Differential Cryptanalysis 1 Information Security Group ICU DCDifferential




![3 -round DES by LC P PH PL [22] [7, 18, 24, 29] [15] 3 -round DES by LC P PH PL [22] [7, 18, 24, 29] [15]](https://slidetodoc.com/presentation_image/5e4677517aaa682aaa97d56731f7f044/image-24.jpg)

![Variation of DC/LC q Multiple LC : Kaliski & Robshaw [CR 94] q Differential-Linear Variation of DC/LC q Multiple LC : Kaliski & Robshaw [CR 94] q Differential-Linear](https://slidetodoc.com/presentation_image/5e4677517aaa682aaa97d56731f7f044/image-30.jpg)
- Slides: 38

Differential Cryptanalysis 1 © Information Security Group, ICU

DC(Differential Cryptanalysis) q Introduction m Biham and Shamir : CR 90, CR 92 m Efficient than Key Exhaustive Search m Chosen Plaintext Attack m O(Breaking DES 16) ~ 247 m Utilize the probabilistic distribution between input XOR and output XOR values Iteratively m Stimulate to announce hidden criteria of DES [Cop 92] m Apply to other DES-like Ciphers * E. Biham, A. Shamir, ”Differential Cryptanalysis of the Data Encryption Standard”, Springer. Verlag, 1993 2 © Information Security Group, ICU

Eli Biham q Eli biham (http: //www. cs. technion. ac. il/~biham/) is an Israeli cryptographer and cryptanalyst, currently a professor at the Technion Israeli Institute of Technology Computer Science department. biham received his Ph. D. for inventing (publicly) differential cryptanalysis, while working under Adi Shamir. It had, it turned out, been invented at least twice before. A team at IBM discovered it during their work on DES, and was requested/required to keep their discovery secret by the NSA, who evidently knew about it as well. q In addition to his many contributions to cryptanalysis, biham has taken part in the design of several new cryptographic primitives: m Serpent (with Ross Anderson and Lars Knudsen), a block cipher which was one of the final five contenders to become the Advanced Encryption Standard m Tiger (with Ross Anderson), a hash function fast on 64 -bit machines, and m Py (with Jennifer Seberry), a fast stream cipher which has some cryptanalytic claims against it. 3 © Information Security Group, ICU

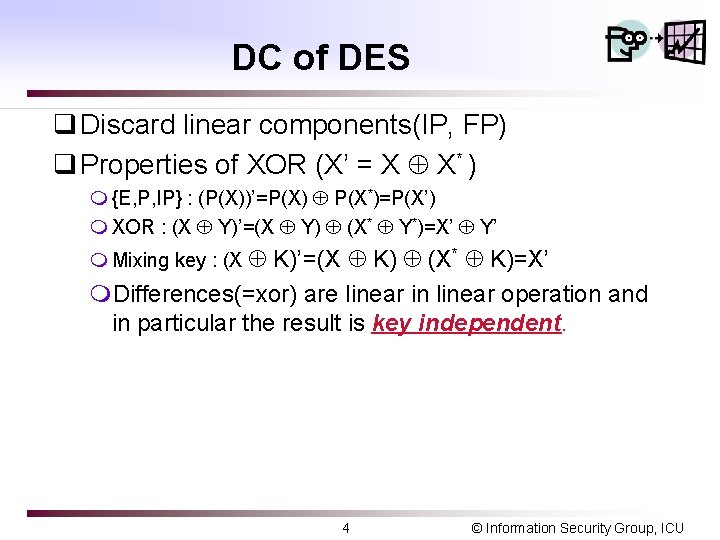
DC of DES q Discard linear components(IP, FP) q Properties of XOR (X’ = X X* ) m {E, P, IP} : (P(X))’=P(X) P(X*)=P(X’) m XOR : (X Y)’=(X Y) (X* Y*)=X’ Y’ m Mixing key : (X K)’=(X K) (X* K)=X’ m. Differences(=xor) are linear in linear operation and in particular the result is key independent. 4 © Information Security Group, ICU

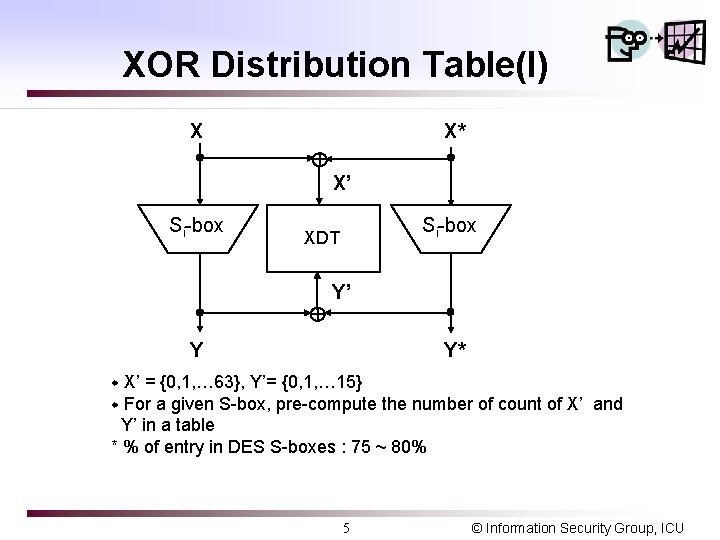
XOR Distribution Table(I) X X* X’ Si-box XDT Y’ Y Y* X’ = {0, 1, … 63}, Y’= {0, 1, … 15} w For a given S-box, pre-compute the number of count of X’ and Y’ in a table * % of entry in DES S-boxes : 75 ~ 80% w 5 © Information Security Group, ICU

