Dray Tek Corp V 3300 Vigor Access Vigor






















- Slides: 137

Dray. Tek Corp. V 3300 Vigor. Access Vigor. CMS/View Confidential

Vigor 3300 series Confidential

Topic n n n n Load Balance Qo. S High Availability Firewall / URL Filtering DMZ VPN Vo. IP 3 Confidential

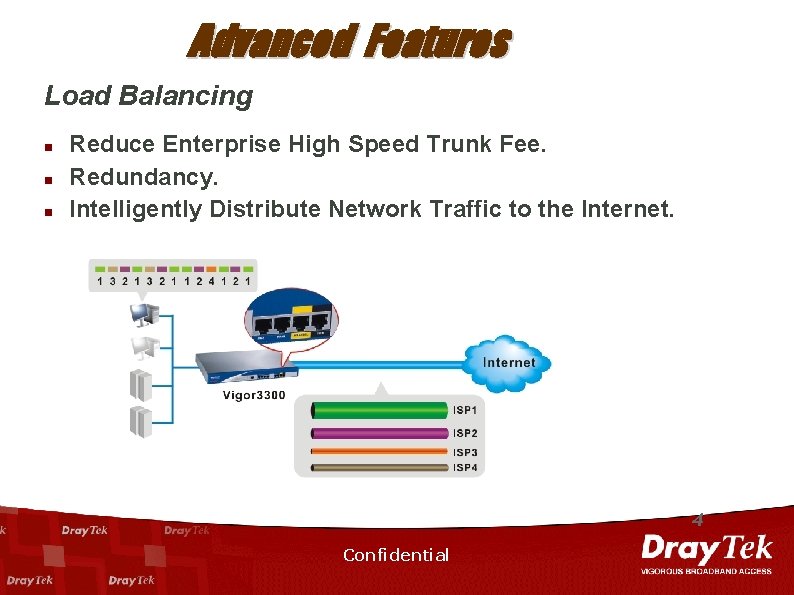
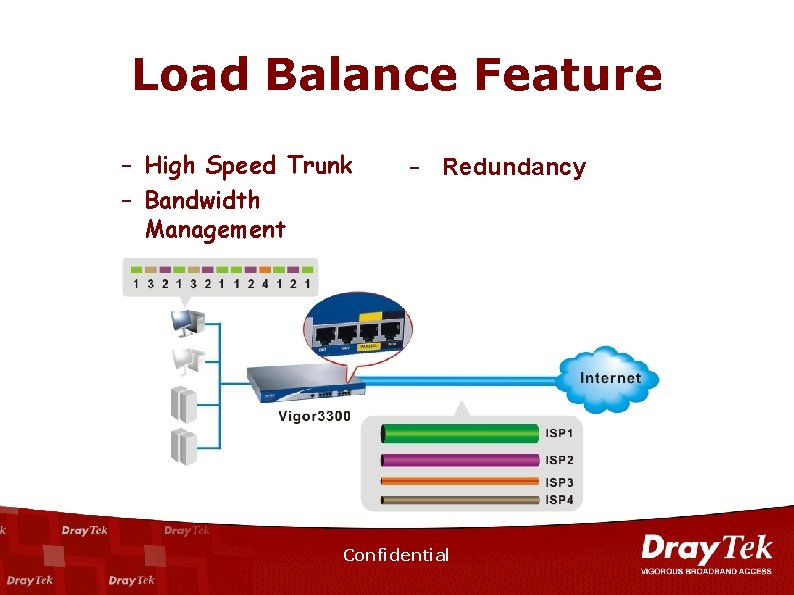
Advanced Features Load Balancing n n n Reduce Enterprise High Speed Trunk Fee. Redundancy. Intelligently Distribute Network Traffic to the Internet. 4 Confidential

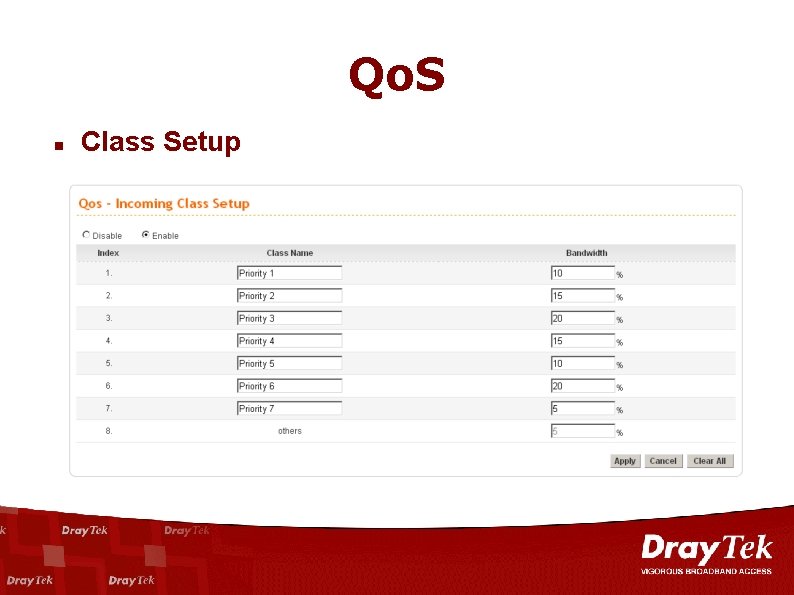
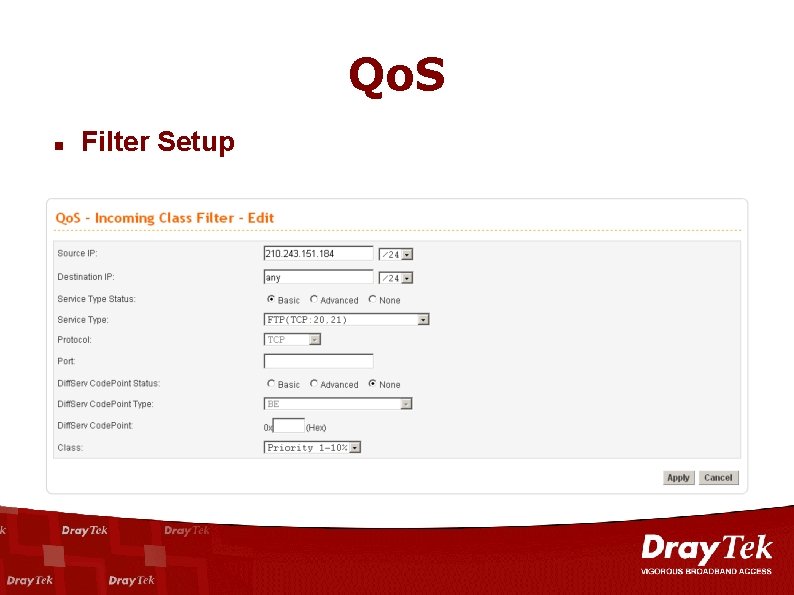
Advanced Features Qo. S (Quality of Service) n n Allows the Network Administrator to Monitor, Analyze, and Allocate Bandwidth for Various Types of Network Traffic in Real Time and/or for Business-Critical Traffic. Benefit of Vigor Qo. S – 8 Priority Queue. – Bandwidth Reservation. – Management by IP Address, Application, Service. Oriented and Diff. Serv-codepoint. 5 Confidential

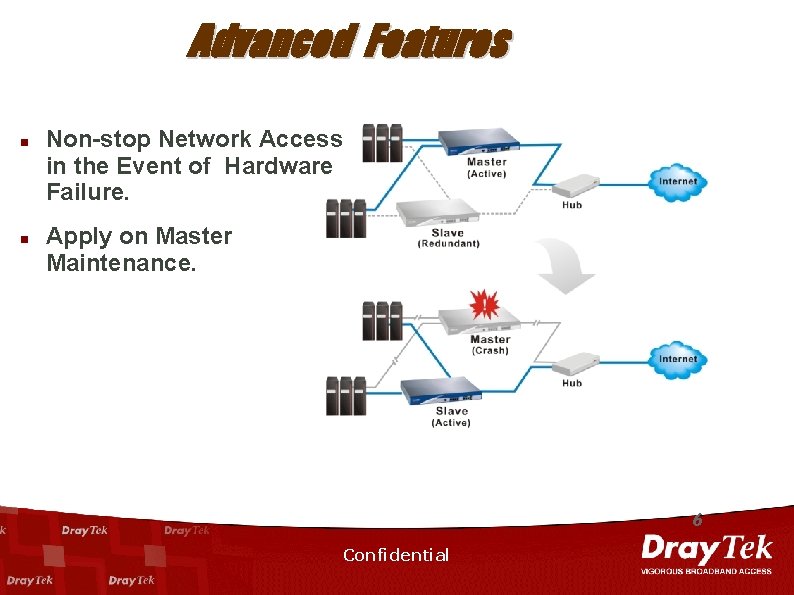
Advanced Features n n Non-stop Network Access in the Event of Hardware Failure. Apply on Master Maintenance. 6 Confidential

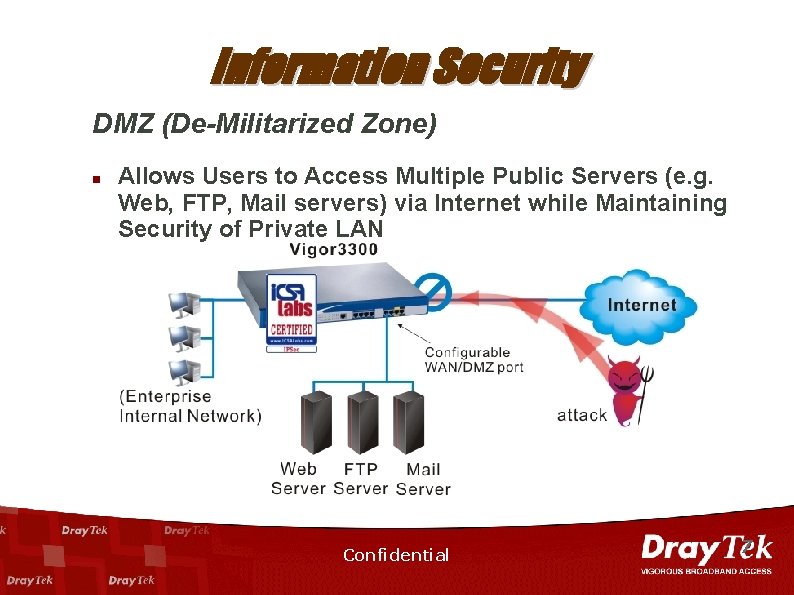
Information Security DMZ (De-Militarized Zone) n Allows Users to Access Multiple Public Servers (e. g. Web, FTP, Mail servers) via Internet while Maintaining Security of Private LAN Confidential 7

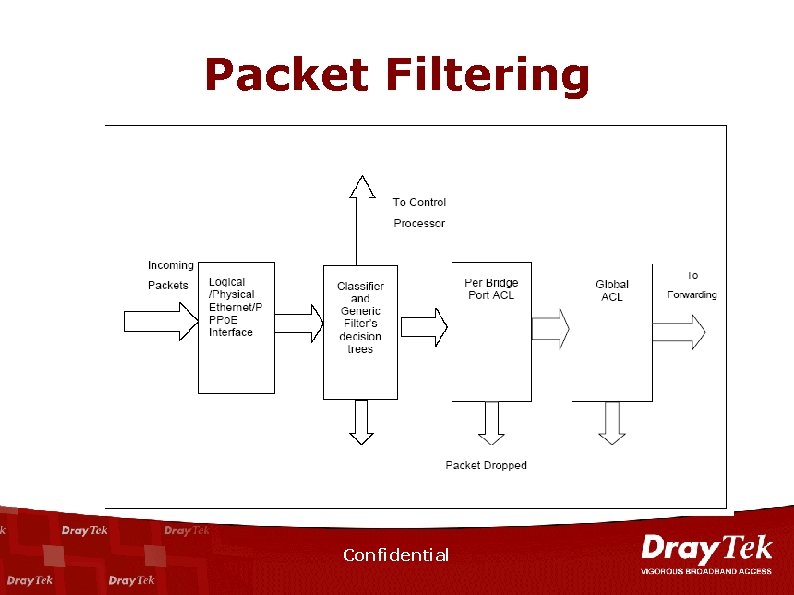
Information Security Firewall n n Protect the Trusted Network from Various Types Attacks that Explore Protocol Security Holes. Benefit of Vigor Firewall – IP-based Packet Filtering. – URL Filtering. – Denial of Service (Dos) Prevention. Confidential 8

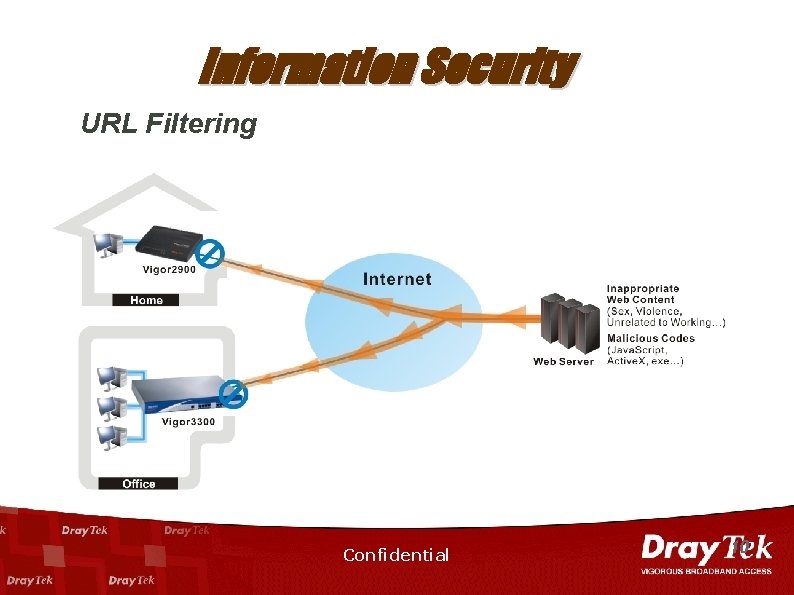
Information Security URL Filtering n n Inappropriate content blocking. – Improve Staff Working Efficiency. – Protect Children from Unhealthy Information. Benefit of Vigor Content Filtering – Malicious Code Prevention. (Java, Active. X, Cookie, exe, zip, . . . etc. ) – Filtering based on Access List, Keywords, or Time of Day. Confidential 9

Information Security URL Filtering Confidential 10

Information Security n Benefit of Vigor VPN – Supports 200 IPSec Tunnels. – Hardware-based accelerator of DES/3 DES, AES/HMAC-SHA-1/HMAC-MD 5 Encryption. – IPSec, PPTP, L 2 TP over IPSec. – 30 Mbps throughput in AES/3 DES. – Preshared key and Certificate Authority (X. 509 v 3) Authentication. – DHCP over IPsec – RADIUS client support. 11 Confidential

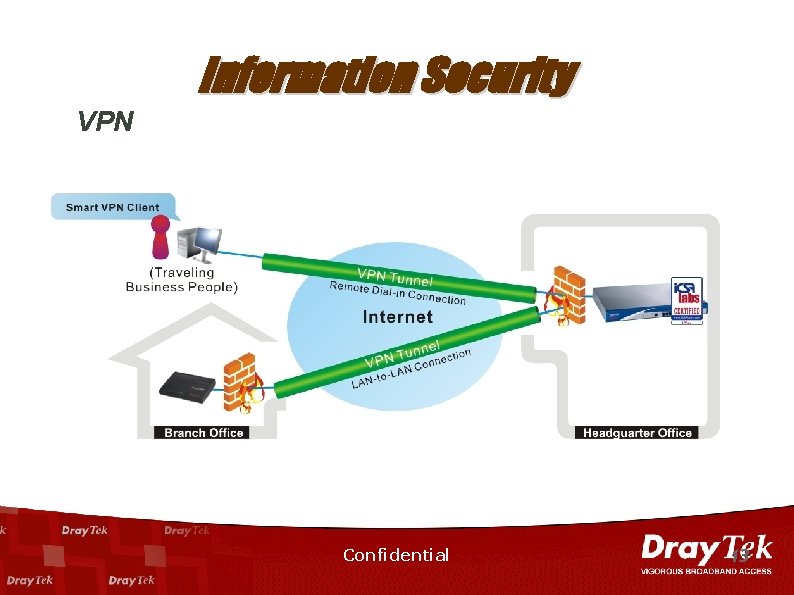
Information Security VPN - Dray. Tek VPN Solution n n LAN-to-LAN VPN connection (Gateway-to-Gateway) Made by two Routers to Connect two Portions of Private Networks. The Vigor router support IPSec tunnel protocols. Remote Dial-in VPN connection (Host-to-Gateway) Made by a remote access client, or a single user computer, that connects to a private network. In this type of connection, the Vigor router support IPSec tunnel for DHCP over IPsec protocols. Confidential 12

Information Security VPN Confidential 13

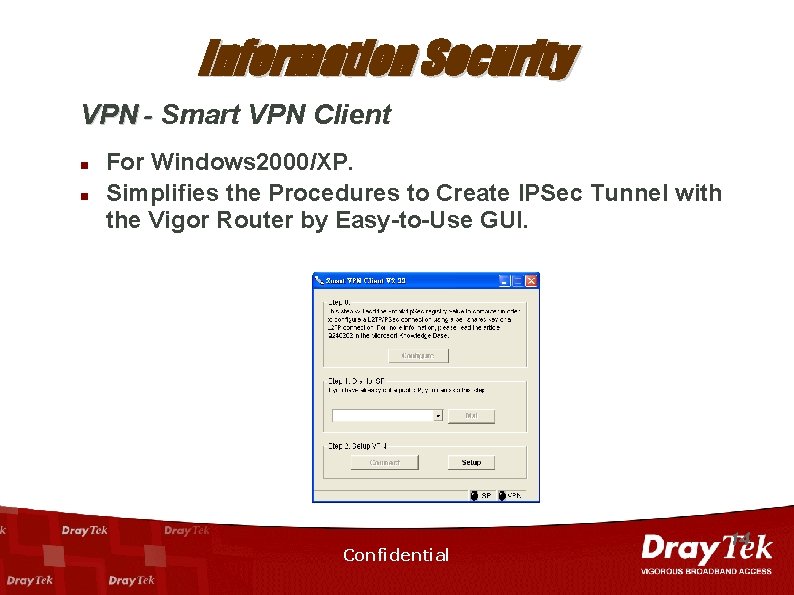
Information Security VPN - Smart VPN Client n n For Windows 2000/XP. Simplifies the Procedures to Create IPSec Tunnel with the Vigor Router by Easy-to-Use GUI. Confidential 14

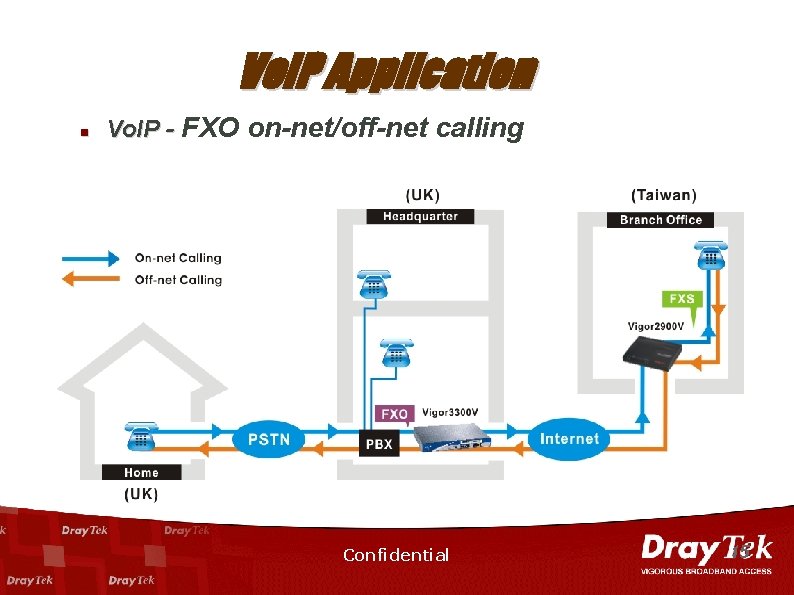
Vo. IP Application n Vo. IP - FXO on-net/off-net calling Confidential 15

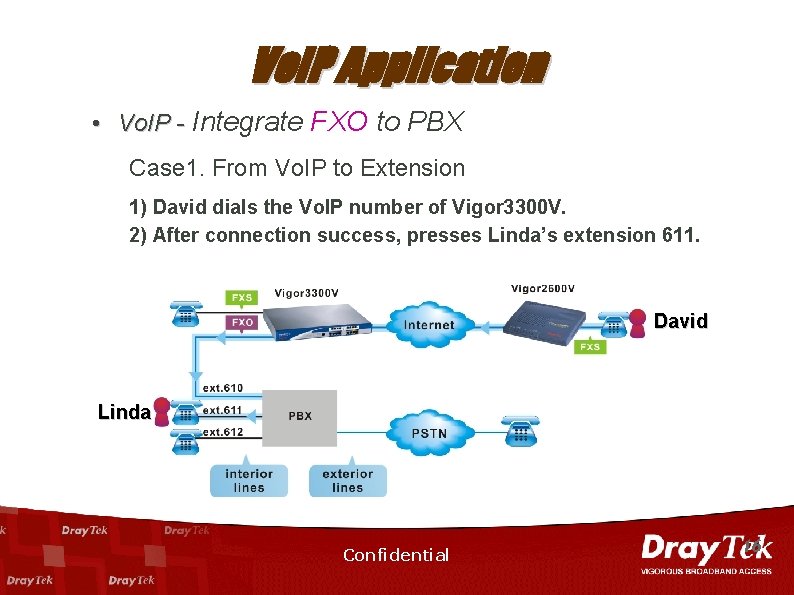
Vo. IP Application • Vo. IP - Integrate FXO to PBX Case 1. From Vo. IP to Extension 1) David dials the Vo. IP number of Vigor 3300 V. 2) After connection success, presses Linda’s extension 611. David Linda Confidential 16

