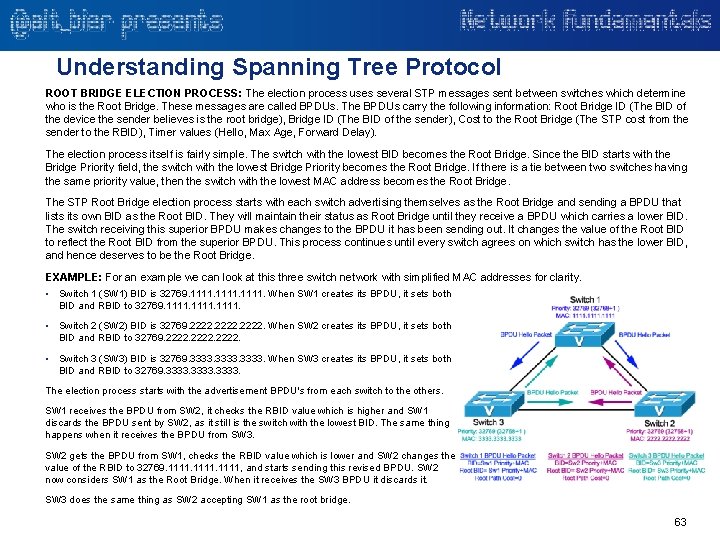
Understanding Spanning Tree Protocol ROOT BRIDGE ELECTION PROCESS: The election process uses several STP messages sent between switches which determine who is the Root Bridge. These messages are called BPDUs. The BPDUs carry the following information: Root Bridge ID (The BID of the device the sender believes is the root bridge), Bridge ID (The BID of the sender), Cost to the Root Bridge (The STP cost from the sender to the RBID), Timer values (Hello, Max Age, Forward Delay). The election process itself is fairly simple. The switch with the lowest BID becomes the Root Bridge. Since the BID starts with the Bridge Priority field, the switch with the lowest Bridge Priority becomes the Root Bridge. If there is a tie between two switches having the same priority value, then the switch with the lowest MAC address becomes the Root Bridge. The STP Root Bridge election process starts with each switch advertising themselves as the Root Bridge and sending a BPDU that lists its own BID as the Root BID. They will maintain their status as Root Bridge until they receive a BPDU which carries a lower BID. The switch receiving this superior BPDU makes changes to the BPDU it has been sending out. It changes the value of the Root BID to reflect the Root BID from the superior BPDU. This process continues until every switch agrees on which switch has the lower BID, and hence deserves to be the Root Bridge. EXAMPLE: For an example we can look at this three switch network with simplified MAC addresses for clarity. • Switch 1 (SW 1) BID is 32769. 1111. When SW 1 creates its BPDU, it sets both BID and RBID to 32769. 1111. • Switch 2 (SW 2) BID is 32769. 2222. When SW 2 creates its BPDU, it sets both BID and RBID to 32769. 2222. • Switch 3 (SW 3) BID is 32769. 3333. When SW 3 creates its BPDU, it sets both BID and RBID to 32769. 3333. The election process starts with the advertisement BPDU's from each switch to the others. SW 1 receives the BPDU from SW 2, it checks the RBID value which is higher and SW 1 discards the BPDU sent by SW 2, as it still is the switch with the lowest BID. The same thing happens when it receives the BPDU from SW 3. SW 2 gets the BPDU from SW 1, checks the RBID value which is lower and SW 2 changes the value of the RBID to 32769. 1111, and starts sending this revised BPDU. SW 2 now considers SW 1 as the Root Bridge. When it receives the SW 3 BPDU it discards it. SW 3 does the same thing as SW 2 accepting SW 1 as the root bridge. 63

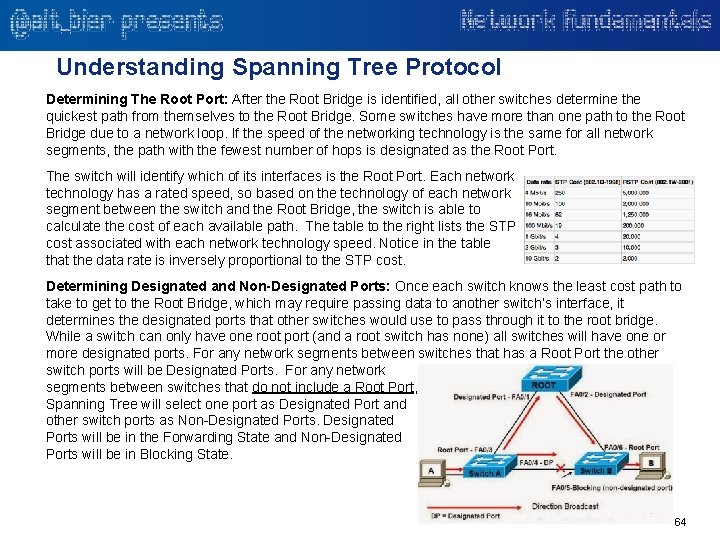
Understanding Spanning Tree Protocol Determining The Root Port: After the Root Bridge is identified, all other switches determine the quickest path from themselves to the Root Bridge. Some switches have more than one path to the Root Bridge due to a network loop. If the speed of the networking technology is the same for all network segments, the path with the fewest number of hops is designated as the Root Port. The switch will identify which of its interfaces is the Root Port. Each network technology has a rated speed, so based on the technology of each network segment between the switch and the Root Bridge, the switch is able to calculate the cost of each available path. The table to the right lists the STP cost associated with each network technology speed. Notice in the table that the data rate is inversely proportional to the STP cost. Determining Designated and Non-Designated Ports: Once each switch knows the least cost path to take to get to the Root Bridge, which may require passing data to another switch’s interface, it determines the designated ports that other switches would use to pass through it to the root bridge. While a switch can only have one root port (and a root switch has none) all switches will have one or more designated ports. For any network segments between switches that has a Root Port the other switch ports will be Designated Ports. For any network segments between switches that do not include a Root Port, Spanning Tree will select one port as Designated Port and other switch ports as Non-Designated Ports will be in the Forwarding State and Non-Designated Ports will be in Blocking State. 64

