Faculty of Computer Science Input and Output Devices


- Slides: 33

Faculty of Computer Science Input and Output Devices Pooling and Interrupts Add footer here 3/4/2021 © 2006

Department of Computing Science I/O Fundamentals Programmed data transfer – An instruction for each data transfer Direct Memory Access (DMA) transfer – Processor requests transfer – DMA controller moves the data between I/O and memory Add footer here Clements, pp. 412 3/4/2021 © 2006

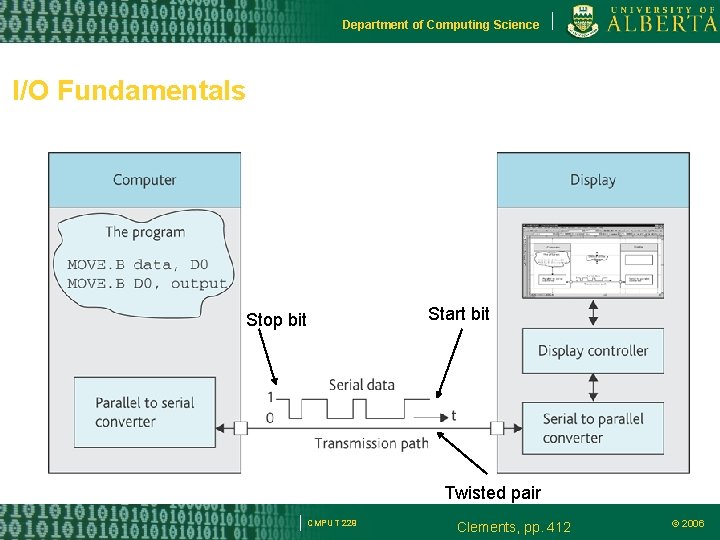
Department of Computing Science I/O Fundamentals Start bit Stop bit Twisted pair CMPUT 229 Clements, pp. 412 © 2006

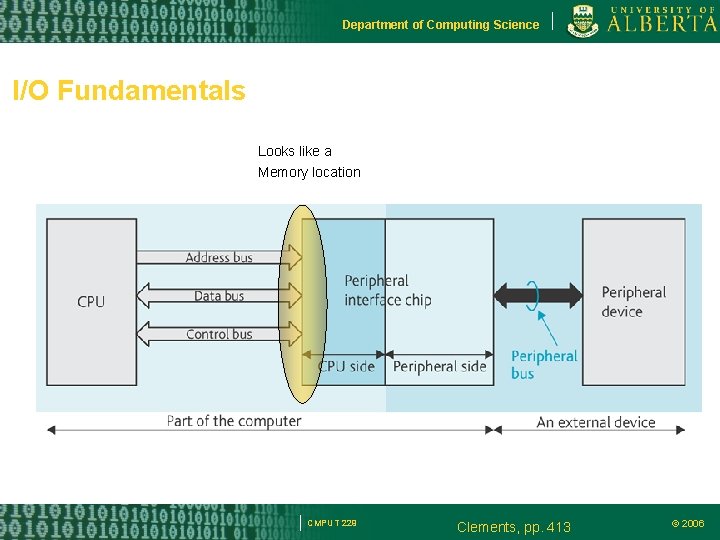
Department of Computing Science I/O Fundamentals Looks like a Memory location CMPUT 229 Clements, pp. 413 © 2006

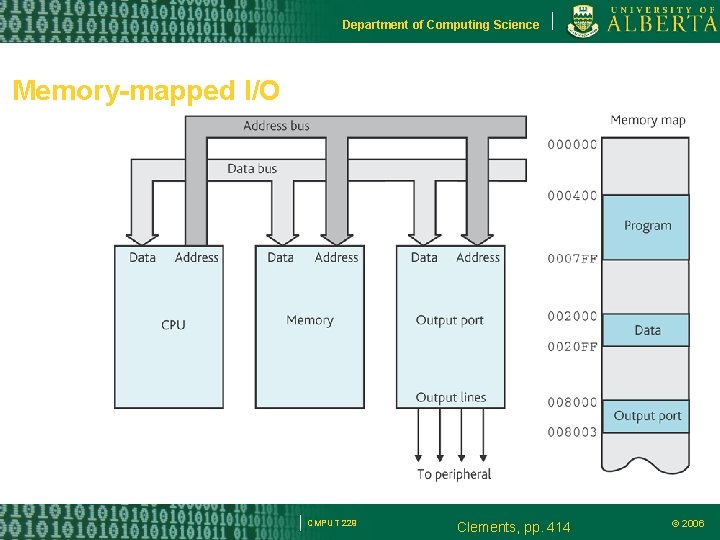
Department of Computing Science Memory-mapped I/O CMPUT 229 Clements, pp. 414 © 2006