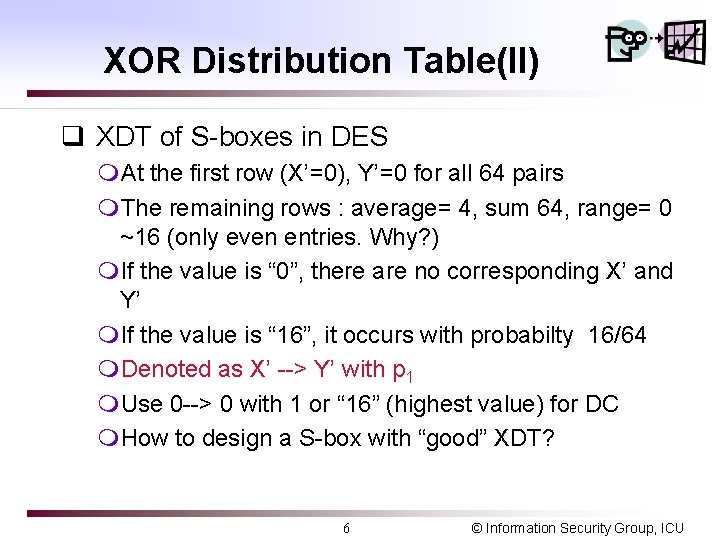
XOR Distribution Table(II) q XDT of S-boxes in DES m. At the first row (X’=0), Y’=0 for all 64 pairs m. The remaining rows : average= 4, sum 64, range= 0 ~16 (only even entries. Why? ) m. If the value is “ 0”, there are no corresponding X’ and Y’ m. If the value is “ 16”, it occurs with probabilty 16/64 m. Denoted as X’ --> Y’ with p 1 m. Use 0 --> 0 with 1 or “ 16” (highest value) for DC m. How to design a S-box with “good” XDT? 6 © Information Security Group, ICU

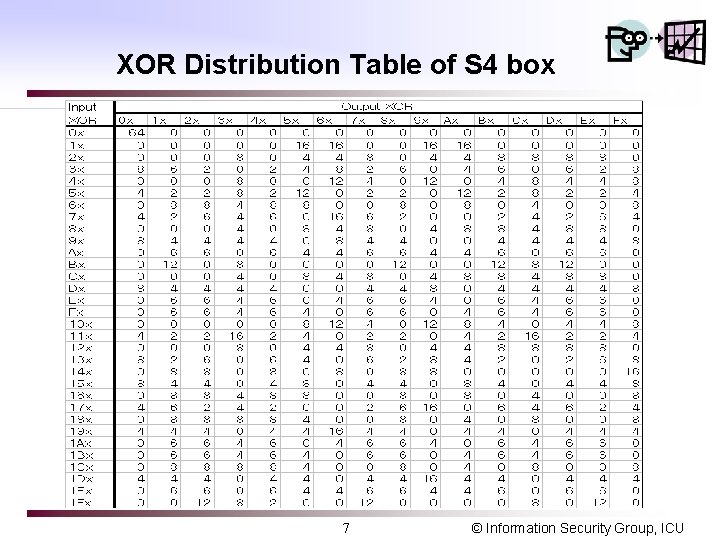
XOR Distribution Table of S 4 box 7 © Information Security Group, ICU

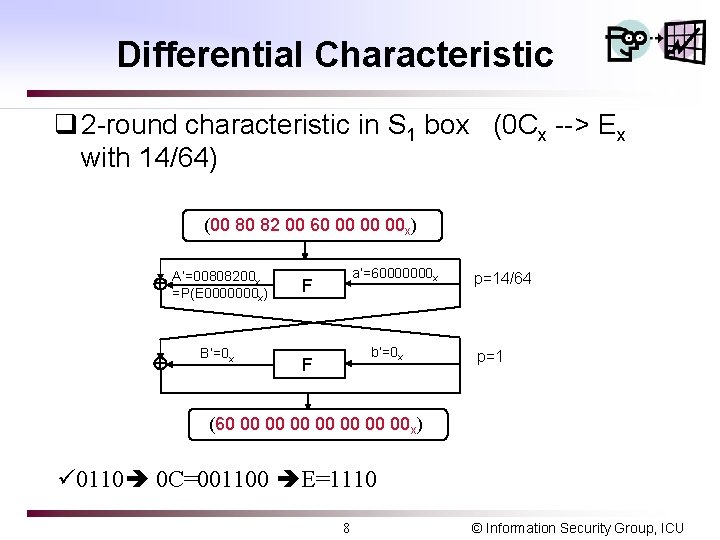
Differential Characteristic q 2 -round characteristic in S 1 box (0 Cx --> Ex with 14/64) (00 80 82 00 60 00 00 00 x) x A’=00808200 =P(E 0000000 ) x B’=0 x a’=60000000 x F b’=0 x F p=14/64 p=1 (60 00 00 x) ü 0110 0 C=001100 E=1110 8 © Information Security Group, ICU

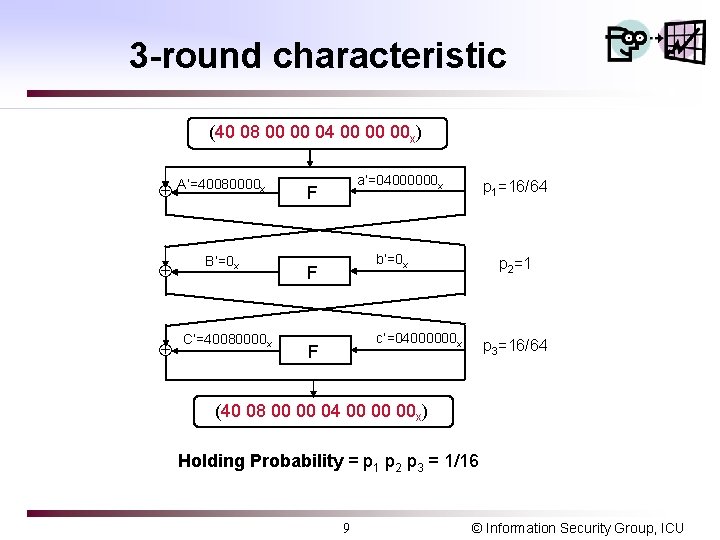
3 -round characteristic (40 08 00 00 04 00 00 00 x) A’=40080000 x B’=0 x C’=40080000 x a’=04000000 x F p 1=16/64 b’=0 x F p 2=1 c’=04000000 x F p 3=16/64 (40 08 00 00 04 00 00 00 x) Holding Probability = p 1 p 2 p 3 = 1/16 9 © Information Security Group, ICU

