ITU T Study Group 17 Security An overview







































































- Slides: 164

ITU T Study Group 17 Security An overview for newcomers Heung Youl YOUM ITU T SG 17 Chairman 22 March 2017

Contents § § § § § Mandate of ITU T and of ITU T Study Groups Importance of telecommunication/ICT security standardization ITU Plenipotentiary Conference (PP 14) actions on ICT security World Telecommunications Standardization Assembly (WTSA 16) mandate for Study Group 17 overview § SG 17 current activities Security Coordination Future meetings Useful references Backup – SG 17 Security Recommendations 2/163

Mandate of ITU T and of ITU T Study Groups § The functions of the Telecommunication Standardization Sector shall be, bearing in mind the particular concerns of the developing countries, to fulfil the purposes of the Union relating to telecommunica tion standardization, as stated in Article 1 of this Constitution, by studying technical, operating and tariff questions and adopting recom mendations on them with a view to standardizing telecommunications on a worldwide basis. (ITU T Constitution Art. 17, Nos 104). § Telecommunication standardization study groups shall study questions adopted in accordance with a procedure established by the world telecommunication standardization assembly and prepare draft recommendations to be adopted in accordance with the procedure set forth in Nos. 246 A to 247 of this Convention. (ITU Convention Art. 14 Nos 192) § The study groups shall, […], study technical, operating and tariff questions and prepare recommendations on them with a view to standardizing telecommunications on a worldwide basis, […]. (ITU Convention Art. 14 Nos 193) 3/163

Contents § § § § § Mandate of ITU T and of ITU T Study Groups Importance of telecommunication/ICT security standardization ITU Plenipotentiary Conference (PP 14) actions on ICT security World Telecommunications Standardization Assembly (WTSA 16) mandate for Study Group 17 overview § SG 17 current activities Security Coordination Future meetings Useful references Backup – SG 17 Security Recommendations 4/163

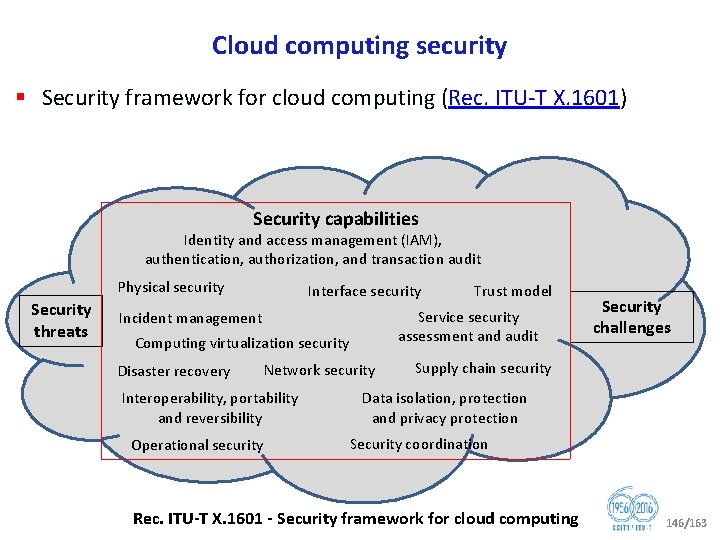
Importance of telecommunication/ICT security standardization (1/4) § National laws are often inadequate to protect against attacks. § They are insufficient from the timing perspective (i. e. laws cannot keep up with the pace of technological change), and, since attacks are often transnational, national laws may well be inapplicable anyway. § What this means is that the defenses must be largely technical, procedural and administrative (organizational); i. e. those that can be addressed in standards. § The development of standards in an open forum that comprises international specialists from a wide variety of environments and backgrounds provides the best possible opportunity to ensure relevant, complete and effective standards. § SG 17 provides the environment in which such standards can be, and are being, developed. 5/163

Importance of telecommunication/ICT security standardization (2/4) § The primary challenges are the time it takes to develop a standard (compared to the speed of technological change and the emergence of new threats) and the shortage of skilled and available resources. § We must work quickly to respond to the rapidly evolving technical and threat environment but we must also ensure that the standards we produce are given sufficient consideration and review to ensure that they are complete and effective. § We must recognize and respect the differences in developing countries respective environments: their telecom infrastructures may be at different levels of development from those of the developed countries; their ability to participate in, and contributing directly to the security standards work may be limited by economic and other considerations; and their needs and priorities may be quite different. 6/163

Importance of telecommunication/ICT security standardization (3/4) § ITU T can help the developing countries by fostering awareness of the work we are doing (and why we are doing it), by encouraging participation in the work particularly via the electronic communication facilities now being used (e. g. web based meetings and teleconferencing), and, most particularly, by encouraging the members from the developing countries to articulate their concerns and priorities regarding the telecommunication/ICT security. § The members from the developed nations should not confuse their own needs with those of the developing countries, nor should they make assumptions about what the needs and priorities of the developing countries may be. 7/163

Importance of telecommunication/ICT security standardization (4/4) § For on going credibility, we need performance measures that provide some indication of the effectiveness of our standards. In the past there has been too much focus on quantity (i. e. how many standards are produced) than on the quality and effectiveness of the work. § Going forward, we really need to know which standards are being used (and which are not being used), how widely they are used, and how effective they are. § This is not going to be easy to determine but it would do much more to the ITU T’s credibility if it could demonstrate the value and effectiveness of standards that have been developed rather than simply saying “we produced x number of standards”. § The number of standards produced is irrelevant: what counts is the impact they have. 8/163

§ Mandate of ITU T and of ITU T Study Groups § Importance of telecommunication/ICT security standardization § ITU Plenipotentiary Conference (PP 14) actions on ICT security § World Telecommunications Standardization Assembly (WTSA 16) mandate for Study Group 17 § Study Group 17 overview § SG 17 current activities § Security Coordination § Future meetings § Useful references § Backup – SG 17 Security Recommendations 9/163

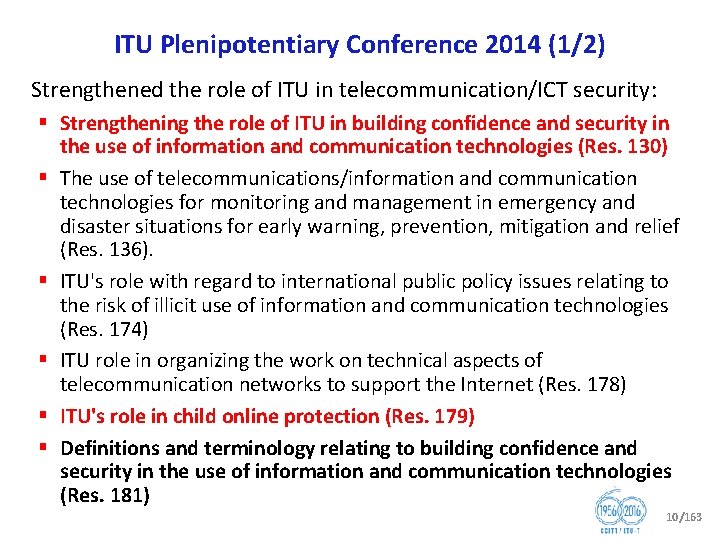
ITU Plenipotentiary Conference 2014 (1/2) Strengthened the role of ITU in telecommunication/ICT security: § Strengthening the role of ITU in building confidence and security in the use of information and communication technologies (Res. 130) § The use of telecommunications/information and communication technologies for monitoring and management in emergency and disaster situations for early warning, prevention, mitigation and relief (Res. 136). § ITU's role with regard to international public policy issues relating to the risk of illicit use of information and communication technologies (Res. 174) § ITU role in organizing the work on technical aspects of telecommunication networks to support the Internet (Res. 178) § ITU's role in child online protection (Res. 179) § Definitions and terminology relating to building confidence and security in the use of information and communication technologies (Res. 181) 10/163

ITU Plenipotentiary Conference 2014 (2/2) New Resolutions: § Combating counterfeit telecommunication/ information and communication technology devices (Resolution 188) § Assisting Member States to combat and deter mobile device theft (Resolution 189) § Facilitating the Internet of Things to prepare for a globally connected world (Resolution 197) § To promote efforts for capacity building on software defined networking in developing countries (Resolution 199) § Creating an enabling environment for the deployment and use of information and communication technology applications (Resolution 201) § Connect 2020 Agenda for global telecommunication/ information and communication technology development (Resolution 200). 11/163

§ Mandate of ITU T and of ITU T Study Groups § Importance of telecommunication/ICT security standardization § ITU Plenipotentiary Conference (PP 14) actions on telecommunication/ICT security § World Telecommunications Standardization Assembly (WTSA 16) mandate for Study Group 17 § Study Group 17 overview § SG 17 current activities § Security Coordination § Future meetings § Useful references § Backup – SG 17 Security Recommendations 12/163

ITU T SG 17 mandate established by World Telecommunication Standardization Assembly (WTSA 16) Title: Security Responsible for building confidence and security in the use of information and communication technologies (ICTs). This includes studies relating to cybersecurity, security management, countering spam and identity management. It also includes security architecture and framework, protection of personally identifiable information, and security of applications and services for the Internet of things (Io. T), smart grid, smartphone, software defined networking (SDN), Internet Protocol television (IPTV), web services, social network, cloud computing, big data analytics, mobile financial system and telebiometrics. Also responsible for the application of open system communications, including directory and object identifiers, and for technical languages, the method for their usage and other issues related to the software aspects of telecommunication systems and test specification languages in support of conformance testing to improve the quality of Recommendations. 13/163

ITU T SG 17 mandate established by World Telecommunication Standardization Assembly (WTSA 16) Lead Study Group for: – Security – Identity management – Languages and description techniques § Responsible for specific E, F, X and Z series Recommendations § Responsible for 12 Questions 14/163

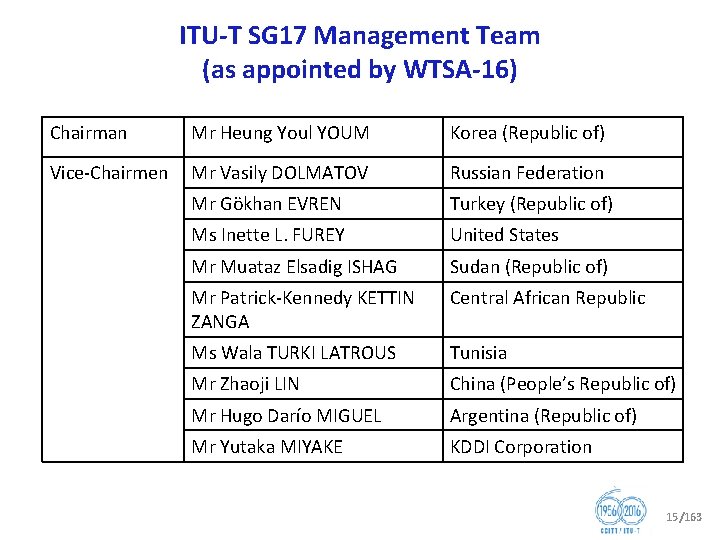
ITU T SG 17 Management Team (as appointed by WTSA 16) Chairman Mr Heung Youl YOUM Korea (Republic of) Vice Chairmen Mr Vasily DOLMATOV Russian Federation Mr Gökhan EVREN Turkey (Republic of) Ms Inette L. FUREY United States Mr Muataz Elsadig ISHAG Sudan (Republic of) Mr Patrick Kennedy KETTIN ZANGA Central African Republic Ms Wala TURKI LATROUS Tunisia Mr Zhaoji LIN China (People’s Republic of) Mr Hugo Darío MIGUEL Argentina (Republic of) Mr Yutaka MIYAKE KDDI Corporation 15/163

§ Mandate of ITU T and of ITU T Study Groups § Importance of telecommunication/ICT security standardization § ITU Plenipotentiary Conference (PP 14) actions on telecommunication/ICT security § World Telecommunications Standardization Assembly (WTSA 16) mandate for Study Group 17 § Study Group 17 overview § SG 17 current activities § Security Coordination § Future meetings § Useful references § Backup – SG 17 Security Recommendations 16/163

ITU T Study Group 17 Overview § Meets twice a year. Last September 2016 SG 17 meeting had 143 participants from 29 Member States, 18 Sector Members, 1 Associates, and 1 Academia. § As of 1 January 2017, SG 17 is responsible for 344 approved Recommendations, 26 approved Supplements and 3 approved Implementer’s Guides in the E, F, X and Z series. § Large program of work: • 81 new or revised Recommendations and other texts are currently under development • 25 new work items added to work program in 2016 • Results of September 2016 meeting and AAP Last Call: approval of 21 Recommendations, 1 Amendment, 2 Supplements, 1 Implementer Guide, 2 Technical Corrigenda; 7 Recommendations in TAP. 17/163

SG 17 – Mission § Building confidence and security in the use of information and communication technologies (ICTs) is one of the top priorities of the ITU (PP Res. 130, WSIS Action Line C 5). § Strengthening the trust framework, authentication, and protection of personally identifiable information is a prerequisite for the development of the Information Society and for building confidence among users of ICTs. § Security of and for telecommunications and Information and Communication Technologies (ICT security) remains an area where technical security standards will be needed. § New emerging technologies such as cloud computing, smart grid, intelligent transportation systems, 5 G, SDN, Big Data analytics, Io. T, need technical measures to protect PII of citizens, as well as technical measures to protect children online. New security approaches to adequately address security threats may be required. 18/163

Foundation of SG 17 § Study Group 17’s work on security has had continued and remarkable growth throughout this study period resulting in a center of excellence – a core competency in security. § Study Group 17 is the Standardization Sector’s lead study group in security; is the right place for international inter governmental security standardization. § The work of SG 17 has been maintained effectively throughout this study period. § A foundation of security Recommendations has been established, collaboration arrangements with other bodies are in place, and an ongoing work program of security Questions for the next study period. 19/163

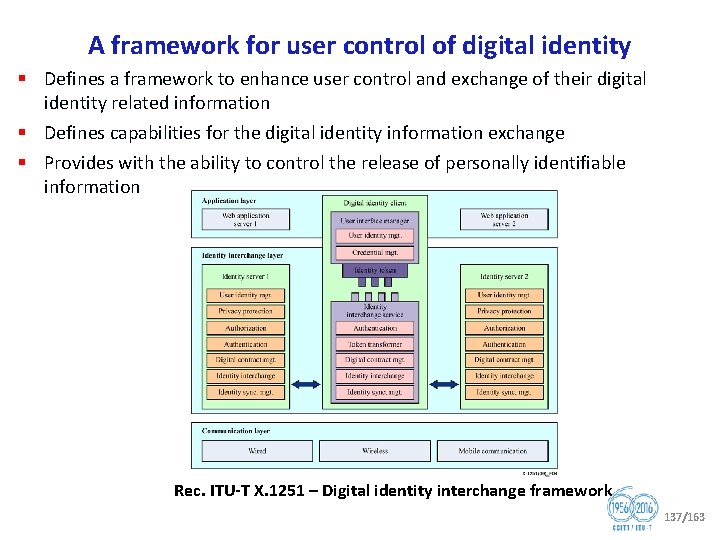
Study Group 17 is the Lead Study Group on: ● Security ● Identity management (Id. M) ● Languages and description techniques § A study group may be designated by WTSA or TSAG as the lead study group for ITU‑T studies forming a defined programme of work involving a number of study groups. § This lead study group is responsible for the study of the appropriate core Questions. § In addition, in consultation with the relevant study groups and in collaboration, where appropriate, with other standards bodies, the lead study group has the responsibility to define and maintain the overall framework and to coordinate, assign (recognizing the mandates of the study groups) and prioritize the studies to be carried out by the study groups, and to ensure the preparation of consistent, complete and timely Recommendations. * Extracted from WTSA 16 Resolution 1 20/163

SG 17 is “Parent” for Joint Coordination Activities (JCAs) on: ● Identity management ● Child online protection § A joint coordination activity (JCA) is a tool for management of the work programme of ITU T when there is a need to address a broad subject covering the area of competence of more than one study group. A JCA may help to coordinate the planned work effort in terms of subject matter, time frames for meetings, collocated meetings where necessary and publication goals including, where appropriate, release planning of the resulting Recommendations. § The establishment of a JCA aims mainly at improving coordination and planning. The work itself will continue to be conducted by the relevant study groups and the results are subject to the normal approval processes within each study group. A JCA may identify technical and strategic issues within the scope of its coordination role, but will not perform technical studies nor write Recommendations. A JCA may also address coordination of activities with recognized standards development organizations (SDOs) and forums, including periodic discussion of work plans and schedules of deliverables. The study groups take JCA suggestions into consideration as they carry out their work. * Extracted from Recommendation ITU T A. 1 21/163

ITU T Joint Coordination Activity on Identity Management (JCA Id. M) § Coordinates the ITU T identity management (Id. M) work. § Ensures that the ITU T Id. M work is progressed in a well coordinated way between study groups, in particular with SG 2, SG 13, SG 15, SG 16, and SG 17. § Analyzes Id. M standardization items and coordinates an associated roadmap with ITU T Q 10/17. § Acts as a point of contact within ITU T and with other SDOs/Fora on Id. M in order to avoid duplication of work and assist in implementing the Id. M tasks assigned by WTSA 16 Resolution 2 and in implementing GSC 17 Resolution 4 on identity management. § In carrying out the JCA Id. M’s external collaboration role, representatives from other relevant recognized SDOs/Fora and regional/national organizations may be invited to join the JCA Id. M. § Maintains Id. M roadmap and landscape document/WIKI. JCA Id. M co chairmen: Mr Abbie Barbir, Mr Hiroshi Takechi 22/163

Id. M Coordination with other bodies ITU-T JCA-Id. M ITU-T SGx /163

ITU T Joint Coordination Activity on Child Online Protection (JCA COP) – will discuss for its continuation in this meeting Purpose and objectives: § Coordinates activity on COP across ITU T study groups, in particular Study Groups 2, 9, 13, 15, 16 and 17, and coordinates with ITU R, ITU D and the Council Working Group on Child Online Protection § Provides a visible contact point for COP in ITU T § Cooperates with external bodies working in the field of COP, and enables effective two way communication with these bodies Tasks: § Maintain a list of representatives for COP in each study group § Exchange information relevant to COP between all stakeholders; e. g. information from: – Member States on their national efforts to develop COP related technical approaches and standards – NGOs on their COP activities and on COP information repositories – GSMA on an industry perspective on COP § Promote a coordinated approach towards any identified and necessary areas of standardization § Address coordination of activity with relevant SDOs and forums, including periodic discussion of work plans and schedules of deliverables on COP (if any) JCA COP Chairman: Mr Philip Rushton. 24/163

Coordination on Child Online Protection ITU-T JCA-COP - ITU Member States - ITU-T SGx, JCA-AHF - ITU CWG COP - ITU-R, ITU-D /163

ITU T SG 17 Regional Group for Africa (SG 17 RG AFR) § The main objective of the Regional Group will be to encourage national authorities and operators from countries in Africa to work together and better contribute to ITU T SG 17 activities in general and in particular in line with the SG 17 mandate. § To encourage active participation of African administrations, regulators and operators in the work of ITU T SG 17 and to report periodically the outcomes and deliverables § To facilitate the participation of Member States and Sector Members of the African region in ITU T meetings related to ICT security § To encourage African countries to contribute actively in developing ITU T security Recommendations work § … § SG 17 RG AFR chairman: Mr Michael Katundu, Kenya § SG 17 RG AFR vice chairmen: – Mr Mohamed M. K. Elhaj, Sudan – Mr Patrick Mwesigwa, Uganda – Mr Mohamed Touré, Guinea • See SG 17 RG AFR web page for more information http: //www. itu. int/en/ITU T/studygroups/2013 2016/17/sg 17 rgafr. 26/163

ITU T SG 17 Regional Group for Africa (SG 17 RG AFR) § Second meeting: Khartoum, Sudan, 27 – 28 July 2016 § Hosted by National Telecommunication Corporation (NTC) § Preceded by a three day Joint ITU/ATU Workshop on "Cybersecurity Strategy in African Countries". § Attendance: 23 participants from 10 different countries § The meeting discussed one contribution and gave feedback for improvements. § Using an updated list of hot topics of interest to Africa, the meeting agreed a structure of the regional group having three working groups: – WG 1: Cybersecurity, co chaired by Mr Adetunji BASORUN (Nigeria), and Mr N'takpe Ernest BOKA (Côte d'Ivoire, République du)). – WG 2: Electronic Transaction and Mobile Security, co chaired by Mr Abubakar MAINA (Nigeria), and Mr William KADIO (Côte d'Ivoire, République du)). – WG 3: Internet Infrastructure Security, co chaired by Mr Mutaz ISHAG (Sudan, Republic of), and Mr Egide NDAYIZEYE (Burundi), Mr Bertrand Kisito NGA (Cameroon). § Bridging standardization gap (BSG) training session by TSB § See SG 17 RG AFR web page for more information http: //www. itu. int/en/ITU T/studygroups/2013 2016/17/sg 17 rgafr. 27/163

