COSC 1306 COMPUTER SCIENCE AND PROGRAMMING JehanFranois Pris


























































![Evolution (I) • 1977: Apple ][ – First widely successful massproduced PC – Killer Evolution (I) • 1977: Apple ][ – First widely successful massproduced PC – Killer](https://slidetodoc.com/presentation_image_h/f6f859844ebf5236e29fa42f62e959bf/image-81.jpg)





























- Slides: 133

COSC 1306 COMPUTER SCIENCE AND PROGRAMMING Jehan-François Pâris jfparis@uh. edu

INTRODUCTION TO COMPUTERS AND COMPUTING

Module Overview • The computing phenomenon – Pervasiveness – Computers or computing? • Historical perspective – Four predecessors – The birth of computers – Its evolution

THE COMPUTING PHENOMENON

Computers have changed our lives • They are everywhere • They have changed our lives – Electronic mail – WWW – Online order processing – Ticketless travel

Case study • A friend of mine now teaches in a small University in Montevideo, Uruguay

Then • Before the Internet, his life would have been difficult – No access to a good university library – Could only communicate with colleagues through • Expensive international calls • Slow Uruguayan postal service • Nearly total isolation from CS community

Now • He has – Full access to research papers posted online – Can communicate with colleagues through • Email, instant messages, Facebook, … • Skype – Submits papers to conferences through

My point • Internet has abolished distance • Inexpensive personal computers allow us to work virtually everywhere – Still need a good Internet connection • Changed the lives of computer scientists and mathematicians working in – Small colleges in the boondocks – Decent universities in developing

Counterpoint • Human contacts still count: – Main reason why scientists travel • No Internet access means exclusion – Case of most African countries

The iceberg • Most computing takes place where we do not see it

Examples • • • Car computers Set-top box Digital television Fly-by-wire planes Smart phones Many medical appliances

An analogy • Mid-nineteenth century big textile factories used – Steam-powered looms • One steam engine powered several looms – Power went through transmission belts and pulleys • Dangerous

transmission belts

An analogy (cont'd) • Stream engines were progressively replaced by electrical motors – Quickly found it was better to have one smaller motor per loom • Got rid of transmission belts • Allowed more flexible plant layouts • Now electrical motors are everywhere – Car power windows, razors, toothbrushes, …

How it applies • Started with a few giant "electronic brains" • Replaced by time sharing computers and individual terminals • Moved to personal computers • Each of us is now likely to have several computing devices

Counterpoint • Are we now living in the best of all possible worlds?

Social problems • Lack of privacy • Distraction • Nothing is forgotten

More pressing problems • What happens when computers that control critical aspects of our lives go wrong? – In 1985 a Canadian-built radiationtreatment device began blasting holes through patients' bodies. How a series of simple computer errors sabotaged a state-of-the-art medical wonder.

The full report • An Investigation of the Therac-25 Accidents Nancy Leveson, U of Washington Clark S. Turner, UC Irvine IEEE Computer, Vol. 26, No. 7, July 1993, pp. 18 -41 http: //courses. cs. vt. edu/cs 3604/lib/Th erac_25/Therac_1. html

Another big problem • In fly-by-wire planes, pilots’ inputs are handled by an on-board computer – What happens when pilots’ inputs conflict with safety rules implemented in the on-board computer?

The answer • It depends – On Boeing planes, the pilot wins • Great for airlines with highly-trained pilots • Not so good otherwise – On Airbus planes, the computer wins • Great for airlines with not-so-welltrained pilots • Pilots can still override computer

An outcome • On June 1, 2009 Air France flight 447 from Rio to Paris crashed in mid-Atlantic – Cause of crash was aerodynamic stall – Preceded by problems with speed sensors • Inquiry noted that "pilots had not been trained to fly the aircraft in manual mode "

A long-term problem • An increasing large number of documents are exclusively stored in digital format without any hard copy – Most of your recent pictures – Your grades • Will they survive as well as hard copies do?

The issues • Disk failures: • Hard to figure exact mean time to fail of hard drives –Ten thousand to one million hours –Ten thousand hours is slightly more than 11 years –An array of 150 disks will experience an average of one

The issues (cont’d) • Offline storage media become rapidly obsolete – Who can read a 5. 25” floppy? – A 4 MB floppy? – A 100 MB Zip disk?

That’s not all • Hard copies were easy to authenticate – Type of paper and ink that were used – Typewriter font • Electronic forgeries are harder to detect – Can use digital signatures • Become easier to break over time – Pictures can be “Photoshopped”®

My conclusion • We are not in the best of all possible worlds • Rolling clock backward is not possible – The genie is out the bottle! • Must understand the issues and push for action – Course will only help you with first part

HISTORICAL PERSPECTIVE

Three stages • The ancestors • The pioneers • The continuation

The ancestors • Their contributions made computing possible – Blaise Pascal – Joseph Marie Jacquard – Charles Babbage – Samuel Morse – Herman Hollerith • All died well before computers were

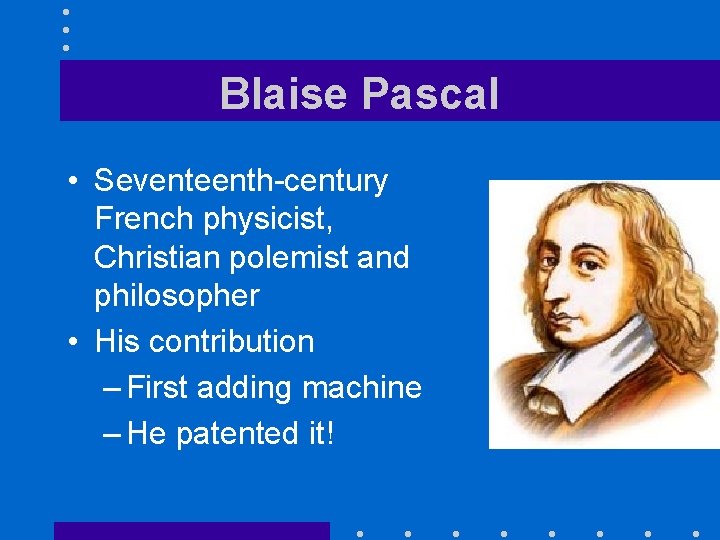
Blaise Pascal • Seventeenth-century French physicist, Christian polemist and philosopher • His contribution – First adding machine – He patented it!