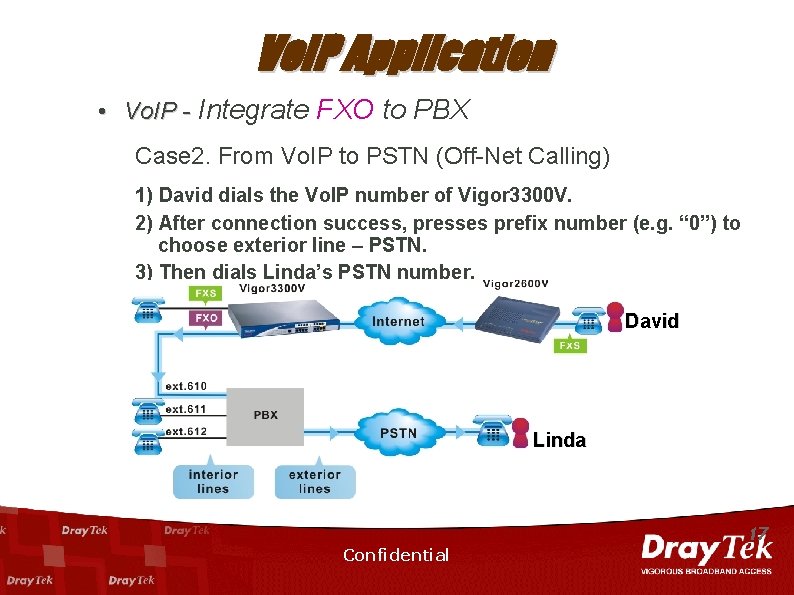
Vo. IP Application • Vo. IP - Integrate FXO to PBX Case 2. From Vo. IP to PSTN (Off-Net Calling) 1) David dials the Vo. IP number of Vigor 3300 V. 2) After connection success, presses prefix number (e. g. “ 0”) to choose exterior line – PSTN. 3) Then dials Linda’s PSTN number. David Linda 17 Confidential

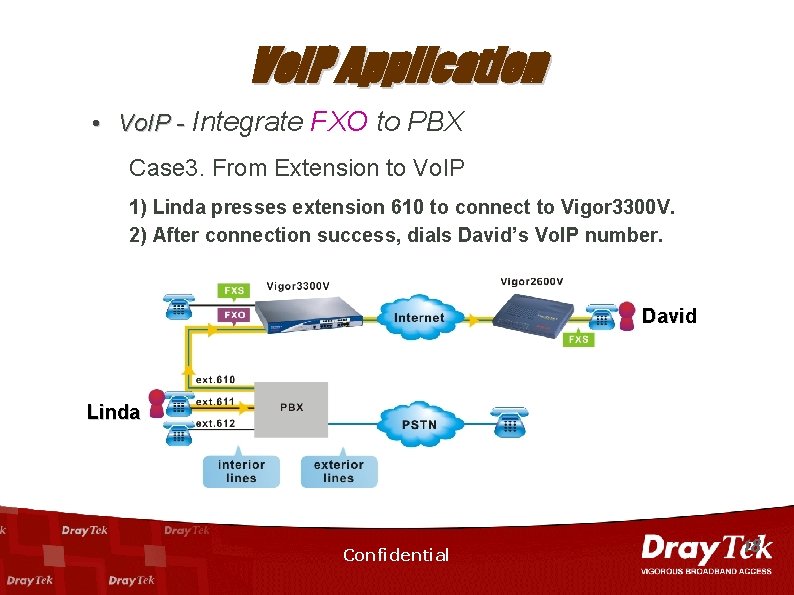
Vo. IP Application • Vo. IP - Integrate FXO to PBX Case 3. From Extension to Vo. IP 1) Linda presses extension 610 to connect to Vigor 3300 V. 2) After connection success, dials David’s Vo. IP number. David Linda Confidential 18

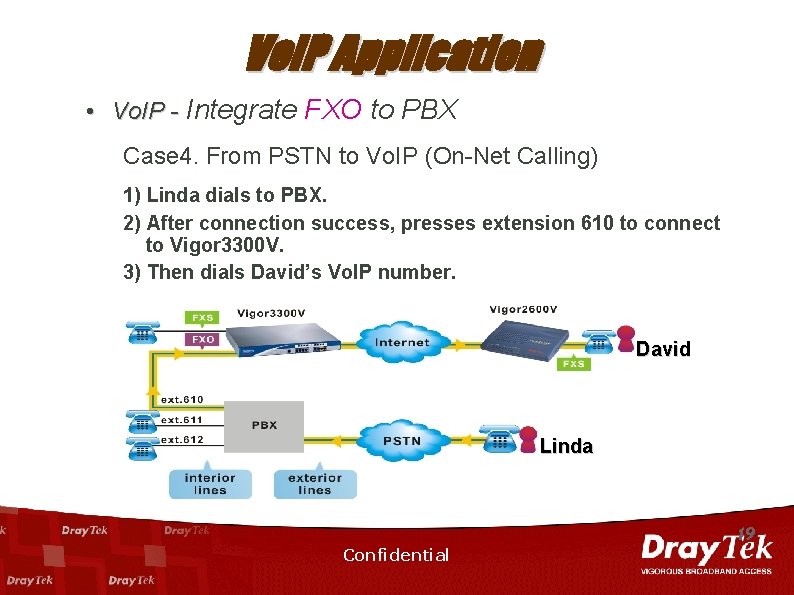
Vo. IP Application • Vo. IP - Integrate FXO to PBX Case 4. From PSTN to Vo. IP (On-Net Calling) 1) Linda dials to PBX. 2) After connection success, presses extension 610 to connect to Vigor 3300 V. 3) Then dials David’s Vo. IP number. David Linda 19 Confidential

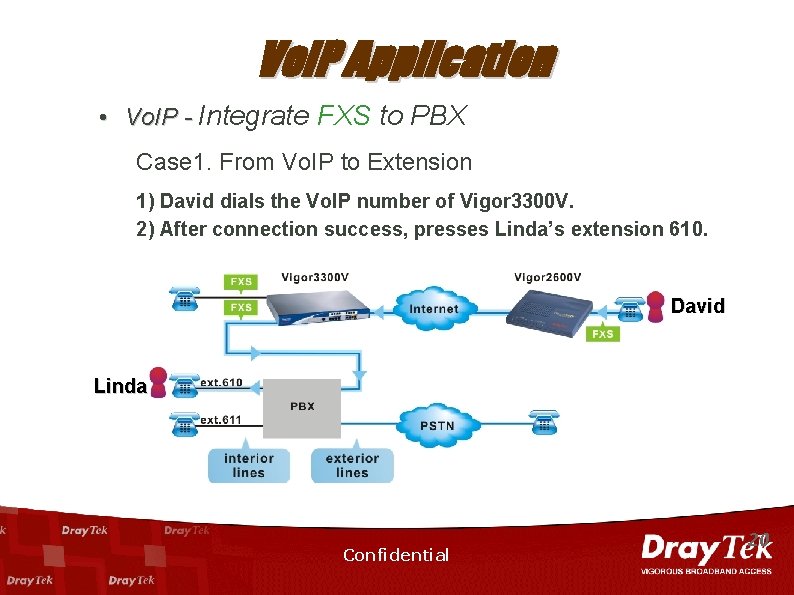
Vo. IP Application • Vo. IP - Integrate FXS to PBX Case 1. From Vo. IP to Extension 1) David dials the Vo. IP number of Vigor 3300 V. 2) After connection success, presses Linda’s extension 610. David Linda Confidential 20

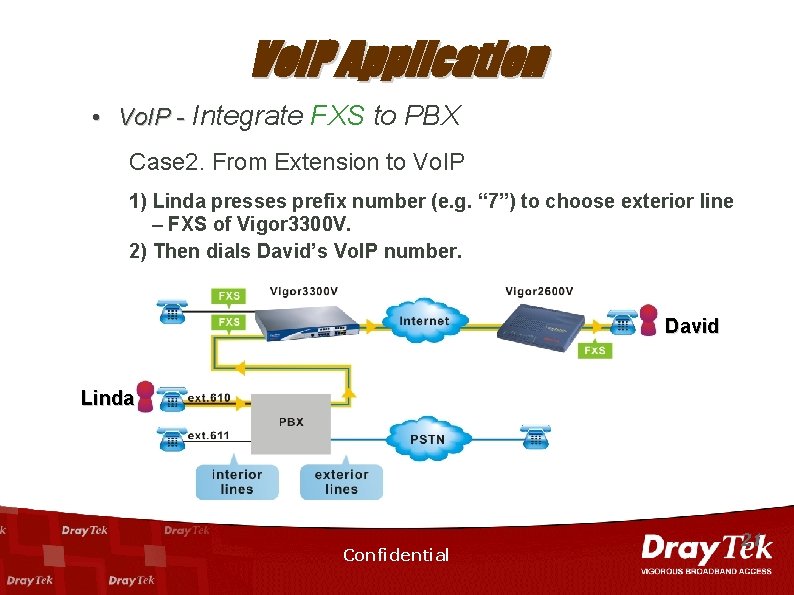
Vo. IP Application • Vo. IP - Integrate FXS to PBX Case 2. From Extension to Vo. IP 1) Linda presses prefix number (e. g. “ 7”) to choose exterior line – FXS of Vigor 3300 V. 2) Then dials David’s Vo. IP number. David Linda Confidential 21

Vigor 3300 V Series Enterprise Multiservice Security Vo. IP Router Technical Training

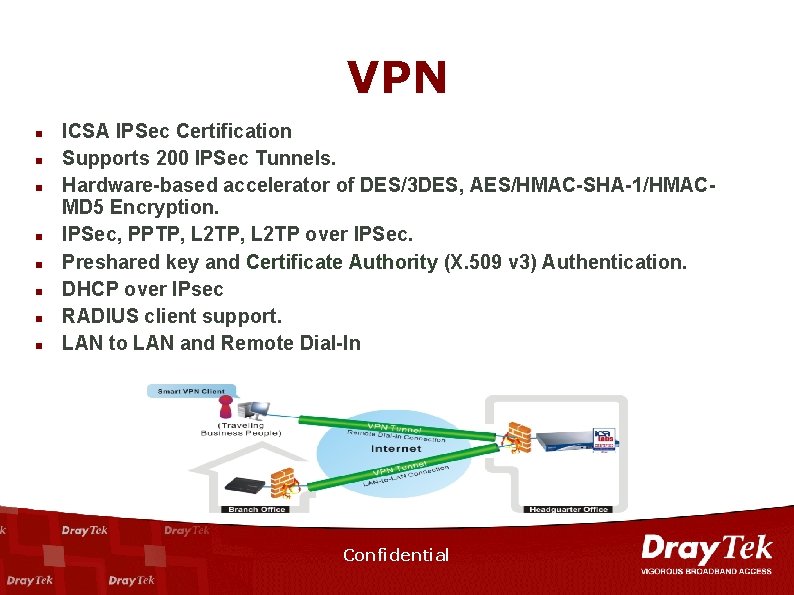
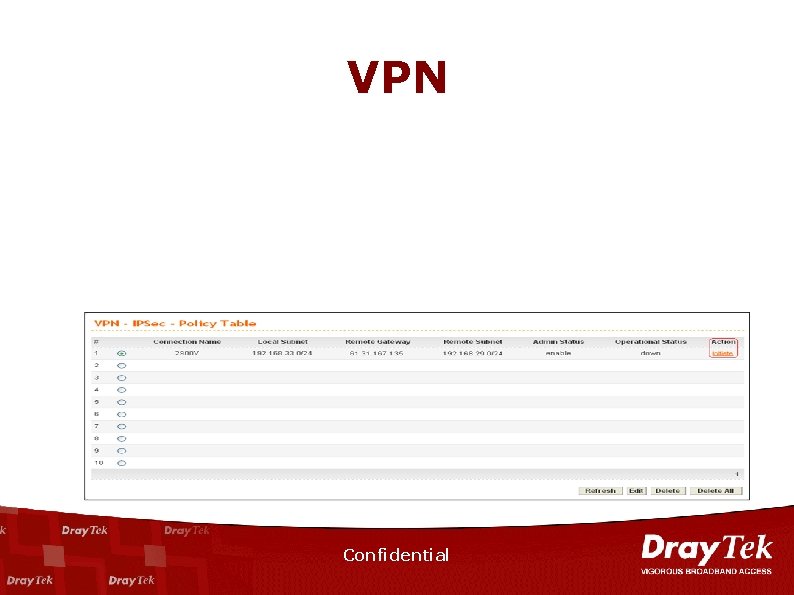
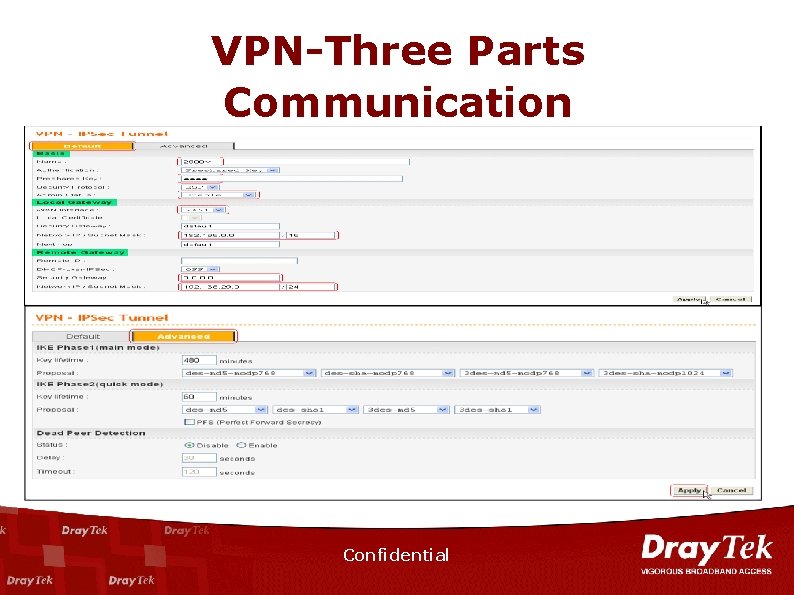
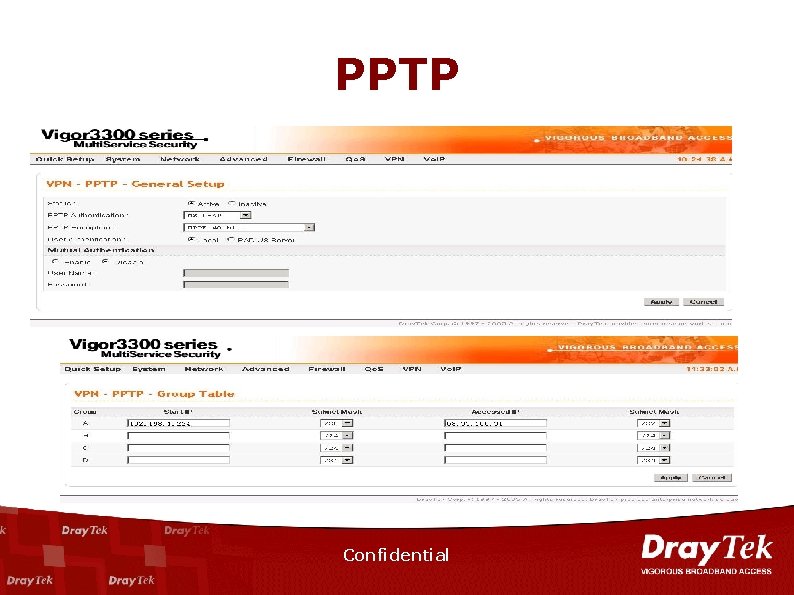
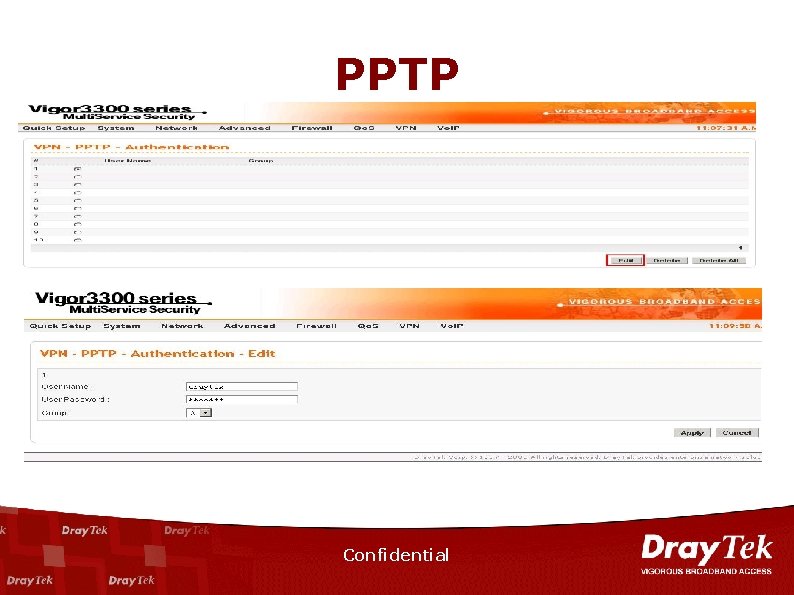
VPN n n n n ICSA IPSec Certification Supports 200 IPSec Tunnels. Hardware-based accelerator of DES/3 DES, AES/HMAC-SHA-1/HMACMD 5 Encryption. IPSec, PPTP, L 2 TP over IPSec. Preshared key and Certificate Authority (X. 509 v 3) Authentication. DHCP over IPsec RADIUS client support. LAN to LAN and Remote Dial-In Confidential

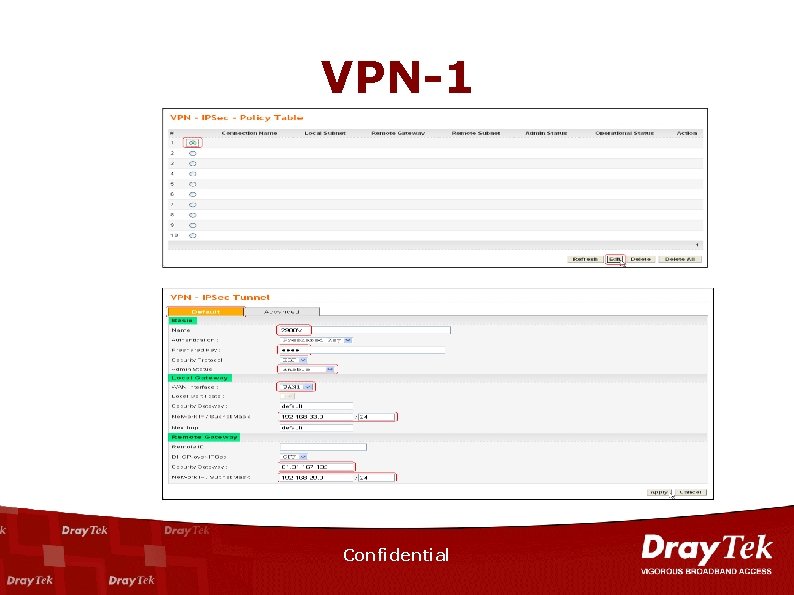
VPN-1 Confidential

VPN Confidential

VPN-Three Parts Communication Confidential

PPTP Confidential

PPTP Confidential

Topic n 4 x WAN n – Load Balance – Redundancy n n – IPSec, PKI(X. 509), CA – PPTP Firewall – IP Filter – Do. S – Content Filtering Qo. S VPN n Vo. IP – FXS/FXO n Advanced – High Availability Confidential

Load Balance Feature – High Speed Trunk – Bandwidth Management – Redundancy Confidential