Participation of Governments in SG 17 28/163

Participation of Telecommunication Operators and Service Providers in SG 17 29/163

Participation of manufacturers, vendors, scientific or industrial organizations, Associates, and other entities dealing with telecommunication matters in SG 17 30/163

Participation of Universities, research establishments and Academia in SG 17 31/163

Hot Topics within Study Group 17 Technical solution toolkit for trust Identity management and telebiometrics Application security solutions 32/163

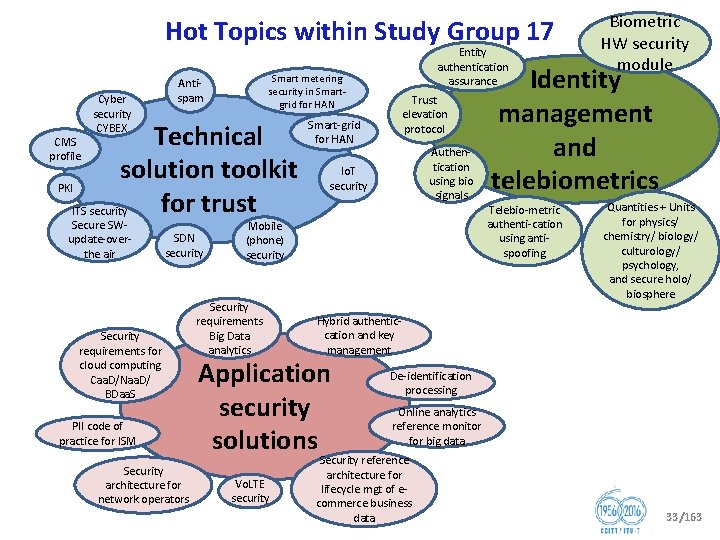
Hot Topics within Study Group 17 Cyber security CYBEX Smart metering security in Smart grid for HAN Anti spam Technical solution toolkit PKI for trust ITS security CMS profile Secure SW update over the air SDN security Security requirements for cloud computing Caa. D/Naa. D/ BDaa. S PII code of practice for ISM Security architecture for network operators Entity authentication assurance Trust elevation protocol Smart grid for HAN Authen tication using bio signals Io. T security Mobile (phone) security Security requirements Big Data analytics Identity management and telebiometrics Telebio metric authenti cation using anti spoofing Quantities + Units for physics/ chemistry/ biology/ culturology/ psychology, and secure holo/ biosphere Hybrid authentic cation and key management Application security solutions Vo. LTE security Biometric HW security module De identification processing Online analytics reference monitor for big data Security reference architecture for lifecycle mgt of e commerce business data 33/163

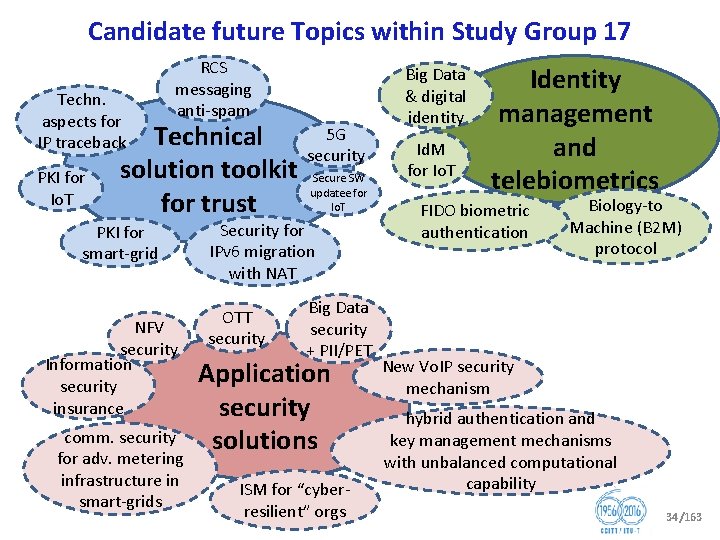
Candidate future Topics within Study Group 17 Techn. aspects for IP traceback PKI for Io. T RCS messaging anti spam 5 G Technical security solution toolkit Secure SW updatee for Io. T for trust PKI for smart grid NFV security Information security insurance comm. security for adv. metering infrastructure in smart grids Security for IPv 6 migration with NAT OTT security Big Data security + PII/PET Application security solutions ISM for “cyber resilient” orgs Big Data & digital identity Id. M for Io. T Identity management and telebiometrics FIDO biometric authentication Biology to Machine (B 2 M) protocol New Vo. IP security mechanism hybrid authentication and key management mechanisms with unbalanced computational capability 34/163

§ Mandate of ITU T and of ITU T Study Groups § Importance of telecommunication/ICT security standardization § ITU Plenipotentiary Conference (PP 14) actions on telecommunication/ICT security § World Telecommunications Standardization Assembly (WTSA 16) mandate for Study Group 17 § Study Group 17 overview § SG 17 current activities § Security Coordination § Future meetings § Useful references § Backup – SG 17 Security Recommendations 35/163

ITU T Study Group 17 Overview § Work organized into 4 Working Parties with 12 Questions § 1 joint Correspondence Group with SG 20, 5 interim Rapporteur groups meetings took place since last August 2016 SG 17 meeting § See SG 17 web page for more information http: //itu. int/ITU T/go/sg 17 36/163

Question 1/17 Telecommunication/ICT security coordination § Security Coordination • • Coordinate security matters within SG 17, with ITU T SGs, ITU D, ITU R and externally with other SDOs Maintain reference information on LSG security webpage § ICT Security Standards Roadmap • Searchable database of approved ICT security standards from ITU T, ISO/IEC, ETSI, IETF and others § Security Compendium • Catalogue of approved security related Recommendations and security definitions extracted from approved Recommendations § ITU T Security Manual • 6 th edition was published as a Technical Report in October 2015 • Technical Report on the successful use of security standards § Promotion (ITU T security work and attract participation) § Security Workshops 37/163

Question 1/17 (cnt’d) Telecommunication/ICT security coordination § SG 17 Strategic Plan / Vision for SG 17 § Internal SG 17 Coordination § Terminology issues that impact users of Recommendations § References in Recommendations to withdrawn standards § Guidelines for correspondence groups § Quality of standards § Regional and sub regional coordinators for SG 17 § Actions/achievements in support of WTSA, PP, WTDC Resolutions § Quality of SG 17 work § Templates for Agenda of Questions; for CG Reports; and for new work items § Regional Group of Africa § Bridging the standardization gap § Rapporteur: Ms Wala Turki LASTROUS 38/163

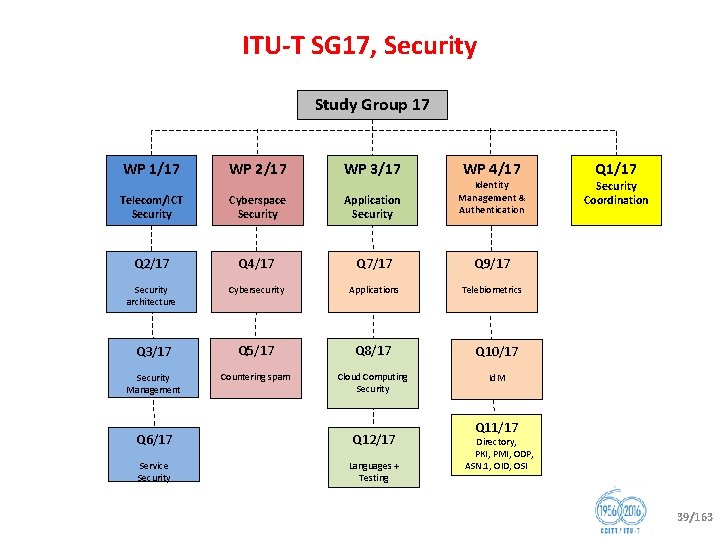
ITU T SG 17, Security Study Group 17 WP 1/17 WP 2/17 WP 3/17 Telecom/ICT Security Cyberspace Security Application Security Identity Management & Authentication Q 2/17 Q 4/17 Q 7/17 Q 9/17 Security architecture Cybersecurity Applications Telebiometrics Q 3/17 Q 5/17 Q 8/17 Q 10/17 Security Management Countering spam Cloud Computing Security Id. M Q 6/17 Q 12/17 Service Security Languages + Testing WP 4/17 Q 1/17 Security Coordination Q 11/17 Directory, PKI, PMI, ODP, ASN. 1, OID, OSI 39/163

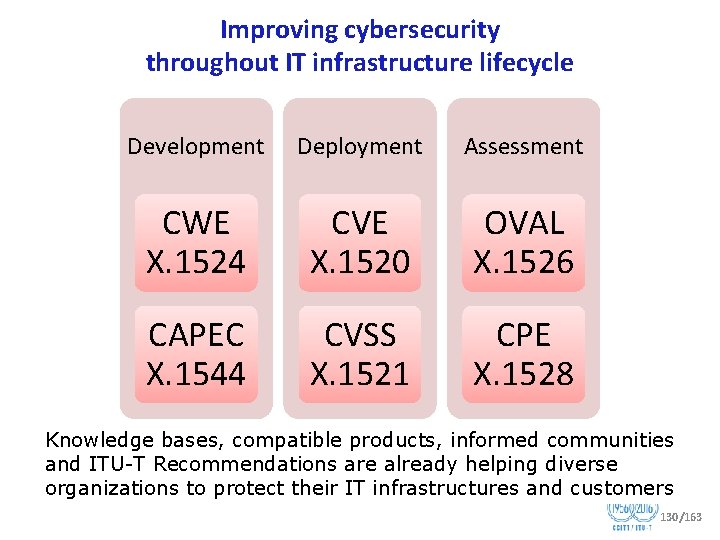
New SG 17 Working Party Structure • • • WP 1 “Telecom/ICT security” – Q 2/17 Security architecture and framework – Q 3/17 Telecommunication information security management – Q 6/17 Security aspects of ubiquitous telecommunication services WP 2 “Cyberspace security” – Q 4/17 Cybersecurity – Q 5/17 Countering spam by technical means WP 3 “Service and application security” – Q 7/17 Secure application services – Q 8/17 Cloud computing security – Q 12/17 Formal languages for telecommunication software and testing WP 4 “Application security” – Q 9/17 Telebiometrics – Q 10/17 Identity management architecture and mechanisms – Q 11/17 Generic technologies to support secure applications Q 1/17 Telecommunication/ICT security coordination 40/163

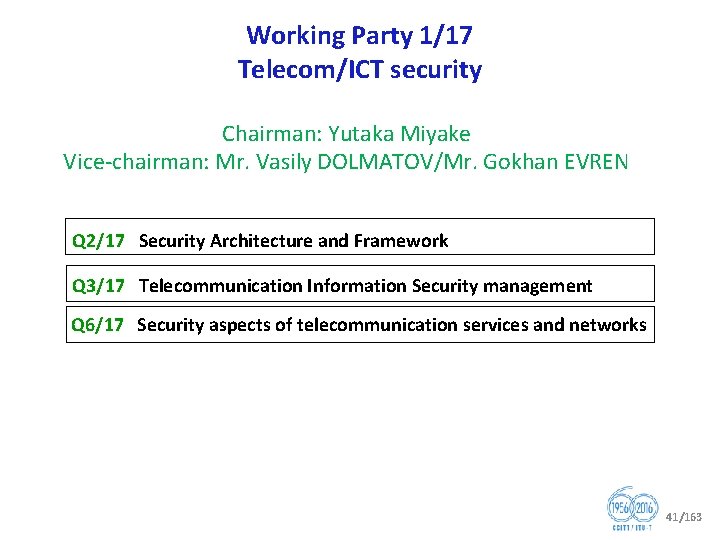
Working Party 1/17 Telecom/ICT security Chairman: Yutaka Miyake Vice chairman: Mr. Vasily DOLMATOV/Mr. Gokhan EVREN Q 2/17 Security Architecture and Framework Q 3/17 Telecommunication Information Security management Q 6/17 Security aspects of telecommunication services and networks 41/163

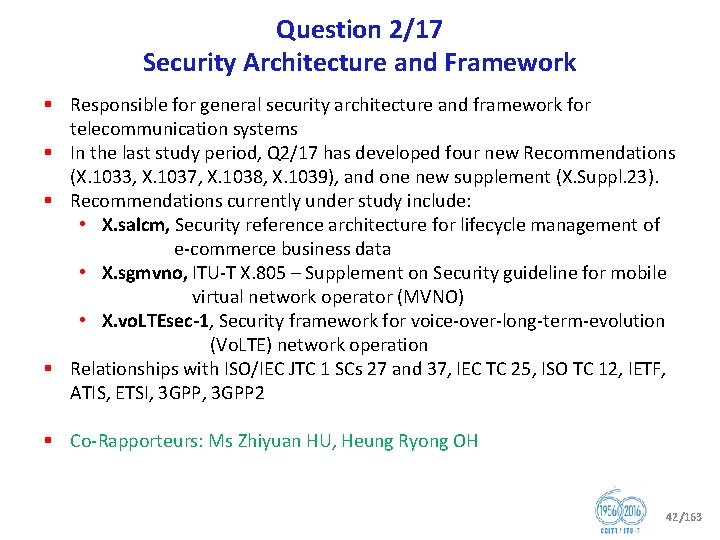
Question 2/17 Security Architecture and Framework § Responsible for general security architecture and framework for telecommunication systems § In the last study period, Q 2/17 has developed four new Recommendations (X. 1033, X. 1037, X. 1038, X. 1039), and one new supplement (X. Suppl. 23). § Recommendations currently under study include: • X. salcm, Security reference architecture for lifecycle management of e commerce business data • X. sgmvno, ITU T X. 805 – Supplement on Security guideline for mobile virtual network operator (MVNO) • X. vo. LTEsec 1, Security framework for voice over long term evolution (Vo. LTE) network operation § Relationships with ISO/IEC JTC 1 SCs 27 and 37, IEC TC 25, ISO TC 12, IETF, ATIS, ETSI, 3 GPP 2 § Co Rapporteurs: Ms Zhiyuan HU, Heung Ryong OH 42/163

Question 3/17 Telecommunication information security management § § Responsible for information security management X. 1051, etc. In the last study period, Q 3/17 has developed one revised Recommendation (X. 1051), and one new Supplement (X. Suppl. 27). § Developing specific guidelines including: • X. 1058 (X. gpim), Information technology – Code of practice for personally identifiable information protection (common text with ISO/IEC 29151) • X. sgsm, Information security management guidelines for small and medium telecommunication organizations • X. sup 13 rev, Supplement 13 to ITU T X. 1051: Supplement on information security management users' guide for Recommendation ITU T X. 1051 • X. sup gpim, ITU T X. gpim Supplement on Code of practice for personally Identifiable information protection based on ITU T X. gpim for telecommunications organizations • X. sup grm, Supplement to ITU T X. 1055: Risk management implementation guidance on the assets of telecommunication organizations accessible by global IP based networks Close collaboration with ISO/IEC JTC 1/SC 27 Rapporteur: Ms Miho NAGANUMA For approval § § 43/163

Question 6/17 Security aspects of telecommunication services and networks Responsible for multicast security, home network security, mobile security, networked ID security, IPTV security, ubiquitous sensor network security, intelligent transport system security, and smart grid security. § In the last study period, Q 6/17 has developed 2 new Recommendations (X. 1198, X. 1314), 2 technical corrigenda (X. 1311 Cor. 1, X. 1314 Cor. 1), and 3 new supplements (X. Suppl. 19, X. Suppl. 24, X. Suppl. 26). § Recommendations currently under study include: For approval § X. 1126 (X. msec 11), Guidelines on mitigating the negative effects of infected terminals in mobile networks For approval § X. 1362 (X. iotsec 1), Simple encryption procedure for Internet of things (Io. T) environments For approval § X. 1373 (X. itssec 1), Software update capability for ITS communications devices § X. iotsec 2, Security framework for Internet of things § X. itssec 2, Security guidelines for V 2 X communication systems For § X. msec 9, Functional security requirements and architecture for mobile phone anti determination theft measures § X. sdnsec 1, Requirements for security services based on software defined networking § X. sgsec 2, Security guidelines for home area network (HAN) devices in smart grid systems § X. sgsec 3, Security guidelines for smart metering service in smart grids § § § Close relationship with JCA IPTV and ISO/IEC JTC 1/SC 6/WG 7 Rapporteur: Mr Jonghyun BAEK 44/163

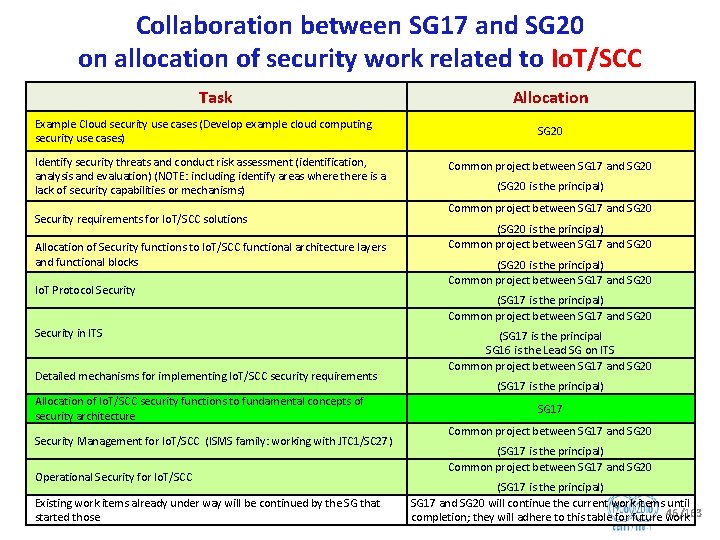
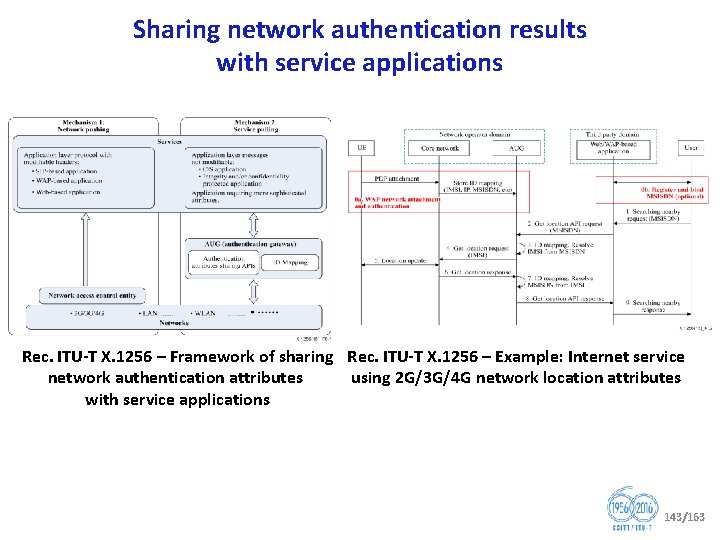
Summary of agreements between ITU T Study Groups 17 and 20 on Io. T security studies § TSAG agreed mechanisms for collaboration between SG 17 and SG 20 § § Colocation of meetings Correspondence group/e meetings Joint rapporteur group meetings Workshops and tutorials § Standardization Roadmap on Security and Privacy for Io. T (Io. Tsec) § SG 20 and SG 17 maintain a document of standardization activities on Security and Privacy for Io. T that outlines: § Potential topics/aspects for standardization and the time planning. § New and ongoing work items related to Io. T/SCC security in SG 17 and SG 20. § ITU T Recommendations relevant to Io. T/SCC security. 45/163

