The TCPIP Protocol 1 Introduction To TCPIP Transmission




















- Slides: 77

The TCP/IP Protocol 1

Introduction To TCP/IP • Transmission Control Protocol/Internet Protocol (TCP/IP) – – Most commonly used network protocol suite today Wide vendor support Open protocol Provides access to Internet services • Windows Server 2003 – Can use several protocols – Many of its main features require the use of TCP/IP 2

Internet History 1961 -1972: Early packet-switching principles • 1961: Kleinrock - queueing theory shows ` effectiveness of packet-switching • 1964: Baran - packet-switching in military nets • 1967: ARPAnet conceived by Advanced Research Projects Agency • 1969: first ARPAnet node operational • 1972: ARPAnet demonstrated publicly, NCP (Network Control Protocol) first host-host protocol, first email program. ARPAnet has 15 nodes 3

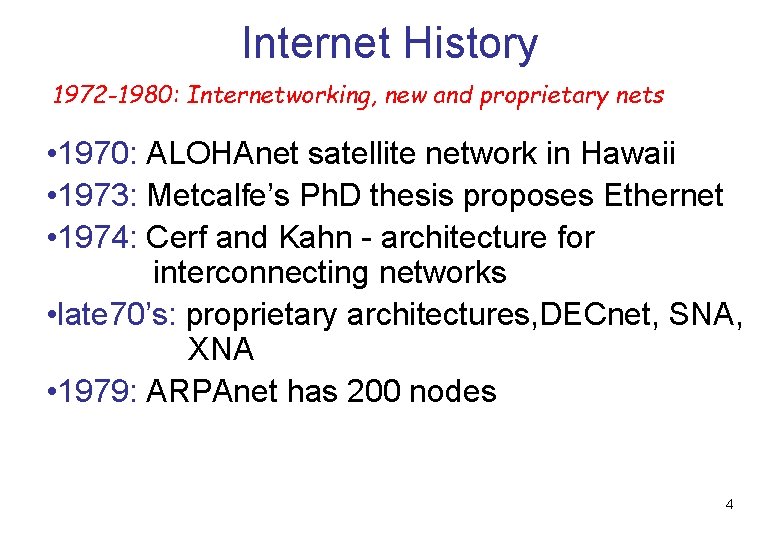
Internet History 1972 -1980: Internetworking, new and proprietary nets • 1970: ALOHAnet satellite network in Hawaii • 1973: Metcalfe’s Ph. D thesis proposes Ethernet • 1974: Cerf and Kahn - architecture for interconnecting networks • late 70’s: proprietary architectures, DECnet, SNA, XNA • 1979: ARPAnet has 200 nodes 4

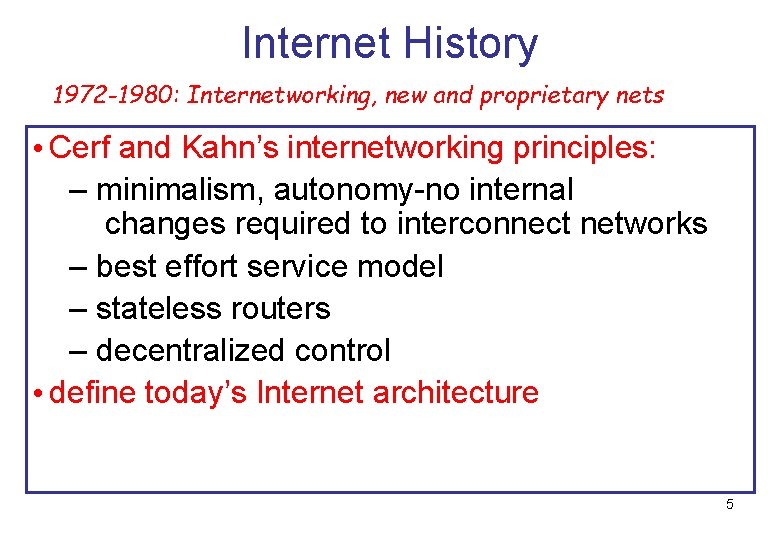
Internet History 1972 -1980: Internetworking, new and proprietary nets • Cerf and Kahn’s internetworking principles: – minimalism, autonomy-no internal changes required to interconnect networks – best effort service model – stateless routers – decentralized control • define today’s Internet architecture 5

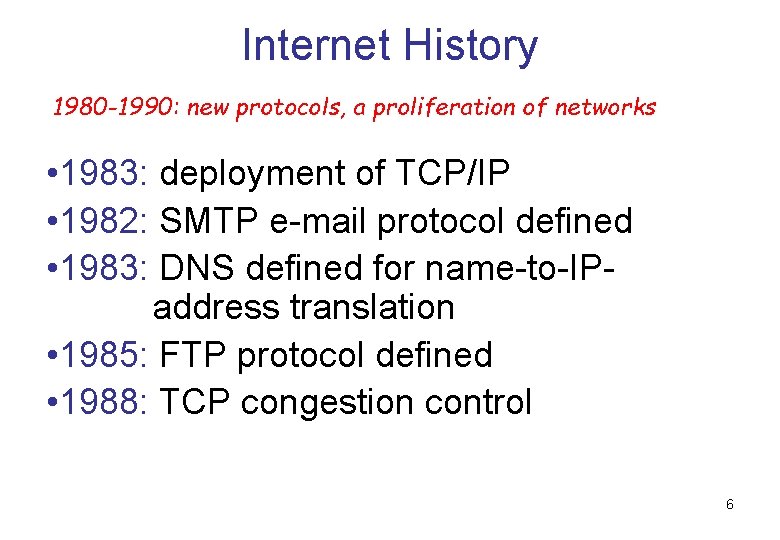
Internet History 1980 -1990: new protocols, a proliferation of networks • 1983: deployment of TCP/IP • 1982: SMTP e-mail protocol defined • 1983: DNS defined for name-to-IPaddress translation • 1985: FTP protocol defined • 1988: TCP congestion control 6

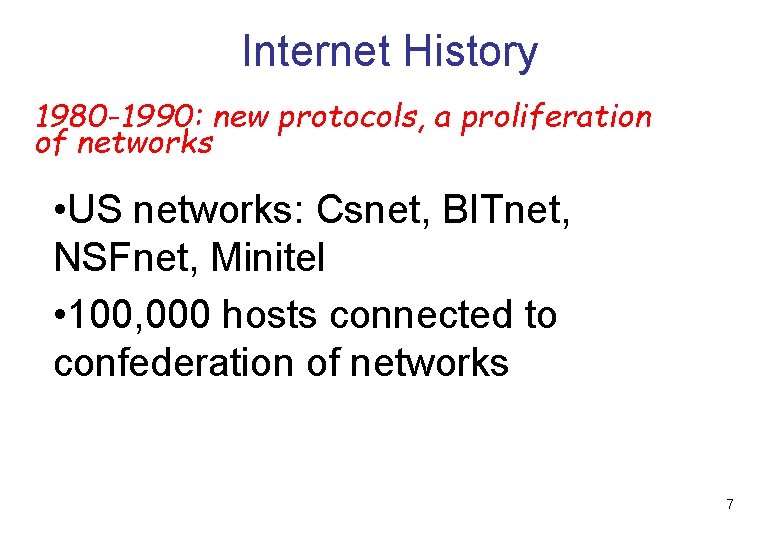
Internet History 1980 -1990: new protocols, a proliferation of networks • US networks: Csnet, BITnet, NSFnet, Minitel • 100, 000 hosts connected to confederation of networks 7

Internet History 1990, 2000’s: commercialization, the Web, new apps • Early 1990’s: ARPAnet decommissioned • 1991: NSF lifts restrictions on commercial use of NSFnet (decommissioned, 1995) • early 1990 s: Web –hypertext [Bush 1945, Nelson 1960’s] –HTML, HTTP: Berners-Lee – 1994: Mosaic, later Netscape –late 1990’s: commercialization of the Web 8

Internet History 1990, 2000’s: commercialization, the Web, new apps • Late 1990’s – 2000’s: • more killer apps: instant messaging, peer-2 -peer file sharing (e. g. , Naptser) • network security to forefront • est. 50 million host, 100 million+ users • backbone links running at Gbps • now: 10 -40 Gbps (youtube, social networking) 9

The (capital “I”) Internet § The world-wide network of TCP/IP networks § Different people or organisations own different parts § Different parts use different technologies § Interconnections between the parts § Interconnections require agreements § sale/purchase of service § contracts § “peering” agreements § No central control or management 10

The principle of “Internetworking” § We have lots of little networks § Many different owners/operators § Many different types § Ethernet, dedicated leased lines, dialup, optical, broadband, wireless, . . . § Each type has its own idea of low level addressing and protocols § We want to connect them all together and provide a unified view of the whole lot (treat the collection of networks as a single large internetwork) 11

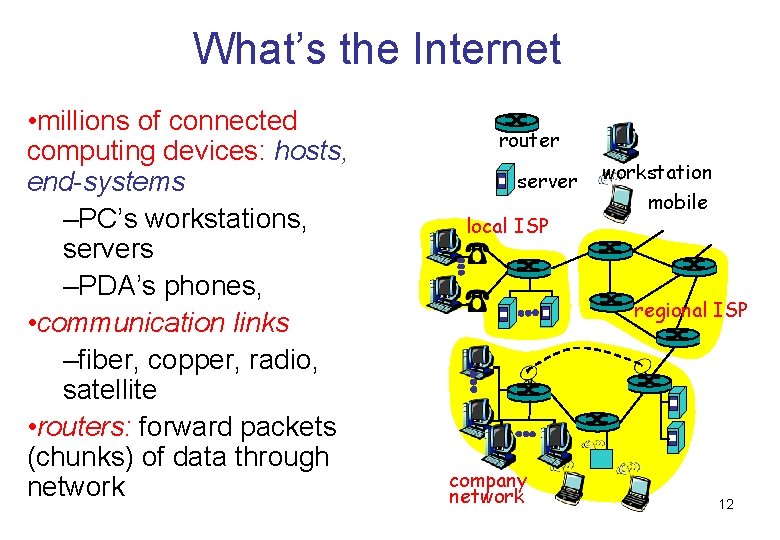
What’s the Internet • millions of connected computing devices: hosts, end-systems –PC’s workstations, servers –PDA’s phones, • communication links –fiber, copper, radio, satellite • routers: forward packets (chunks) of data through network router server local ISP workstation mobile regional ISP company network 12