Understanding Spanning Tree Protocol Optional STP Configurations: Beyond the basics of STP operations there are some configuration options that can enhance and improve its performance if implemented. Port Fast – Port Fast immediately brings an interface configured as an access or trunk port to the forwarding state from a blocking state, bypassing the listening and learning states. You can use Port Fast on interfaces connected to a single workstation or server to allow those devices to immediately connect to the network, rather than waiting for the spanning tree to converge. BPDU Guard – The BPDU guard feature can be enabled on the switch entirely or per port, but the feature operates with some differences. When you enable BPDU guard at the switch level it will monitor all Port Fast-enabled ports on the switch for BPDUs and if it sees any it will disable that port. When you enable BPDU guard at the interface level it works the same way regardless of the Port-Fast setting. Root Guard – A Layer 2 network can include connections to switches that are owned and managed by multiple groups. In such a topology, spanning tree might reconfigure itself and select a non-optimal switch as the root switch. You can avoid this situation by enabling root guard on switch interfaces that connect to switches outside of your control. If spanning-tree calculations cause an interface leading to a foreign switch to be selected as the root port, root guard then places the interface in the rootinconsistent (blocked) state to prevent the foreign switch from becoming the root switch or the path to the root. 65

Configuring / Monitoring Spanning Tree Protocol You can enable a spanning tree on a per-VLAN basis. The switch maintains a separate instance of spanning tree for each VLAN (except on VLANs on which you have disabled a spanning tree). To enable a spanning tree on a per-VLAN basis, perform the following commands : – configure terminal – spanning-tree vlan <vlan-id> – end To configure the bridge priority of a VLAN, perform the following commands : To verify spanning tree settings for a VLAN, perform the following command: – show spanning-tree vlan <vlan-id> Monitor Spanning-Tree status with the following commands: – show spanning-tree active – show spanning-tree detail – configure terminal – show spanning-tree interface <interface-id> – spanning-tree vlan <vlan-id> priority <bridge-priority> – show spanning-tree summary – end – show spanning-tree vlan bridge To configure Port Fast on an interface, perform the following commands : – configure terminal – Interface <interface-id> – spanning-tree portfast – end 66

Routing Configuring, and Troubleshooting Routing

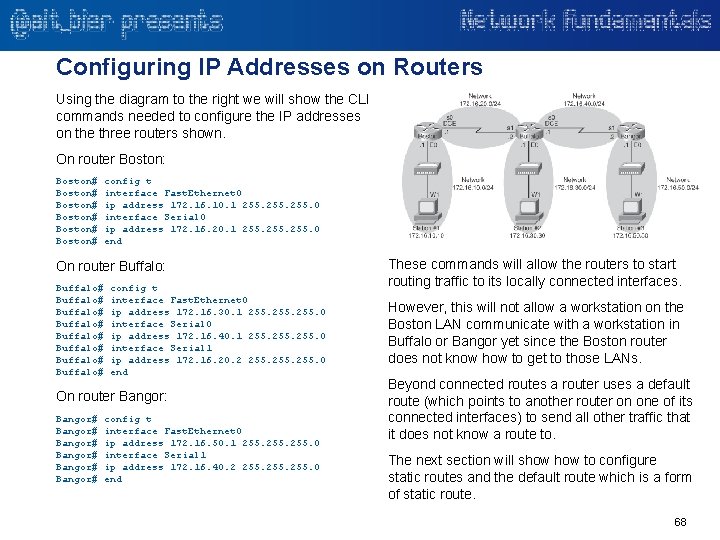
Configuring IP Addresses on Routers Using the diagram to the right we will show the CLI commands needed to configure the IP addresses on the three routers shown. On router Boston: Boston# Boston# config t interface Fast. Ethernet 0 ip address 172. 16. 10. 1 255. 0 interface Serial 0 ip address 172. 16. 20. 1 255. 0 end On router Buffalo: Buffalo# Buffalo# config t interface Fast. Ethernet 0 ip address 172. 16. 30. 1 255. 0 interface Serial 0 ip address 172. 16. 40. 1 255. 0 interface Serial 1 ip address 172. 16. 20. 2 255. 0 end On router Bangor: Bangor# Bangor# config t interface Fast. Ethernet 0 ip address 172. 16. 50. 1 255. 0 interface Serial 1 ip address 172. 16. 40. 2 255. 0 end These commands will allow the routers to start routing traffic to its locally connected interfaces. However, this will not allow a workstation on the Boston LAN communicate with a workstation in Buffalo or Bangor yet since the Boston router does not know how to get to those LANs. Beyond connected routes a router uses a default route (which points to another router on one of its connected interfaces) to send all other traffic that it does not know a route to. The next section will show to configure static routes and the default route which is a form of static route. 68

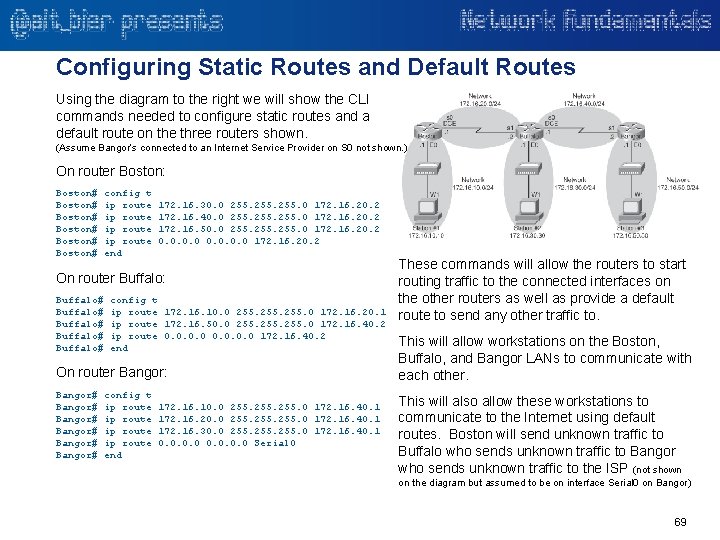
Configuring Static Routes and Default Routes Using the diagram to the right we will show the CLI commands needed to configure static routes and a default route on the three routers shown. (Assume Bangor’s connected to an Internet Service Provider on S 0 not shown. ) On router Boston: Boston# Boston# config t ip route end 172. 16. 30. 0 255. 0 172. 16. 20. 2 172. 16. 40. 0 255. 0 172. 16. 20. 2 172. 16. 50. 0 255. 0 172. 16. 20. 2 0. 0 172. 16. 20. 2 On router Buffalo: Buffalo# Buffalo# config t ip route 172. 16. 10. 0 255. 0 172. 16. 20. 1 ip route 172. 16. 50. 0 255. 0 172. 16. 40. 2 ip route 0. 0 172. 16. 40. 2 end On router Bangor: Bangor# Bangor# config t ip route end 172. 16. 10. 0 255. 0 172. 16. 40. 1 172. 16. 20. 0 255. 0 172. 16. 40. 1 172. 16. 30. 0 255. 0 172. 16. 40. 1 0. 0 Serial 0 These commands will allow the routers to start routing traffic to the connected interfaces on the other routers as well as provide a default route to send any other traffic to. This will allow workstations on the Boston, Buffalo, and Bangor LANs to communicate with each other. This will also allow these workstations to communicate to the Internet using default routes. Boston will send unknown traffic to Buffalo who sends unknown traffic to Bangor who sends unknown traffic to the ISP (not shown on the diagram but assumed to be on interface Serial 0 on Bangor) 69