Collaboration between SG 17 and SG 20 on allocation of security work related to Io. T/SCC Task Example Cloud security use cases (Develop example cloud computing security use cases) Identify security threats and conduct risk assessment (identification, analysis and evaluation) (NOTE: including identify areas where there is a lack of security capabilities or mechanisms) Security requirements for Io. T/SCC solutions Allocation of Security functions to Io. T/SCC functional architecture layers and functional blocks Io. T Protocol Security in ITS Detailed mechanisms for implementing Io. T/SCC security requirements Allocation of Io. T/SCC security functions to fundamental concepts of security architecture Security Management for Io. T/SCC (ISMS family: working with JTC 1/SC 27) Operational Security for Io. T/SCC Existing work items already under way will be continued by the SG that started those Allocation SG 20 Common project between SG 17 and SG 20 (SG 20 is the principal) Common project between SG 17 and SG 20 (SG 17 is the principal SG 16 is the Lead SG on ITS Common project between SG 17 and SG 20 (SG 17 is the principal) SG 17 and SG 20 will continue the current work items until 46/163 completion; they will adhere to this table for future work

Working Party 2/17 Cyberspace security Chairman: Koji Nakao Vice chairman: Ms. Inette FUREY Q 4/17 Cybersecurity Q 5/17 Countering spam by technical means 47/163

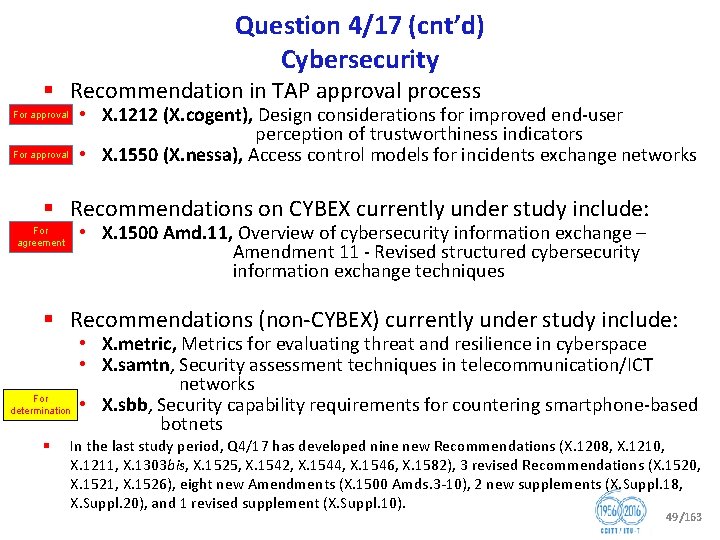
Question 4/17 Cybersecurity § Cybersecurity by design no longer possible; a new paradigm: • know your weaknesses minimize the vulnerabilities • know your attacks share the heuristics within trust communities § Current work program (6 Recommendations under development) § X. 1500 suite: Cybersecurity Information Exchange (CYBEX) – non prescriptive, extensible, complementary techniques for the new paradigm • • • Weakness, vulnerability and state Event, incident, and heuristics Information exchange policy Identification, discovery, and query Identity assurance Exchange protocols § Non CYBEX deliverables include compendiums and guidelines for • Abnormal traffic detection • Botnet mitigation • Attack source attribution (including traceback) • Extensive relationships with many external bodies • Rapporteur: Mr Youki KADOBAYASHI 48/163

Question 4/17 (cnt’d) Cybersecurity § Recommendation in TAP approval process • X. 1212 (X. cogent), Design considerations for improved end user perception of trustworthiness indicators • X. 1550 (X. nessa), Access control models for incidents exchange networks For approval § Recommendations on CYBEX currently under study include: • X. 1500 Amd. 11, Overview of cybersecurity information exchange – Amendment 11 Revised structured cybersecurity information exchange techniques For agreement § Recommendations (non CYBEX) currently under study include: For determination § • X. metric, Metrics for evaluating threat and resilience in cyberspace • X. samtn, Security assessment techniques in telecommunication/ICT networks • X. sbb, Security capability requirements for countering smartphone based botnets In the last study period, Q 4/17 has developed nine new Recommendations (X. 1208, X. 1210, X. 1211, X. 1303 bis, X. 1525, X. 1542, X. 1544, X. 1546, X. 1582), 3 revised Recommendations (X. 1520, X. 1521, X. 1526), eight new Amendments (X. 1500 Amds. 3 10), 2 new supplements (X. Suppl. 18, X. Suppl. 20), and 1 revised supplement (X. Suppl. 10). 49/163

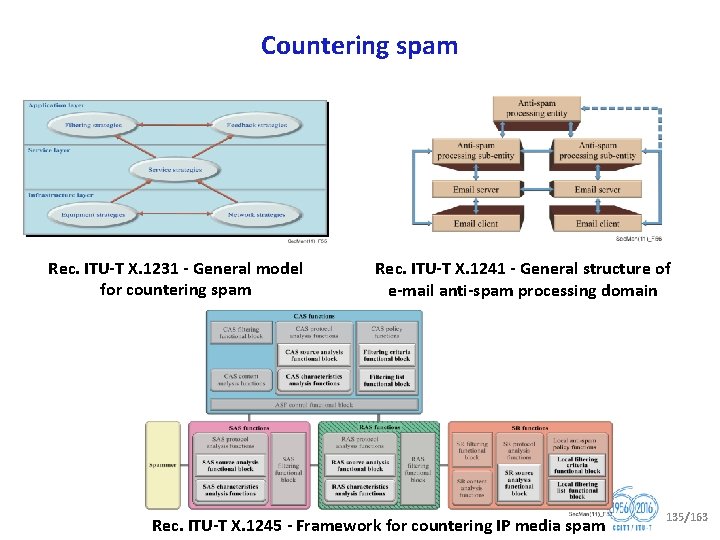
Question 5/17 Countering spam by technical means § Lead group in ITU T on countering spam by technical means in support of WTSA 12 Resolution 52 (Countering and combating spam) § In the last study period, Q 5/17 has developed 2 new Recommendations (X. 1246, X. 1247), one Corrigendum (X. 1243 Cor. 1), and two new Supplements (X. Suppl. 25, X. Suppl. 28): § Recommendations currently under study include (see structure in next slide): For determination For agreement • X. cspim, Technical requirements for countering instant messaging spam (SPIM) • X. ctss, ITU T X. 1231 – Supplement on Technical framework for countering telephone service scam • X. gcsfmpd, ITU T X. 1231 – Supplement on guidance of countering spam for mobile phone developers • X. gcspi, ITU T X. 1242 – Supplement on Guidelines on countermeasures against short message service (SMS) phishing and smishing attack • X. tfcma, Technical framework for countering mobile in application advertising spam § Effective cooperation with ITU D, IETF, ISO/IEC JTC 1, 3 GPP, OECD, M 3 AAWG, ENISA and other organizations § Rapporteur: Mr Yanbin ZHANG 50/163

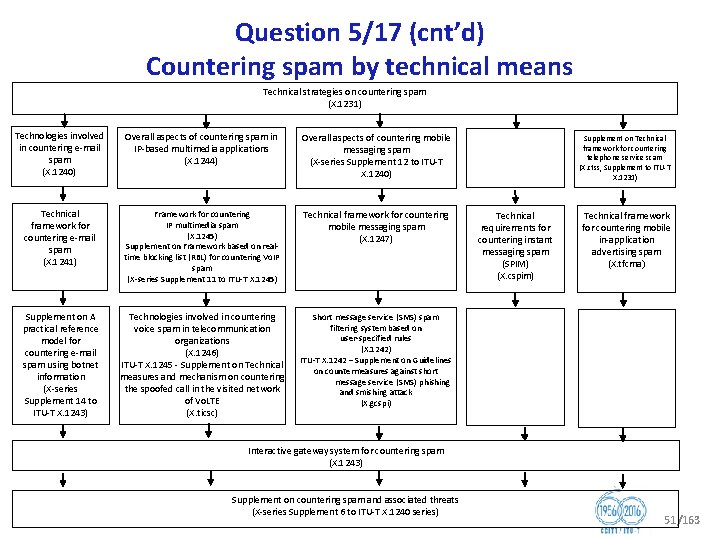
Question 5/17 (cnt’d) Countering spam by technical means Technical strategies on countering spam (X. 1231) Technologies involved in countering e mail spam (X. 1240) Overall aspects of countering spam in IP based multimedia applications (X. 1244) Overall aspects of countering mobile messaging spam (X series Supplement 12 to ITU T X. 1240) Supplement on Technical framework for countering telephone service scam (X. ctss, Supplement to ITU T X. 1231) Technical framework for countering e mail spam (X. 1241) Framework for countering IP multimedia spam (X. 1245) Supplement on Framework based on real time blocking list (RBL) for countering Vo. IP spam (X series Supplement 11 to ITU T X. 1245) Technical framework for countering mobile messaging spam (X. 1247) Technical requirements for countering instant messaging spam (SPIM) (X. cspim) Technical framework for countering mobile in application advertising spam (X. tfcma) Supplement on A practical reference model for countering e mail spam using botnet information (X series Supplement 14 to ITU T X. 1243) Technologies involved in countering voice spam in telecommunication organizations (X. 1246) ITU T X. 1245 Supplement on Technical measures and mechanism on countering the spoofed call in the visited network of Vo. LTE (X. ticsc) Short message service (SMS) spam filtering system based on user specified rules (X. 1242) ITU T X. 1242 – Supplement on Guidelines on countermeasures against short message service (SMS) phishing and smishing attack (X. gcspi) Interactive gateway system for countering spam (X. 1243) Supplement on countering spam and associated threats (X series Supplement 6 to ITU T X. 1240 series) 51/163

Working Party 3/17 Identity management and cloud computing security Chairman: Arnaud Taddei Vice chairman: Mr. Zhaoji LIN Q 8/17 Cloud computing security Q 12/17 Formal languages for telecommunication software and testing 52/163

Question 7/17 Secure application services § Responsible for web security, security protocols, peer to peer security § In the last study period, Q 7/17 has developed 8 new Recommendations (X. 1144, X. 1155, X. 1156, X. 1157, X. 1158, X. 1159, X. 1163), and 2 new supplements (X. Suppl. 21, X. Suppl. 22). § Recommendations currently under study include: For consent § X. fdip, Framework of de identification processing service for telecommunication service providers § X. hakm, Guidelines on hybrid authentication and key management mechanisms in the client server model § X. srfb, Security requirements and framework for Big Data analytics in mobile Internet services § X. websec 6, Security framework and requirements for open capabilities of telecommunication services § X. websec 7, Reference monitor for online analytics services § X. websec 8, Secure protection guidelines of value added service for operators § Relationships include: OASIS, OMA, W 3 C, ISO/IEC JTC 1/SC 27, Kantara Initiative § Rapporteur: Mr Jae Hoon NAH 53/163

Question 8/17 Cloud computing security • In the last study period, Q 8/17 has developed 5 new Recommendations (X. 1601, X. 1602, X. 1631, X. 1642), and one revised Recommendation (X. 1601). • Recommendations currently under study include: – Security aspects of cloud computing X. dsms, Data security requirements for the monitoring service of cloud computing X. GSBDaa. S, Guidelines on security of Big Data as a Service X. SRCaa. S, Security requirements for Communication as a Service application environments X. SRIaa. S, Security requirements of public infrastructure as a service (Iaa. S) in cloud computing X. SRNaa. S, Security requirements of Network as a Service (Naa. S) in cloud computing – Security aspects of service oriented architecture § Working closely with ITU T SG 13, ISO/IEC JTC 1/SCs 27 and 38, and Cloud Security Alliance on cloud computing § Rapporteur: Mr Liang WEI 54/163

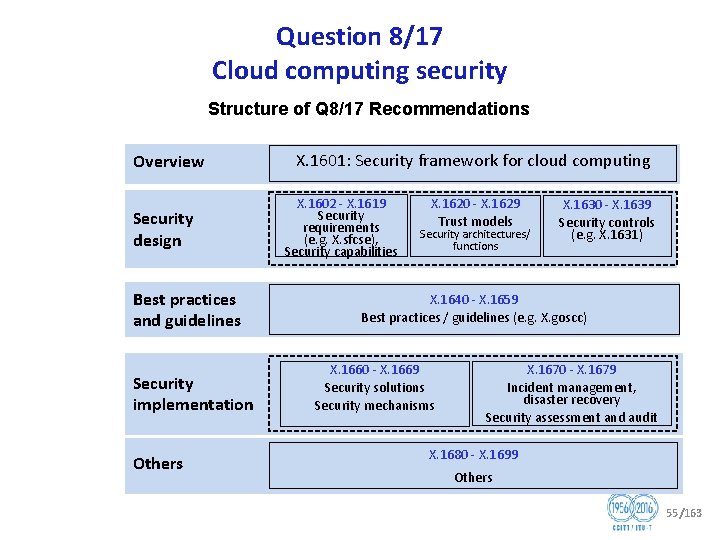
Question 8/17 Cloud computing security Structure of Q 8/17 Recommendations Overview Security design X. 1601: Security framework for cloud computing X. 1602 X. 1619 Security requirements (e. g. X. sfcse), Security capabilities X. 1620 X. 1629 Trust models Security architectures/ functions Security implementation Best practices and guidelines X. 1630 X. 1639 Security controls (e. g. X. 1631) X. 1640 X. 1659 Best practices / guidelines (e. g. X. goscc) X. 1660 X. 1669 Security solutions Security mechanisms X. 1670 X. 1679 Incident management, disaster recovery Security assessment and audit Others X. 1680 X. 1699 Others 55/163

Collaboration between SG 13 and SG 17 on cloud computing security tasks Task Example Cloud security use cases (Develop example cloud computing security use cases) Functional Architecture Identify the security threats (Identify cloud computing security threats for service categories and deployment models) Generic security requirements based on threats analysis and use cases Security requirements for cloud computing solutions and mechanisms based on use cases/threat analysis, taking into account generic security requirements Identify areas where there is a lack of security capabilities or mechanisms Allocation of Security functions to cloud computing functional architecture layers and functional blocks Detailed description of Security functions Fundamental concepts for security architectures Defining trust models Existing Security mechanisms (applicable to cloud computing service categories and deployment models) New security mechanisms (applicable to cloud computing service categories and deployment models) Allocation SG 13 Common project between SG 13 and SG 17 Principal: SG 17 Common project between SG 13 and SG 17 Principal: SG 13 SG 17 Common project between SG 13 and SG 17 Principal: SG 17 Security Management (ISMS family: working with JTC 1/SC 27) SG 17 Security Best Practices & Guidelines SG 17 Operational Security Existing work items already under way SG 17 Continue in existing Question 56/163

Question 12/17 Formal languages for telecommunication software and testing § Languages and methods for requirements, specification implementation § Q 12/17 consists of three parts: § Formal languages for telecommunication software § Methodology using formal languages for telecommunication software § Testing languages § In the last study period, Q 12/17 has developed 6 new Recommendations (Z. 161. 1, Z. 161. 2, Z. 161. 3, Z. 161. 4, Z. 161. 5, Z. 165. 1, ), 38 revised Recommendations (Z. 100, Z. 101, Z. 102, Z. 103, Z. 104, Z. 105, Z. 106, Z. 107, Z. 109, Z. 111, Z. 100 Annex F 1/F 2/F 3, Z. 109, Z. 161. 1, Z. 161. 2, Z. 161. 3, Z. 161. 4, Z. 161. 5, Z. 165. 1, Z. 166 , Z. 167, Z. 168, Z. 169, Z. 170), 4 revised implementer’s guides (Z. Imp 100 V 2. 0. 1, V 2. 0. 2, V 3. 0. 0, V 3. 0. 1), and one revised Supplement (Z. Sup 1). § Rapporteur: Mr Dieter HOGREFE 57/163

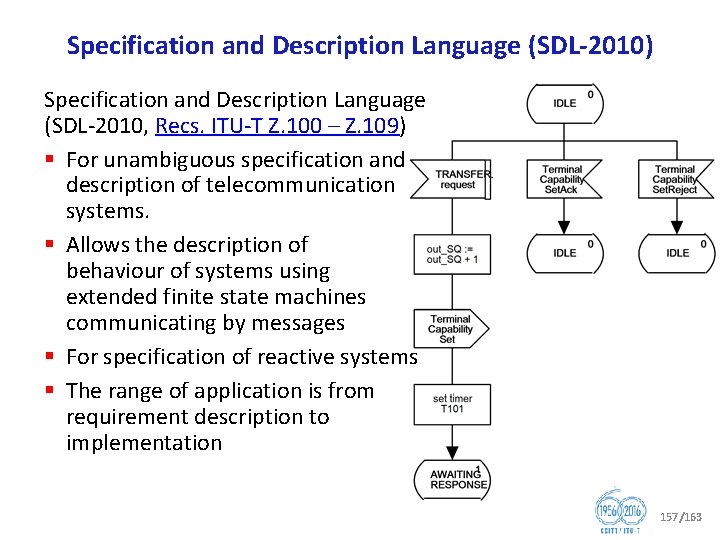
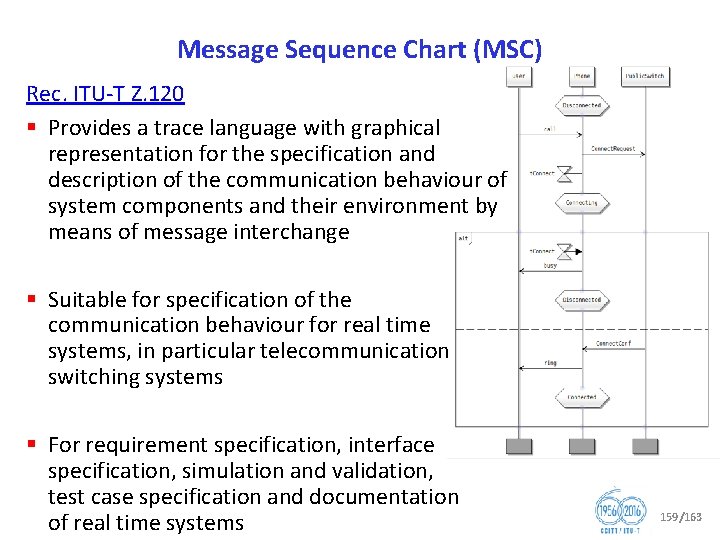
Question 12/17 Formal languages for telecommunication software and testing (part: Formal languages for telecommunication software) § Languages and methods for requirements, specification implementation § Recommendations for: § § Specification and Description Language (Z. 100 series) Message Sequence Chart (Z. 120 series) User Requirements Notation (Z. 150 series) Framework and profiles for Unified Modeling Language, as well as use of languages (Z. 110, Z. 111, Z. 450). § These techniques enable high quality Recommendations to be written from which formal tests can be derived, and products to be cost effectively developed. § Relationship with SDL Forum Society 58/163

Question 12/17 Formal languages for telecommunication software and testing (part: Formal languages for telecommunication software) § Specification and Description Language (Z. 100 series) under development: § Z. 100 Annex F 1 (revised), Specification and Description Language Overview of SDL 2010 – SDL formal definition: General overview § Z. 100 Annex F 2 (revised), Specification and Description Language Overview of SDL 2010 – SDL formal definition: Static semantics § Z. 100 Annex F 3 (revised), Specification and Description Language Overview of SDL 2010 – SDL formal definition: Dynamic semantics § Z. 109 (revised), Specification and Description Language – Unified modeling language profile for SDL 2010 59/163

Question 12/17 Formal languages for telecommunication software and testing (part: Methodology using formal languages for telecommunication software) § Covers the use of formal ITU system design languages (ASN. 1, SDL, MSC, URN, TTCN, CHILL) to define the requirements, architecture, and behaviour of telecommunications systems: requirements languages, data description, behaviour specification, testing and implementation languages. § The formal languages for these areas of engineering are widely used in industry and ITU‑T and commercial tools support them. The languages can be applied collectively or individually for specification of standards and the realization of products, but in all cases a framework and methodology is essential for effective use. § Responsible formal languages methodology Recommendations: Z. 110, Z. 450, and Z. Supp 1. 60/163

Question 12/17 Formal languages for telecommunication software and testing (part: Methodology using formal languages for telecommunication software) § Methodology using formal languages for telecommunication software under development: • Z. 151 (revised), User Requirements Notation (URN) Language definition 61/163