Searching Way for round keys (1) Choose suitable Plaintext (Pt) XOR. (2) Get 2 Pts for a chosen Pt and obtain the corresponding Ct by encryption (3) From Pt XOR and pair of Ct, get the expected output XOR for the S-boxes of final round. (4) Count the maximum potential key at the final round using the estimated key (5) Right key is a subkey of having large number of pairs of expected output XOR 10 © Information Security Group, ICU

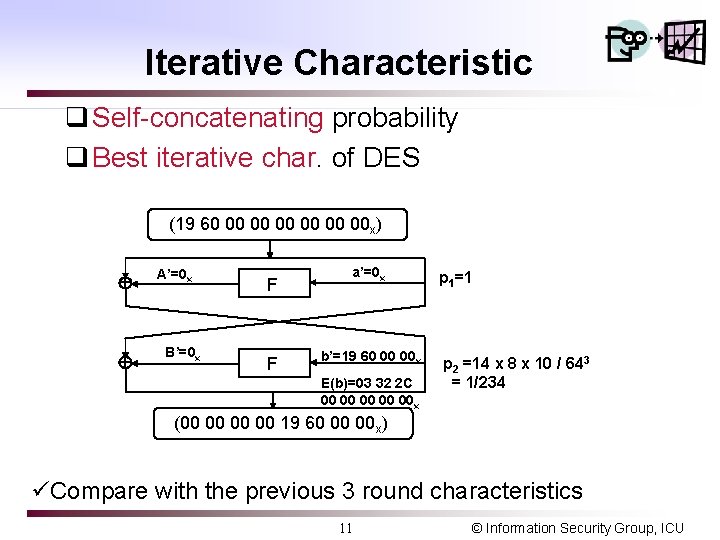
Iterative Characteristic q Self-concatenating probability q Best iterative char. of DES (19 60 00 00 00 x) A’=0 x B’=0 x F F a’=0 x b’=19 60 00 00 x E(b)=03 32 2 C 00 00 00 x p 1=1 p 2 =14 x 8 x 10 / 643 = 1/234 (00 00 19 60 00 00 x) üCompare with the previous 3 round characteristics 11 © Information Security Group, ICU

12 © Information Security Group, ICU

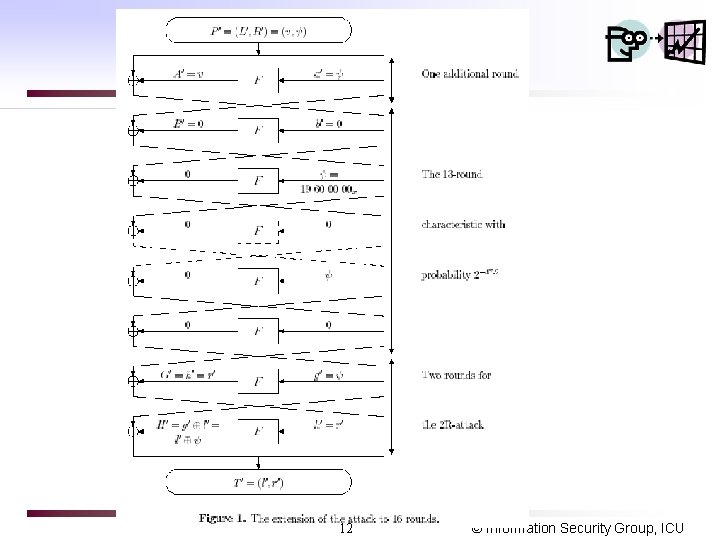
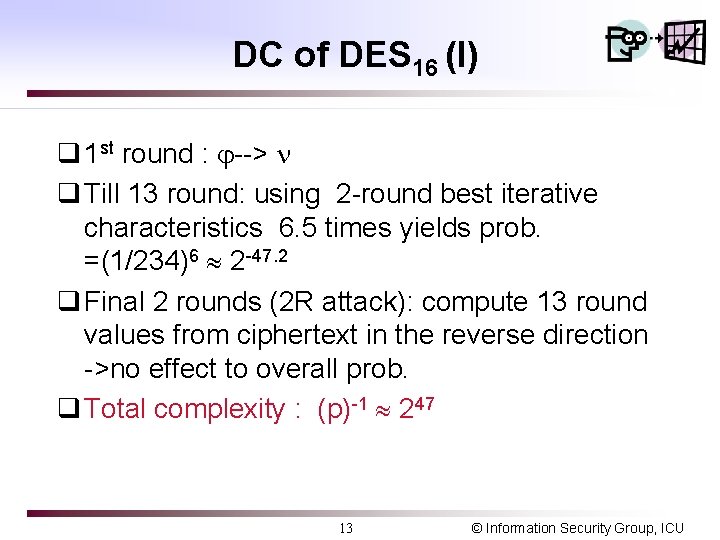
DC of DES 16 (I) q 1 st round : --> q Till 13 round: using 2 -round best iterative characteristics 6. 5 times yields prob. =(1/234)6 2 -47. 2 q Final 2 rounds (2 R attack): compute 13 round values from ciphertext in the reverse direction ->no effect to overall prob. q Total complexity : (p)-1 247 13 © Information Security Group, ICU