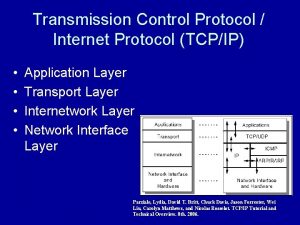
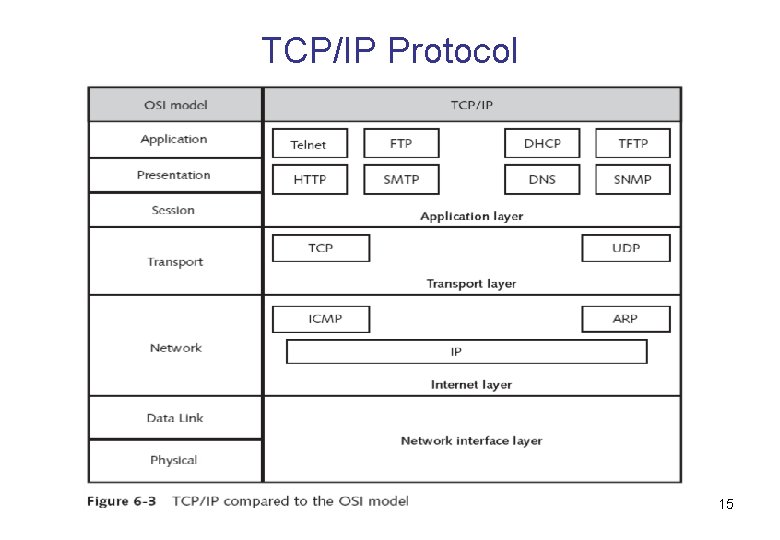
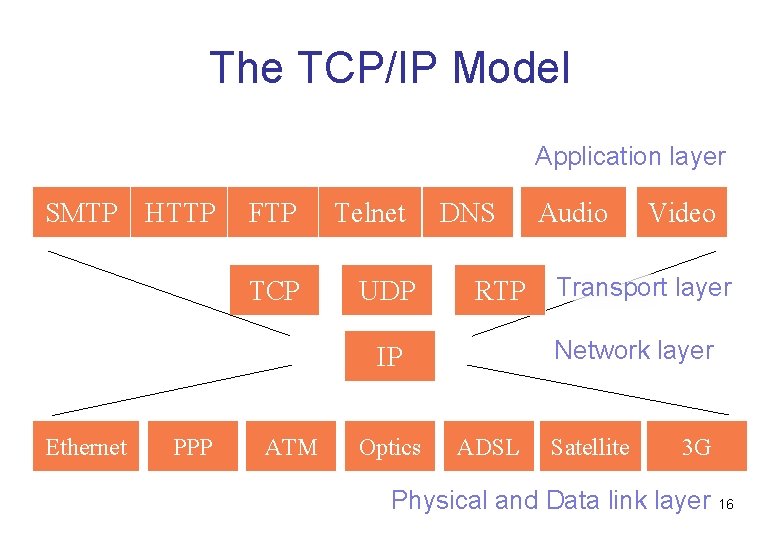
TCP/IP Architecture Overview • The TCP/IP model can be broken down into four layers: – Application – Transport – Internet – Physical Network Interface • Application layer provides access to network resources. It defines rules, commands, and procedures for client to talk to a service running on a server 13

TCP/IP Architecture Overview (continued) • Transport layer is responsible for preparing data ready to be transported across the network • Internet layer is responsible for logical addressing and routing • Physical Network Interface layer consists of the network card driver and the network card itself 14

TCP/IP Protocol 15

The TCP/IP Model Application layer SMTP HTTP FTP TCP Telnet UDP DNS RTP PPP ATM Optics Video Transport layer Network layer IP Ethernet Audio ADSL Satellite 3 G Physical and Data link layer 16

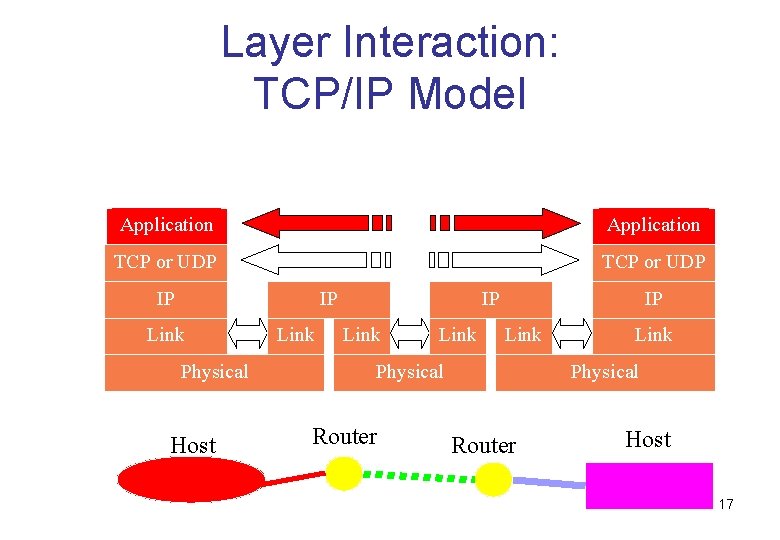
Layer Interaction: TCP/IP Model Application TCP or UDP IP IP Link Physical Host Link IP Link Physical Router Host 17

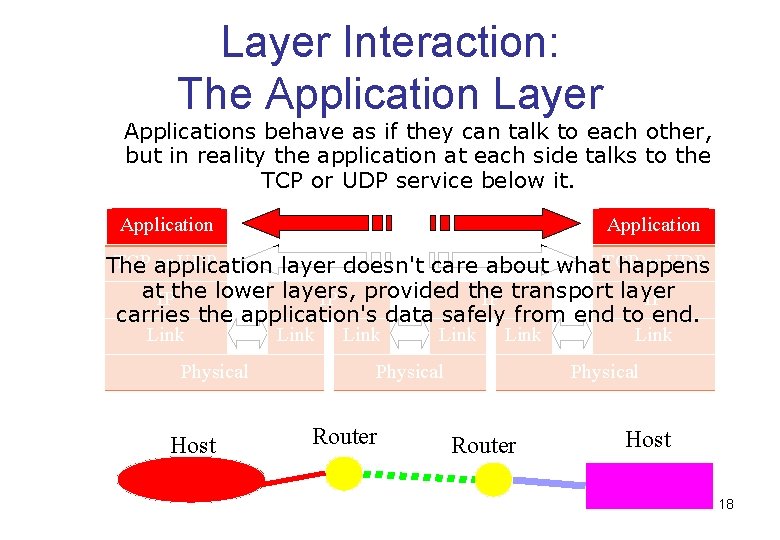
Layer Interaction: The Application Layer Applications behave as if they can talk to each other, but in reality the application at each side talks to the TCP or UDP service below it. Application TCP application or UDP The layer doesn't care about what. TCP happens at. IPthe lower layers, IP provided the IP transport layer IP carries the application's data safely from end to end. Link Physical Host Link Physical Router Link Physical Router Host 18

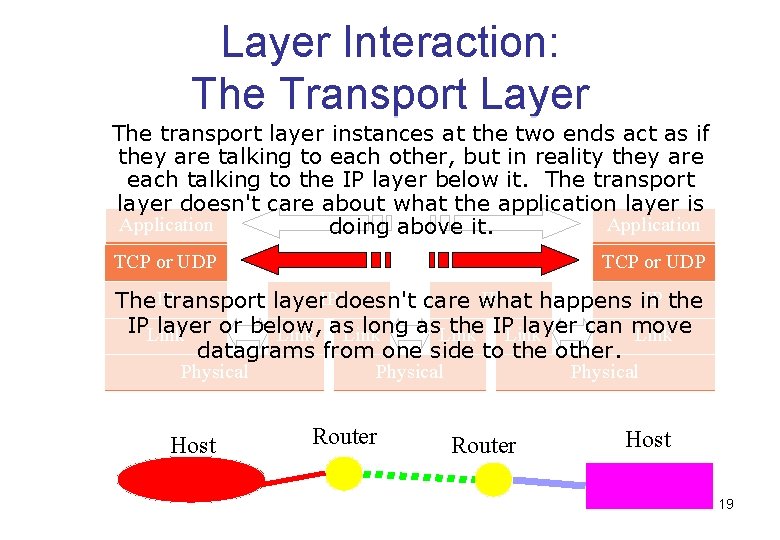
Layer Interaction: The Transport Layer The transport layer instances at the two ends act as if they are talking to each other, but in reality they are each talking to the IP layer below it. The transport layer doesn't care about what the application layer is Application doing above it. TCP or UDP IP IP the The IP transport layer. IPdoesn't care what happens in IPLink layer or below, long as. Link the IPLink layer can move Link as Link datagrams from one side to the other. Physical Host Physical Router Host 19

