The Impact of Information Technology on the Audit



















- Slides: 41

The Impact of Information Technology on the Audit Process Chapter 12 12 -1 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall.

Learning Objectives Describe how IT improves internal control. Identify risks to accounting systems specific to IT. Explain how general controls and application controls reduce IT risks. Describe how general controls affect the auditor’s testing of application controls. 12 -2 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall.

Learning Objectives Use test data, parallel simulation, and embedded audit module approaches to test automated controls. Identify issues for e-commerce systems and other specialized IT systems. 12 -3 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall.

1 Describe how IT improves internal control. 12 -4 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall.

Computer controls replace manual controls Higher-quality information is available 12 -5 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall.

2 Identify risks to accounting systems specific to IT. 12 -6 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall.

Ø Risks to hardware and data Ø Reduced audit trail Ø Need for IT experience and separation of IT duties 12 -7 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall.

Reliance on hardware and software Data loss 12 -8 Unauthorized access Systematic vs. random errors Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall.

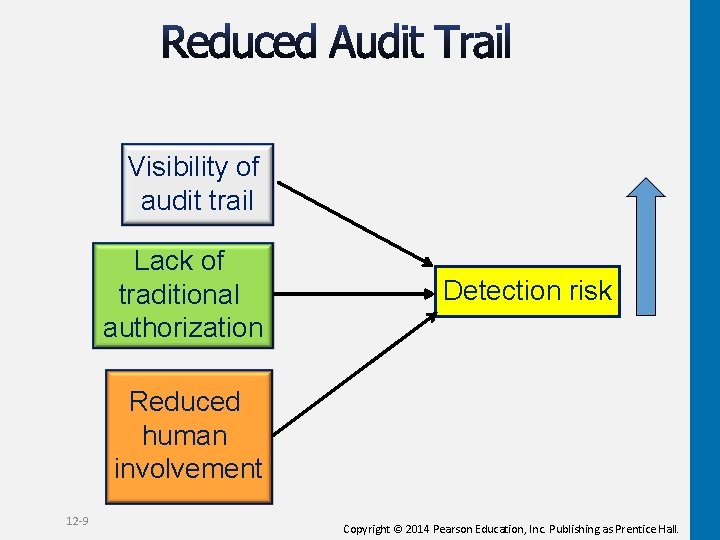
Visibility of audit trail Lack of traditional authorization Detection risk Reduced human involvement 12 -9 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall.

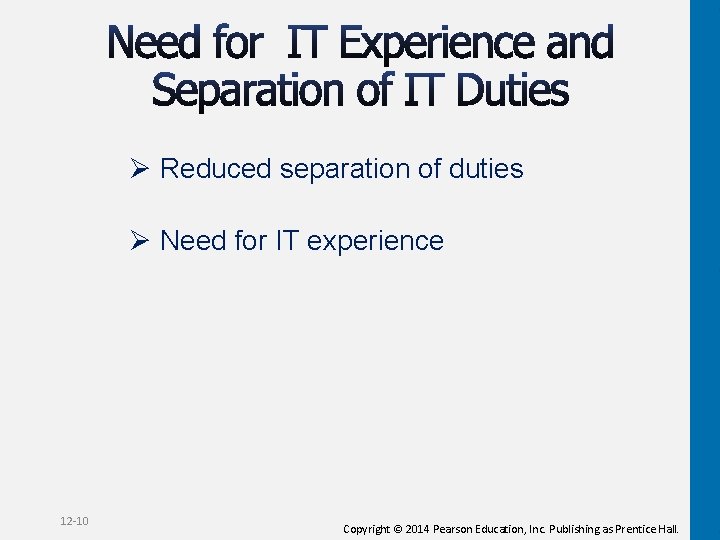
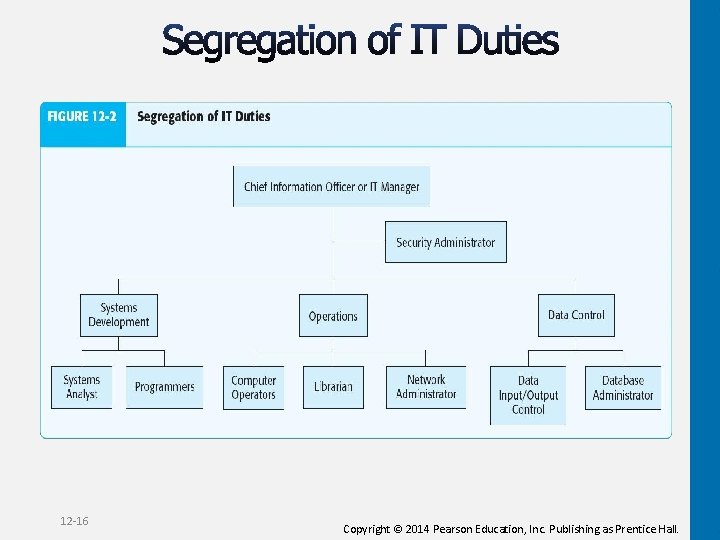
Ø Reduced separation of duties Ø Need for IT experience 12 -10 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall.