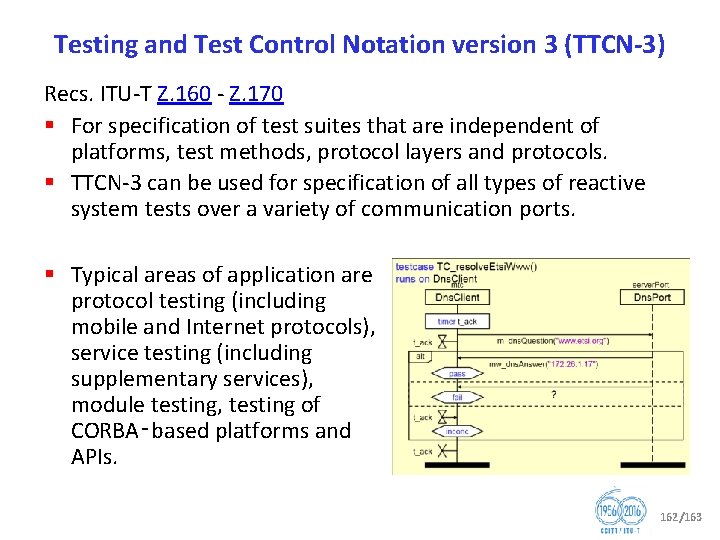
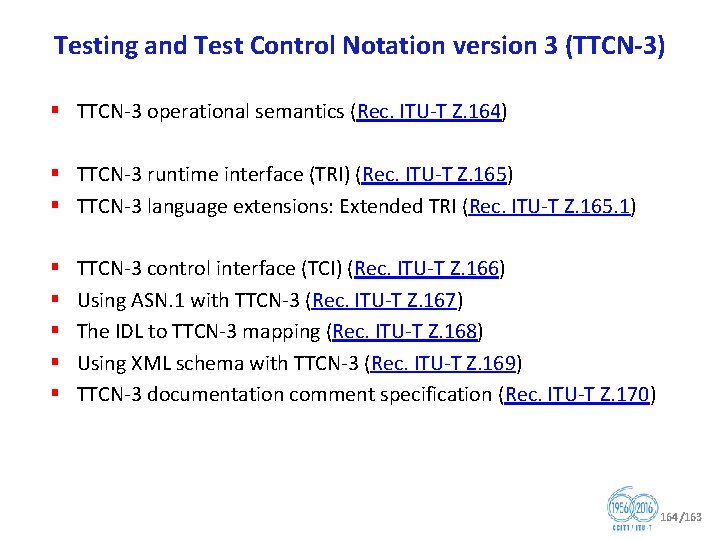
Question 12/17 Formal languages for telecommunication software and testing (1/2) (part: Testing languages) § Testing and Test Control Notation version 3 (TTCN 3) under development: • • • • Z. 161 (revised), Testing and Test Control Notation version 3: TTCN 3 core language Z. 161. 1 (revised), Testing and Test Control Notation version 3: TTCN 3 language extensions: Support of interfaces with continuous signals Z. 161. 2 (revised), Testing and Test Control Notation version 3: TTCN 3 language extensions: Configuration and deployment support Z. 161. 3 (revised), Testing and Test Control Notation version 3: TTCN 3 language extensions: Advanced parameterization Z. 161. 4 (revised), Testing and Test Control Notation version 3: TTCN 3 Language Extensions: Behaviour Types Z. 161. 5 (revised), Testing and Test Control Notation version 3: TTCN 3 Language extensions: Performance and real time testing Z. 164 (revised), Testing and Test Control Notation version 3: TTCN 3 operational semantics Z. 165 (revised), Testing and Test Control Notation version 3: TTCN 3 runtime interface (TRI) Z. 165. 1 (revised), Testing and Test Control Notation version 3: TTCN 3 extension package: Extended TRI Z. 166 (revised), Testing and Test Control Notation version 3: TTCN 3 control interface (TCI) Z. 167 (revised), Testing and Test Control Notation version 3: Using ASN. 1 with TTCN 3 Z. 168 (revised), Testing and Test Control Notation version 3: The IDL to TTCN 3 mapping Z. 169 (revised), Testing and Test Control Notation version 3: Using XML schema with TTCN 3 Z. 170 (revised), Testing and Test Control Notation version 3: TTCN 3 documentation comment specification 62/163

Question 12/17 Formal languages for telecommunication software and testing (2/2) (part: Testing languages) § Provides support for WTSA 16 Resolution 76 on conformance and interoperability testing § Close liaisons with SG 11, JCA CIT and ETSI. 63/163

Working Party 4/17 Application Security Chairman: Mr Kepeng LI Vice chairman: Mr Jae Hoon NAH Q 9/17 Telebiometrics Q 10/17 Identity management architecture and mechanisms Q 11/17 Generic technologies (Directory, public key infrastructure (PKI), privilege management infrastructure (PMI), Abstract Syntax Notation One (ASN. 1), object identifiers (OIDs)) to support secure applications 64/163

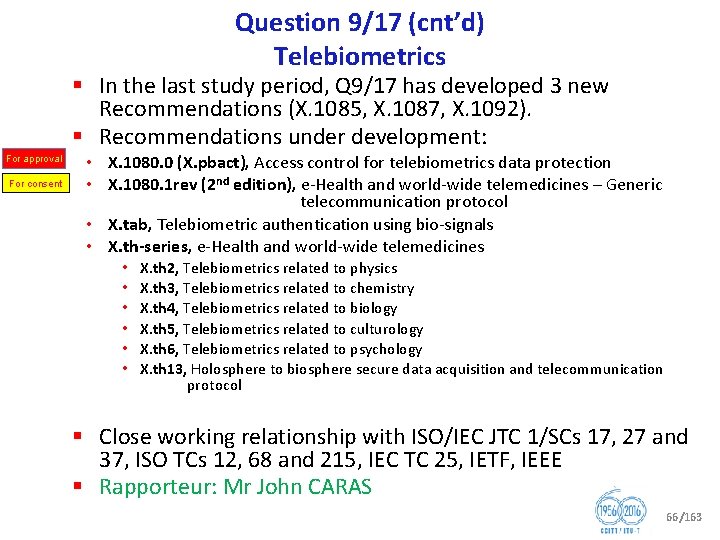
Question 9/17 Telebiometrics § Current focus: • Security requirements and guidelines for applications of telebiometrics • Requirements for evaluating security, conformance and interoperability with privacy protection techniques for applications of telebiometrics • Requirements for telebiometric applications in a high functionality network • Requirements for telebiometric multi factor authentication techniques based on biometric data protection and biometric encryption • Requirements for appropriate generic protocols providing safety, security, privacy protection, and consent “for manipulating biometric data” in applications of telebiometrics, e. g. , e health, telemedicine 65/163

Question 9/17 (cnt’d) Telebiometrics § In the last study period, Q 9/17 has developed 3 new Recommendations (X. 1085, X. 1087, X. 1092). § Recommendations under development: For approval For consent • X. 1080. 0 (X. pbact), Access control for telebiometrics data protection • X. 1080. 1 rev (2 nd edition), e Health and world wide telemedicines – Generic telecommunication protocol • X. tab, Telebiometric authentication using bio signals • X. th series, e Health and world wide telemedicines • • • X. th 2, Telebiometrics related to physics X. th 3, Telebiometrics related to chemistry X. th 4, Telebiometrics related to biology X. th 5, Telebiometrics related to culturology X. th 6, Telebiometrics related to psychology X. th 13, Holosphere to biosphere secure data acquisition and telecommunication protocol § Close working relationship with ISO/IEC JTC 1/SCs 17, 27 and 37, ISO TCs 12, 68 and 215, IEC TC 25, IETF, IEEE § Rapporteur: Mr John CARAS 66/163

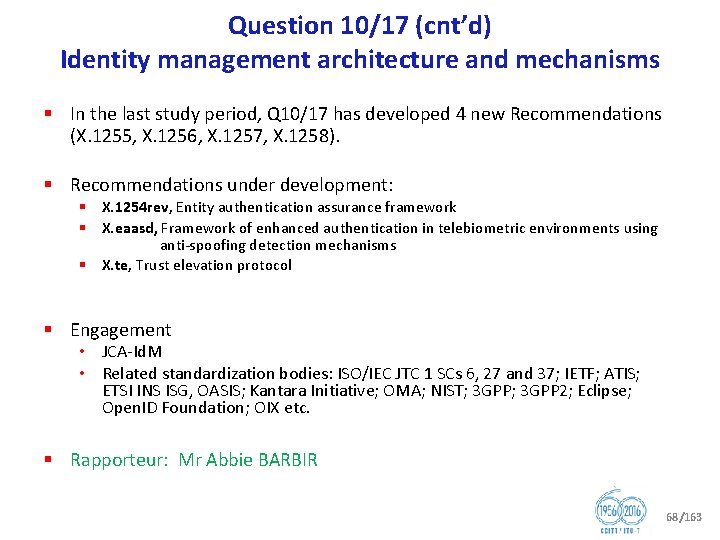
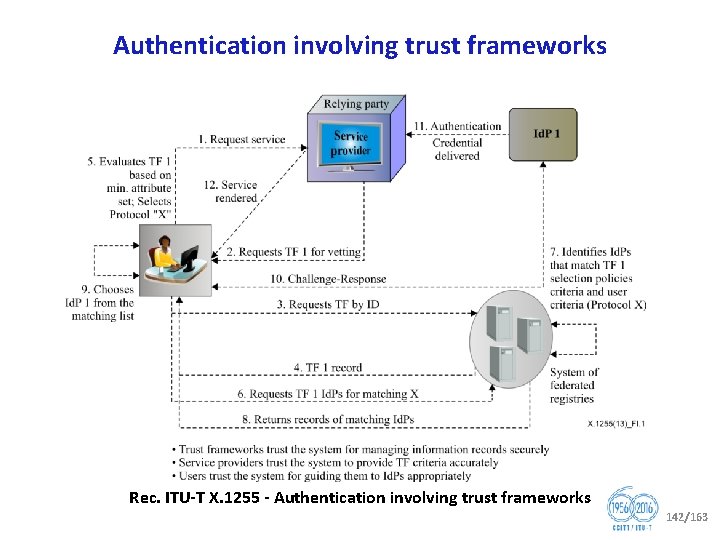
Question 10/17 Identity management architecture and mechanisms § Identity Management (Id. M) • Id. M is a security enabler by providing trust in the identity of both parties to an e transaction • Id. M also provides network operators an opportunity to increase revenues by offering advanced identity based services • The focus of ITU T’s Id. M work is on global trust and interoperability of diverse Id. M capabilities in telecommunication. • Work is focused on leveraging and bridging existing solutions • This Question is dedicated to the vision setting and the coordination and organization of the entire range of Id. M activities within ITU T § Key focus • Adoption of interoperable federated identity frameworks that use a variety of authentication methods with well understood security and privacy • Encourage the use of authentication methods resistant to known and projected threats • Provide a general trust model for making trust based authentication decisions between two or more parties • Ensure security of online transactions with focus on end to end identification and authentication of the participants and components involved in conducting the transaction, including people, devices, and services. 67/163

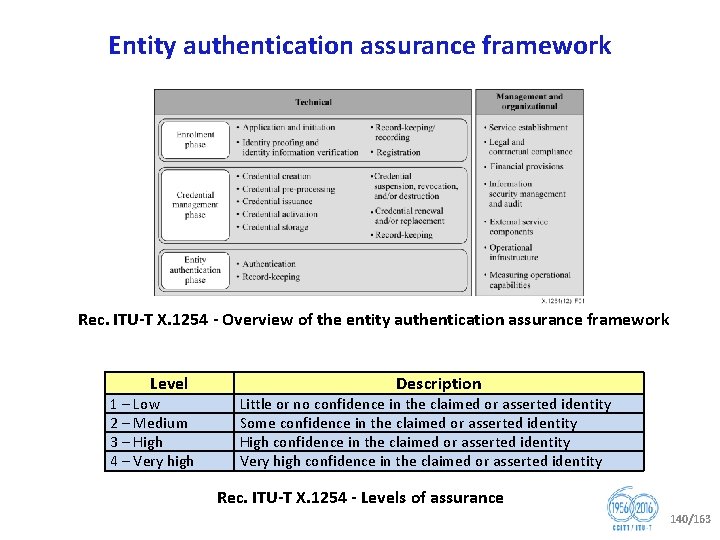
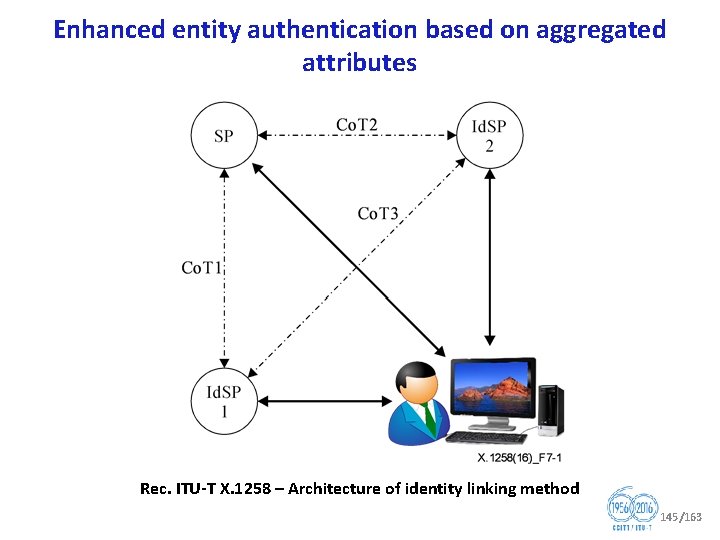
Question 10/17 (cnt’d) Identity management architecture and mechanisms § In the last study period, Q 10/17 has developed 4 new Recommendations (X. 1255, X. 1256, X. 1257, X. 1258). § Recommendations under development: § X. 1254 rev, Entity authentication assurance framework § X. eaasd, Framework of enhanced authentication in telebiometric environments using anti spoofing detection mechanisms § X. te, Trust elevation protocol § Engagement • JCA Id. M • Related standardization bodies: ISO/IEC JTC 1 SCs 6, 27 and 37; IETF; ATIS; ETSI INS ISG, OASIS; Kantara Initiative; OMA; NIST; 3 GPP 2; Eclipse; Open. ID Foundation; OIX etc. § Rapporteur: Mr Abbie BARBIR 68/163

Question 11/17 Generic technologies to support secure applications § Q 11/17 consists of four main parts: § X. 500 directory, Public Key Infrastructure (PKI), Privilege Management Infrastructure (PMI) § Abstract Syntax Notation 1 (ASN. 1), Object Identifier (OID) § Open Distributed Processing (ODP) § Open Systems Interconnection (OSI) § In the last study period, Q 11/17 has developed 4 new Recommendations (F. 511, X. 675, X. 696, X. 1341), 36 revised Recommendations (X. 500, X. 501, X. 509, X. 511, X. 518, X. 519, . X. 520, X. 521, X. 525, X. 667, X. 680 X. 683, X. 690 X. 696, X. 906, X. 911), and 14 Corrigenda (X. 226 Cor. 1, X. 227 bis Cor. 1, X. 509 Cor. 2, X. 509 Cor. 3, X. 520 Cor. 1, X. 680 Cor. 2, X. 682 Cor. 1, X. 683 Cor. 1, X. 690 Cor. 2, X. 691 Cor. 1, X. 694 Cor. 2, X. 691 Cor. 3, X. 691 Cor. 4) to the X. 500 , X. 680 , and X. 690 series of Recommendations, and 1 Technical Report. § Rapporteur: Mr Jean Paul LEMAIRE 69/163

Question 11/17 Generic technologies to support secure applications (parts: Directory, PKI, PMI) § Three Directory Projects: • ITU T X. 500 Series of Recommendations | ISO/IEC 9594 all parts – The Directory • ITU T E. 115 Computerized directory assistance • ITU T F. 511 Directory Service Support of tag based identification services § X. 500 series is a specification for a highly secure, versatile and distributed directory § X. 500 work is collaborative with ISO/IEC JTC 1/SC 6/WG 10 70/163

Question 11/17 Generic technologies to support secure applications (parts: Directory, PKI, PMI) § Recommendations under development: For consent § X. 680 (2015) Cor. 1, Information technology – Abstract Syntax Notation One (ASN. 1): Specification of basic notation: Technical Corrigendum 1 § X. 696 (2015) Cor. 1, Information technology – Abstract Syntax Notation One (ASN. 1): Specification of Octet Encoding Rules (OER): Technical Corrigendum 1 § X. pki em, Information Technology Public Key Infrastructure: Establishment and maintenance § X. pki prof, Information Technology Public Key Infrastructure: Profile 71/163

Question 11/17 Generic technologies to support secure applications (parts: Directory, PKI, PMI) § ITU T X. 509 on public key/attribute certificates is the cornerstone for security: • Base specification for public key certificates and for attribute certificates • Has a versatile extension feature allowing additions of new fields to certificates • Basic architecture for revocation • Base specification for Public Key Infrastructure (PKI) • Base specifications for Privilege Management Infrastructure (PMI) § ITU T X. 509 is used in many different areas: • Basis for e. Government, e. Business, etc. all over the world • Used for IPsec, cloud computing, and many other areas • Is the base specification for many other groups (PKIX in IETF, ESI in ETSI, CA Browser Forum, etc. ) 72/163

Question 11/17 Generic technologies to support secure applications (parts: ASN. 1, OID) Developing and maintaining the heavily used Abstract Syntax Notation One (ASN. 1) and Object Identifier (OID) specifications § Recommendations are in the X. 680 (ASN. 1), X. 690 ( ASN. 1 Encoding Rules), X. 660/X. 670 (OID Registration), and X. 890 (Generic Applications, such as Fast Infoset, Fast Web services, etc) series § Giving advice on the management of OID Registration Authorities, particularly within developing countries, through the OID Project Leader Mr Olivier Dubuisson § Approving new top arcs of the Object Identifier tree as necessary § Promoting use of OID resolution system by other groups such as SG 16 § Repository of OID allocations and a database of ASN. 1 modules § Promoting the term “description and encoding of structured data” as what ASN. 1 is actually about § ASN. 1 Packed Encoding Rules reduces the bandwidth required for communication thus conserving energy (e. g. , compared with XML) § Recommendations under development: For § X. 894 (X. cms), Information technology – Generic applications of ASN. 1 – Cryptographic Message Syntax disapproval § X. CMS prof, Cryptographic Message Syntax (CMS) Profile § X. jsoner, Information technology – ASN. 1 encoding rules: Specification of Javascript Object Notation (JSON) Encoding Rules (JSON/ER) § X. oiddev, Information technology – Use of object identifiers in the Internet of things For § X. oid iot, ITU T X. 660 Supplement on Guidelines for using object identifiers for the Internet of things agreement § Work is collaborative with ISO/IEC JTC 1/SC 6/WG 10 73/163

Question 11/17 Generic technologies to support secure applications (part: ODP) § Open Distributed Processing (ODP) § ODP (X. 900 series in collaboration with ISO/IEC JTC 1/SC 7/WG 19) § Work is carried out in collaboration with ISO/IEC JTC 1 74/163

Question 11/17 Generic technologies to support secure applications (part: OSI) § Ongoing maintenance of the OSI X series Recommendations and the OSI Implementer’s Guide: • • • § § OSI Architecture Message Handling Transaction Processing Commitment, Concurrency and Recovery (CCR) Remote Operations Reliable Transfer Quality of Service Upper layers – Application, Presentation, and Session Lower Layers – Transport, Network, Data Link, and Physical 109 approved Recommendations (from former study periods) Work is carried out in collaboration with ISO/IEC JTC 1 75/163

§ Mandate of ITU T and of ITU T Study Groups § Importance of telecommunication/ICT security standardization § ITU Plenipotentiary Conference (PP 14) actions on telecommunication/ICT security § World Telecommunications Standardization Assembly (WTSA 16) mandate for Study Group 17 § Study Group 17 overview § SG 17 current activities § Security Coordination § Future meetings § Useful references § Backup – SG 17 Security Recommendations 76/163

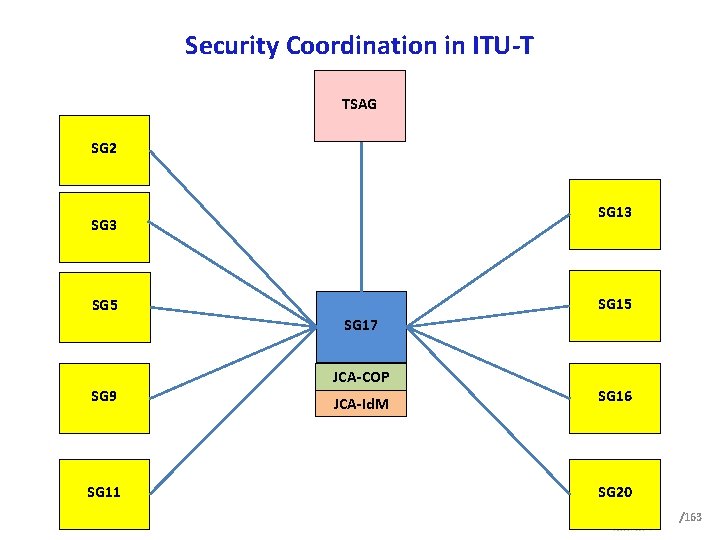
Security Coordination in ITU T TSAG SG 2 SG 13 SG 15 SG 17 JCA COP SG 9 SG 11 JCA Id. M SG 16 SG 20 /163