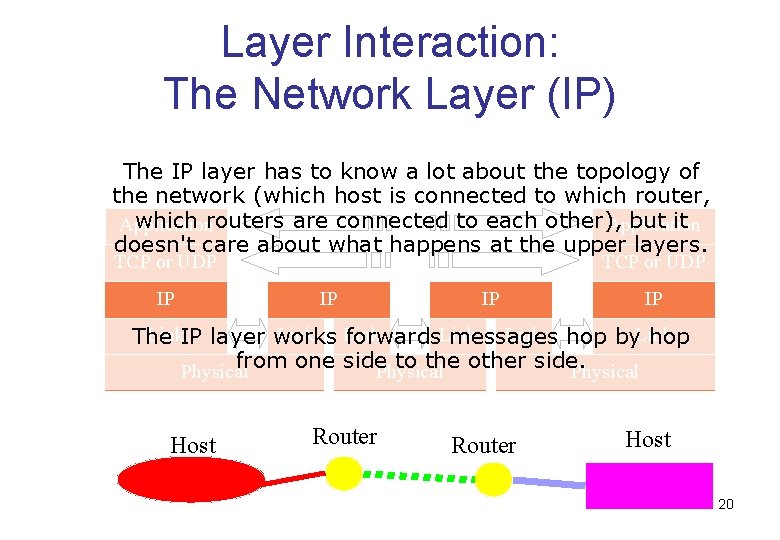
Layer Interaction: The Network Layer (IP) The IP layer has to know a lot about the topology of the network (which host is connected to which router, which routers are connected to each other), but it Application doesn't care about what happens at the upper layers. TCP or UDP IP IP IP Link. IP layer works Link hop by. Link The forwards. Link messages hop from one side to the other side. Physical Host Router Host 20

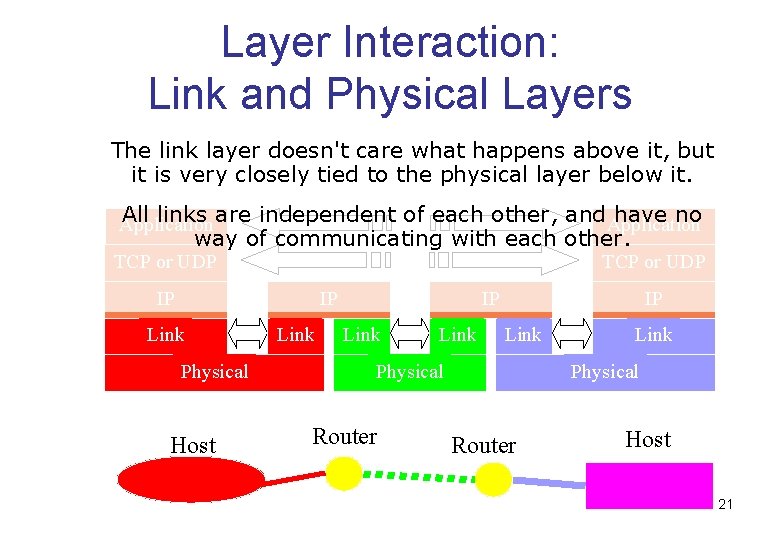
Layer Interaction: Link and Physical Layers The link layer doesn't care what happens above it, but it is very closely tied to the physical layer below it. All links are independent of each other, and. Application have no Application way of communicating with each other. TCP or UDP IP IP Link Physical Host Link IP Link Physical Router Host 21

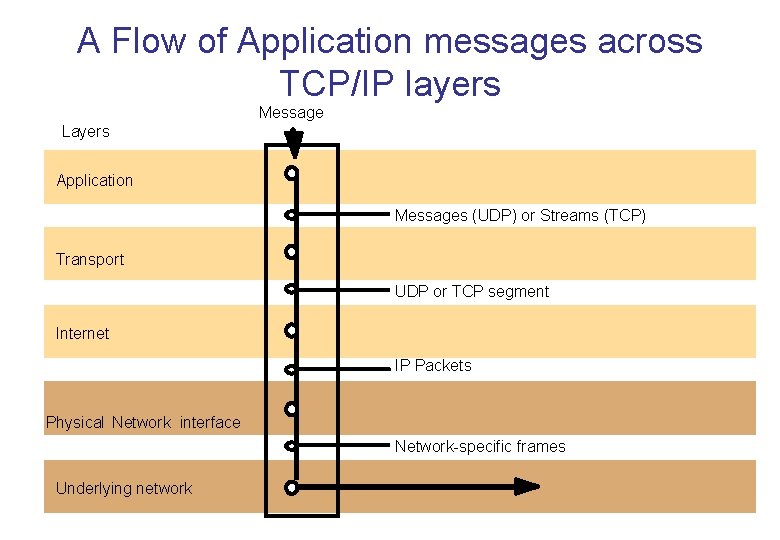
A Flow of Application messages across TCP/IP layers Message Layers Application Messages (UDP) or Streams (TCP) Transport UDP or TCP segment Internet IP Packets Physical Network interface Network-specific frames Underlying network 22

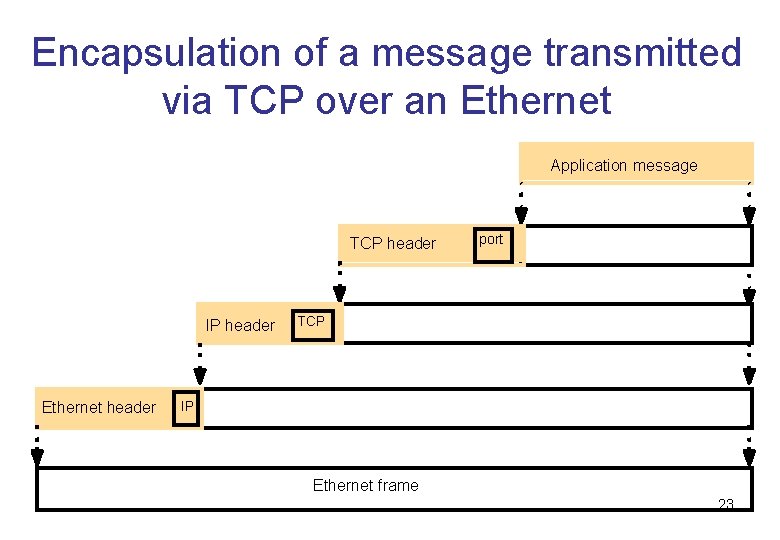
Encapsulation of a message transmitted via TCP over an Ethernet Application message TCP header IP header Ethernet header port TCP IP Ethernet frame 23

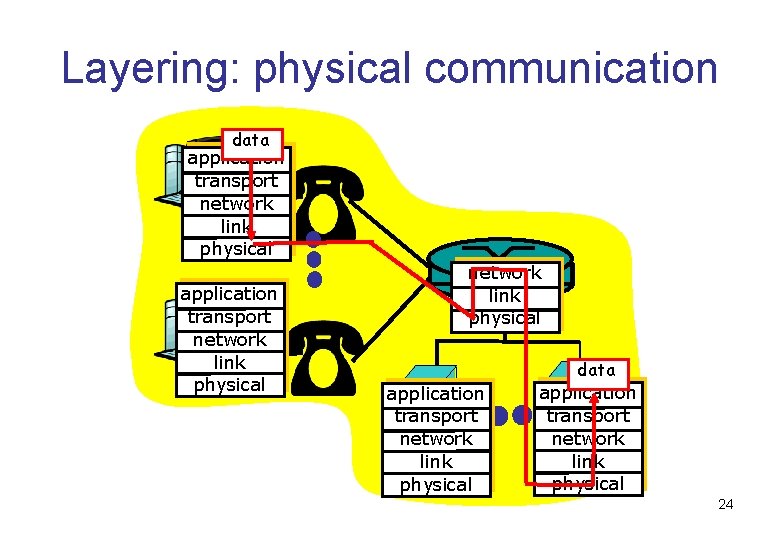
Layering: physical communication data application transport network link physical application transport network link physical data application transport network link physical 24

Application Layer Protocols • There are many Application layer protocols, each of which is associated with a client application and service provided by a server (Client/Server Model) – HTTP – FTP – TELNET – SMTP – POP 3 – IMAP 4 25

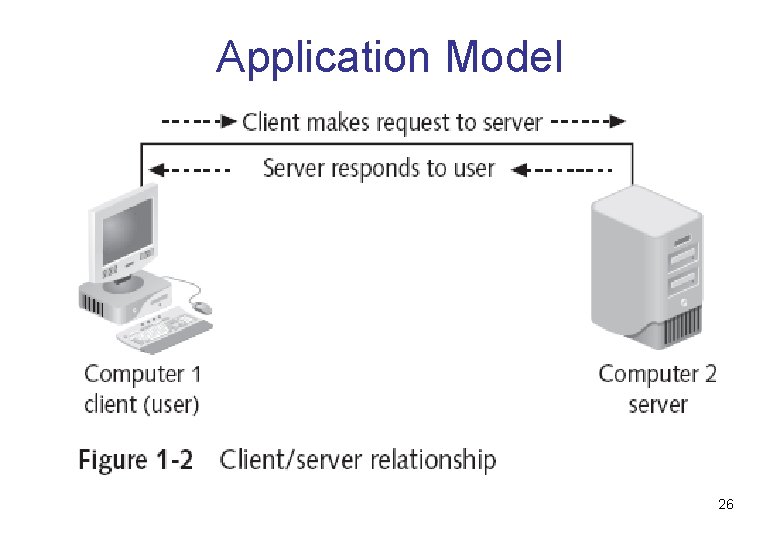
Application Model 26

Application Layer Protocols • • • HTTP Hypertext Transfer Protocol (HTTP) is the most common protocol used on the Internet today HTTP defines the commands that Web browsers can send and how Web servers are capable of responding FTP File Transfer Protocol (FTP) is file-sharing protocol FTP is implemented in stand-alone FTP clients as well as in Web browsers It is safe to say that most FTP users today are using Web browsers 27

