Vigor Pro 100 Unified Security Firewall Dray Tek














- Slides: 54

Vigor. Pro 100 Unified Security Firewall Dray. Tek Corp. Confidential

Agenda n n n UTM Vigor. Pro 100: Unified Security Firewall Web Portal and Service Flow Competition Analysis Live Demo Confidential

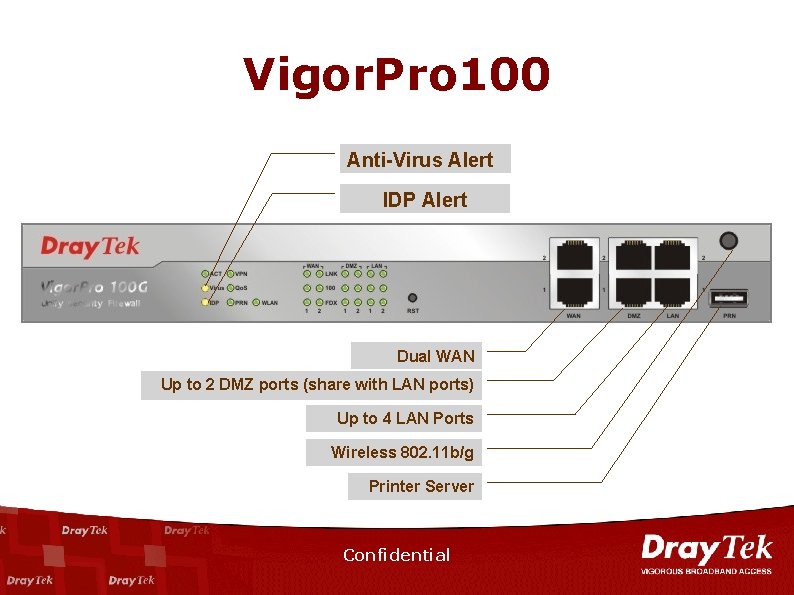
Vigor. Pro 100 Anti-Virus Alert IDP Alert Dual WAN Up to 2 DMZ ports (share with LAN ports) Up to 4 LAN Ports Wireless 802. 11 b/g Printer Server Confidential

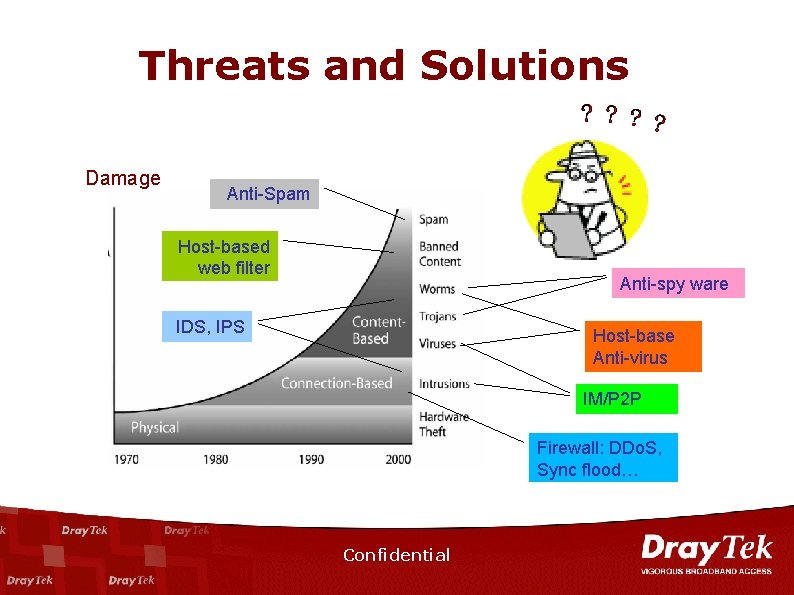
Threats and Solutions Damage Anti-Spam Host-based web filter Anti-spy ware IDS, IPS Host-base Anti-virus IM/P 2 P Firewall: DDo. S, Sync flood… Confidential

Firewall n Restrict access to certain, IP, ports or services that administrator does not want unauthorized people do – Packet filter • Network level • Source/destination IP, source/destination port(TCP/UDP) (L 3/L 4) – Application gateway (proxy server) • Host using various forms of proxy servers to proxy traffics instead of routing it • Capable of inspect the content(L 7) Confidential

NIDS Confidential

NIDS n n NIDS can detect unsuccessful attack by anomalous protocol or traffic behavior Signature: specific patterns base on known vulnerabilities or exploits Confidential

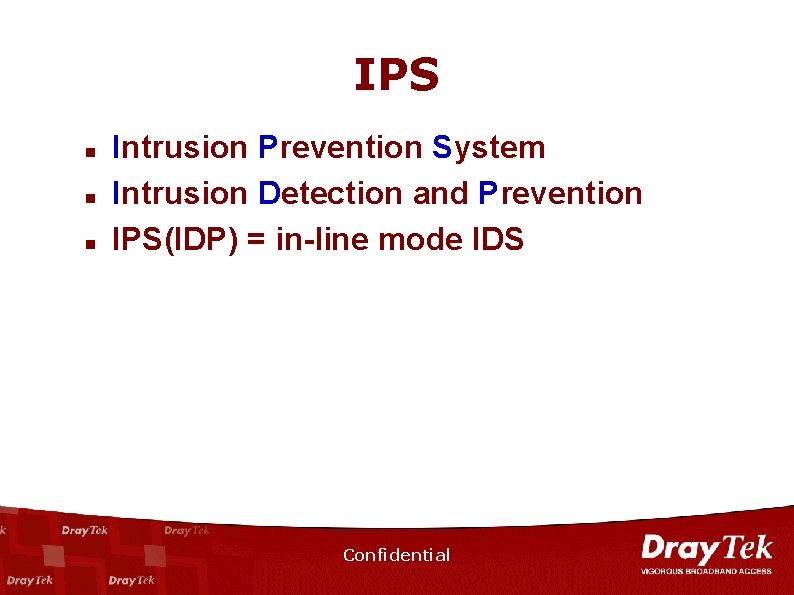
IPS n n n Intrusion Prevention System Intrusion Detection and Prevention IPS(IDP) = in-line mode IDS Confidential