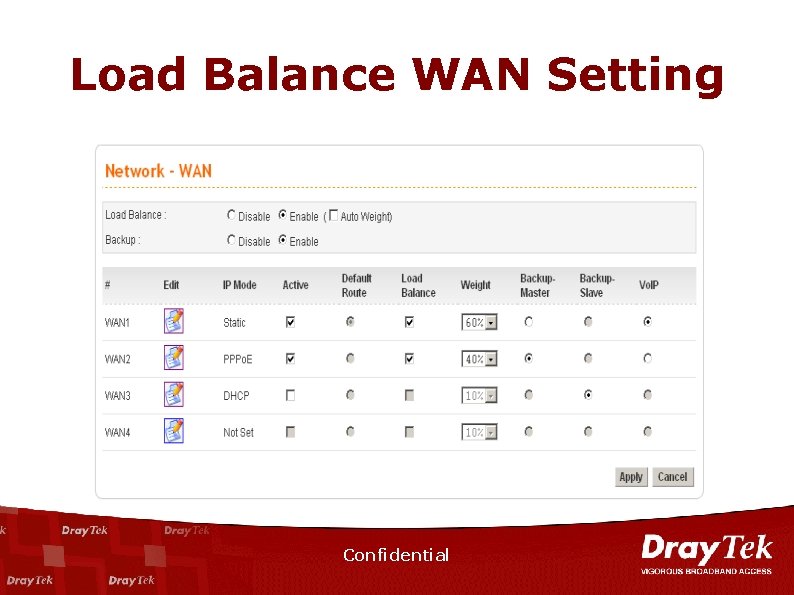
Load Balance WAN Setting Confidential

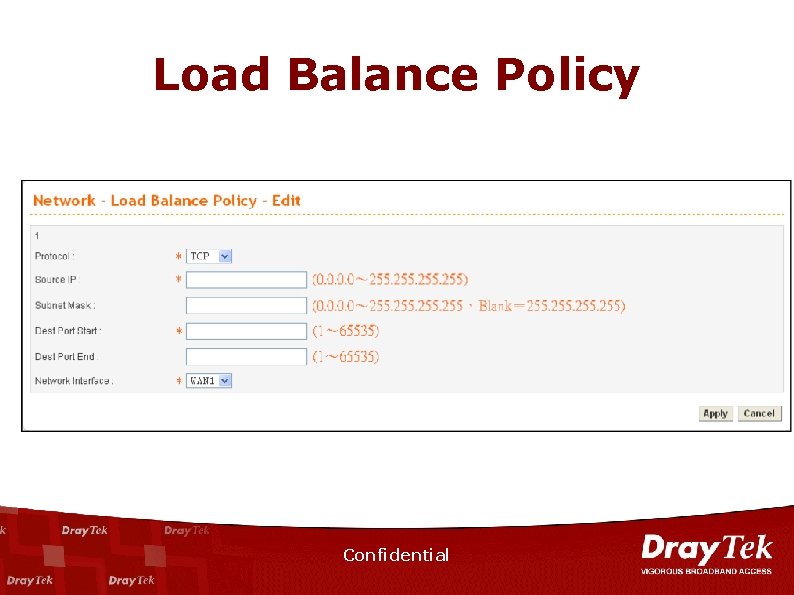
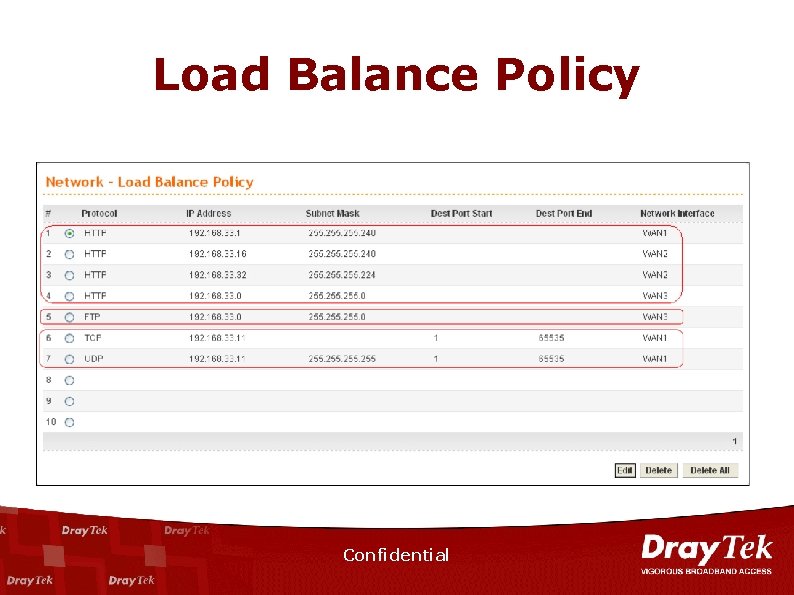
Load Balance Policy Confidential

Load Balance Policy Confidential

Firewall n n n IP Based Packet Filtering Do. S Prevention URL Filter – Various Access Control – Malicious Code Prevention – Filter Schedule Confidential

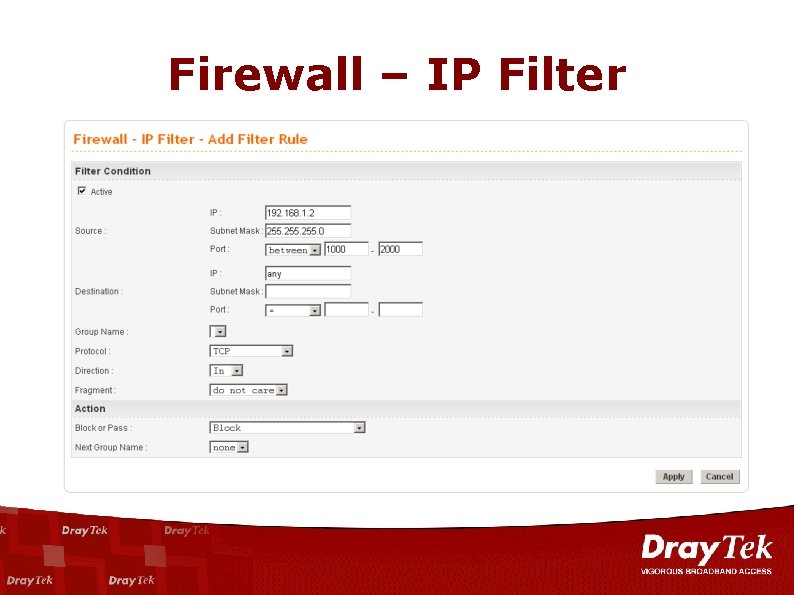
Firewall – IP Filter

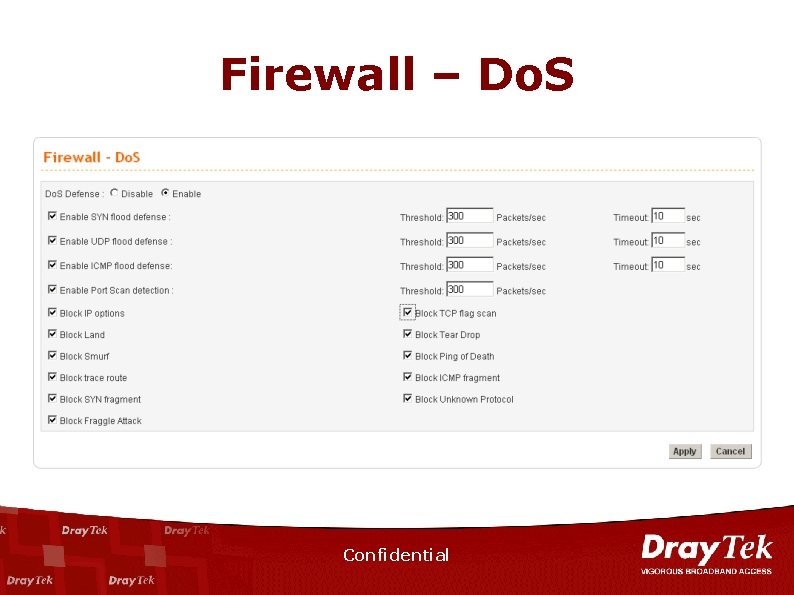
Firewall – Do. S Confidential

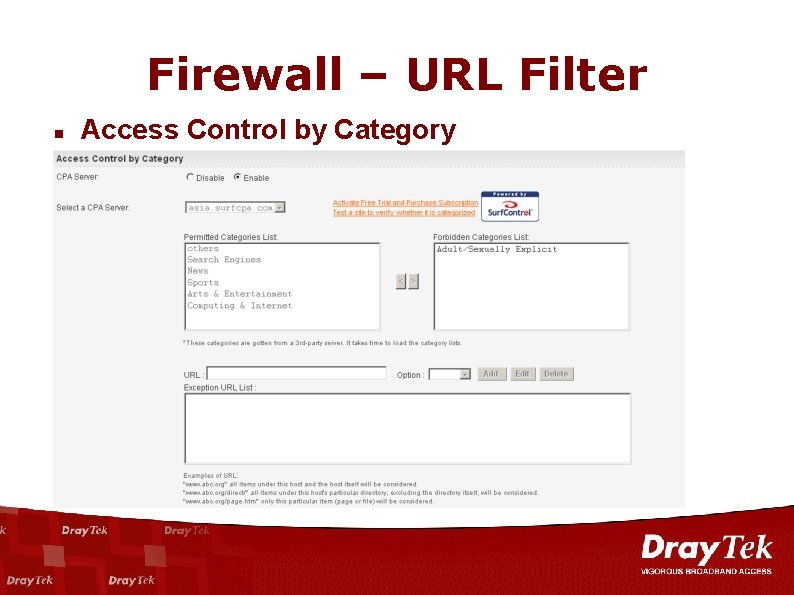
Firewall – URL Filter n Access Control by Category

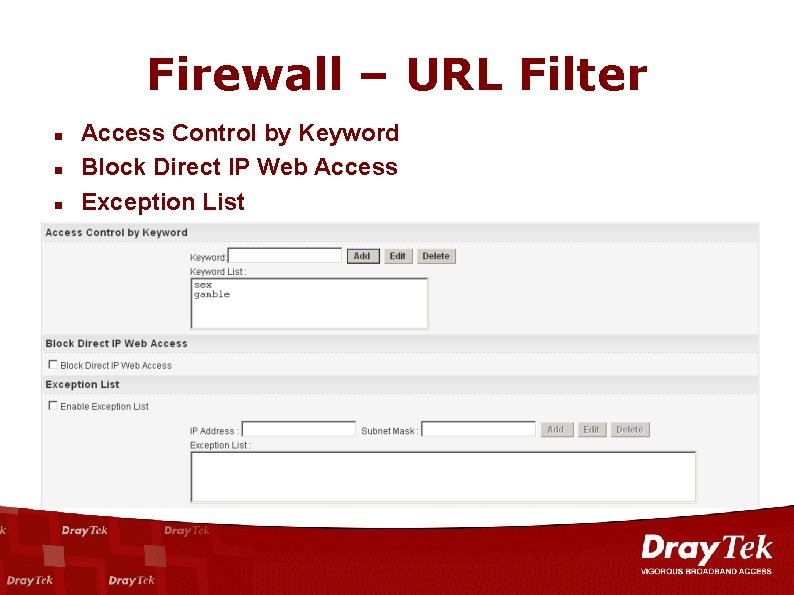
Firewall – URL Filter n n n Access Control by Keyword Block Direct IP Web Access Exception List

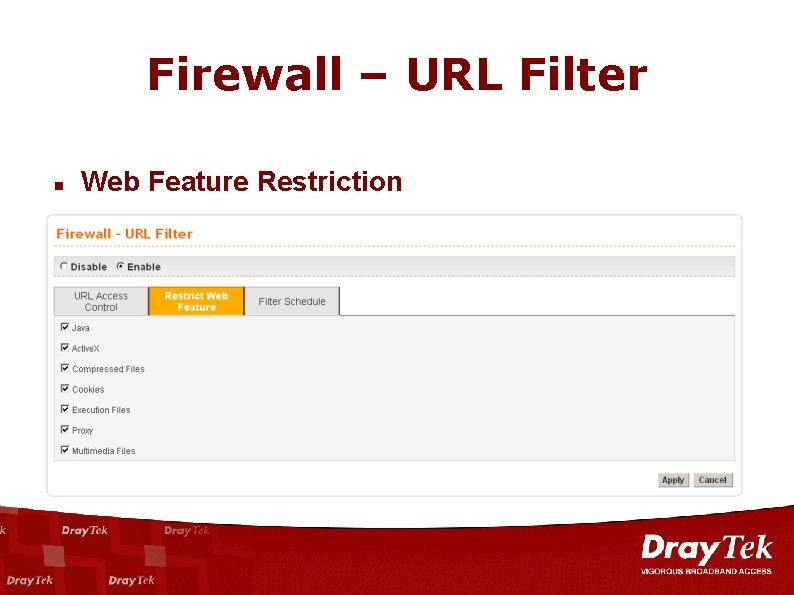
Firewall – URL Filter n Web Feature Restriction

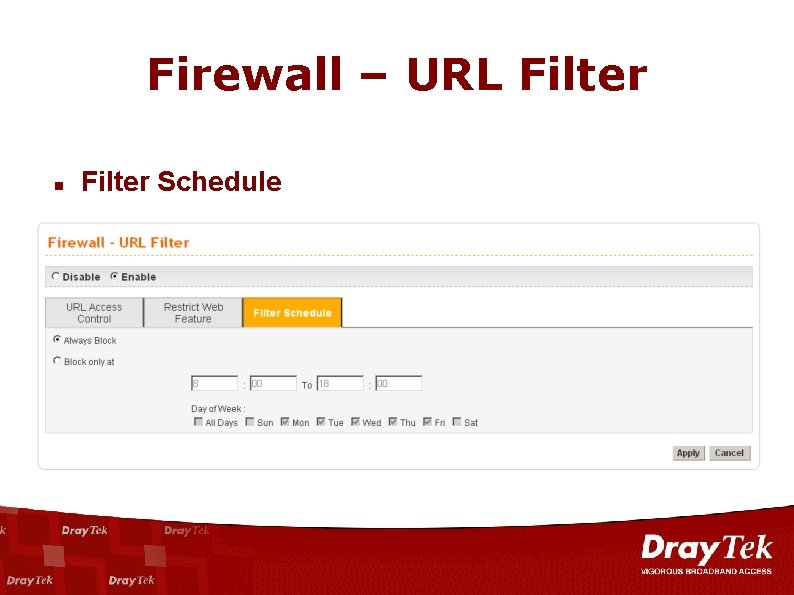
Firewall – URL Filter n Filter Schedule

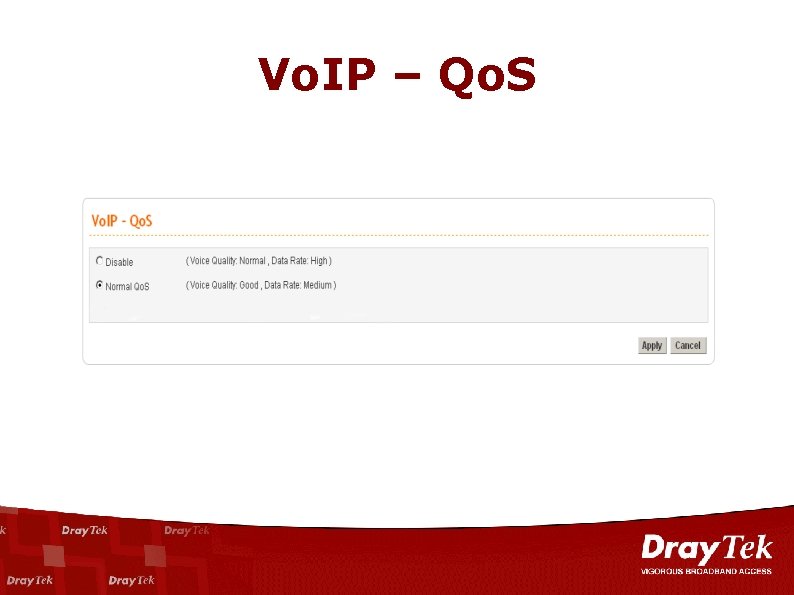
Qo. S n For Both Incoming & Outgoing – 8 Priority (Class). – Bandwidth Reservation. – Managed by IP Address, Application, Service. Oriented and Diff. Serv-codepoint.

Qo. S n Class Setup

Qo. S n Filter Setup

Vo. IP n n n n n FXS/FXO SIP/MGCP Per Port Settings Group Tone Settings Qo. S NAT Traversal Incoming Call Barring Call History Advance Speed Dail

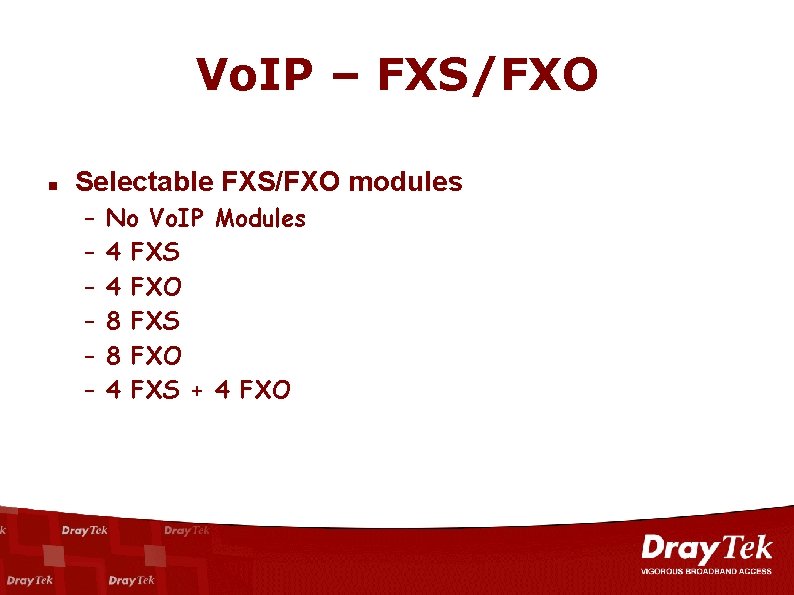
Vo. IP – FXS/FXO n Selectable FXS/FXO modules – – – No Vo. IP Modules 4 FXS 4 FXO 8 FXS 8 FXO 4 FXS + 4 FXO

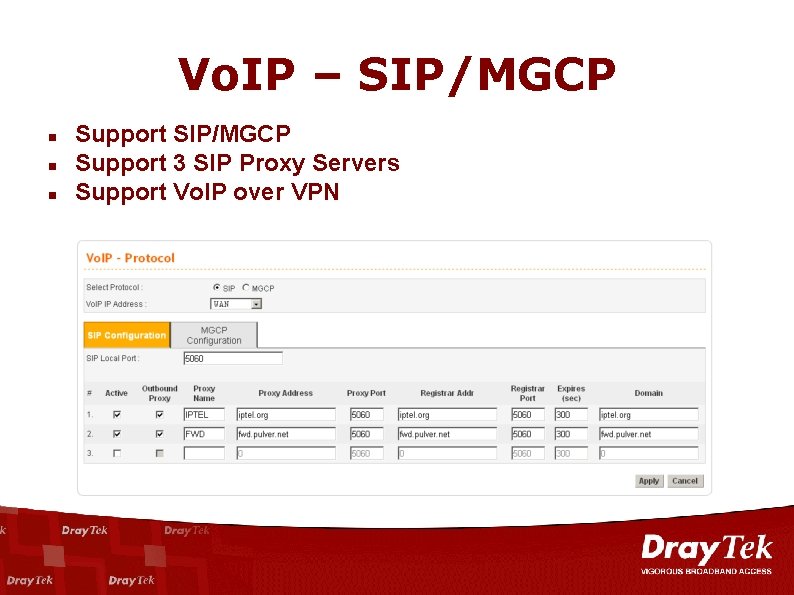
Vo. IP – SIP/MGCP n n n Support SIP/MGCP Support 3 SIP Proxy Servers Support Vo. IP over VPN