Application Layer Protocols TELNET • Telnet is a terminal emulation protocol that is primarily used to connect remotely to UNIX and Linux Systems • The Telnet protocol specifies how a telnet server and telnet client communicate 28

Application Layer Protocols • • SMTP Simple Mail Transfer Protocol (SMTP) is used to send and receive e-mail messages between e-mail servers that are communicating It is used by e-mail client software, such as Outlook Express, to send messages to the server SMTP is never used to retrieve e-mail from a server when you are reading it Other protocols control the reading of e-mail messages 29

Application Layer Protocols POP 3 • Post Office Protocol version 3 (POP 3) is the most common protocol used for reading e-mail messages • This protocol has commands to download messages and delete messages from the mail server • POP 3 does not support sending messages • POP 3 supports only a single inbox and does not support multiple folders for storage on the server 30

Application Layer Protocols IMAP 4 • Internet Message Access Protocol version 4 (IMAP 4) is another common protocol used to read e-mail messages • IMAP 4 can download message headers only and allow you to choose which messages to download • IMAP 4 allows for multiple folders on the server side to store messages 31

Transport Layer Protocols • Transport layer protocols (TCP & UDP) are responsible for getting data ready to move across the network • The most common task performed by Transport layer protocols is breaking entire messages down into segments suitable to form packets • Transport layer protocols use port numbers • When a segment is addressed to a particular port, the Transport layer protocol knows to which service to deliver the packet 32

TCP • Transmission Control Protocol (TCP) is the most commonly used Transport layer protocol for most Internet services • TCP is connection-oriented and reliable • Connection-oriented means that TCP creates and verifies a connection with a remote host before sending information • Verifies that the remote host exists and is willing to communicate before starting the conversation • Provides flow control, segmentation, and error control 33

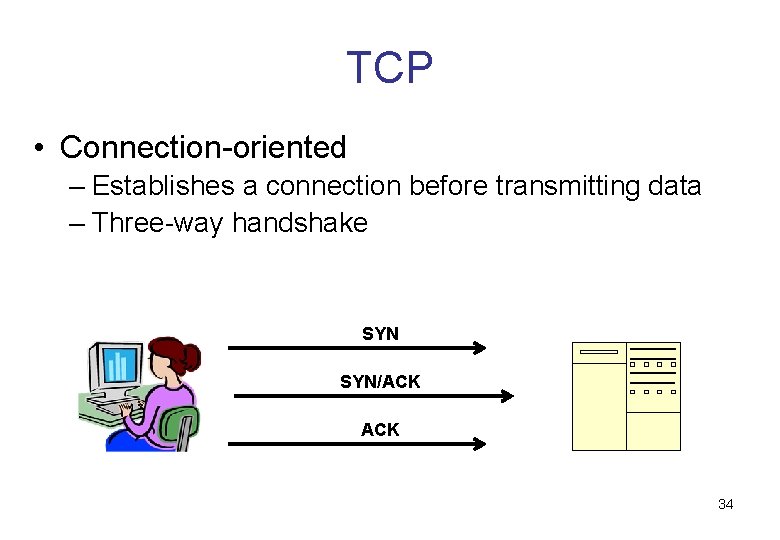
TCP • Connection-oriented – Establishes a connection before transmitting data – Three-way handshake SYN/ACK 34

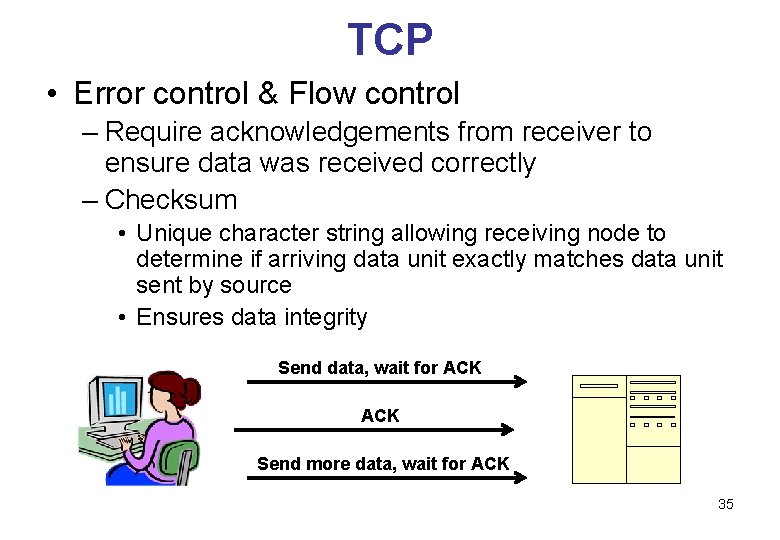
TCP • Error control & Flow control – Require acknowledgements from receiver to ensure data was received correctly – Checksum • Unique character string allowing receiving node to determine if arriving data unit exactly matches data unit sent by source • Ensures data integrity Send data, wait for ACK Send more data, wait for ACK 35

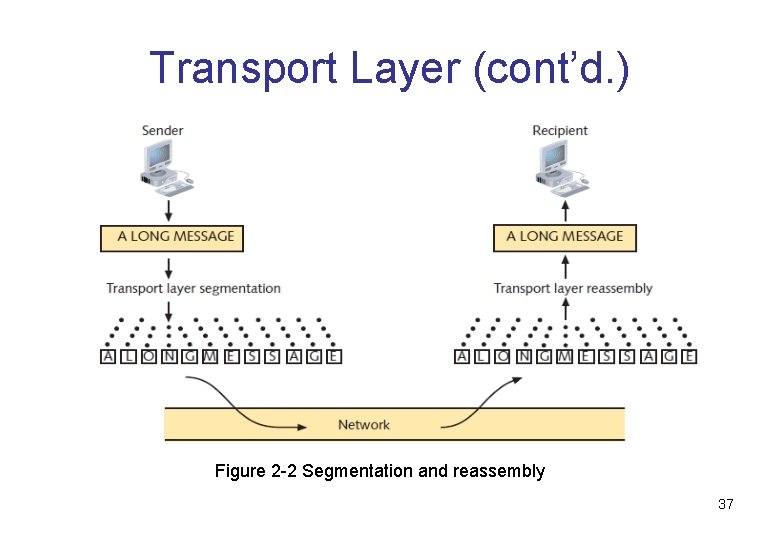
TCP • Segmentation – Breaking large data units received from Session layer into multiple smaller units called segments – Increases data transmission efficiency – MTU (maximum transmission unit): Largest data unit network will carry (Ethernet default: 1500 bytes) • Sequencing – Method of identifying segments belonging to the same group of subdivided data • Reassembly – Process of reconstructing segmented data units 36

Transport Layer (cont’d. ) Figure 2 -2 Segmentation and reassembly 37

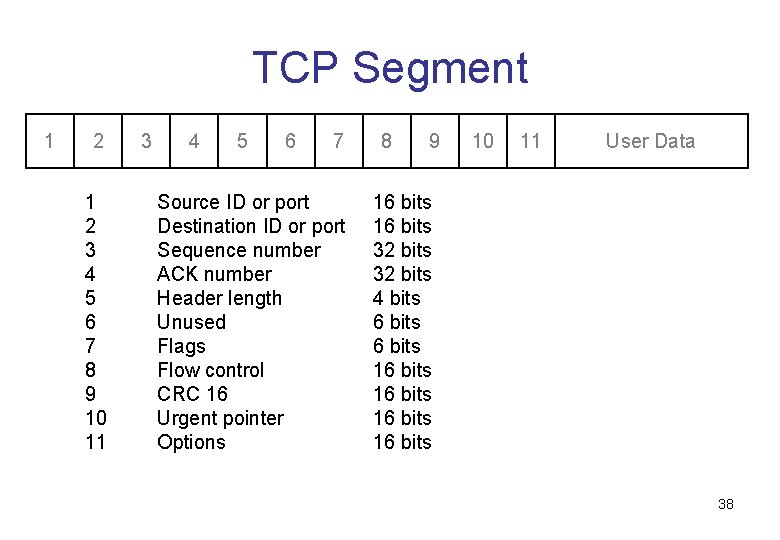
TCP Segment 1 2 3 4 5 6 7 8 9 10 11 3 4 5 6 7 Source ID or port Destination ID or port Sequence number ACK number Header length Unused Flags Flow control CRC 16 Urgent pointer Options 8 9 10 11 User Data 16 bits 32 bits 4 bits 6 bits 16 bits 38

UDP • User Datagram Protocol (UDP) – Not as commonly used as TCP – Used for different services – Connectionless and unreliable • UDP is the appropriate if – Unconcerned about missing packets – Want to implement reliability in a special way • Streaming audio and video are in this category 39