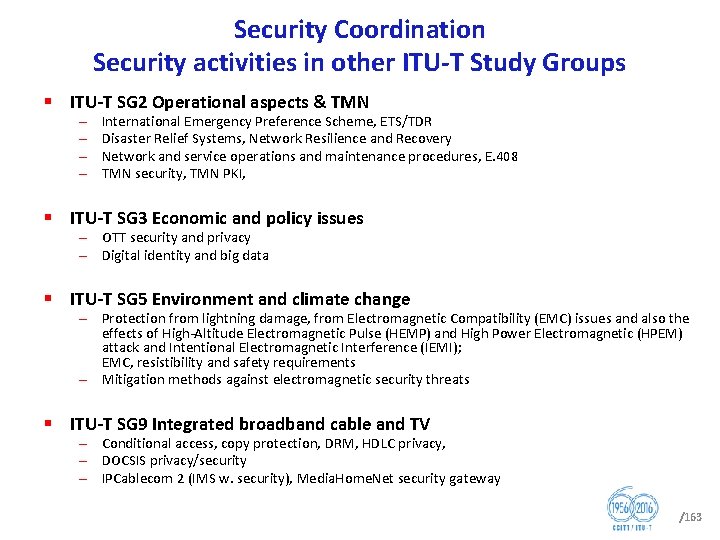
Security Coordination Security activities in other ITU T Study Groups § ITU T SG 2 Operational aspects & TMN – – International Emergency Preference Scheme, ETS/TDR Disaster Relief Systems, Network Resilience and Recovery Network and service operations and maintenance procedures, E. 408 TMN security, TMN PKI, § ITU T SG 3 Economic and policy issues – OTT security and privacy – Digital identity and big data § ITU T SG 5 Environment and climate change – Protection from lightning damage, from Electromagnetic Compatibility (EMC) issues and also the effects of High Altitude Electromagnetic Pulse (HEMP) and High Power Electromagnetic (HPEM) attack and Intentional Electromagnetic Interference (IEMI); EMC, resistibility and safety requirements – Mitigation methods against electromagnetic security threats § ITU T SG 9 Integrated broadband cable and TV – Conditional access, copy protection, DRM, HDLC privacy, – DOCSIS privacy/security – IPCablecom 2 (IMS w. security), Media. Home. Net security gateway /163

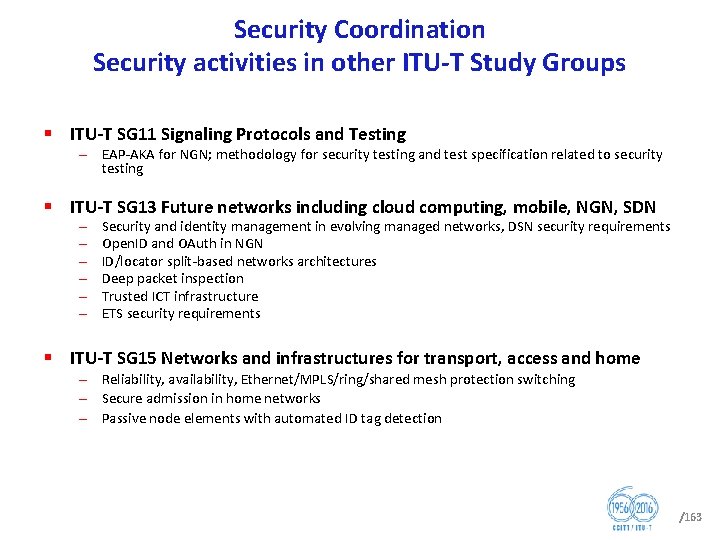
Security Coordination Security activities in other ITU T Study Groups § ITU T SG 11 Signaling Protocols and Testing – EAP AKA for NGN; methodology for security testing and test specification related to security testing § ITU T SG 13 Future networks including cloud computing, mobile, NGN, SDN – – – Security and identity management in evolving managed networks, DSN security requirements Open. ID and OAuth in NGN ID/locator split based networks architectures Deep packet inspection Trusted ICT infrastructure ETS security requirements § ITU T SG 15 Networks and infrastructures for transport, access and home – Reliability, availability, Ethernet/MPLS/ring/shared mesh protection switching – Secure admission in home networks – Passive node elements with automated ID tag detection /163

Security Coordination Security activities in other ITU T Study Groups § ITU T SG 16 Multimedia – Secure Vo. IP and multimedia security (H. 233, H. 234, H. 235, H. 323, JPEG 2000), NAT/FW traversal – Multimedia information access with tag based identification – Common Alerting Services for Digital Signage § ITU T SG 20 Io. T and its applications including smart cities and communities (SC&C) – Io. T security – security for smart cities and communities /163

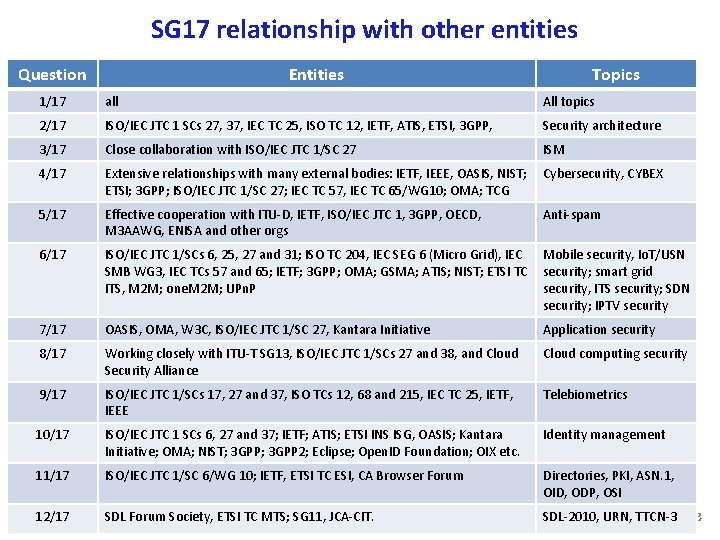
SG 17 relationship with other entities Question Entities Topics 1/17 all All topics 2/17 ISO/IEC JTC 1 SCs 27, 37, IEC TC 25, ISO TC 12, IETF, ATIS, ETSI, 3 GPP, Security architecture 3/17 Close collaboration with ISO/IEC JTC 1/SC 27 ISM 4/17 Extensive relationships with many external bodies: IETF, IEEE, OASIS, NIST; Cybersecurity, CYBEX ETSI; 3 GPP; ISO/IEC JTC 1/SC 27; IEC TC 57, IEC TC 65/WG 10; OMA; TCG 5/17 Effective cooperation with ITU D, IETF, ISO/IEC JTC 1, 3 GPP, OECD, M 3 AAWG, ENISA and other orgs 6/17 ISO/IEC JTC 1/SCs 6, 25, 27 and 31; ISO TC 204, IEC SEG 6 (Micro Grid), IEC Mobile security, Io. T/USN SMB WG 3, IEC TCs 57 and 65; IETF; 3 GPP; OMA; GSMA; ATIS; NIST; ETSI TC security; smart grid ITS, M 2 M; one. M 2 M; UPn. P security, ITS security; SDN security; IPTV security 7/17 OASIS, OMA, W 3 C, ISO/IEC JTC 1/SC 27, Kantara Initiative Application security 8/17 Working closely with ITU T SG 13, ISO/IEC JTC 1/SCs 27 and 38, and Cloud Security Alliance Cloud computing security 9/17 ISO/IEC JTC 1/SCs 17, 27 and 37, ISO TCs 12, 68 and 215, IEC TC 25, IETF, IEEE Telebiometrics 10/17 ISO/IEC JTC 1 SCs 6, 27 and 37; IETF; ATIS; ETSI INS ISG, OASIS; Kantara Initiative; OMA; NIST; 3 GPP 2; Eclipse; Open. ID Foundation; OIX etc. Identity management 11/17 ISO/IEC JTC 1/SC 6/WG 10; IETF, ETSI TC ESI, CA Browser Forum Directories, PKI, ASN. 1, OID, ODP, OSI 12/17 SDL Forum Society, ETSI TC MTS; SG 11, JCA CIT. 81/163 SDL 2010, URN, TTCN 3 Anti spam

Coordination with other bodies Study Group 17 ITU-D, ITU-R, xyz… /163

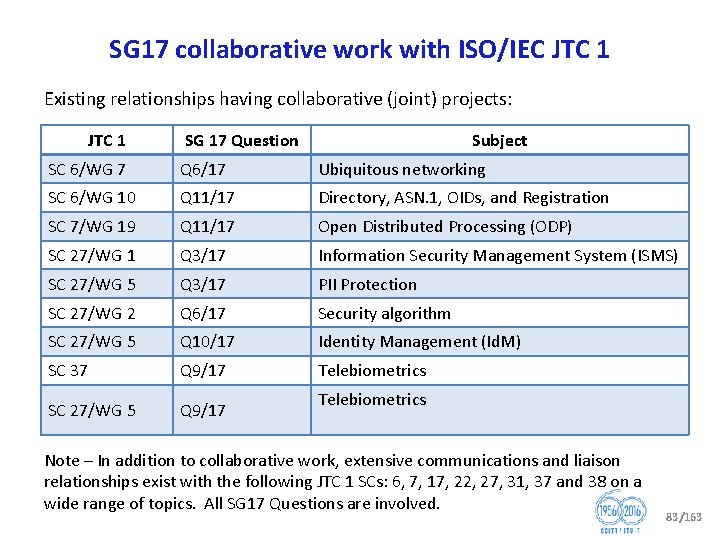
SG 17 collaborative work with ISO/IEC JTC 1 Existing relationships having collaborative (joint) projects: JTC 1 SG 17 Question Subject SC 6/WG 7 Q 6/17 Ubiquitous networking SC 6/WG 10 Q 11/17 Directory, ASN. 1, OIDs, and Registration SC 7/WG 19 Q 11/17 Open Distributed Processing (ODP) SC 27/WG 1 Q 3/17 Information Security Management System (ISMS) SC 27/WG 5 Q 3/17 PII Protection SC 27/WG 2 Q 6/17 Security algorithm SC 27/WG 5 Q 10/17 Identity Management (Id. M) SC 37 Q 9/17 Telebiometrics SC 27/WG 5 Q 9/17 Telebiometrics Note – In addition to collaborative work, extensive communications and liaison relationships exist with the following JTC 1 SCs: 6, 7, 17, 22, 27, 31, 37 and 38 on a wide range of topics. All SG 17 Questions are involved. 83/163

SG 17 collaborative work with ISO/IEC JTC 1 (cnt’d) § Guide for ITU T and ISO/IEC JTC 1 Cooperation • http: //itu. int/rec/T REC A. 23 201002 I!Ann. A § Listing of common text and technically aligned Recommendations | International Standards • http: //www. itu. int/en/ITU T/studygroups/2013 2016/17/Documents/reference info/Common and aligned Rec ISO. docx § Mapping between ISO/IEC International Standards and ITU T Recommendations • http: //www. itu. int/en/ITU T/studygroups/2013 2016/17/Documents/reference info/ISO Rec mapping 01 15. docx § Relationships of SG 17 Questions with JTC 1 SCs that categorizes the nature of relationships as: – joint work (e. g. , common texts or twin texts) – technical collaboration by liaison mechanism – informational liaison • http: //itu. int/en/ITU T/studygroups/com 17/Pages/relationships. aspx 84/163

§ Mandate of ITU T and of ITU T Study Groups § Importance of telecommunication/ICT security standardization § ITU Plenipotentiary Conference (PP 14) actions on telecommunication/ICT security § World Telecommunications Standardization Assembly (WTSA 16) mandate for Study Group 17 § Study Group 17 overview § SG 17 current activities § Security Coordination § Future meetings § Useful references § Backup – SG 17 Security Recommendations 85/163

Future Study Group 17 Meetings For 2017, the Study Group 17 meetings in this study period are scheduled for: § Monday 28 August – Wednesday 6 September 2017, Geneva or Monday 16 – Friday 27 October 2017, Geneva (portion) § 28 February – 9 March 2018 , Geneva (to be confirmed). 86/163

§ Mandate of ITU T and of ITU T Study Groups § Importance of telecommunication/ICT security standardization § ITU Plenipotentiary Conference (PP 14) actions on telecommunication/ICT security § World Telecommunications Standardization Assembly (WTSA 16) mandate for Study Group 17 § Study Group 17 overview § SG 17 current activities § Security Coordination § Future meetings § Useful references § Backup – SG 17 Security Recommendations 87/163

Reference links § § § § § Webpage for ITU T Study Group 17 • http: //itu. int/ITU T/studygroups/com 17 Webpage on ICT security standard roadmap • http: //itu. int/ITU T/studygroups/com 17/ict Webpage on ICT cybersecurity organizations • http: //itu. int/ITU T/studygroups/com 17/nfvo Webpage for JCA on identity management • http: //www. itu. int/en/ITU T/jca/idm Webpage for JCA on child online protection • http: //www. itu. int/en/ITU T/jca/COP Webpage on lead study group on security • http: //itu. int/en/ITU T/studygroups/com 17/Pages/telesecurity. aspx Webpage on lead study group on identity management • http: //itu. int/en/ITU T/studygroups/com 17/Pages/idm. aspx Webpage on lead study group on languages and description techniques • http: //itu. int/en/ITU T/studygroups/com 17/Pages/ldt. aspx ITU Security Manual: Security in Telecommunications and Information Technology • http: //www. itu. int/dms_pub/itu t/opb/tut/T TUT SEC 2015 PDF E. pdf 88/163

ICT Discovery Museum • Located at ITU HQs, 2 nd floor Montbrillant building • Showcases the evolution of ICTs through the ages with interactive exhibitions and educational programmes • Free guided tours available in all 6 UN languages (to be reserved in advance) • Open Monday to Friday, 10: 00 to 17: 00 • info@ictdiscovery. org +41 22 730 6155 89/163

SAFE : Security is Absolutely First Everywhere Thank you very much for your attention! 90/163

§ Mandate of ITU T and of ITU T Study Groups § Importance of telecommunication/ICT security standardization § ITU Plenipotentiary Conference (PP 14) actions on telecommunication/ICT security § World Telecommunications Standardization Assembly (WTSA 16) mandate for Study Group 17 § Study Group 17 overview § SG 17 current activities § Security Coordination § Future meetings § Useful references § Backup – SG 17 Security Recommendations 91/163

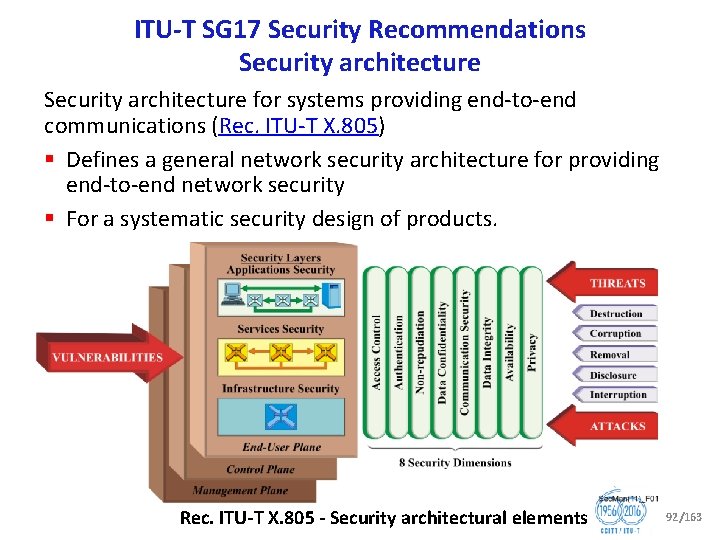
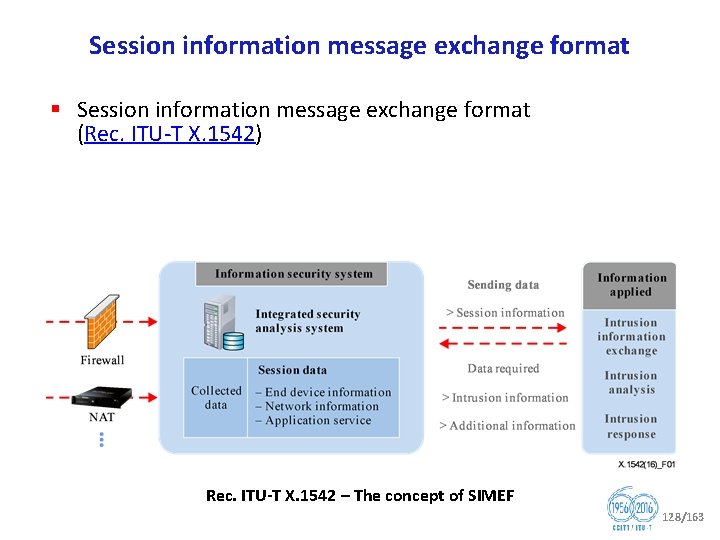
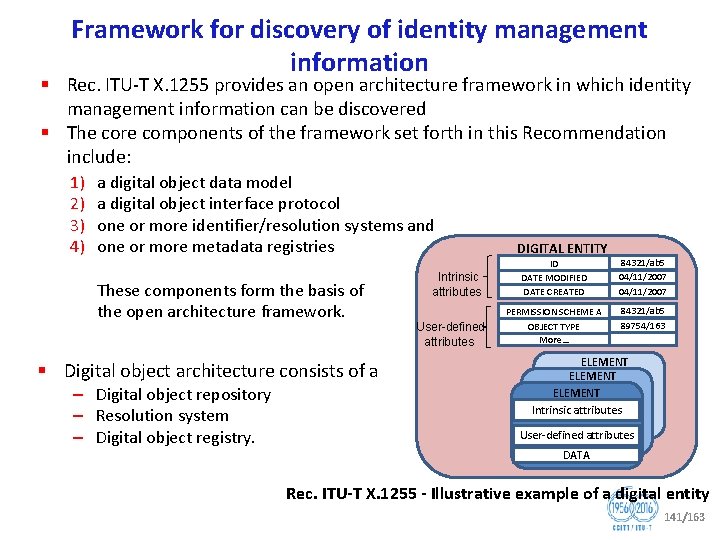
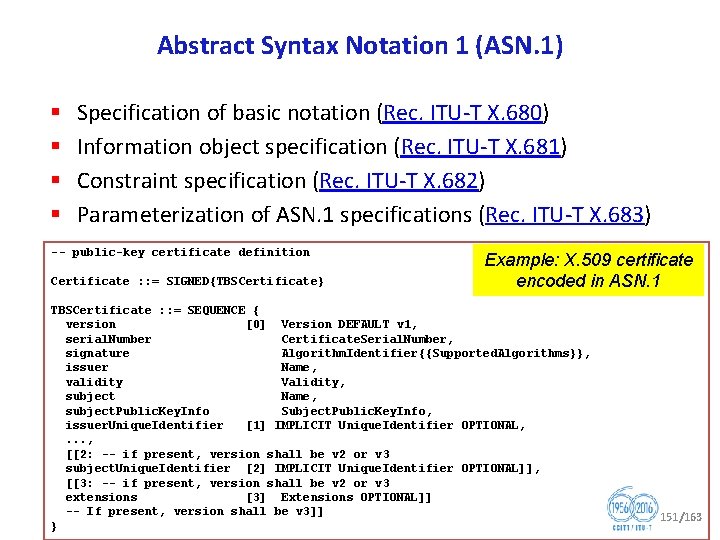
ITU T SG 17 Security Recommendations Security architecture for systems providing end to end communications (Rec. ITU T X. 805) § Defines a general network security architecture for providing end to end network security § For a systematic security design of products. Rec. ITU T X. 805 Security architectural elements 92/163