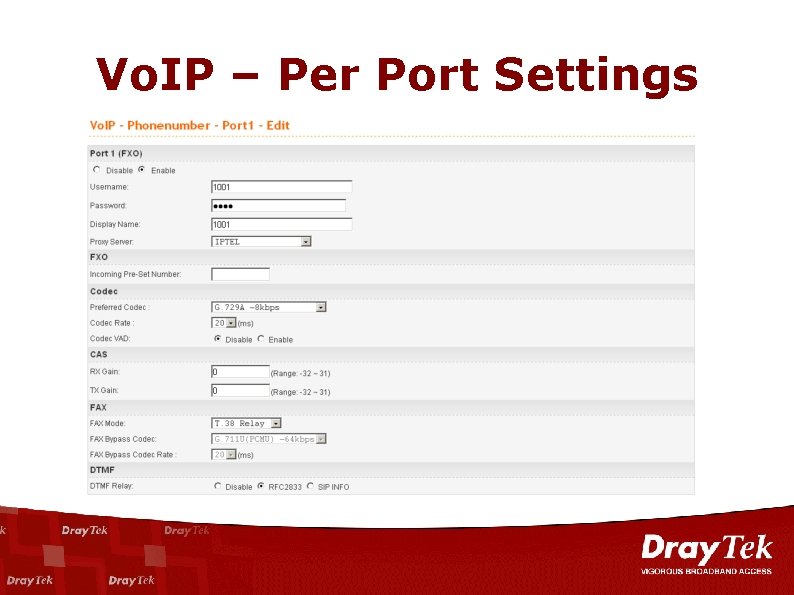
Vo. IP – Per Port Settings

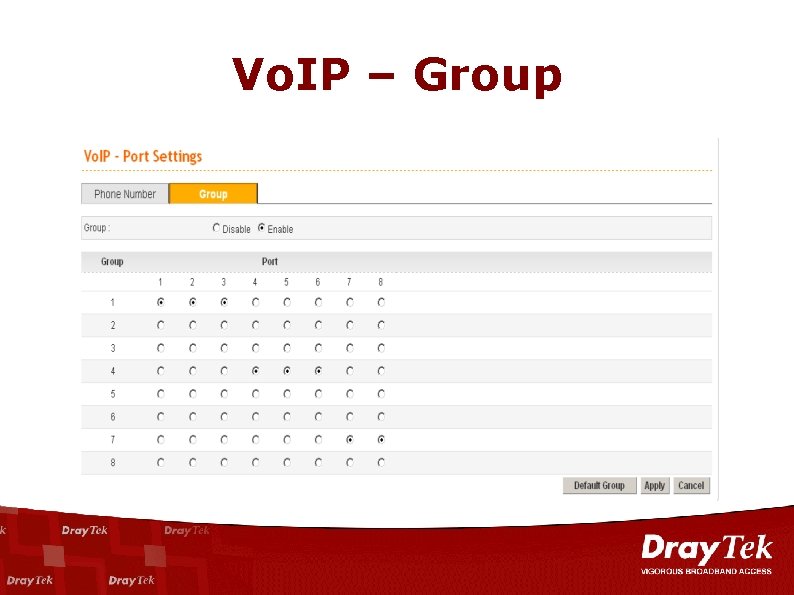
Vo. IP – Group

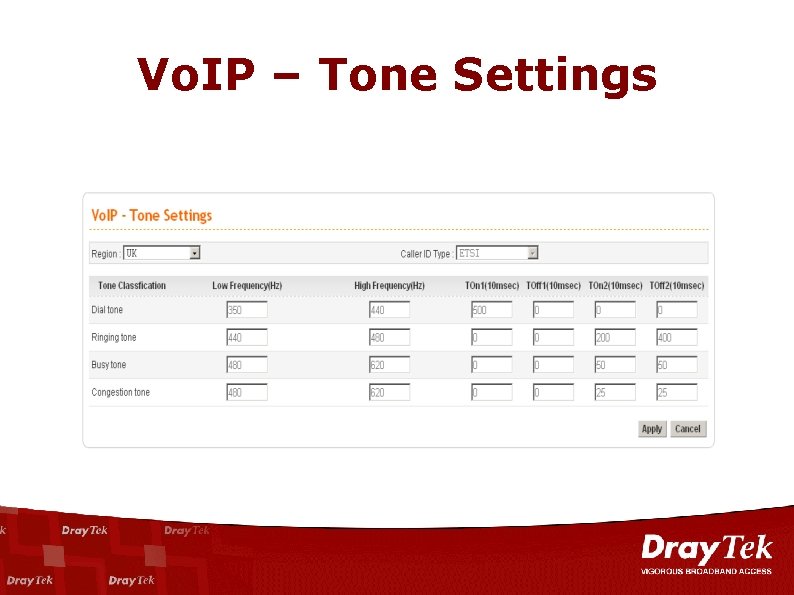
Vo. IP – Tone Settings

Vo. IP – Qo. S

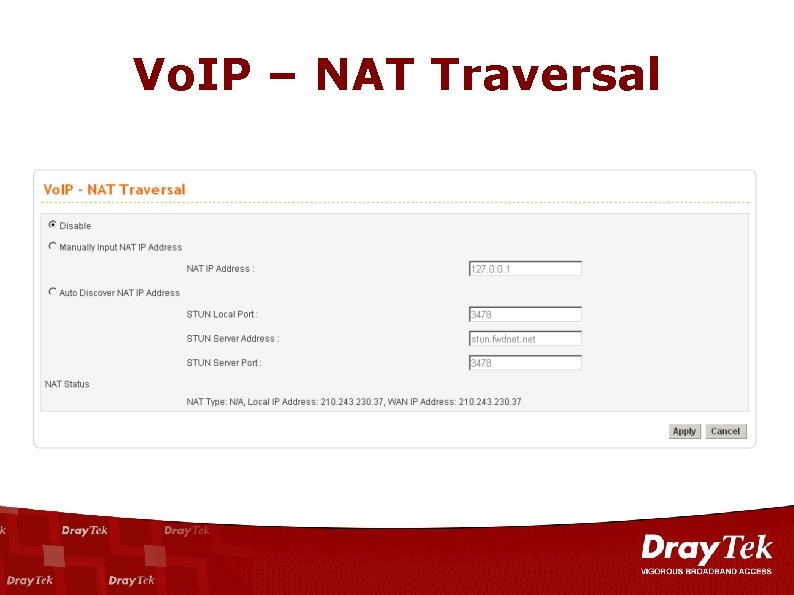
Vo. IP – NAT Traversal

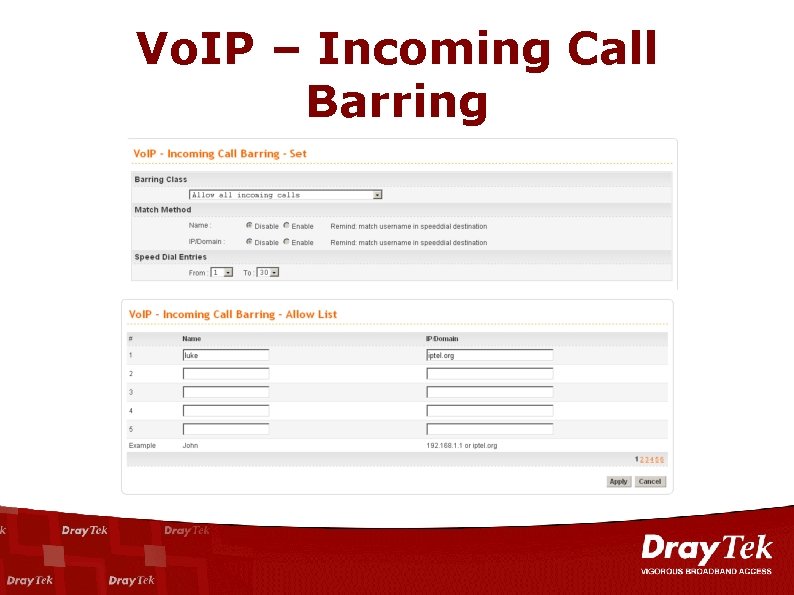
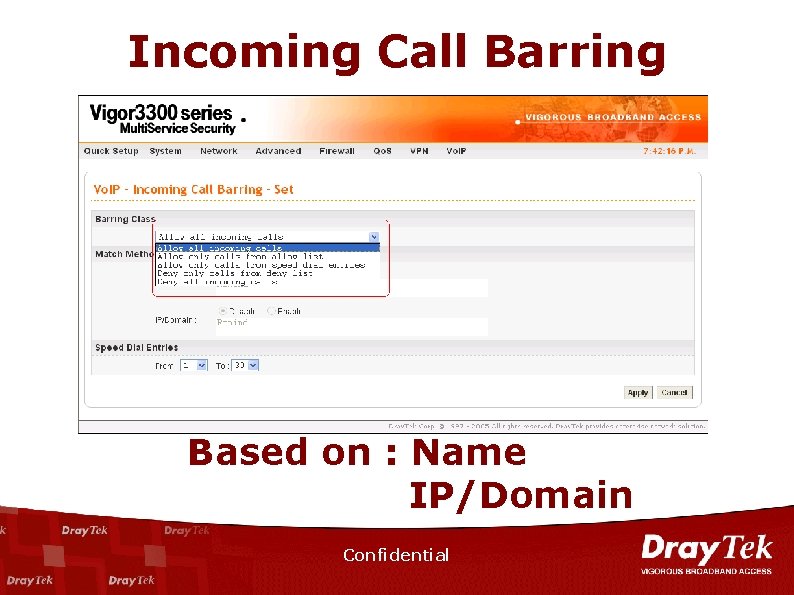
Vo. IP – Incoming Call Barring

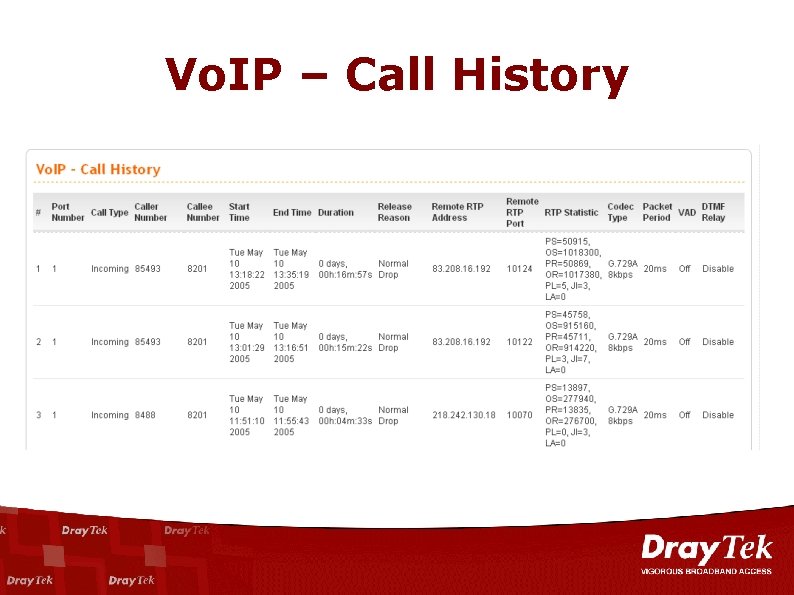
Vo. IP – Call History

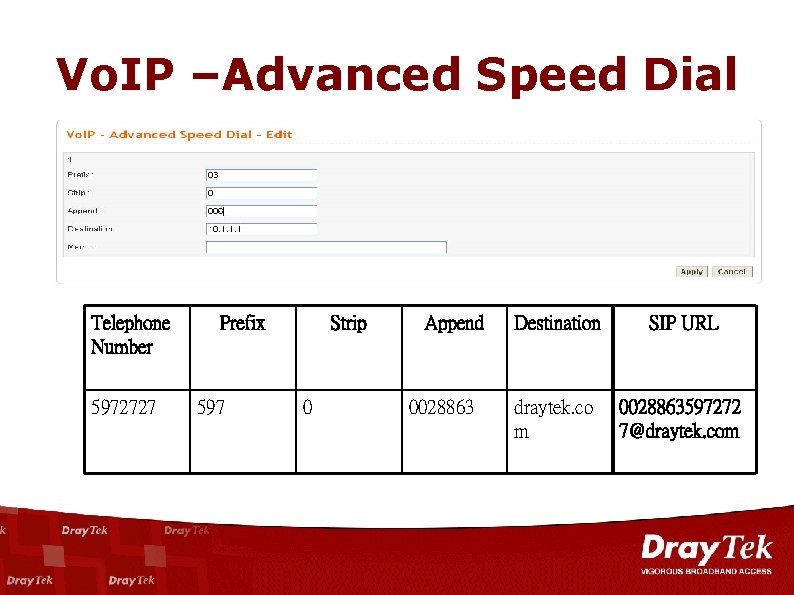
Vo. IP –Advanced Speed Dial Telephone Number 5972727 Prefix 597 Strip 0 Append 0028863 Destination SIP URL draytek. co m 0028863597272 7@draytek. com

SIP Call, Proxy, Outbound Proxy and Domain Confidential

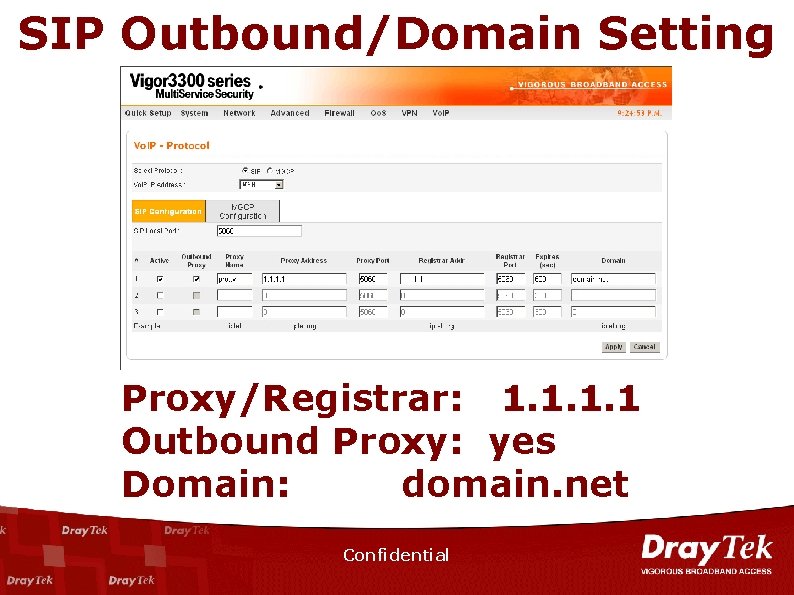
SIP Outbound/Domain Setting Proxy/Registrar: 1. 1 Outbound Proxy: yes Domain: domain. net Confidential

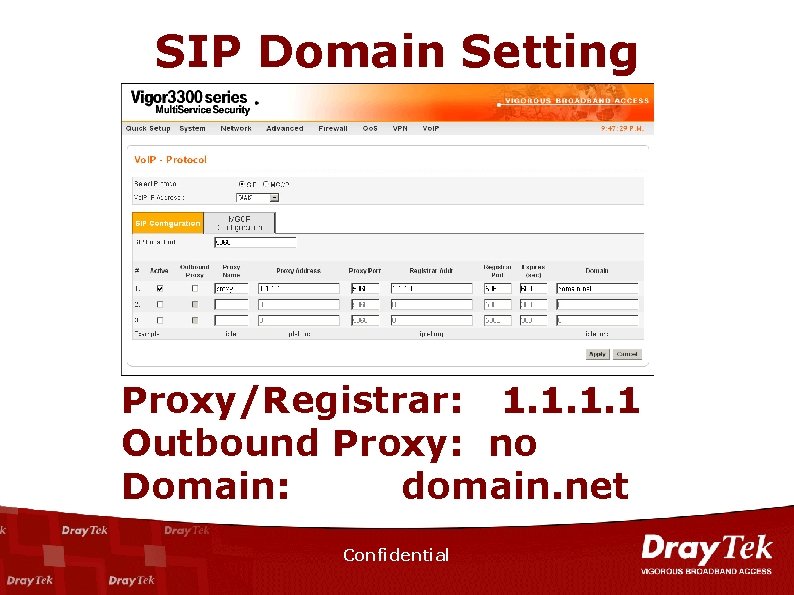
SIP Domain Setting Proxy/Registrar: 1. 1 Outbound Proxy: no Domain: domain. net Confidential

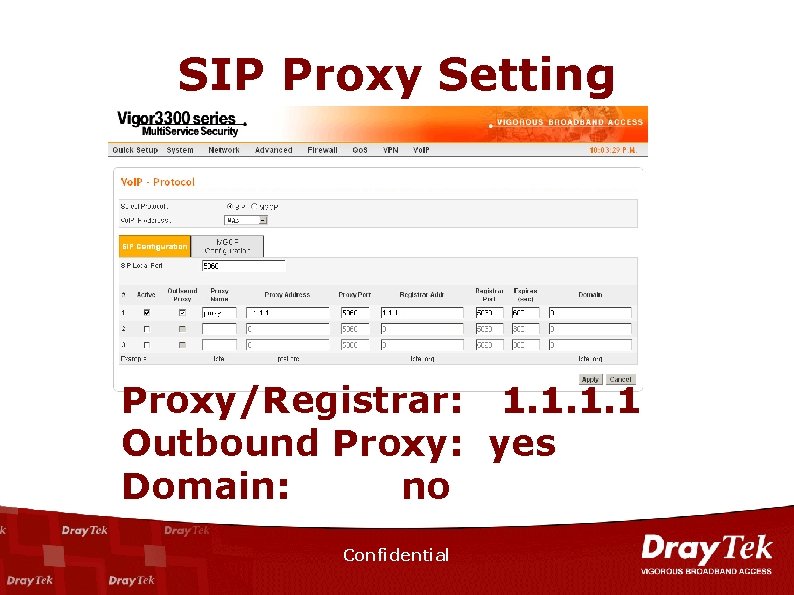
SIP Proxy Setting Proxy/Registrar: 1. 1 Outbound Proxy: yes Domain: no Confidential

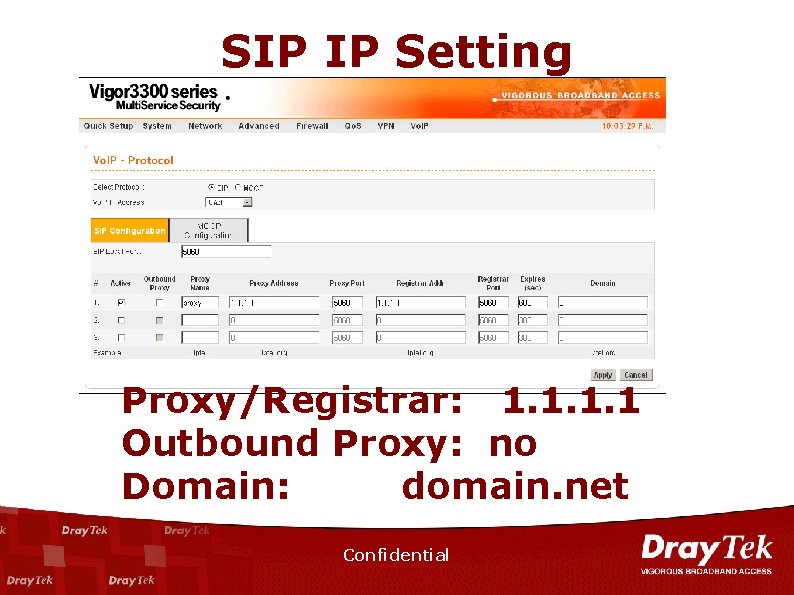
SIP IP Setting Proxy/Registrar: 1. 1 Outbound Proxy: no Domain: domain. net Confidential

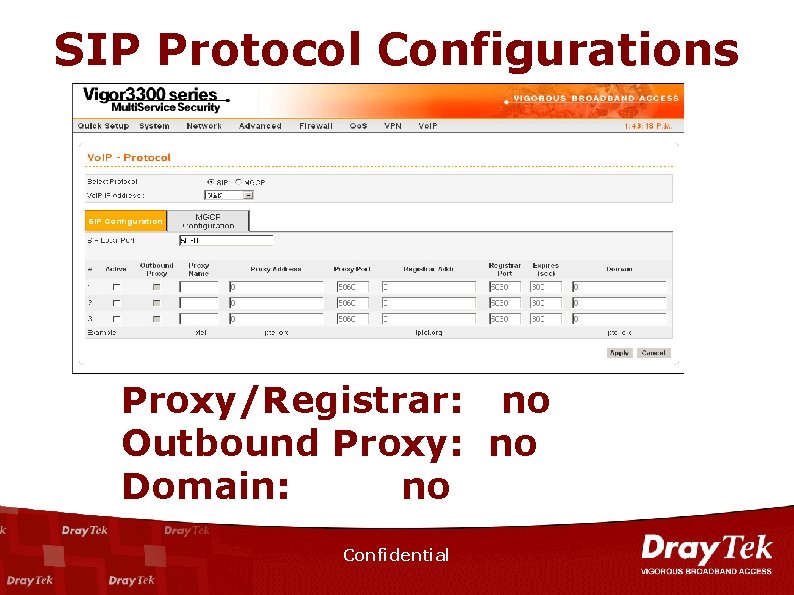
SIP Protocol Configurations Proxy/Registrar: no Outbound Proxy: no Domain: no Confidential