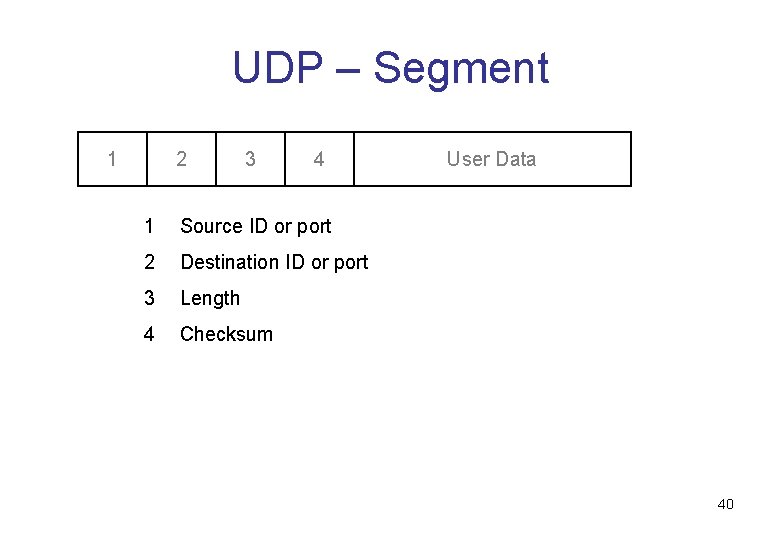
UDP – Segment 1 2 3 4 1 Source ID or port 2 Destination ID or port 3 Length 4 Checksum User Data 40

TCP versus UDP • TCP is connection-oriented and reliable – Like registered mail • UDP is connectionless and unreliable – Like sending a message split on several postcards and assuming that the receiver will be able to put the message together 41

Internet Layer Protocols • Internet layer protocols are responsible for all tasks related to logical addressing • An IP address is a logical address • Any protocol that is aware of other networks exists at this layer • Each Internet layer protocol is very specialized • They include: IP, RIP and OSPF, ICMP, IGMP, and ARP 42

Internet Layer Protocols • • IP Internet Protocol (IP) is responsible for the logical addressing of each packet created by the Transport layer to produce a complete IP Packet As each packet is built, IP adds the source and destination IP address to the IP packet ICMP Internet Control Messaging Protocol (ICMP) is used to send IP error and control messages between routers and hosts The most common use of ICMP is the ping utility 43

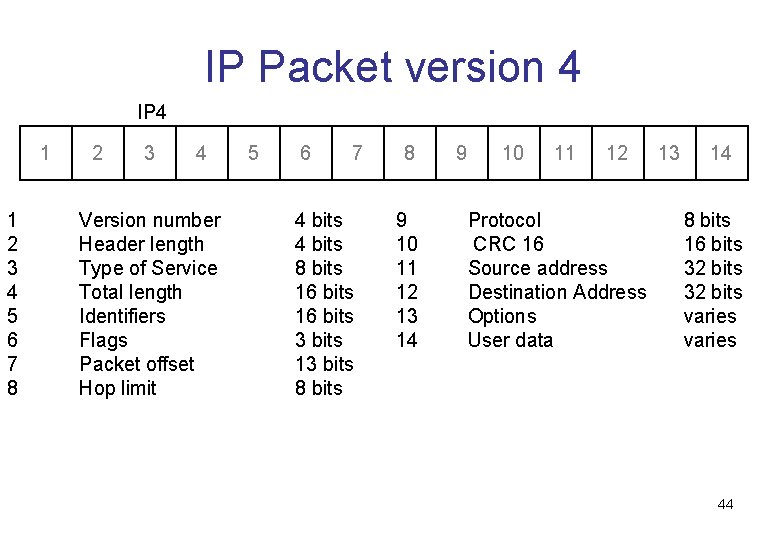
IP Packet version 4 IP 4 1 1 2 3 4 5 6 7 8 2 3 4 Version number Header length Type of Service Total length Identifiers Flags Packet offset Hop limit 5 6 7 4 bits 8 bits 16 bits 3 bits 13 bits 8 9 10 11 12 13 14 9 10 11 12 Protocol CRC 16 Source address Destination Address Options User data 13 14 8 bits 16 bits 32 bits varies 44

Internet Layer Protocols IGMP • Internet Group Management Protocol (IGMP) is used for the management of multicast groups • Hosts use IGMP to inform routers of their membership in multicast groups • Routers use IGMP to announce that their networks have members in particular multicast groups • The use of IGMP allows multicast packets to be distributed only to routers that have interested hosts connected 45

Internet Layer Protocols ARP • Address Resolution Protocol (ARP) is used to convert logical IP addresses to physical MAC addresses • This is an essential part of the packet delivery process 46

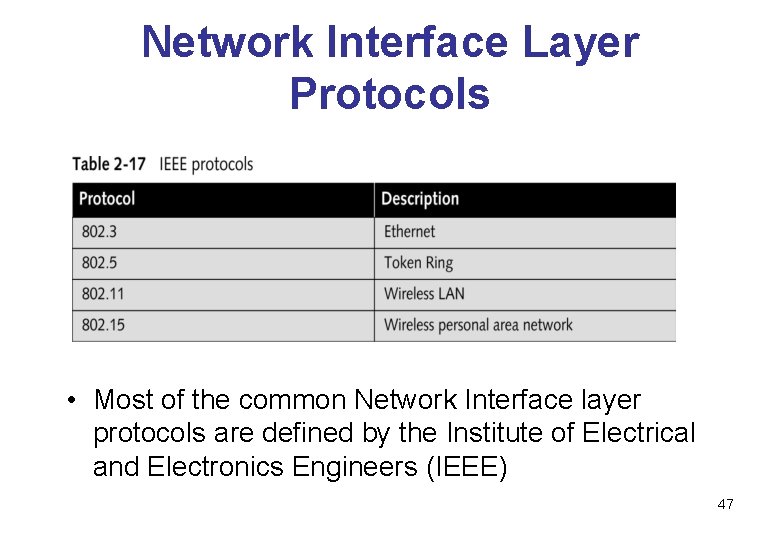
Network Interface Layer Protocols • Most of the common Network Interface layer protocols are defined by the Institute of Electrical and Electronics Engineers (IEEE) 47

IP Addresses • Internet Protocol (IP): – a protocol used in the internet layer. – IP makes use of the existing networks to deliver information, where these networks may use a variety of protocols. • Each computer has two addresses: – hardware address: used by the underlying network protocol for deliver data frame; – IP address: used by the internetworking protocols for deliver IP Packet. • Hardware address is also known as physical address. 48

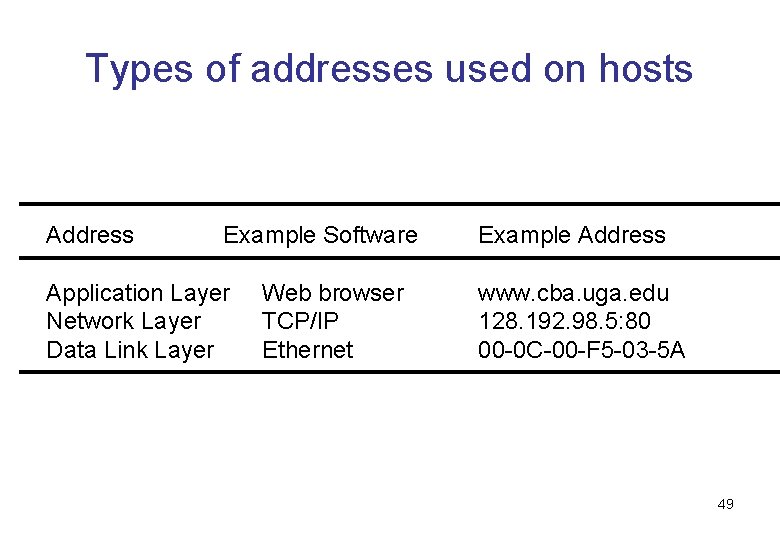
Types of addresses used on hosts Address Example Software Application Layer Network Layer Data Link Layer Web browser TCP/IP Ethernet Example Address www. cba. uga. edu 128. 192. 98. 5: 80 00 -0 C-00 -F 5 -03 -5 A 49

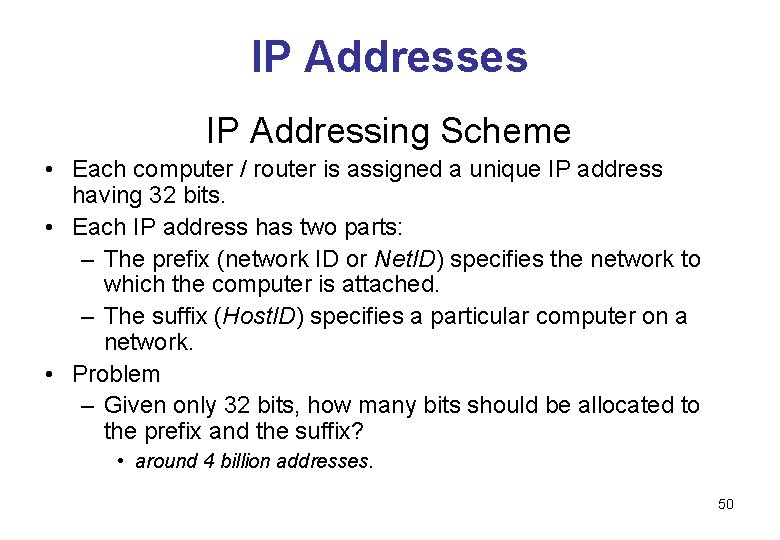
IP Addresses IP Addressing Scheme • Each computer / router is assigned a unique IP address having 32 bits. • Each IP address has two parts: – The prefix (network ID or Net. ID) specifies the network to which the computer is attached. – The suffix (Host. ID) specifies a particular computer on a network. • Problem – Given only 32 bits, how many bits should be allocated to the prefix and the suffix? • around 4 billion addresses. 50

IP Addresses IP Addressing Scheme • Considerations – If the prefix has many bits (large prefix, small suffix), there are many networks you can built but each network can only have a few computers. – If the prefix has a few bits (small prefix, large suffix), there are only few networks you can built but each network can have many computers. 51