La machine de Pascal • Could only add and subtract • Costly to build • Not a commercial success

Long-term impact • Showed that arithmetic operations could be performed by mechanical devices – Proof of concept • People kept building and using mechanical computing machines until the late sixties

Joseph Marie Jacquard • Self-taught French inventor • Invented in 1801 a mechanical loom that simplified the weaving of fabrics with complex patterns (brocade, damask, …) • Key idea was to use punched cards to store the patterns

Jacquard loom

Long-term impact • Jacquard loom was quickly adopted – Reduced manpower needs for weaving of fabrics with complex patterns • Caused a workers' revolt in Lyon in 1831 – Still in use today • Showed that information could be stored in a machine-readable form

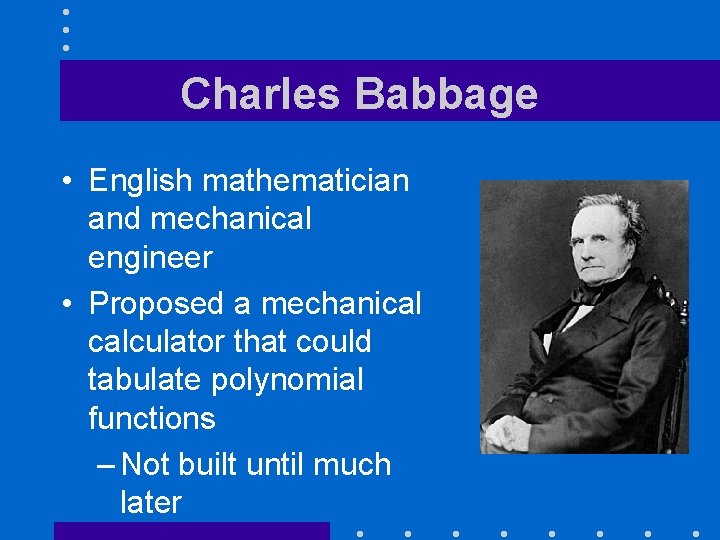
Charles Babbage • English mathematician and mechanical engineer • Proposed a mechanical calculator that could tabulate polynomial functions – Not built until much later

Motivation • Polynomials were used—and are still used—to compute logarithms, sines, cosines and so on – Boole wanted to speed up the computation of numerical tables

The differential engine

Long-term impact • Boole went on to design a much more ambitious analytical engine – Prototype of a modern computer • Some difference engines were built later – One was used to produce printed logarithmic tables • Showed that computations can be programmed

Samuel Morse • American painter and inventor • Invented the telegraph – First practical application of electricity – "Queen Victoria's Internet" • Huge immediate impact on many human

Long-term impact • Was developed to avoid continued fighting after peace treaty (Treaty of Ghent 1814) – Did not guarantee universal peace among nations • Showed that information could travel fast over long distances

Herman Hollerith • American statistician • Tried to speed up the processing of the 1890 census • Invented the tabulating machine

Tabulating machine and sorter

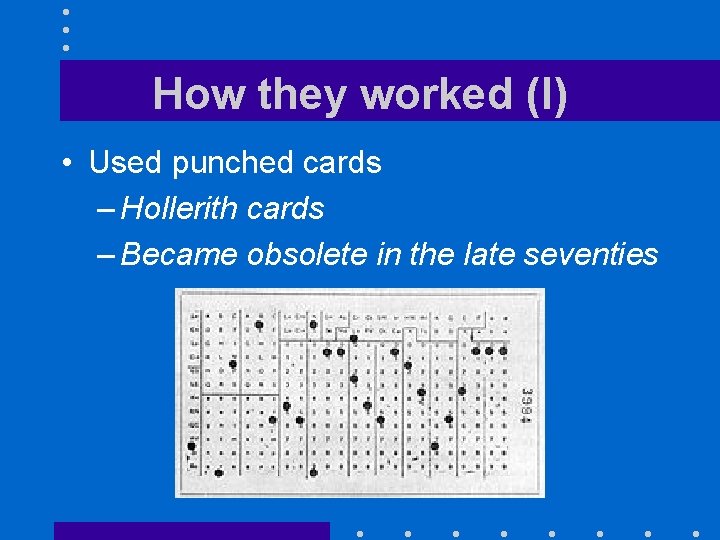
How they worked (I) • Used punched cards – Hollerith cards – Became obsolete in the late seventies

How they worked (II) • When tabulating machine read a card, it could – Add the values stored in some columns to one of its registers – Instruct the sorter to open one of its slots • Next step was to make cards move within tabulator and sorter without any

Long-term impact • Tabulating machines were produced until the mid-seventies – Were used all around the world – Made IBM • While Babbage’s differential engine was purely mechanical, Hollerith tabulating machines were electromechanical.

More inventors (I) • Charles Sanders Pierce – American philosopher, logician and inventor – Showed in 1880’s that Boolean algebra could be implemented by electrical circuits

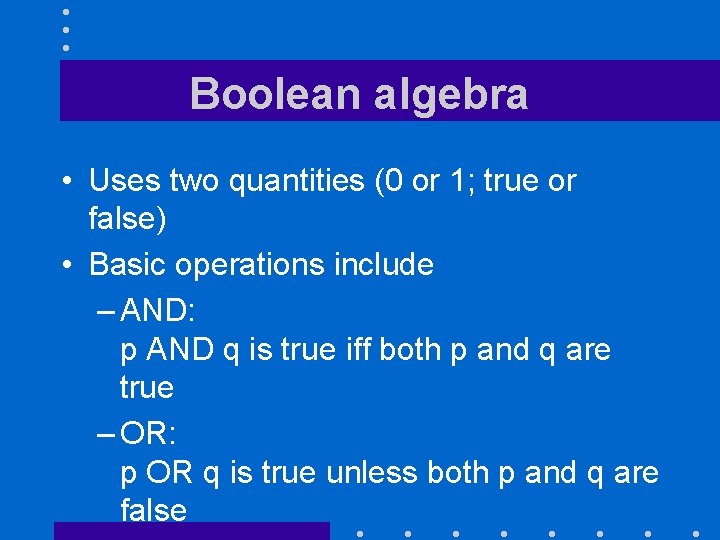
Boolean algebra • Uses two quantities (0 or 1; true or false) • Basic operations include – AND: p AND q is true iff both p and q are true – OR: p OR q is true unless both p and q are false

