INTERNET DEFINITION l l l The Internet is










![192. 168. 1. 3 - - [10/Jan/2004: 19: 22: 09 +0000] "GET /cmt 3092 192. 168. 1. 3 - - [10/Jan/2004: 19: 22: 09 +0000] "GET /cmt 3092](https://slidetodoc.com/presentation_image/1c93d9f145116e651acd1350abe62c8b/image-42.jpg)















- Slides: 79

INTERNET

DEFINITION l l l The Internet is a network that connects thousands of other computer networks. The Internet, simply, is a federation of computer networks that speak the same protocols. The Internet consists of thousands of networks worldwide.

Basic Principle l l l Any point (node) on the network would have equal status and the capability to originate, pass and receive messages. Messages would be divided into separately addressed packets starting from a specified source and transferring to a specified destination. The packets, which collectively form the message, would be sent individually, finding their own way to the destination. The route each packet took would not be important but the end result of a successfully communicated message was paramount.

TIMELINE l l 1965 Department of Defense’s Advanced Research Project Association (ARPA) sponsors research into a "cooperative network of timesharing computer". (How could U. S. authorities talk to each other after a nuclear attack? ) 1969 Researchers at four US campuses create the first hosts of the ARPANET, connecting Stanford Research Institute, UCLA, UC Santa Barbara, and the University of UTAH with 56 KB communications lines.

TIMELINE l ARPA’s goals l l l Allow multiple users to send and receive info at same time Network operated packet switching technique l Digital data sent in small packages called packets l Packets contained data, address info, error-control info and sequencing info l Greatly reduced transmission costs of dedicated communications lines Network designed to be operated without centralized control l If portion of network fails, remaining portions still able to route packets

Who is in charge? l l There is no single person or body in overall control of the Internet. There agreed procedures for communication and various voluntary committees that set technical standards. What is illegal under copyright, libel or obscenity laws in one country may be acceptable in another.

ISOC l l The Internet Society (ISOC) is a voluntary organization with more than one hundred members and is regarded as having the greatest influence over how the Internet develops in the future. www. isoc. org

ISOC - IAB l l The Internet Architecture Board (IAB) is appointed by ISOC and has responsibility for technical management and direction of the Internet. ISOC controls the TCP/IP standard through both the IAB and its task forces. However, the process for change on the Internet is usually through documents called Request For Comments (RFCs).

Inter. NIC l l The Internet Network Information Center consists of three organizations known collectively as Inter. NIC is also the registrar for domains and network numbers for the Internet. www. internic. org

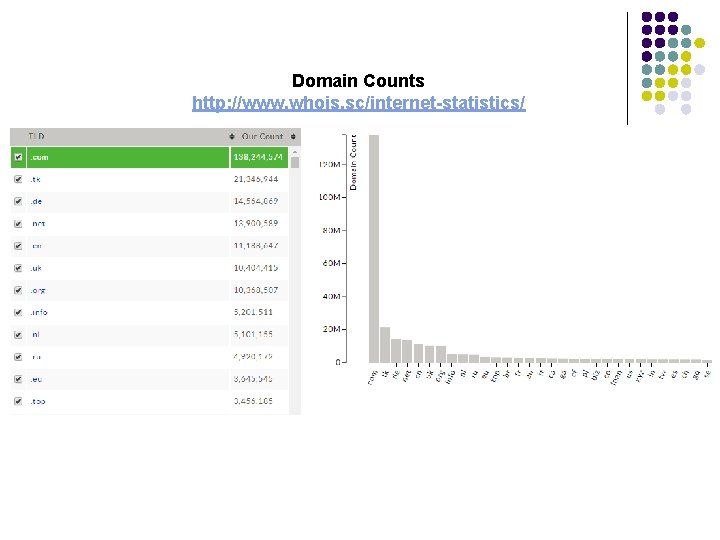
Domain Counts http: //www. whois. sc/internet-statistics/

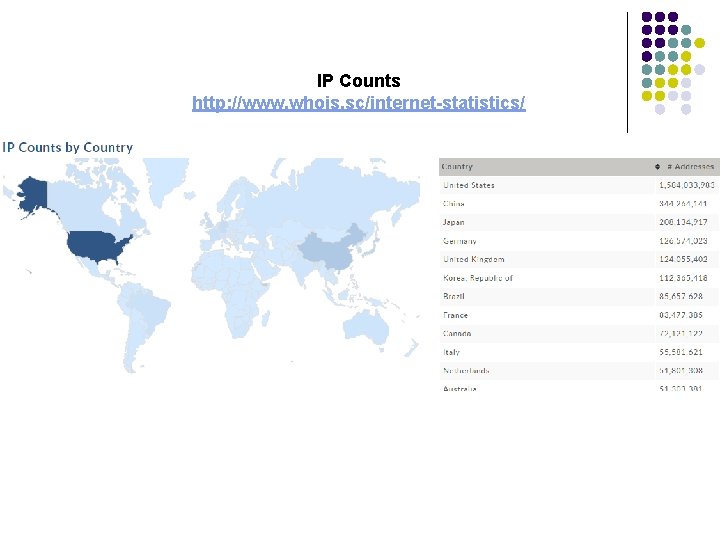
IP Counts http: //www. whois. sc/internet-statistics/

TCP/IP Protocol l 52/64 Internet’s standard protocol is TCP/IP, consists of two protocols TCP (Transmission Control Protocol) and IP (Internet Protocol). Both are software required for Internet communication. TCP is responsible for dividing messages to packets and sending them to other computer securely. TCP on the other computer receives the packets and forms the message. IP protocol, gives an IP address to each computer and gets the messages to their destinations through routers.

IP Addresses l l l IP addresses are formed of 32 bits. Since it is hard to remember those codes they are converted into dotted decimal notation. (4, 294, 967, 296) This conversion is done by using 8 bits with dots in between. Original IP 11000001100110100001101 Divided into 4: 11000001. 100011001101. 0000111 Each 8 bits converted to decimal: 193. 140. 205. 13. New standart is IP. V 6 (281, 474, 976, 710, 656) 255 l 53/64 https: //en. wikipedia. org/wiki/List_of_countries_by_I Pv 4_address_allocation

IP Addresses l l l l 54/64 But these numbers are also not easy. So a naming scheme is used called DNS (Domain Name System). We use domain names instead of numbers. IP address: 79. 123. 181. 130 Domain name: www. mis. boun. edu. tr Last part gives country name. Before that we have type of domain such as education (edu), commercial (com), etc. Name of organization which may be abbreviated Name of computer (together with subnet name) DNS servers convert IPs to domain names or vice versa.