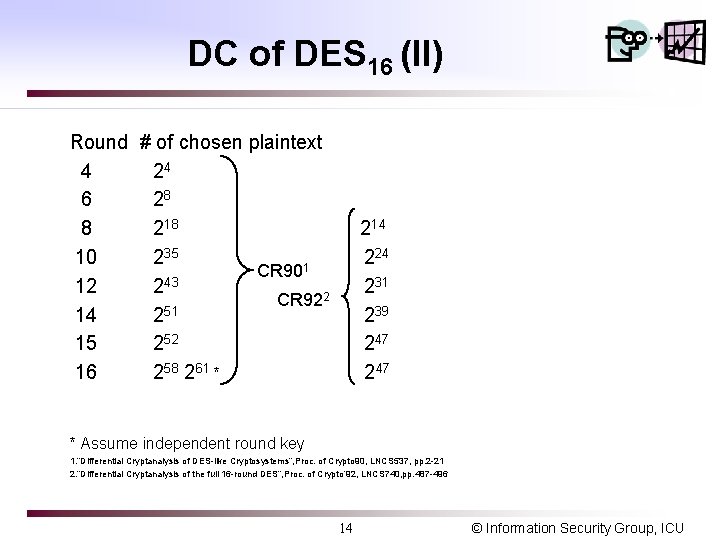
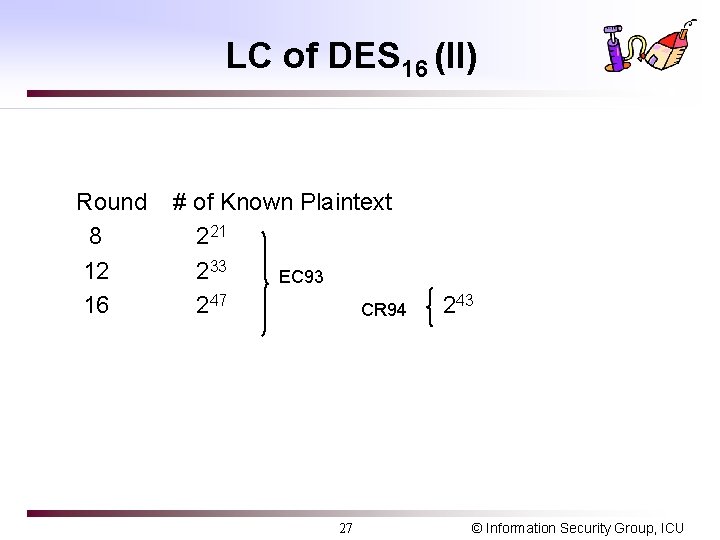
DC of DES 16 (II) Round # of chosen plaintext 4 24 6 28 8 218 10 235 CR 901 12 243 CR 922 51 14 2 15 252 16 258 261 * 214 224 231 239 247 * Assume independent round key 1. “Differential Cryptanalysis of DES-like Cryptosystems”, Proc. of Crypto 90, LNCS 537, pp. 2 -21 2. “Differential Cryptanalysis of the full 16 -round DES”, Proc. of Crypto’ 92, LNCS 740, pp. 487 -496 14 © Information Security Group, ICU

Additional result of DES by DC q P Permutation : can’t strengthen DES q Change the order of S-box : can weaken much or strengthen only up to 248 q Replacement XORs by addition : can weaken much in some cases q Modifying S-boxes mrandom : 218 - 220 mmodifying one entry (i. e. , S(0) ->S(4)) : 233 muniform distribution table : 226 15 © Information Security Group, ICU

Linear Cryptanalysis 16 © Information Security Group, ICU

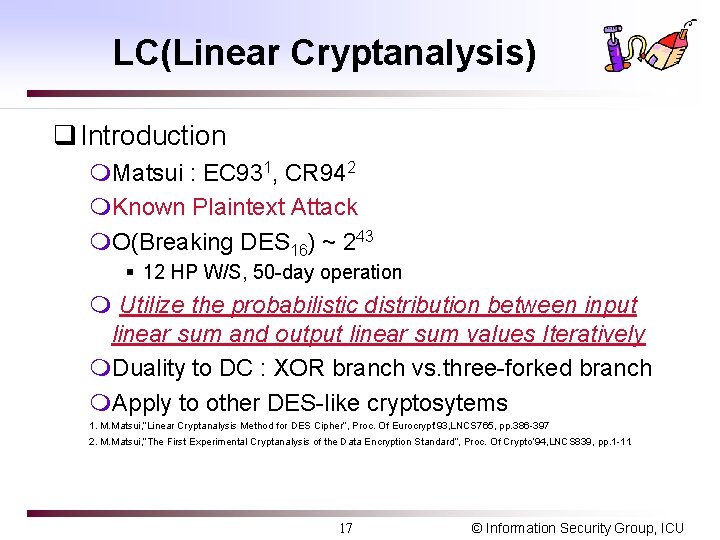
LC(Linear Cryptanalysis) q Introduction m. Matsui : EC 931, CR 942 m. Known Plaintext Attack m. O(Breaking DES 16) ~ 243 § 12 HP W/S, 50 -day operation m Utilize the probabilistic distribution between input linear sum and output linear sum values Iteratively m. Duality to DC : XOR branch vs. three-forked branch m. Apply to other DES-like cryptosytems 1. M. Matsui, ”Linear Cryptanalysis Method for DES Cipher”, Proc. Of Eurocrypt’ 93, LNCS 765, pp. 386 -397 2. M. Matsui, ”The First Experimental Cryptanalysis of the Data Encryption Standard”, Proc. Of Crypto’ 94, LNCS 839, pp. 1 -11. 17 © Information Security Group, ICU