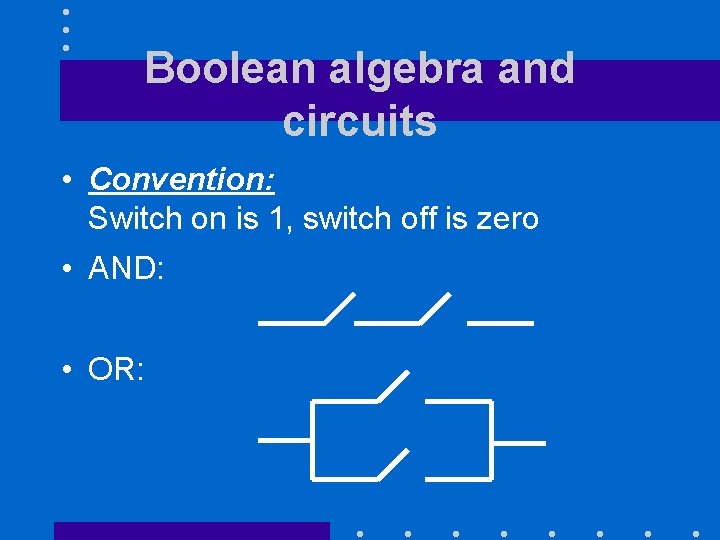
Boolean algebra and circuits • Convention: Switch on is 1, switch off is zero • AND: • OR:

More inventors (II) • John Atanasoff and Clifford Berry – Iowa State College – Built a very limited computer using vacuum tubes in the 1930’s

World War II • United States had to build very quickly large armed forces – Train and equip them • Needed better ballistic tables to predict naval gun trajectories – Resulted in development of two computers

Harvard Mark I • Designed by Howard H. Aiken • Built by IBM from switches, relays and other electromechanical parts • First programmable computer – Read its instructions from a punched paper tape – Executed them in sequence – Loops were implemented by making a paper loop

ENIAC • Electronic Numerical Integrator And Computer • Designed and built at University of Pennsylvania by a team headed by John Mauchly and J. Presper Eckert • Used vacuum tubes – Thousand times faster than Harvard Mark I • Came too late to contribute to was effort

EDVAC • Successor to ENIAC • Designed by same authors • Used binary arithmetic – Simpler • Stored its programs in its memory – Could even modify them while running (Von Neumann architecture)

Other WW II Computers • Set of top secret machines developed in UK to crack German Enigma code • Collectively known as Colossus • Existence was not known until much later

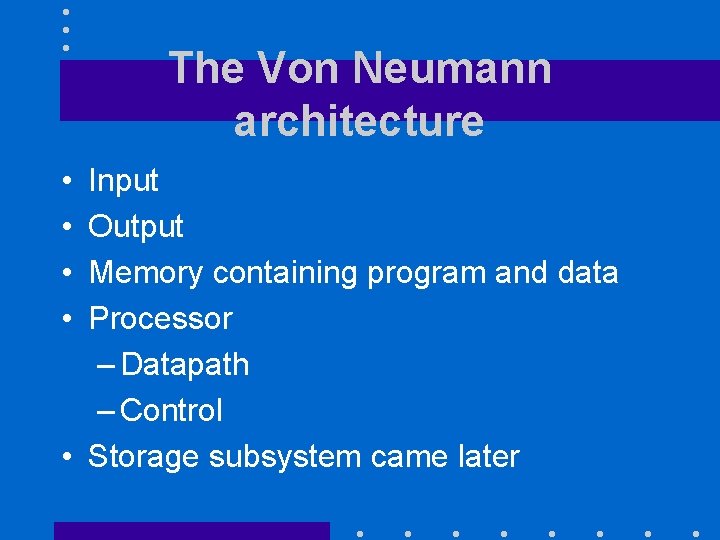
The Von Neumann architecture • • Input Output Memory containing program and data Processor – Datapath – Control • Storage subsystem came later

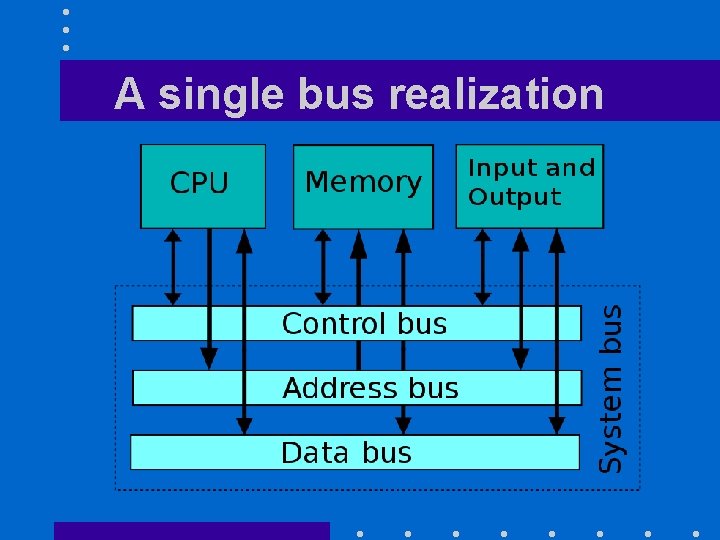
A single bus realization

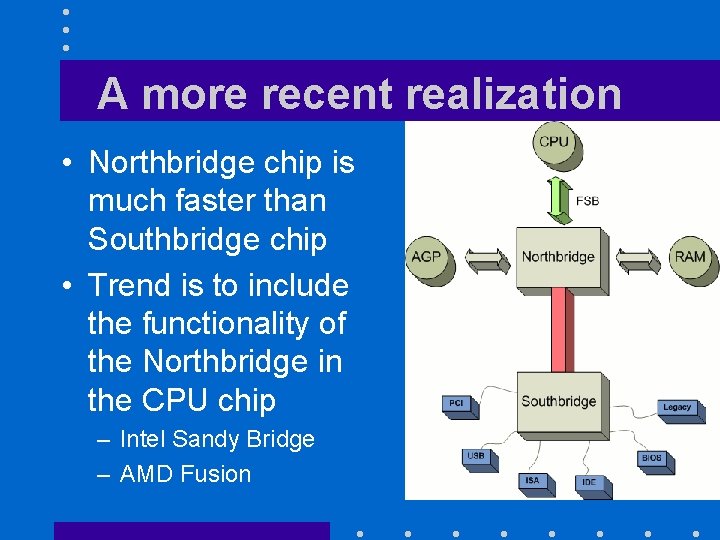
A more recent realization • Northbridge chip is much faster than Southbridge chip • Trend is to include the functionality of the Northbridge in the CPU chip – Intel Sandy Bridge – AMD Fusion