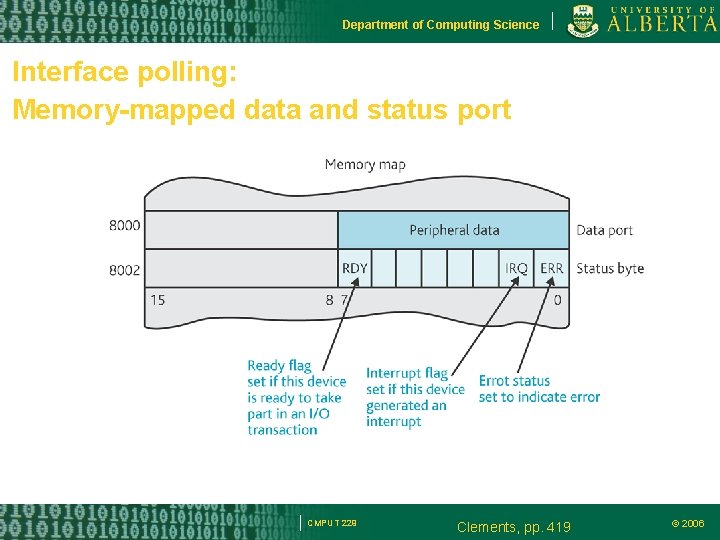
Department of Computing Science Memory-mapped I/O Each memory-mapped I/O device occupies at least two memory locations: – A location for the data input or data output – A location for the status byte associated with the port Example – Assume the following semantics for bit 0 of the status byte: • 1: port is ready for data • 0: port is busy CMPUT 229 © 2006

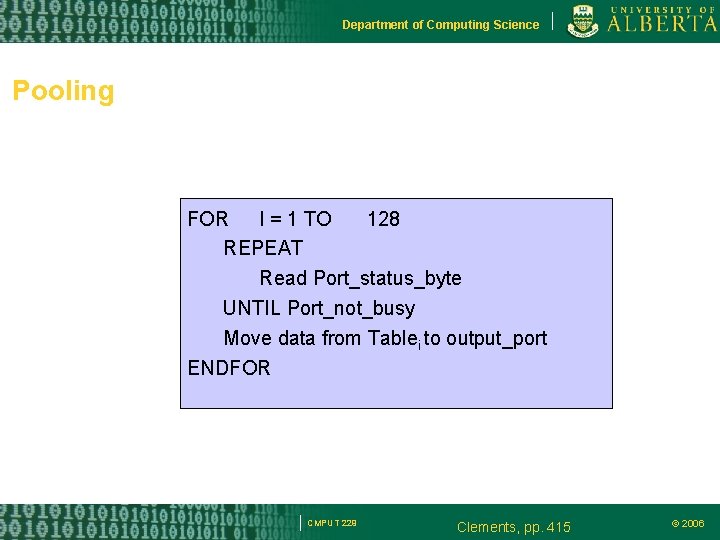
Department of Computing Science Pooling FOR I = 1 TO 128 REPEAT Read Port_status_byte UNTIL Port_not_busy Move data from Tablei to output_port ENDFOR CMPUT 229 Clements, pp. 415 © 2006

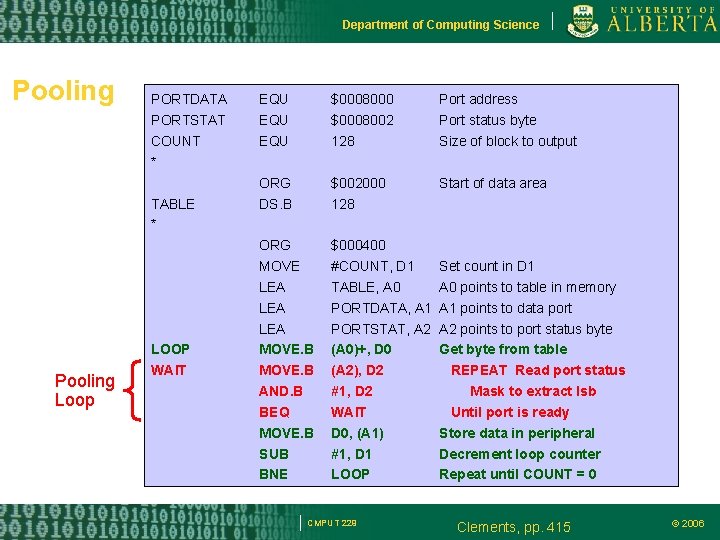
Department of Computing Science Pooling PORTDATA PORTSTAT COUNT * TABLE * Pooling Loop LOOP WAIT EQU EQU $0008000 $0008002 128 Port address Port status byte Size of block to output ORG DS. B $002000 128 Start of data area ORG MOVE LEA LEA MOVE. B AND. B BEQ MOVE. B SUB BNE $000400 #COUNT, D 1 TABLE, A 0 PORTDATA, A 1 PORTSTAT, A 2 (A 0)+, D 0 (A 2), D 2 #1, D 2 WAIT D 0, (A 1) #1, D 1 LOOP CMPUT 229 Set count in D 1 A 0 points to table in memory A 1 points to data port A 2 points to port status byte Get byte from table REPEAT Read port status Mask to extract lsb Until port is ready Store data in peripheral Decrement loop counter Repeat until COUNT = 0 Clements, pp. 415 © 2006

