IT Auditing and the Challenge of New Technologies



































































































- Slides: 127

IT Auditing and the Challenge of New Technologies June 16, 2011 Presented by: Jay Bowman, CISA, CISM

This Morning’s Topics • Evolution of technology and its applications • What this means in terms of opportunities • What this means in terms of risks • What this means in terms of providing internal audit coverage. • Actions you and your institution can take 2

Evolution of Technology The rapid changes in technology during our lifetimes has made possible services our parents couldn’t even dream of. • Building Blocks • Computers • Telephones • Technology-Based Services 3

Technology Building Blocks 4

Technology Building Blocks 5

Technology Building Blocks 6

Technology Building Blocks 7

Technology Building Blocks 8

Technology Building Blocks 9

Computers 10

Computers 11

Computers 12

Computers 13

Computers 14

Computers 15

Computers 16

Computers 17

Computers 18

Telephones 19

Telephones 20

Telephones 21

Telephones 22

Telephones 23

Telephones 24

Telephones 25

Telephones 26

Telephones 27

Telephones 28

Telephones 29

Telephones 30

Telephones 31

Technology-Based Services The Atlanta Payments Project 32

Technology-Based Services The Atlanta Payments Project • Electronic Payments Services • Implementation Considerations and Obstacles 33

Technology-Based Services The Atlanta Payments Project • Electronic Payments Services • Check Authorization • Telephone Banking • Point-of-Sale Transactions • Automated Clearinghouse (ACH) • Check Truncation 34

Technology-Based Services The Atlanta Payments Project • Implementation Considerations & Obstacles • Technology • Storage Limitations and Costs • Communications Speeds and Costs • Processor Speeds and Costs • Consumer Acceptance 35

Considerations and Obstacles • Storage Limitations and Costs 36

Considerations and Obstacles • Communications Speeds and Costs 37

Considerations and Obstacles • Processor Speeds and Costs 38

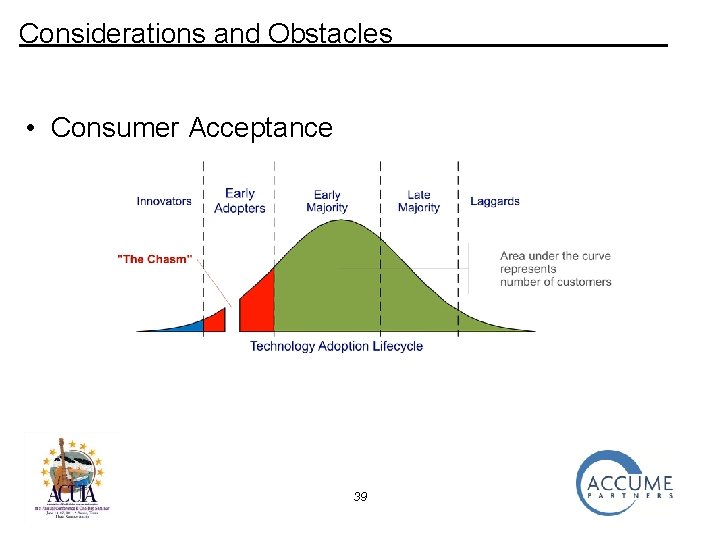
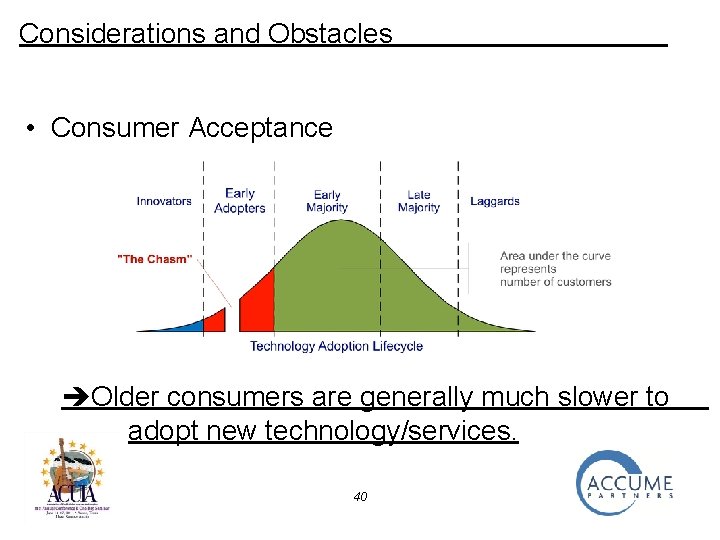
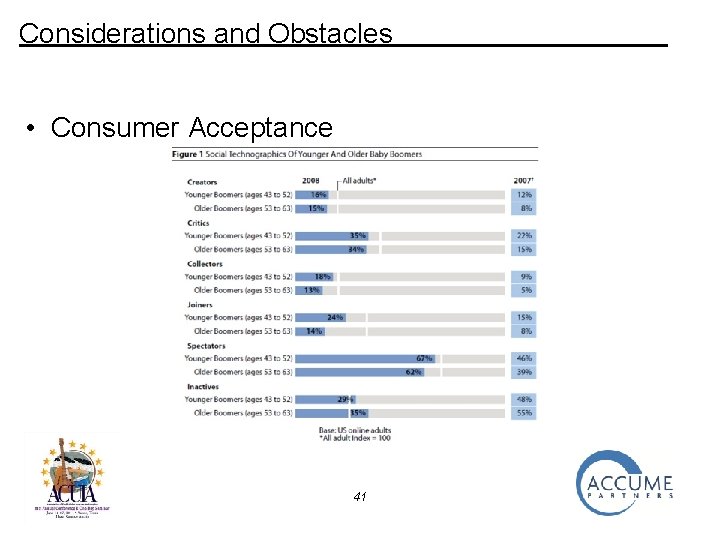
Considerations and Obstacles • Consumer Acceptance 39