Incoming Call Barring Based on : Name IP/Domain Confidential

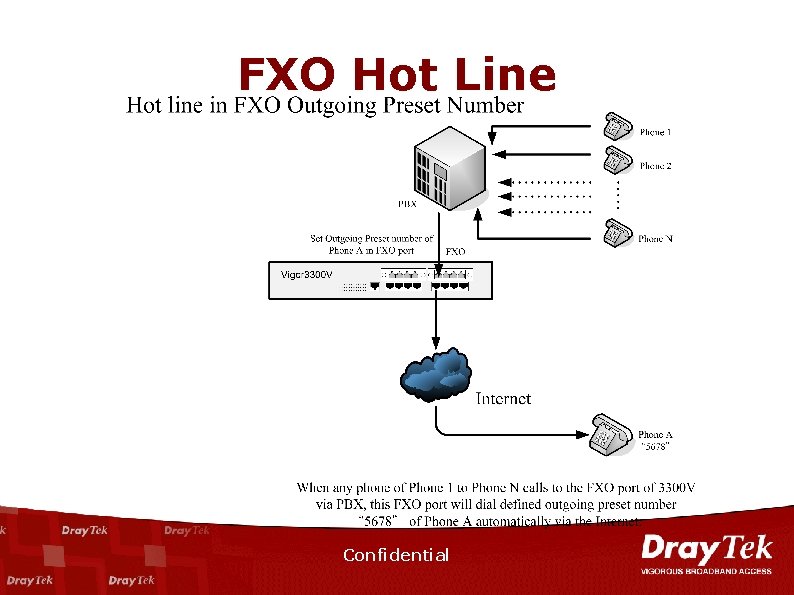
FXO Hot Line Confidential

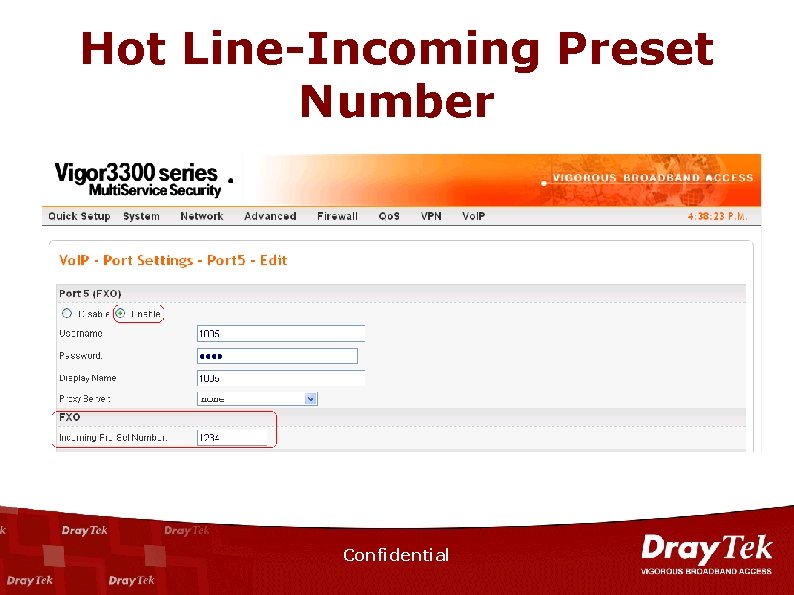
Hot Line-Incoming Preset Number Confidential

FXO Hot Line Confidential

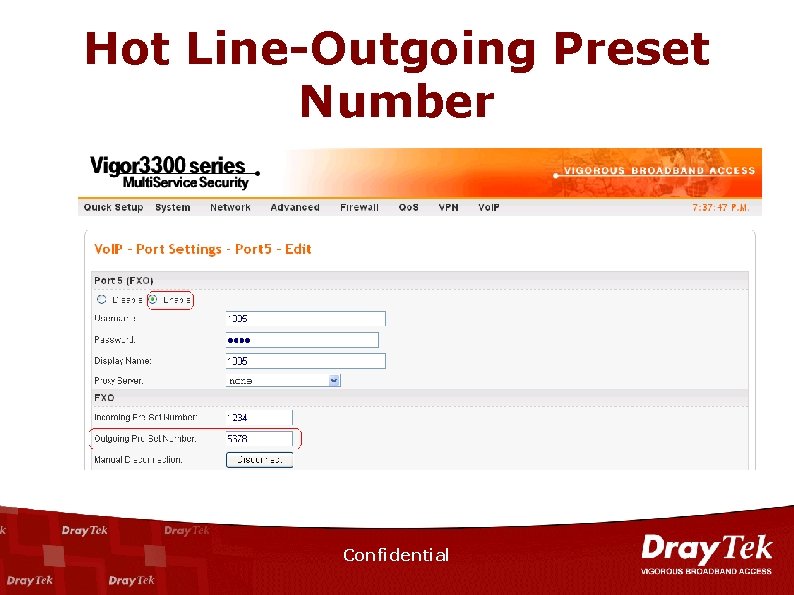
Hot Line-Outgoing Preset Number Confidential

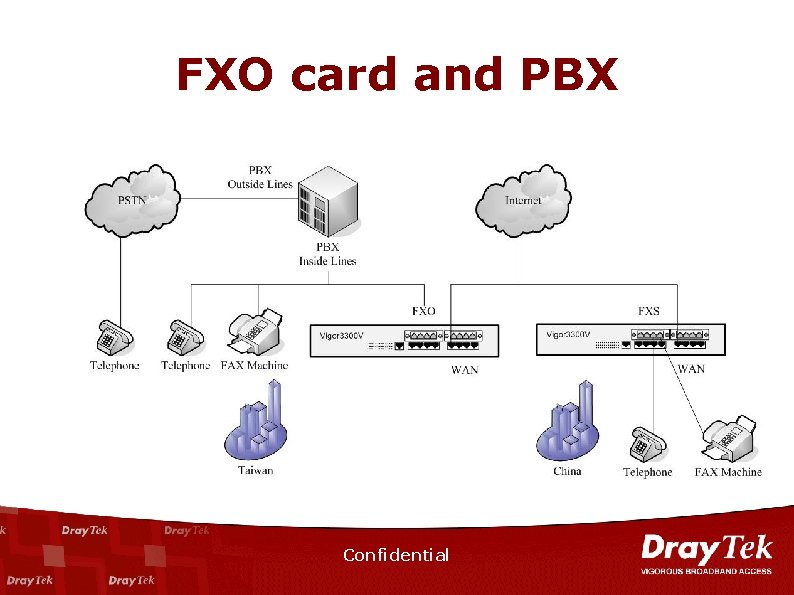
FXO card and PBX Confidential

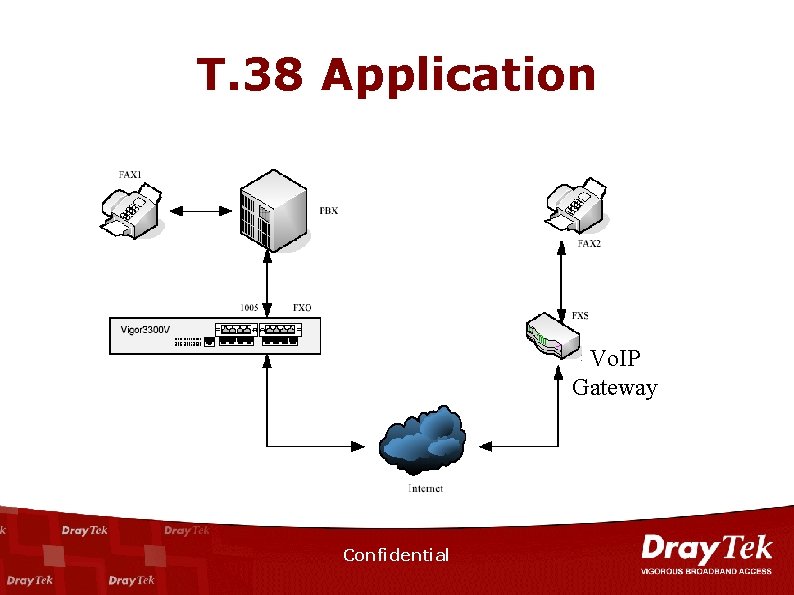
T. 38 Application Vo. IP Gateway Confidential

Advanced n n High Availability NAT – Port Redirection – DMZ n n Port Mirror VPN Confidential

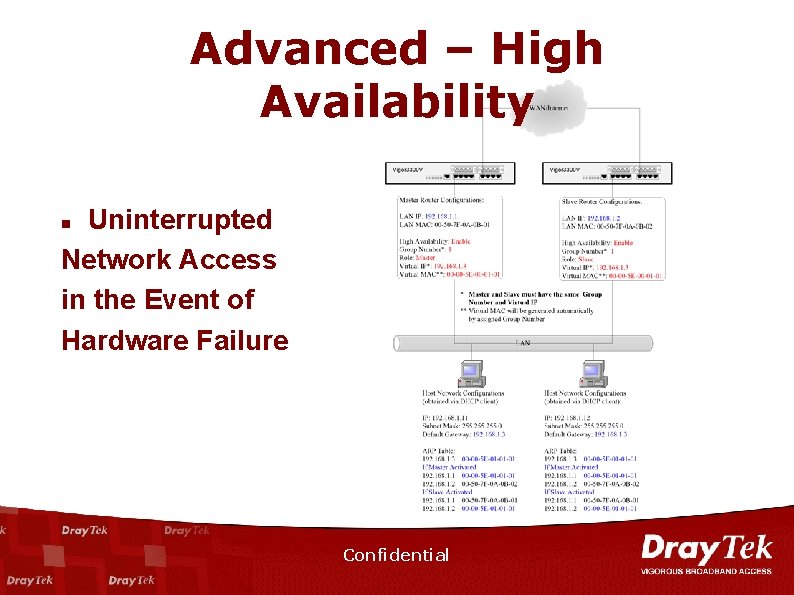
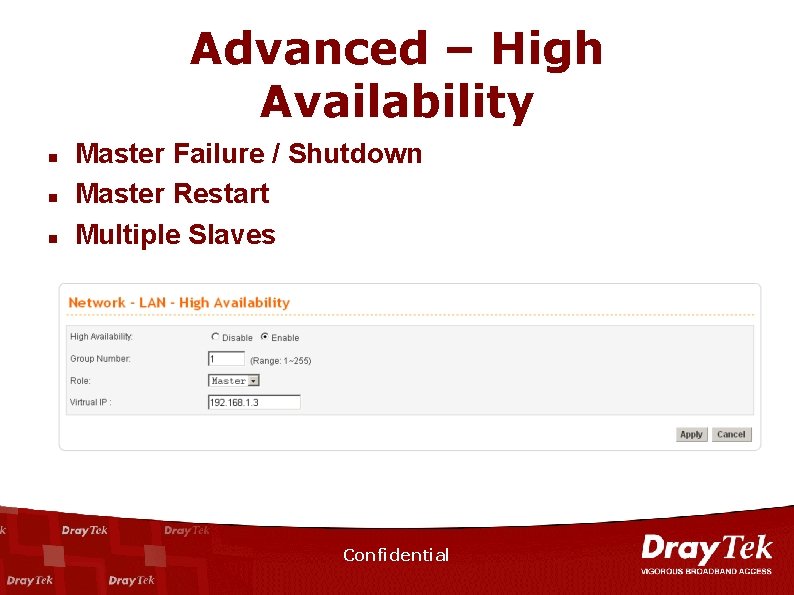
Advanced – High Availability Uninterrupted Network Access in the Event of Hardware Failure n Confidential

Advanced – High Availability n n n Master Failure / Shutdown Master Restart Multiple Slaves Confidential

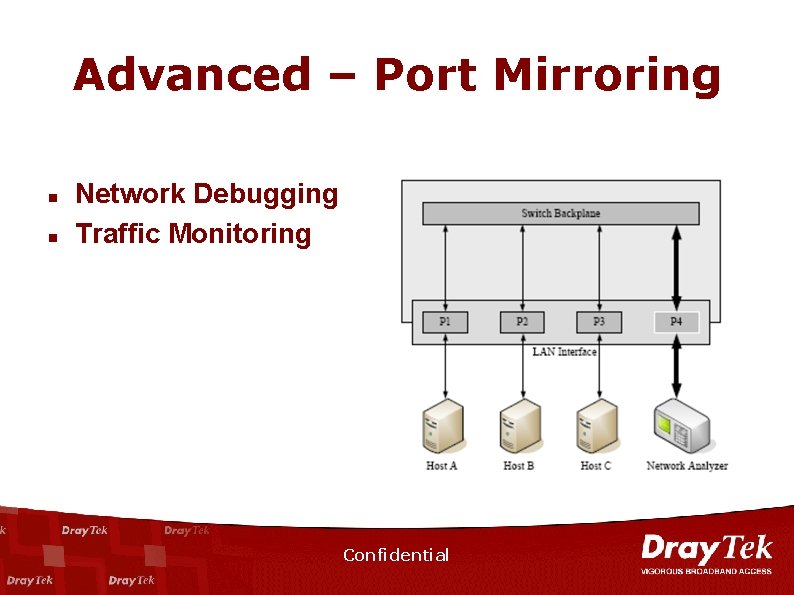
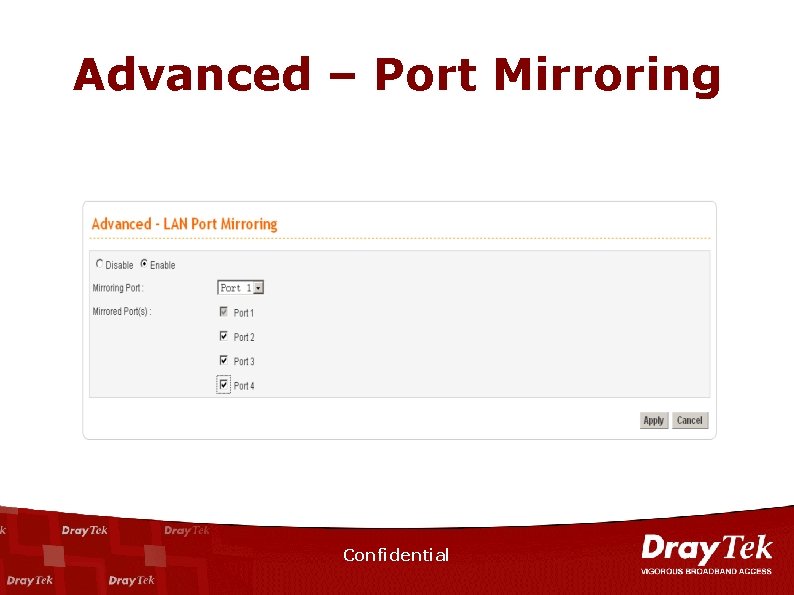
Advanced – Port Mirroring n n Network Debugging Traffic Monitoring Confidential

Advanced – Port Mirroring Confidential

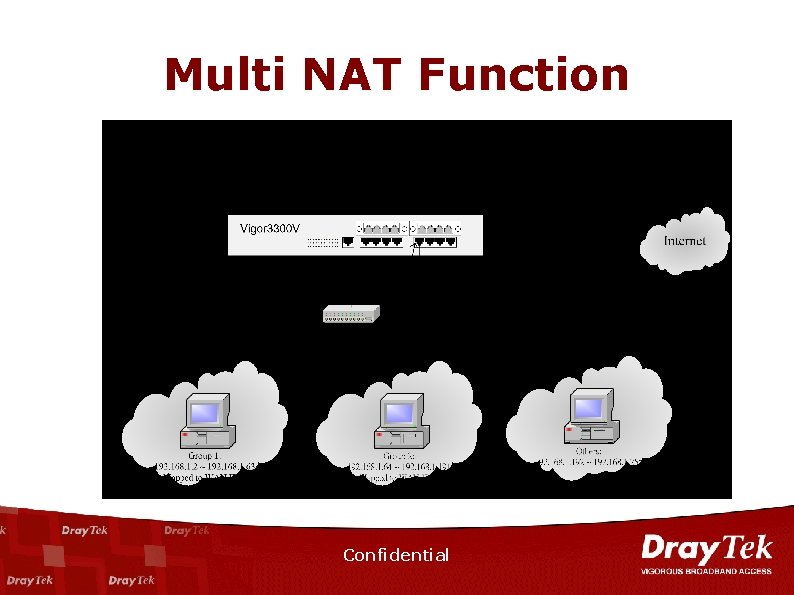
Multi NAT Function Confidential

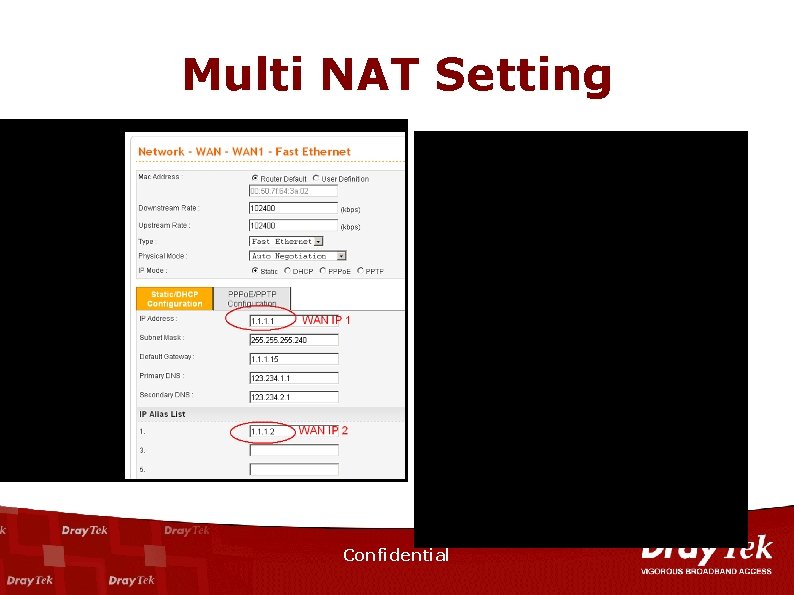
Multi NAT Setting Confidential

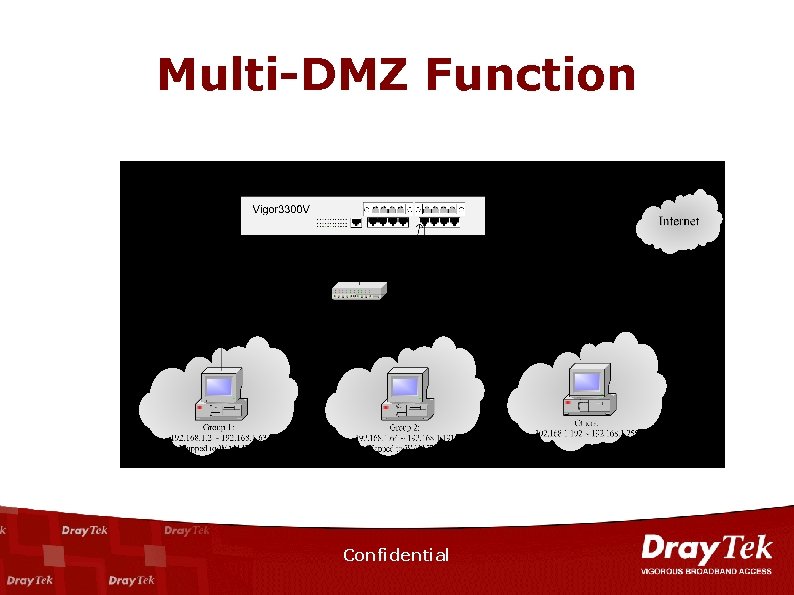
Multi-DMZ Function Confidential

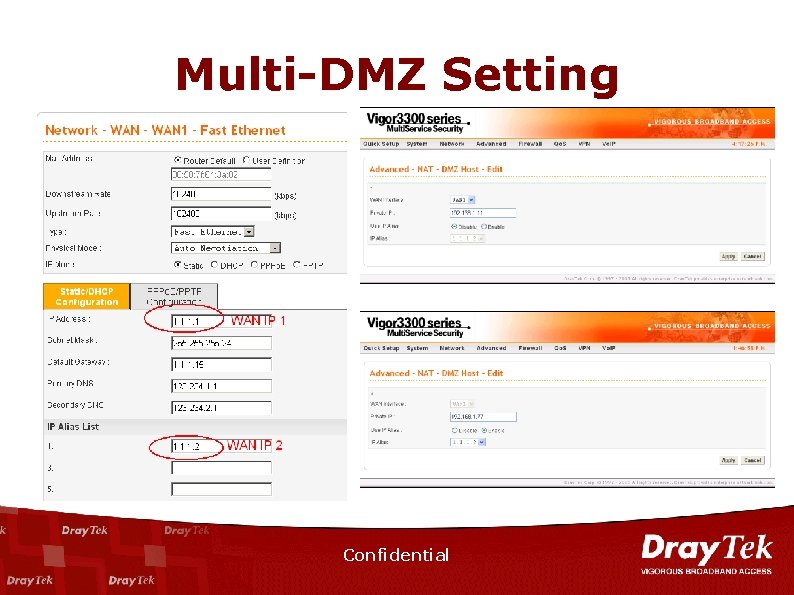
Multi-DMZ Setting Confidential

Vigor. Access Series Confidential

Content n n n System Benefit and Introduction Application ADSL 2/2+ Bridging Functions Advanced Features Confidential

System Benefit n n n n New DSL Technology-ADSL 2/2+ Scalable Reliability Multimedia Qo. S Inventory Saving Friendly EMS-Vigor CMS Confidential

Introduction n n ADSL 2/2+ IP DSLAM Target on outdoor and/or small-size CO side – 24 DSL Ports per Unit – Maximum 168 Ports for Master-Slave Architecture n n Splitter Built-in Data Flow – ATM/AAL 5/SAR on CPE side – IP/Ethernet Packet on Network side n n n Bridging Functions: 802. 1 d, 802. 1 p, 802. 1 q Multicasting Support - IGMP Snooping Packet Filtering, Scheduling, Qo. S Confidential