A laptop motherboard

THE FIRST GENERATION • Used vacuum tubes – Were power hungry and unreliable • UNIVAC – First commercially successful computer • IBM – Well established tabulating machine maker

The UNIVAC I

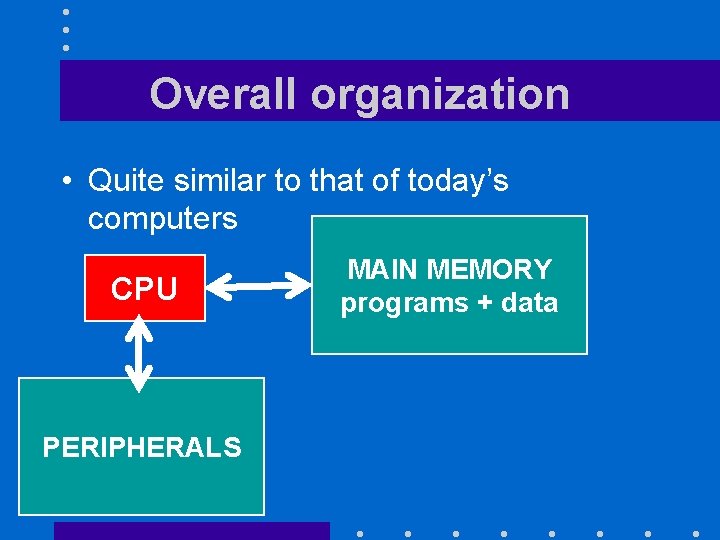
Overall organization • Quite similar to that of today’s computers CPU PERIPHERALS MAIN MEMORY programs + data

Evolution • Revolution was started by UNIVAC • IBM quickly become the leader – Was a true computer company – Well introduced in most businesses • Already used IBM tabulating machines • In the sixties and seventies, most people identified IBM as “the” computer maker

Batch systems • Allow users to submit a batches of requests to be processed in sequence • Include a command language specifying what to do with the inputs – Compile – Link edit – Execute and so forth

An IBM 1401

Interactive systems • Came later • Allow users to interact with the OS through their terminals: • Include an interactive command language – UNIX shells, Windows Power. Shell – Can also be used to write scripts

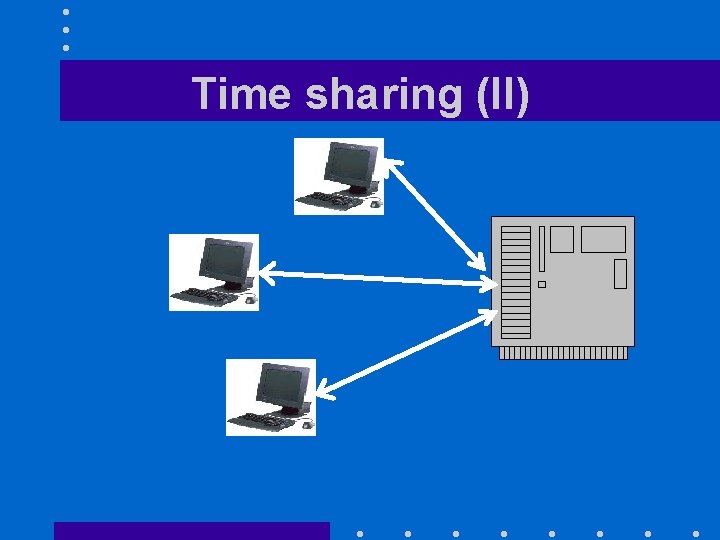
Time sharing (I) • Lets several interactive users to access a single computer at the same time • Standard solution when computers were expensive

Time sharing (II)

UNIX (I) • Started at Bell Labs in the early 70's as an attempt to build a sophisticated time-sharing system on a very small minicomputer. • First OS to be almost entirely written in C • Ported to the VAX architecture in the late 70’s at U. C. Berkeley: – Added virtual memory and

The fathers of UNIX Ken Thompson and Denis Ritchie

UNIX (II) • Became the standard operating systems for workstations – Selected by Sun Microsystems • Became less popular because – Two many variants • Berkeley BSD, ATT System V, … – PCs displaced workstations – Windows has a better user interface

UNIX Today • Several free versions exist (Free. BSD, Linux): – Source code of these free versions is available at no cost – Ideal platform for OS research • UNIX/Linux-based kernels used by – Apple OS X and i. OS operating system – Android operating systems

Time sharing (III) • Time sharing become much less important by the end of the eighties – Personal computers became almost as cheap as terminals – Time sharing could not support graphical user interfaces

Why? • A graphical user interface must transfer a lot of data between the processor and the display unit – Cannot do it if distance exceeds a few feet • The workstation was born – Combines a computer with its display

Graphical user interfaces • Called GUIs (pronounced goo-eys): Macintosh, Windows, X-Windows, Linux • Require a dedicated computer for each user • Pioneered at XEROX Palo Alto Research Center • Popularized by the Macintosh • Dominated the market with Microsoft Windows

Xerox PARC (I) • Founded by XEROX in 1970 • Invented – Laser printing – Ethernet – The GUI paradigm – Object-oriented programming (Smalltalk)

Xerox PARC (II) • All their inventions were brought to market by other concerns • Popular belief is that Xerox management blew it • In reality – Alto workstations were very expensive – Smalltalk was very slow – Group was too small to deliver a full system