Considerations and Obstacles • Consumer Acceptance Older consumers are generally much slower to adopt new technology/services. 40

Considerations and Obstacles • Consumer Acceptance 41

Technology-Based Services The Atlanta Payments Project • Electronic Payments Services • Check Authorization • Telephone Banking • Point-of-Sale Transactions • Automated Clearinghouse (ACH) • Check Truncation 42

Technology-Based Services • Check Authorization 43

Technology-Based Services • Check Authorization 44

Technology-Based Services • Telephone Banking 45

Technology-Based Services • Point-of-Sale Transactions 46

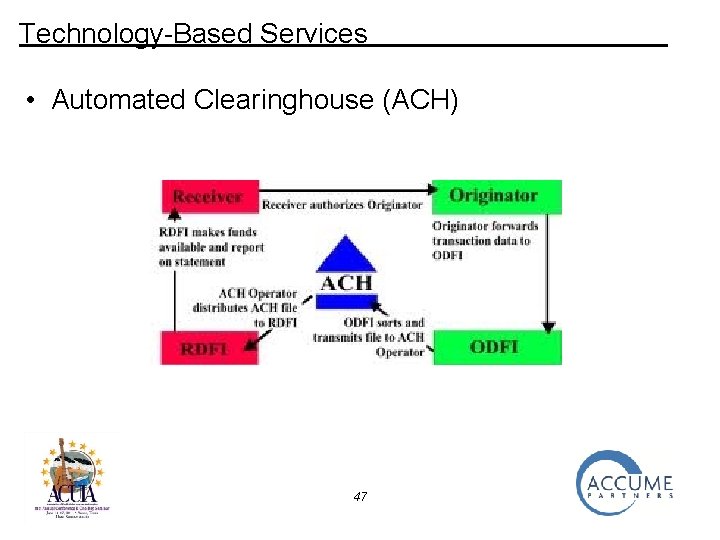
Technology-Based Services • Automated Clearinghouse (ACH) 47

Technology-Based Services • Check Truncation 48

_______ What does all this mean in terms of IT internal audit? 49

_______ What does all this mean in terms of IT internal audit? 50

_______ New technologies carry the same risks challenges and rewards as the old technologies! 51

_______ New technologies carry the same risks challenges and rewards as the old technologies! And the same audit requirements! 52

New Technologies? First, what we’re really talking about is new applications of existing technologies. • Cloud Computing • Mobile Banking 53

Cloud Computing 54

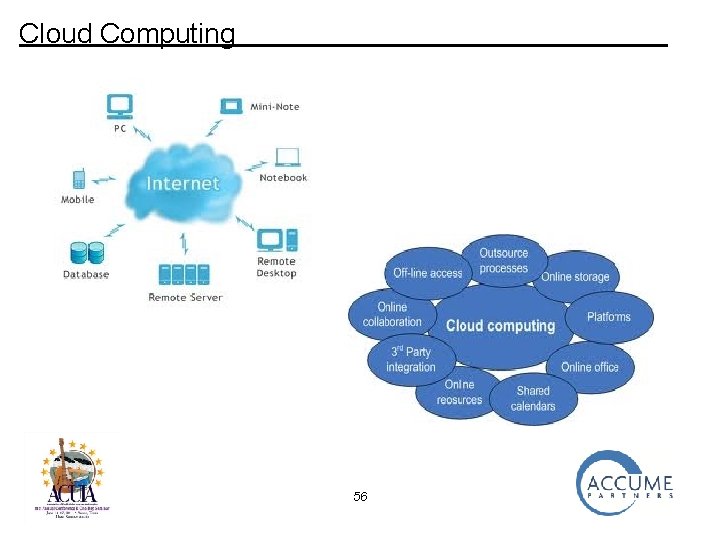
Cloud Computing The “new” cloud computing is an evolution of the “old” distributed computing • Relies on the Internet instead of private networks • All resources may not be “owned” or “controlled” by the user of the cloud 55

Cloud Computing 56

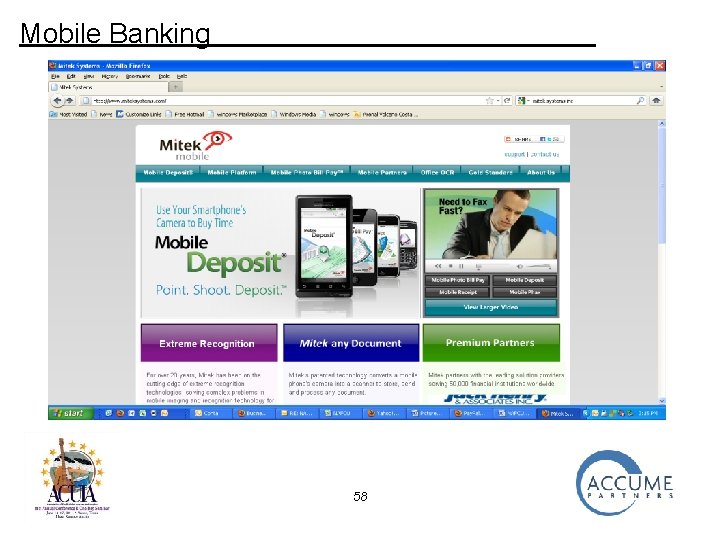
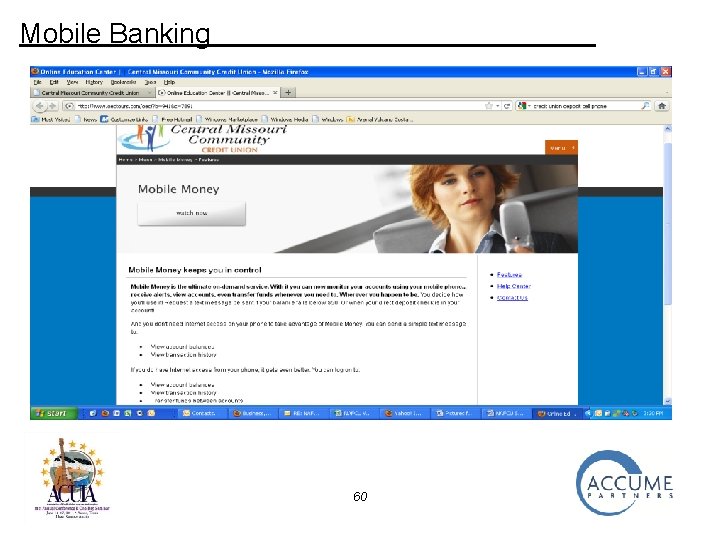
Mobile Banking An evolution the “old” telephone banking • Un-tethered • Technology and cost impediments disappearing • Potential limited only by imagination and the ability of management to allocate time to plan, implement and market 57