Verifying Routes Using the router Boston from the previous examples we can verify the routes that this router has in its routing table (called the Routing Information Base RIB) with the following CLI command: Boston# show ip route Codes: C - connected, S - static, R - RIP, M - mobile, B – BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N 1 - OSPF NSSA external type 1, N 2 - OSPF NSSA external type 2 E 1 - OSPF external type 1, E 2 - OSPF external type 2 i - IS-IS, su - IS-IS summary, L 1 - IS-IS level-1, L 2 - IS-IS level-2 ia - IS-IS inter area, * - candidate default, U - per-user static route o - ODR, P - periodic downloaded static route C 172. 16. 10. 0/24 is directly connected, Fast. Ethernet 0 C 172. 16. 20. 0/24 is directly connected, Serial 0 S 172. 16. 30. 0/24 is directly connected, Serial 0 S 172. 16. 40. 0/24 is directly connected, Serial 0 S 172. 16. 50. 0/24 is directly connected, Serial 0 S* 0. 0/0 is directly connected, Serial 0 Note that the output from show ip route will show all the routes in the RIB classifying them by route type and where the routes were learned from. On this simple example router it is a short list. But on a real production router this list could be quite large. This command can be modified to show subsets of the RIB list instead. Here are some common uses: • show ip route connected Shows only routes for connected subnets • show ip route static Shows only static routes • show ip route bgp Shows only routes from a specific routing protocol • show ip route 172. 16. 10. 0 Shows only routes for a specific subnet 70

Administrative Distance & Floating Static Routes Administrative distance is used to apply a sort of prioritization (weight factors) on static routes, so that different routes to a given destination would follow a certain prioritization. The Administrative Distance (AD) is an integer from 0 to 255 where 0 indicates a first priority route and 255 means that no traffic is allowed to pass through this route. The default AD of directly connected interfaces is 0 and static routes is 1. To add an administrative distance to a route simply add the desired integer to the end of the route. Using the router Boston from the previous examples let us assume that we have just installed a backup internet circuit on Serial 1 (ISDN or some small non-preferred path). Given that this is only a backup and not to be used unless our primary fails we cannot change our default route which points at the primary. Instead we can additional static route with a higher administrative distance. This is called a Floating Static Route, since even though it is in the routing table it will float over the preferred route and only be used if that preferred route is no longer available. Boston# ip route 0. 0 Serial 0 Boston# ip route 0. 0 Serial 1 200 The first route has an implied AD of 1 and will be preferred over the second route which has an AD of 200 until that first route is no longer viable (e. g. circuit failure on Serial 0). This method of using administrative distance to adjust routes can be used with any static route not just a default route. Dynamic routing protocols also use administrative distance and different protocols have different defaults meaning by default one dynamic route may be preferred over another. Some of these AD defaults: BGP=20, EIGRP=90, OSPF=110 71

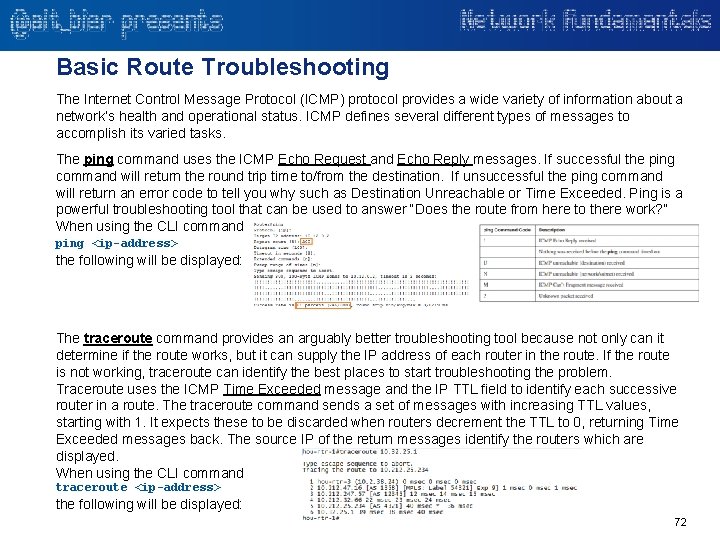
Basic Route Troubleshooting The Internet Control Message Protocol (ICMP) protocol provides a wide variety of information about a network’s health and operational status. ICMP defines several different types of messages to accomplish its varied tasks. The ping command uses the ICMP Echo Request and Echo Reply messages. If successful the ping command will return the round trip time to/from the destination. If unsuccessful the ping command will return an error code to tell you why such as Destination Unreachable or Time Exceeded. Ping is a powerful troubleshooting tool that can be used to answer “Does the route from here to there work? ” When using the CLI command ping <ip-address> the following will be displayed: The traceroute command provides an arguably better troubleshooting tool because not only can it determine if the route works, but it can supply the IP address of each router in the route. If the route is not working, traceroute can identify the best places to start troubleshooting the problem. Traceroute uses the ICMP Time Exceeded message and the IP TTL field to identify each successive router in a route. The traceroute command sends a set of messages with increasing TTL values, starting with 1. It expects these to be discarded when routers decrement the TTL to 0, returning Time Exceeded messages back. The source IP of the return messages identify the routers which are displayed. When using the CLI command traceroute <ip-address> the following will be displayed: 72