IP Addresses l l Start menu / command nslookup www. mis. boun. edu. tr Server: ardic. cc. boun. edu. tr Address: 193. 140. 192. 20 Name: miss. mis. boun. edu. tr Address: 79. 123. 181. 130 Aliases: www. mis. boun. edu. tr l 54/64 ping www. mis. boun. edu. tr

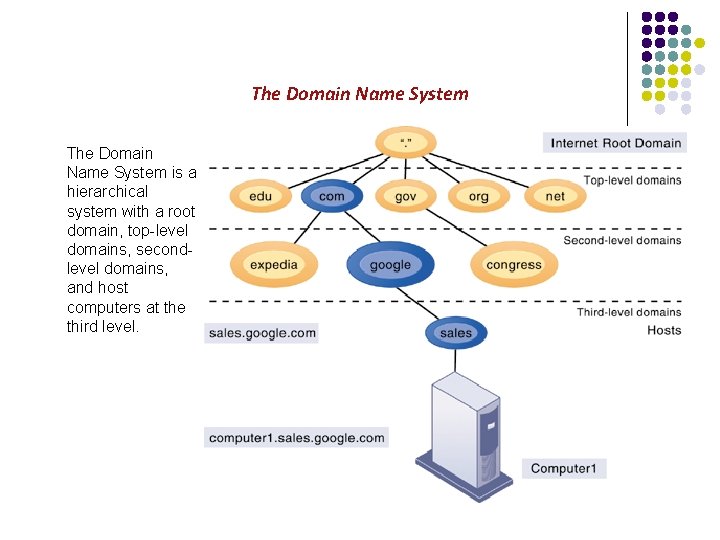
The Domain Name System is a hierarchical system with a root domain, top-level domains, secondlevel domains, and host computers at the third level.

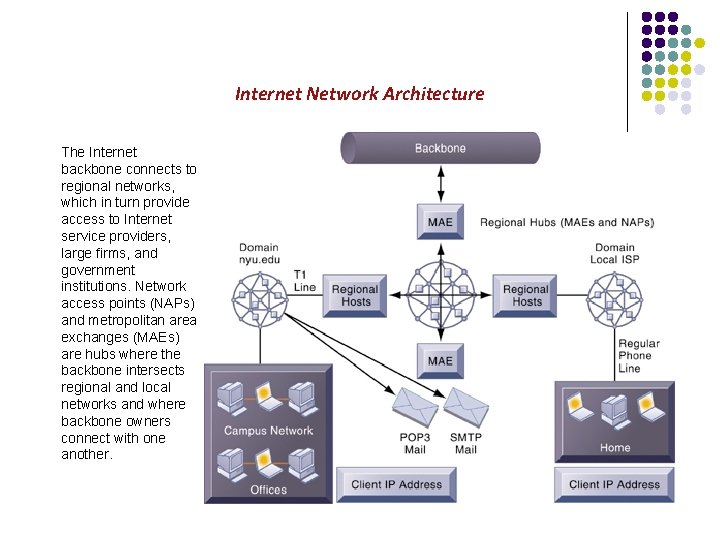
Internet Network Architecture The Internet backbone connects to regional networks, which in turn provide access to Internet service providers, large firms, and government institutions. Network access points (NAPs) and metropolitan area exchanges (MAEs) are hubs where the backbone intersects regional and local networks and where backbone owners connect with one another.

PACKET SWITCHING 53/64 l Method of slicing digital messages into parcels (packets), sending packets along different communication paths as they become available, and then reassembling packets at destination l Previous circuit-switched networks required assembly of complete point-to-point circuit l Packet switching more efficient use of network’s communications capacity

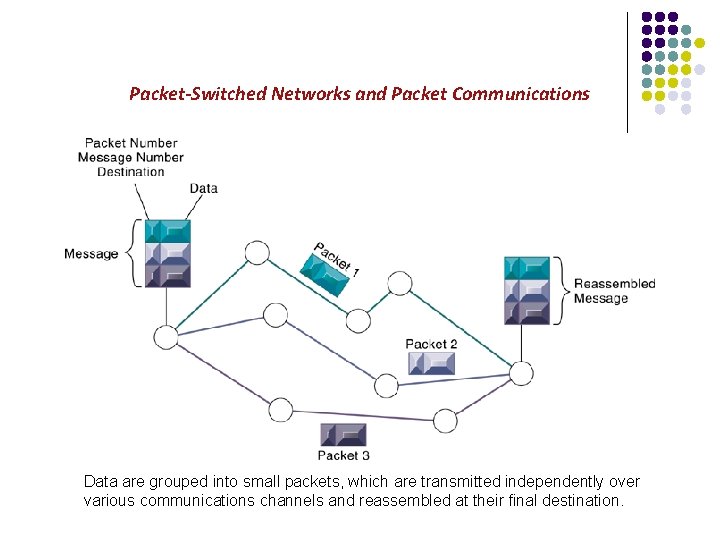
Packet-Switched Networks and Packet Communications Data are grouped into small packets, which are transmitted independently over various communications channels and reassembled at their final destination.

INTERNET SERVICES l l l 53/64 E-mail (SMTP) Chatting and instant messaging Electronic discussion groups / newsgroups Telnet File Transfer Protocol (FTP) World Wide Web (WWW)

The Global Internet l The Web l l Hypertext Markup Language (HTML) Hypertext Transfer Protocol (HTTP): l l Communications standard used for transferring Web pages Uniform resource locators (URLs): l Addresses of Web pages § l http: //www. megacorp. com/content/features/082602. html Web servers § Software for locating and managing Web pages

WWW l l l 53/64 The World Wide Web (WWW) was developed by Tim Berners-Lee and other research scientists at CERN, the European center for nuclear research, in the late 1980 s and early 1990 s. WWW is a client-server model and uses TCP connections to transfer information or web pages from server to client. WWW uses a Hypertext model. Hypertext allows interactive accesses to a collection of documents. Documents can hold l Text (hypertext), Graphics, Sound, Animations, Video Documents are linked together l Non-distributed – all documents stored locally (e. g on CD-Rom). l Distributed – documents stored at remote servers on the Internet.

WWW l l l 53/64 A web page is identified by: l The protocol used to access the web page. l The computer on which the web page is stored. l The TCP port that the server is listening on to allow a client to access the web page. l Directory pathname of web page on server. Specific syntax for Uniform Resource Locator (URL): protocol: //computer_name: port/document_name l Protocol can be http, file, mailto. Computer name can be DNS name or IP address. TCP port is optional (http uses port 80 as its default port). document_name is path on server to web page (file).

