Your Security in the IT Market Hash Function








- Slides: 19

Your Security in the IT Market Hash Function Design: Overview of the basic components in SHA-3 competition Daniel Joščák, S. ICZ a. s. & MFF UK 07/05/2009, SPI Brno www. i. cz

Your Security in the IT Market Hash functions in cryptology ► Key component of many protocols ● ● Electronic signature Integrity check One-way function … ► Fingerprints or message digests www. i. cz

Your Security in the IT Market Good hash ftion must be ► Collision resistant: it is hard to find two distinct inputs m 1 and m 2, s. t. H(m 1) = H(m 2). ► 1 st preimage resistant: given h, it is hard to find any m s. t. h = H(m). ► 2 nd preimage resistant: given m 1, it is hard to find m 2≠ m 1 s. t. H(m 1) = H(m 2) ► Efficient (speed matters) www. i. cz

Your Security in the IT Market Why to build them? ► Weaknesses in old wide spread h. f. ● MD 2, MD 4, MD 5, SHA 1 ► Real collisions producing algorithms former functions ‘ www. i. cz ● ● Wang et al. 04 Klíma 05 Rechberger et al. 06 Stevens 05 and 06 (new target collisions)

Your Security in the IT Market Need for a new function ► “only” SHA 2 functions are fine ► SHA 3 competition organized by NIST ● deadline 31. oct. 2008 ● 51 submissions new candidates for SHA-3 www. i. cz

Your Security in the IT Market Areas for research and improvements 1. Mode of use for compression function 2. Compression function itself www. i. cz

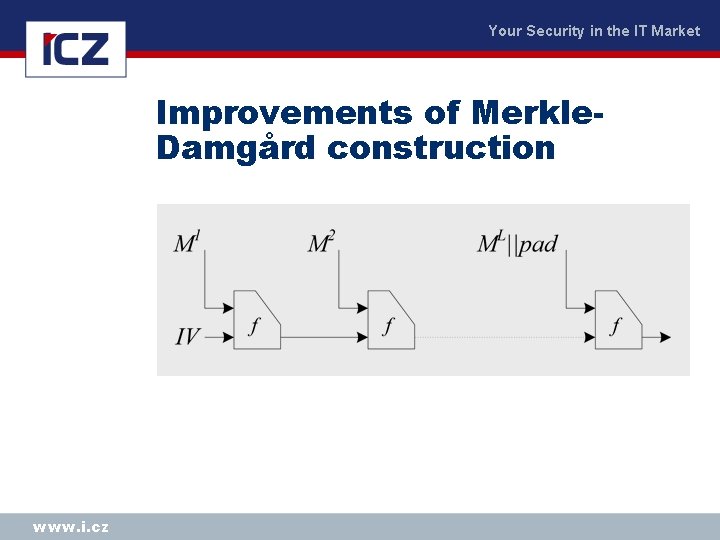
Your Security in the IT Market Improvements of Merkle. Damgård construction www. i. cz

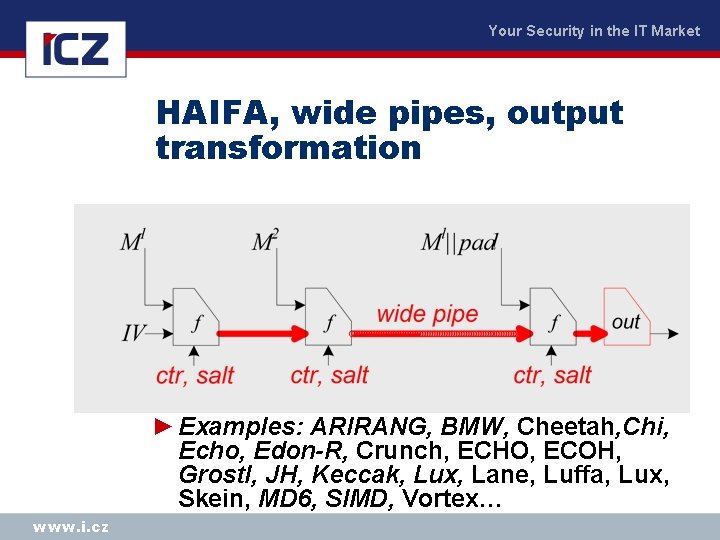
Your Security in the IT Market HAIFA, wide pipes, output transformation ► Examples: ARIRANG, BMW, Cheetah, Chi, Echo, Edon-R, Crunch, ECHO, ECOH, Grostl, JH, Keccak, Lux, Lane, Luffa, Lux, Skein, MD 6, SIMD, Vortex… www. i. cz

