CMPE 208 Presentation Terminal Access Controller Access Control















![Reference v v [1] “The TACACS+ Protocol”, Version 1. 78. by D. Carrel, Lol Reference v v [1] “The TACACS+ Protocol”, Version 1. 78. by D. Carrel, Lol](https://slidetodoc.com/presentation_image/126eea7400c17d7934b38da262050a64/image-21.jpg)

- Slides: 22

CMPE 208 Presentation Terminal Access Controller Access Control System Plus (TACACS+) By MARVEL (Libing, Bhavana, Ramya, Maggie, Nitin)

Agenda v v v Introduction – TACACS+ Format and Header Values TACACS+ Operations (AAA) Vulnerabilities Conclusion

Introduction – TACACS+ v TACACS+ (terminal access controller access-control system plus), pronounced as “tack-acks plus” v TACACS+ originated from the TACACS and extended TACACS protocols. But it is not compatible with them. v A Cisco proprietary protocol. v provides the access control for routers, network access servers, and many other networked computing devices through one or more centralized servers. v Provides separate Authentication, Authorization, and Accounting services for server access.

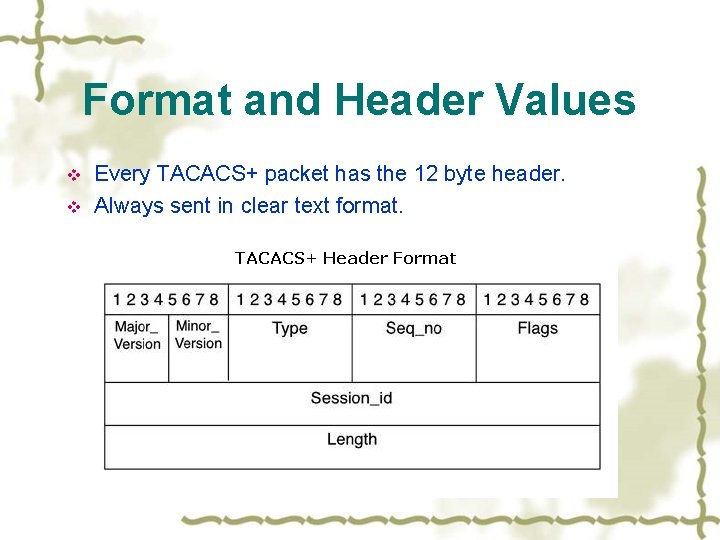
Format and Header Values v v Every TACACS+ packet has the 12 byte header. Always sent in clear text format.

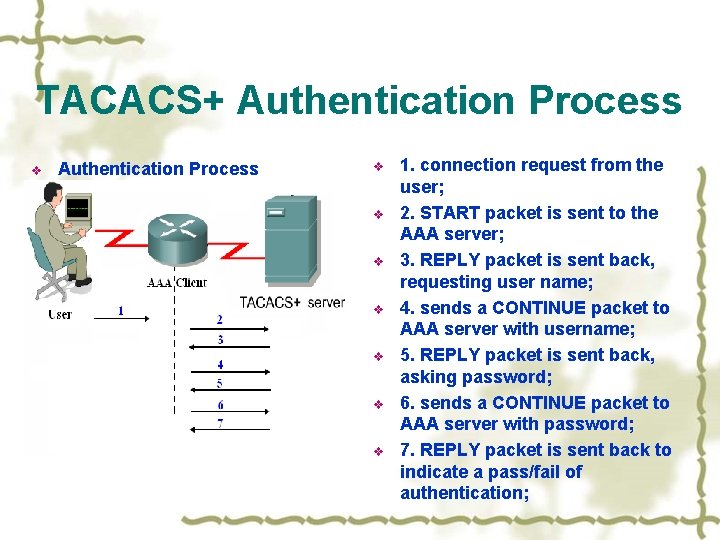
TACACS+ Authentication v v who is allowed to gain access to the network. Using usernames and passwords, or “one time” passwords. takes place when the user first logs in to a machine or requests a service of it. packet types: START, CONTINUE and REPLY. START and CONTINUE are always sent by the client; REPLY is always sent by the daemon.

TACACS+ Authentication Process v v v v 1. connection request from the user; 2. START packet is sent to the AAA server; 3. REPLY packet is sent back, requesting user name; 4. sends a CONTINUE packet to AAA server with username; 5. REPLY packet is sent back, asking password; 6. sends a CONTINUE packet to AAA server with password; 7. REPLY packet is sent back to indicate a pass/fail of authentication;

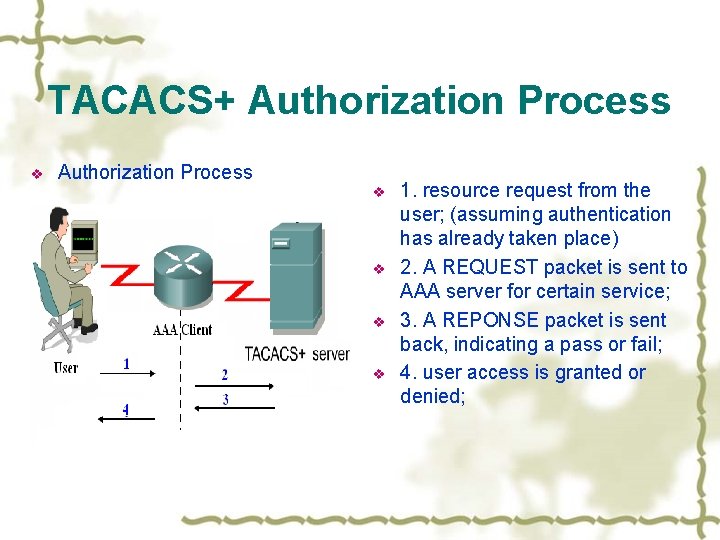
TACACS+ Authorization v what a user is allowed to do. v what services the user has access to. v customize the service for the particular user. v An authorization session is defined as a single pair of messages, a REQUEST followed by a RESPONSE.