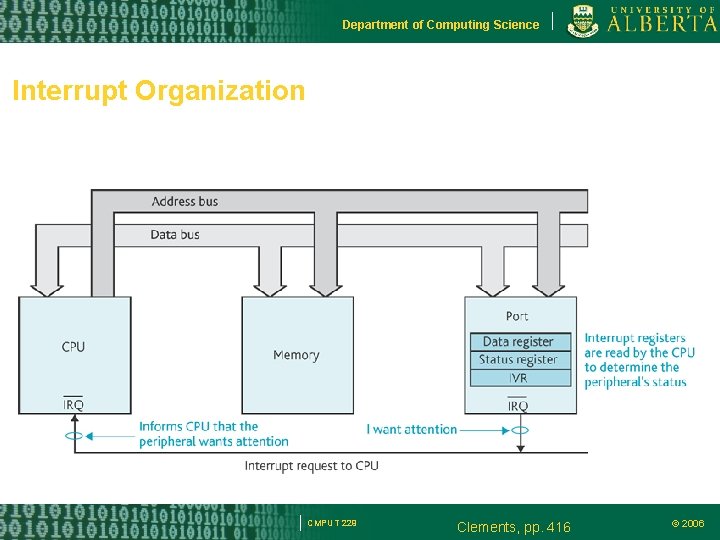
Department of Computing Science Interrupt Organization CMPUT 229 Clements, pp. 416 © 2006

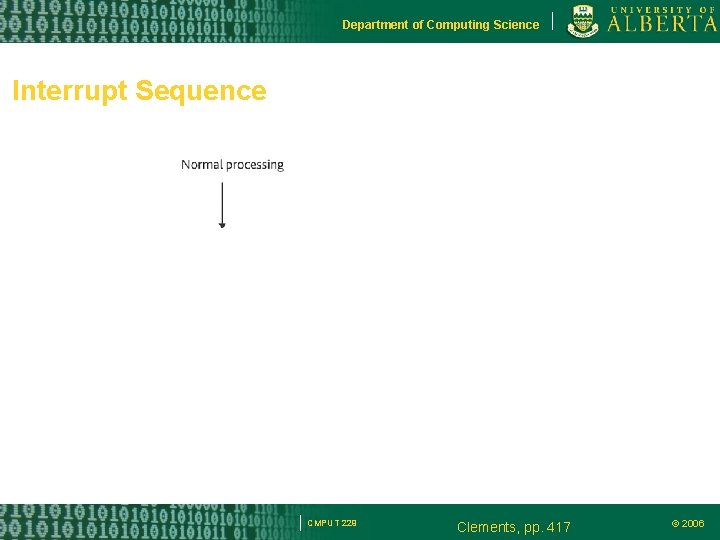
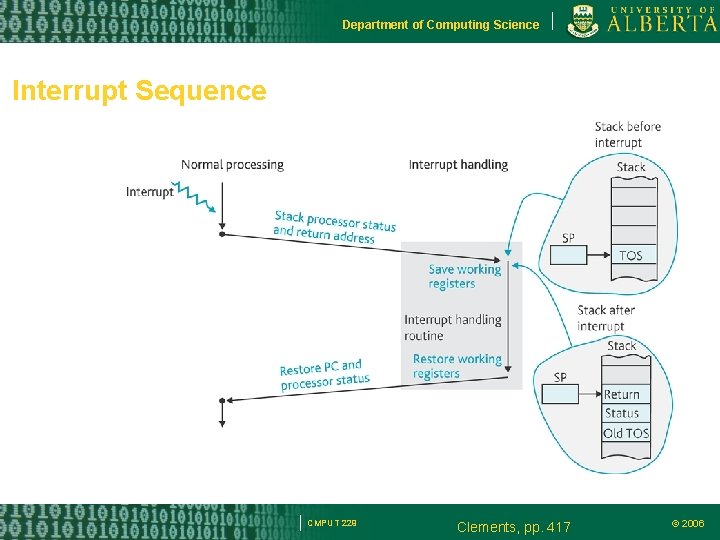
Department of Computing Science Interrupt Sequence CMPUT 229 Clements, pp. 417 © 2006

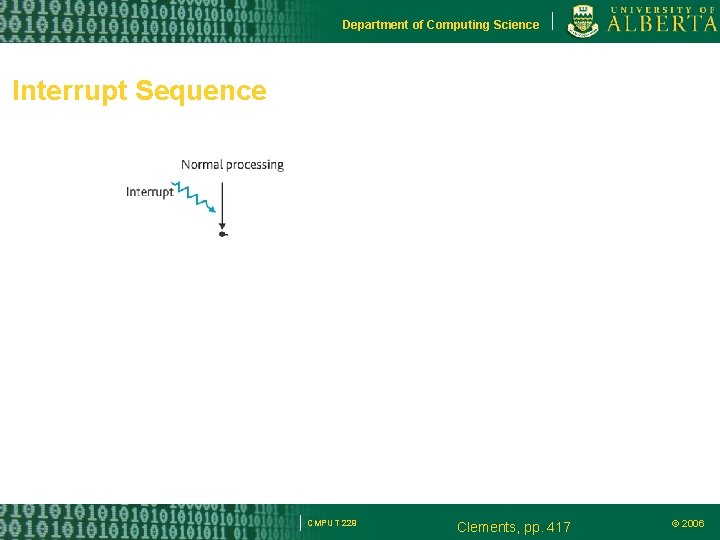
Department of Computing Science Interrupt Sequence CMPUT 229 Clements, pp. 417 © 2006