The personal computer • By 1971, it was possible to put a very simple CPU on a single chip – Intel 4004 was a four-bit microprocessor designed for a desktop calculator – Followed by an 8 -bit version 8008 • Used to build very basic personal computers
![Evolution I 1977 Apple First widely successful massproduced PC Killer Evolution (I) • 1977: Apple ][ – First widely successful massproduced PC – Killer](https://slidetodoc.com/presentation_image_h/f6f859844ebf5236e29fa42f62e959bf/image-81.jpg)
Evolution (I) • 1977: Apple ][ – First widely successful massproduced PC – Killer app was Visicalc spreadsheet • 1981: IBM PC – Big success because people trusted IBM – Microsoft designed the OS (PC-DOS)

Evolution (II) • 1984: Macintosh – First mass-produced PC with GUI – Was not an instant success – Rescued by laser printer • 1992: Windows 3. 1 – MSDOS + Windows 3. 1 offered the first GUI solution for IBM PCs

How IBM lost the PC market (I) • IBM PC used “off-the-shelf” components • Microsoft retained the rights to sell PCDOS to other computer makers (MSDOS) • Sole specific part was BIOS – Very basic operating system stored in read-only memory – Loads MS-DOS/Windows in main memory

How IBM lost the PC market (II) • Chip makers learned to produce functionally equivalent BIOS without violating IBM copyright – Reverse engineering: • Define IBM BIOS by all its outputs for all possible inputs • Hire people who had never seen the IBM BIOS to rewrite it

How IBM lost the PC market (III) • Rivals could sell PCs at cheaper prices than IBM – Leaner cost structure • Could come with new models faster than IBM did – Less cumbersome review process

The new frontiers • Smaller devices: – Now-defunct PDAs, smart phones, tablets – Cheaper than PCs (but tablets) – Much bigger market • New microprocessor architectures: – Intel—and AMD—pulverized the competition (Motorola 68000, MIPS, Power. PC, Sun SPARC)

Challenges • Openness • Digital divide • Addiction

HOW COMPUTERS WORK

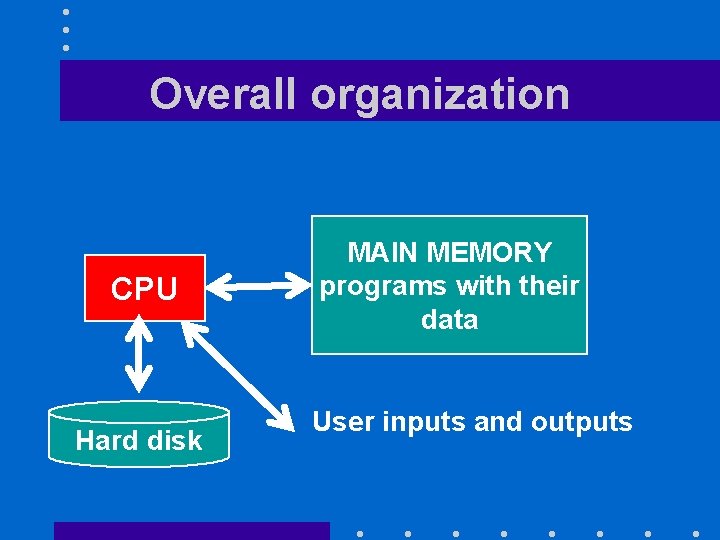
Overall organization CPU Hard disk MAIN MEMORY programs with their data User inputs and outputs

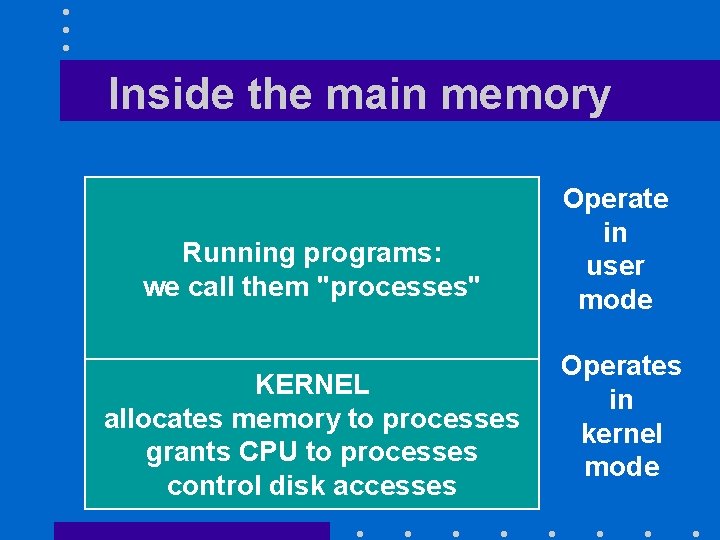
Inside the main memory Running programs: we call them "processes" KERNEL allocates memory to processes grants CPU to processes control disk accesses Operate in user mode Operates in kernel mode

The running programs • Reside in main memory – while they are running • Include many background processes – We do not see them – Take space and often CPU time • Having a large main memory allows us to run more programs at the same time

TIP • If your computer becomes slow whenever you switch among programs – You need more memory • If your computer takes a lot of time to boot – You could have a slow disk – Your OS has a lot of things to load into main memory • Useful and not so useful

The kernel • Responsible for – Managing the resources • Which process should get the CPU • How our files are stored • … – Enforcing security and preventing crashes

Security issues • Must protect running programs from attempts to modify them by other programs – Mostly programming issues – Also viruses • Must protect our data on disk – Especially if computer is shared

Running a program • OS creates a process – Allocates memory space to the process – Disk copy of program is brought from disk into main memory • Process competes with other processes for CPU time • Process is deleted when program terminates

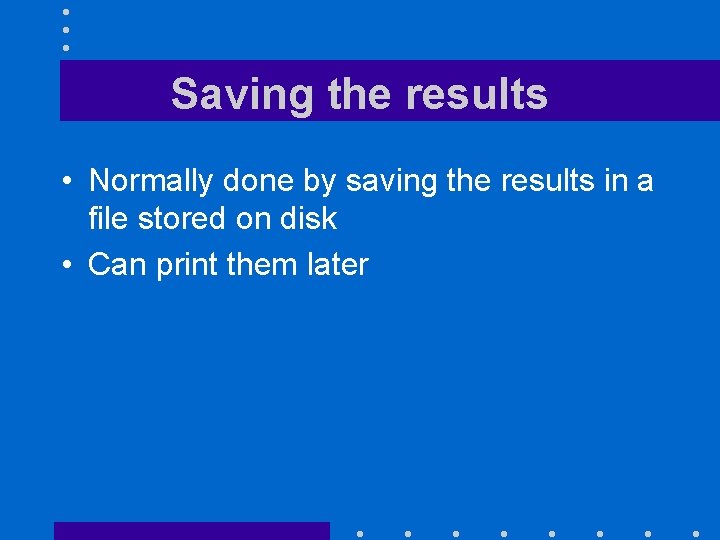
Saving the results • Normally done by saving the results in a file stored on disk • Can print them later