3 Explain how general controls and application controls reduce IT risks. 12 -11 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall.

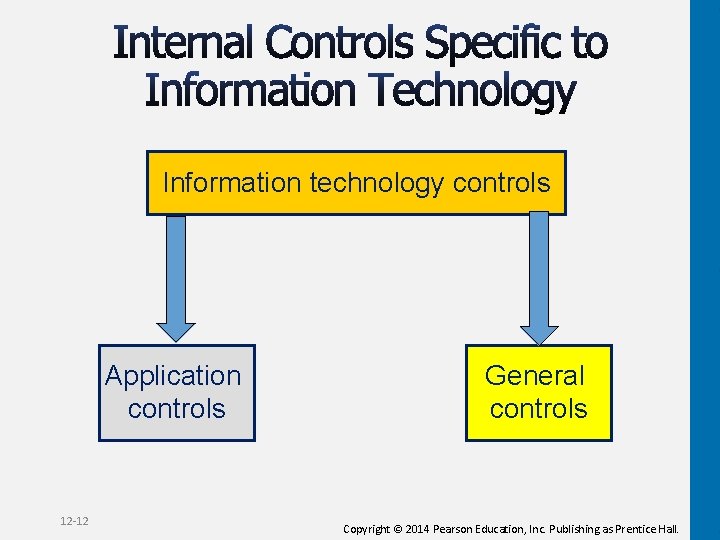
Information technology controls Application controls 12 -12 General controls Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall.

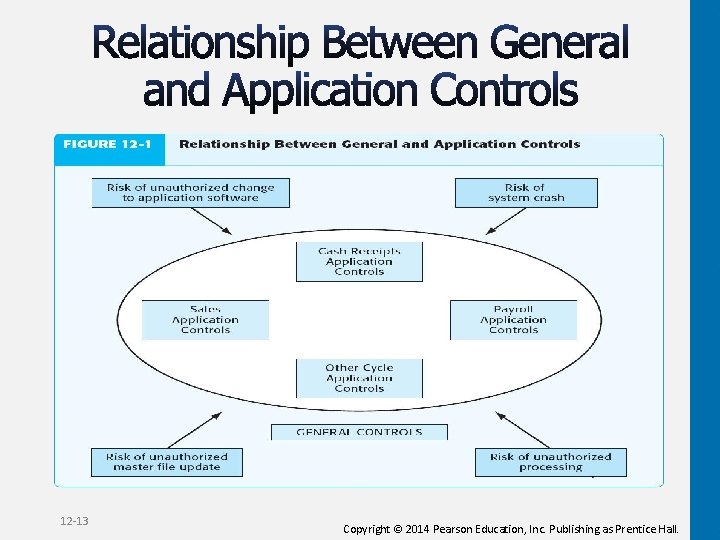
12 -13 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall.