Routing with OSPF • Open Shortest Path First (OSFP) is a Routing Protocol used to exchange routing information between different networks – Interior gateway protocol – Link State aka SPF protocol – Incremental Updates – Classless Inter Domain Routing (CIDR) – Fast convergence – Runs on IP Protocol 89 • Developed by OSPF working group of IETF (RFC 1247) – OSPFv 2 standard described in RFC 2328

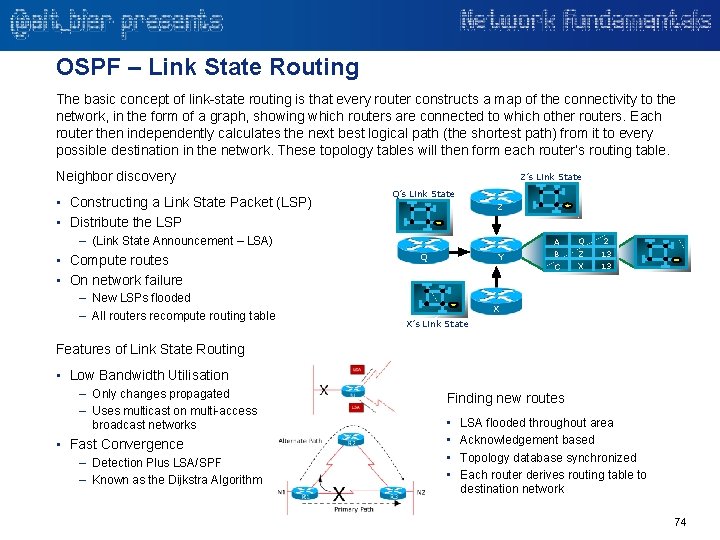
OSPF – Link State Routing The basic concept of link-state routing is that every router constructs a map of the connectivity to the network, in the form of a graph, showing which routers are connected to which other routers. Each router then independently calculates the next best logical path (the shortest path) from it to every possible destination in the network. These topology tables will then form each router’s routing table. Neighbor discovery • Constructing a Link State Packet (LSP) • Distribute the LSP Z’s Link State Q’s Link State Z – (Link State Announcement – LSA) • Compute routes • On network failure – New LSPs flooded – All routers recompute routing table Q Y A Q 2 B Z 13 C X 13 X X’s Link State Features of Link State Routing • Low Bandwidth Utilisation – Only changes propagated – Uses multicast on multi-access broadcast networks • Fast Convergence – Detection Plus LSA/SPF – Known as the Dijkstra Algorithm Finding new routes • • LSA flooded throughout area Acknowledgement based Topology database synchronized Each router derives routing table to destination network 74

OSPF – Protocol Messages Unlike other routing protocols, OSPF does not carry data via a transport protocol, such as UDP or TCP. Instead, OSPF forms IP datagrams directly, packaging them using protocol number 89 for the IP Protocol field. OSPF defines five different message types, for various types of communication: • Hello – Hello messages are used to allow a router to discover other adjacent routers on its local links and networks. This establishes relationships between neighboring devices (called adjacencies) and sends key parameters about how OSPF is to be used in the autonomous system or area. During normal operation, routers send hello messages to their neighbors at regular intervals (the hello interval); if a router stops receiving hello messages from a neighbor, after a set period (the dead interval) the router will assume the neighbor has gone down. • Database Description – Database Description messages contain descriptions of the topology of the autonomous system or area. They send the contents of the link-state database (LSDB) for the area. . Communicating a large LSDB may require several messages to be sent by having the sending device designated as a master device and sending messages in sequence, with the slave (recipient of the LSDB information) responding with acknowledgements. • Link State Request – These messages are used by one router to request updated information about a portion of the LSDB from another router. The message specifies the link(s) that the requesting device wants more current information on. • Link State Update – These messages contain updated information about the state of certain links on the LSDB. They are sent in response to a Link State Request message, and also broadcast or multicast by routers on a regular basis. Their contents are used to update the information in the LSDBs of routers that receive them. • Link State Acknowledgment – These messages provide reliability to the link-state exchange process, by explicitly acknowledging receipt of a Link State Update message. 75

OSPF – Areas An OSPF network is divided into areas that are logical groupings of hosts and networks. An area includes its connecting router having interfaces connected to the network. Each area maintains a separate link state database whose information may be summarized towards the rest of the network by the connecting router. Thus, the topology of an area is unknown outside the area. This reduces the routing traffic between parts of an autonomous system. In summary, OSPF Areas: • Are a group of contiguous hosts and networks – Reduces routing traffic • Per area topology database – Invisible outside the area • Backbone area MUST be contiguous – All other areas must be connected to the backbone OSPF defines several area types: • Backbone area – The backbone area (also known as area 0) forms the core of an OSPF network. All other areas are connected to it, either directly or through other routers. A Virtual Link can be used when it is not possible to physically connect an area to the backbone • Stub area – A stub area is an area which does not receive route advertisements external to the autonomous system (AS) and routing from within the area is based entirely on a default route. • Not-so-stubby area (NSSA) – A not-so-stubby area is a type of stub area that can import AS-external routes and send them to other areas, but still cannot receive AS-external routes from other areas. NSSA is an extension of the stub area that allows the injection of external routes in a limited fashion. • Transit area – A transit area is an area with two or more OSPF border routers and is used to pass network traffic from one adjacent area to another. 76

OSPF – Router Classifications OSPF defines the following overlapping classifications of routers: • Internal router (IR) – An internal router has all its interfaces belonging to the same area. • Area border router (ABR) – An area border router is a router that connects one or more areas to the main backbone network. It is considered a member of all areas it is connected to. An ABR keeps multiple copies of the link-state database, one for each area to which it’s connected. • Backbone router (BR) – A backbone router has an interface to the backbone area. Backbone routers may also be area routers, but do not have to be. • Autonomous system boundary router (ASBR) – An autonomous system boundary router uses multiple routing protocols typically an exterior protocol (e. g. BGP) to exchange information between different AS’s and it’s OSPF area. An ASBR distributes these external routes via External LSAs that it floods to all areas via ABR. The router type is an attribute of an OSPF process. A given physical router may have one or more OSPF processes. For example, a router connected to more than one area, and which receives routes from another BGP AS, is both an area border router (ABR) and an autonomous system boundary router (ASBR). 77