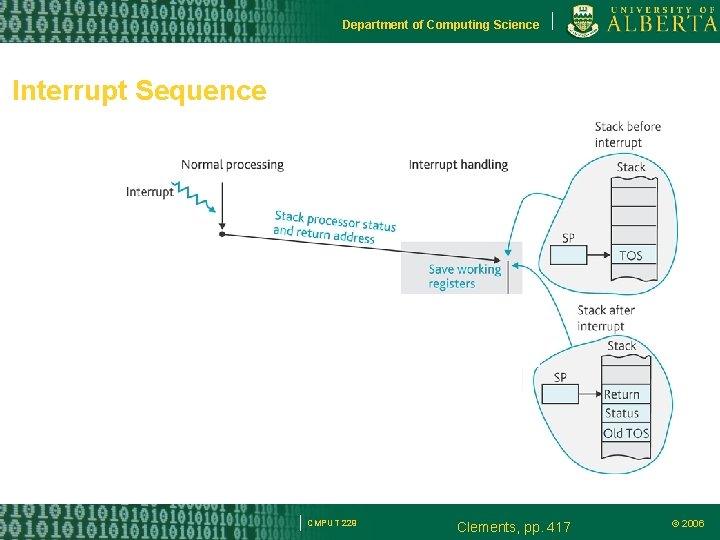
Department of Computing Science Interrupt Sequence CMPUT 229 Clements, pp. 417 © 2006

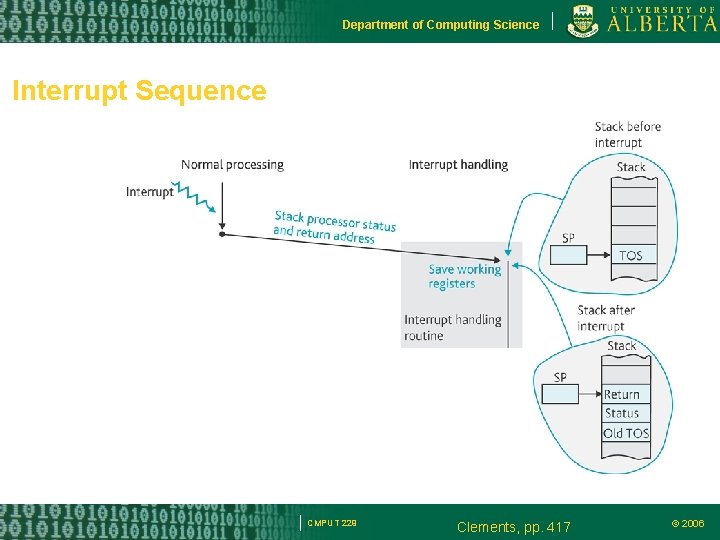
Department of Computing Science Interrupt Sequence CMPUT 229 Clements, pp. 417 © 2006

Department of Computing Science Interrupt Sequence CMPUT 229 Clements, pp. 417 © 2006

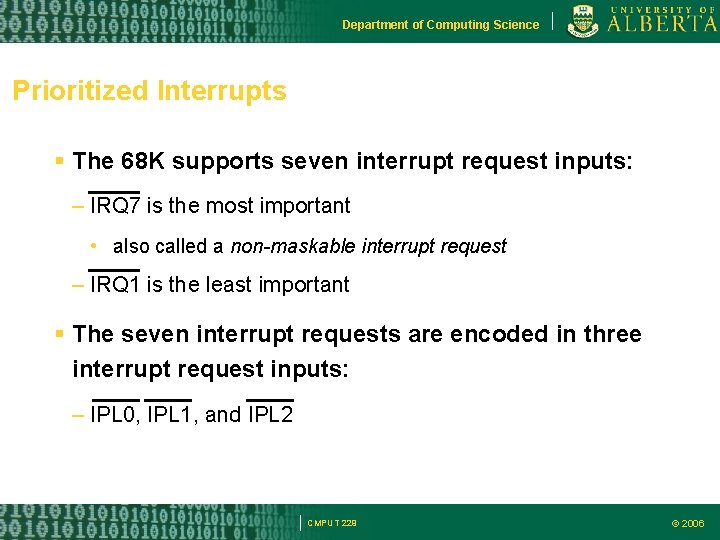
Department of Computing Science Prioritized Interrupts The 68 K supports seven interrupt request inputs: – IRQ 7 is the most important • also called a non-maskable interrupt request – IRQ 1 is the least important The seven interrupt requests are encoded in three interrupt request inputs: – IPL 0, IPL 1, and IPL 2 CMPUT 229 © 2006