What is inside a program? • Instructions: – Telling the CPU what to do • Constants: – Stable values • Variables: • Memory locations where results can be stored

What is an algorithm? • “Effective method expressed as a finite list of well-defined instructions for calculating a function” – Wikipedia

Three important points • It must be an effective method – Guaranteed to produce the result • The instructions should be well-defined – Anybody using the algorithm should obtain the same answer • It should have a finite number of steps – An algorithm must terminate after a finite number of finite steps

Example: Converting C into F • If you travel outside of the US, temperatures are likely to be given in Celsius not Fahrenheit. • How the scales differ: – In Fahrenheit: Water freezes at 32 F and boils at 212 F – In Celsius: Water freezes at 0 C and boils at 100

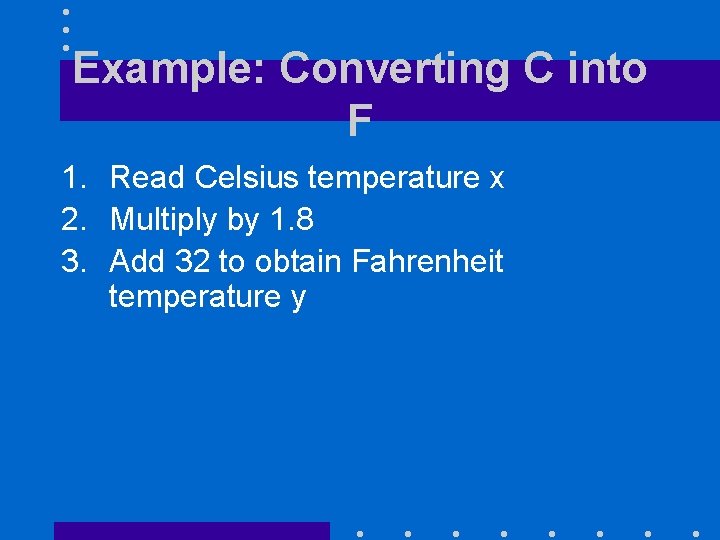
Example: Converting C into F 1. Read Celsius temperature x 2. Multiply by 1. 8 3. Add 32 to obtain Fahrenheit temperature y

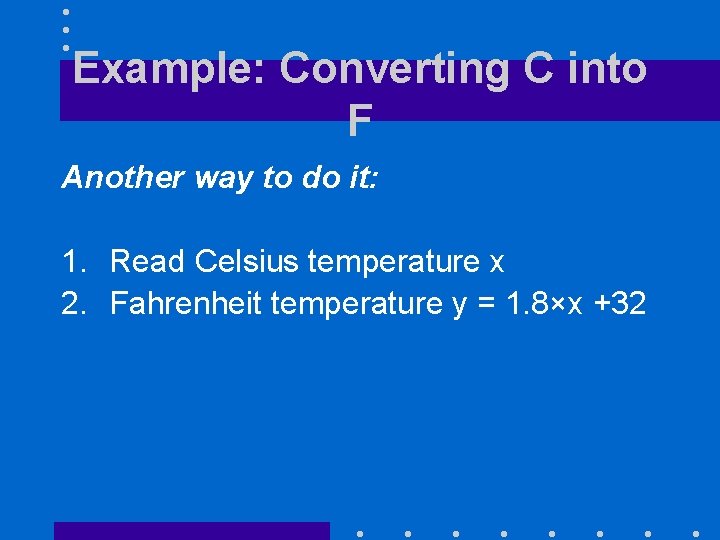
Example: Converting C into F Another way to do it: 1. Read Celsius temperature x 2. Fahrenheit temperature y = 1. 8×x +32

Counter-example (I) • British weatherman's rule of thumb: – Multiply C temperature by 2 – Add 30 • Very good for temperatures in 41 -59 F range • During a Texas summer, better use: – Multiply C temperature by 2 – Add 25

Counter-example (II) • These two rules are heuristics, not algorithms – Do not always give the right conversion – Still useful • Double and add 25 rule converts 30 C into 85 F • Right answer is 86 F

Example: Euclid’s algorithm • Used to compute the greatest common divisor of two numbers • Uses two temporary values A and B • Proceeds by successive subtractions • Always use a finite number of steps

Example: Euclid’s algorithm 1. 2. 3. 4. 5. 6. 7. 8. Read two values into X and Y If Y = 0 go to step 8 If X > Y go to step 6 Y Y – X (or subtract X from Y) Go to step 2 X X– Y (or subtract Y from X) Go to step 2 Answer is X

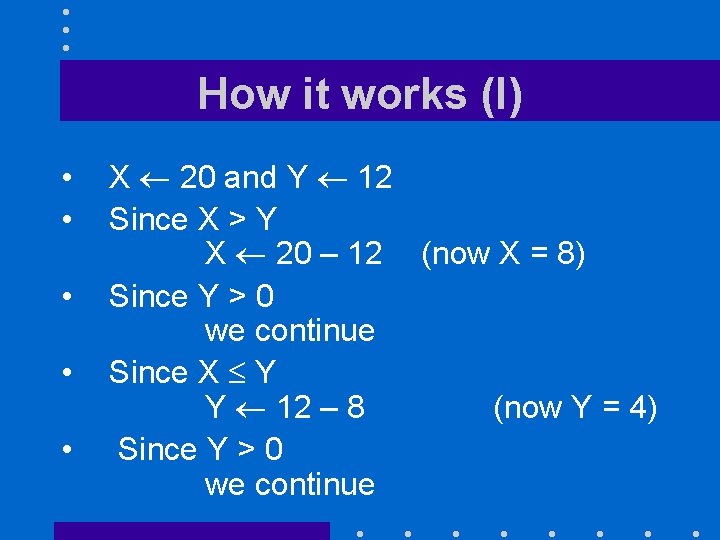
How it works (I) • • • X 20 and Y 12 Since X > Y X 20 – 12 (now X = 8) Since Y > 0 we continue Since X Y Y 12 – 8 (now Y = 4) Since Y > 0 we continue