WWW l l 53/64 The browser is the client, WWW (or web) server is the server. Browser: l The browser makes TCP connection to the web server. l The browser sends request for the particular web page that it wishes to display. l The browser reads the contents of the web page from the TCP connection and displays it in the browsers window. l The browser closes the TCP connection used to transfer the web page. Each separate item in a web page (e. g. , pictures, audio) require a separate TCP connection. Hyper. Text Transport Protocol (HTTP) specifies commands that the client (browser) issues to the server (web server) and the responses that the server sends back to the client

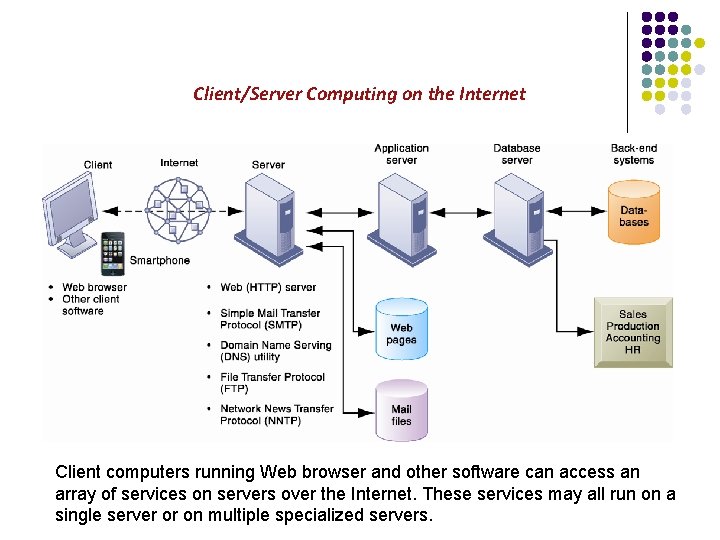
Client/Server Computing on the Internet Client computers running Web browser and other software can access an array of services on servers over the Internet. These services may all run on a single server or on multiple specialized servers.

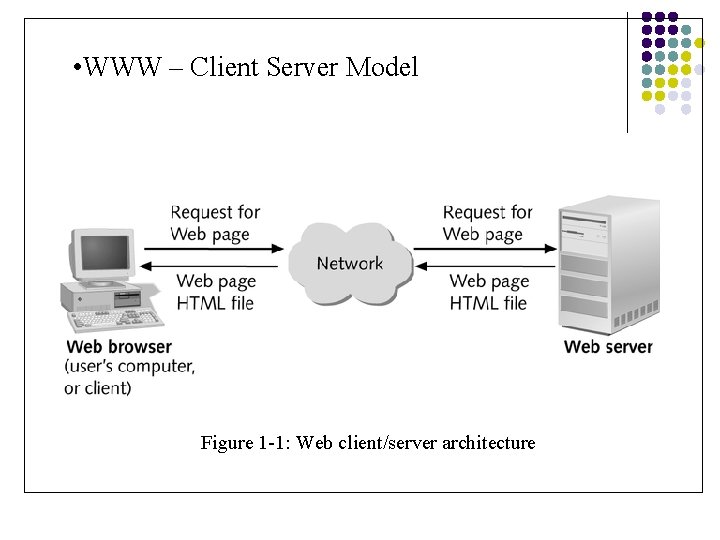
• WWW – Client Server Model Figure 1 -1: Web client/server architecture

Web Server Basics l Duties l l Listen to a port When a client is connected, read the HTTP request Perform some lookup function Send HTTP response and the requested data

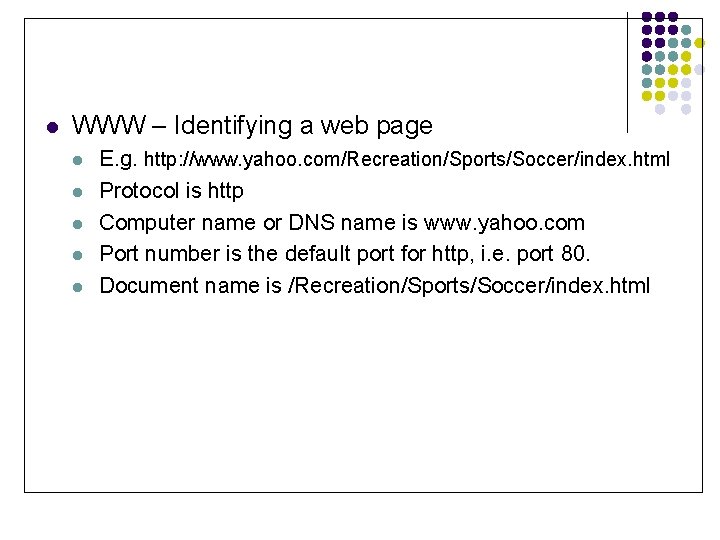
l WWW – Identifying a web page l l l E. g. http: //www. yahoo. com/Recreation/Sports/Soccer/index. html Protocol is http Computer name or DNS name is www. yahoo. com Port number is the default port for http, i. e. port 80. Document name is /Recreation/Sports/Soccer/index. html

Serving a Page l User of client machine types in a URL

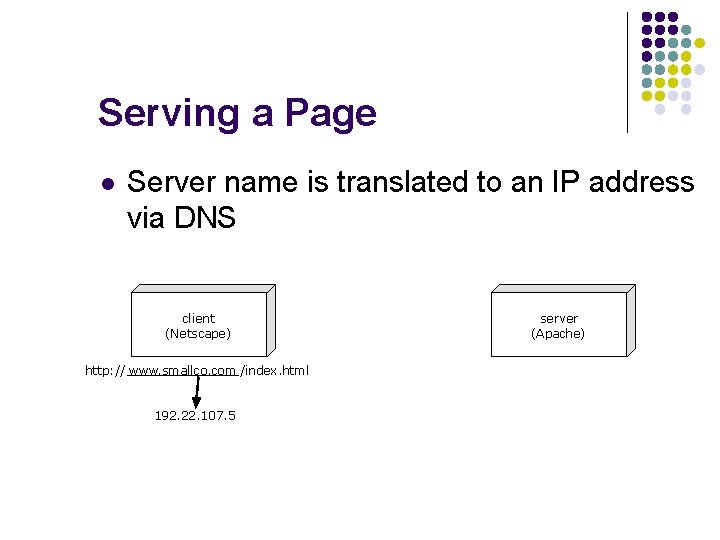
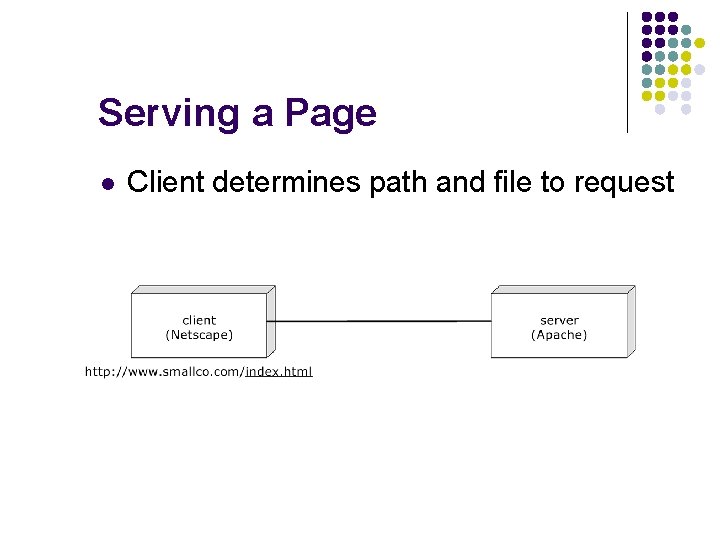
Serving a Page l Server name is translated to an IP address via DNS client (Netscape) http: // www. smallco. com /index. html 192. 22. 107. 5 server (Apache)