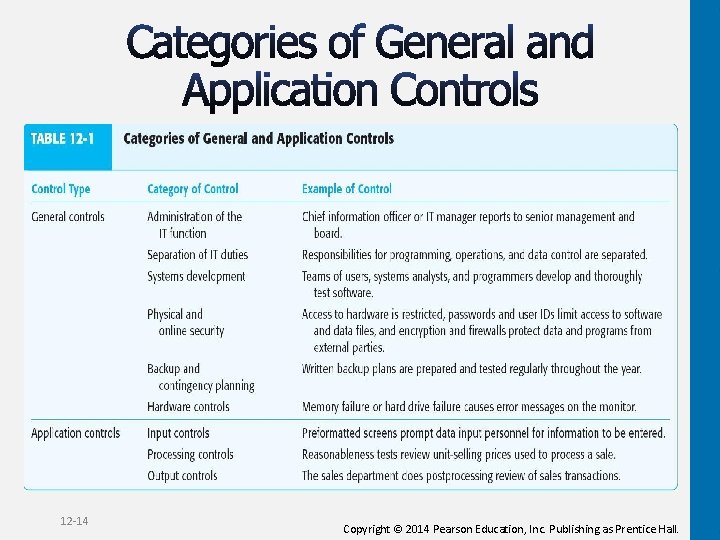
12 -14 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall.

The perceived importance of IT within an organization is often dictated by the attitude of the board of directors and senior management. 12 -15 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall.

12 -16 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall.

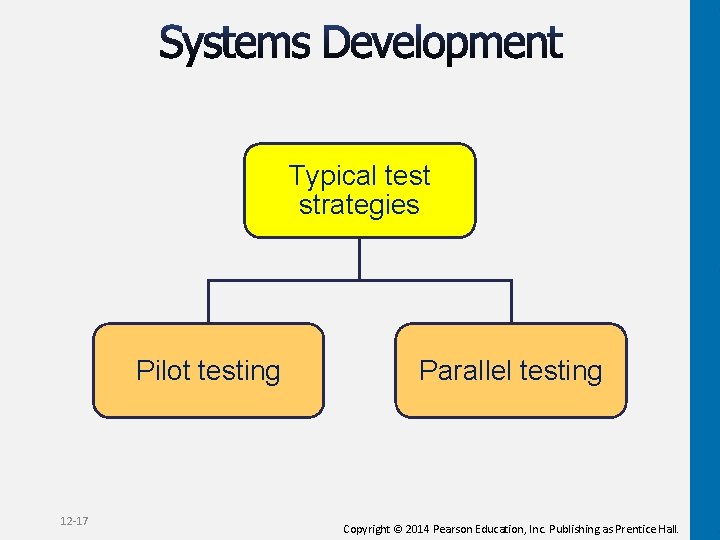
Typical test strategies Pilot testing 12 -17 Parallel testing Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall.

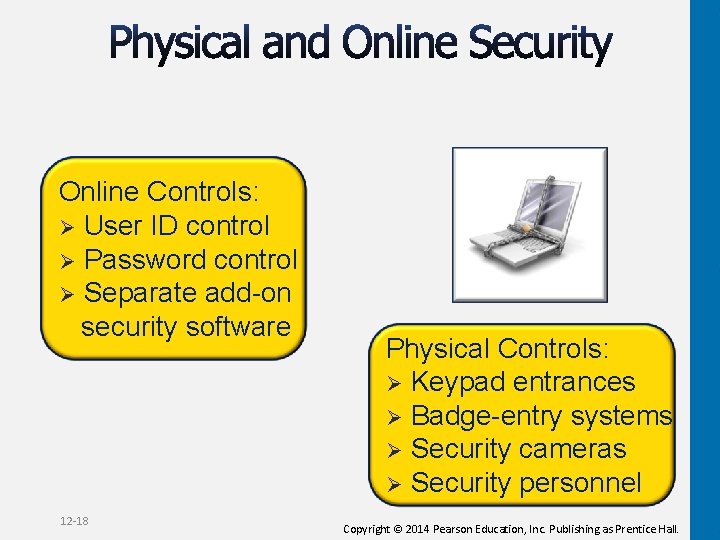
Online Controls: Ø User ID control Ø Password control Ø Separate add-on security software 12 -18 Physical Controls: Ø Keypad entrances Ø Badge-entry systems Ø Security cameras Ø Security personnel Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall.