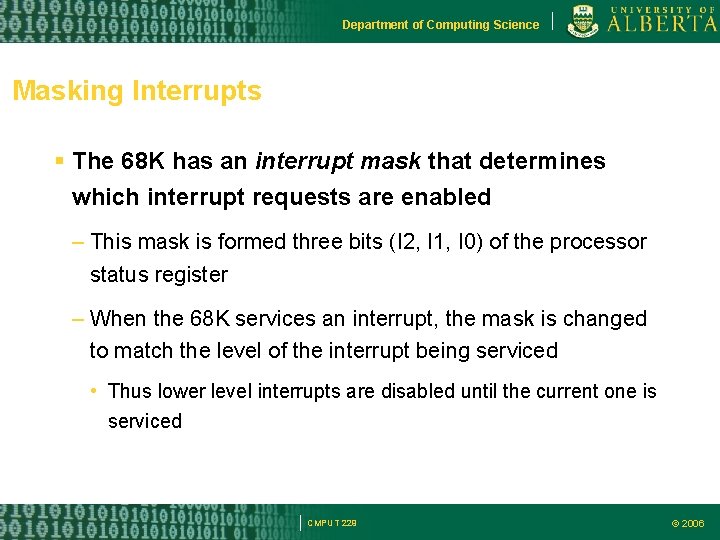
Department of Computing Science Masking Interrupts The 68 K has an interrupt mask that determines which interrupt requests are enabled – This mask is formed three bits (I 2, I 1, I 0) of the processor status register – When the 68 K services an interrupt, the mask is changed to match the level of the interrupt being serviced • Thus lower level interrupts are disabled until the current one is serviced CMPUT 229 © 2006

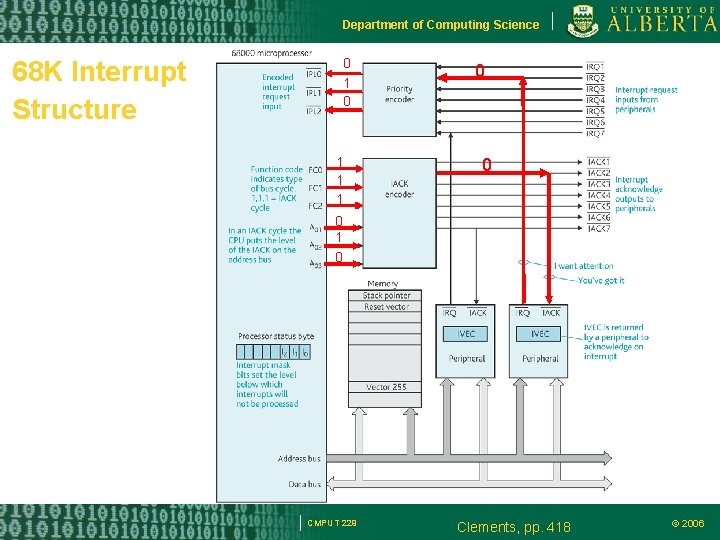
Department of Computing Science 68 K Interrupt Structure 0 1 1 1 0 0 0 1 0 CMPUT 229 Clements, pp. 418 © 2006

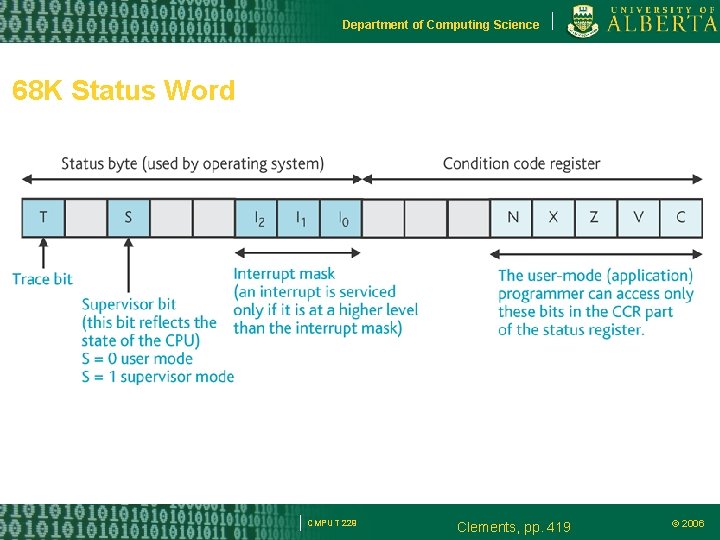
Department of Computing Science 68 K Status Word CMPUT 229 Clements, pp. 419 © 2006

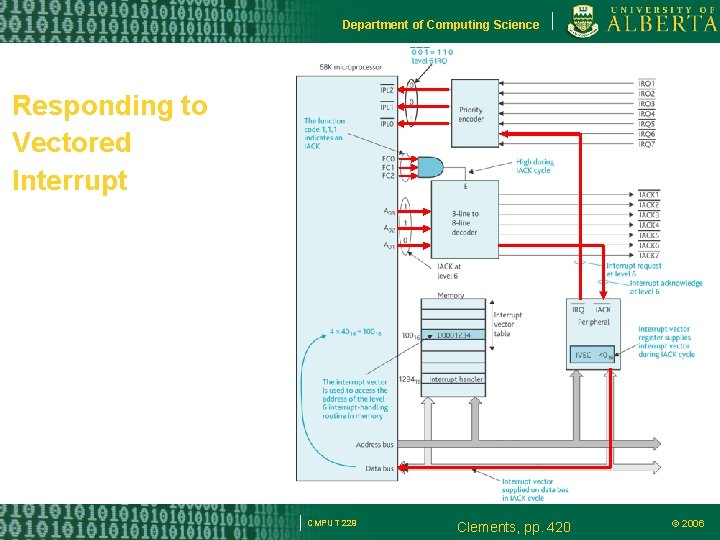
Department of Computing Science Vectored Interrupts How the processor finds out which device requested an interruption: – Polling: test sequentially each possible interruptor – Vectorized: The interruptor identifies its own interrupt handling routine CMPUT 229 © 2006