Serving a Page l Client connects to server using IP address and port number

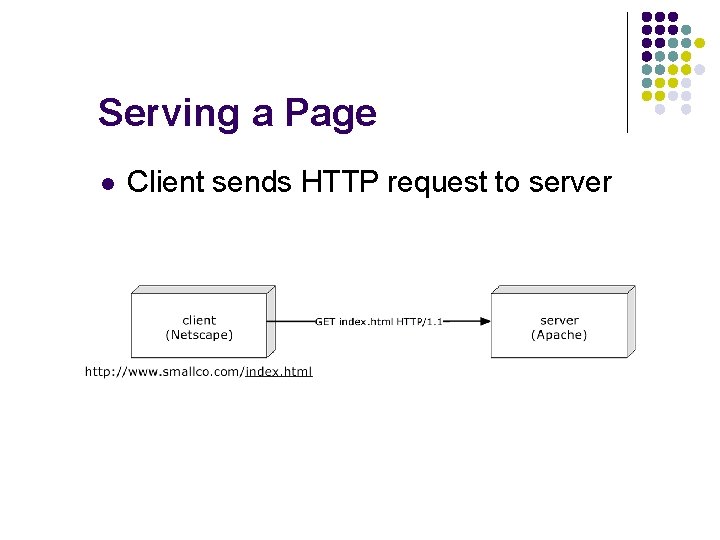
Serving a Page l Client determines path and file to request

Serving a Page l Client sends HTTP request to server

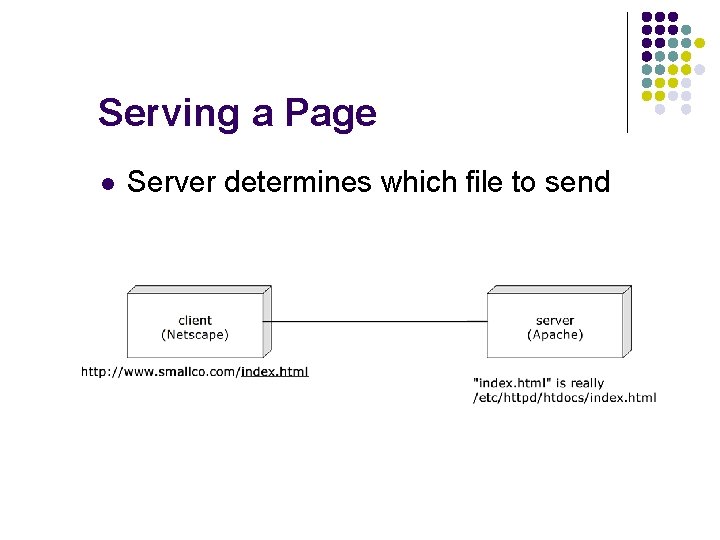
Serving a Page l Server determines which file to send

Serving a Page l Server sends response code and the document

Serving a Page l Connection is broken

HTTP l HTTP is… l l Designed for document transfer Generic l l l not tied to web browsers exclusively can serve any data type Stateless l no persistant client/server connection

HTTP Protocol Definitions l MIME l l l Multipurpose Internet Mail Extensions Standards for encoding different media types in a message Originally developed for emailing files and messages in different languages

l WWW – HTTP Protocol l When a user types in http: //www. yahoo. com/Recreation/Sports/Soccer/index. html, l the broswer creates a HTTP GET Request message and sends it over a TCP connection to the web server. In the above case, the HTTP GET Request message would be GET /Recreation/Sports/Soccer/index. html HTTP/1. 0 User-Agent: Internet. Explorer/5. 0 Accept: text/html, text/plain, image/gif, audio/au “rn”

l WWW – HTTP Request messages l HTTP Request messages are sent from client to server. Request Line Type of Request (e. g. GET) l Optional HTTP Header Additional information such as brower being used, media types accepted “rn” Optional Data Delimiter Carriage return User data e. g. contents of Line feed completed form There a number of valid HTTP Request messages l Get – Used to request a web page from a web server l Head – Return the header of a web page, used by search engines to test the validity of hyperlinks l Post – Used to send data (e. g. results of registration form) to a web server l Put / Delete – Not typically implemented by browsers.

l WWW – HTTP Response messages l HTTP Response messages are sent from server to client. Status Line Success/Failure Indication Number between 200 and 599 l Optional HTTP Header Type of content returned e. g. text/html or image/gif “rn” Optional Data Delimiter Requested Data e. g. web page The Status Line gives information about the success of the previous HTTP Request l 200 – 299 Success l 300 – 399 Redirection – Document has been moved l 400 – 499 Client Error – Bad Request, Unauthorised, Not found l 500 – 599 Server Error – Internal Error, Service Overloaded
![192 168 1 3 10Jan2004 19 22 09 0000 GET cmt 3092 192. 168. 1. 3 - - [10/Jan/2004: 19: 22: 09 +0000] "GET /cmt 3092](https://slidetodoc.com/presentation_image/1c93d9f145116e651acd1350abe62c8b/image-42.jpg)
192. 168. 1. 3 - - [10/Jan/2004: 19: 22: 09 +0000] "GET /cmt 3092 HTTP/1. 1" 301 366 192. 168. 1. 3 - - [10/Jan/2004: 19: 22: 10 +0000] "GET /cmt 3092/ HTTP/1. 1" 200 343 192. 168. 1. 3 - - [10/Jan/2004: 19: 22: 17 +0000] "GET /cmt 3092/xampp-win 321. 2. exe HTTP/1. 1" 404 1243 192. 168. 1. 3 - - [10/Jan/2004: 19: 22: 47 +0000] "GET /cmt 3092/xampp-win 321. 2. exe HTTP/1. 1" 404 1117 192. 168. 1. 3 - - [10/Jan/2004: 19: 23: 29 +0000] "GET /cmt 3092/ HTTP/1. 1" 200 344 192. 168. 1. 3 - - [10/Jan/2004: 19: 23: 36 +0000] "GET /cmt 3092/xampp-win 32 -1. 2. exe HTTP/1. 1" 200 28329331 192. 168. 1. 3 - - [10/Jan/2004: 19: 33: 08 +0000] "GET /cmt 3092 HTTP/1. 1" 301 366

l WWW - Hyperlinks (or links) l l Each document contains links (pointers) to other documents. The link represented by "active area" on screen l Graphic - button Text - highlighted By selecting a particular link, the client fetches the referenced document from a server for display. Links may become invalid. Link is simply a text name for a remote document. Remote document may be moved to a new location while name in link remains in place. l l l

l WWW – Hyperlinks between web pages l l l l Each hyperlink is specified in HTML by using a special tag. An item on a page is associated with another HTML document. Each link is passive, no action is taken until link is selected. HTML tags for a hyperlink are <A> and </A> The linked document is specified by parameter to the tag: HREF="document URL" <A HREF=“http: //www. gcd. ie”>Click here to go to GCD web site. </A> Whatever is between the HTML tags, <A> and </A> is the highlighted hyperlink.