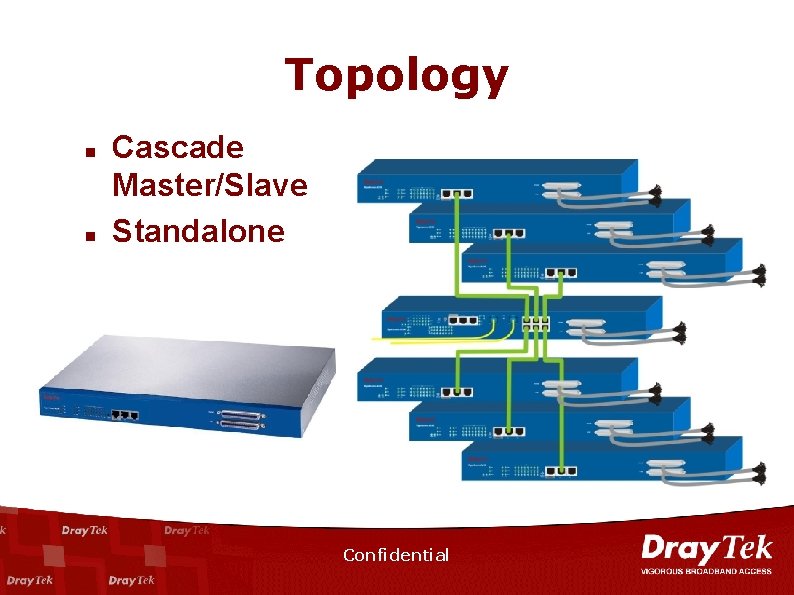
Topology n n Cascade Master/Slave Standalone Confidential

Specification n n n Max 168 (7*24) ADSL 2/2+ Ports 1 or 2 Giga Fiber Uplink Max 8 VCCs per DSL Port 4000 MAC Addresses 256 Multicast Groups 4094 VLAN ID, Concurrent 512 VLANs Confidential

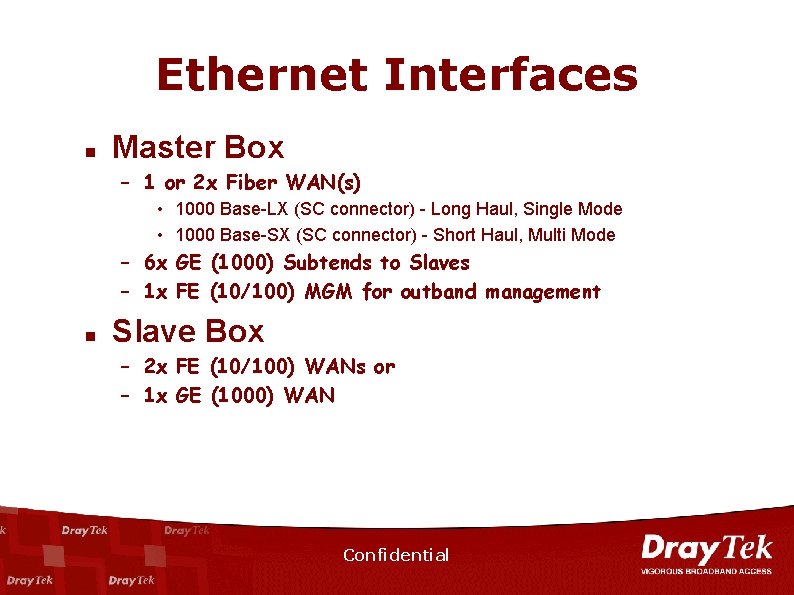
Ethernet Interfaces n Master Box – 1 or 2 x Fiber WAN(s) • 1000 Base-LX (SC connector) - Long Haul, Single Mode • 1000 Base-SX (SC connector) - Short Haul, Multi Mode – 6 x GE (1000) Subtends to Slaves – 1 x FE (10/100) MGM for outband management n Slave Box – 2 x FE (10/100) WANs or – 1 x GE (1000) WAN Confidential

Content n n n System Benefit and Introduction Application ADSL 2/2+ Bridging Functions Advanced Features Confidential

Application n n Broadband FTTB Application Broadband Enterprise Application DSL Extension Application Campus/Hospital Application Hotel Application Confidential

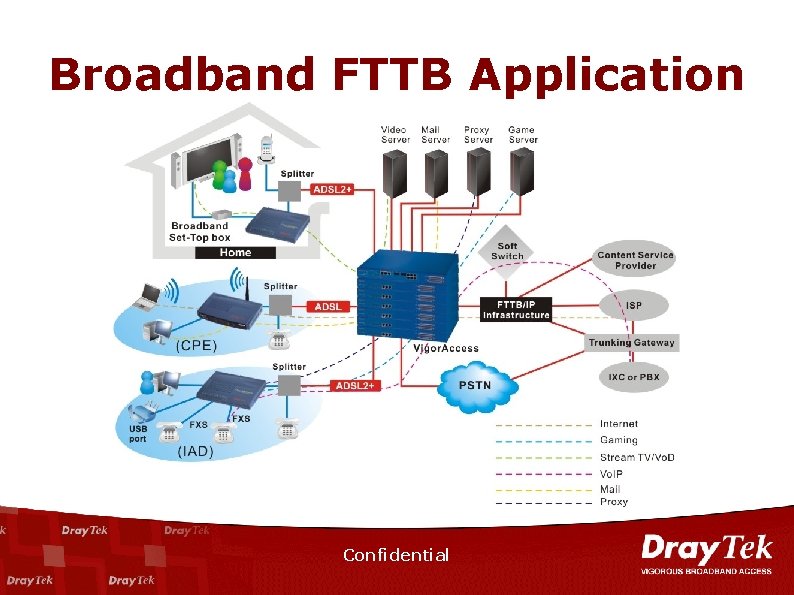
Broadband FTTB Application Confidential

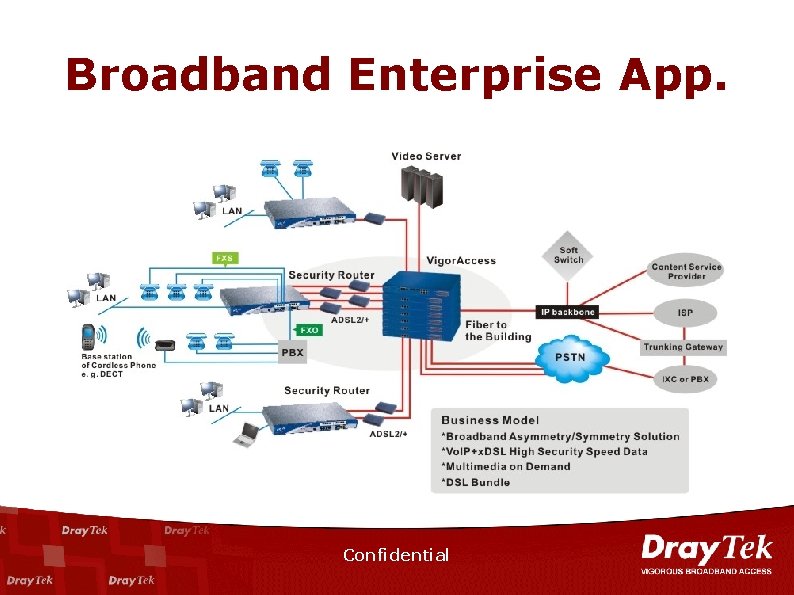
Broadband Enterprise App. Confidential

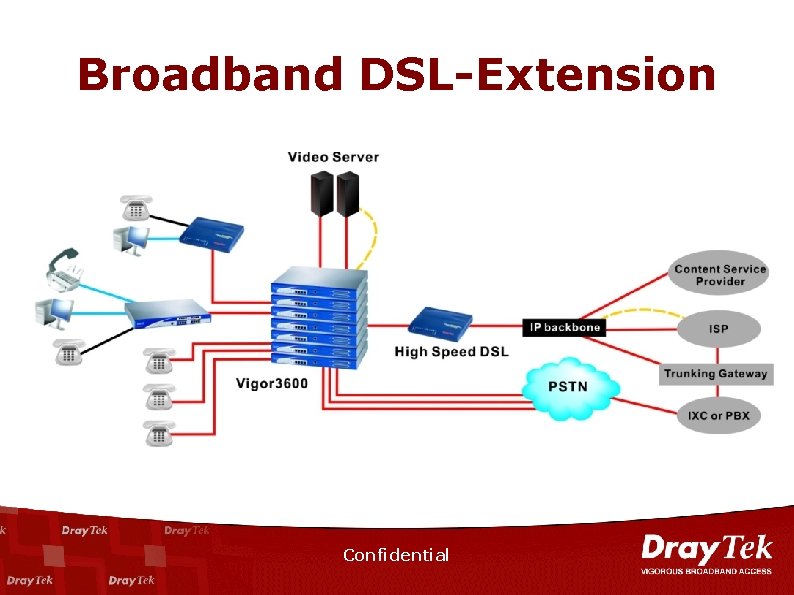
Broadband DSL-Extension Confidential

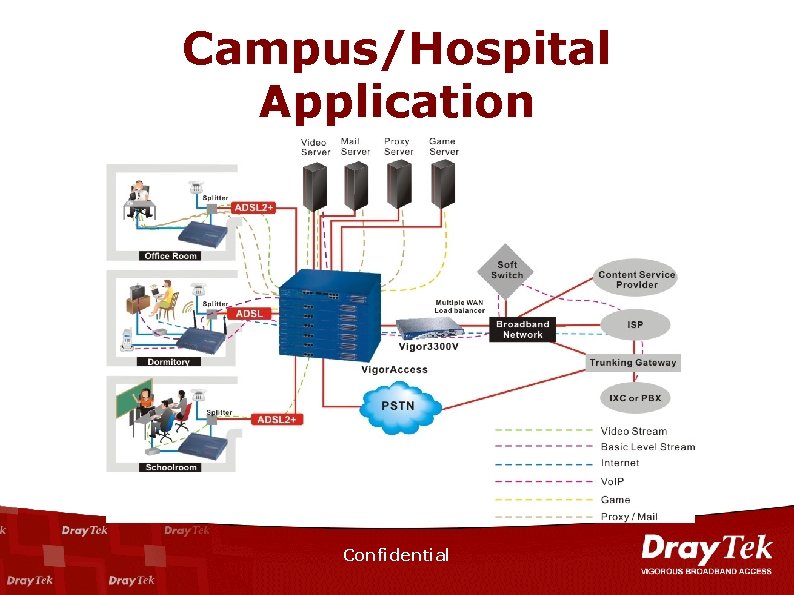
Campus/Hospital Application Confidential

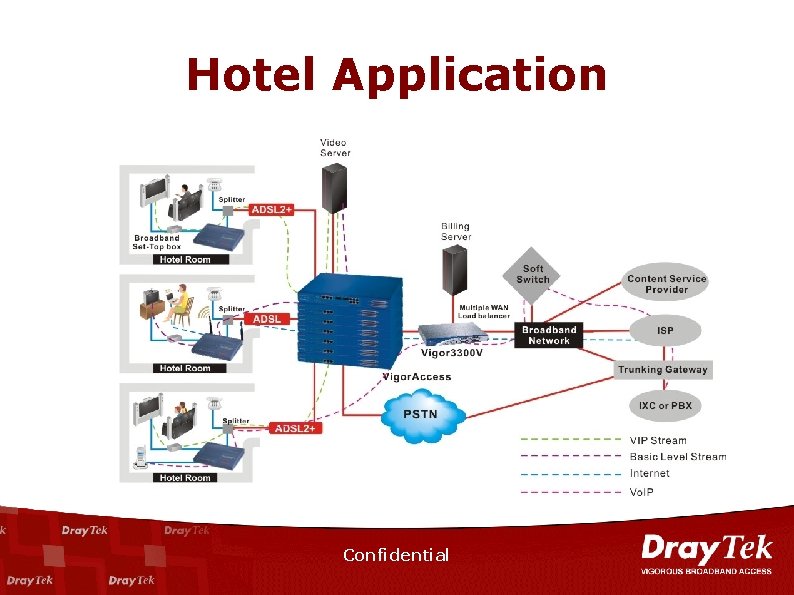
Hotel Application Confidential

Content n n n System Benefit and Introduction Application ADSL 2/2+ Bridging Functions Advanced Features Confidential

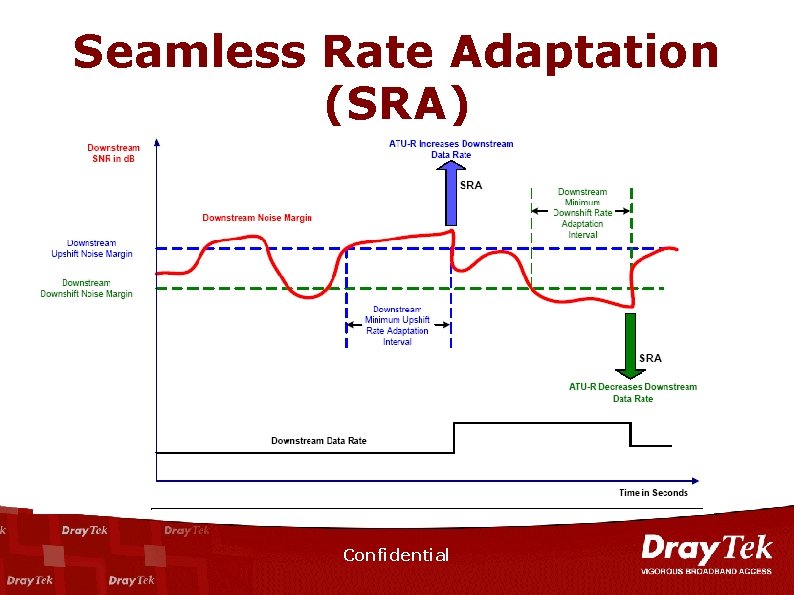
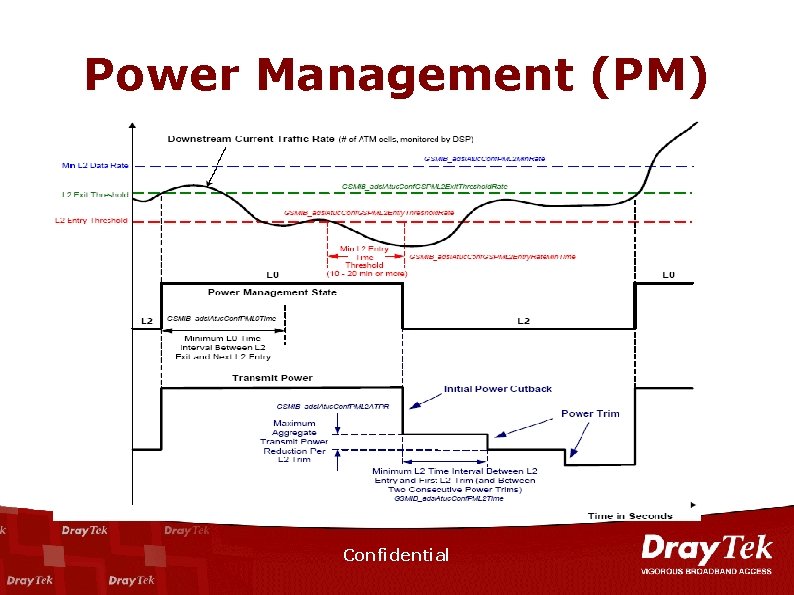
ADSL 2/2+ n n n Higher Data Rate Longer Reach - READSL 2 Annex M-Uplink 3 M bps Seamless Rate Adaptation Power Management Loop Diagnostics – DELT: Double Ended Line Testing – SELT: Single Ended Line Testing Confidential

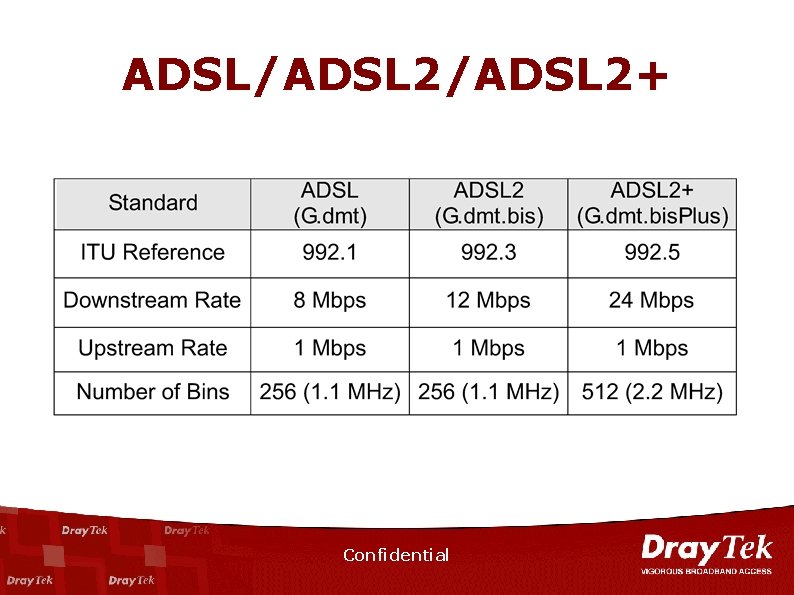
ADSL/ADSL 2+ Confidential

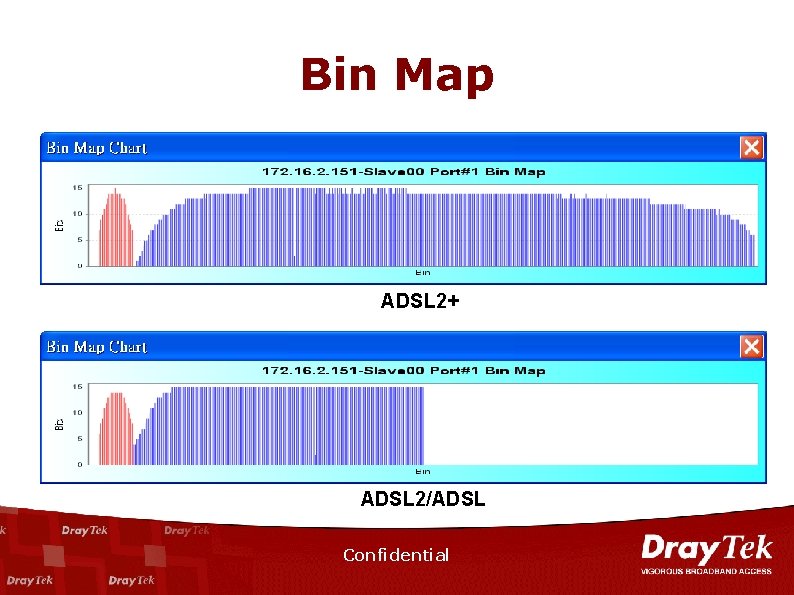
Bin Map ADSL 2+ ADSL 2/ADSL Confidential

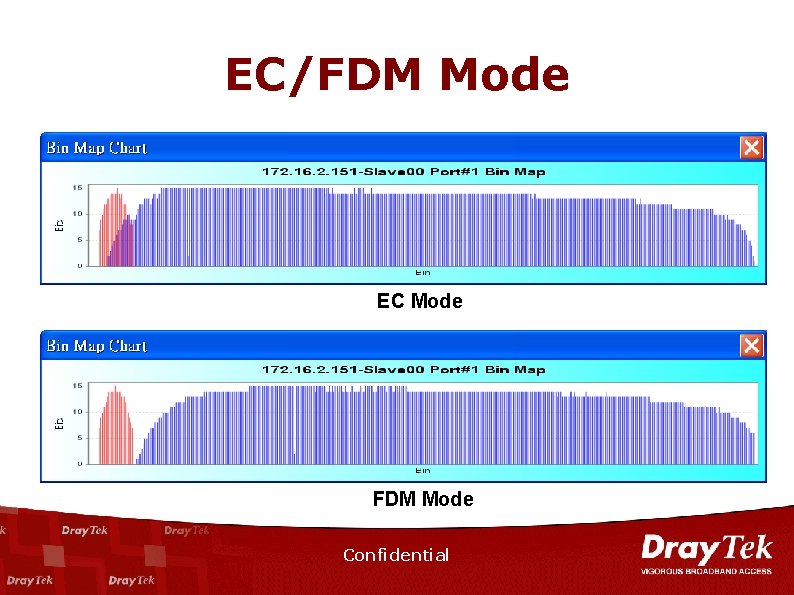
EC/FDM Mode EC Mode FDM Mode Confidential

Seamless Rate Adaptation (SRA) Confidential

Power Management (PM) Confidential

Content n n n System Benefit and Introduction Application ADSL 2/2+ Bridging Functions Advanced Features Confidential

Bridging Functions n n 802. 1 d Address Learning and Aging Broadcast Flooding 802. 1 q VLAN Bridging Multicasting - IGMP Snooping Confidential

IGMP Snooping n n A layer-2 switch supported IGMP snooping can passively snoop on IGMP Query, Report and Leave packets to learn the IP Multicast group membership. Multicast traffic of a group is only forwarded to ports that have members of that group. Confidential

Content n n n System Benefit and Introduction Application ADSL 2/2+ Bridging Functions Advanced Features Confidential

Advanced Features n n n Security Packet Filtering Qo. S Confidential

Security n n MAC Address Tracking MAC Address Access Control List – Global Deny – Per Port Accept n IP Address Access Control List Confidential

Packet Filtering Confidential

Qo. S n n Prioritized Bridging Input Rate Limiting (IRL) – AAL 5 based n Output Rate Limiting (IRL) – Ethernet/ATM port based n n Packet Priority to Traffic Class Mapping 802. 1 p Re-Tagging Confidential