Security architecture § OSI security architecture (Rec. ITU T X. 800) § OSI security models (Recs. ITU T X. 802, X. 803, X. 830, X. 831, X. 832, X. 833, X. 834, X. 835) § OSI security frameworks for open systems (Recs. ITU T X. 810, X. 811, X. 812, X. 813, X. 814, X. 815, X. 816, X. 841) § Security architecture for systems providing end to end communications (Rec. ITU T X. 805) § Security architecture aspects (Recs. ITU T X. 1031, X. 1032) § IP based telecommunication network security system (TNSS) (Rec. ITU T X. 1032) § Security of the individual information service provided by the operators (Rec. ITU T X. 1033) 93/163

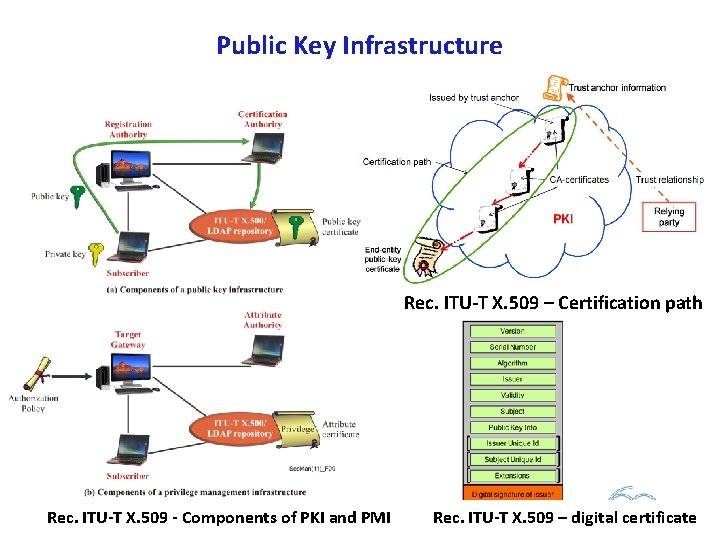
Fast Info Set Public Key Infrastructure and Trusted Third Party Services § Fast infoset security (Rec. ITU T X. 893) § Public Key Infrastructure and Trusted Third Party Services: § Public key and attribute certificate frameworks (Rec. ITU T X. 509) § Guidelines for the use of Trusted Third Party services (Rec. ITU T X. 842) § Specification of TTP services to support the application of digital signatures (Rec. ITU T X. 843) 94/163

Public Key Infrastructure Rec. ITU T X. 509 – Certification path Rec. ITU T X. 509 Components of PKI and PMI 95/78 Rec. ITU T X. 509 – digital certificate

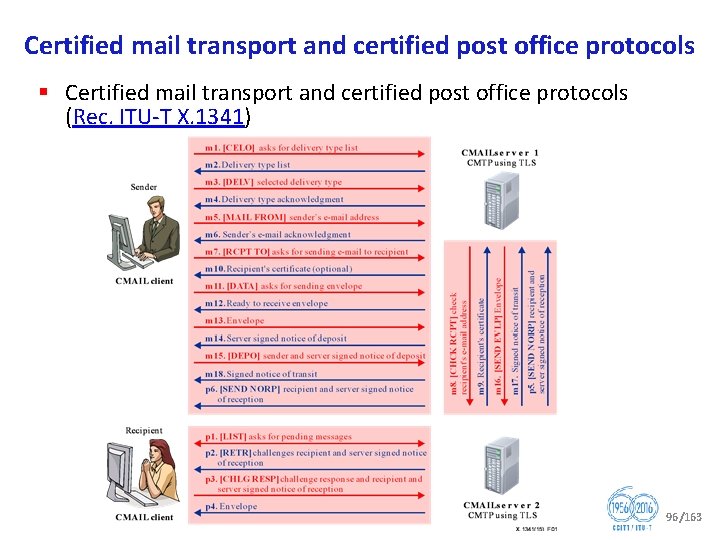
Certified mail transport and certified post office protocols § Certified mail transport and certified post office protocols (Rec. ITU T X. 1341) 96/163

Security protocols § § § § § EAP guideline (Rec. ITU T X. 1034) Password authenticated key exchange protocol (Rec. ITU T X. 1035) Technical security guideline on deploying IPv 6 (Rec. ITU T X. 1037) Guideline on secure password based authentication protocol with key exchange (Rec. ITU T X. 1151) Secure end to end data communication techniques using trusted third party services (Rec. ITU T X. 1152) Management framework of a one time password based authentication service (Rec. ITU T X. 1153) General framework of combined authentication on multiple identity service provider environments (Rec. ITU T X. 1154) Non repudiation framework based on a one time password (Rec. ITU T X. 1156) Delegated non repudiation architecture based on ITU T X. 813 (Rec. ITU T X. 1159) OSI Network + transport layer security protocol (Recs. ITU T X. 273, X. 274) 97/163

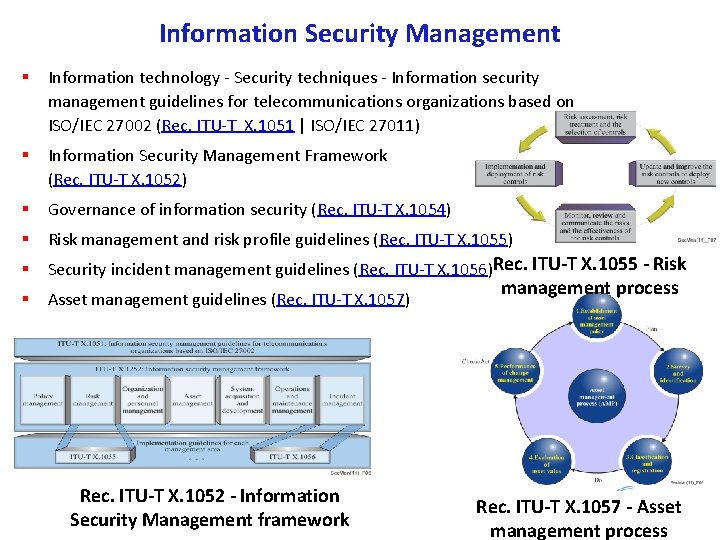
Information Security Management § Information technology Security techniques Information security management guidelines for telecommunications organizations based on ISO/IEC 27002 (Rec. ITU T X. 1051 | ISO/IEC 27011) § Information Security Management Framework (Rec. ITU T X. 1052) § Governance of information security (Rec. ITU T X. 1054) § Risk management and risk profile guidelines (Rec. ITU T X. 1055) § Security incident management guidelines (Rec. ITU T X. 1056)Rec. ITU T X. 1055 Risk § Asset management guidelines (Rec. ITU T X. 1057) Rec. ITU T X. 1052 Information Security Management framework management process Rec. ITU T X. 1057 Asset management process

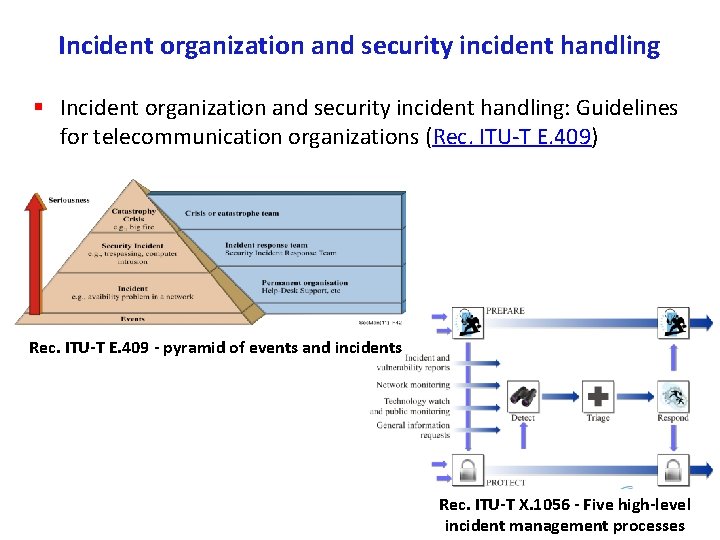
Incident organization and security incident handling § Incident organization and security incident handling: Guidelines for telecommunication organizations (Rec. ITU T E. 409) Rec. ITU T E. 409 pyramid of events and incidents Rec. ITU T X. 1056 Five high level incident management processes

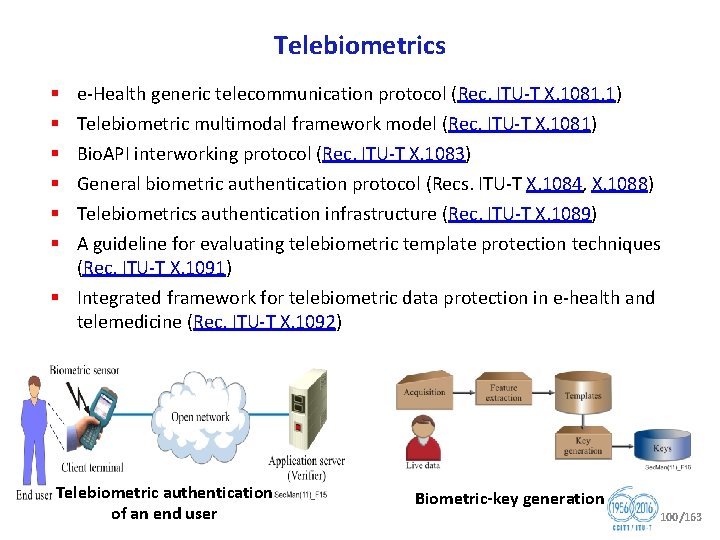
Telebiometrics § § § e Health generic telecommunication protocol (Rec. ITU T X. 1081. 1) Telebiometric multimodal framework model (Rec. ITU T X. 1081) Bio. API interworking protocol (Rec. ITU T X. 1083) General biometric authentication protocol (Recs. ITU T X. 1084, X. 1088) Telebiometrics authentication infrastructure (Rec. ITU T X. 1089) A guideline for evaluating telebiometric template protection techniques (Rec. ITU T X. 1091) § Integrated framework for telebiometric data protection in e health and telemedicine (Rec. ITU T X. 1092) Telebiometric authentication of an end user Biometric key generation 100/163

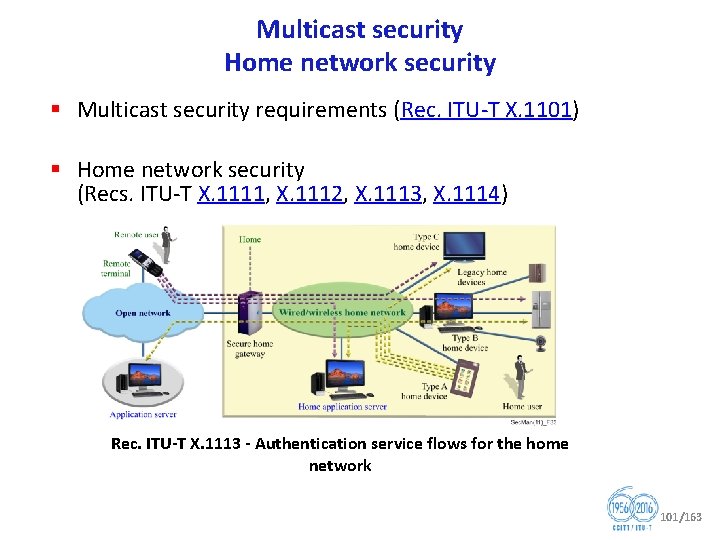
Multicast security Home network security § Multicast security requirements (Rec. ITU T X. 1101) § Home network security (Recs. ITU T X. 1111, X. 1112, X. 1113, X. 1114) Rec. ITU T X. 1113 Authentication service flows for the home network 101/163

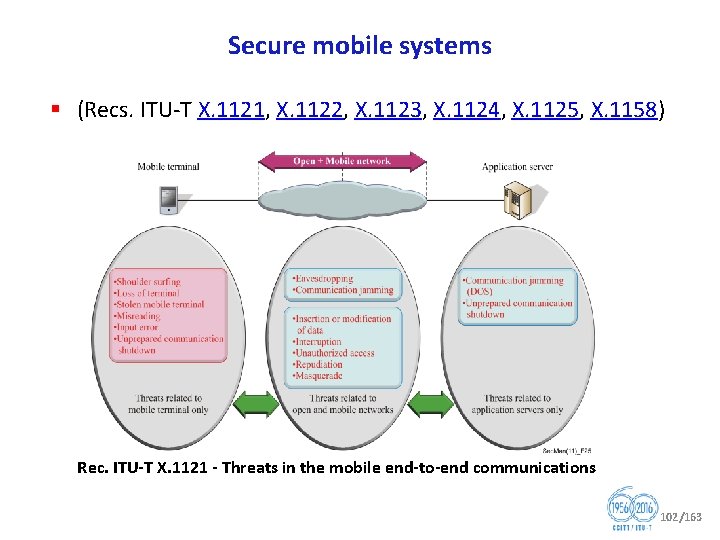
Secure mobile systems § (Recs. ITU T X. 1121, X. 1122, X. 1123, X. 1124, X. 1125, X. 1158) Rec. ITU T X. 1121 Threats in the mobile end to end communications 102/163

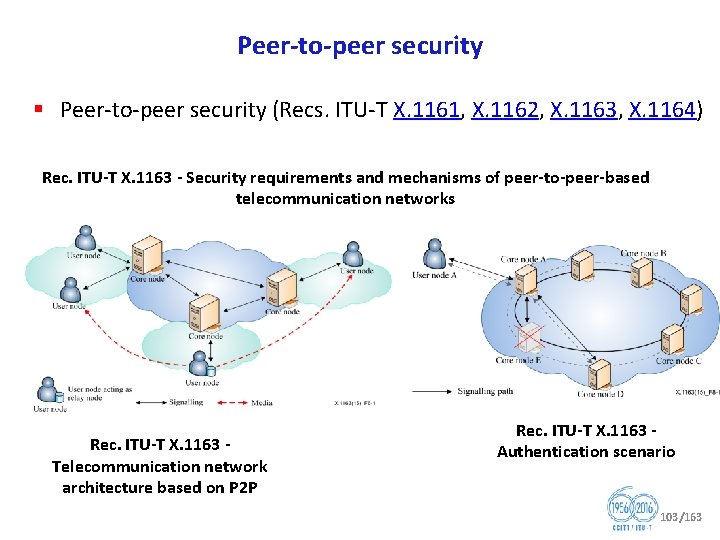
Peer to peer security § Peer to peer security (Recs. ITU T X. 1161, X. 1162, X. 1163, X. 1164) Rec. ITU T X. 1163 Security requirements and mechanisms of peer to peer based telecommunication networks Rec. ITU T X. 1163 Telecommunication network architecture based on P 2 P Rec. ITU T X. 1163 Authentication scenario 103/163

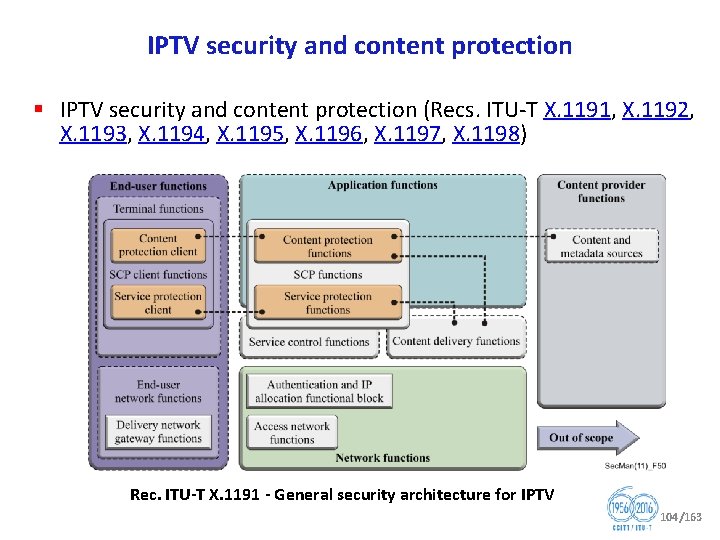
IPTV security and content protection § IPTV security and content protection (Recs. ITU T X. 1191, X. 1192, X. 1193, X. 1194, X. 1195, X. 1196, X. 1197, X. 1198) Rec. ITU T X. 1191 General security architecture for IPTV 104/163

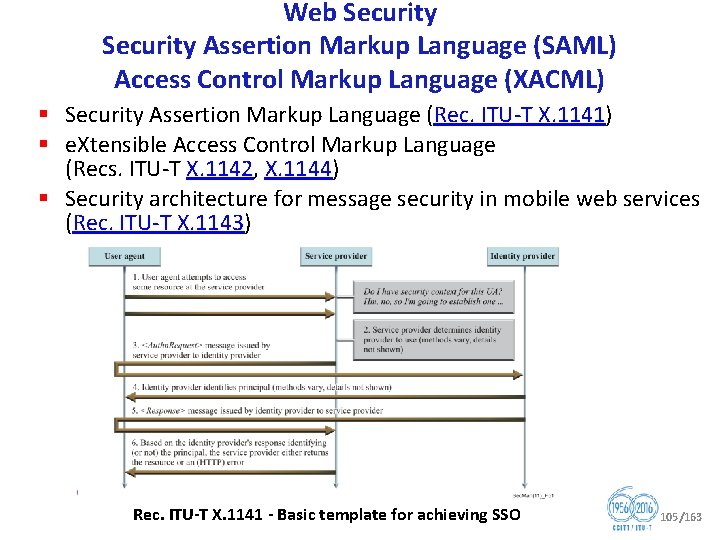
Web Security Assertion Markup Language (SAML) Access Control Markup Language (XACML) § Security Assertion Markup Language (Rec. ITU T X. 1141) § e. Xtensible Access Control Markup Language (Recs. ITU T X. 1142, X. 1144) § Security architecture for message security in mobile web services (Rec. ITU T X. 1143) Rec. ITU T X. 1141 Basic template for achieving SSO 105/163

Secure Application Services § Guidelines on local linkable anonymous authentication for electronic services (Rec. ITU T X. 1155) Rec. ITU T X. 1151 Concept of local linkability 106/163

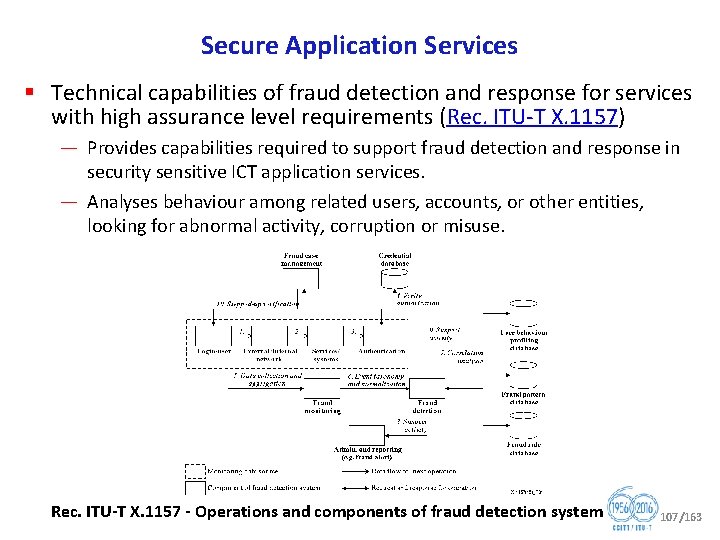
Secure Application Services § Technical capabilities of fraud detection and response for services with high assurance level requirements (Rec. ITU T X. 1157) — Provides capabilities required to support fraud detection and response in security sensitive ICT application services. — Analyses behaviour among related users, accounts, or other entities, looking for abnormal activity, corruption or misuse. Rec. ITU T X. 1157 Operations and components of fraud detection system 107/163

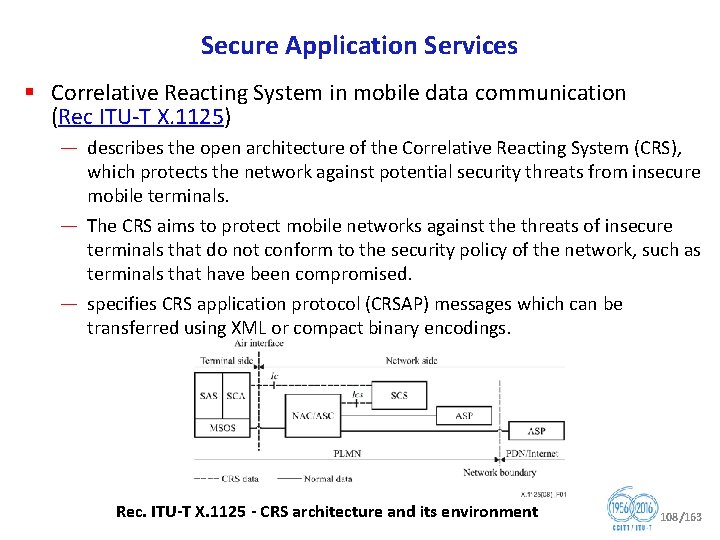
Secure Application Services § Correlative Reacting System in mobile data communication (Rec ITU T X. 1125) — describes the open architecture of the Correlative Reacting System (CRS), which protects the network against potential security threats from insecure mobile terminals. — The CRS aims to protect mobile networks against the threats of insecure terminals that do not conform to the security policy of the network, such as terminals that have been compromised. — specifies CRS application protocol (CRSAP) messages which can be transferred using XML or compact binary encodings. Rec. ITU T X. 1125 CRS architecture and its environment 108/163