Mobile Banking 58

Mobile Banking 59

Mobile Banking 60

Mobile Banking 61

Opportunities • Reduce (or keep the lid on) costs • Attract new members • Retain existing members 62

Risks • Increased costs (without corresponding increases in members and/or revenues) • Loss of members • Security and/or privacy breaches • Access control • Regulatory criticism 63

_______ How do we audit the new technology applications? 64

How do we audit the new technology applications? By following the same methodical, risk-based approach that has successfully been applied in earlier phases of the evolution of technology and its applications. 65

The Challenges • To provide “appropriate” Information Technology (IT) coverage that complements internal audits of financial and operational areas in a timely and costeffective manner. • To present complex technical findings in business terms that Management and Directors can understand properly respond to. 66

The Alternatives • • • Internal Auditor performs IT audits Full-time IT internal auditor on staff Co-source IT internal audits Rely on external auditors Other 67

The Alternatives • • • Internal Auditor performs IT audits Full-time IT internal auditor on staff Co-source IT internal audits Rely on external auditors Other 68

Issues Surrounding Alternatives • Adequacy of Coverage – Subject Matter Expertise – Depth of coverage – Availability of time • • • Maintenance of Requisite Knowledge Awareness of Best Practices Continuity/Institutional Knowledge Regulatory Environment Cost 69

IT Audit Approach • Risk Assessment • IT Internal Audits • Monitoring and Follow-up 70

IT Audit Approach • IT Internal Audit Risk Assessment 71

IT Internal Audit Risk Assessment • Risk Categories – – – Financial Operational Technology Reputational Regulatory Compliance • Evaluation Process/Management Involvement • Risk Ratings/Allocation of Resources 72

IT Internal Audit Risk Assessment • Risk Categories – – – Financial Operational Technology Reputational Regulatory Compliance • Evaluation Process/Management Involvement • Risk Ratings/Allocation of Resources 73

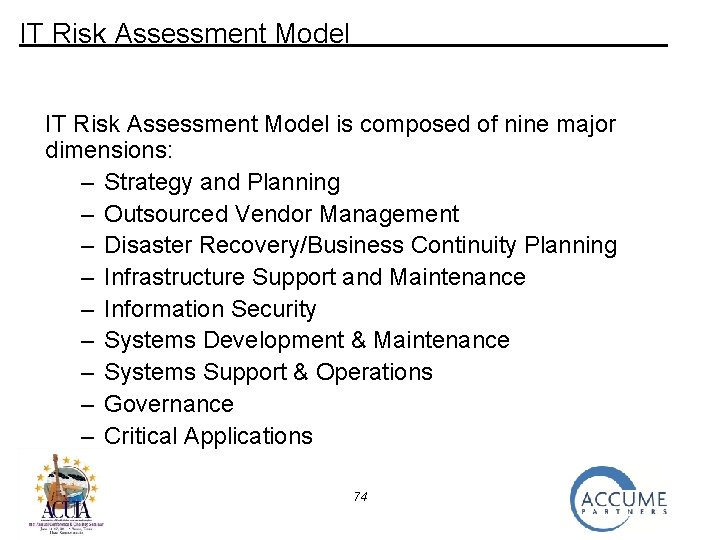
IT Risk Assessment Model is composed of nine major dimensions: – Strategy and Planning – Outsourced Vendor Management – Disaster Recovery/Business Continuity Planning – Infrastructure Support and Maintenance – Information Security – Systems Development & Maintenance – Systems Support & Operations – Governance – Critical Applications 74

Strategy and Planning is critical to ensure that IT goals support the overall goals of the institution 75

Strategy and Planning is critical to ensure that IT goals support the overall goals of the institution • IT strategy and plans should be formalized and aligned with the institution’s business and strategic goals (3 years and up) 76

Strategy and Planning is critical to ensure that IT goals support the overall goals of the institution • IT strategy and plans should be formalized and aligned with the institution’s business and strategic goals (3 years and up) • Short-range IT (annual) plans describe the implementation steps/ projects, identifies appropriate resources, and includes detailed budgets. 77

Strategy and Planning is critical to ensure that IT goals support the overall goals of the institution • IT strategy and plans should be formalized and aligned with the institution’s business and strategic goals (3 years and up) • Short-range IT (annual) plans describe the implementation steps/ projects, identifies appropriate resources, and includes detailed budgets. • Plans should consider technological changes and opportunities, and will define the information systems architecture for the institution. 78

Strategy and Planning is critical to ensure that IT goals support the overall goals of the institution • IT strategy and plans should be formalized and aligned with the institution’s business and strategic goals (3 years and up) • Short-range IT (annual) plans describe the implementation steps/ projects, identifies appropriate resources, and includes detailed budgets. • Plans should consider technological changes and opportunities, and will define the information systems architecture for the institution. • Progress against the plans is monitored by senior management 79