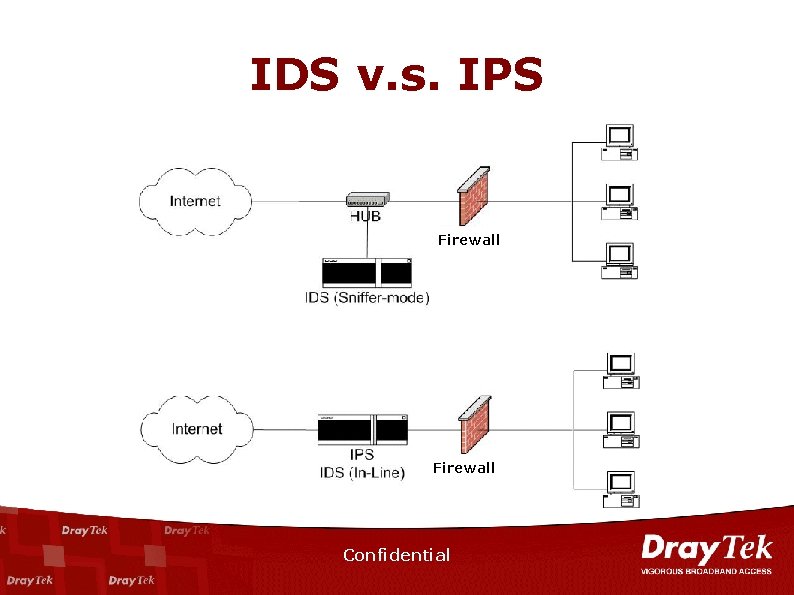
IDS v. s. IPS Firewall Confidential

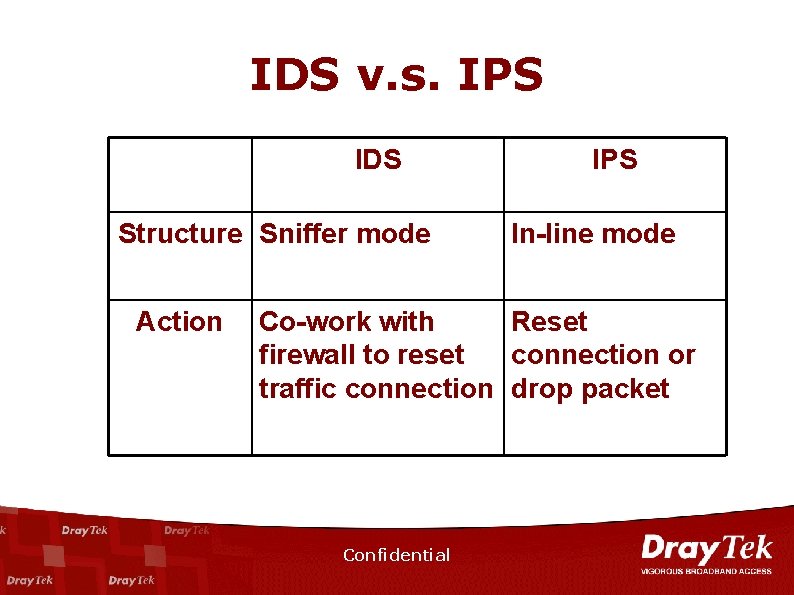
IDS v. s. IPS IDS Structure Sniffer mode Action IPS In-line mode Co-work with Reset firewall to reset connection or traffic connection drop packet Confidential

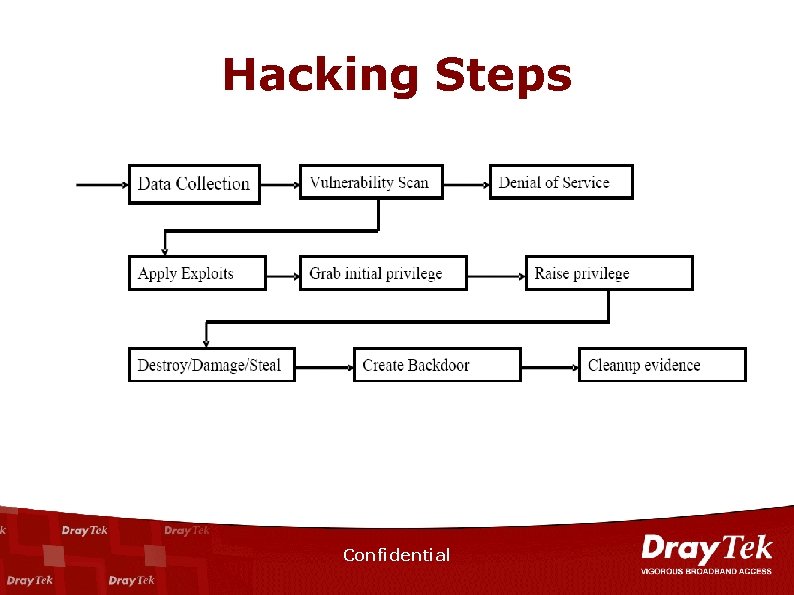
Hacking Steps Confidential

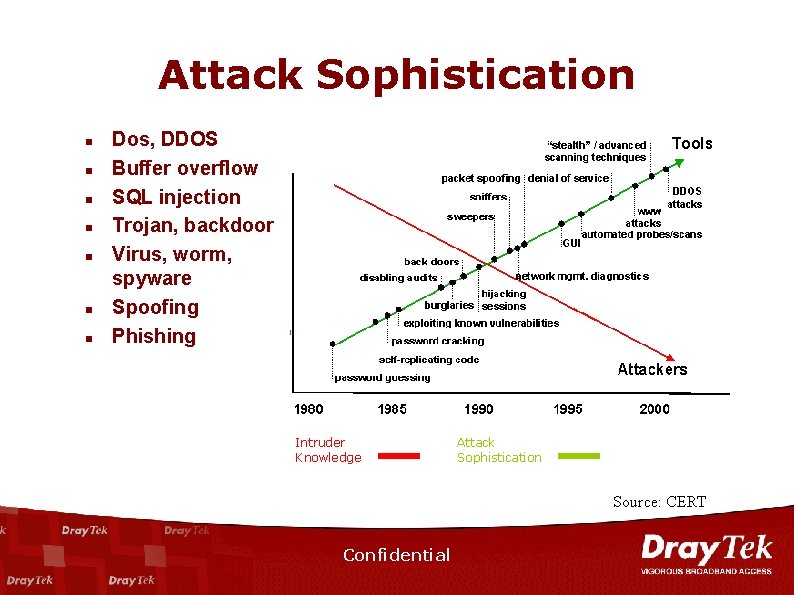
Attack Sophistication n n n Dos, DDOS Buffer overflow SQL injection Trojan, backdoor Virus, worm, spyware Spoofing Phishing Intruder Knowledge Attack Sophistication Source: CERT Confidential

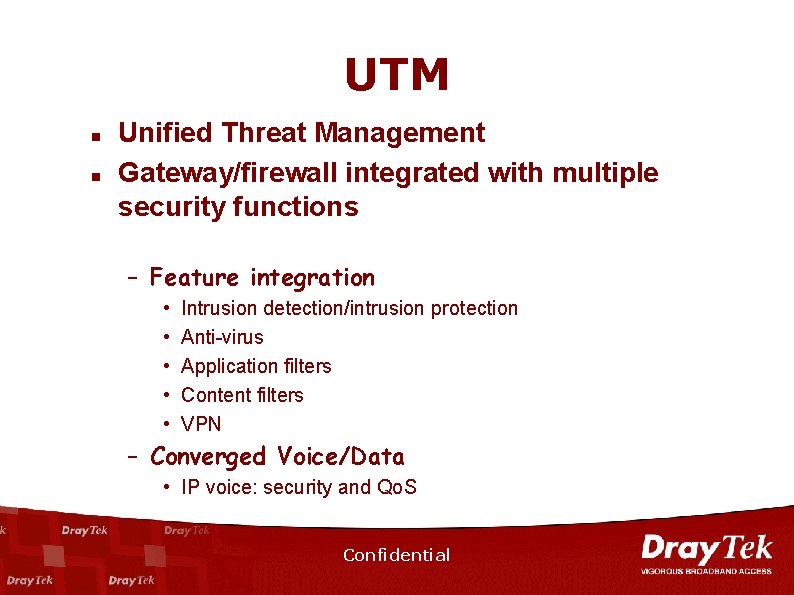
UTM n n Unified Threat Management Gateway/firewall integrated with multiple security functions – Feature integration • • • Intrusion detection/intrusion protection Anti-virus Application filters Content filters VPN – Converged Voice/Data • IP voice: security and Qo. S Confidential