l WWW – Document Representation l l l l Each WWW document is called a page. Initial page for individual or organization is called a home page. Page can contain many different types of information; page must specify: l Content – The actual information l Type of content – The type of information, e. g. text, pictures etc l Links to other documents Rather than having a fixed representation for every browser, pages are formatted with a mark up language. This allows browser to format page to fit display. Different browsers can display pages in different ways. This also allows text-only browser to discard graphics for example. Standard is called Hyper. Text Markup Language (HTML).

l WWW – HTML l l l HTML specifies l Major structure of document l Formatting instructions for browsers to execute. l Hypertext links – Links to other documents l Additional information about document contents Two parts to document: l Head contains details about the document. l Body contains the information/content of the document. Each web page is represented in ASCII text with embedded HTML tags that give formatting instructions to the browser. l Formatted section begins with tag, <TAGNAME> l End of formatted section is indicated by </TAGNAME>

l WWW – HTML Example <HTML> <HEAD> <TITLE> Example Page for lecture</TITLE> </HEAD> <BODY> Lecture notes for today go here! <CENTER> <TABLE BORDER=3> <TR> <TD><A HREF=". /lecture 10. html">Previous Lecture</A> <TD><A HREF=". /lecture 12. html">Next Lecture</A> <TD><A HREF=". /Contents. html">Table of contents</A> <TD><A HREF=". /solutions. html">Solutions to Assignments</A> <TD><A HREF=". /index. html">Index of terms</A> </TABLE> </CENTER> </BODY> </HTML>

l WWW – Other HTML Tags l l Headings - <H 1>, <H 2> Lists l <OL> - Ordered (numbered) list <UL> - Unordered (bulleted) list l <LI> - List item Tables l <TABLE>, </TABLE> - Define table l <TR> - Begin row l <TD> - Begin item in row Parameters l Keyword-value pairs in HTML tags l <TABLE BORDER=3> l l l

l WWW – Embedding Graphics l l IMG tag specifies insertion of graphic l Parameters: l SRC="filename" l ALIGN= - alignment relative to text <img SRC=“GCD. gif" height=35 width=30> The above line would insert the image in the file GCD. gif into any web page. Image must be in format known to browser, e. g. , Graphics Interchange Format (GIF), Joint Photographic Experts Group (JPEG), Bitmap etc

• WWW – Style The layout and format of an HTML document can be simplified by using CSS (Cascading Style Sheets) <html> <head> <style type="text/css"> body {background-color: yellow} h 1 {background-color: #00 ff 00} h 2 {background-color: transparent} p {background-color: rgb(250, 0, 255)} </style> </head> <body> <h 1>This is header 1</h 1> <h 2>This is header 2</h 2> <p>This is a paragraph</p> </body> </html>

l WWW – Caching Web pages l l Downloading HTML documents from servers can be slow due to a number of conditions: l Parts of the Internet can be congested l Dialup connection is typically very slow, 33 Kbps or 56 Kbps l Web server can have a lot of clients connecting to it at the same time, causing it to be overloaded. If a user returns to previous HTML document, then this could require downloading the document from the server again. A browser can hold copies of recently visited pages. This avoids having to download pages again. An organisation can use a HTTP proxy that caches documents for multiple users. Thus improving the speed at which pages can be displayed on each users computer.

The Global Internet l Search engines l l Started as simpler programs using keyword indexes Google improved indexing and created page ranking system l Mobile search: 20% of all searches in 2012 l Search engine marketing l l Major source of Internet advertising revenue Search engine optimization (SEO) l Adjusting Web site and traffic to improve rankings in search engine results

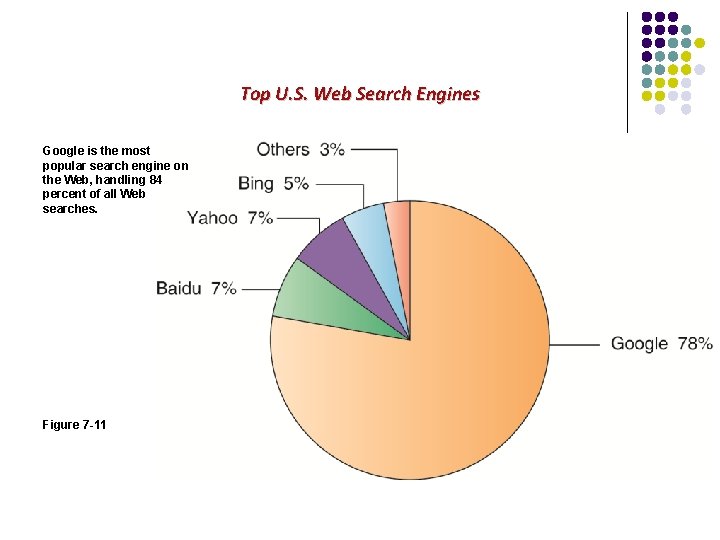
Top U. S. Web Search Engines Google is the most popular search engine on the Web, handling 84 percent of all Web searches. Figure 7 -11

RANKING l l Order a keyword term appears – keyword terms that appear sooner in the document’s listing or index tend to be ranked higher Frequency of keyword term – keywords that appear multiple times in a document’s index tend to be ranked higher

RANKING l l Occurrence of keyword in the title – keywords that appear in the document’s title, or perhaps metatag description or keyword description fields, can be given higher weight than terms only in the document body Rare, or less frequent, keywords – rare or unusual keywords that do not appear as frequently in the engine’s index database are often ranked more highly than common terms or keywords.

The Global Internet l Social search l l Semantic search l l Google +1, Facebook Like Anticipating what users are looking for rather than simply returning millions of links Intelligent agent shopping bots l Use intelligent agent software for searching Internet for shopping information

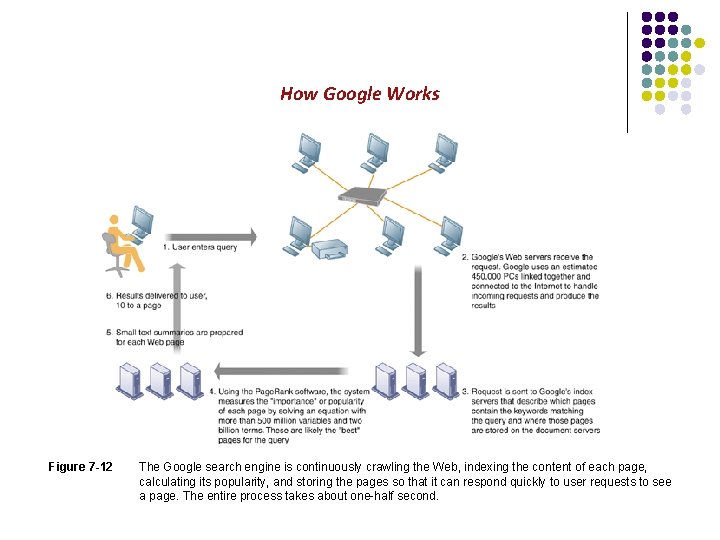
How Google Works Figure 7 -12 The Google search engine is continuously crawling the Web, indexing the content of each page, calculating its popularity, and storing the pages so that it can respond quickly to user requests to see a page. The entire process takes about one-half second.

