Information Technology Security ITS Audit IT Security Audit












































- Slides: 47

Information Technology Security (ITS) Audit IT Security Audit Summary Derek A. Holbert, Ph. D. IT Specialist CJIS Audit Unit 304 -625 -5479 <daholbert@fbi. gov>

ITS Security Audit Objectives • • Scope Framework Process, time frame, selection IT process

ITS Audit Scope • • Scope automated program that Criminal Justice Information Services (CJIS) offers has its own unique audit program. The ITS audit encompasses all those programs into one audit to ensure that all security risks and vulnerabilities have been identified that could affect CJIS data.

ITS Audit Framework - CJIS Security Policy • • • The purpose of the CJIS Security Policy (CSP) is to provide a minimum level of Information Technology (IT) security requirements determined acceptable for the transmission, processing, and storage of CJIS data. The CJIS Systems Agency (CSA) can have more strict technical security guidelines. The CJIS Security Policy is evolving on a yearly basis, as technology changes we have to adjust.

ITS Audit Shall Statements • There are over 600 shall statements within the CJIS Security Policy. • Current version of 5. 8. • Shared management responsibility with CSA and Federal agencies.

ITS Security Audit Criminal Justice Information (CJI) • Criminal Justice Information is the term used to refer to all of the FBI CJIS provided data necessary for law enforcement and civil agencies to perform their missions including, but not limited to biometric, identity history, biographic, property, and case/incident history data.

ITS Audit Framework – Outsourcing Standard • The intent of this Security and Management Control Outsourcing Standard (Outsourcing Standard) is to require that the Contractor maintain a security program consistent with federal and state laws, regulations, and standards (including the FBI Criminal Justice Information Services (CJIS) Security Policy) as well as with rules, procedures, and standards established by the Compact Council and the United States Attorney General.

ITS Audit Framework – Outsourcing Standard • The provisions of this Outsourcing Standard are established by the Compact Council pursuant to 28 CFR Part 906 and are subject to the scope of that rule. They apply to all personnel, systems, networks, and facilities supporting and/or acting on behalf of the Authorized Recipient to perform noncriminal justice administrative functions requiring access to CHRI with a direct connection to the FBI CJIS Wide Area Network (WAN).

ITS Audit • CHRI: • Is a subset of CJI • All CHRI is CJI, but not all CJI is CHRI • For noncriminal justice purposes: • Made available as a result of national fingerprintbased check • Information is considered CHRI if it confirms • the existence or nonexistence of CHRI

ITS Audit • CSA/SIB is notified approximately 1 year in advance that it will be audited in a particular month. • Initial contact call to CSA/SIB approximately 6 months prior to audit. • Determine local agencies to subsequently visit • Send pre audit questionnaire • Conduct Audit by all audit programs, typically same week.

ITS Audit • Onsite visit • IT audit questionnaire & physical inspection • Complete policy packet and leave with agency (DRAFT) • Compile policy packets from all agencies and create draft audit report. CSA/SIB responds to the draft findings • Response is sent to appropriate sanctioning body. Criminal Justice agencies = APB and Noncriminal Justice agencies = Compact Council

ITS Audit Process/Time Frame/Selection • Audits are on a three year cycle. • CSA is expected to visit all local agencies within a three year time frame. • SIB is expected to have a plan to audit all agencies • Identify a small statistical sample of local agencies to audit. Between 10– 20 depending on resources, geographic location, and agencies. • Look for trends in the state and also nationally. • ITS audit is approximately 2 -3 hours.