Outsourced Vendor Management (VM) Management of the institution retains responsibility regardless of whether functions are outsourced • A VM policy establishing ownership and procedures has been approved by the Board • Risk assessments are performed prior to outsourcing • Vendor evaluation and selection procedures are formalized • Standard for contracts and service level agreements have been established • Existing service providers are reviewed and monitored • A VM program report is presented annually to the Board 80

Disaster Recovery/Business Continuity Planning The institution has developed and documented a comprehensive IT Disaster Recovery Plan and associated Business Continuity Plans. • The Plan includes a Risk Assessment of likely threat scenarios • Threat scenarios address impact on systems, facilities and people • Business Impact Analyses (BIAs) have been prepared for all departments and functions • Qualified personnel are responsible for maintaining the Plan current • The plan is tested regularly with feedback to address “failures” • The Board receives an annual report on the plan and testing results 81

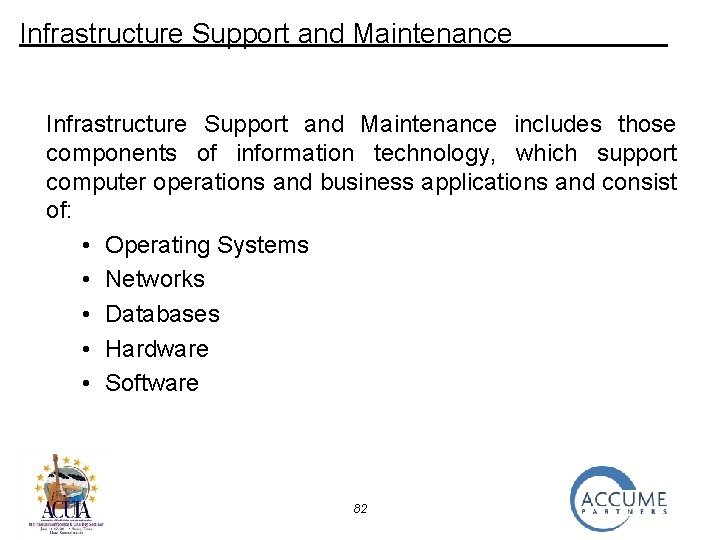
Infrastructure Support and Maintenance includes those components of information technology, which support computer operations and business applications and consist of: • Operating Systems • Networks • Databases • Hardware • Software 82

Infrastructure Support and Maintenance The institution has resources and procedures in place to provide a stable, serviceable IT environment • A current and complete inventory of hardware, software, and network (data and voice) devices is maintained • Qualified resources monitor and maintain the network infrastructure • There is a formal plan to ensure the IT infrastructure is stable, and meets business requirements in terms of cost, availability, scalability, redundancy, interoperability, functionality etc. • There is formal equipment maintenance plans for all hardware, software, and network devices • Monitoring mechanisms are in place to alert management of device and system failures. • There are service contracts to provide back-up equipment and assistance in the event of an infrastructure failure. 83

Information Security Information security policies, procedures, standards, and guidance and/or the information security architecture will define how security features and functionality are to be administered. • Tools and Techniques • Access Restrictions • Authentication • Password Strengths • Security Monitoring and Logon Attempts 84

Information Security The institution has resources and procedures in place to appropriately secure infrastructure and information • There is a Board-approved information security policy. • The policy has been distributed to all employees who annually sign an affirmation of their understanding • There is an information security officer who is independent of IT functions. • Users are assigned formal roles/profiles for the network and system that are based on job responsibilities. • The organization maintains virus detection software for all workstations and servers • There have been no security breaches. 85

Systems Development & Maintenance Many institutions do not develop or maintain applications inhouse. For those institutions that do develop software, the areas of focus consist of: • Systems Development Life Cycle (SDLC) • Application Version Control • Change Control Procedures • User Acceptance Testing 86

Systems Development & Maintenance The institution has the necessary organization, tools and procedures to ensure reliable systems are developed timely and securely • The institution has adopted a Systems Development Life Cycle (SDLC) methodology • There is a centralized Project Management function to coordinate and manage IT resources across the institution. • Separate environments are maintained for testing new systems and/or system enhancement and modifications. • A controlled process is used to move changes into production 87

System Support and Operations Those IT functions that support processing: • Job Scheduling • Data and Software Back-up • Production Control • Media Management • Help Desk • Procedural Documentation • Anti-virus Measures 88

System Support and Operations The institutions has the organization, tools and procedures to scheduled and operate systems timely and reliably • An Operations Procedural Manual has been developed which includes escalation procedures to be performed in the event of a systems failure. • Automated job schedulers ensure batch jobs are processed timely and in the correct order. • Monitoring devices ensure operational failures are detected for corrective action. Production failures are recorded analyzed. • All software and data are back-up on a routine basis • An Operations Committee meets regularly to review systems performance agaiand discuss ways to improve overall operations. • A centralized help desk responds to system problems. 89

Governance IT policies and practices should align with applicable statutory and regulatory guidance such as: • HIPAA (personnel-related requirements) • Sarbanes-Oxley (not credit unions…yet) • Gramm-Leach-Bliley Act • NCUA guidance • FFIEC IT Handbooks 90

Governance The institution has the organization, tools and procedures to ensure compliance with applicable guidance • The institution has developed a process to identify IT statutory and regulatory requirements. • An IT governance committee focuses on the development of standards and employee education to foster compliance with external guidance and internal policies. • Documented, comprehensive IT Policies and Procedures are reviewed, updated and approved at least annually • An IT Control Self Assessment Process to evaluate compliance with documented IT Policies and Procedures. • A Privacy/Security Risk Assessment and Privacy/Security Audit are conducted annually. 91

Critical Applications For applications critical to its mission and ongoing operations, the institution has instituted appropriate procedures and controls. • The institution had developed and maintains an inventory of mission critical applications • The organization has identified and/or developed specific controls for each critical applications related to: – Security – Data Validation and Control – Error Processing – Interface Controls – Accounting Controls – Error Reporting – System Testing • A Systems Control Self Evaluation is periodically performed for each critical system. 92