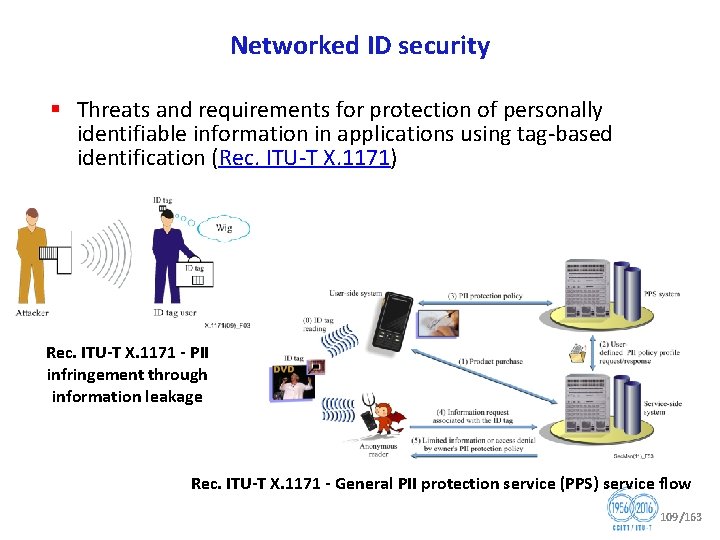
Networked ID security § Threats and requirements for protection of personally identifiable information in applications using tag based identification (Rec. ITU T X. 1171) Rec. ITU T X. 1171 PII infringement through information leakage Rec. ITU T X. 1171 General PII protection service (PPS) service flow 109/163

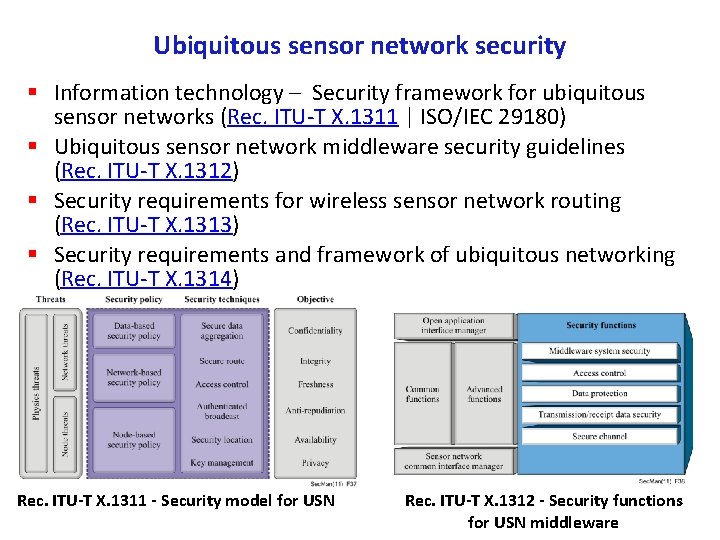
Ubiquitous sensor network security § Information technology – Security framework for ubiquitous sensor networks (Rec. ITU T X. 1311 | ISO/IEC 29180) § Ubiquitous sensor network middleware security guidelines (Rec. ITU T X. 1312) § Security requirements for wireless sensor network routing (Rec. ITU T X. 1313) § Security requirements and framework of ubiquitous networking (Rec. ITU T X. 1314) Rec. ITU T X. 1311 Security model for USN Rec. ITU T X. 1312 Security functions for USN middleware

CYBERSPACE SECURITY – Cybersecurity § Overview of cybersecurity (Rec. ITU T X. 1205) § A vendor neutral framework for automatic notification of security related information and dissemination of updates (Rec. ITU T X. 1206) § Guidelines for telecommunication service providers for addressing the risk of spyware and potentially unwanted software (Rec. ITU T X. 1207) § A cybersecurity indicator of risk to enhance confidence and security in the use of telecommunication/information and communication technologies (Rec. ITU T X. 1208) § Capabilities and their context scenarios for cybersecurity information sharing and exchange (Rec. ITU T X. 1209) § Overview of source based security troubleshooting mechanisms for Internet protocol based networks (Rec. ITU T X. 1210) 111/163

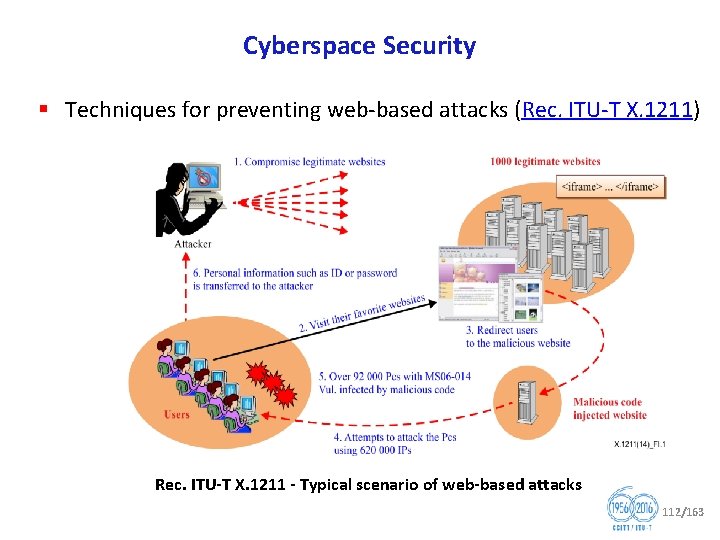
Cyberspace Security § Techniques for preventing web based attacks (Rec. ITU T X. 1211) Rec. ITU T X. 1211 Typical scenario of web based attacks 112/163

Definition of Cybersecurity § Definition of Cybersecurity (ref. Rec. ITU T X. 1205, Overview of cybersecurity): Cybersecurity is the collection of tools, policies, security concepts, security safeguards, guidelines, risk management approaches, actions, training, best practices, assurance and technologies that can be used to protect the cyber environment and organization and user’s assets. Organization and user’s assets include connected computing devices, personnel, infrastructure, applications, services, telecommunications systems, and the totality of transmitted and/or stored information in the cyber environment. Cybersecurity strives to ensure the attainment and maintenance of the security properties of the organization and user’s assets against relevant security risks in the cyber environment. The general security objectives comprise the following: – Availability – Integrity, which may include authenticity and non repudiation – Confidentiality. 113/163

Capacity building with ITU T cybersecurity standards § Existing process oriented standards, as well as checklist standards, should be complemented with detailed knowledge base of cybersecurity, because: § Cyber risks are highly volatile § Chain reactions are typical difficult to estimate the risk without considering technical detail § You’ll need to communicate the detail § ITU T provides knowledge base standards. 114/163

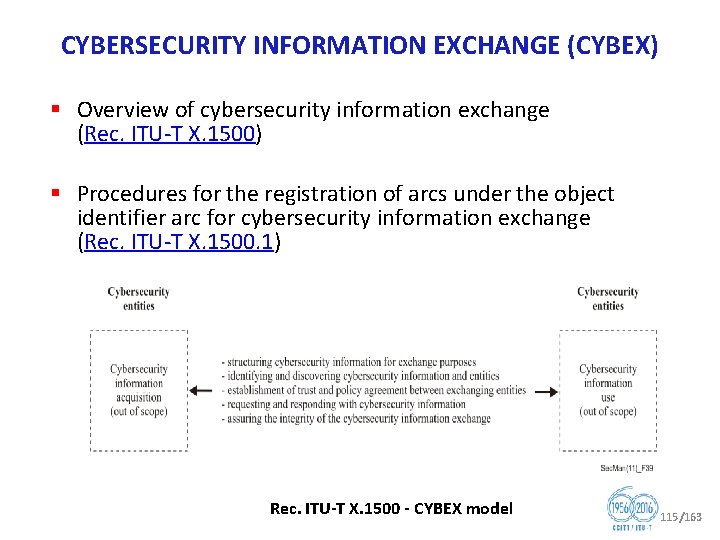
CYBERSECURITY INFORMATION EXCHANGE (CYBEX) § Overview of cybersecurity information exchange (Rec. ITU T X. 1500) § Procedures for the registration of arcs under the object identifier arc for cybersecurity information exchange (Rec. ITU T X. 1500. 1) Rec. ITU T X. 1500 CYBEX model 115/163

Knowledge base of vulnerabilities CVE: Common Vulnerability Enumeration § A structured means to exchange information on security vulnerabilities and exposures § Provides a common identifier with status indicator, a brief description and references to related vulnerability report and advisories for publicly known problems. § Standardized as Rec. ITU T X. 1520 § Applicable to national vulnerability databases: Ø U. S. NIST NVD Ø Japan JVN • CVE community: http: //cve. mitre. org/ • R. Martin, “Managing Vulnerabilities in Networked Systems”, IEEE Computer, 34 (11), Nov 2001. 116/163

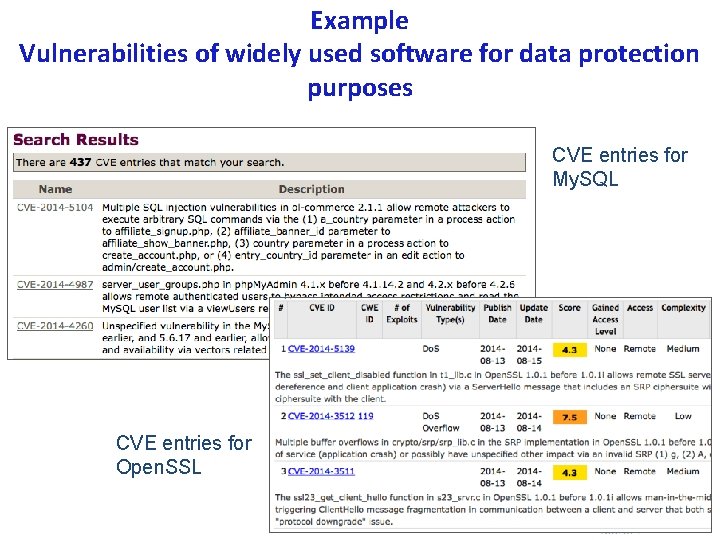
Example Vulnerabilities of widely used software for data protection purposes CVE entries for My. SQL CVE entries for Open. SSL

Ongoing proliferation of CVE • More than 150 CVE compatible products and services U. S. : NIST NVD Japan: IPA JVN 118/163

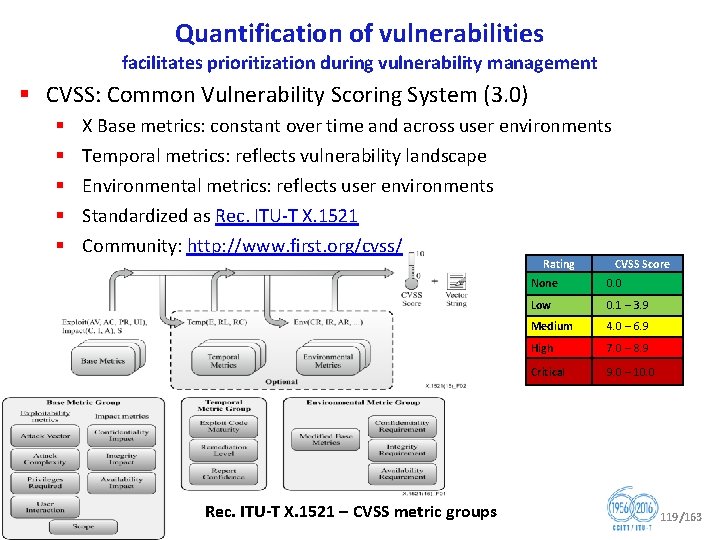
Quantification of vulnerabilities facilitates prioritization during vulnerability management § CVSS: Common Vulnerability Scoring System (3. 0) § § § X Base metrics: constant over time and across user environments Temporal metrics: reflects vulnerability landscape Environmental metrics: reflects user environments Standardized as Rec. ITU T X. 1521 Community: http: //www. first. org/cvss/ Rating Rec. ITU T X. 1521 – CVSS metric groups CVSS Score None 0. 0 Low 0. 1 – 3. 9 Medium 4. 0 – 6. 9 High 7. 0 – 8. 9 Critical 9. 0 – 10. 0 119/163

Taxonomy of vulnerabilities Common Weakness Enumeration (CWE) Rec. ITU T X. 1524 § Group same kind of vulnerabilities into a weakness, and give it a distinct number § Provides common names for publicly known problems in the commercial or open source software § Intended for security tools and services that can find weaknesses in source code and operational systems § Helps better understand manage software weaknesses related to architecture and design § Community: http: //cwe. mitre. org/ 120/163

CWE top 25 http: //cwe. mitre. org/top 25/ § Prioritized list of dangerous software errors § Intended to minimize software vulnerability and data breach Rank Score ID Name [1] 93. 8 CWE-89 Improper Neutralization of Special Elements used in an SQL Command [2] 83. 3 CWE-78 Improper Neutralization of Special Elements used in an OS Command [3] 79 CWE-120 Buffer Copy without Checking Size of Input [4] 77. 7 CWE-79 [5] 76. 9 CWE-306 Missing Authentication for Critical Function [6] 76. 8 CWE-862 Missing Authorization [7] 75 CWE-798 Use of Hard-coded Credentials [8] 75 CWE-311 Missing Encryption of Sensitive Data [9] 74 CWE-434 Unrestricted Upload of File with Dangerous Type [10] 73. 8 CWE-807 Reliance on Untrusted Inputs in a Security Decision [11] 73. 1 CWE-250 Execution with Unnecessary Privileges [12] 70. 1 CWE-352 Cross-Site Request Forgery (CSRF) [13] 69. 3 CWE-22 [14] 68. 5 CWE-494 Download of Code Without Integrity Check [15] 67. 8 CWE-863 Incorrect Authorization [16] 66 CWE-829 Inclusion of Functionality from Untrusted Control Sphere [17] 65. 5 CWE-732 Incorrect Permission Assignment for Critical Resource [18] 64. 6 CWE-676 Use of Potentially Dangerous Function Ø Procurement [19] 64. 1 CWE-327 Use of a Broken or Risky Cryptographic Algorithm [20] 62. 4 CWE-131 Incorrect Calculation of Buffer Size Ø Development, etc. [21] 61. 5 CWE-307 Improper Restriction of Excessive Authentication Attempts [22] 61. 1 CWE-601 URL Redirection to Untrusted Site [23] 61 CWE-134 Uncontrolled Format String [24] 60. 3 CWE-190 Integer Overflow or Wraparound [25] 59. 9 CWE-759 Use of a One-Way Hash without a Salt § Any software for data protection needs serious consideration of these failure modes, among others § Useful for: Improper Neutralization of Input During Web Page Generation Improper Limitation of a Pathname to a Restricted Directory

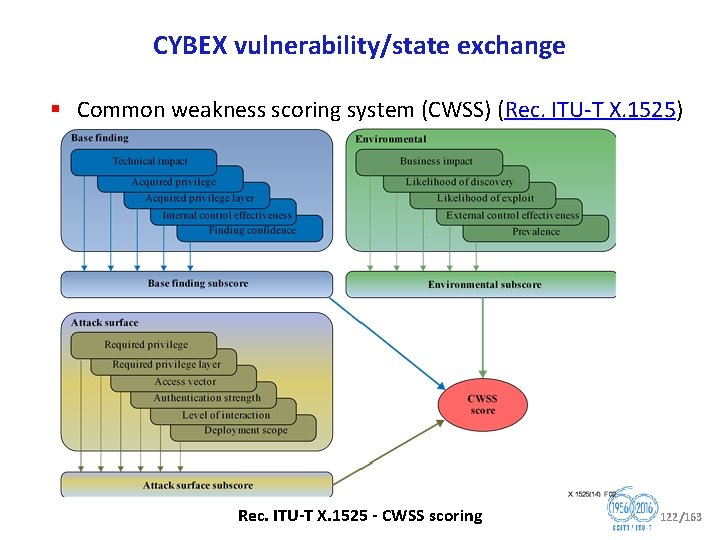
CYBEX vulnerability/state exchange § Common weakness scoring system (CWSS) (Rec. ITU T X. 1525) Rec. ITU T X. 1525 CWSS scoring 122/163

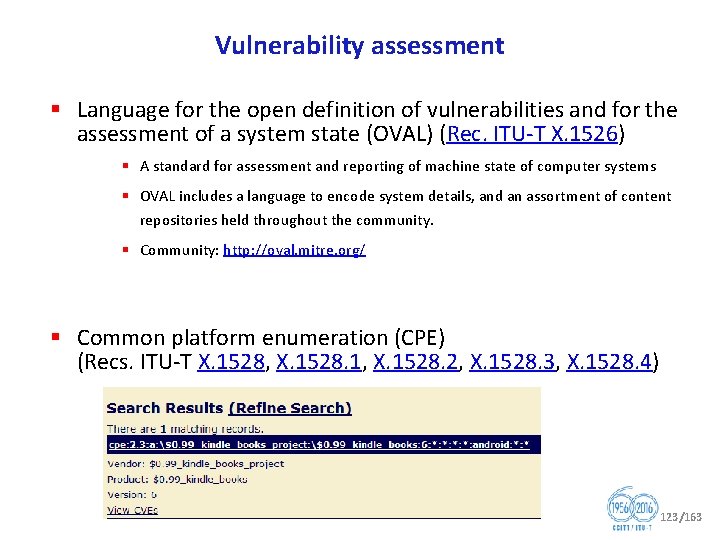
Vulnerability assessment § Language for the open definition of vulnerabilities and for the assessment of a system state (OVAL) (Rec. ITU T X. 1526) § A standard for assessment and reporting of machine state of computer systems § OVAL includes a language to encode system details, and an assortment of content repositories held throughout the community. § Community: http: //oval. mitre. org/ § Common platform enumeration (CPE) (Recs. ITU T X. 1528, X. 1528. 1, X. 1528. 2, X. 1528. 3, X. 1528. 4) 123/163

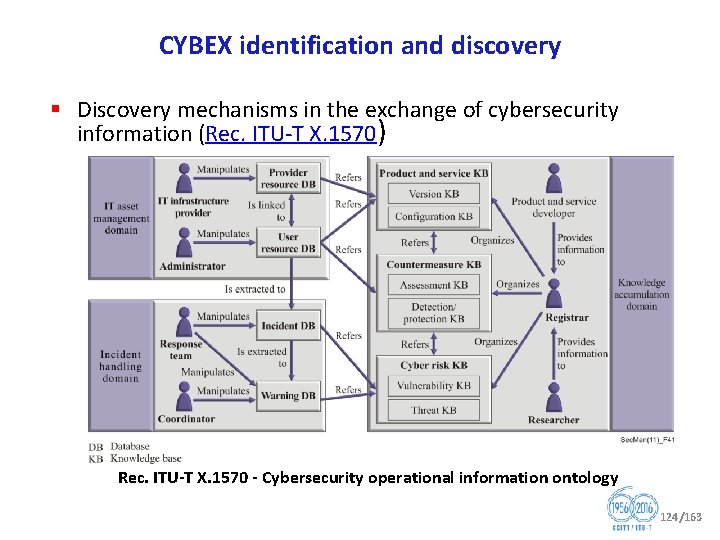
CYBEX identification and discovery § Discovery mechanisms in the exchange of cybersecurity information (Rec. ITU T X. 1570) Rec. ITU T X. 1570 Cybersecurity operational information ontology 124/163

CYBEX event/incident/heuristics exchange § Incident object description exchange format (IODEF) (Rec. ITU T X. 1541) § describes the information model for IODEF format (IETF RFC 5070) and provides an associated data model specified with XML schema. IODEF specifies a data model representation for sharing commonly exchanged information about computer security or other incident types. § IODEF enhances operational capabilities and improves situational awareness. § The IODEF structured format (in XML Schema) allows for: – increased automation in the processing of incident information through the exchange of structure incident information, eliminating the need for security analysts to parse free form textual documents; – decreased effort in correlating similar data (even when highly structured) from different sources enhancing situational awareness; – a common format on which to provide interoperability between tools for incident handling and analysis, specifically when information comes from multiple entities. 125/163