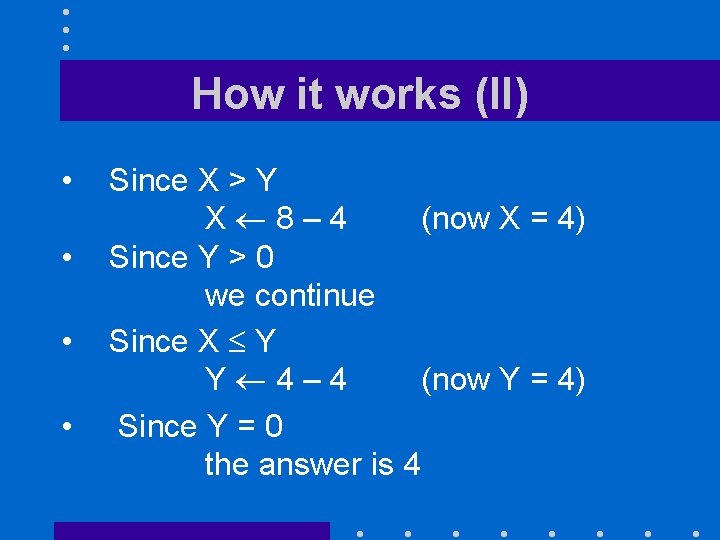
How it works (II) • • Since X > Y X 8– 4 (now X = 4) Since Y > 0 we continue Since X Y Y 4– 4 (now Y = 4) Since Y = 0 the answer is 4

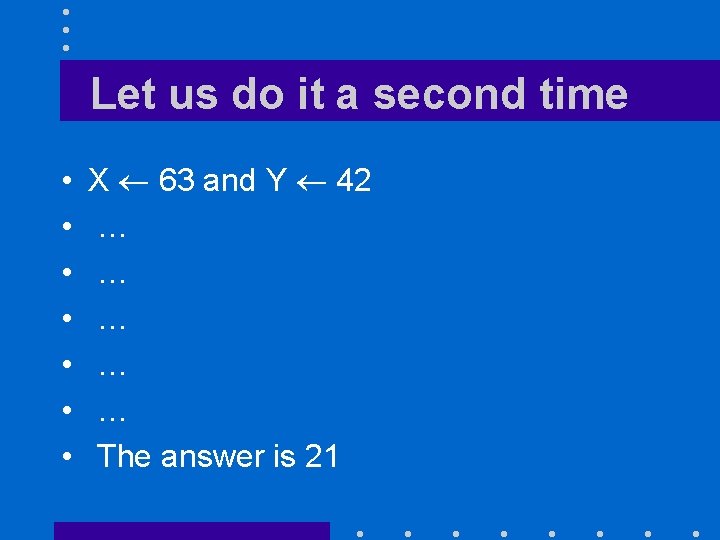
Let us do it a second time • • X 63 and Y 42 … … … The answer is 21

Observations (I) • The algorithm always takes a finite number of steps – Start with two finite numbers – Subtract at each step a strictly positive number from larger of two numbers – Stop when second number is equal to zero

Observations (II) • Algorithm contains loops – Several steps are repeated until some condition is met – Makes algorithm more compact

A program is not algorithm • It is the expression of an algorithm in a programming language • Picking the right algorithm is the most important task – After that, we just have to code!

Example • Finding a name in a table • Naïve solution is sequential search • Binary search is much faster

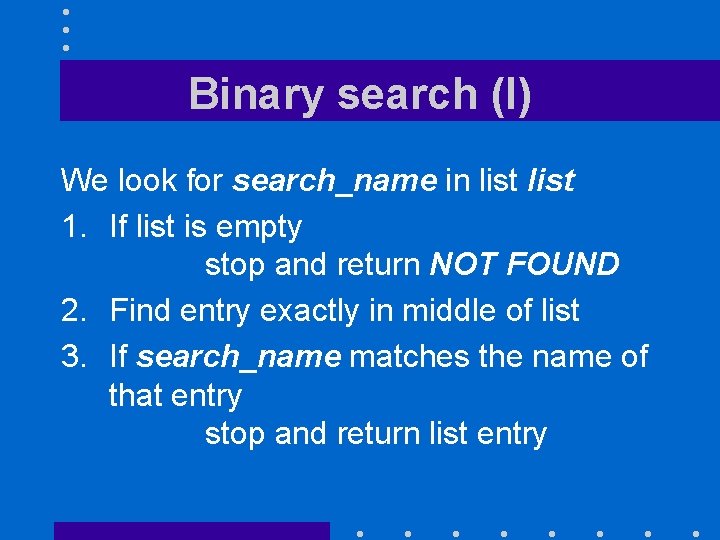
Sequential search (I) We look for search_name in list 1. Start at beginning of list 2. If list is empty stop and return NOT FOUND 3. If search_name matches name of first list entry stop and return list entry 4. If we have reached the end of the list stop and return NOT FOUND

Sequential search (II) 5. Look for next list entry 6. If search_name matches name of next list entry stop and return list entry 7. If we have reached the end of the list stop and return NOT FOUND 8. Go to step 5

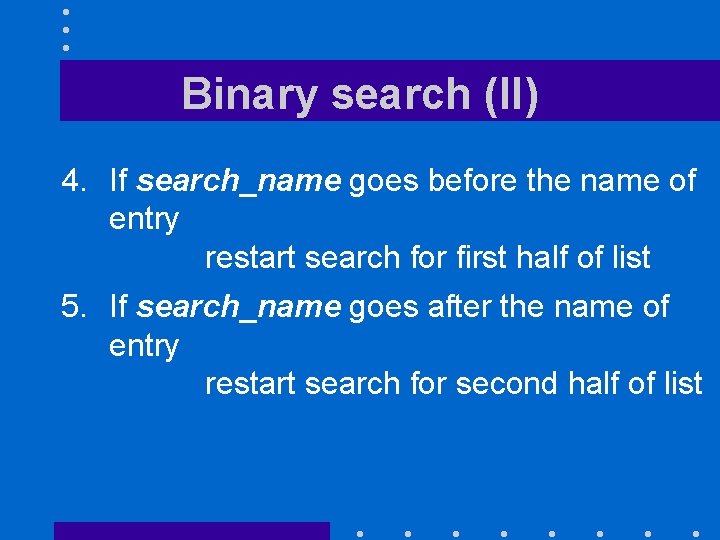
Binary search (I) We look for search_name in list 1. If list is empty stop and return NOT FOUND 2. Find entry exactly in middle of list 3. If search_name matches the name of that entry stop and return list entry