IT Audit Approach • IT Internal Audits 93

IT Internal Audit Schedule • Derived from Risk Assessment – Specific Audits/Frequency • IT audits are sequenced and cycled based on relative risk • Timetable for Deliverables – Other Considerations • Alignment with financial / operational audit plan • Significant Change (e. g. new processing system) • Support of External Auditors • Key Management/Staff Availability • Regulatory Examination Schedule • Major issue: Granular IT audits vs. “IT General Controls” audit 94

General Controls vs. Granular • • • Risk assessment results Size of institution and IT shop Infrastructure complexity In-house vs. outsourced core processing Regulatory atmosphere and guidance Available funding 95

IT Internal Audits • Core Application Admin & Security • Network Admin & Security • e-Banking/Mobile Banking • Computer Operations • Disaster Recovery/Business Continuity • Third-Party Vendor Management • GLBA 501(b) Customer Information Privacy • Fed. Line Advantage 96

Core Application Admin & Security • Logical Access Controls – Procedures for granting, removing and changing access – Review sample of access control requests – Test for separated employees still on system – Evaluate granting of administrator/high-level access • New Releases and Fixes – Timely installation – Appropriate user testing and signoff – Updating of IT and user documentation • System-specific requirements – Changing default IDs and passwords – Tailoring system settings • Review and Action upon System Exception Reports 97

Network Admin & Security • Logical Access Controls – Procedures for granting, removing and changing access – Review sample of access control requests – Test for separated employees still on network – Evaluate granting of administrator/high-level access • New Equipment, Software Releases and Fixes – Timely installation – Appropriate user testing and signoff – Updating of Network documentation • Network-specific requirements – Changing default IDs and passwords – Tailoring system settings • Network Vulnerability Assessments (Penetration Tests) – Frequency, Independence, Rotation, Due Diligence – Scope/depth/focus of findings; actions in response 98

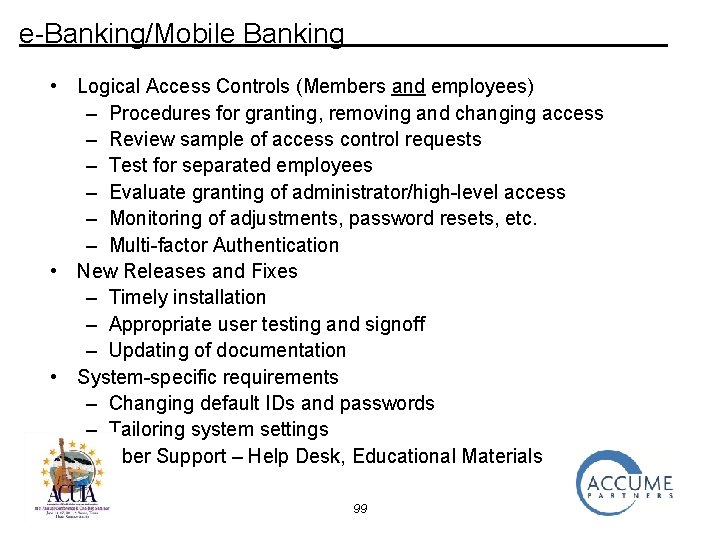
e-Banking/Mobile Banking • Logical Access Controls (Members and employees) – Procedures for granting, removing and changing access – Review sample of access control requests – Test for separated employees – Evaluate granting of administrator/high-level access – Monitoring of adjustments, password resets, etc. – Multi-factor Authentication • New Releases and Fixes – Timely installation – Appropriate user testing and signoff – Updating of documentation • System-specific requirements – Changing default IDs and passwords – Tailoring system settings • Member Support – Help Desk, Educational Materials 99

Computer Operations • Physical Access Controls – Procedures/basis for granting, removing access • Operations employees • Senior management • Housekeeping/Building Maintenance/Security – Access Control Mechanisms/Monitors – Visitor Access Procedures/Controls • Physical Infrastructure – Temperature/humidity sensors and alarms – Threat/motion sensors and alarms – Overall housekeeping • Operations Staff – Training – Background checks 100

Computer Operations (continued) • Operating Policies/Procedures/Manuals – Current – Complete • Job Scheduling/Monitoring – Automatic sequences – Manual scheduling – Logging of operator activities/intervention – Management review of logs • Computer Room Equipment – Current Inventory – Maintenance scheduling and logging – Failure logging and remediation • Sensitive Materials Handling and Disposal – Negotiable instruments – Confidential reports 101

Disaster Recovery/Business Continuity • Plan Development and Support – Qualified Individual(s) in Charge – Appropriate skill sets and sufficient time – Designated individuals through institution – Involvement of key vendors – Board/Management support For each of the following areas, determine • Existence • Completeness • Currency 102

Disaster Recovery/Business Continuity (continued) • • • Risk Assessment – Reasonably foreseeable threats – Likelihood, severity, impact – Systems, infrastructure, staff – Must address pandemic flu Business Impact Analyses (BIAs) – All departments and functions – Impact on their functions, other departments, members, overall institution Detailed Plans – IT: Disaster Recovery Plan – Other Departments: Business Continuity Plans – Contents: • Equipment and software lists • Inventories of forms and supplies • Procedures 103

Disaster Recovery/Business Continuity (continued) • Alternate Location(s) – Designated – Stocked with pre-staged procedures, supplies, equipment • Administrative Components – Designated Individuals who can Declare Disaster – Disaster/Damage Assessment Procedures – Employee Notification Procedures/Calling Trees – Other Notification Lists • Directors/Supervisory Committee Chair • Public Safety Officials • Regulators • Key Vendors • Key Members 104