OSPF – Router Relationships OSPF supports complex networks with multiple routers, including backup routers, to balance traffic load on multiple links to other subnets. Routers running OSPF form adjacencies when they have detected each other on the network. This detection is initiated when a router identifies itself in a Hello protocol packet. Upon acknowledgment, this establishes a TWO-WAY state which is the most basic relationship. OSPF uses the terms designated router (DR) and backup designated router (BDR), in reference to the attributes of routers on the same network which will act as a hub or interface for other routers on the network to reduce protocol traffic between routers. Upon election of a BR and BDR by the Hello protocol and database synchronization the routers will establish a FULL state relationship. • Designated router (DR) – – A designated router is the router elected among all routers on a particular network segment. The basic neighbor discovery process (Hello), facilitates the DR election. There is only one DR per network. The DR generates link advertisements and assists in database synchronization • Backup designated router (BDR) – A backup designated router is a router that becomes the designated router if the current designated router has a problem or fails. – The BDR is the OSPF router with second highest priority at the time of the last election. Link-State Advertisements (LSA’s) propagate and are acknowledged along adjacencies. 78

OSPF – Hello Protocol Key Concepts • When the OSPF protocol process starts on a router, neighbors must be discovered and adjacencies established. • The router sends and listed for Hello messages to discover its neighbors. After an adjacency is formed, the Hello protocol serves as a keepalive mechanism to detect failed neighbors or adjacencies. The Hello protocol also performs other functions such as the discovery and election of Designated Routers. • When an OSPF router receives a Hello from an OSPF neighbor, it stores the information contained in the Hello in a neighbor database. • The Hello’s are sent to all SPF routers as multicast (224. 0. 0. 5). • Hello. Interval - OSPF routers send Hello’s on OSPF enabled interfaces every 10 seconds on multi-access and point-to-point segments and every 30 seconds on Non-Broadcast Multi-Access (NBMA) segments. • Router. Dead. Interval – This is the period of time a router will wait to hear a Hello from a neighbor before declaring the neighbor as down. By default this is four times the Hello. Interval or 40 seconds. Hello Protocol Packets Each Hello Packet Contains: • Router priority • Hello interval • Router dead interval • Network mask • List of neighbors • DR and BDR • Options: E-bit, MC-bit, etc… 79

OSPF – Link-State Advertisements (LSA’s) are a basic communication means for OSPF to communicate the router's local routing topology to all other local routers in the same OSPF area. OSPF is designed for scalability, so some LSAs are not flooded out on all interfaces, but only on those that belong to the appropriate area. In this way detailed information can be kept localized, while summary information is flooded to the rest of the network. There are six distinct types of LSA’s defined in OSPF • Type 1 : Router LSA – Describes the state and cost of the router’s links to the area – All a router’s links in an area must be in a single LSA – Router indicates if it is an ASBR, ABR, or end of virtual link – Flooded throughout a particular area and no more • Type 2 : Network LSA – Generated for every network describing attached routers – Only the designated router originates this LSA – Flooded throughout a particular area and no more • Type 3 & 4: Summary LSA – Describes the destination outside the area but still in the AS – Originated by an ABR is it flooded throughout a single area – Only inter-area routes are advertised into the backbone – Type 4 is the information about the ASBR • Type 5 & 7: External LSA (Type 7 is External for NSSA) – Defines routes to destination external to the AS, default route is also sent as external – Two types of external LSA: • E 1: Consider the total cost up to the external destination • E 2: Considers only the cost of the outgoing interface to the external destination – Type 7 LSAs used to describe external LSA for one specific OSPF area type, the Not-so-stubby Area • Type 6: Group membership LSA – Multicast extensions for OSPF (MOSPF) – Not supported by most devices and almost never seen • Type 8, 9, 10 & 11: Opaque / Link-Local LSA – – – Type 8 used by OSPFv 3 for link-local address advertisement Type 9 is a link-local “opaque” LSA Type 10 is an area-local “opaque” LSA Type 11 is an AS “opaque” LSA An “opaque” LSA contains a standard LSA header followed by application specific information that may be used directly by applications. 80

OSPF – Routing Metrics OSPF uses path cost as its basic routing metric. This is typically based on the bandwidth of links on a given path. Logically a packet will face more overhead in crossing a 56 Kbps serial link than crossing a 100 Mbps Ethernet link. Respectively it will take less time in crossing a higher bandwidth link than a lower bandwidth link. OSPF uses this logic to calculate the cost. Cost is the inverse proportional of bandwidth. Higher bandwidth has a lower cost. Lower bandwidth has a higher cost. OSPF uses following formula to calculate the cost Cost = Reference bandwidth / Interface bandwidth in bps. Reference bandwidth was defined as arbitrary value in OSPF documentation (RFC 2338). Vendors use their own reference bandwidth. Cisco uses 100 Mbps (108) bandwidth as reference bandwidth. Using the Cisco reference bandwidth, the OSPF cost equation would be: Cost = 108 / Interface bandwidth in bps Key points – Cost is a positive integer value. – Any decimal value would be rounded back in nearest positive integer. – Any value below 1 would be considered as 1. Metrics, however, are only directly comparable when of the same type. Four types of metrics are recognized by OSPF. In decreasing preference, these types are: – – Intra-area (all routes inside an area) Inter-area (routes advertised between areas by ABR) External Type 1 (routes imported to OSPF which include the external path cost and the sum of internal path costs) External Type 2 (routes imported to OSPF which include solely the external path cost; Cisco default) 81

OSPF – Configuring OSPF Using the example network topology to the right we will configure OSPF on the routers via the CLI: Enable OSPF on both routers with the router ospf <process#> command. Then define what networks will be advertised using the network <ip-network> <inverse-mask> area <area#> command: The network commands entered on both routers include subnets directly connected to both routers. As soon as OSPF is configured on the routers and neighbor relationship is established we should see a message like this: %OSPF-5 -ADJCHG: Process 1, Nbr 192. 168. 0. 2 on Fast. Ethernet 0/1 from LOADING to FULL, Loading Done To verify the routers have become neighbors use the show ip ospf neighbors command: To verify that routes have been exchanged use the show ip routes command: Routes shown with a code of “O” are those that have been learned via OSPF. 82