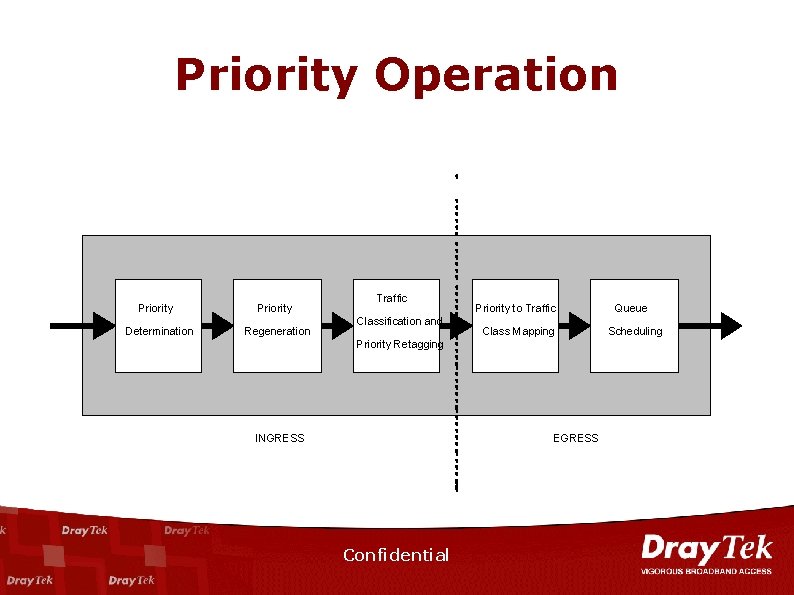
Priority Operation Priority Determination Priority Regeneration Traffic Classification and Priority to Traffic Class Mapping Priority Retagging INGRESS EGRESS Confidential Queue Scheduling

Vigor. CMS/View Series Confidential

Management n n n n n Serial CLI Telnet CLI SNMP v 1/v 2 TFTP Firmware Upgrade Configuration Backup/Restore Inband/Outband Management VLAN Single IP Management Access Control Confidential

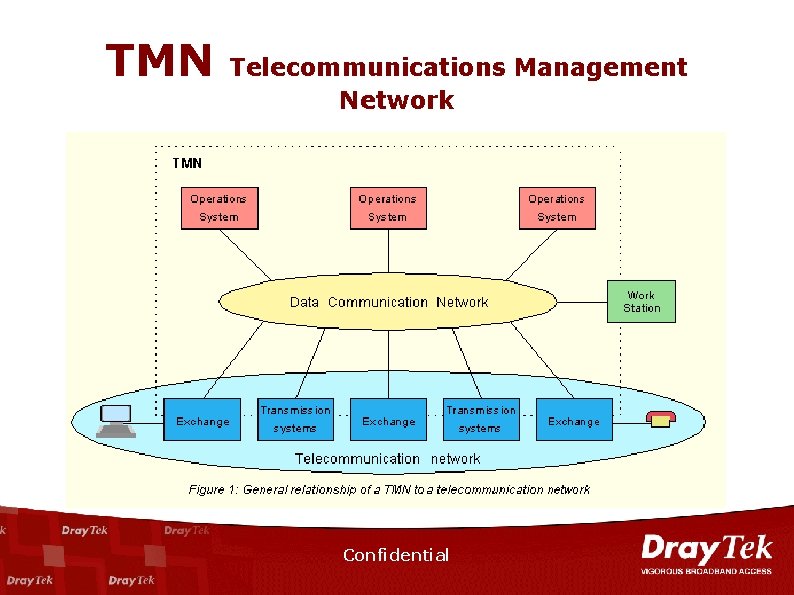
TMN Telecommunications Management Network Confidential

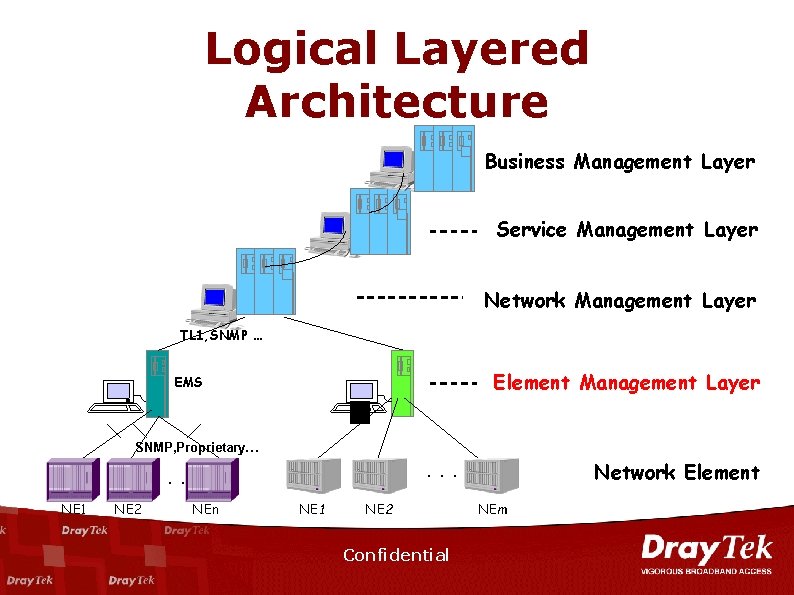
Logical Layered Architecture Business Management Layer Service Management Layer Network Management Layer TL 1, SNMP … Element Management Layer EMS SNMP, Proprietary… NE 1 NE 2 NEn Network Element . . . NE 1 NE 2 Confidential NEm

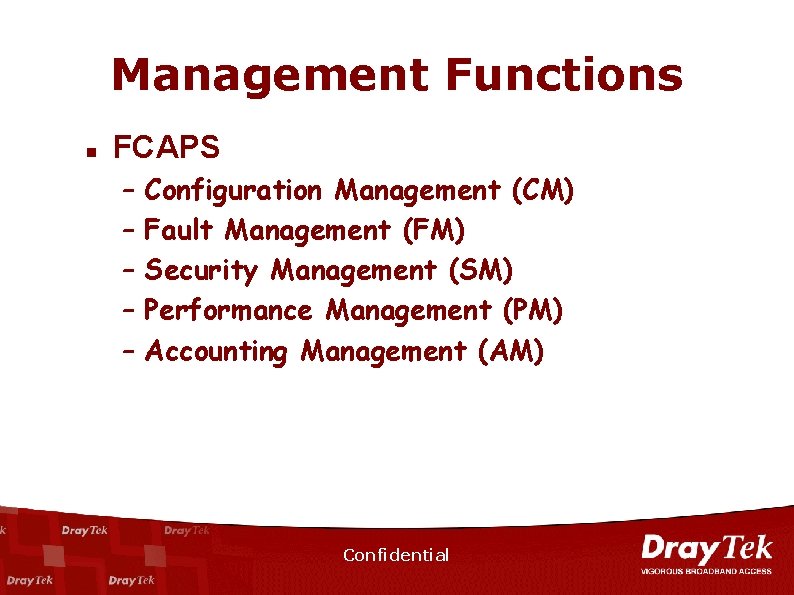
Management Functions n FCAPS – – – Configuration Management (CM) Fault Management (FM) Security Management (SM) Performance Management (PM) Accounting Management (AM) Confidential

Vigor CMS n n n n Centralized Management System Client/Server Multi-Tier Architecture Easy to Use GUI Pure Java Implementation Support Commercial Databases Customized Northbound Interface Scalability - 1000 to 10000 NEs Confidential

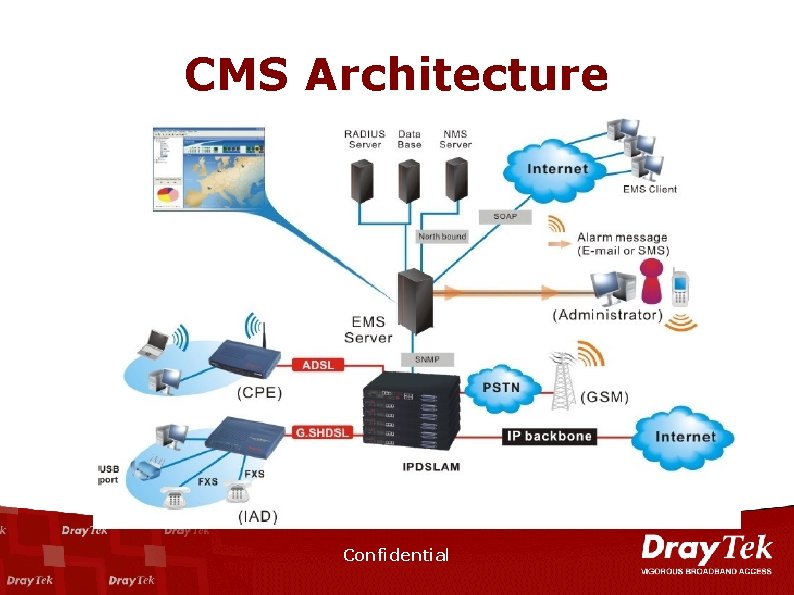
CMS Architecture Confidential

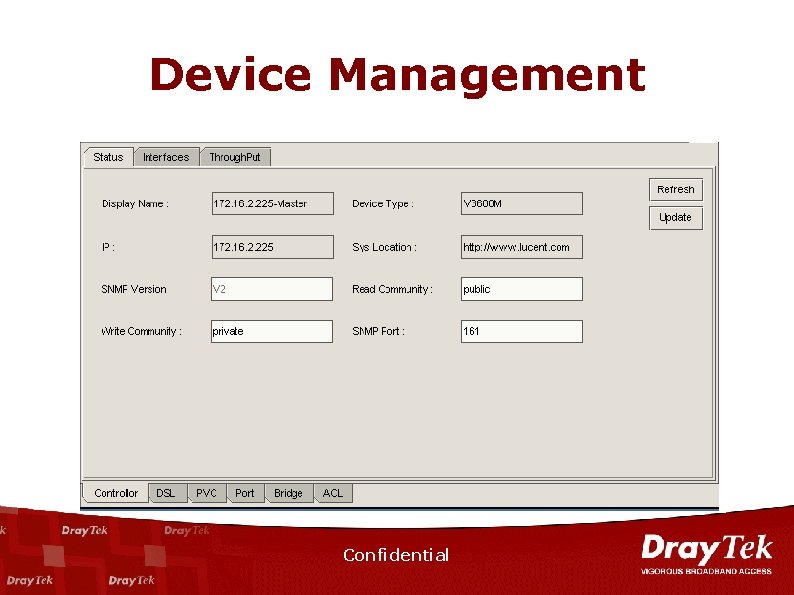
Device Management Confidential

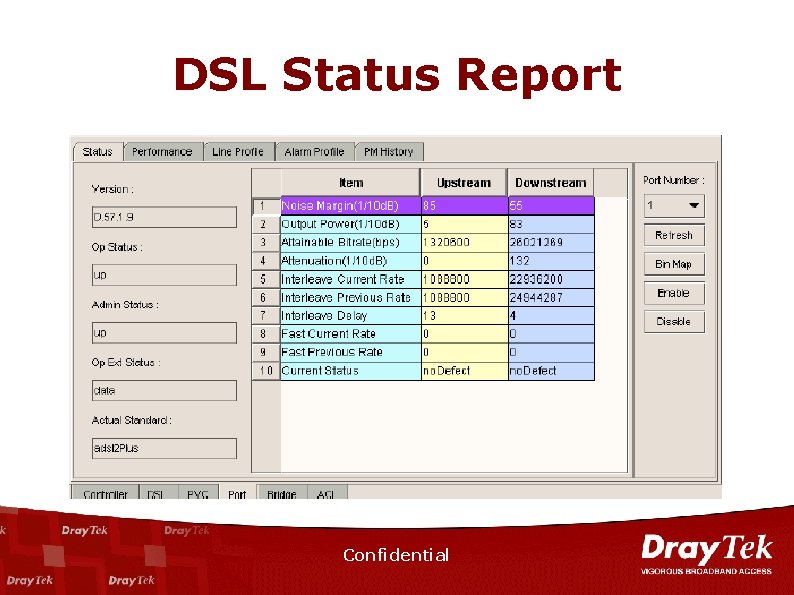
DSL Status Report Confidential

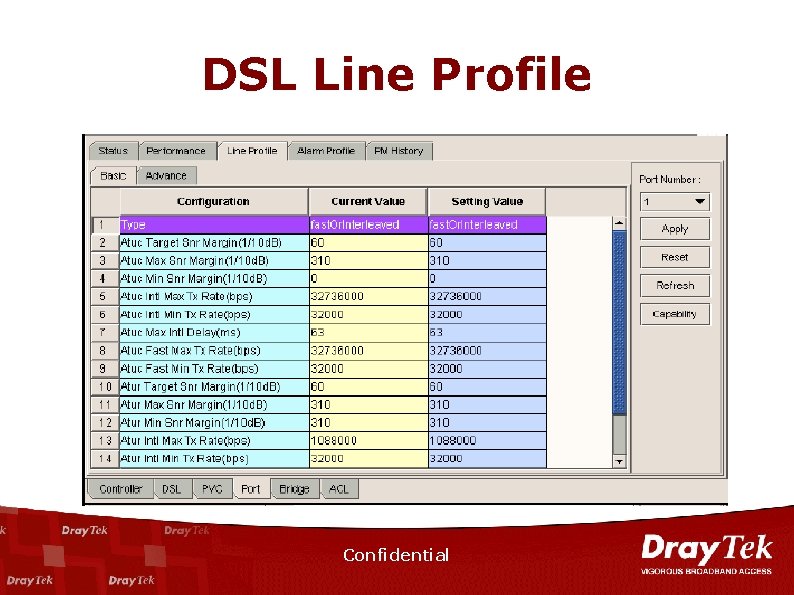
DSL Line Profile Confidential

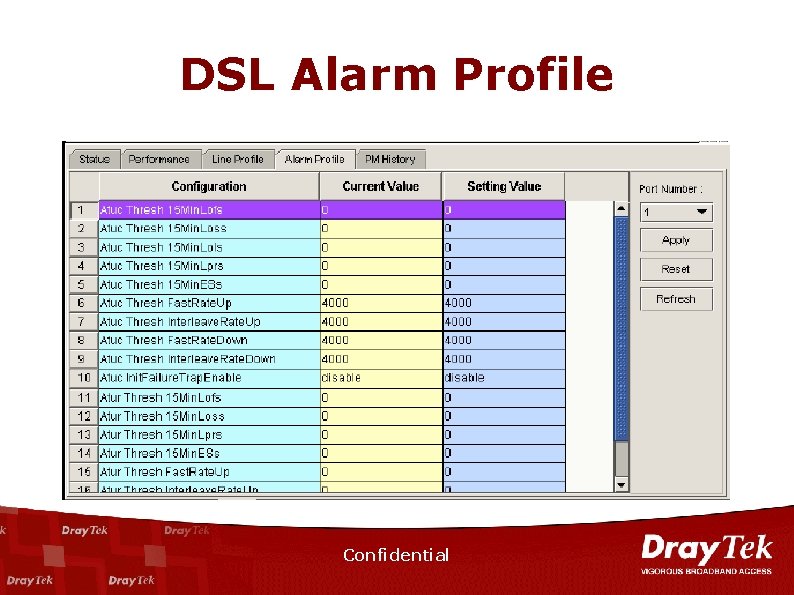
DSL Alarm Profile Confidential

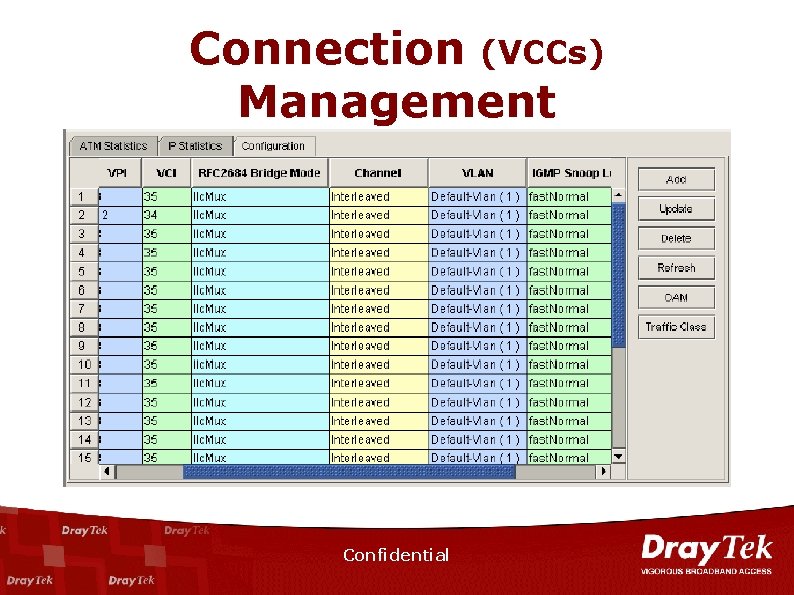
Connection (VCCs) Management Confidential