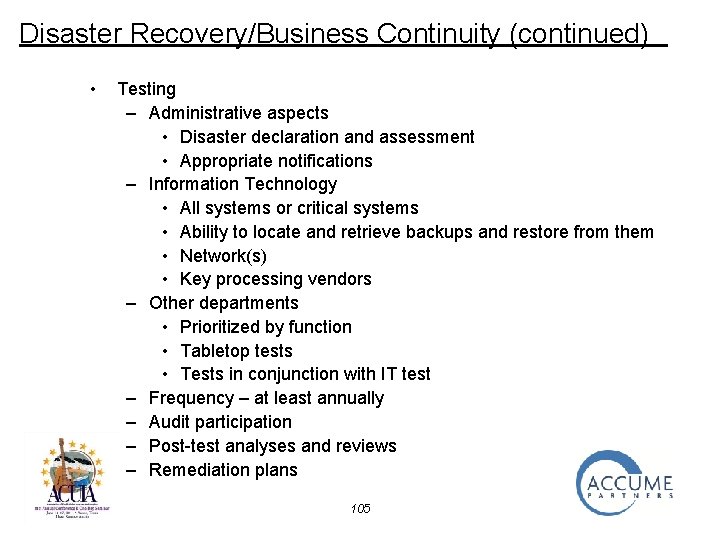
Disaster Recovery/Business Continuity (continued) • Testing – Administrative aspects • Disaster declaration and assessment • Appropriate notifications – Information Technology • All systems or critical systems • Ability to locate and retrieve backups and restore from them • Network(s) • Key processing vendors – Other departments • Prioritized by function • Tabletop tests • Tests in conjunction with IT test – Frequency – at least annually – Audit participation – Post-test analyses and reviews – Remediation plans 105

Third Party Vendor Management • Policy – Fixes responsibility and accountability – Establishes procedures for major components • Risk Assessment – pre-decision to outsource – Potential Impact on Strategic Goals – Management Oversight and Evaluation – Contingency Plans – Regulatory Requirements & Guidance • Vendor Selection Process – Identification of Potential Vendors – Due Diligence and Selection – Contract Negotiation and Award 106

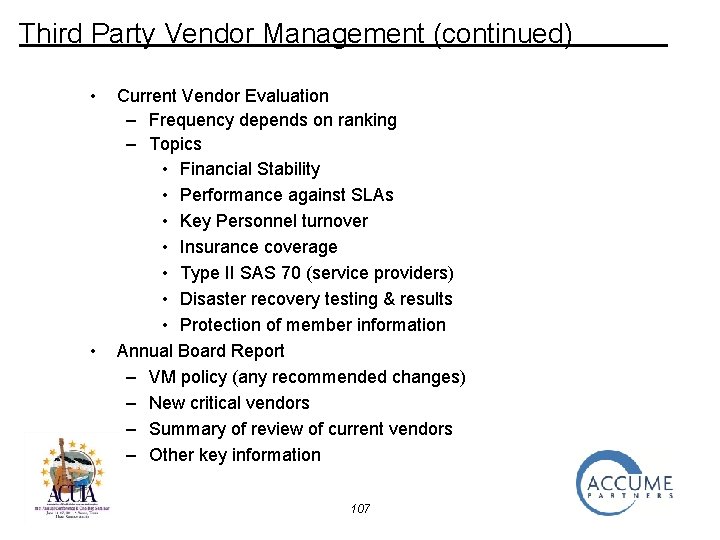
Third Party Vendor Management (continued) • • Current Vendor Evaluation – Frequency depends on ranking – Topics • Financial Stability • Performance against SLAs • Key Personnel turnover • Insurance coverage • Type II SAS 70 (service providers) • Disaster recovery testing & results • Protection of member information Annual Board Report – VM policy (any recommended changes) – New critical vendors – Summary of review of current vendors – Other key information 107

GLBA 501 (b) Customer Information Privacy • • Board-approved Privacy Policy – Fixes responsibility – Establishes program – Requires reporting Privacy Program Privacy Risk Assessment – Assess and document risk of unauthorized access to non-public member information – Scope should include: • IT infrastructure • Manual (i. e. paper) instances • Third party processors – Is it sufficiently granular? Specific? Third-party processors – Explicit contractual provision – Due diligence on effectiveness of controls 108

GLBA 501 (b) Customer Information Privacy (cont. ) • Third-party processors – Explicit contractual provision – Due diligence on effectiveness of controls • Employee training – All employees – Annual – Relevant – Documented • Annual Report to Board – Summary of program over previous year – Recommended policy changes (if any) – Incidents (if any) – Specific contents per guidance 109

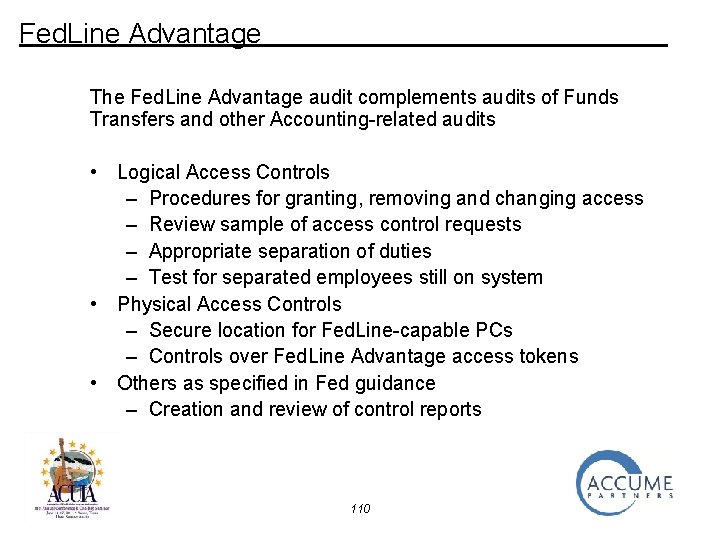
Fed. Line Advantage The Fed. Line Advantage audit complements audits of Funds Transfers and other Accounting-related audits • Logical Access Controls – Procedures for granting, removing and changing access – Review sample of access control requests – Appropriate separation of duties – Test for separated employees still on system • Physical Access Controls – Secure location for Fed. Line-capable PCs – Controls over Fed. Line Advantage access tokens • Others as specified in Fed guidance – Creation and review of control reports 110