Why UTM n More add-on value – Integrated functionality, all-in-one – Network level protection n Reduce management efforts – Separate device: independent logging and multiple GUI – Easy configuration & management – Easy troubleshooting – ……… ……. . Confidential

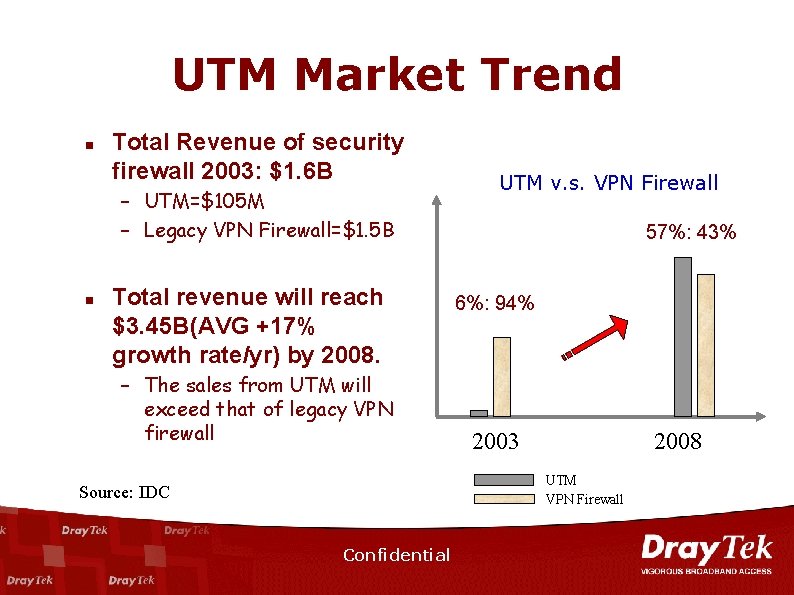
UTM Market Trend n Total Revenue of security firewall 2003: $1. 6 B – UTM=$105 M – Legacy VPN Firewall=$1. 5 B n Total revenue will reach $3. 45 B(AVG +17% growth rate/yr) by 2008. – The sales from UTM will exceed that of legacy VPN firewall UTM v. s. VPN Firewall 57%: 43% 6%: 94% 2003 2008 UTM VPN Firewall Source: IDC Confidential

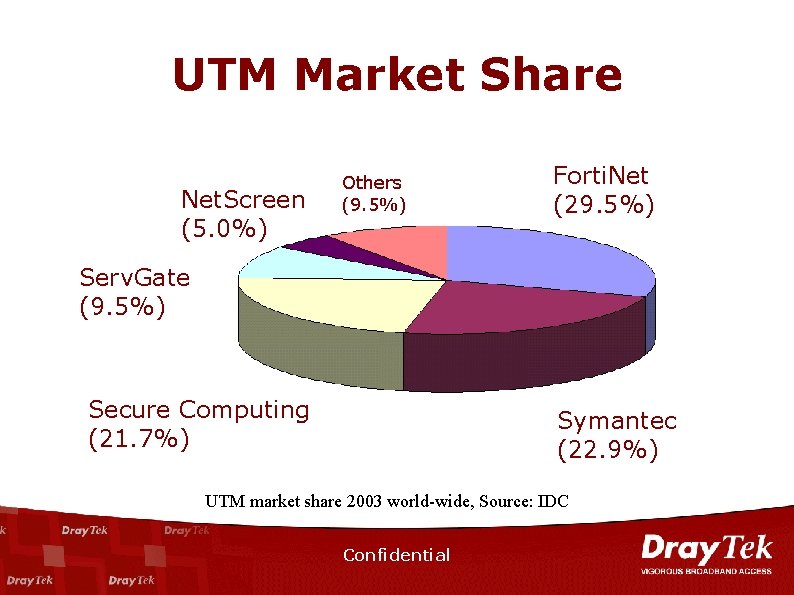
UTM Market Share Net. Screen (5. 0%) Others (9. 5%) Forti. Net (29. 5%) Serv. Gate (9. 5%) Secure Computing (21. 7%) Symantec (22. 9%) UTM market share 2003 world-wide, Source: IDC Confidential

n n n UTM Vigor. Pro 100: Unified Security Firewall Web Portal and Service Flow Competition Analysis Live Demo Confidential

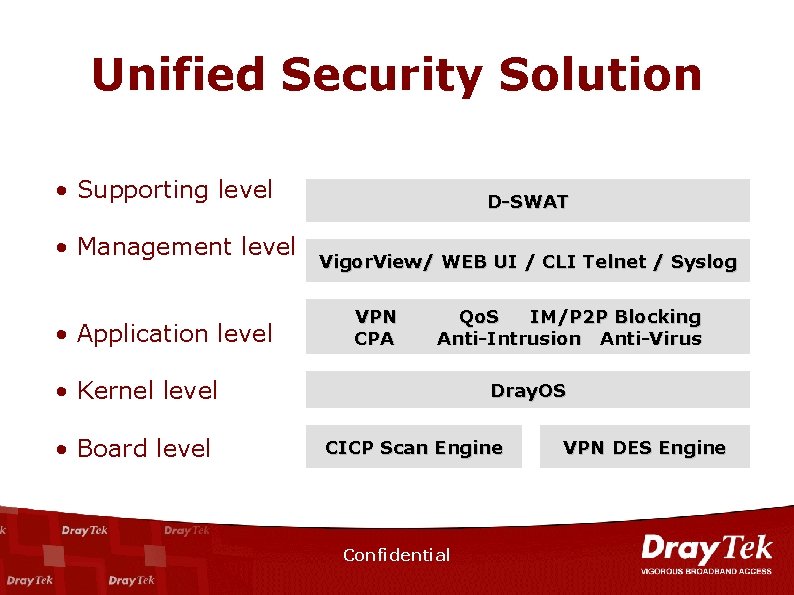
Unified Security Solution • Supporting level • Management level • Application level D-SWAT Vigor. View/ WEB UI / CLI Telnet / Syslog VPN CPA Qo. S IM/P 2 P Blocking Anti-Intrusion Anti-Virus • Kernel level • Board level Dray. OS CICP Scan Engine Confidential VPN DES Engine