Routing with EIGRP • EIGRP is the Enhanced Interior Gateway Routing Protocol • EIGRP is a Routing Protocol used to exchange routing information between different networks – Interior gateway protocol – Distance Vector Protocol – Incremental Updates – Classless Inter Domain Routing (CIDR) • Developed as a proprietary protocol later became open standard – Converted to open standard in 2013 – Described in RFC 7868 published in 2016

EIGRP – Distance Vector Routing EIGRP is classified as a distance vector routing protocol A distance-vector routing protocol requires that a router inform its neighbors of topology changes periodically. Compared to link-state protocols, which require a router to inform all the nodes in a network of topology changes, distance-vector routing protocols have less computational complexity and message overhead The term distance vector refers to the fact that the protocol manipulates vectors (arrays) of distances to other nodes in the network. Routers using distance-vector protocol do not have knowledge of the entire path to a destination. Instead they use two methods: Direction in which router or exit interface a packet should be forwarded, and Distance from its destination. "Direction" usually means the next hop address and the exit interface. "Distance" is a measure of the cost to reach a node usually in hops. In EIGRP The Diffusing Update Algorithm (DUAL) is the algorithm used to obtain loop-freedom throughout a route computation. This allows all routers involved in a topology change to synchronize at the same time. Routers that are not affected by topology changes do not re-compute. 84

EIGRP – Neighbor Discovery and Maintenance To distribute routing information throughout a network, EIGRP uses non-periodic incremental routing updates. That is, EIGRP only sends routing updates about paths that have changed when those paths change. The basic problem with sending only routing updates is that you may not know when a path through a neighboring router is no longer available. EIGRP relies on neighbor relationships to reliably propagate routing table changes throughout the network; two routers become neighbors when they see each other's hello packets on a common network. EIGRP sends hello packets every 5 seconds on high bandwidth links and every 60 seconds on low bandwidth or multipoint links. The rate at which EIGRP sends hello packets is called the hello interval, and you can adjust it per interface with the ip hello-interval eigrp command. The hold time is the amount of time that a router will consider a neighbor alive without receiving a hello packet. The hold time is typically three times the hello interval, by default, 15 seconds and 180 seconds. You can adjust the hold time with the ip hold-time eigrp command. It is important to note: For updates, EIGRP sends Update and Query packets to a multicast address. You can gather information about neighbors with the show ip eigrp neighbors command. 85

EIGRP – Building the Topology Table EIGRP unlike other routing protocols does not rely on the routing (or forwarding) table in the router to hold all of the information it needs to operate. Instead, it builds a second table, the topology table, from which it installs routes in the routing table. To see the basic format of the topology table, issue the show ip eigrp topology command. Output from this command shows the successor routes (that is, the preferred routes) and feasible successor routes (that is, backup routes) known to the EIGRP routing process The topology table contains the information needed to build a set of distances and vectors to each reachable network, including: • • lowest bandwidth on the path total delay path reliability path loading minimum path maximum transmission unit (MTU) feasible distance reported distance route source (external routes are marked) Metrics: EIGRP uses the minimum bandwidth on the path to a destination network and the total delay to compute routing metrics. Although other metrics can be configured it is not recommended to avoid routing loops. The bandwidth and delay metrics are determined from values configured on the interfaces of routers in the path to the destination network. Startup Mode: When two routers first become neighbors, they exchange topology tables during startup mode. For each table entry a router receives during startup mode, it advertises the same entry back to its new neighbor with a maximum metric (a poison route used for loop prevention). 86

EIGRP – Configuring EIGRP Using the example network to the right we will configure EIGRP on the routers via the CLI: On Router 0 (Router_A): Here, we define EIGRP process with “router eigrp 10”, where 10 is the autonomous system. The networks are advertised using the “network < network id>” command, thus we advertise the networks 10. 0 and 20. 0. On Router 1 (Router_B) we have only one network i. e 20. 0 so we advertise that. Make sure you use the same autonomous number while defining EIGRP. As soon as EIGRP is configured on the neighbor router and neighbor ship is established we see this message. The command “show ip eigrp neighbors” shows the neighbor tables and the formed neighbors 87

EIGRP – Configuring EIGRP Passive-Interface: In routing protocols like EIGRP we have a command “passive-interface” which will restrict or disable updates being sent from a specific interface. Using the passive-interface will prevent routing updates from being sent or received on the interface it is applied. The command used to disable routing updates being sent on specific interface is: passive-interface <interface> The command used to disable routing updates being sent on all interfaces is: passive-interface default To enable an interface and allow EIGRP updates to be advertised on that port, you can use the no passive-interface <interface> Authentication: EIGRP can use authentication to secure routing updates. A shared authentication key which is same on both routes must be configured. The password is known as the ‘key’. The steps to configure authentication are: • • Key chain is configured to keep keys Router (config)# key chain <keychain_name> Configure the key id in the keychain Router (config-keychain)# key <key-id> Authentication password is configured Router (config-keychain-key)# key-string <passwd-text> Configure interfaces for authentication Router (config)#int <interface name> Enable EIGRP message authentication Router (config-if)# ip authentication mode eigrp <AS> md 5 Specify the keychain to be used Router (config-if)# ip authentication key-chain eigrp <AS> <keychain_name> Complete these same steps on the other router(s) To verify authentication is working use the debug eigrp packets command. 88

EIGRP – Inserting Prefixes Into EIGRP Routing Two ways to insert prefixes into EIGRP: – redistribute command – network command The redistribute static command will insert all static routes into the EIGRP table. – Since EIGRP considers static routes directly connected networks this is not necessary – You may want to do this if you are applying metrics or want more control over static routes – Configuration Example: The redistribute <routing-protocol> command will insert everything from a <routing-protocol> into the EIGRP table. Care required with redistribute <routing-prot>! – Will not scale if uncontrolled – Best avoided if at all possible (used with “route-maps” and under tight administrative control) The network <network-prefix> command will insert a specific network in the EIGRP table. – A matching route must exist in the RIB before the network is added to the EIGRP topology table – Configuration Example: 89