IT Audit Approach • Monitoring and Follow-up 111

Monitoring and Follow-Up • Follow-up Matrix – Should contain all findings that were not “closed” at the time audit report was presented to Supervisory Committee – Used by Supervisory Committee to track progress against stated plans and target dates – Can/should also be used by Management to supervise and guide efforts 112

Choosing the Right Approach • Issues revisited – Coverage – Competence – Currency (of technical information) – Continuity – Climate (regulatory) – Cost • Using this template, and based on their knowledge of credit union, Management and the Supervisory Committee can arrive at the right approach 113

One more thing… 114

One more thing… Should we be auditing Governance? 115

One more thing… Should we be auditing Governance? 116

Governance Redux The institution has the organization, tools and procedures to ensure compliance with applicable guidance • The institution has developed a process to identify IT statutory and regulatory requirements. • An IT governance committee focuses on the development of standards and employee education to foster compliance with external guidance and internal policies. • Documented, comprehensive IT Policies and Procedures are reviewed, updated and approved at least annually • An IT Control Self Assessment Process to evaluate compliance with documented IT Policies and Procedures. • A Privacy/Security Risk Assessment and Privacy/Security Audit are conducted annually. 117

Governance Redux Which of these areas are likely to undergo change as • New legislation is passed? • New regulations are promulgated? • New technologies are investigated and implemented? 118

Governance Redux The institution has the organization, tools and procedures to ensure compliance with applicable guidance • The institution has developed a process to identify IT statutory and regulatory requirements. • An IT governance committee focuses on the development of standards and employee education to foster compliance with external guidance and internal policies. • Documented, comprehensive IT Policies and Procedures are reviewed, updated and approved at least annually • An IT Control Self Assessment Process to evaluate compliance with documented IT Policies and Procedures. • A Privacy/Security Risk Assessment and Privacy/Security Audit are conducted annually. ALL OF THEM 119

Actions You and Your Institution Can Take Understand the new technologies and services • Maturity and potential • Costs • Security and privacy implications • Competitive landscape—what are other institutions in our trade area doing? • Other risks • Loss due to fraud or theft • Regulatory criticism • Reputational 120

Actions You and Your Institution Can Take Know your member base (and potential member base) • What are their access needs (bricks and mortar vs. hand-held devices) • Is membership aging? Becoming younger? • How do we know needs? • Surveys? • Anecdotal data? • Understand your institution’s vision and strategic • What markets (segments, communities) are we in? • Where do we want to go? 121

Actions You and Your Institution Can Take • Understand the strengths of management and staff • Do we have the in-house expertise to embrace, exploit and control new technologies? • If yes, let’s set a timetable • If no, we either need to develop it or find a thirdparty vendor 122

Actions You and Your Institution Can Take • Ensure Development/Implementation is orderly and controlled • Planning is critical • Realistic timeframes • Milestones/checkpoints • Progress reporting as appropriate • Metrics (usage, costs) • Policies and procedures • Marketing and Educational materials • Staff training • Roll-out sequencing 123

Actions You and Your Institution Can Take Post-Rollout Oversight • Projected vs. Actual • Usage • Costs • Revenues • Anecdotal information on • Overall progress • Member reaction • Unexpected things that went right/wrong • Plans for activities prior to next status report • Management’s assessment 124

Governance Redux IT Internal Audit coverage should include the guidance and oversight received from the Board (i. e. Governance) This coverage can be accomplished in “pieces” throughout the other IT audit areas 125

Conclusions____________ Technology will continue to evolve Credit Unions can choose to adopt new technologies and offer new services or not, but Competitors and members will be watching and evaluating Risks and challenges remain relatively the same Your IT Internal Audit program can and must evolve, too. 126