Offsite storage of critical files is a key element to a backup and contingency plan 12 -19 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall.

These controls are built into computer equipment by the manufacturer to detect and report equipment failures. 12 -20 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall.

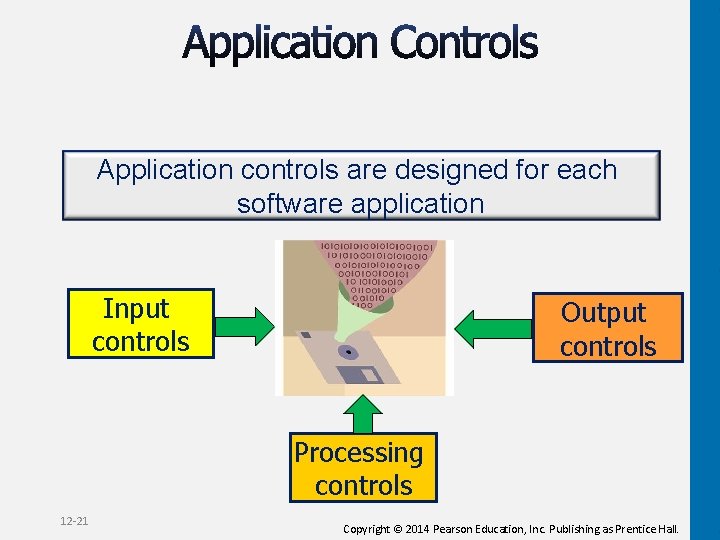
Application controls are designed for each software application Input controls Output controls Processing controls 12 -21 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall.

These controls are designed by an organization to ensure that the information being processed is authorized, accurate, and complete. 12 -22 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall.

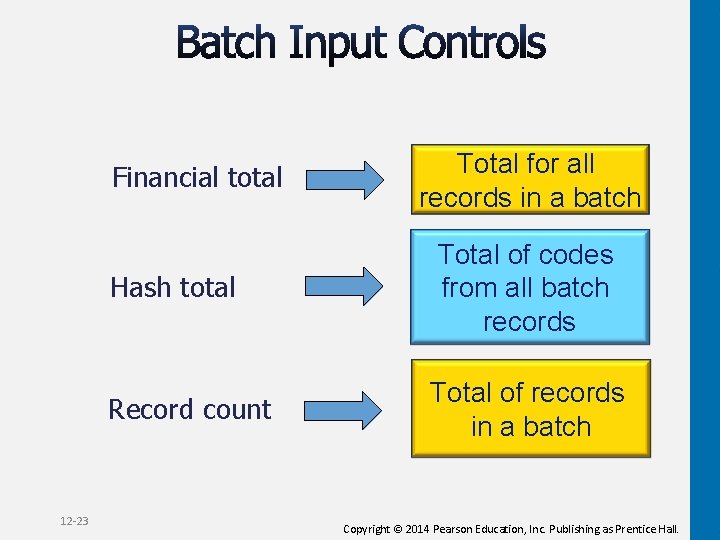
Financial total 12 -23 Total for all records in a batch Hash total Total of codes from all batch records Record count Total of records in a batch Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall.