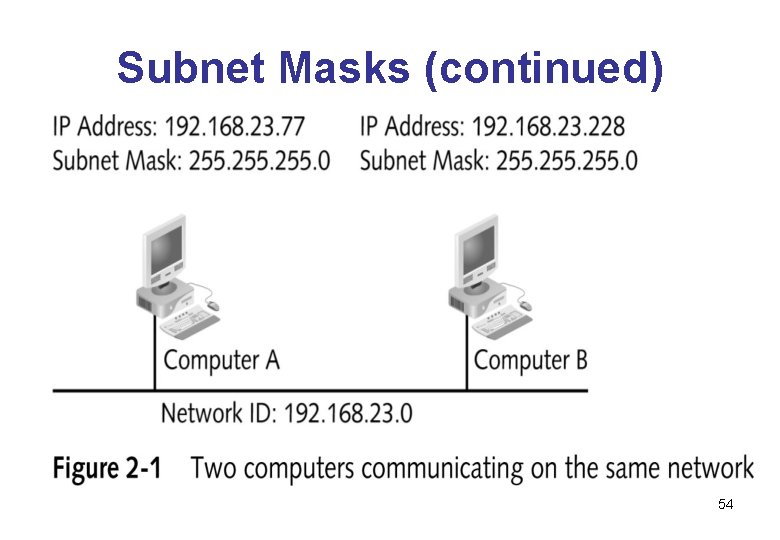
Subnet Masks • A subnet mask defines which part of its IP address is the network ID and which part is the host ID • Subnet masks are composed of four octets just like an IP address • Wherever there is a 255 in the subnet mask, that octet is part of the network ID • Wherever there is a 0 in the subnet mask, that octet is part of the host ID 52

Subnet Masks (continued) • A computer uses its subnet mask to determine – Which network it is on – Whether other computers are on the same network or a different network • If two computers on the same network are communicating, then they can deliver packets directly to each other • If two computers are on different networks, they must use a router to communicate 53

Subnet Masks (continued) 54

IP Address Classes • The IP addressing scheme defines three primary classes (A, B, C), where each class has a distinct prefix/suffix size, and two reserved classes (D&E). • The internet can accommodate large networks, medium networks, and small networks. • Classes A, B, C are the primary classes. The IP addresses of computers and routers belong to these classes. • Class D is used for multicasting. When a packet is sent to an IP multicast address, all the computers sharing this address will receive this packet. • Class E addresses are considered experimental and are not used 55

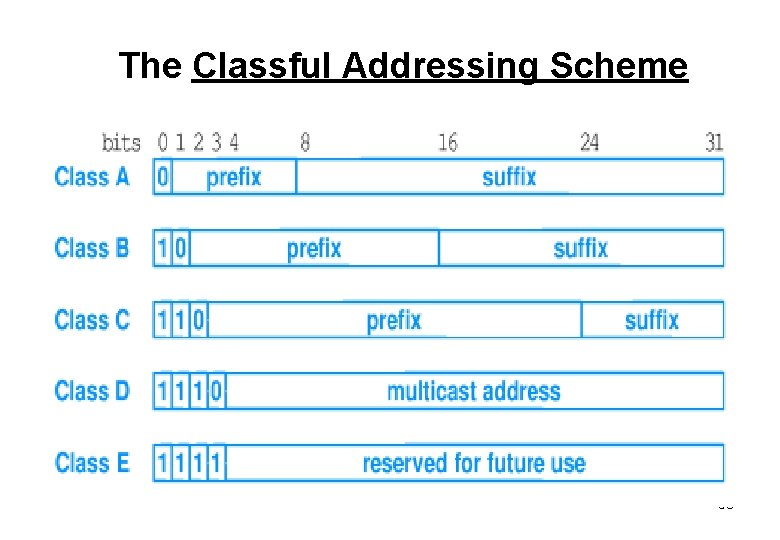
The Classful Addressing Scheme 56

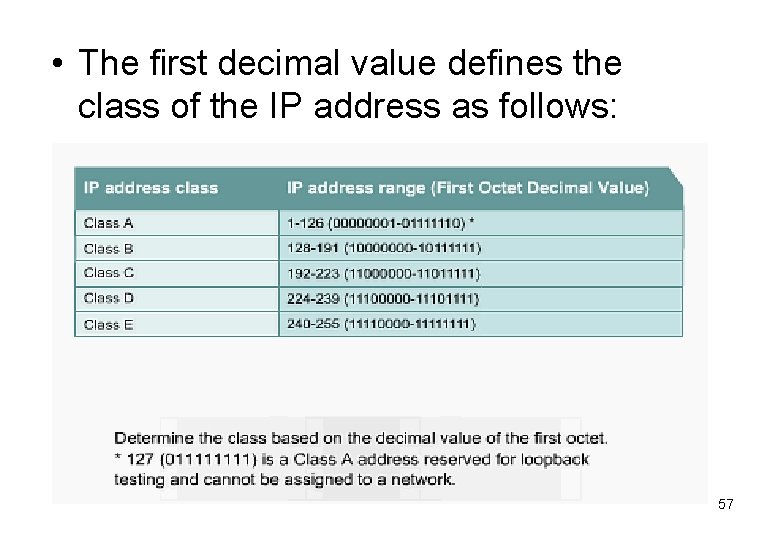
• The first decimal value defines the class of the IP address as follows: 57

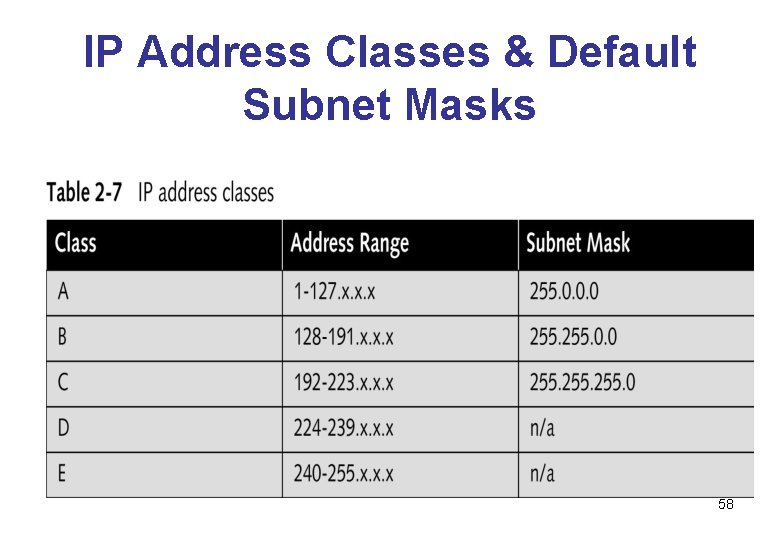
IP Address Classes & Default Subnet Masks 58

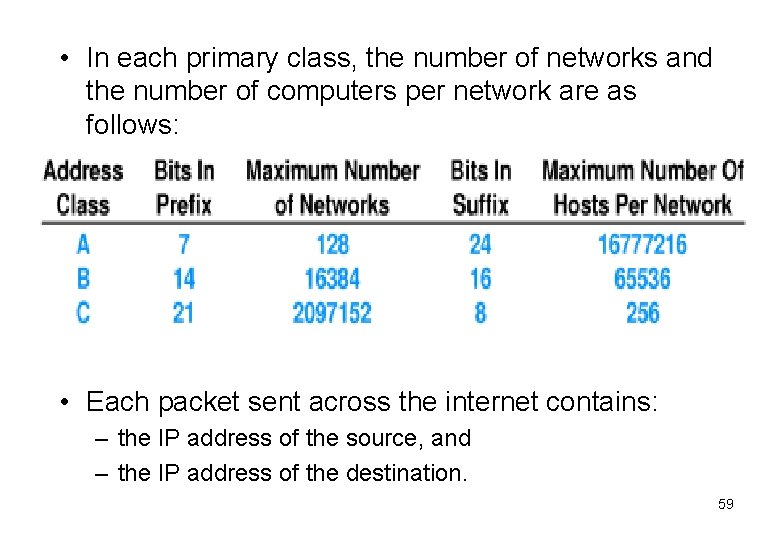
• In each primary class, the number of networks and the number of computers per network are as follows: • Each packet sent across the internet contains: – the IP address of the source, and – the IP address of the destination. 59

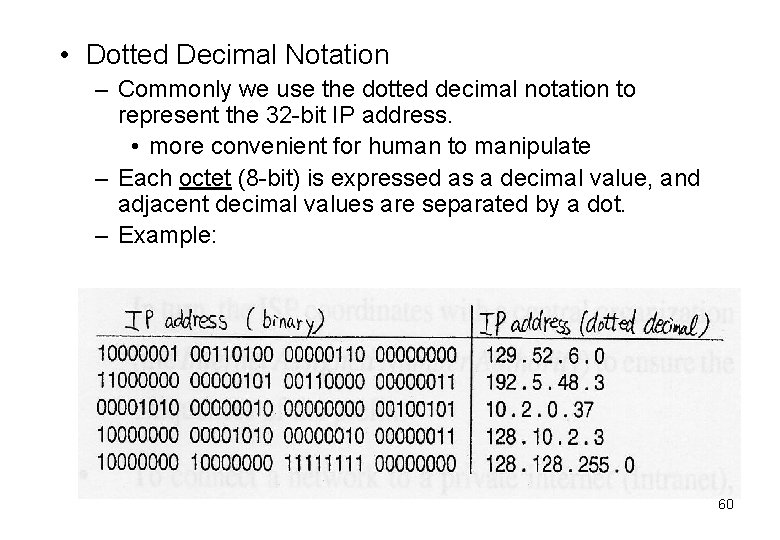
• Dotted Decimal Notation – Commonly we use the dotted decimal notation to represent the 32 -bit IP address. • more convenient for human to manipulate – Each octet (8 -bit) is expressed as a decimal value, and adjacent decimal values are separated by a dot. – Example: 60