The Global Internet l Web 2. 0 l l l Second-generation services Enabling collaboration, sharing information, and creating new services online Features l l Interactivity Real-time user control Social participation (sharing) User-generated content

The Global Internet l Web 2. 0 services and tools l Blogs: chronological, informal Web sites created by individuals § § § l l RSS (Really Simple Syndication): syndicates Web content so aggregator software can pull content for use in another setting or viewing later Blogosphere Microblogging Wikis: collaborative Web sites where visitors can add, delete, or modify content on the site Social networking sites: enable users to build communities of friends and share information

The Global Internet l Web 3. 0: The “Semantic Web” l l l A collaborative effort led by W 3 C to add layer of meaning to the existing Web Goal is to reduce human effort in searching for and processing information Making Web more “intelligent” and intuitive Increased communication and synchronization with computing devices, communities “Web of things” Increased cloud computing, mobile computing

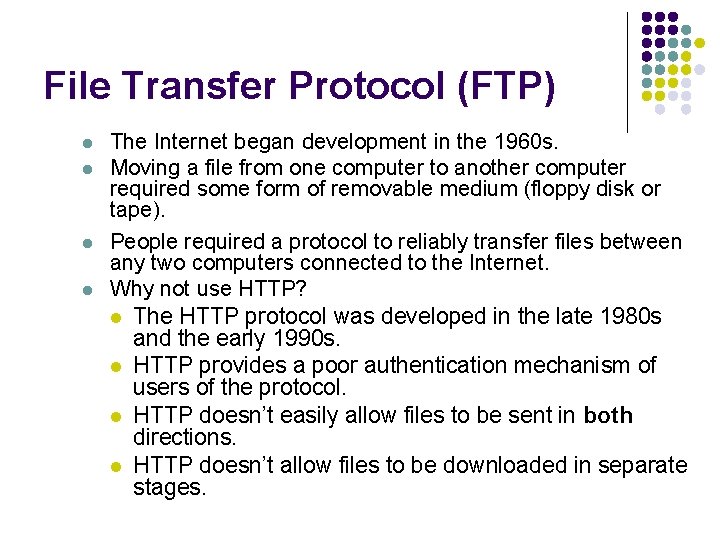
File Transfer Protocol (FTP) l l 53/64 The Internet began development in the 1960 s. Moving a file from one computer to another computer required some form of removable medium (floppy disk or tape). People required a protocol to reliably transfer files between any two computers connected to the Internet. Why not use HTTP? l The HTTP protocol was developed in the late 1980 s and the early 1990 s. l HTTP provides a poor authentication mechanism of users of the protocol. l HTTP doesn’t easily allow files to be sent in both directions. l HTTP doesn’t allow files to be downloaded in separate stages.

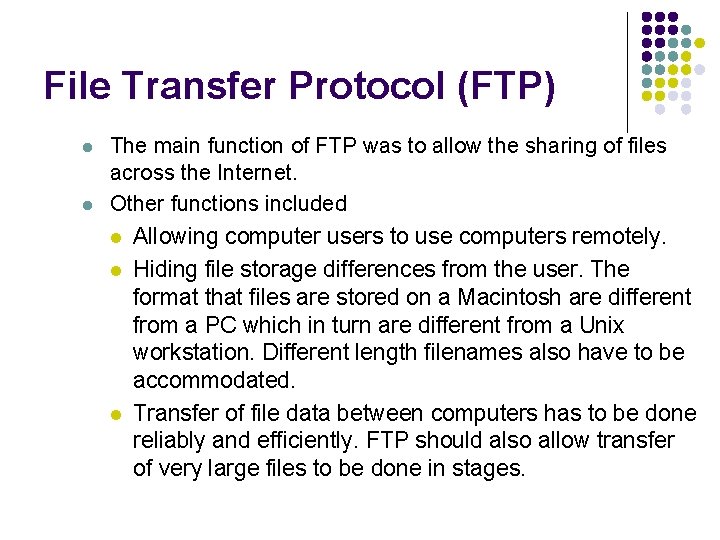
File Transfer Protocol (FTP) l l The main function of FTP was to allow the sharing of files across the Internet. Other functions included l Allowing computer users to use computers remotely. l l 53/64 Hiding file storage differences from the user. The format that files are stored on a Macintosh are different from a PC which in turn are different from a Unix workstation. Different length filenames also have to be accommodated. Transfer of file data between computers has to be done reliably and efficiently. FTP should also allow transfer of very large files to be done in stages.

l FTP l l l FTP is a client/server program An FTP client program enables the user to interact with an ftp server in order to access files on the ftp server computer. Client programs can be: l Simple command line interfaces. E. g. MS-Dos Prompt C: ftp. maths. tcd. ie l Integrated with Web browsers, e. g. Netscape Navigator, Internet Explorer. FTP provides similar services to those available on most filesystems: list directories, create new files, download files, delete files. FTP uses TCP connections and the default server port for FTP is 21.

l FTP - Transfer modes l Batch transfer l l l User creates list of files to be transferred by ftp program. Users request is dropped into a queue of similar requests. FTP program reads requests and performs transfers of files. Transfer program can retry until successful. Good for slow or unreliable transfers. Interactive transfer l l User starts ftp program User can interactively list contents of directories, transfer files, delete files etc. User can find and transfer files immediately Quick feedback in case of mistakes, e. g. , spelling errors

l FTP - Sample Commands l Command Description ftp maths. tcd. ie Open connection to computer ls List Directory contents cd Change to another directory bin Change to binary transfer, used for downloading executables. get Download a file from remote computer put Upload a file to the remote computer mget Start download of multiple files mput Start upload of multiple files

l FTP - Checkpointing l l A data transfer may be aborted after only transferring part of a file. l This could be due to the client or the server crashing, the TCP connection being broken due to congestion, phone hanging up during dial up connection. FTP allows the file transfer from where the transfer was stopped, no need to re-transfer part of file. FTP achieves this by sending restart markers between the server and the client. Restart markers are saved in a restart file by the client. Client sends restart marker when it wants to continue the transfer of a previously stopped transfer.