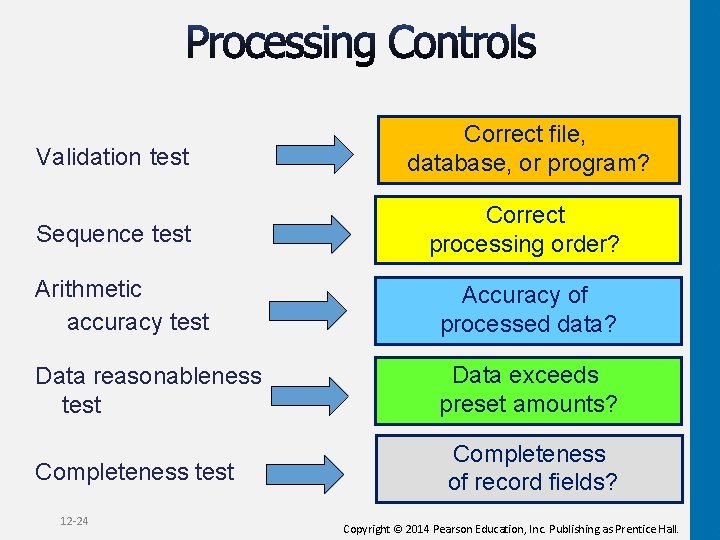
Validation test Correct file, database, or program? Sequence test Correct processing order? Arithmetic accuracy test Accuracy of processed data? Data reasonableness test Data exceeds preset amounts? Completeness test 12 -24 Completeness of record fields? Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall.

These controls focus on detecting errors after processing is completed rather than on preventing errors. 12 -25 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall.

4 Describe how general controls affect the auditor’s testing of application controls. 12 -26 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall.

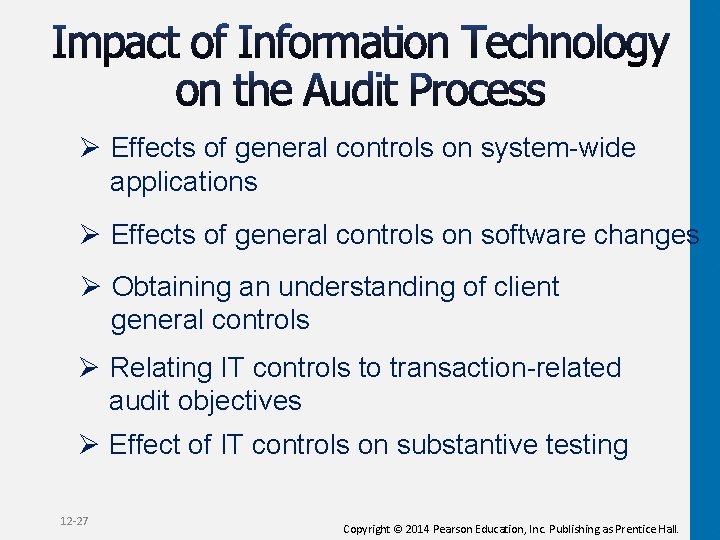
Ø Effects of general controls on system-wide applications Ø Effects of general controls on software changes Ø Obtaining an understanding of client general controls Ø Relating IT controls to transaction-related audit objectives Ø Effect of IT controls on substantive testing 12 -27 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall.

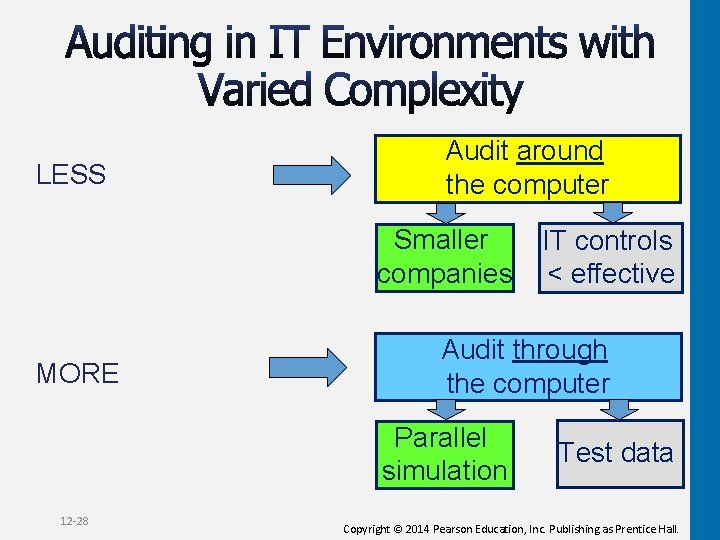
LESS Audit around the computer Smaller companies MORE Audit through the computer Parallel simulation 12 -28 IT controls < effective Test data Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall.