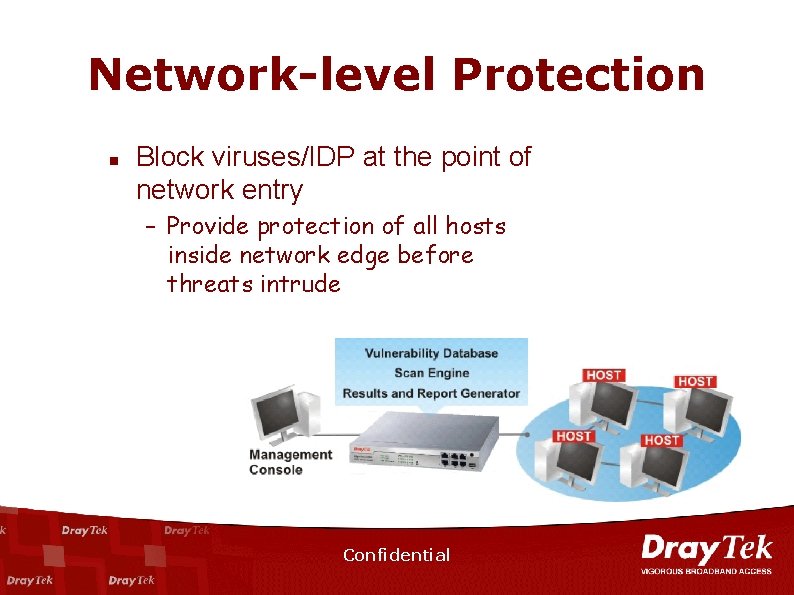
Network-level Protection n Block viruses/IDP at the point of network entry – Provide protection of all hosts inside network edge before threats intrude Confidential

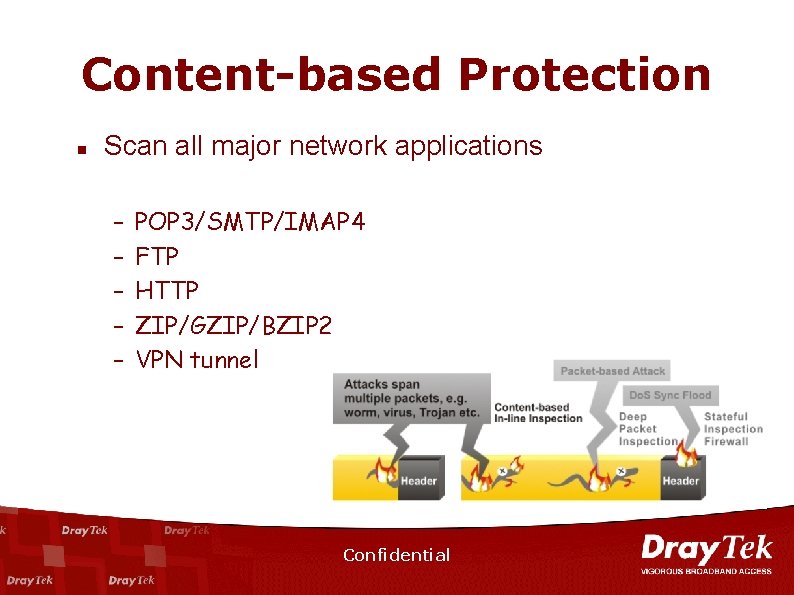
Content-based Protection n Scan all major network applications – – – POP 3/SMTP/IMAP 4 FTP HTTP ZIP/GZIP/BZIP 2 VPN tunnel Confidential

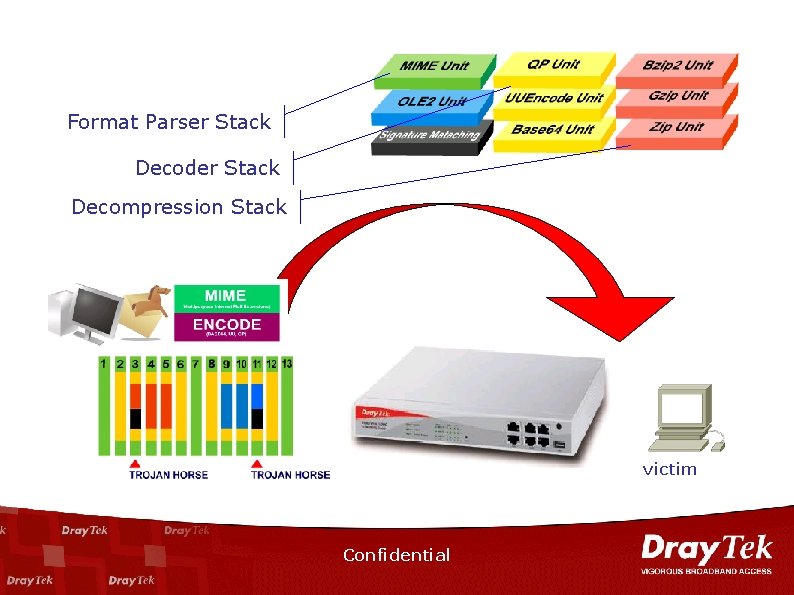
MSSI n MSSI™(Multi-Stack Stateful Inspection) – The patent-pending technology developed by Dray. Tek – Inline scanning – No proxy: scan on the fly, real-time response – Cross packets inspection – No file size limitation ** The methodology of proxy-based virus scanning is a patent of Trend. Micro http: //www. trendmicro. com/en/about/news/pr/archive/2005/pr 080905. htm Confidential

Format Parser Stack Decoder Stack Decompression Stack victim Confidential

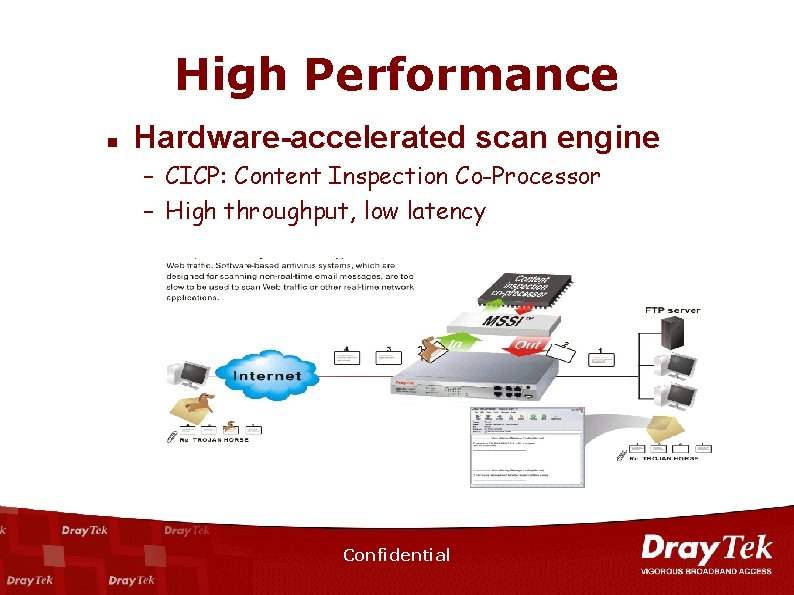
High Performance n Hardware-accelerated scan engine – CICP: Content Inspection Co-Processor – High throughput, low latency Confidential