Department of Computing Science Interface polling: Memory-mapped data and status port CMPUT 229 Clements, pp. 419 © 2006

Department of Computing Science Responding to Vectored Interrupt CMPUT 229 Clements, pp. 420 © 2006

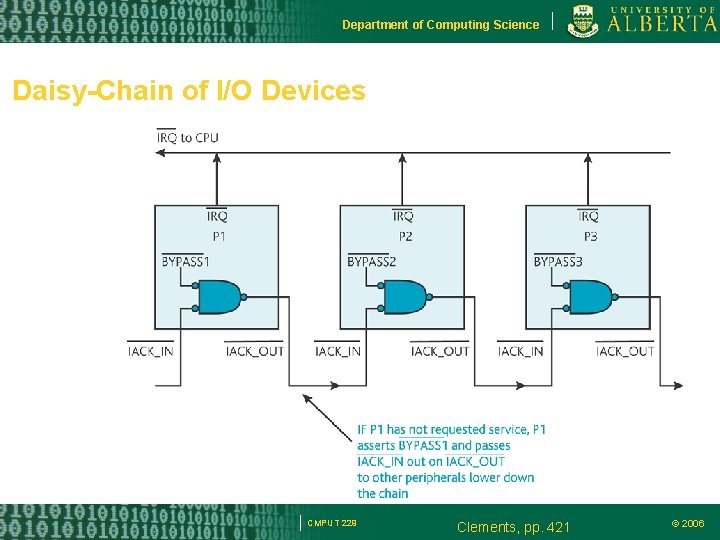
Department of Computing Science Daisy-chaining There 256 interrupt vector numbers – But the 68 K supports only seven levels of interrupt Daisy-chain links several peripherals together in a line. Devices closer to the CPU have more chances of having their interrupts acknowledged. CMPUT 229 © 2006

Department of Computing Science Daisy-Chain of I/O Devices CMPUT 229 Clements, pp. 421 © 2006

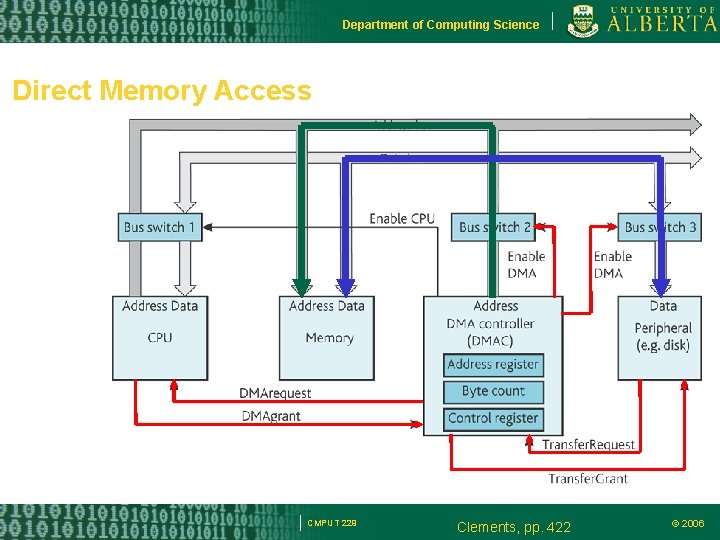
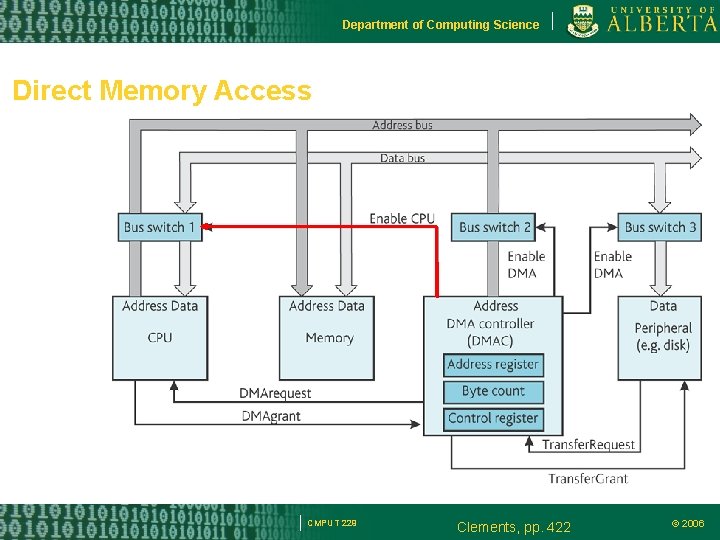
Department of Computing Science Direct Memory Access Transfer data from a peripheral and memory DMA grabs the data and address bus Releases the processor from executing many instructions to transfer the data. CMPUT 229 © 2006