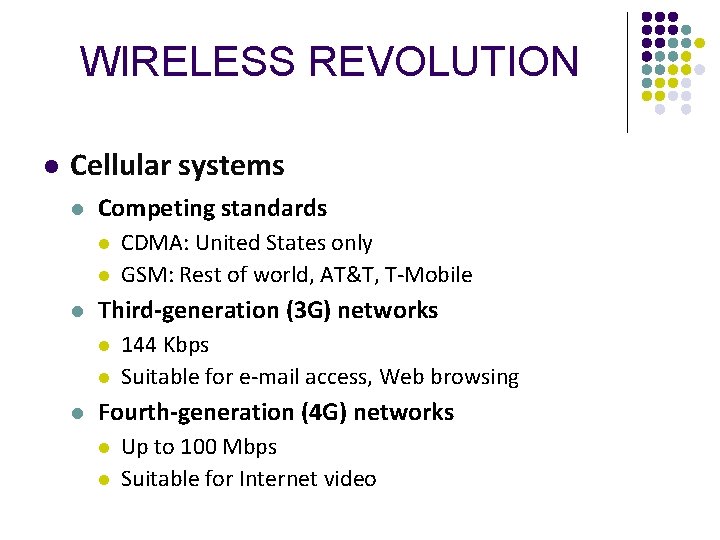
WIRELESS REVOLUTION l Cellular systems l Competing standards l l l Third-generation (3 G) networks l l l CDMA: United States only GSM: Rest of world, AT&T, T-Mobile 144 Kbps Suitable for e-mail access, Web browsing Fourth-generation (4 G) networks l l Up to 100 Mbps Suitable for Internet video

WIRELESS REVOLUTION l Wireless computer networks and Internet access l Bluetooth (802. 15) l l l Links up to 8 devices in 10 -m area using low-power, radio-based communication Useful for personal networking (PANs) Wi-Fi (802. 11) l l l Set of standards: 802. 11 Used for wireless LAN and wireless Internet access Use access points: device with radio receiver/transmitter for connecting wireless devices to a wired LAN

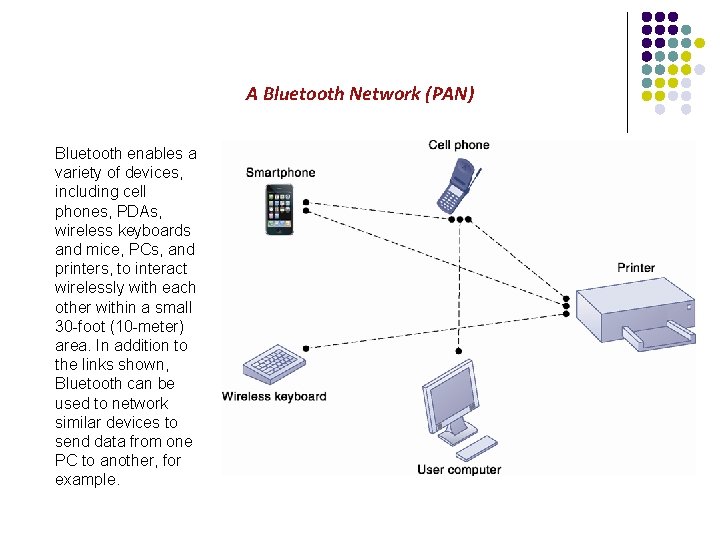
A Bluetooth Network (PAN) Bluetooth enables a variety of devices, including cell phones, PDAs, wireless keyboards and mice, PCs, and printers, to interact wirelessly with each other within a small 30 -foot (10 -meter) area. In addition to the links shown, Bluetooth can be used to network similar devices to send data from one PC to another, for example.

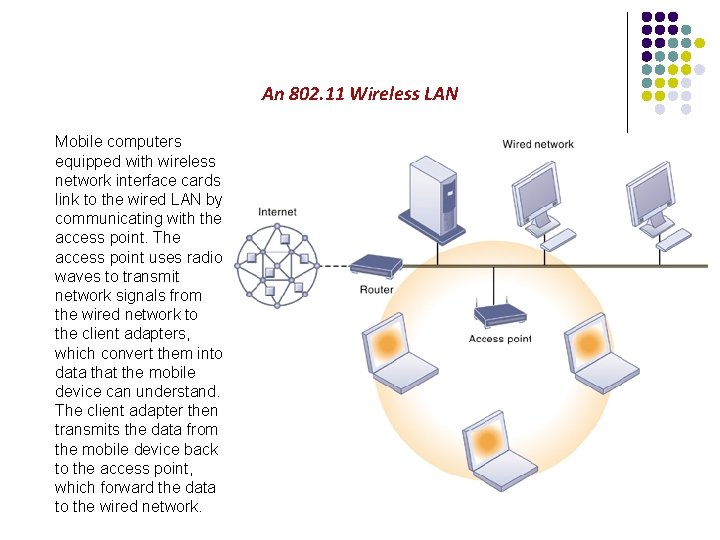
An 802. 11 Wireless LAN Mobile computers equipped with wireless network interface cards link to the wired LAN by communicating with the access point. The access point uses radio waves to transmit network signals from the wired network to the client adapters, which convert them into data that the mobile device can understand. The client adapter then transmits the data from the mobile device back to the access point, which forward the data to the wired network.

WIRELESS REVOLUTION l Wireless computer networks and Internet access l Wi-Fi (cont. ) l l l Hotspots: one or more access points in public place to provide maximum wireless coverage for a specific area Weak security features Wi. Max (802. 16) l l Wireless access range of 31 miles Require Wi. Max antennas

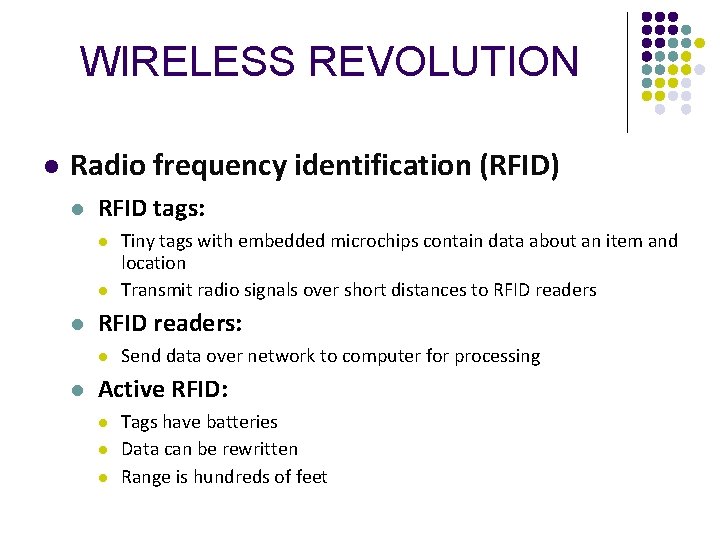
WIRELESS REVOLUTION l Radio frequency identification (RFID) l RFID tags: l l l RFID readers: l l Tiny tags with embedded microchips contain data about an item and location Transmit radio signals over short distances to RFID readers Send data over network to computer for processing Active RFID: l l l Tags have batteries Data can be rewritten Range is hundreds of feet

WIRELESS REVOLUTION l RFID (cont. ) l Passive RFID: l l Common uses: l l Range is shorter Smaller, less expensive Powered by radio frequency energy Automated toll-collection Tracking goods in a supply chain Requires companies to have special hardware and software Reduction in cost of tags making RFID viable for many firms