IM/P 2 P n IM(Instant Message)/P 2 P(Peer-to-Peer) – Application to deliver text, document, picture, audio, web-phone, conference… through internet n n IM: MSN, Yahoo messenger, ICQ… P 2 P: e. Mule, Edonkey, Kaza. A, Bit Torrent, Skype Confidential

IM/P 2 P in Business n Pros – Instant and efficient communication or conference – Freeware, free rate n Cons – Reduce productivity: employees use it for personal purpose during business hour – Security hole • Virus, worms, spyware • Confidential material or information could be easily disclosed – P 2 P file-sharing ware against law in some countries – Waste bandwidth Confidential

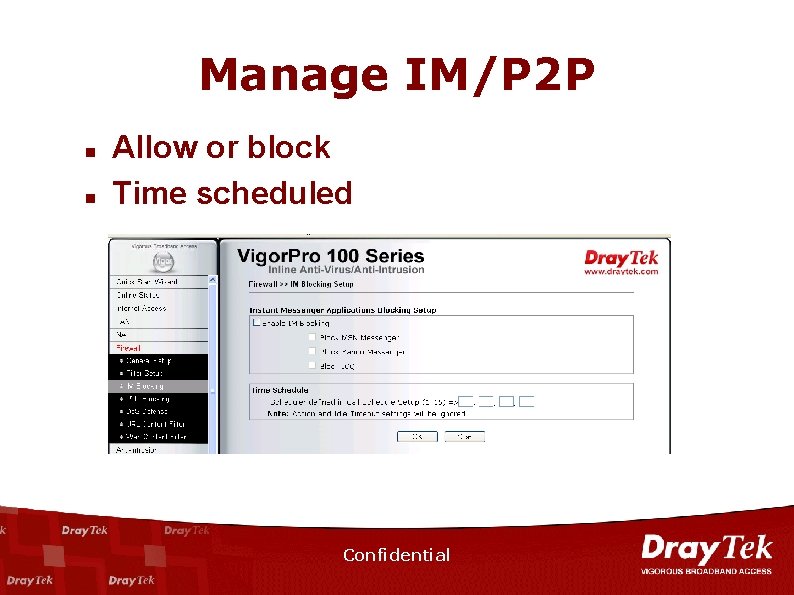
Manage IM/P 2 P n n Allow or block Time scheduled Confidential

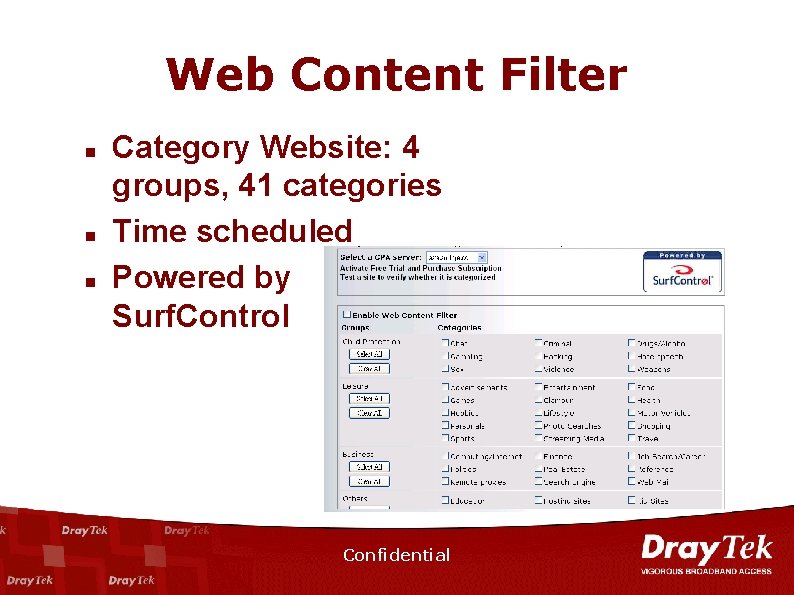
Web Content Filter n Manage internet access, prevent internet misuse – Make the network away from gaming, chat room, porno, file-sharing … website – Improve employee productivity – Reduce the risk of legal liability as result of improper internet activity Confidential

Web Content Filter n n n Category Website: 4 groups, 41 categories Time scheduled Powered by Surf. Control Confidential

Dual WAN n n Load balance: share the internet traffic Bandwidth fail-over Bandwidth On Demand Configurable internet access mode: PPPo. E, DHCP client, Static IP and PPTP Confidential

Lower TCO n Total Cost of Ownership – The all-in-one unified security firewall – Multi-functionality, single IP management • Too complicated to manage discrete network components • All functionality can be managed and troubleshooting remotely • no IT personnel truck-roll required – D-SWAT Confidential

n n n UTM Vigor. Pro 100: Unified Security Firewall Web Portal and Service Flow Competition Analysis Live Demo Confidential

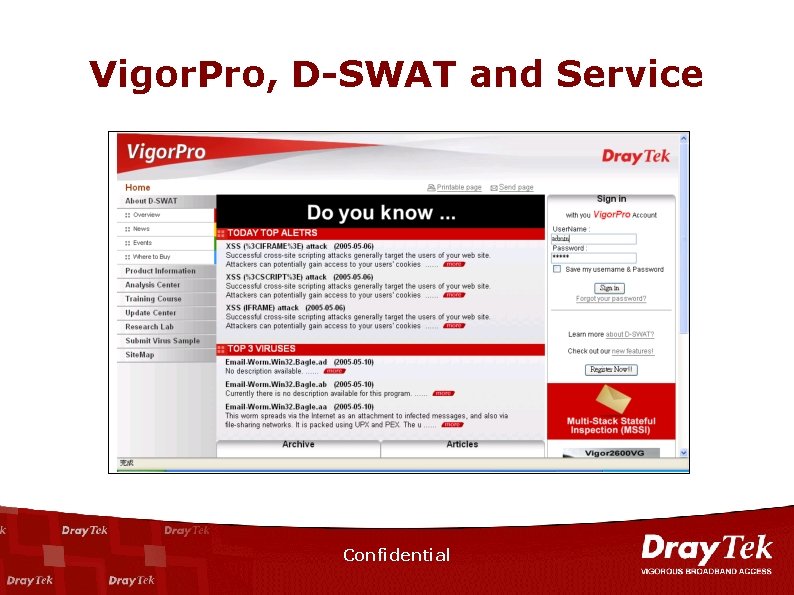
Vigor. Pro, D-SWAT and Service Confidential

D-SWAT n n The Dray. Tek Security Warning and Anti-attack Team Research –Hacking technique analysis –Virus sample collection & analysis –Exploit collection & analysis n Service –Security portal website –Virus signature update –Security advisories –News letter § Training –Hacking Techniques –Incident handling Confidential