12 -29 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall.

5 Use test data, parallel simulation, and embedded audit module approaches to test automated controls. 12 -30 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall.

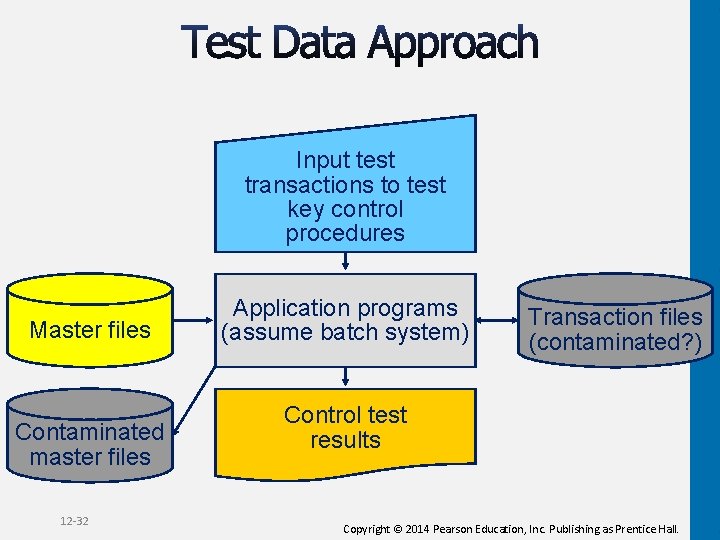
1. Test data should include all relevant conditions that the auditor wants tested. 2. Application programs tested by the auditors’ test data must be the same as those the client used throughout the year. 3. Test data must be eliminated from the client’s records. 12 -31 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall.

Input test transactions to test key control procedures Master files Contaminated master files 12 -32 Application programs (assume batch system) Transaction files (contaminated? ) Control test results Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall.

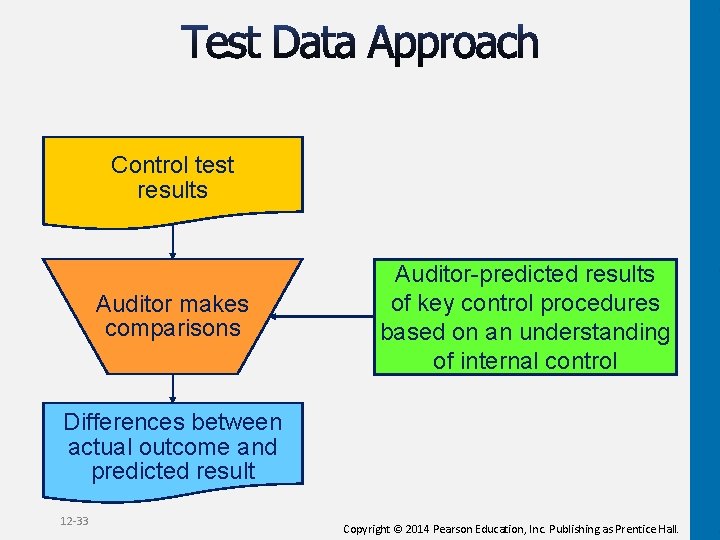
Control test results Auditor makes comparisons Auditor-predicted results of key control procedures based on an understanding of internal control Differences between actual outcome and predicted result 12 -33 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall.