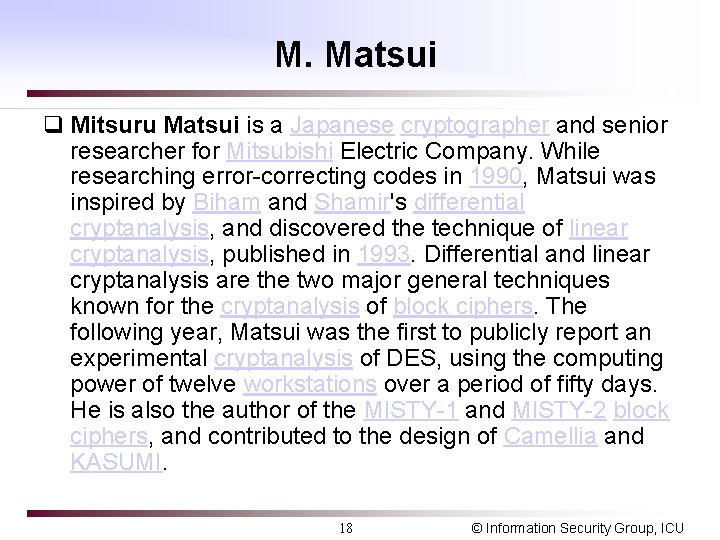
M. Matsui q Mitsuru Matsui is a Japanese cryptographer and senior researcher for Mitsubishi Electric Company. While researching error-correcting codes in 1990, Matsui was inspired by Biham and Shamir's differential cryptanalysis, and discovered the technique of linear cryptanalysis, published in 1993. Differential and linear cryptanalysis are the two major general techniques known for the cryptanalysis of block ciphers. The following year, Matsui was the first to publicly report an experimental cryptanalysis of DES, using the computing power of twelve workstations over a period of fifty days. He is also the author of the MISTY-1 and MISTY-2 block ciphers, and contributed to the design of Camellia and KASUMI. 18 © Information Security Group, ICU

Eurocrypt 1992 -Hungary 19 © Information Security Group, ICU

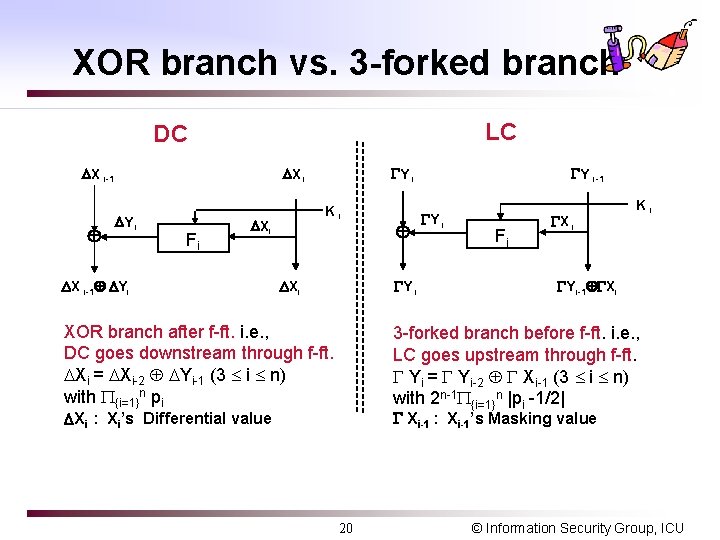
XOR branch vs. 3 -forked branch LC DC X i-1 X i Y i Fi Ki X i-1 Yi Y i Xi Y i XOR branch after f-ft. i. e. , DC goes downstream through f-ft. Xi = Xi-2 Yi-1 (3 i n) with {i=1}n pi Y i-1 Y i Fi X i Ki Yi-1 Xi 3 -forked branch before f-ft. i. e. , LC goes upstream through f-ft. Yi = Yi-2 Xi-1 (3 i n) with 2 n-1 {i=1}n |pi -1/2| Xi-1 : Xi-1’s Masking value Xi : Xi’s Differential value 20 © Information Security Group, ICU

Basic principle of LC (Goal) : Find linear approximation P[i 1, i 2, …, ia] C[j 1, j 2, …, jb]=K[k 1, k 2, …, kc] with significant prob. p ( ½) where A[i, j, …, k]=A[i] A[j] … A[k] (Algorithm)MLE(Maximum Likelihood Estimation) (Step 1) For given P and C, compute X=P[i 1, i 2, …, ia] C[j 1, j 2, …, jb], let N = # of Pt given, (Step 2) if |X=0| > N/2 K[k 1, k 2, …, Kc]=0 else 1. if |X=0| < N/2 K[k 1, k 2, …, kc]=1 else 0. 21 © Information Security Group, ICU