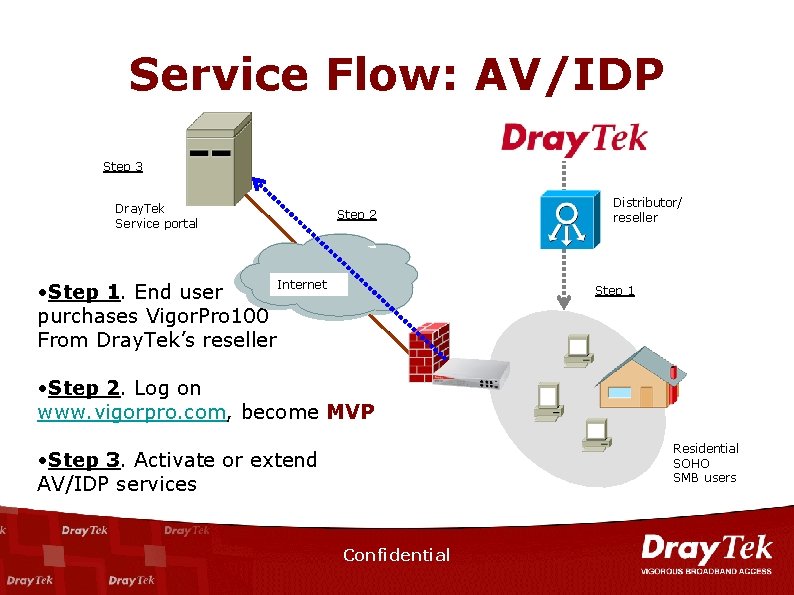
Service Flow: AV/IDP Step 3 Dray. Tek Service portal • Step 1. End user purchases Vigor. Pro 100 From Dray. Tek’s reseller Step 2 Internet Distributor/ reseller Step 1 • Step 2. Log on www. vigorpro. com, become MVP Residential SOHO SMB users • Step 3. Activate or extend AV/IDP services Confidential

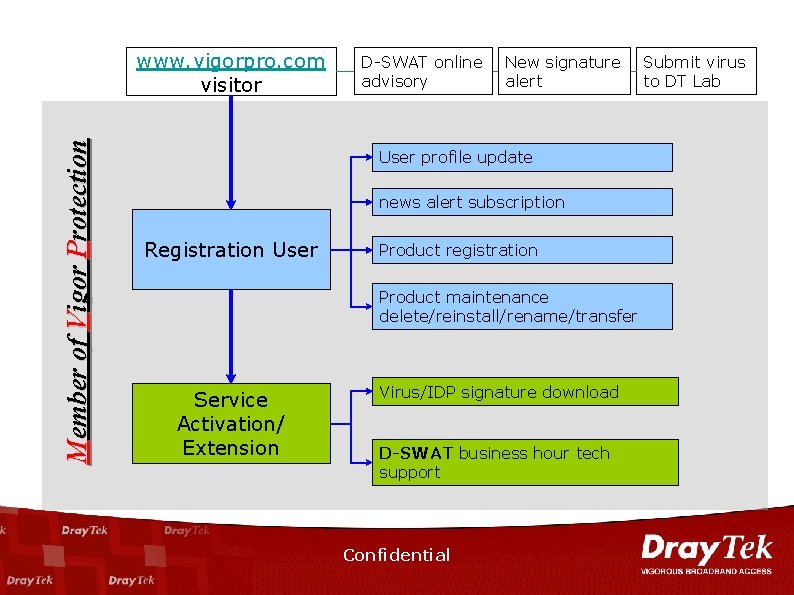
Member of Vigor Protection www. vigorpro. com visitor D-SWAT online advisory New signature alert User profile update news alert subscription Registration User Product registration Product maintenance delete/reinstall/rename/transfer Service Activation/ Extension Virus/IDP signature download D-SWAT business hour tech support Confidential Submit virus to DT Lab

Member of Vigor Protection Want to Become Dray. Tek’s MVP ? ? Visit www. vigorpro. com and registration Confidential

Get Your Network Protected by Becoming Dray. Tek’s MVP n Knowledge Center for network threat – Online threat advisory by D-SWAT – Online virus, exploit analysis – Most updated news alert n Extended service: AV/IDP/Web Content Filter – – Product registration and maintenance Service activation Service extension Dedicated tech support by D-SWAT Confidential

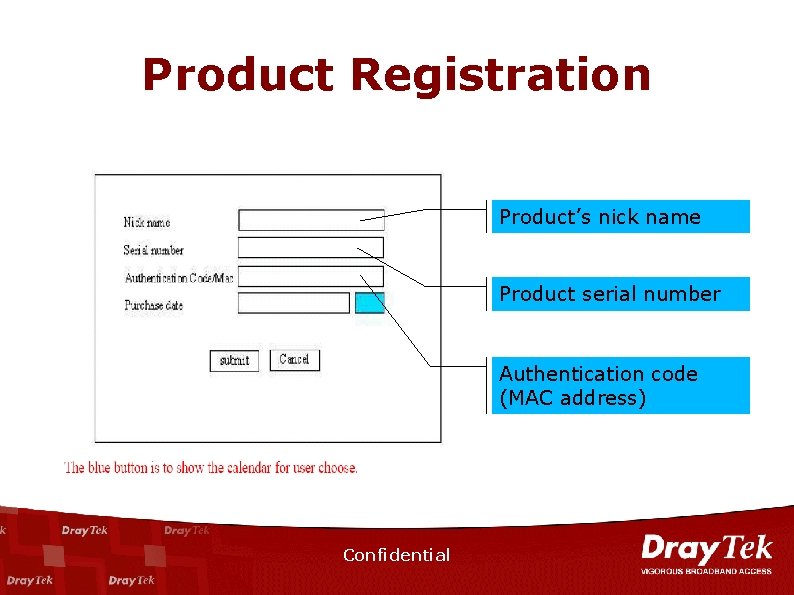
Product Registration Product’s nick name Product serial number Authentication code (MAC address) Confidential

Product Maintenance Confidential

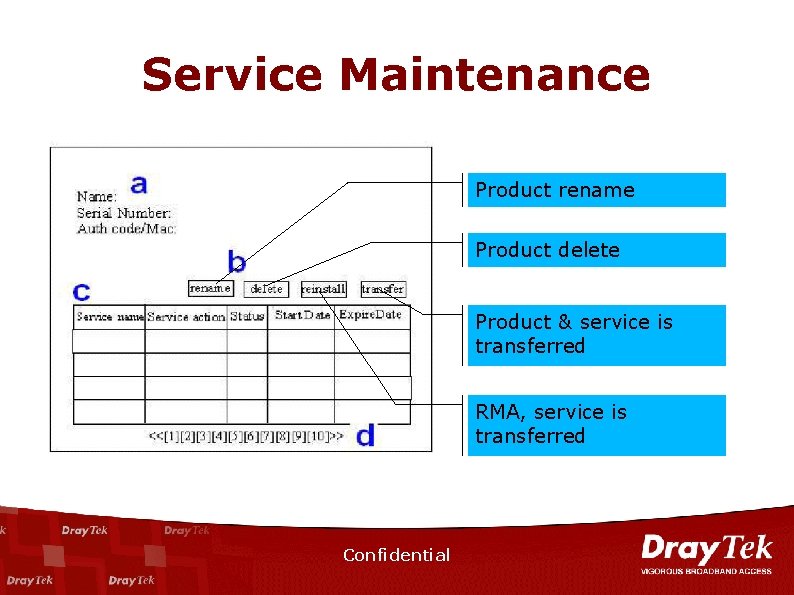
Service Maintenance Product rename Product delete Product & service is transferred RMA, service is transferred Confidential