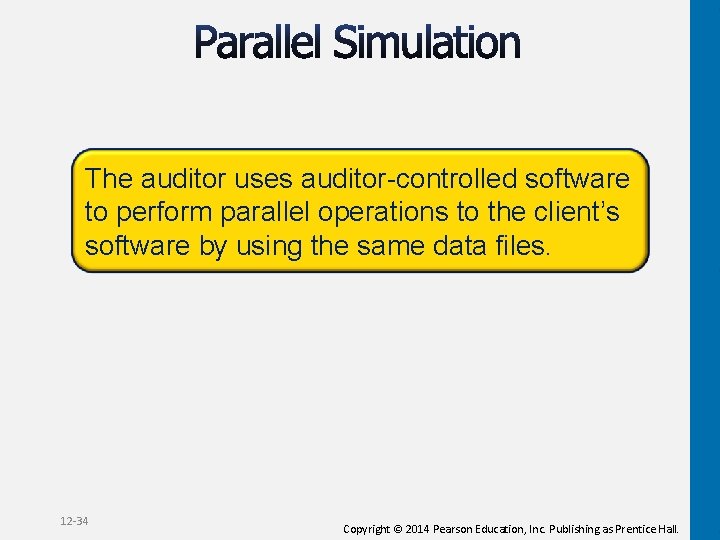
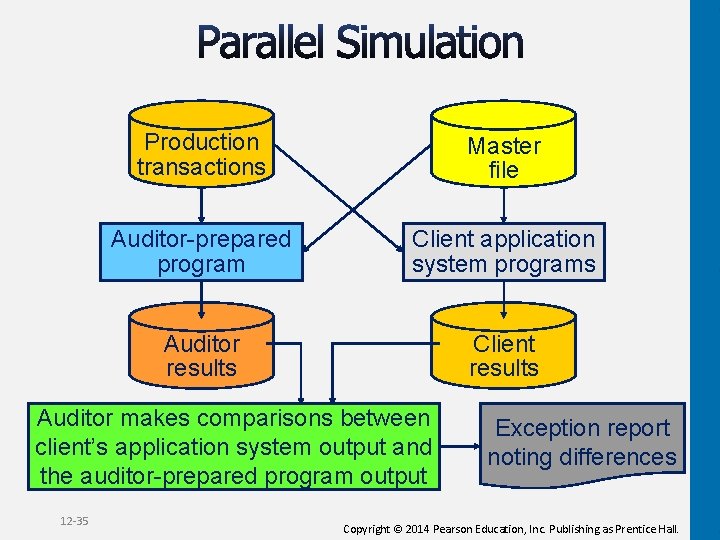
The auditor uses auditor-controlled software to perform parallel operations to the client’s software by using the same data files. 12 -34 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall.

Production transactions Master file Auditor-prepared program Client application system programs Auditor results Client results Auditor makes comparisons between client’s application system output and the auditor-prepared program output 12 -35 Exception report noting differences Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall.

Auditor inserts an audit module in the client’s application system to identify specific types of transactions. 12 -36 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall.

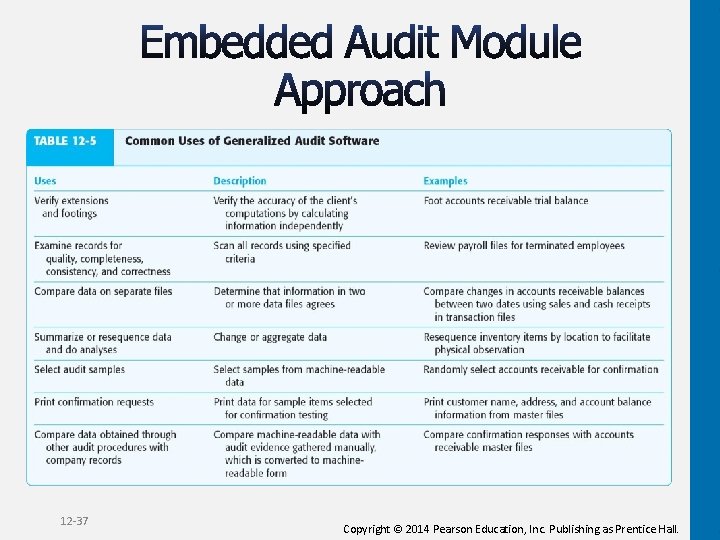
12 -37 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall.

6 Identify issues for e-commerce systems and other specialized IT systems. 12 -38 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall.