ITS Audit IT Audit Process –two portions • Administrative Review • Management control/Security addendum/ Outsourcing • Personnel security • Security awareness training • Technical Review • User identification(ID), authentication, advanced authentication, encryption, firewall, event logging, IDPS, & Anti-Virus (AV) • Policies

ITS Audit • Outsourcing • ‘Outsourcing’ is when a noncriminal justice agency, who is receiving CHRI for noncriminal justice purposes (licensing and/or employment) based on fingerprint submission are receiving services from any personnel not defined as the ‘authorized recipient’ • The federal authority, state statute, or regulatory obligation will define the‘authorized recipient’

ITS Audit • Outsourcing applies only if ALL of the following are met: • Using any outside personnel (whether governmental or private contractor) • To perform a noncriminal justice function • With unescorted access to unencrypted CJI

ITS Audit • Outsourcing requires: • Prior approval from the Compact Officer/Chief Administrator in writing

ITS Audit • Scenario: The Department of Education (NCJA) is submitting fingerprint based record checks for the licensing of teachers under an FBI approved state statute (under Federal 92. 544). There is no additional statute that covers agency personnel for access the CHRI, so the Department is not fingerprinting internal staff processing the licensure. The DOE is defined within the statue of the authorized recipient. When the CHRI results are returned from the CSA, the DOE saves the pdf of the CHRI results on a network file share. The network, including the file share, is maintained by the State Department of Technology Services (NCJA) which provides them unescorted access to unencrypted CJI.

ITS Audit • Is the NCJA in compliance? • Yes or No

ITS Audit • No • Here’s why: The Department of Education is defined within the statute as the authorized recipient. Any outside personnel performing services is considered outsourcing. The Security and Management Control Outsourcing Standard for Non-Channeler (Outsourcing Standard) requires prior approval, in writing, from the State Compact Officer/Chief Administrator in order for the agency to allow access.

ITS Audit • Scenario: The Department of Health and Welfare is submitting fingerprint based record checks for the licensing under an FBI approved state statute (under Federal 92. 544). The Department of Health and Welfare is defined in statute as the authorized recipient. The agency is saving the CHRI provided by the CSA within a structured query language (SQL) database. In addition, the agency is emailing CHRI to the individual of record

ITS Audit • Continued • A private contractor is providing IT services that allows personnel unescorted access to the CHRI. The Department of Health and Welfare has received verbal permission from the State Compact Officer prior to outsourcing noncriminal justice functions that allowed contractor personnel unescorted access to CHRI. • Is the NCJA in compliance? • Yes or No

ITS Audit • No • Here’s why: Although the State Compact Officer approved outsourcing, the approval was not provided in writing for verification during the audit.

ITS Audit • Scenario: The Department of Human Services (NCJA) is submitting fingerprint-based record checks for employment with the State agency under an FBI approved state statute (under Federal 92. 544). The statute authorizes the check for all DHS employees, but only employees of DHS. In addition, the statute defines the DHS as the “authorized recipient” of the CHRI results. The agency is recording the CHRI results within a webbased application. A third party contractor is servicing the web-based application, and has unescorted access to unencrypted CHRI. • Is the NCJA in compliance? • Yes or No

• No • Here’s why: Because personnel outside of the authorized recipient have unescorted access to unencrypted CHRI, the agency is outsourcing. The Security and Management Control Outsourcing Standard for Non-Channeler (Outsourcing Standard) requires prior approval, in writing, from the State Compact Officer/Chief Administrator in order for the agency to allow access.

ITS Audit Rank 2016 Percent 2017 Percent 2018 Percent 1 Outsourcing 77% Outsourcing 96% Outsourcing 94%

ITS Audit • Personnel Security • The ability to conduct fingerprints is based on federal authority or a state statute.

ITS Audit • Scenario: The Department of Education (NCJA) is submitting fingerprint based record checks for the licensing of teachers under an FBI approved state statute (under Federal 92. 544). There is no additional statute that covers agency personnel for access the CHRI, so the Department is not fingerprinting internal staff processing the licensure. • Is the NCJA in compliance? • Yes or No

ITS Audit • Yes • Here’s why: A NCJA is only authorized to submit a fingerprint-based record check when an authority (FBI approved state statute) to do so exists. Because the proper authority does not exist, the agency would fall under the exemption in Appendix J of the CJIS Security Policy.