Beta Program n n Beta sample availability: now Firmware: v 2. 6. 0_rc 6 or above Signature: Dray. Tek in house www. vigorpro. com MVP beta: – Provide AV/IDP license key for beta signature download – The MAC address needs to be stored in Dray. Tek’s server prior to get Vigor. Pro 100 registered n Beta issue: vigorpro 100 -beta@draytek. com Confidential

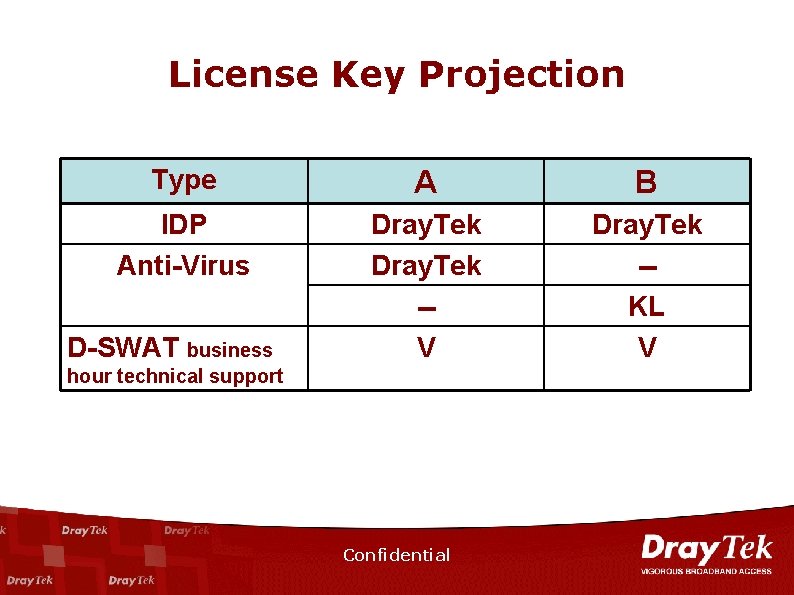
License Key Projection Type A B IDP Anti-Virus Dray. Tek -V Dray. Tek -KL V D-SWAT business hour technical support Confidential

n n n UTM Vigor. Pro 100: Unified Security Firewall Web Portal and Service Flow Competition Analysis Live Demo Confidential

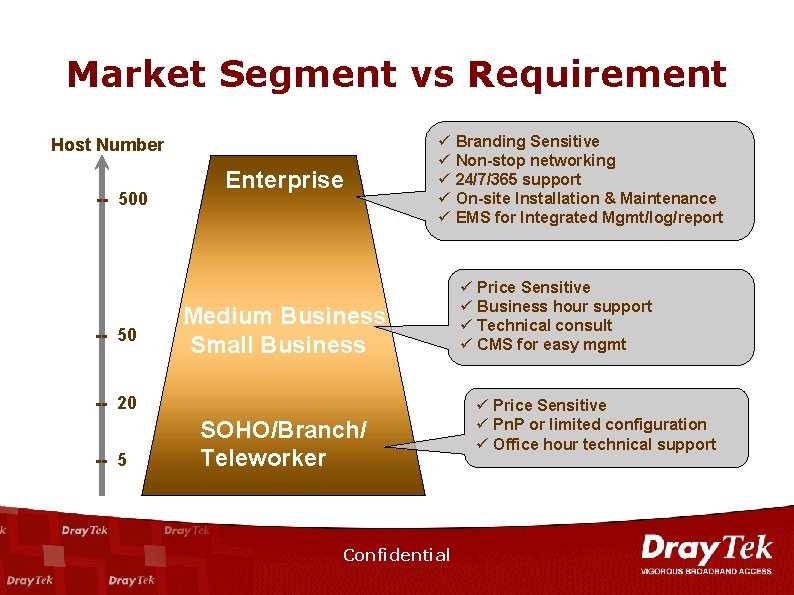
Market Segment vs Requirement Host Number -- 500 -- 50 Enterprise ü Branding Sensitive ü Non-stop networking ü 24/7/365 support ü On-site Installation & Maintenance ü EMS for Integrated Mgmt/log/report Medium Business Small Business -- 20 -- 5 SOHO/Branch/ Teleworker Confidential ü Price Sensitive ü Business hour support ü Technical consult ü CMS for easy mgmt ü Price Sensitive ü Pn. P or limited configuration ü Office hour technical support

Confidential

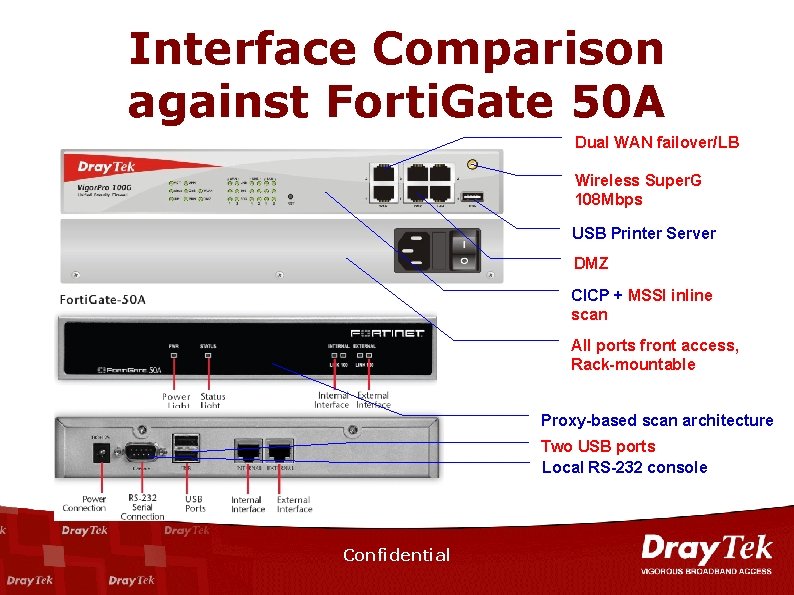
Interface Comparison against Forti. Gate 50 A Dual WAN failover/LB Wireless Super. G 108 Mbps USB Printer Server DMZ CICP + MSSI inline scan All ports front access, Rack-mountable Proxy-based scan architecture Two USB ports Local RS-232 console Confidential