Thank you! Jay Bowman, CISA, CISM Director jbowman@accumepartners. com Phone: (484) 844 -7132 127
 Auditing computer based information system
Auditing computer based information system Auditing standards differ from auditing procedures
Auditing standards differ from auditing procedures Welcome to teen challenge uk - teen challenge uk
Welcome to teen challenge uk - teen challenge uk Transcontinent
Transcontinent New disruptive technologies 2021
New disruptive technologies 2021 New disruptive technologies
New disruptive technologies Cv looking for a new challenge
Cv looking for a new challenge Ready for a new challenge
Ready for a new challenge Hình ảnh bộ gõ cơ thể búng tay
Hình ảnh bộ gõ cơ thể búng tay Frameset trong html5
Frameset trong html5 Bổ thể
Bổ thể Tỉ lệ cơ thể trẻ em
Tỉ lệ cơ thể trẻ em Gấu đi như thế nào
Gấu đi như thế nào Tư thế worms-breton
Tư thế worms-breton Hát lên người ơi alleluia
Hát lên người ơi alleluia Các môn thể thao bắt đầu bằng tiếng chạy
Các môn thể thao bắt đầu bằng tiếng chạy Thế nào là hệ số cao nhất
Thế nào là hệ số cao nhất Các châu lục và đại dương trên thế giới
Các châu lục và đại dương trên thế giới Công của trọng lực
Công của trọng lực Trời xanh đây là của chúng ta thể thơ
Trời xanh đây là của chúng ta thể thơ Mật thư tọa độ 5x5
Mật thư tọa độ 5x5 101012 bằng
101012 bằng độ dài liên kết
độ dài liên kết Các châu lục và đại dương trên thế giới
Các châu lục và đại dương trên thế giới Thể thơ truyền thống
Thể thơ truyền thống Quá trình desamine hóa có thể tạo ra
Quá trình desamine hóa có thể tạo ra Một số thể thơ truyền thống
Một số thể thơ truyền thống Cái miệng nó xinh thế
Cái miệng nó xinh thế Vẽ hình chiếu vuông góc của vật thể sau
Vẽ hình chiếu vuông góc của vật thể sau Thế nào là sự mỏi cơ
Thế nào là sự mỏi cơ đặc điểm cơ thể của người tối cổ
đặc điểm cơ thể của người tối cổ V. c c
V. c c Vẽ hình chiếu đứng bằng cạnh của vật thể
Vẽ hình chiếu đứng bằng cạnh của vật thể Tia chieu sa te
Tia chieu sa te Thẻ vin
Thẻ vin đại từ thay thế
đại từ thay thế điện thế nghỉ
điện thế nghỉ Tư thế ngồi viết
Tư thế ngồi viết Diễn thế sinh thái là
Diễn thế sinh thái là Dot
Dot So nguyen to
So nguyen to Tư thế ngồi viết
Tư thế ngồi viết Lời thề hippocrates
Lời thề hippocrates Thiếu nhi thế giới liên hoan
Thiếu nhi thế giới liên hoan ưu thế lai là gì
ưu thế lai là gì Khi nào hổ mẹ dạy hổ con săn mồi
Khi nào hổ mẹ dạy hổ con săn mồi Khi nào hổ mẹ dạy hổ con săn mồi
Khi nào hổ mẹ dạy hổ con săn mồi Hệ hô hấp
Hệ hô hấp Từ ngữ thể hiện lòng nhân hậu
Từ ngữ thể hiện lòng nhân hậu Thế nào là mạng điện lắp đặt kiểu nổi
Thế nào là mạng điện lắp đặt kiểu nổi Aabe application form
Aabe application form Audit note book
Audit note book Auditing revenue cycle
Auditing revenue cycle Understanding the entity and its environment template
Understanding the entity and its environment template Modern auditing and assurance services
Modern auditing and assurance services Database security methods
Database security methods Auditing networks perimeters and systems
Auditing networks perimeters and systems Modern auditing and assurance services
Modern auditing and assurance services Modern auditing and assurance services
Modern auditing and assurance services Authentication authorization accounting and auditing
Authentication authorization accounting and auditing Sri lanka accounting standards
Sri lanka accounting standards Chapter 9 auditing sales and receivables
Chapter 9 auditing sales and receivables Database security and auditing
Database security and auditing New york pennsylvania new jersey delaware
New york pennsylvania new jersey delaware New oil and new wineskin
New oil and new wineskin Weaknesses and strengths of the articles of confederation
Weaknesses and strengths of the articles of confederation What forces are defining the new marketing realities
What forces are defining the new marketing realities New classical and new keynesian macroeconomics
New classical and new keynesian macroeconomics Chapter 16 toward a new heaven and a new earth
Chapter 16 toward a new heaven and a new earth Leanne keene french ambassador arrives from paris
Leanne keene french ambassador arrives from paris New classical and new keynesian macroeconomics
New classical and new keynesian macroeconomics Opportunities and challenges of media and information
Opportunities and challenges of media and information International standard on auditing 240
International standard on auditing 240 Latin word for audit
Latin word for audit Hirarki standar auditing
Hirarki standar auditing Second party audits
Second party audits What is auditing around the computer
What is auditing around the computer Firewall security audit
Firewall security audit Voucher welfare
Voucher welfare Definition of auditing
Definition of auditing Real time auditing definition
Real time auditing definition Critical point auditing
Critical point auditing Information technology auditing
Information technology auditing Canadian auditing standards
Canadian auditing standards Subject matter in auditing
Subject matter in auditing Introduction to audit
Introduction to audit Audit approach
Audit approach Auditing 1
Auditing 1 Mobile audit technology
Mobile audit technology Supervision and review in audit
Supervision and review in audit Audit is important
Audit is important Firewalk network auditing tool
Firewalk network auditing tool Continuous auditing
Continuous auditing Cost auditing standards
Cost auditing standards Pcaob auditing standard no. 5
Pcaob auditing standard no. 5 Conclusion of auditing
Conclusion of auditing What is private audit
What is private audit Fruity wifi
Fruity wifi Distinguish between auditing investigation
Distinguish between auditing investigation Continuous auditing workflow
Continuous auditing workflow Pcaob auditing standards
Pcaob auditing standards Continuous auditing automation
Continuous auditing automation Finance and investment cycle
Finance and investment cycle Impact of information technology on auditing
Impact of information technology on auditing Tujuan audit
Tujuan audit Teori permintaan dan penawaran jasa audit
Teori permintaan dan penawaran jasa audit Auditing the revenue cycle
Auditing the revenue cycle Test data method auditing
Test data method auditing Internal auditing assurance & advisory services
Internal auditing assurance & advisory services Auditing chapter 1
Auditing chapter 1 End user computing controls examples
End user computing controls examples Economic demand for auditing
Economic demand for auditing Continuous monitoring vs continuous auditing
Continuous monitoring vs continuous auditing Substantive procedures
Substantive procedures Business risk approach to auditing
Business risk approach to auditing Operational auditing
Operational auditing Issai standards
Issai standards Operational auditing
Operational auditing Continuous auditing workflow
Continuous auditing workflow Continuous auditing workflow
Continuous auditing workflow Information technology auditing james hall
Information technology auditing james hall Operational auditing
Operational auditing Ssis log provider for sql server
Ssis log provider for sql server Continuous auditing continuous monitoring
Continuous auditing continuous monitoring Contemporary issues in auditing
Contemporary issues in auditing Pdc model of internal control
Pdc model of internal control Auditing & attestation
Auditing & attestation Siklus auditing dimulai dari
Siklus auditing dimulai dari