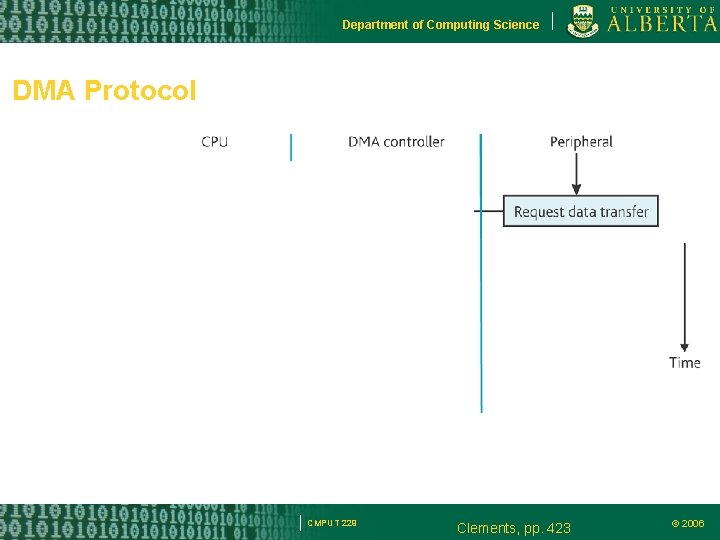
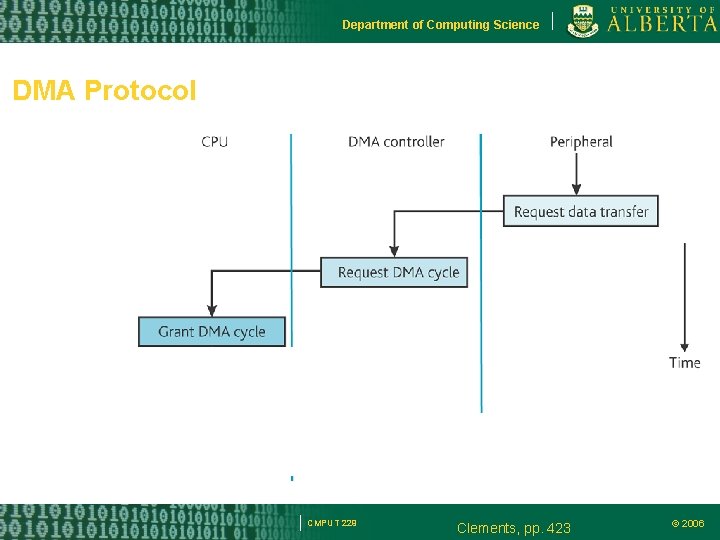
Department of Computing Science DMA Protocol CMPUT 229 Clements, pp. 423 © 2006

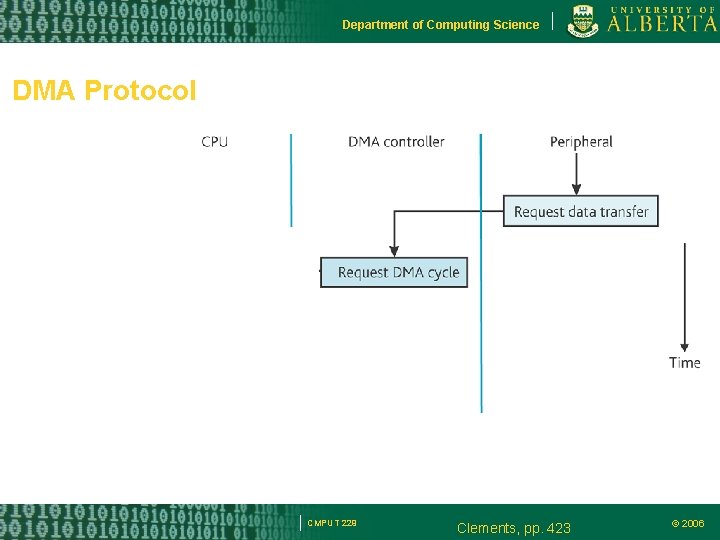
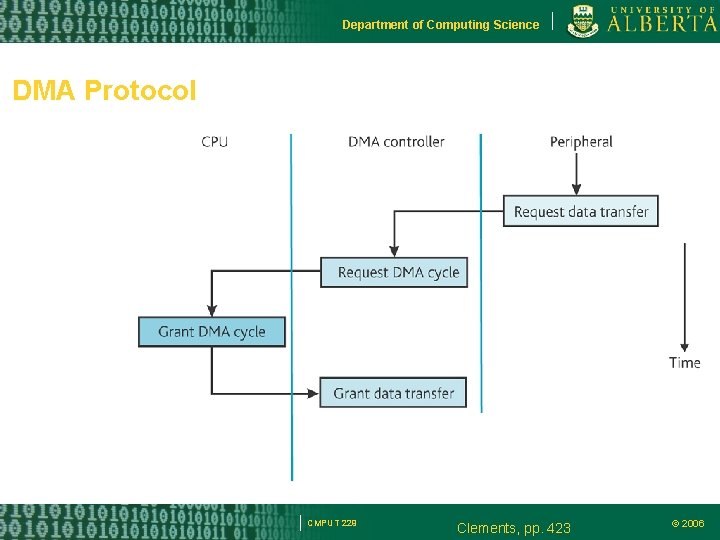
Department of Computing Science DMA Protocol CMPUT 229 Clements, pp. 423 © 2006