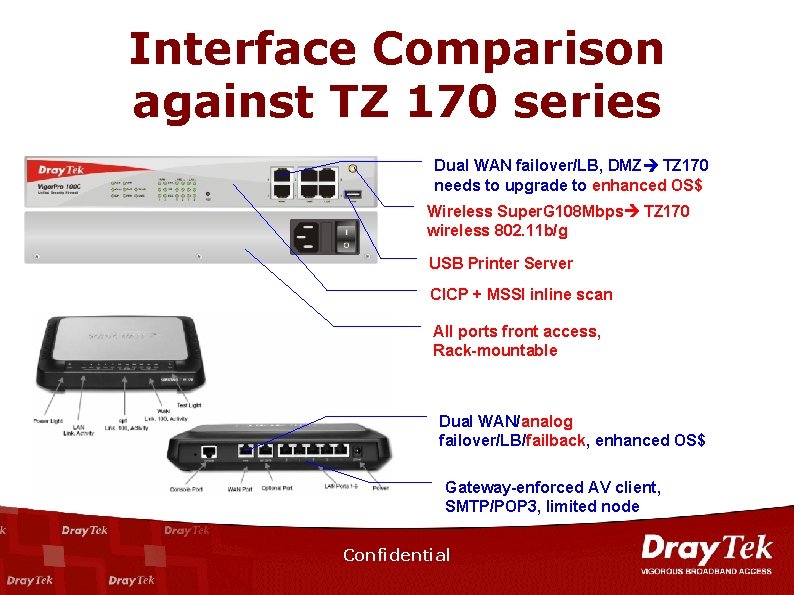
Interface Comparison against TZ 170 series Dual WAN failover/LB, DMZ TZ 170 needs to upgrade to enhanced OS$ Wireless Super. G 108 Mbps TZ 170 wireless 802. 11 b/g USB Printer Server CICP + MSSI inline scan All ports front access, Rack-mountable Dual WAN/analog failover/LB/failback, enhanced OS$ Gateway-enforced AV client, SMTP/POP 3, limited node Confidential

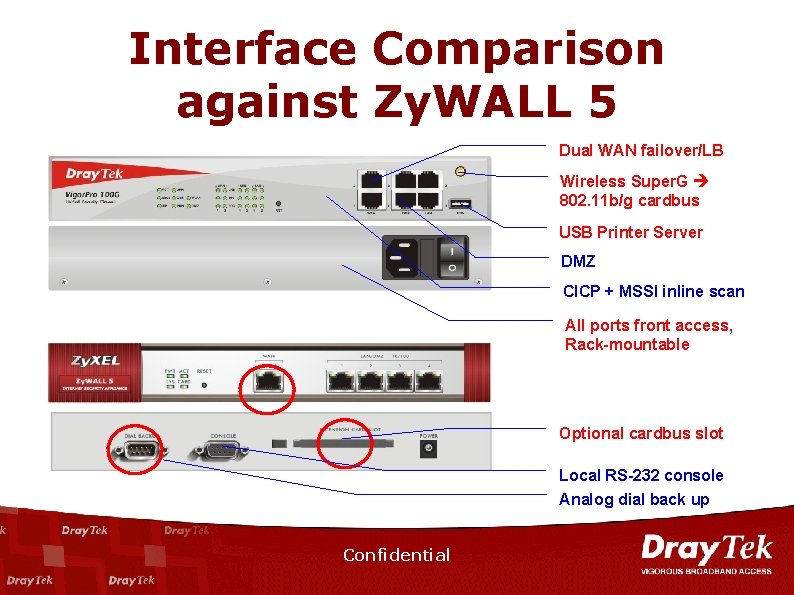
Interface Comparison against Zy. WALL 5 Dual WAN failover/LB Wireless Super. G 802. 11 b/g cardbus USB Printer Server DMZ CICP + MSSI inline scan All ports front access, Rack-mountable Optional cardbus slot Local RS-232 console Analog dial back up Confidential

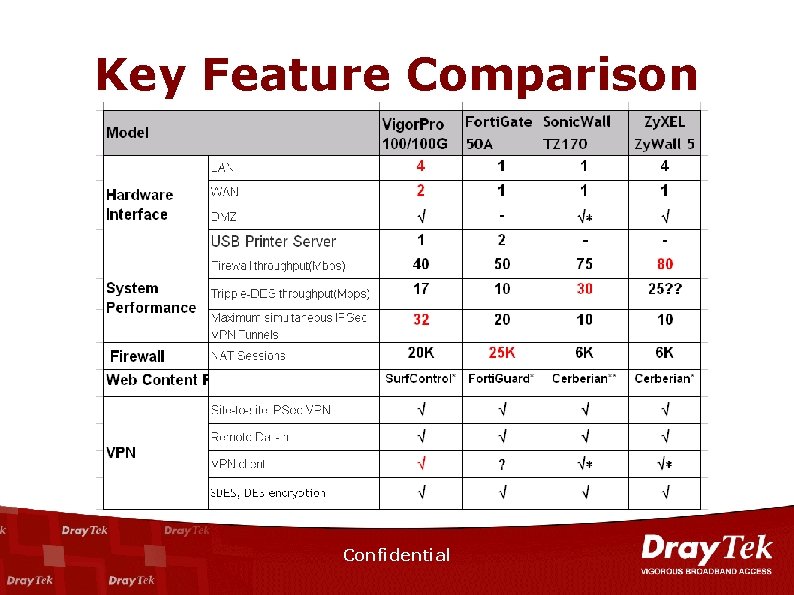
Key Feature Comparison Confidential

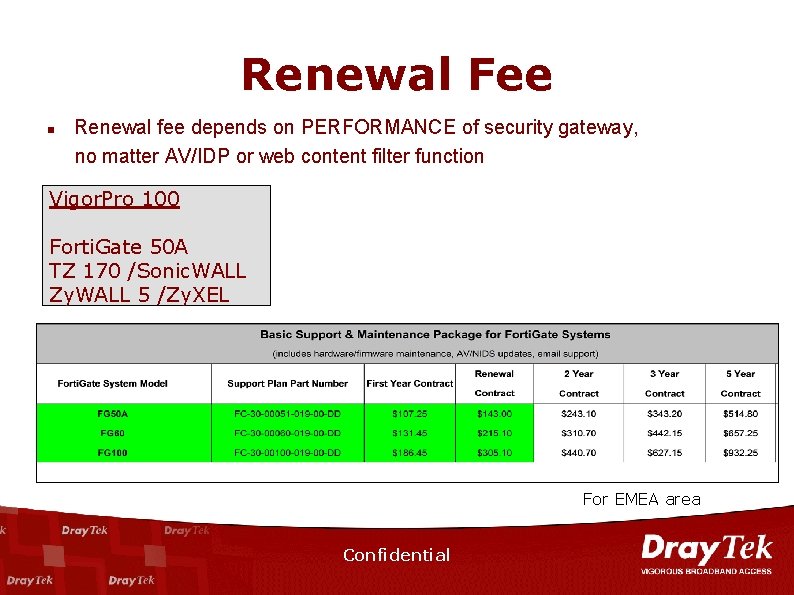
Renewal Fee n Renewal fee depends on PERFORMANCE of security gateway, no matter AV/IDP or web content filter function Vigor. Pro 100 Forti. Gate 50 A TZ 170 /Sonic. WALL Zy. WALL 5 /Zy. XEL For EMEA area Confidential

TCO: Take TZ 170 as Example Confidential

TCO Index – – – Host number supported Feature enhancement via OS update Signature: AV, IDP Web content filter VPN client Supporting and maintenance Confidential

Victim 172. 16. 3. 136 Attacker 192. 168. 1. 10 Confidential

END Confidential