Knowledge base of attack patterns § Common Attack Pattern Enumeration and Classification (CAPEC) (Rec. ITU T X. 1544) – Dictionary of attack patterns, solutions & mitigations – Facilitates communication of incidents, issues, as well as validation techniques and mitigation strategies – Community: http: //capec. mitre. org/ CAPEC example: SQL injection 126

CYBEX event/incident/heuristics exchange § Malware attribute enumeration and classification (MAEC) (Rec. ITU T X. 1546) Rec. ITU T X. 1546 – High level MAEC overview 127/163

Session information message exchange format § Session information message exchange format (Rec. ITU T X. 1542) Rec. ITU T X. 1542 – The concept of SIMEF 128/163

CYBEX assured exchange § CYBEX assured exchange: § Real time inter network defence (RID) (Rec. ITU T X. 1580) § Transport of real time inter network defence messages (Rec. ITU T X. 1581) § Transport protocols supporting cybersecurity information exchange (Rec. ITU T X. 1582) 129/163

Improving cybersecurity throughout IT infrastructure lifecycle Development Deployment Assessment CWE X. 1524 CVE X. 1520 OVAL X. 1526 CAPEC X. 1544 CVSS X. 1521 CPE X. 1528 Knowledge bases, compatible products, informed communities and ITU-T Recommendations are already helping diverse organizations to protect their IT infrastructures and customers 130/163

Examples of CYBEX usage q National coordination centers for cybersecurity make use of vulnerability information identifiers and scoring standards for public alerting purposes. q Incident response teams efficiently keep track of vulnerabilities and attack patterns through a set of concise identifiers as predicated by CYBEX. q System administrators assess presence of vulnerabilities using software tools that employ CYBEX. q Cloud and network service providers keep track of vulnerabilities in their infrastructure, where they are prioritized according to impact, using the standardized scoring method. q Embedded and Io. T product developers learn typical patterns of software weaknesses through public knowledge base that is also part of CYBEX. q Vulnerability researchers collectively maintain knowledge bases of vulnerabilities, each of which can be linked and integrated through common vulnerability identifiers. 131/163

Emergency communications § Common alerting protocol (CAP 1. 1) (Rec. ITU T X. 1303) § Common alerting protocol (CAP 1. 2) (Rec. ITU T X. 1303 bis) § CAP is a simple but general format for exchanging all hazard emergency alerts and public warnings over all kinds of networks. § CAP allows a consistent warning message to be disseminated simultaneously over many different warning systems. 132/163

Countering spam § Technical strategies for countering spam (Rec. ITU T X. 1231) § Technologies involved in countering email spam (Rec. ITU T X. 1240) § Technical framework for countering email spam (Rec. ITU T X. 1241) § Short message service (SMS) spam filtering system based on user specified rules (Rec. ITU T X. 1242) § Interactive gateway system for countering spam (Rec. ITU T X. 1243) Note: These Recommendations do not address the content related aspects of telecommunications (ref. ITR 2012). 133/163

Countering spam § Overall aspects of countering spam in IP based multimedia applications (Rec. ITU T X. 1244) § Framework for countering spam in IP based multimedia applications (Rec. ITU T X. 1245) § Technologies involved in countering voice spam in telecommunication organizations (Rec. ITU T X. 1246) § Technical framework for countering mobile messaging spam (Rec. ITU T X. 1247) Note: These Recommendations do not address the content related aspects of telecommunications (ref. ITR 2012). 134/163

Countering spam Rec. ITU T X. 1231 General model for countering spam Rec. ITU T X. 1241 General structure of e mail anti spam processing domain Rec. ITU T X. 1245 Framework for countering IP media spam 135/163

Identity Management (Id. M) § Baseline capabilities for enhanced global identity management and interoperability (Rec. ITU T X. 1250) § A framework for user control of digital identity (Rec. ITU T X. 1251) § Baseline identity management terms and definitions (Rec. ITU T X. 1252) § Security guidelines for identity management systems (Rec. ITU T X. 1253) § Entity authentication assurance framework (Rec. ITU T X. 1254) § Framework for discovery of identity management information (Rec. ITU T X. 1255) § Guidelines on protection of personally identifiable information in the application of RFID technology (Rec. ITU T X. 1275) § Guidelines and framework for sharing network authentication results with service applications (Rec. ITU T X. 1256) § Identity and access management taxonomy (Rec. ITU T X. 1257) § Enhanced entity authentication based on aggregated attributes (Rec. ITU T X. 1258) 136/163

A framework for user control of digital identity § Defines a framework to enhance user control and exchange of their digital identity related information § Defines capabilities for the digital identity information exchange § Provides with the ability to control the release of personally identifiable information Rec. ITU T X. 1251 – Digital identity interchange framework 137/163

Baseline identity management terms and definitions § Provides 70 definitions of key terms used in identity management (Id. M) 6. 30 identity: A representation of an entity in the form of one or more attributes that allow the entity or entities to be sufficiently distinguished within context. For identity management (Id. M) purposes, the term identity is understood as contextual identity (subset of attributes), i. e. , the variety of attributes is limited by a framework with defined boundary conditions (the context) in which the entity exists and interacts. NOTE – Each entity is represented by one holistic identity that comprises all possible information elements characterizing such entity (the attributes). However, this holistic identity is a theoretical issue and eludes any description and practical usage because the number of all possible attributes is indefinite Rec. ITU T X. 1252 – Relationships between entity, identities and attributes 138/163

Security guidelines for identity management systems § Rec. ITU T X. 1253 provides security guidelines – for Id. M systems – how an Id. M system should be deployed and operated for secure identity services in a next generation network (NGN) or cyberspace environment – with advice on how to employ various security mechanisms to protect a general Id. M system – the required proper security procedures when two Id. M systems interoperate § Identifies security threats in Id. M systems § Provides security guidelines for Id. M systems how to manage security when a general Id. M system is deployed and operated. 139/163

Entity authentication assurance framework Rec. ITU T X. 1254 Overview of the entity authentication assurance framework Level 1 – Low 2 – Medium 3 – High 4 – Very high Description Little or no confidence in the claimed or asserted identity Some confidence in the claimed or asserted identity High confidence in the claimed or asserted identity Very high confidence in the claimed or asserted identity Rec. ITU T X. 1254 Levels of assurance 140/163

Framework for discovery of identity management information § Rec. ITU T X. 1255 provides an open architecture framework in which identity management information can be discovered § The core components of the framework set forth in this Recommendation include: 1) 2) 3) 4) a digital object data model a digital object interface protocol one or more identifier/resolution systems and one or more metadata registries These components form the basis of the open architecture framework. § Digital object architecture consists of a – Digital object repository – Resolution system – Digital object registry. Intrinsic attributes User-defined attributes DIGITAL ENTITY ID DATE MODIFIED DATE CREATED 84321/ab 5 04/11/2007 PERMISSION SCHEME A OBJECT TYPE More… 84321/ab 5 89754/163 ELEMENT Intrinsic attributes User defined attributes DATA Rec. ITU T X. 1255 Illustrative example of a digital entity 141/163

Authentication involving trust frameworks Rec. ITU T X. 1255 Authentication involving trust frameworks 142/163

Sharing network authentication results with service applications Rec. ITU T X. 1256 – Framework of sharing Rec. ITU T X. 1256 – Example: Internet service network authentication attributes using 2 G/3 G/4 G network location attributes with service applications 143/163

Identity and access management taxonomy Rec. ITU T X. 1257 – Example IAM domain model taxonomy for assigning business meaning 144/163

Enhanced entity authentication based on aggregated attributes Rec. ITU T X. 1258 – Architecture of identity linking method 145/163

Cloud computing security § Security framework for cloud computing (Rec. ITU T X. 1601) Security capabilities Identity and access management (IAM), authentication, authorization, and transaction audit Physical security Security threats Interface security Service security assessment and audit Incident management Computing virtualization security Disaster recovery Network security Interoperability, portability and reversibility Operational security Trust model Security challenges Supply chain security Data isolation, protection and privacy protection Security coordination Rec. ITU T X. 1601 Security framework for cloud computing 146/163

Cloud computing security § Security requirements for software as a service application environments (Rec. ITU T X. 1602) § Analyses the maturity levels of software as a service (Saa. S) application and proposes security requirements to provide a consistent and secure service execution environment for Saa. S applications. § The requirements originate from cloud service providers (CSP) and cloud service partners (CSN) as they need a Saa. S application environment to meet their demands on security. § The requirements are general and independent of any service or scenario specific model (e. g. web services, or representational state transfer (REST)), assumptions or solutions. § The target audiences of Rec. ITU T X. 1602 are cloud service providers (CSPs) and cloud service partners (CSNs) such as application developers. § Recommends four maturity levels of Saa. S applications: custom level, configurable level, multi tenant level, and scalable level. § Defines security requirements for the Saa. S application environment. 147/163

Cloud computing security § Guidelines for cloud service customer data security (Rec. ITU T X. 1641) § Guidelines for the operational security of cloud computing (Rec. ITU T X. 1642) – Provides generic operational security guidelines for cloud computing from the perspective of cloud service providers (CSPs). – Analyses the security requirements and metrics for the operation of cloud computing. – Provides a set of security measures and detailed security activities for the daily operation and maintenance to help CSPs mitigate security risks and address security challenges for the operation of cloud computing. 148/163

Cloud computing security § Information technology – Security techniques – Code of practice for information security controls based on ISO/IEC 27002 for cloud services (Rec. ITU T X. 1631 | ISO/IEC 27017) § Provides guidelines for information security controls applicable to the provision and use of cloud services by providing: – additional implementation guidance for relevant controls specified in ISO/IEC 27002; – additional controls with implementation guidance that specifically relate to cloud services. § Provides controls and implementation guidance for both cloud service providers and cloud service customers. 149/163

ITU T X. 500 series on Directory § Information technology – Open Systems Interconnection – The Directory: Overview of concepts, models and services (Rec. ITU T X. 500| ISO/IEC 9594 1) § Information technology – Open Systems Interconnection – The Directory: Models (Rec. ITU T X. 501 | ISO/IEC 9594 2) § Information technology – Open Systems Interconnection – The Directory: Public key and attribute certificate frameworks (Rec. ITU T X. 509 | ISO/IEC 9594 8) § Information technology – Open Systems Interconnection – The Directory: Abstract service definition (Rec. ITU T X. 511 | ISO/IEC 9594 3) § Information technology – Open Systems Interconnection – The Directory: Procedures for distributed operation (Rec. ITU T X. 518 | ISO/IEC 9594 4) § Information technology – Open Systems Interconnection – The Directory: Protocol specifications (Rec. ITU T X. 519 | ISO/IEC 9594 5) § Information technology – Open Systems Interconnection – The Directory: Selected attribute types (Rec. ITU T X. 520 | ISO/IEC 9594 6) § Information technology – Open Systems Interconnection – The Directory: Selected object classes (Rec. ITU T X. 521 | ISO/IEC 9594 7) § Information technology – Open Systems Interconnection – The Directory: Replication (Rec. ITU T X. 525 | ISO/IEC 9594 9) § Information technology – Open Systems Interconnection – The Directory: Use of systems management for administration of the Directory) (Rec. ITU T X. 530 | ISO/IEC 9594 10) 150/163

Abstract Syntax Notation 1 (ASN. 1) § § Specification of basic notation (Rec. ITU T X. 680) Information object specification (Rec. ITU T X. 681) Constraint specification (Rec. ITU T X. 682) Parameterization of ASN. 1 specifications (Rec. ITU T X. 683) -- public-key certificate definition Example: X. 509 certificate Certificate : : = SIGNED{TBSCertificate} encoded in ASN. 1 TBSCertificate : : = SEQUENCE { version [0] Version DEFAULT v 1, serial. Number Certificate. Serial. Number, signature Algorithm. Identifier{{Supported. Algorithms}}, issuer Name, validity Validity, subject Name, subject. Public. Key. Info Subject. Public. Key. Info, issuer. Unique. Identifier [1] IMPLICIT Unique. Identifier OPTIONAL, . . . , [[2: -- if present, version shall be v 2 or v 3 subject. Unique. Identifier [2] IMPLICIT Unique. Identifier OPTIONAL]], [[3: -- if present, version shall be v 2 or v 3 extensions [3] Extensions OPTIONAL]] -- If present, version shall be v 3]] 151/163 }

ASN. 1 encoding rules § Specification of Basic Encoding Rules (BER), Canonical Encoding Rules (CER) and Distinguished Encoding Rules (DER) (Rec. ITU T X. 690) § Specification of Packed Encoding Rules (PER) (Rec. ITU T X. 691) § Specification of Encoding Control Notation (ECN) (Rec. ITU T X. 692) § XML Encoding Rules (XER) (Rec. ITU T X. 693) § Mapping W 3 C XML schema definitions into ASN. 1 (Rec. ITU T X. 694) § Registration and application of PER encoding instructions (Rec. ITU T X. 695) § Specification of Octet Encoding Rules (OER) (Rec. ITU T X. 696) 152/163

Object Identifier (OID) an object identifier or OID is an identifier used to name an object. Structurally, an OID consists of a node in a hierarchically-assigned namespace, formally defined using the ITU-T's ASN. 1 standard, X. 690. Successive numbers of the nodes, starting at the root of the tree, identify each node in the tree. Designers set up new nodes by registering them under the node's registration authority. The root of the tree contains the following three arcs: • 0: ITU-T • 1: ISO • 2: joint-iso-itu-t 153/163

Object Identifier (OID) § Basic Reference Model: Naming and addressing (Rec. ITU T X. 650) § Procedures for the operation of object identifier registration authorities: General procedures and top arcs of the international object identifier tree (Rec. ITU T X. 660) § Procedures for the operation of OSI Registration Authorities: Registration of object identifier arcs beneath the top level arc jointly administered by ISO and ITU T (Rec. ITU T X. 662) § Procedures for the operation of OSI Registration Authorities: Registration of application processes and application entities (Rec. ITU T X. 665) § Procedures for the operation of OSI Registration Authorities: Joint ISO and ITU T registration of international organizations (Rec. ITU T X. 666) 154/163

Object Identifier (OID) § § § § Procedures for the operation of object identifier registration authorities: Generation of universally unique identifiers and their use in object identifiers (Rec. ITU T X. 667) Procedures for the operation of OSI Registration Authorities: Registration of object identifier arcs for applications and services using tag based identification (Rec. ITU T X. 668) Procedures for ITU T registration of identified organizations (Rec. ITU T X. 669) Use of registration agents to register names subordinate to country names in the X. 660 RH name tree (Rec. ITU T X. 670) Procedures for a Registration Authority operating on behalf of countries to register organization names subordinate to country names in the X. 660 RH name tree (Rec. ITU T X. 671) Object identifier resolution system (ORS) (Rec. ITU T X. 672) Procedures for the registration of arcs under the Alerting object identifier arc (Rec. ITU T X. 674) OID based resolution framework for heterogeneous identifiers and locators (Rec. ITU T X. 675) 155/163

Open Distributed Processing (ODP) Reference Model: Overview (Rec. ITU T X. 901) Reference model: Foundations (Rec. ITU T X. 902) Reference model: Architecture (Rec. ITU T X. 903) Reference Model: Architectural Semantics (Rec. ITU T X. 904) Use of UML for ODP system specifications (Rec. ITU T X. 906) Naming framework (Rec. ITU T X. 910) Reference model – Enterprise language (Rec. ITU T X. 911) Interface Definition Language (Rec. ITU T X. 920) Interface references and binding (Rec. ITU T X. 930) Protocol support for computational interactions (Rec. ITU T X. 931) Trading Function: Specification (Rec. ITU T X. 950) Trading function: Provision of trading function using OSI Directory service (Rec. ITU T X. 952) § Type repository function (Rec. ITU T X. 960) § § § 156/163

Specification and Description Language (SDL 2010) Specification and Description Language (SDL 2010, Recs. ITU T Z. 100 – Z. 109) § For unambiguous specification and description of telecommunication systems. § Allows the description of behaviour of systems using extended finite state machines communicating by messages § For specification of reactive systems § The range of application is from requirement description to implementation 157/163

Specification and Description Language (SDL 2010) § § § § § Overview of SDL 2010 (Rec. ITU T Z. 100) Basic SDL 2010 (Rec. ITU T Z. 101) Comprehensive SDL 2010 (Rec. ITU T Z. 102) Shorthand notation and annotation in SDL 2010 (Rec. ITU T Z. 103) Data and action language in SDL 2010 (Rec. ITU T Z. 104) SDL 2010 combined with ASN. 1 modules (Rec. ITU T Z. 105) Common interchange format for SDL 2010 (Rec. ITU T Z. 106) Object oriented data in SDL 2010 (Rec. ITU T Z. 107) Unified modeling language profile for SDL 2010 (Rec. ITU T Z. 109) 158/163

Message Sequence Chart (MSC) Rec. ITU T Z. 120 § Provides a trace language with graphical representation for the specification and description of the communication behaviour of system components and their environment by means of message interchange § Suitable for specification of the communication behaviour for real time systems, in particular telecommunication switching systems § For requirement specification, interface specification, simulation and validation, test case specification and documentation of real time systems 159/163

Message Sequence Chart (MSC) User Requirements Notation (URN) § Application of formal description techniques: § § § Criteria for use of formal description techniques by ITU T (Rec. ITU T Z. 110) Notations and guidelines for the definition of ITU T languages (Rec. ITU T Z. 111) Guidelines for UML profile design (Rec. ITU T Z. 119) § Message Sequence Chart (MSC): § § Message Sequence Chart (MSC) (Rec. ITU T Z. 120) Specification and Description Language (SDL) data binding to Message Sequence Charts (MSC) (Rec. ITU T Z. 121) § User Requirements Notation (URN): § User Requirements Notation (URN) – Language requirements and framework (Rec. ITU T Z. 150) § User Requirements Notation (URN) Language definition (Rec. ITU T Z. 151) 160/163

User Requirements Notation (URN) Recs. ITU T Z. 150, Z. 151 § URN is the first and currently only standard which explicitly addresses goals (non functional requirements with GRL) in addition to scenarios (functional requirements with UCMs) in a graphical way in one unified language § For the elicitation, analysis, specification, and validation of requirements § URN combines modelling concepts and notations for goals (mainly for non functional requirements and quality attributes) and scenarios (mainly for operational requirements, functional requirements, and performance and architectural reasoning). 161/163

Testing and Test Control Notation version 3 (TTCN 3) Recs. ITU T Z. 160 Z. 170 § For specification of test suites that are independent of platforms, test methods, protocol layers and protocols. § TTCN 3 can be used for specification of all types of reactive system tests over a variety of communication ports. § Typical areas of application are protocol testing (including mobile and Internet protocols), service testing (including supplementary services), module testing, testing of CORBA‑based platforms and APIs. 162/163

Testing and Test Control Notation version 3 (TTCN 3) § TTCN 3 core language (Rec. ITU T Z. 161) § TTCN 3 language extensions: Support of interfaces with continuous signals (Rec. ITU T Z. 161. 1) § TTCN 3 language extensions: Configuration and deployment support (Rec. ITU T Z. 161. 2) § TTCN 3 language extensions: Advanced parameterization (Rec. ITU T Z. 161. 3) § TTCN 3 language extensions: Behaviour types (Rec. ITU T Z. 161. 4) § TTCN 3 Language extensions: Performance and real time testing (Rec. ITU T Z. 161. 5) § TTCN 3 tabular presentation format (TFT) (Rec. ITU T Z. 162) § TTCN 3 graphical presentation format (GFT) (Rec. ITU T Z. 163) 163/163

Testing and Test Control Notation version 3 (TTCN 3) § TTCN 3 operational semantics (Rec. ITU T Z. 164) § TTCN 3 runtime interface (TRI) (Rec. ITU T Z. 165) § TTCN 3 language extensions: Extended TRI (Rec. ITU T Z. 165. 1) § § § TTCN 3 control interface (TCI) (Rec. ITU T Z. 166) Using ASN. 1 with TTCN 3 (Rec. ITU T Z. 167) The IDL to TTCN 3 mapping (Rec. ITU T Z. 168) Using XML schema with TTCN 3 (Rec. ITU T Z. 169) TTCN 3 documentation comment specification (Rec. ITU T Z. 170) 164/163