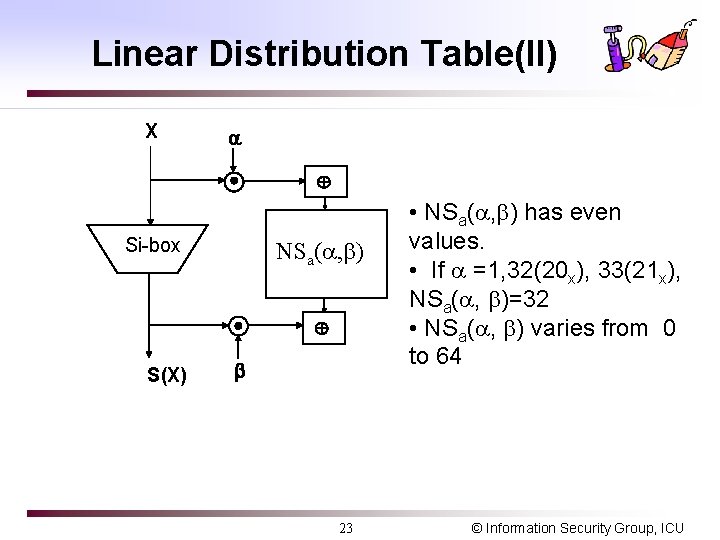
Linear Distribution Table(I) q For a S-box Sa, (a=1, 2, …, 8) of DES NSa( , )= #{x | 0 x < 64, parity(x ) = parity(S(x) )} 1 63 , 1 15, : dot product (bitwise AND) q Ex) NS 5(16, 15) =12 m The 5 -th input bit at S 5 -box is equal to the linear sum of 4 output bits with probability 12/64. m X[15] F(X, K)[7, 18, 24, 29]=K[22] with 0. 19 m X[15] F(X, K)[7, 18, 24, 29]=K[22] 1 with 1 -0. 19=0. 81 (Note) least significant at the right and index 0 at the least significant bit (Little endian) 22 © Information Security Group, ICU

Linear Distribution Table(II) X Si-box NSa( , ) S(X) 23 • NSa( , ) has even values. • If =1, 32(20 x), 33(21 x), NSa( , )=32 • NSa( , ) varies from 0 to 64 © Information Security Group, ICU
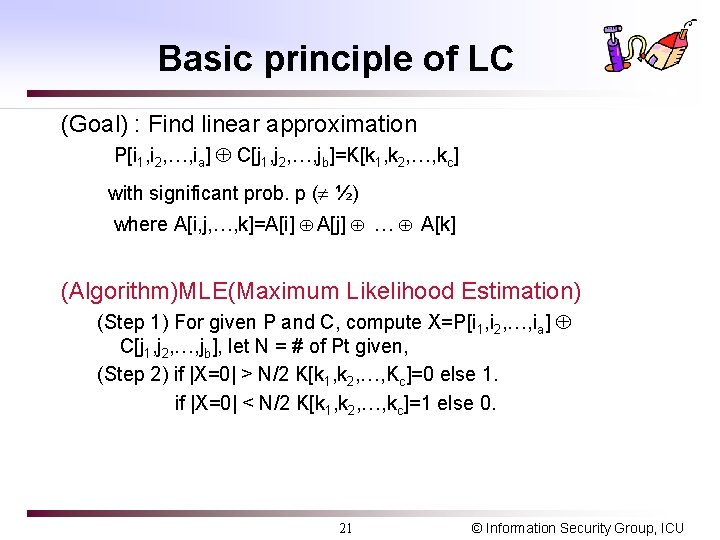
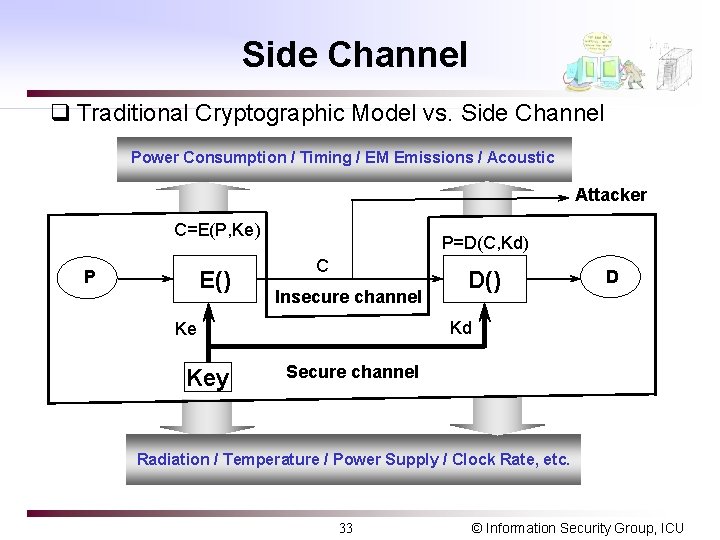
![3 round DES by LC P PH PL 22 7 18 24 29 15 3 -round DES by LC P PH PL [22] [7, 18, 24, 29] [15]](https://slidetodoc.com/presentation_image/5e4677517aaa682aaa97d56731f7f044/image-24.jpg)
3 -round DES by LC P PH PL [22] [7, 18, 24, 29] [15] F 1 K 1 X 2[7, 18, 24, 29] PH[7, 18, 24, 29] PL[15] = K 1[22] ----- (1) X 1 p 1=12/64 K 2 X 2 F 2 K 3 X 2[7, 18, 24, 29] CH[7, 18, 24, 29] [22] CH [7, 18, 24, 29] F 3 [15] X 3 CL[15] = K 3[22] ----- (2) p 3=12/64 CL C (1) (2) => X 2[7, 18, 24, 29] CH[7, 18, 24, 29] CL[15] X 2[7, 18, 24, 29] PH[7, 18, 24, 29] PL[15] = K 1[22] K 3[22] holding prob. = (p 1 * p 3 ) + (1 - p 1) *(1 -p 3) * Discard IP and FP like DC 24 © Information Security Group, ICU