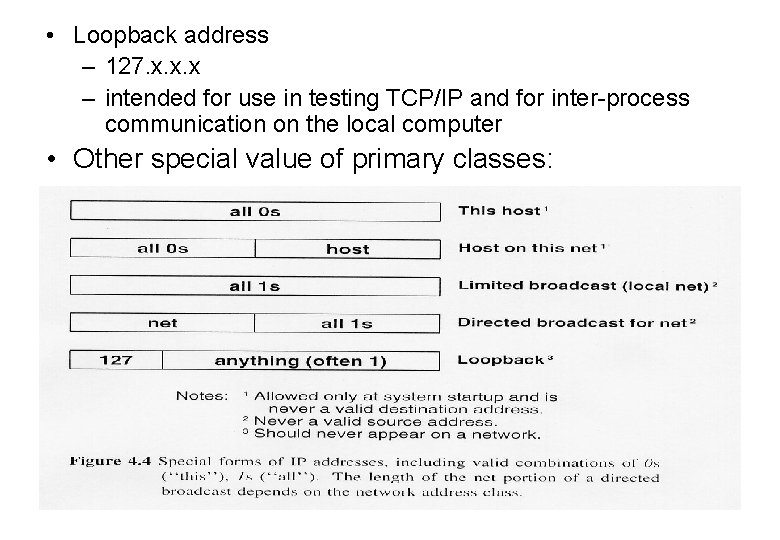
• Loopback address – 127. x. x. x – intended for use in testing TCP/IP and for inter-process communication on the local computer • Other special value of primary classes: 61

Assigning IP Addresses • Assigning Prefix Address – Each network must have a unique prefix address throughout an internet. – To connect a network to the global internet, an organization obtains a unique prefix address from the Internet Service Provider (ISP). – In turn, the ISP coordinates with a central organization (the Internet Assigned Number Authority (IANA, on or before 1998); the Internet Corporation for Assigned Names and Numbers (ICANN, after 1998)) to ensure the uniqueness of the prefix. – To connect a network to a private internet (Intranet), the organization can determine the prefix while ensuring its uniqueness. 62

Assigning IP Addresses • Assigning Suffix Address – Each computer must have a unique suffix address in the same network; while two computers in two different networks can have identical suffix address or Host. ID. – If the suffix is 00… 0 or 11… 1, the corresponding IP addresses have special meaning. Do not assign these suffixes. • An IP address with suffix equal to 00… 0 is used to refer to the network itself. • An IP address with suffix equal to 11… 1 is a directed broadcast address, i. e. , it refers to all hosts on the network. 63

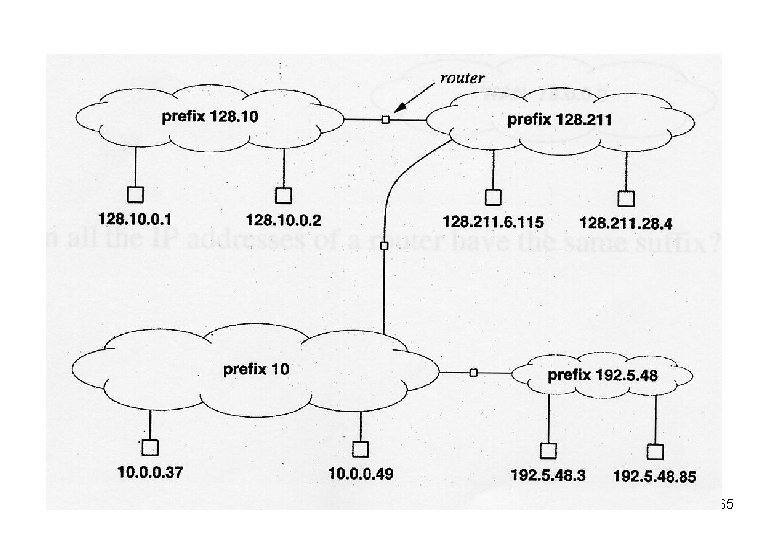
• Example – An organization wants to form a private TCP/IP internet with four networks, where one network is large (with many computers), two are medium, and one is small. – Firstly, assign a unique prefix to each network: • Assign a class A prefix for the large network (say, 10). • Assign a class B prefix for each of the two medium networks (say, 128. 10 and 128. 11). • Assign a class C prefix for the small network (say, 192. 5. 48). – Secondly, assign a unique suffix to each computer within each network: 64

65

Private IP Addresses • You can use these addresses on any private LAN. • You CANNOT use them on the internet. • Internet routers will block them. 66

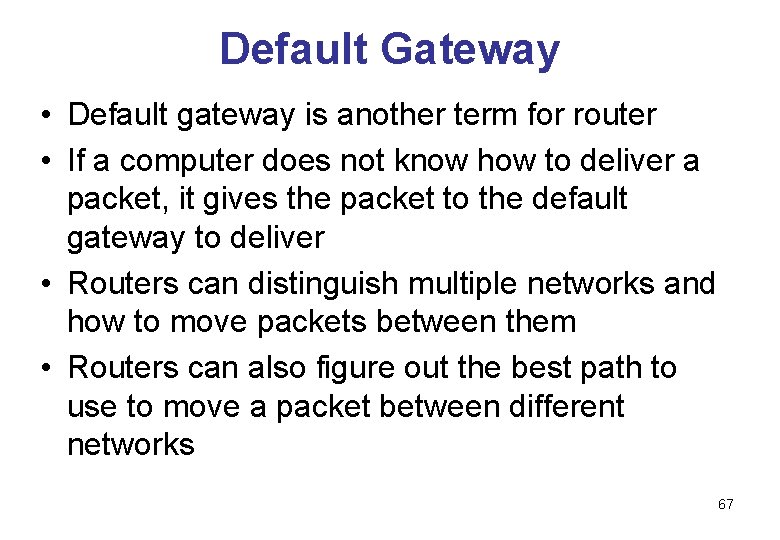
Default Gateway • Default gateway is another term for router • If a computer does not know how to deliver a packet, it gives the packet to the default gateway to deliver • Routers can distinguish multiple networks and how to move packets between them • Routers can also figure out the best path to use to move a packet between different networks 67

Classful IP Address § A classful network had a “natural” or “implied” prefix length or netmask: § Class A: prefix length /8 (netmask 255. 0. 0. 0) § Class B: prefix length /16 (netmask 255. 0. 0) § Class C: prefix length /24 (netmask 255. 0) § Modern (classless) routing systems have explicit prefix lengths or netmasks § You can't just look at an IP address to tell what the prefix length or netmask should be. Protocols and configurations need explicit netmask or prefix length. 68

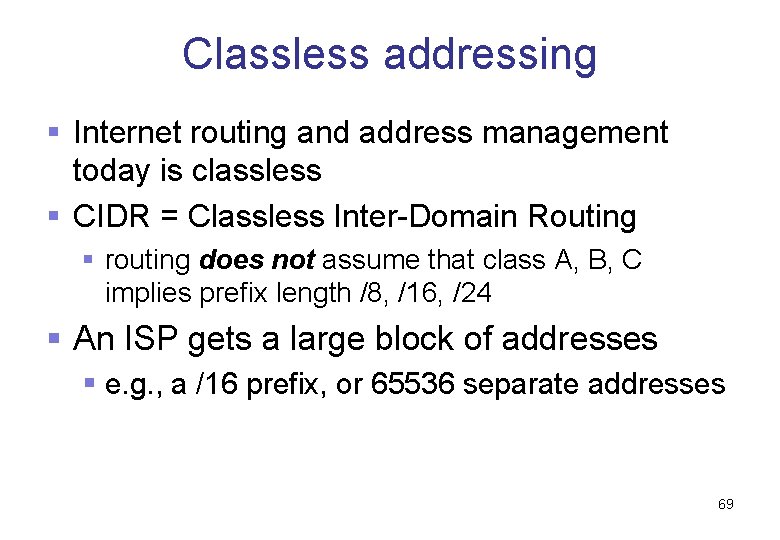
Classless addressing § Internet routing and address management today is classless § CIDR = Classless Inter-Domain Routing § routing does not assume that class A, B, C implies prefix length /8, /16, /24 § An ISP gets a large block of addresses § e. g. , a /16 prefix, or 65536 separate addresses 69

Classless addressing • Allocate smaller blocks to customers – e. g. , a /26 prefix (64 addresses) to 4 customers for their medium public networks, a /28 prefix (16 addresses) to 32 customers for their medium public networks, and a /29 prefix (8 addresses) to another 64 customers for their small public networks (and some space left over for other customers) 70

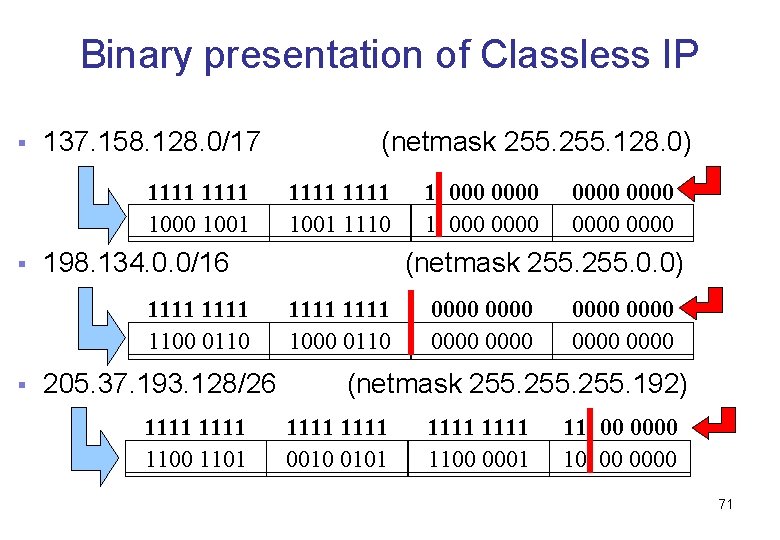
Binary presentation of Classless IP § 137. 158. 128. 0/17 1111 1000 1001 § 1111 1001 1110 198. 134. 0. 0/16 1111 1100 0110 § (netmask 255. 128. 0) 205. 37. 193. 128/26 1111 1100 1101 1 000 0000 0000 (netmask 255. 0. 0) 1111 1000 0110 0000 0000 (netmask 255. 192) 1111 0010 0101 1111 1100 0001 11 00 0000 10 00 0000 71