TACACS+ Authorization Process v v v v 1. resource request from the user; (assuming authentication has already taken place) 2. A REQUEST packet is sent to AAA server for certain service; 3. A REPONSE packet is sent back, indicating a pass or fail; 4. user access is granted or denied;

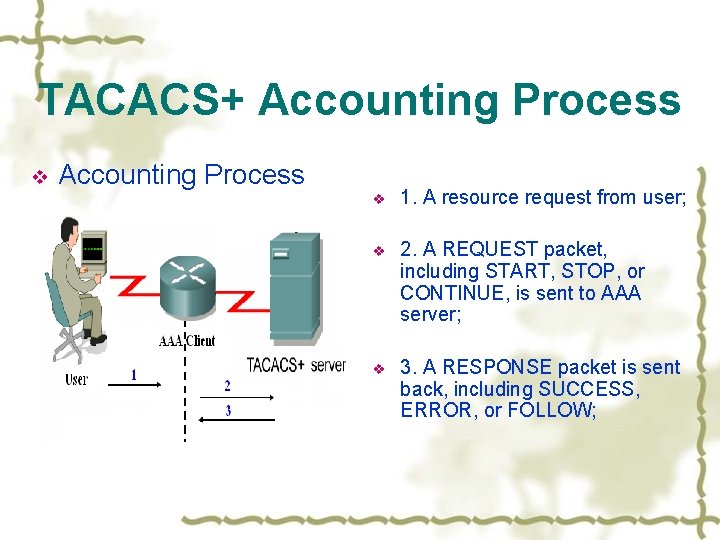
TACACS+ Accounting v follows the processes of authentication & authorization v maintains complete accounting information v used either for billing purposes of the services or for security reasons. v TACACS+ accounting also uses the two message types: a REQUEST and a REPONSE

TACACS+ Accounting Process v 1. A resource request from user; v 2. A REQUEST packet, including START, STOP, or CONTINUE, is sent to AAA server; v 3. A RESPONSE packet is sent back, including SUCCESS, ERROR, or FOLLOW;

Vulnerabilities of TACACS+

Lack of Integrity Checking v No integrity checking exists in TACACS+ v ‘MD 5 - encryption stream cipher’ mechanism is used. v Make changes to accounting packets. Example: Modifying elapsed time from 8000 to 1000

2) Vulnerability to replay attacks v No protection against replay attacks. v TACACS+ session starts with sequence number 1. v Accounting sessions have only one packet. v Duplicate accounting records can be produced, with forged task_id fields.

3) Session ID collision v v More unique IDs the more stronger the encryption is. Multiple sessions get the same ID, leading to frequency analysis attack. Plaintext of one session know leads to decrypt the other session with the same sequence and session ID. TACACS+ server encrypts reply packet with own session ID. (Mostly when the sequence number of the packet is 2).

4) The Birthday paradox v Session IDs are too small. v Leads to less unique IDs. Example: 100, 000 TACAS+ sessions 20, 000 dial up sessions 1000 matches per moth Few 100 user passwords.

5) Lack of Padding v No padding in any fields or end of the packet. v Variable size data fields determined from the packet sizes. v Reveals the length of the user passwords.

6) MD 5 Context Leak v v v Theoretical vulnerability MD 5 - like hashes(16 bytes long) should be avoided. TACACS+ packets encrypted by XOR’ing the MD 5 hashes. MD 5_1=MD 5(session_id, key, version, seq_no) MD 5_2=MD 5(session_id, key, version, seq_no, MD 5_1)

7) Do. S and/or Overflow v Denial of Service – attempt to make resources unavailable to intended users. v Unlike others, it is an implementation defect. v No sanity check v Not check for an integer overflow in calculating the total memory size to allocate.

FIXES v Apply Packet Filtering v Choose Strong Encryption Keys v Avoid running tac_plus as root.

Conclusion v v TACACS+ is a Cisco Proprietary protocol facilitating AAA model in Cisco Devices. It provides AAA communication between AAA client and AAA server. It improves on TACACS and XTACACS by separating the authentication, authorization and accounting. More preferred since it uses TCP- reliable protocol.
![Reference v v 1 The TACACS Protocol Version 1 78 by D Carrel Lol Reference v v [1] “The TACACS+ Protocol”, Version 1. 78. by D. Carrel, Lol](https://slidetodoc.com/presentation_image/126eea7400c17d7934b38da262050a64/image-21.jpg)
Reference v v [1] “The TACACS+ Protocol”, Version 1. 78. by D. Carrel, Lol Grant, Cisco Systems, January, 1997. http: //tools. ietf. org/html/draft-grant-tacacs-02 [2] “TACACS+ Protocol”, Version 1. 76. by D. Carrel, Lol Grant, Cisco Systems, October, 1996. http: //www. cisco. com/warp/public/459/tac-rfc. 1. 76. txt [3] Cisco Access Control Security: AAA Administrative Services, by Brandon Carroll. May 27, 2004 [4] “TACACS+ Authentication for HTTP Server Users” http: //www. cisco. com/warp/public/480/http-2. html [5] “TACACS+ and RADIUS Comparison”. http: //www. cisco. com/warp/public/480/10. html

Q & A? v Thanks!