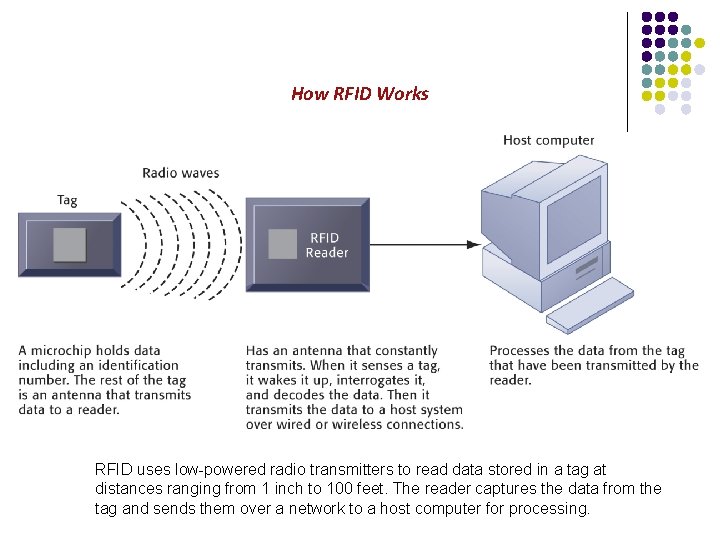
How RFID Works RFID uses low-powered radio transmitters to read data stored in a tag at distances ranging from 1 inch to 100 feet. The reader captures the data from the tag and sends them over a network to a host computer for processing.

WIRELESS REVOLUTION l Wireless sensor networks (WSNs) l l Networks of hundreds or thousands of interconnected wireless devices embedded into physical environment to provide measurements of many points over large spaces Used to monitor building security, detect hazardous substances in air, monitor environmental changes, traffic, or military activity Devices have built-in processing, storage, and radio frequency sensors and antennas Require low-power, long-lasting batteries and ability to endure in the field without maintenance

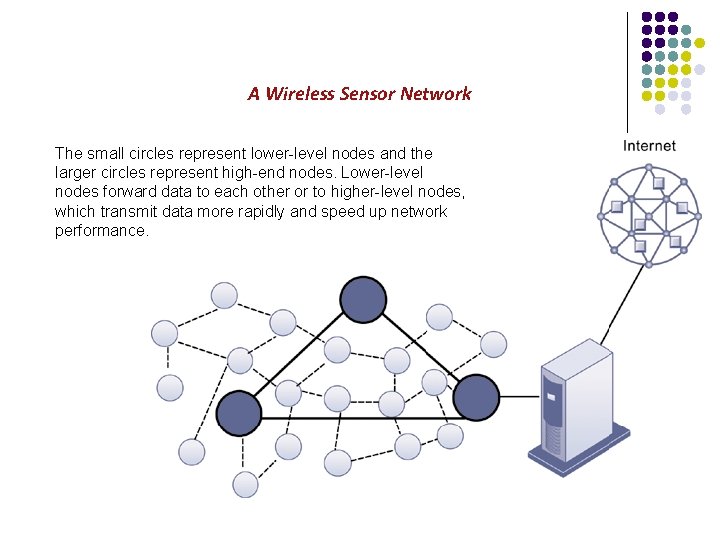
A Wireless Sensor Network The small circles represent lower-level nodes and the larger circles represent high-end nodes. Lower-level nodes forward data to each other or to higher-level nodes, which transmit data more rapidly and speed up network performance.

GLOBAL INTERNET l Voice over IP (Vo. IP) l l Digital voice communication using IP, packet switching Providers § § l Unified communications l l Cable providers Google, Skype Communications systems that integrate voice, data, email, conferencing Virtual private network (VPN) l Secure, encrypted, private network run over Internet § § PPTP Tunneling

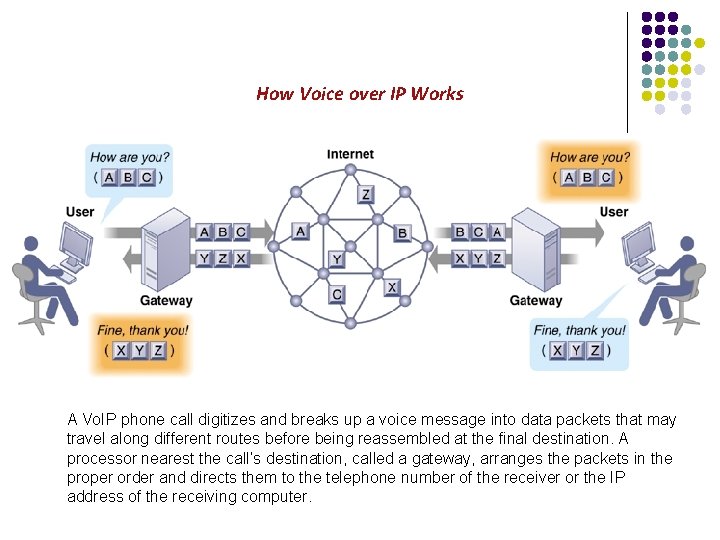
How Voice over IP Works A Vo. IP phone call digitizes and breaks up a voice message into data packets that may travel along different routes before being reassembled at the final destination. A processor nearest the call’s destination, called a gateway, arranges the packets in the proper order and directs them to the telephone number of the receiver or the IP address of the receiving computer.

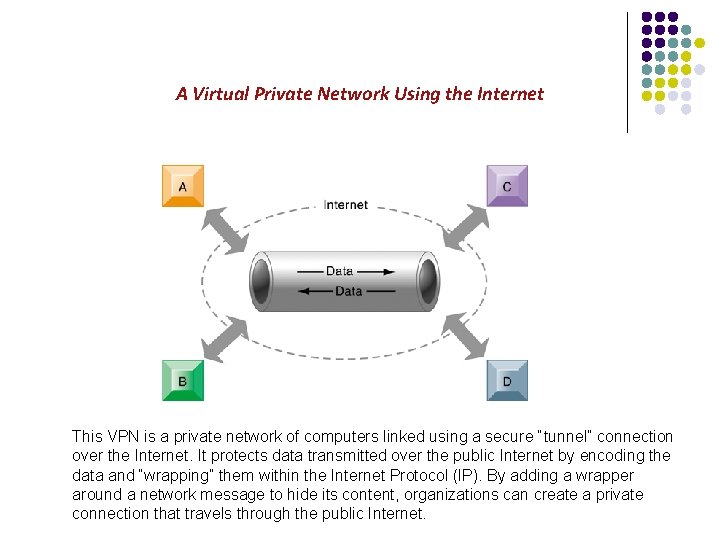
A Virtual Private Network Using the Internet This VPN is a private network of computers linked using a secure “tunnel” connection over the Internet. It protects data transmitted over the public Internet by encoding the data and “wrapping” them within the Internet Protocol (IP). By adding a wrapper around a network message to hide its content, organizations can create a private connection that travels through the public Internet.