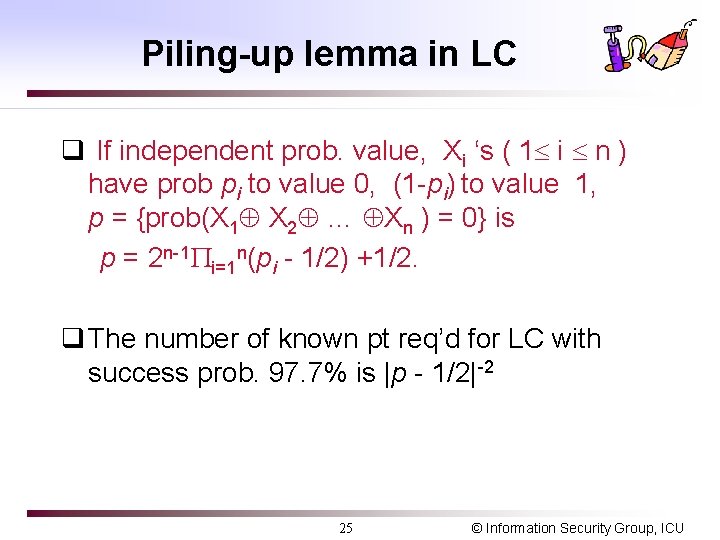
Piling-up lemma in LC q If independent prob. value, Xi ‘s ( 1 i n ) have prob pi to value 0, (1 -pi) to value 1, p = {prob(X 1 X 2 … Xn ) = 0} is p = 2 n-1 i=1 n(pi - 1/2) +1/2. q The number of known pt req’d for LC with success prob. 97. 7% is |p - 1/2|-2 25 © Information Security Group, ICU

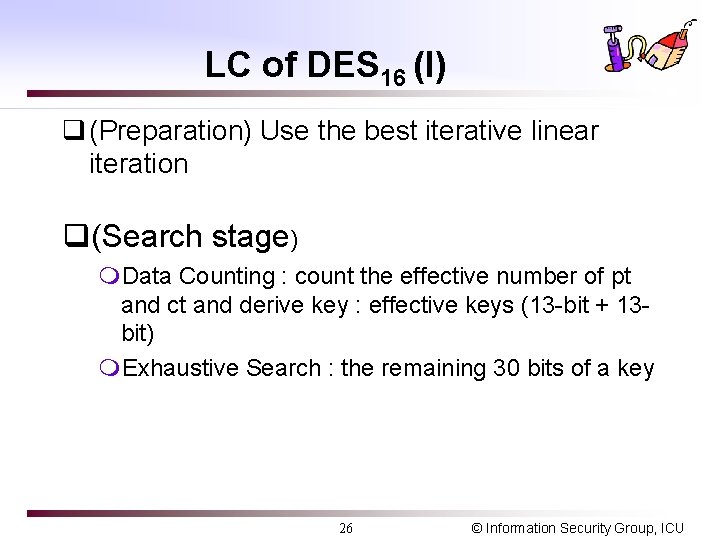
LC of DES 16 (I) q (Preparation) Use the best iterative linear iteration q(Search stage) m. Data Counting : count the effective number of pt and ct and derive key : effective keys (13 -bit + 13 bit) m. Exhaustive Search : the remaining 30 bits of a key 26 © Information Security Group, ICU

LC of DES 16 (II) Round 8 12 16 # of Known Plaintext 221 233 EC 93 247 CR 94 27 243 © Information Security Group, ICU

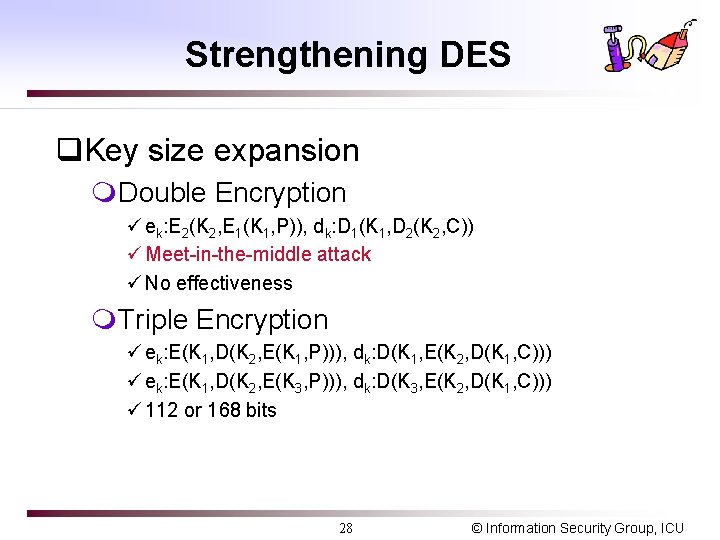
Strengthening DES q. Key size expansion m. Double Encryption ü ek: E 2(K 2, E 1(K 1, P)), dk: D 1(K 1, D 2(K 2, C)) ü Meet-in-the-middle attack ü No effectiveness m. Triple Encryption ü ek: E(K 1, D(K 2, E(K 1, P))), dk: D(K 1, E(K 2, D(K 1, C))) ü ek: E(K 1, D(K 2, E(K 3, P))), dk: D(K 3, E(K 2, D(K 1, C))) ü 112 or 168 bits 28 © Information Security Group, ICU

Variations 29 © Information Security Group, ICU
![Variation of DCLC q Multiple LC Kaliski Robshaw CR 94 q DifferentialLinear Variation of DC/LC q Multiple LC : Kaliski & Robshaw [CR 94] q Differential-Linear](https://slidetodoc.com/presentation_image/5e4677517aaa682aaa97d56731f7f044/image-30.jpg)
Variation of DC/LC q Multiple LC : Kaliski & Robshaw [CR 94] q Differential-Linear Cryptanalysis : Langford & Hellman [CR 94] q Truncated and Higher order DC : Knudsen [FSE 95] q Nonlinear Approximation in LC : Knudsen [EC 96] q Partitioning Cryptanalysis : Harpes & Massey [FSE 97] q Interpolation Attack : Jakobsen & Knudsen [FSE 97] q Differential Attack with Impossible Characteristics : Biham [EC 99], etc. q Related-key Attack : Kelsey, Schneier, Wagner [CR 96] 30 © Information Security Group, ICU