ITS Audit • Scenario: The Board of Nursing (NCJA) is submitting fingerprint-based record checks for the licensing of nurses under an FBI approved state statute (under Federal 92. 544). The agency is using this same statute to fingerprint internal staff for access to CHRI to be thorough. • Is the NCJA in compliance? • Yes or No

ITS Audit • No • Here’s why: The statute does not include authorization to fingerprint for “access to CHRI”, the agency is in violation of the CFR, as CHRI can only be obtained with authorization and cannot be used for the purpose of which is was obtained (meaning, check completed for licensure of board members could not then be used to determine authorization for access to CHRI). Because the proper authority does not exist, the agency would fall under the exemption in Appendix J of the CJIS Security Policy.

ITS Audit Security Awareness Training • • Required topics are defined in policy 4 Tiered approach Unescorted access - janitorial Authorized access, i. e. , limited - clerical and file Physical and logical access, i. e. , terminal access IT employees Required every 2 years for criminal justice community • If agency is outsourcing the private contractor must take security awareness training annually.

ITS Audit Technical Requirements • Technical Review • User ID • Authentication • Advanced authentication • Encryption • Boundary protection • Intrusion detection and prevention system • Event logging • Patch management • Policies

ITS Audit • User ID • Every user have a unique account. This includes a private contractor with remote access • Accounts are validated annually • There must a validation policy that outlines how this process is accomplished

ITS Audit • Authentication • A user account’s password must meet the following attributes: 8 character length, expire every 90 days, have a 10 reuse, cannot be same as dictionary word, cannot be same as user id, and cannot be seen in clear text. • A private contractor who has remote access must have a password on their individual account that meets these requirements.

ITS Audit • Encryption • CJI/CHRI must be encrypted in transit with NIST FIPS 140 -2 approved cryptographic mechanisms. • This includes email transmition

ITS Audit • Boundary Protection • Control access to CJI • Monitor inbound and outbound traffic • Patch regularly • Configuration file backed up • Fail closed • Deny applicable connections on rule set

ITS Audit • Intrusion Detection System

ITS Audit • Event Logging • Capture all applicable logs to write, create, and delete by user and administrator. • Capture successful and unsuccessful login attempts • Capture successful and unsuccessful password changes. • Keep applicable logs for 365 days • Review applicable logs weekly

ITS Audit • Patch Management • Utilize operating systems and hardware devices that can be patched. • Windows XP and Windows Server 2003 is not supported by Windows any longer

ITS Audit • Anti-Virus • Malicious Code Protection • Spam Spyware Protection • Updated when applicable patches are released

ITS Audit • Additional Requirements • System Use Notification • Session Lock • Network Diagram

ITS Audit • Policies • • Standards of Discipline Policy Physical Protection Policy Media Destruction Policy Validation Policy Personally owned Information System Policy Security Incident Response Policy

ITS Audit 4 Network Connections • Public • Precincts, sub stations, and disaster recovery/backup sites • Wireless • Mobile data terminals, i. Phone/Andriod, tablets • Internet • Remote maintenance • IT Support • Vendor • Dial up

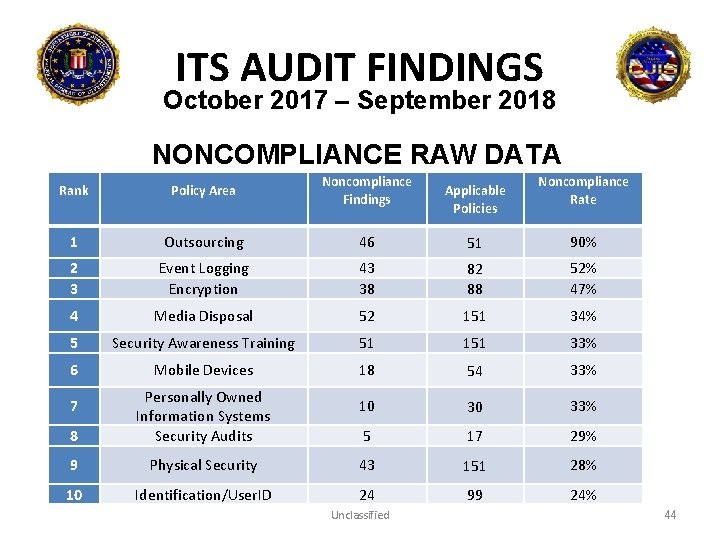
ITS AUDIT FINDINGS October 2017 – September 2018 NONCOMPLIANCE RAW DATA Rank Policy Area Noncompliance Findings 1 Outsourcing 46 51 90% 2 3 Event Logging Encryption 43 38 82 88 52% 47% 4 Media Disposal 52 151 34% 5 Security Awareness Training 51 151 33% 6 Mobile Devices 18 54 33% 10 30 33% 5 17 29% Applicable Policies Noncompliance Rate 8 Personally Owned Information Systems Security Audits 9 Physical Security 43 151 28% 10 Identification/User. ID 24 99 24% 7 Unclassified 44