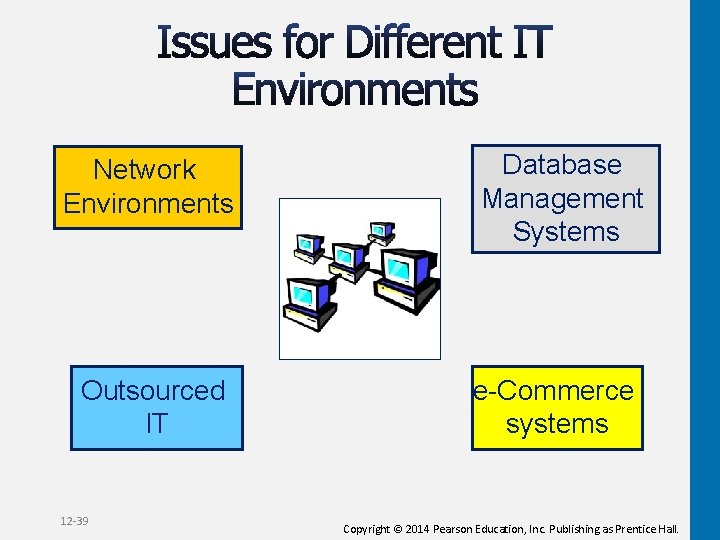
Network Environments Outsourced IT 12 -39 Database Management Systems e-Commerce systems Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall.

12 -40 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall.

Copyright All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form or by any means, electronic, mechanical, photocopying, recording, or otherwise, without the prior written permission of the publisher. Printed in the United States of America. 12 -41 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall.
 Impact of information technology on auditing
Impact of information technology on auditing Chapter 16 the impact of technology
Chapter 16 the impact of technology Perbedaan audit konvensional dengan audit berbasis risiko
Perbedaan audit konvensional dengan audit berbasis risiko Audit klinis adalah
Audit klinis adalah Beda audit medis dan audit klinis
Beda audit medis dan audit klinis Penyelesaian audit dan tanggung jawab pasca audit
Penyelesaian audit dan tanggung jawab pasca audit Konsep dasar audit manajemen
Konsep dasar audit manajemen Perbedaan prosedur audit top-down dengan bottom-up
Perbedaan prosedur audit top-down dengan bottom-up Private audit
Private audit Perbedaan audit konvensional dengan audit berbasis risiko
Perbedaan audit konvensional dengan audit berbasis risiko Audit is derived from the latin word which is
Audit is derived from the latin word which is Audit universe definition
Audit universe definition Overall audit plan and audit program
Overall audit plan and audit program Global technology audit guide
Global technology audit guide Mobile auditing software
Mobile auditing software Materials technology positive impacts
Materials technology positive impacts Science and technology
Science and technology Volvo information technology
Volvo information technology User acceptance of information technology
User acceptance of information technology Conclusion for ict
Conclusion for ict Media literacy vs information literacy
Media literacy vs information literacy Northwestern university information technology
Northwestern university information technology 5 disadvantages of information technology
5 disadvantages of information technology Discuss about information technology and e-business
Discuss about information technology and e-business Positive impacts of ict
Positive impacts of ict History information technology
History information technology Fluency with information technology
Fluency with information technology Issues surrounding information privacy
Issues surrounding information privacy Bridge in ict
Bridge in ict Erp meaning in information technology
Erp meaning in information technology Future trends in media and information
Future trends in media and information Control objectives for information and related technology
Control objectives for information and related technology Control objectives for information and related technology
Control objectives for information and related technology Information technology project management 9th edition
Information technology project management 9th edition Information technology cost management
Information technology cost management Information technology project management 9th edition ppt
Information technology project management 9th edition ppt Information technology chapter 3
Information technology chapter 3 Information technology auditing
Information technology auditing Global information technology management
Global information technology management Information technology resource management
Information technology resource management Cape information technology unit 1 notes
Cape information technology unit 1 notes Btec level 2 information and creative technology
Btec level 2 information and creative technology