Asiacrypt 1996 -Kyongju, Korea 31 © Information Security Group, ICU

Side Channel Attack 32 © Information Security Group, ICU

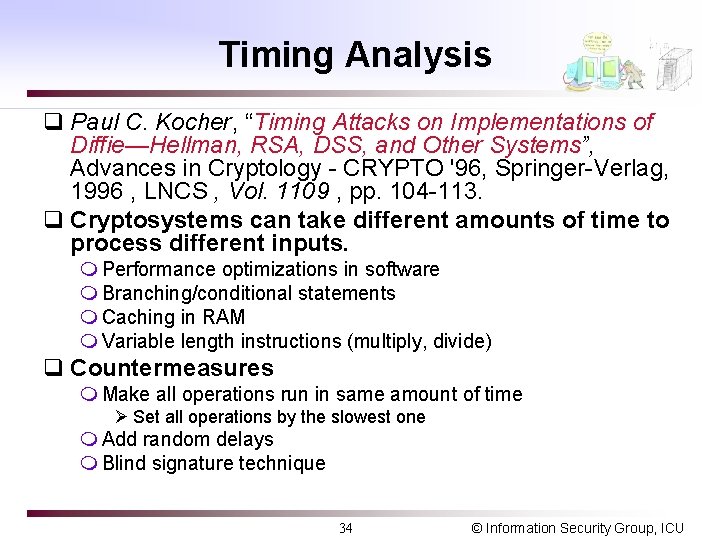
Side Channel q Traditional Cryptographic Model vs. Side Channel Power Consumption / Timing / EM Emissions / Acoustic Attacker C=E(P, Ke) E() P P=D(C, Kd) C Insecure channel D Kd Ke Key D() Secure channel Radiation / Temperature / Power Supply / Clock Rate, etc. 33 © Information Security Group, ICU

Timing Analysis q Paul C. Kocher, “Timing Attacks on Implementations of Diffie—Hellman, RSA, DSS, and Other Systems”, Advances in Cryptology - CRYPTO '96, Springer-Verlag, 1996 , LNCS , Vol. 1109 , pp. 104 -113. q Cryptosystems can take different amounts of time to process different inputs. m Performance optimizations in software m Branching/conditional statements m Caching in RAM m Variable length instructions (multiply, divide) q Countermeasures m Make all operations run in same amount of time Ø Set all operations by the slowest one m Add random delays m Blind signature technique 34 © Information Security Group, ICU

Fault Analysis q D. Boneh, R. De. Millo, and R. Lipton, “On the importance of checking cryptographic protocols for faults”, Journal of Cryptology, Springer-Verlag, Vol. 14, No. 2, pp. 101 -119, 2001 q Aim to cause errors during the processing of a cryptographic device m Simple Fault Analysis m Differential Fault Analysis q Countermeasures m Verify correctness of output before transmitting it to the external m Make devices tamper resistant (strong shielding, detect supply voltages and clock speeds) 35 © Information Security Group, ICU

Power Analysis q Paul C. Kocher and Joshua Jaffe and Benjamin Jun “Differential Power Analysis”, Advances in Cryptology -CRYPTO '99, Springer-Verlag, 1999 , LNCS , Vol. 1666 , pp. 388 -397 q The power consumed by a cryptographic device was analyzed during the processing of the cryptographic operation m Simple Power Analysis m Differential Power Analysis q Countermeasures m Don’t use secret values in conditionals/loops m Ensure little variation in power consumption between instructions m Reducing power variations (shielding, balancing) m Randomness (power, execution, timing) + counters on card m Algorithm redesign (non-linear key update, blinding) m Hardware redesign (decouple power supply, gate level design) 36 © Information Security Group, ICU

EM Emissions q D. Agrawal and B. Archambeault and J. R. Rao and P. Rohatgi “The EM Side-Channel(s)”, Cryptographic Hardware and Embedded Systems - CHES 2002, Springer-Verlag, 2003 , LNCS , Vol. 2523 , pp. 29 -45 q 1950 s TEMPEST q EM side channels include a higher variety of information and can be additionally applied from a certain distance. q Countermeasures m Redesign circuits m Shielding m EM noise 37 © Information Security Group, ICU

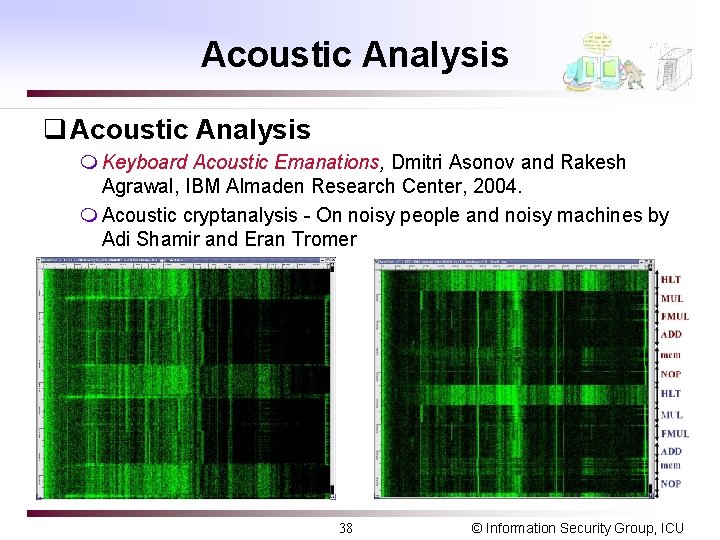
Acoustic Analysis q Acoustic Analysis m Keyboard Acoustic Emanations, Dmitri Asonov and Rakesh Agrawal, IBM Almaden Research Center, 2004. m Acoustic cryptanalysis - On noisy people and noisy machines by Adi Shamir and Eran Tromer 38 © Information Security Group, ICU