Classless addressing exercise • § Consider the address block 133. 27. 162. 0/28 and 133. 27. 163. 48/29. What are the IP addresses range can you obtain from each block? § § in prefix length notation netmasks in decimal IP address ranges What blocks are still available (not yet allocated)? 72

Sockets and Ports 73

Sockets and Ports • Processes assigned unique port numbers • Process’s socket – Port number plus host machine’s IP address • Port numbers – Simplify TCP/IP communications – Ensures data transmitted correctly to the specific application among multiple applications running on same host • Example – Telnet port number: 23 – IPv 4 host address: 10. 43. 3. 87 – Socket address: 10. 43. 3. 87: 23 74

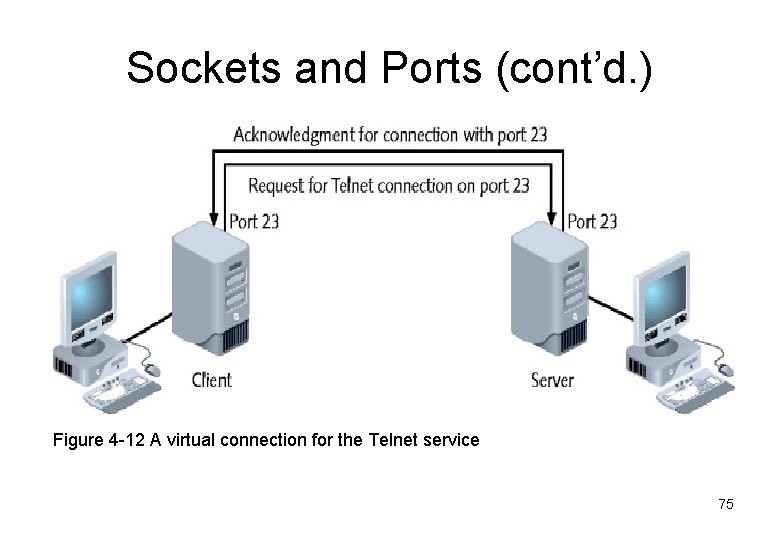
Sockets and Ports (cont’d. ) Figure 4 -12 A virtual connection for the Telnet service 75

Sockets and Ports (cont’d. ) • Port number range: 0 to 65535 • Three types – Well Known Ports • Range: 0 to 1023 • Operating system or administrator use – Registered Ports • Range: 1024 to 49151 • Network users, processes with no special privileges – Dynamic and/or Private Ports • Range: 49152 through 65535 • No restrictions 76

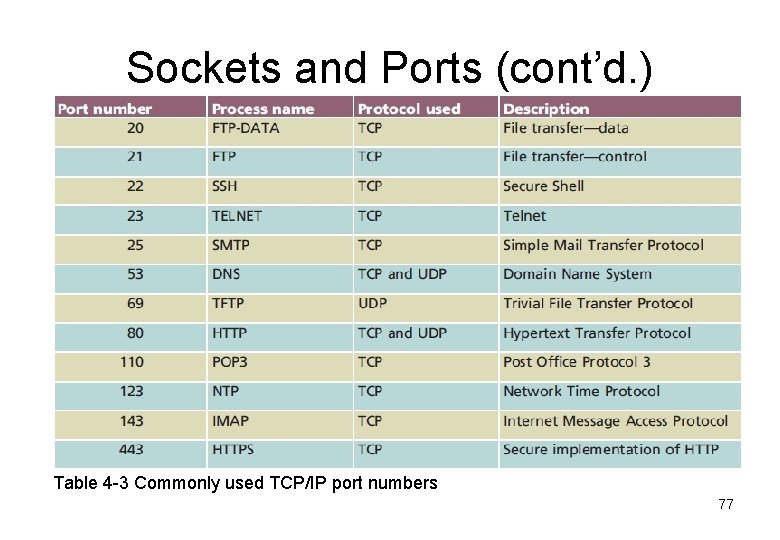
Sockets and Ports (cont’d. ) Table 4 -3 Commonly used TCP/IP port numbers 77
 History of osi model
History of osi model Tcpip
Tcpip Modelo tcpip
Modelo tcpip Osi vs tcp
Osi vs tcp Diagrama tcp
Diagrama tcp Tcp/ip logo
Tcp/ip logo Osi tcpip
Osi tcpip Tcpip model
Tcpip model 4-way handshake
4-way handshake Tcp (transmission control protocol) to protokół
Tcp (transmission control protocol) to protokół Transmission control protocol
Transmission control protocol Introduction of wireless power transmission
Introduction of wireless power transmission Hát kết hợp bộ gõ cơ thể
Hát kết hợp bộ gõ cơ thể Slidetodoc
Slidetodoc Bổ thể
Bổ thể Tỉ lệ cơ thể trẻ em
Tỉ lệ cơ thể trẻ em Gấu đi như thế nào
Gấu đi như thế nào Tư thế worms-breton
Tư thế worms-breton Hát lên người ơi alleluia
Hát lên người ơi alleluia Môn thể thao bắt đầu bằng chữ f
Môn thể thao bắt đầu bằng chữ f Thế nào là hệ số cao nhất
Thế nào là hệ số cao nhất Các châu lục và đại dương trên thế giới
Các châu lục và đại dương trên thế giới Công của trọng lực
Công của trọng lực Trời xanh đây là của chúng ta thể thơ
Trời xanh đây là của chúng ta thể thơ Cách giải mật thư tọa độ
Cách giải mật thư tọa độ Phép trừ bù
Phép trừ bù độ dài liên kết
độ dài liên kết Các châu lục và đại dương trên thế giới
Các châu lục và đại dương trên thế giới Thơ thất ngôn tứ tuyệt đường luật
Thơ thất ngôn tứ tuyệt đường luật Quá trình desamine hóa có thể tạo ra
Quá trình desamine hóa có thể tạo ra Một số thể thơ truyền thống
Một số thể thơ truyền thống Cái miệng nó xinh thế chỉ nói điều hay thôi
Cái miệng nó xinh thế chỉ nói điều hay thôi Vẽ hình chiếu vuông góc của vật thể sau
Vẽ hình chiếu vuông góc của vật thể sau Thế nào là sự mỏi cơ
Thế nào là sự mỏi cơ đặc điểm cơ thể của người tối cổ
đặc điểm cơ thể của người tối cổ Thế nào là giọng cùng tên? *
Thế nào là giọng cùng tên? * Vẽ hình chiếu đứng bằng cạnh của vật thể
Vẽ hình chiếu đứng bằng cạnh của vật thể Tia chieu sa te
Tia chieu sa te Thẻ vin
Thẻ vin đại từ thay thế
đại từ thay thế điện thế nghỉ
điện thế nghỉ Tư thế ngồi viết
Tư thế ngồi viết Diễn thế sinh thái là
Diễn thế sinh thái là Dot
Dot So nguyen to
So nguyen to Tư thế ngồi viết
Tư thế ngồi viết Lời thề hippocrates
Lời thề hippocrates Thiếu nhi thế giới liên hoan
Thiếu nhi thế giới liên hoan ưu thế lai là gì
ưu thế lai là gì Khi nào hổ mẹ dạy hổ con săn mồi
Khi nào hổ mẹ dạy hổ con săn mồi Khi nào hổ con có thể sống độc lập
Khi nào hổ con có thể sống độc lập Sơ đồ cơ thể người
Sơ đồ cơ thể người Từ ngữ thể hiện lòng nhân hậu
Từ ngữ thể hiện lòng nhân hậu Thế nào là mạng điện lắp đặt kiểu nổi
Thế nào là mạng điện lắp đặt kiểu nổi Air ionization in wireless power transmission
Air ionization in wireless power transmission Wireless power transmission project report doc
Wireless power transmission project report doc Relational identity
Relational identity Factors that affect disease transmission
Factors that affect disease transmission Mtved ifsi
Mtved ifsi Guided media
Guided media Lossless transmission line examples
Lossless transmission line examples Transmission line basics
Transmission line basics Transmission du mouvement
Transmission du mouvement Transmission de puissance
Transmission de puissance Transmission de puissance
Transmission de puissance Transmission de puissance avec transformation de mouvement
Transmission de puissance avec transformation de mouvement Transmission bridge
Transmission bridge Transmission mechanism
Transmission mechanism Nerve impulse transmission steps
Nerve impulse transmission steps Les supports de transmission
Les supports de transmission Sound transmission loss
Sound transmission loss Solar power satellites and microwave power transmission
Solar power satellites and microwave power transmission Linked
Linked Konstanta propagasi
Konstanta propagasi Sabal trail transmission
Sabal trail transmission Pneumatic power transmission
Pneumatic power transmission Social studies taught as citizenship transmission adalah
Social studies taught as citizenship transmission adalah كبيل
كبيل