Routing with Border Gateway Protocol • BGP is a Routing Protocol used to exchange routing information between different networks – Exterior gateway protocol – Path Vector Protocol – Incremental Updates – Many options for policy enforcement – Classless Inter Domain Routing (CIDR) • Described in RFC 4271 – RFC 4276 gives an implementation report on BGP – RFC 4277 describes operational experiences using BGP • The Autonomous System Number is the cornerstone of BGP – It is used to uniquely identify networks with a common routing policy

BGP – Path Vector Routing BGP is classified as a path vector routing protocol (see RFC 1322) A path vector protocol defines a route as a pairing between a destination and the attributes of the path to that destination. The routing table maintains the autonomous systems that are traversed in order to reach the destination system. In BGP the autonomous system boundary routers (ASBR) which participate in path vector routing, advertise the reachability of networks. Each router that receives a path vector message modifies its routing table and the message before sending it to the next neighbor. In the modified message it sends its own AS number and replaces the next router entry with its own identification. AS 6337 AS 11268 AS 7018 AS 500 AS 6461 AS 600 12. 6. 126. 0/24 207. 126. 96. 43 1021 0 6461 7018 6337 11268 i AS Path 91

BGP – Autonomous System (AS) An autonomous system (AS) identifies a collection of networks meeting the following requirements: – Collection of networks with same routing policy – Single routing protocol – Under single ownership, trust or administrative control Autonomous Systems are identified by a unique 32 -bit integer (ASN) Until 2007, AS numbers were defined as 16 -bit integers, which allowed for a maximum of 65, 536 assignments. RFC 4893 introduced 32 -bit AS numbers Autonomous systems can be grouped into four categories, depending on their connectivity and operating policy. – A multihomed AS is an AS that maintains connections to more than one other AS. – A stub AS refers to an AS that is connected to only one other AS. – A transit AS is an AS that provides connections through itself to other networks. – An Internet Exchange Point AS (IX or IXP) is physical infrastructure through which Internet service providers (ISPs) or content delivery networks (CDNs) exchange Internet traffic between their networks 92

BGP – General Operations BGP peers internally with other routers in its AS (i. BGP) and externally with other routers outside of its AS (e. BGP) BGP peering traffic runs over TCP port 179 The link or network shared between AS peers is called the Demarcation Zone (DMZ) BGP will learn multiple paths via internal and external BGP speakers It picks the best path and installs it in the routing table (RIB) The best path is sent to external BGP neighbors Policies are applied influencing the best path selection Peering e. BGP AS 100 i. BGP IGP i. BGP AS 1 AS 2 AS 3 AS 4 C DMZ Network AS 101 D B IGP E AS 102 93

BGP – Constructing A Forwarding Table • BGP “in” process – receives path information from peers – results of BGP path selection placed in the BGP table – “best path” flagged • BGP “out” process – announces “best path” information to peers • Best path stored in Routing Table (RIB) • Best paths in the RIB are installed in forwarding table (FIB) if: – prefix and prefix length are unique – lowest “protocol distance” 94

BGP – Configuring External BGP Peering External BGP (e. BGP) Peering Rules: • Only use between BGP speakers in different AS • Should be directly connected • Never run an IGP between e. BGP peers Using the example network to the right we will configure e. BGP peering on routers A and C Router A configuration: AS 100 A C AS 101 B Router C configuration: This sets up basic e. BGP peering. The prefix-list routing policies will be explained later in this section. 95

BGP – Configuring Internal BGP Peering Internal BGP (i. BGP) Peering Rules: • Only use between BGP speakers in the same AS • Not required to be directly connected – IGP routing will provide BGP speaker connectivity – Topology independent • Peer with loop-back interface if possible – Loop-back interface does not go down • i. BGP speakers must be fully meshed – They originate connected networks – They pass on prefixes learned from outside the ASN – Don’t pass on prefixes learned from other i. BGP speakers Using the example network to the right we will configure i. BGP peering on routers A and B Router A configuration: AS 100 A C AS 101 B Router B configuration: 96

BGP – Verify BGP Peering To verify BGP peering and other settings use the show ip bgp summary command The output will show information about each BGP neighbor. For more detailed information about neighbors use show ip bgp neighbor <ip> command 97

BGP – Verify BGP Routing To verify BGP routing is working view the route table with the show ip bgp command The output will show information from the BGP route table. 98

BGP – Inserting Prefixes Into BGP Routing Two ways to insert prefixes into BGP: – redistribute command – network command The redistribute static command will insert all static routes into the BGP table. – Static route must exist before redistribute command will work – Forces origin to be “incomplete” – Configuration Example: The redistribute <routing-protocol> command will insert everything from a <routing-protocol> into the BGP table. Care required with redistribute <routing-protocol>! – Will not scale if uncontrolled – Best avoided if at all possible (used with “route-maps” and under tight administrative control) The network <network-prefix> command will insert a specific network into the BGP table. – A matching route must exist in the RIB before network is announced – Forces origin to be “IGP” – Configuration Example: 99

BGP – Applying Routing Policy in BGP A routing policy can be applied to any external and/or internal routes to control the propagation of those routes. BGP routing policies can be based on AS path, peers, community or the prefix • Rejecting/accepting selected routes • Set attributes to influence path selection Tools: – Prefix-list (filters prefixes) – Filter-list (filters AS’s) – Route-maps using Communities and Local-preference and AS-Path Prepend options Policies applied to a specific BGP neighbor follow this order of operations: • For inbound updates, the order is: – – – • Route-map Filter-list Prefix-list For outbound updates, the order is: – – – Prefix-list Filter-list Route-map 100

BGP – Applying Policy with Prefix Lists – Per neighbor prefix filter can be applied Inbound or Outbound – Based upon network numbers – Examples: • • Deny default route Permit the prefix 35. 0. 0. 0/8 Deny the prefix 172. 16. 0. 0/12 In 192/8 allow up to /24 ip prefix-list EG deny 0. 0/0 ip prefix-list EG permit 35. 0. 0. 0/8 ip prefix-list EG deny 172. 16. 0. 0/12 ip prefix-list EG permit 192. 0. 0. 0/8 le 24 – This allows all prefix sizes in the 192. 0. 0. 0/8 address block, apart from /25, /26, /27, /28, /29, /30, /31 and /32. • In 192/8 deny /25 and above ip prefix-list EG deny 192. 0. 0. 0/8 ge 25 – This denies all prefix sizes /25, /26, /27, /28, /29, /30, /31 and /32 in the address block 192. 0. 0. 0/8. – It has the same effect as the previous example • In 193/8 permit prefixes between /12 & /20 ip prefix-list EG permit 193. 0. 0. 0/8 ge 12 le 20 – This denies all prefix sizes /8, /9, /10, /11, /22, … and higher in the address block 193. 0. 0. 0/8. • Permit all prefixes ip prefix-list EG permit 0. 0/0 le 32 – 0. 0 matches all possible addresses, “ 0 le 32” matches all possible prefix lengths 101