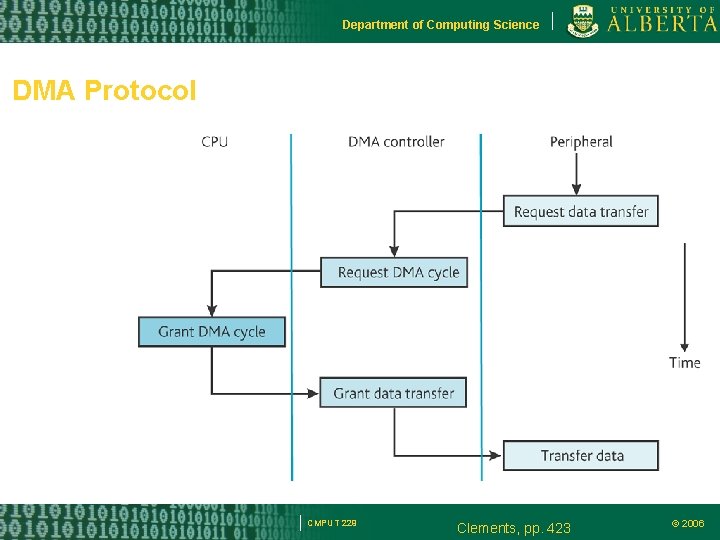
Department of Computing Science DMA Protocol CMPUT 229 Clements, pp. 423 © 2006

Department of Computing Science DMA Protocol CMPUT 229 Clements, pp. 423 © 2006

Department of Computing Science DMA Protocol CMPUT 229 Clements, pp. 423 © 2006

Department of Computing Science Direct Memory Access CMPUT 229 Clements, pp. 422 © 2006

Department of Computing Science Direct Memory Access CMPUT 229 Clements, pp. 422 © 2006

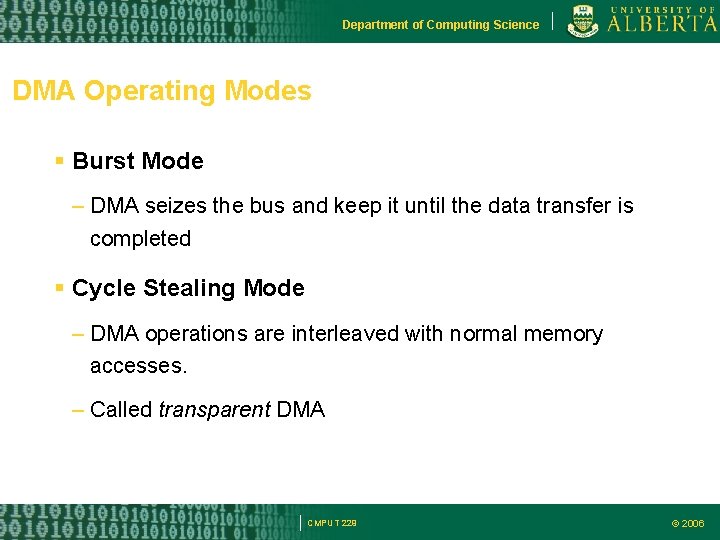
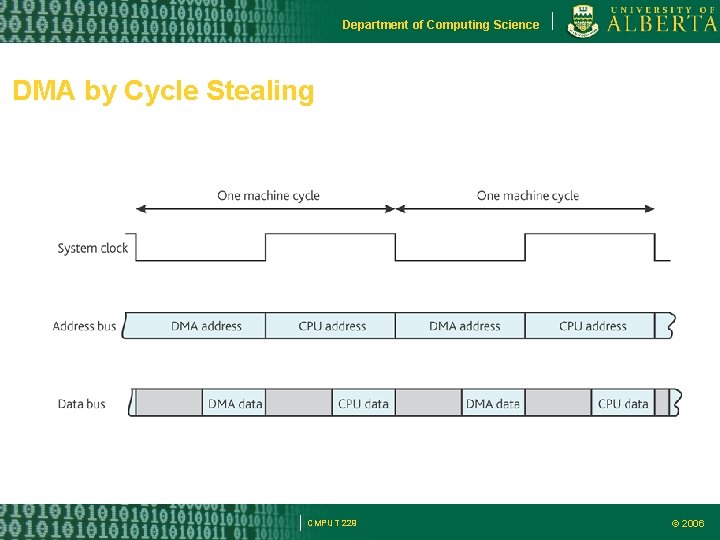
Department of Computing Science DMA Operating Modes Burst Mode – DMA seizes the bus and keep it until the data transfer is completed Cycle Stealing Mode – DMA operations are interleaved with normal memory accesses. – Called transparent DMA CMPUT 229 © 2006

Department of Computing Science DMA by Cycle Stealing CMPUT 229 © 2006