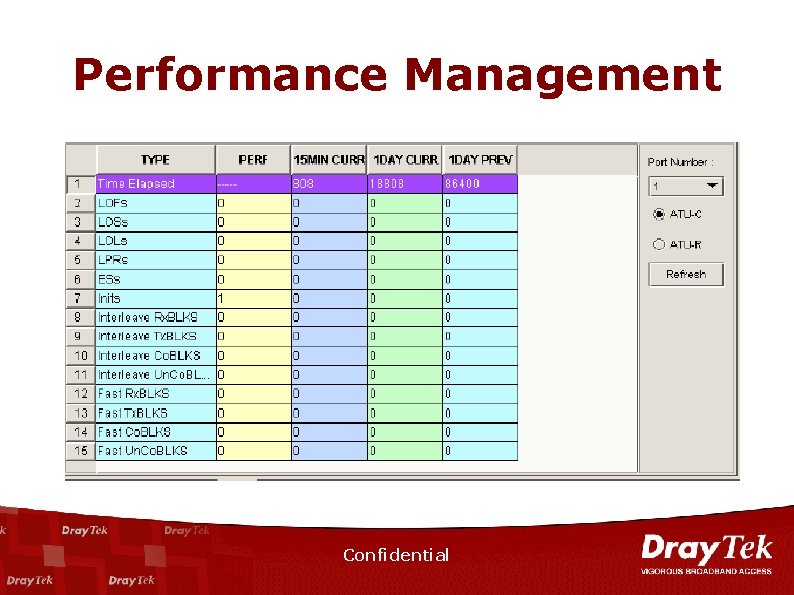
Performance Management Confidential

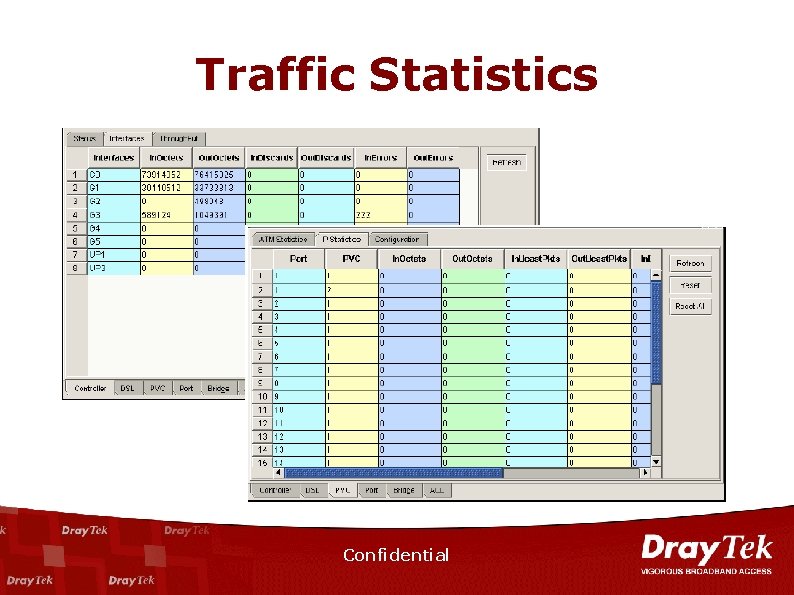
Traffic Statistics Confidential

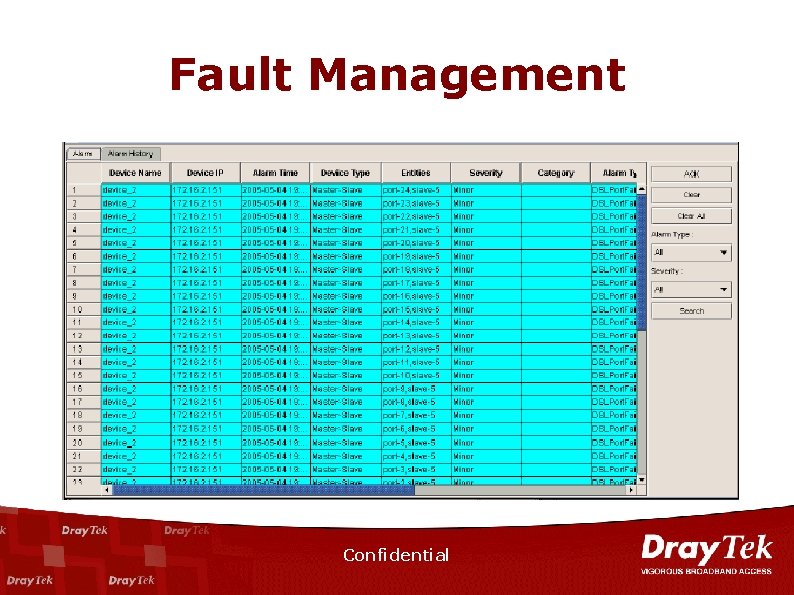
Fault Management Confidential

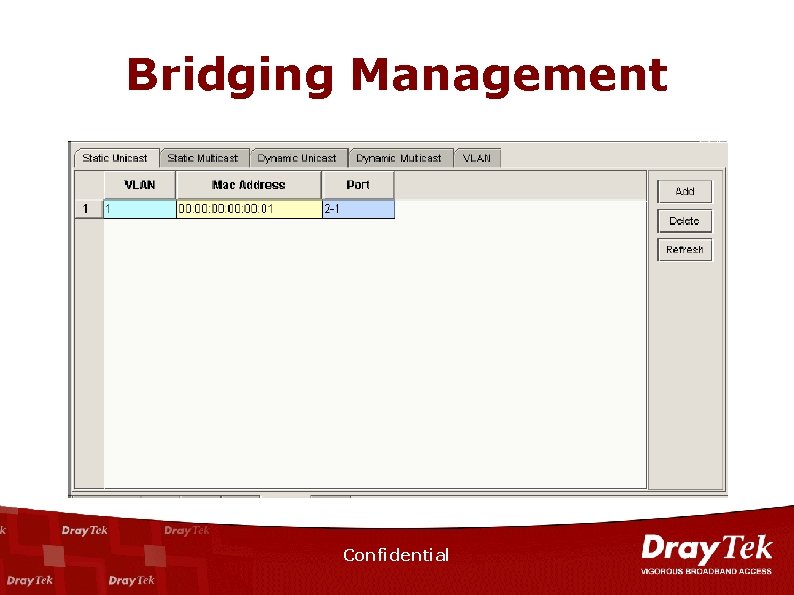
Bridging Management Confidential

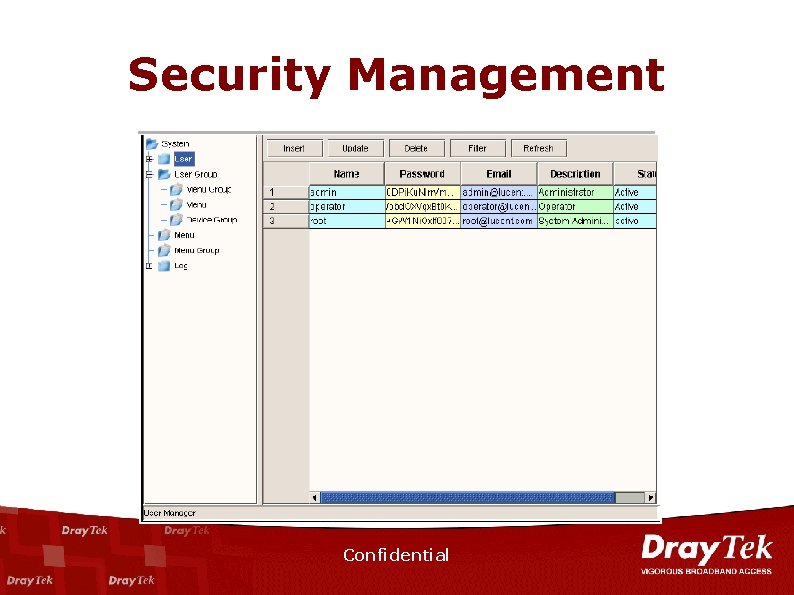
Security Management Confidential

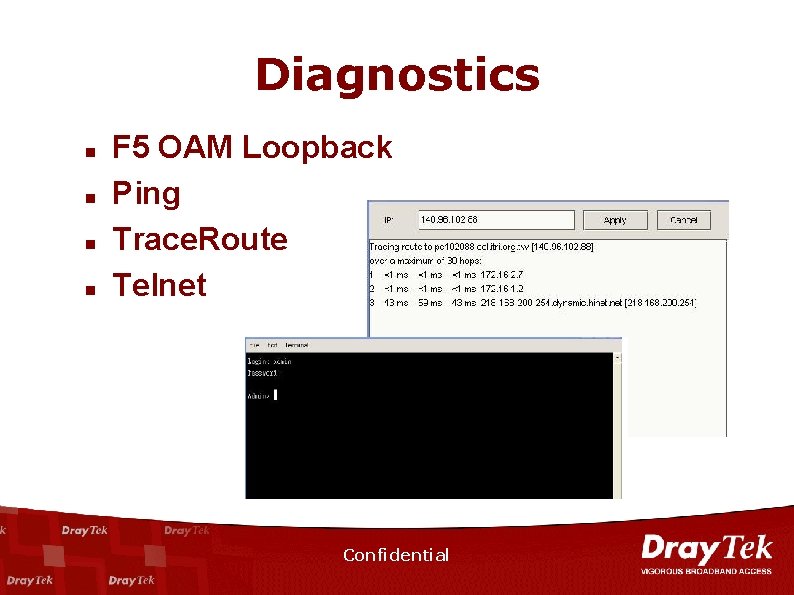
Diagnostics n n F 5 OAM Loopback Ping Trace. Route Telnet Confidential

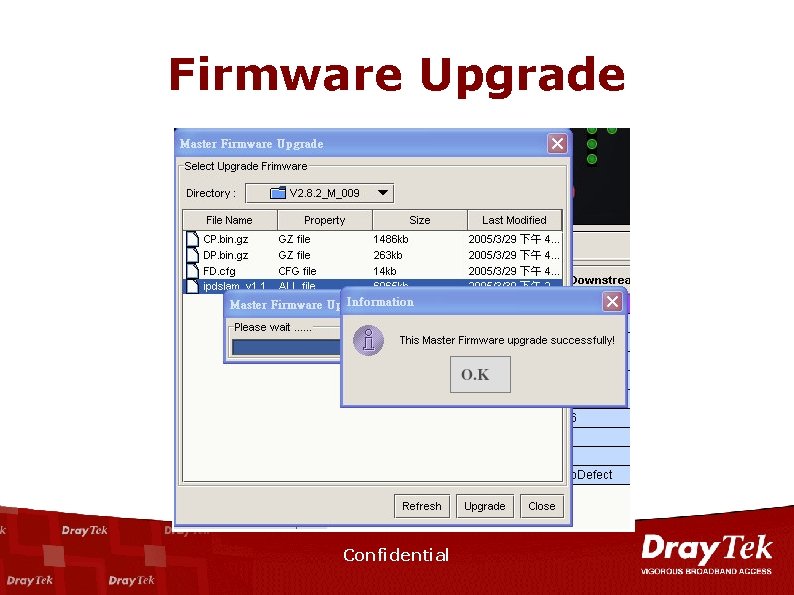
Firmware Upgrade Confidential

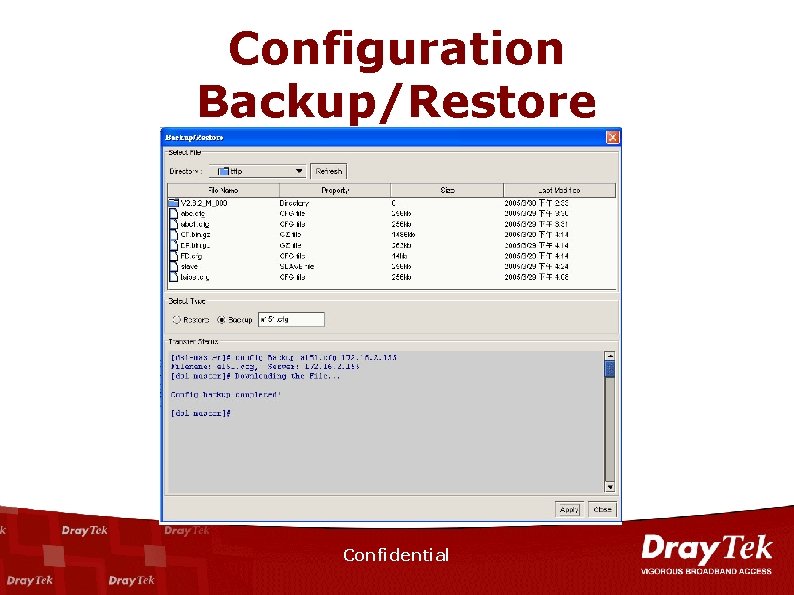
Configuration Backup/Restore Confidential

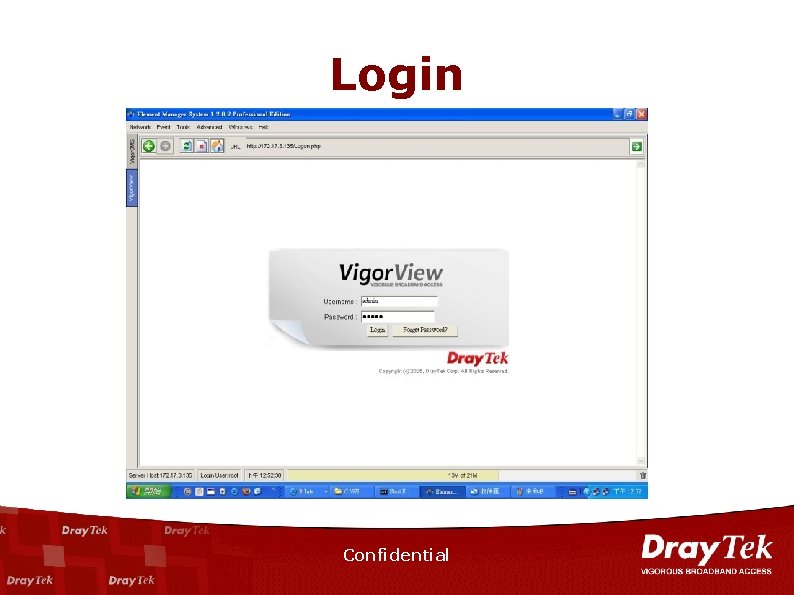
Login Confidential

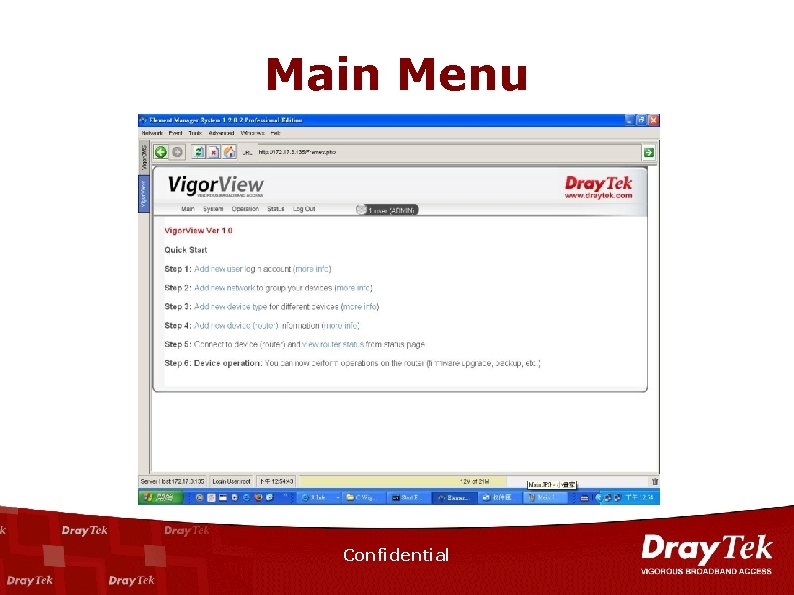
Main Menu Confidential

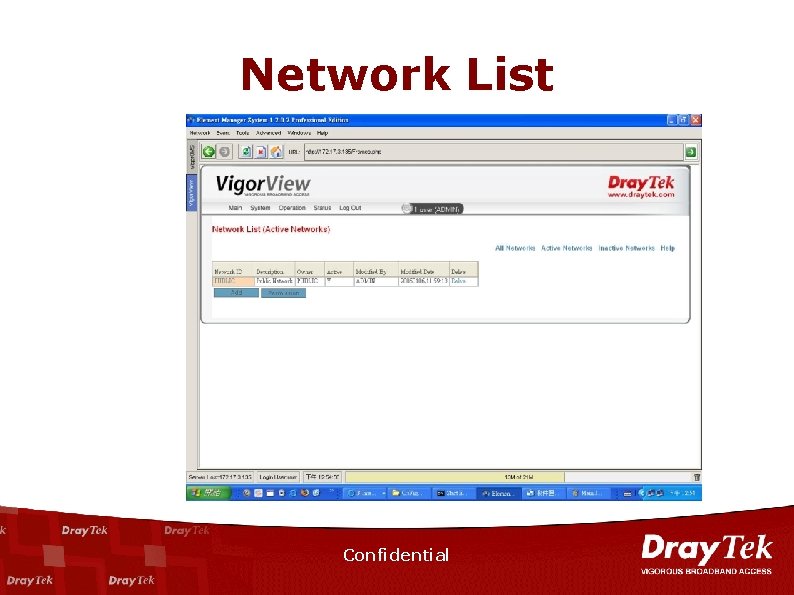
Network List Confidential

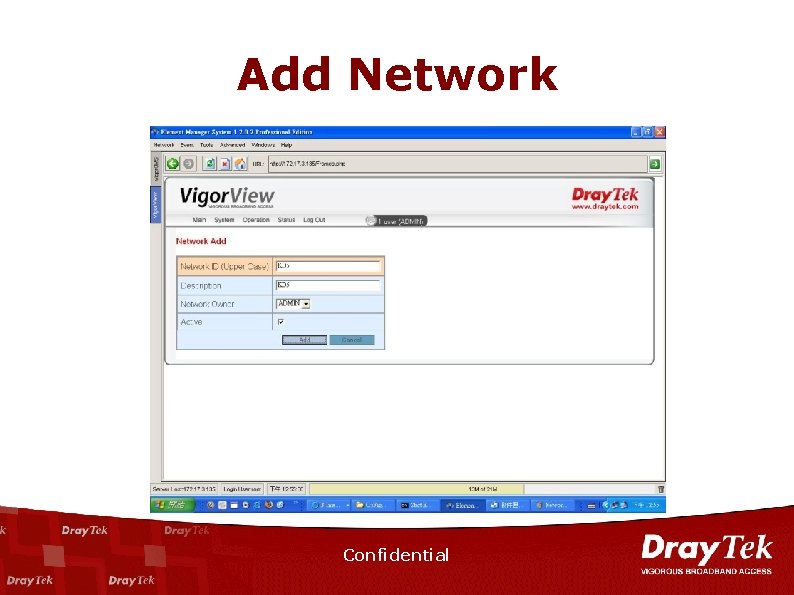
Add Network Confidential

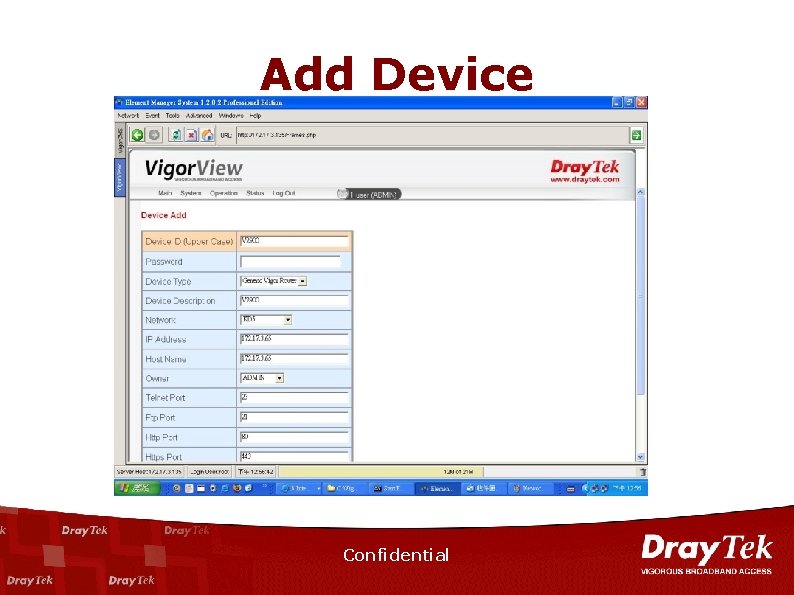
Add Device Confidential

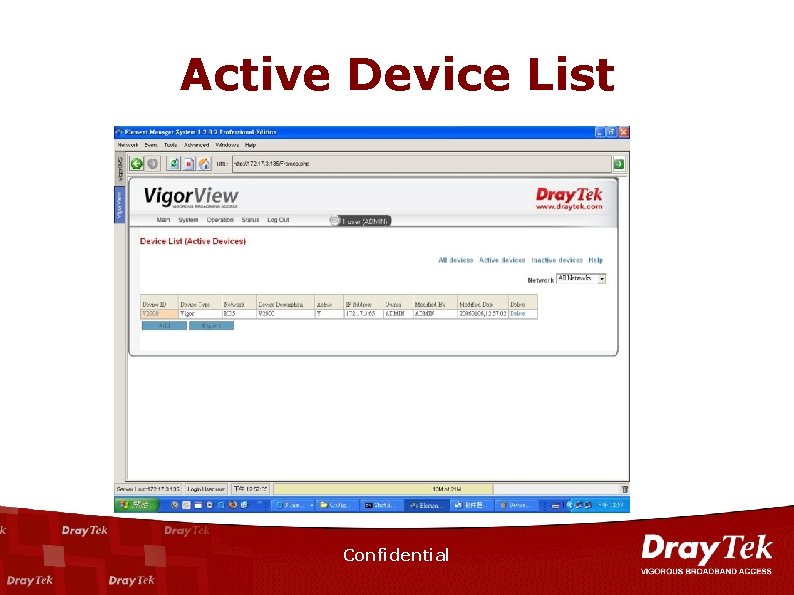
Active Device List Confidential

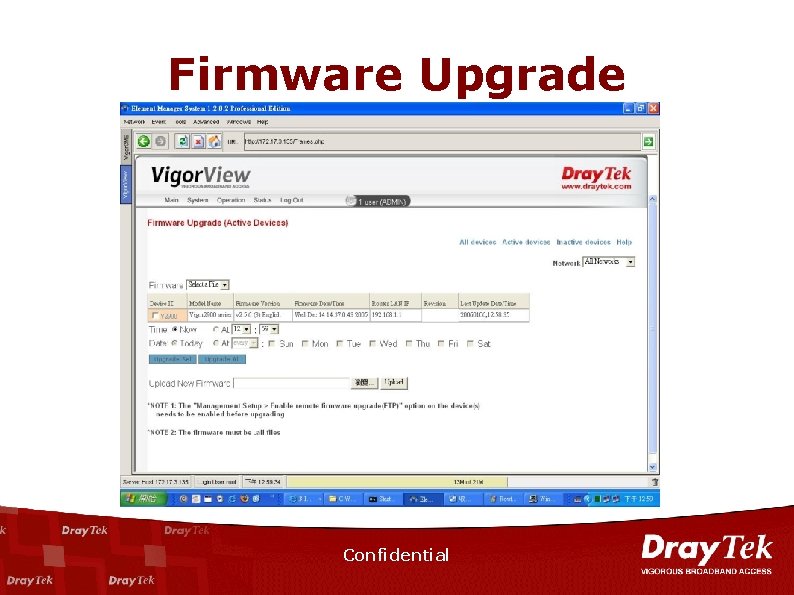
Firmware Upgrade Confidential

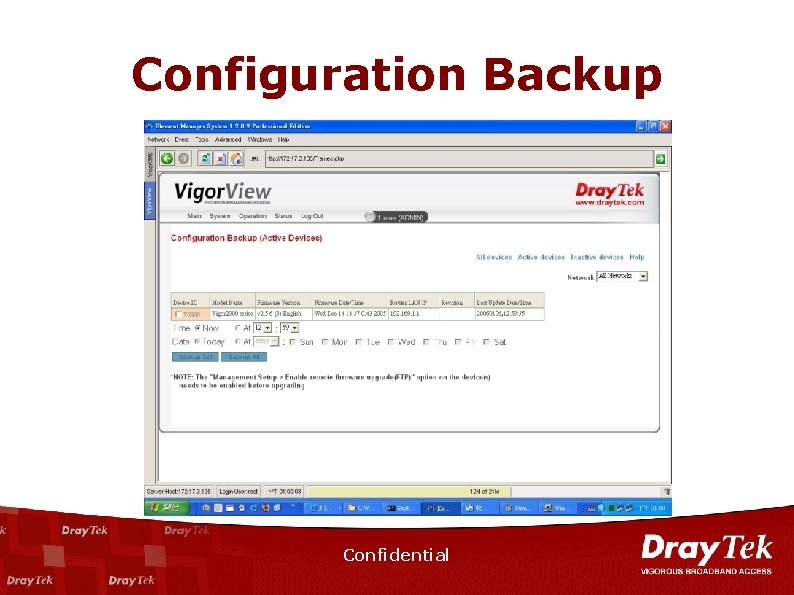
Configuration Backup Confidential

Router Status Confidential

Telnet Confidential

Online Status Confidential