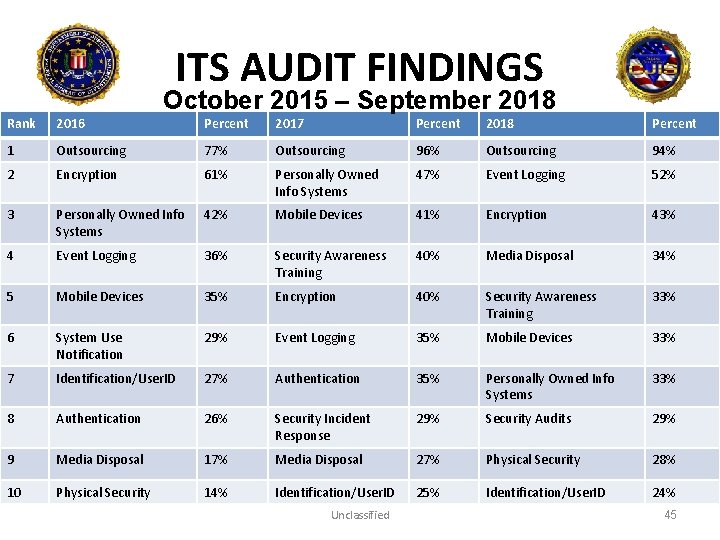
ITS AUDIT FINDINGS October 2015 – September 2018 Rank 2016 Percent 2017 Percent 2018 Percent 1 Outsourcing 77% Outsourcing 96% Outsourcing 94% 2 Encryption 61% Personally Owned Info Systems 47% Event Logging 52% 3 Personally Owned Info Systems 42% Mobile Devices 41% Encryption 43% 4 Event Logging 36% Security Awareness Training 40% Media Disposal 34% 5 Mobile Devices 35% Encryption 40% Security Awareness Training 33% 6 System Use Notification 29% Event Logging 35% Mobile Devices 33% 7 Identification/User. ID 27% Authentication 35% Personally Owned Info Systems 33% 8 Authentication 26% Security Incident Response 29% Security Audits 29% 9 Media Disposal 17% Media Disposal 27% Physical Security 28% 10 Physical Security 14% Identification/User. ID 25% Identification/User. ID 24% Unclassified 45

ITS AUDIT FINDINGS FY 2016 FY 2017 FY 2018 Outsourcing Personally Owned Computers Outsourcing Encryption Event Logging Personally Owned Computers Event Logging Mobile Devices Encryption Security Awareness Training Media Disposal Mobile Devices Encryption Security Awareness Training System Use Notification Event Logging Mobile Devices Identification/User. ID Authentication Personally Owned Computers Authentication Security Incident Response Security Audits Media Disposal Physical Security Identification/User. ID Yellow – 3 years Blue – 2 years Gray – 1 year Unclassified 46

QUESTIONS Please address questions and comments to: Derek A. Holbert, Ph. D. IT Specialist CJIS Audit Unit 304 -625 -5479 <daholbert@fbi. gov>