Binary search (II) 4. If search_name goes before the name of entry restart search for first half of list 5. If search_name goes after the name of entry restart search for second half of list

Example of binary search • List contains Alan Alice Barbara Emily Francis Gina Peter

Example of binary search • We look for Charles in a sorted list of names Alan Alice Barbara Emily Francis Gina Peter

Example of binary search • We compare search name with entry exactly in the middle of the list (Emily) Alan Alice Barbara Emily Francis Gina Peter

Example of binary search • Since Charles comes before Emily we can eliminate second half of list Alan Alice Barbara

Example of binary search • We compare search name with entry exactly in the middle of the list (Alice) Alan Alice Barbara

Example of binary search • Since Charles comes after Alice we can eliminate the first half of list Barbara

Example of binary search • We compare search name with entry exactly in the middle of the list (Barbara) Barbara

Example of binary search • Since Charles comes after Alice we can eliminate the first half of the list Barbara

Example of binary search • Since Charles comes before Barbara we can eliminate one half of the list

• Since list to be searched is now empty we conclude that the list does not contain Charles

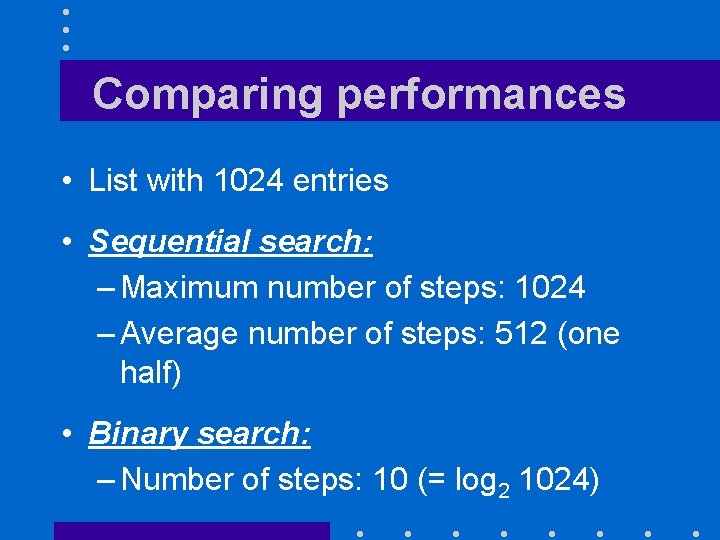
Comparing performances • List with 1024 entries • Sequential search: – Maximum number of steps: 1024 – Average number of steps: 512 (one half) • Binary search: – Number of steps: 10 (= log 2 1024)

Heuristics (I) • Many problems have no practical algorithmic solution – Algorithm will take too long • Example: – Finding the absolute best price for an item – Should check everywhere – Not cost effective

Heuristics (I) • Heuristics provide solutions – That are not guaranteed to work in all cases – That provide a good approximation of the correct solution • Example: – When we want to buy an item, we focus on the stores that are likely to sell the item at a good price

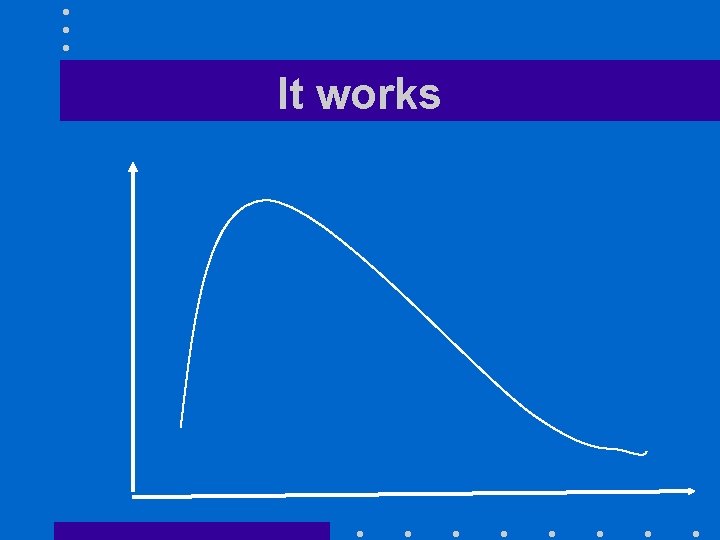
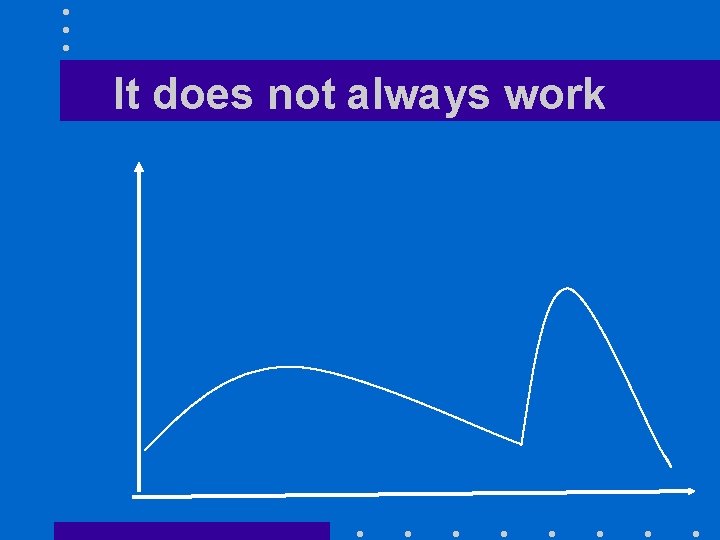
An example • Finding the maximum of a curve – Start at any given point – Move on the curve following the upward direction – Stop when the curve reaches a start going downward

It works

It does not always work