BGP – Applying Policy with Filter Lists – – Filter routes based on AS path and can be applied Inbound or Outbound Uses an access-list for application Uses regular expressions (similar to Unix regex) Regular Expressions Simple filter list regular expression examples: . *. + ^$ _1800$ ^1800_ _790_1800_ _(1800_)+ _(65530)_ match anything match at least one character match routes local to this AS originated by AS 1800 received from AS 1800 via AS 1800 and AS 790 multiple AS 1800 in sequence (used to match AS-PATH prepends) via AS 65530 (confederations) – Not so simple filter list regular expression examples: ^[0 -9]+$ ^[0 -9]+_[0 -9]+$ ^[0 -9]*_[0 -9]+$ _(701|1800)_ Match AS_PATH length of one Match AS_PATH length of two Match AS_PATH length of one or two Match anything which has gone through AS 701 or AS 1800 102

BGP – Applying Policy with Route Maps – – A route-map is like a program for the router to run Has line numbers, like a program Each line is a separate condition/action Concept is basically: if match then do expression and exit else etc – Using “continue” lets you apply multiple conditions/actions in one route-map – Implicit “deny” is the last unseen line of a route-map – Caveats • Lines can have multiple set statements • Lines can have multiple match statements • Line with only a match statement = only prefixes matching go through, the rest are dropped • Line with only a set statement = all prefixes are matched and set • Line with a match/set statement and no other lines = only prefixes matching are set, the rest are dropped 103

BGP – Applying Policy with Route Maps Communities – A BGP community is bit of “extra information” that you can add to one of more prefixes which is advertised to BGP neighbors. – There are 4 well known BGP communities that you can use or you can pick a numeric value that you can use for your own policies. • • NO_EXPORT tells a router it should only propagate i. BGP, and not over e. BGP NO_EXPORT_SUBCONFED does something similar in confederations to limit the i. BGP sessions. NO_ADVERTISE goes a step further and tells the router to not advertise the prefix over BGP at all NOPEER indicates that a prefix “need not” be advertised over peering relationships – A community is a group of prefixes that should be treated the same way. – Most routers don’t automatically propagate communities, you’ll have to enable this explicitly for a BGP neighbor with the “send-community” keyword – Communities are 32 -bit values that are set and can then be matched on. • By default, they show up as decimal numbers. The “ip bgp-community new-format” line changes the display format of communities into two 16 -bit values separated by a colon. • The first 16 -bit number is normally the AS number of the network that sets the community, and the second number is one that conveys the information. – For instance, Level 3 (AS 3356) tags all the prefixes it learns in Pittsburgh with community 3356: 2040. – So if you had a reason to avoid paths that go through Level 3’s network in Pittsburgh, you could look for 3356: 2040 and give prefixes that have this community a lower local preference. – The configuration to the right accomplishes this and is a good example of community matching: – Communities are set and matched upon in route maps – An example of setting a community is below: 104

BGP – Applying Policy with Route Maps Local-preference – The BGP Local Preference attribute or local-pref is used to influence the outbound routing decision of BGP – The local preference has to be set in bound on routes being received to influence the outbound routing behavior. – A higher local preference is preferred and the default is 100. – The BGP best path algorithm states that if local preference is the same then the path with the shortest AS path will be chosen. As local preference is higher up the decision process if we can change that we can influence the routing over the shortest AS-path choice – One important point is that the local-preference value is passed between i. BGP neighbors but it is not passed between e. BGP neighbors. – Local preference is set using route-maps using the command set local-preference – Example of setting local-preference: – You can confirm the local-preference with the command show ip bgp and look for the attribute Loc. Prf for the routes you are setting: 105

BGP – Applying Policy with Route Maps AS-Path Prepend – The AS path is a well-known mandatory attribute, which means that it’s present for all prefixes exchanged between BGP neighbors. When a BGP router sends out an update to a neighbor in a different autonomous system, it adds its own AS number to the front (left side) of the AS path. So the AS path lists all the AS’s that need to be traversed to reach the location where the prefix that the path is attached to is advertised from. – Unlike most other attributes, changes to the AS path are propagated to downstream AS’s. This makes it possible to use the AS path to do traffic engineering in ways that aren’t possible with other attributes. – The AS path is used by BGP in determining the best path. So increasing the number of AS’s in the path for a route would make a route less desirable. – Prepending means adding one or more AS numbers to the left side of the AS path. Normally this is done using one’s own AS number, using someone else’s AS number for this can have unintended side effects. 106

BGP – Managing Policy Changes New policies only apply to the updates going through the router AFTER the policy has been introduced or changed To facilitate policy changes on the entire BGP table the router BGP peerings need to be “refreshed” This is done by clearing the BGP session either in or out, for example: clear ip bgp <neighbour-addr> in|out Do NOT forget in or out — doing so results in a hard reset of the BGP session You have the ability to clear the BGP sessions of groups of neighbors configured according to several criteria clear ip bgp <addr> [in|out] <addr> may be any of the following x. x * ASN external peer-group <name> IP address of a peer all peers in an AS all external peers all peers in a peer-group 107

Questions?

Still Have Questions? This presentation was designed to provide a basic understanding of computer network fundamentals. It was not designed to be a replacement for traditional network training. If you have questions regarding the material presented here you should consider taking either an online self-paced or instructor led network training course. There are many network training options available and we will not attempt to list them all here or endorse any one over another. However, a quick google search provides quite a few options like these: https: //www. cybrary. it/course/comptia-network-plus/ (Free online training) https: //www. cbtnuggets. com/it-training/network-administration-engineering (Paid online training) https: //www. globalknowledge. com/us-en/training/course-catalog/topics/networking-and-wireless/ (Paid instructor led in-person and/or online training) Do your own search and find the training that is right for you. 109