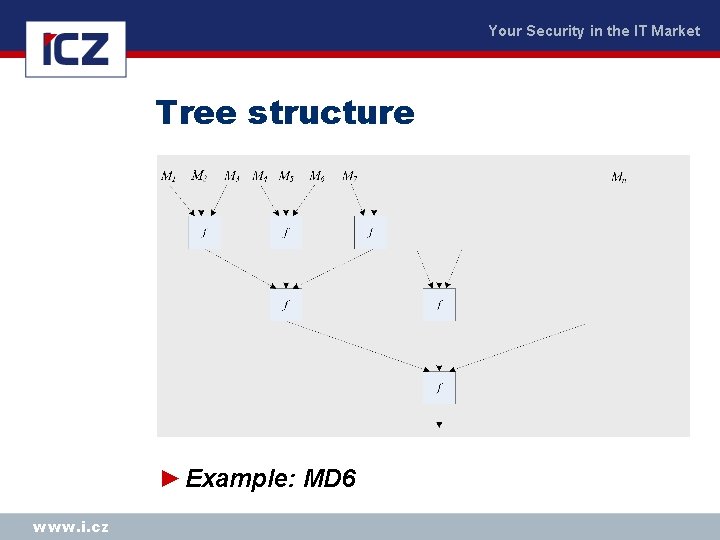
Your Security in the IT Market Tree structure ► Example: MD 6 www. i. cz

Your Security in the IT Market Sponge structure ► Absorbing ● ● ● Initialize state XOR some of the message to the state Apply compression function XOR some more of the message into the state Apply compression function… ► Squeezing ● ● ● Apply compression function Extract some output Apply compression function … ► Examples: Keccak, Luffa. www. i. cz

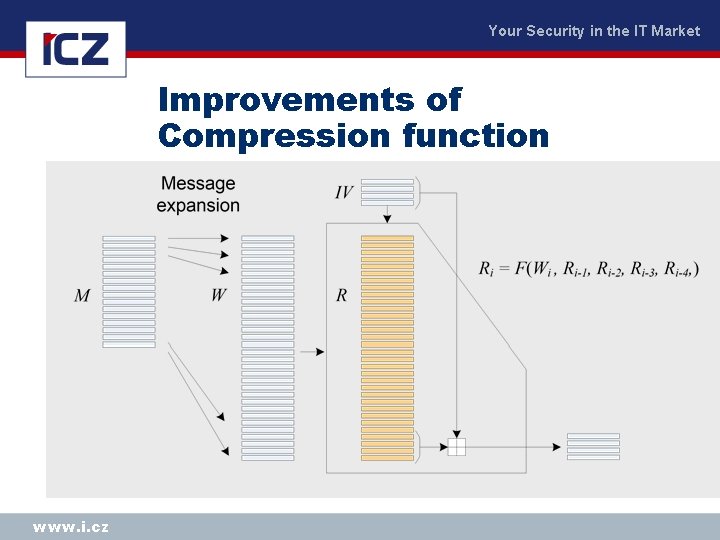
Your Security in the IT Market Improvements of Compression function www. i. cz

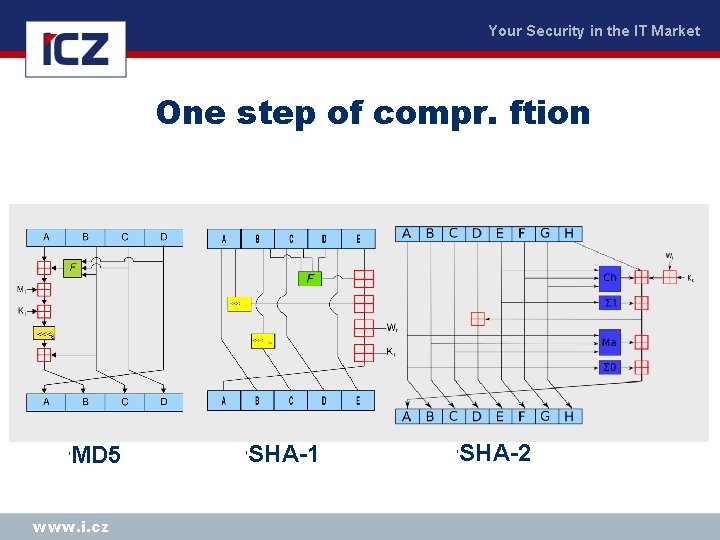
Your Security in the IT Market One step of compr. ftion ‘ MD 5 www. i. cz ‘ SHA-1 ‘ SHA-2

Your Security in the IT Market Feedback Shift Register ► Pros: efficiency in HW, known theory from stream ciphers, easy to implement ► Cons: SW implementation, stream cipher weaknesses ► Examples: MD 6, Shabal, Essence, Na. SHA www. i. cz

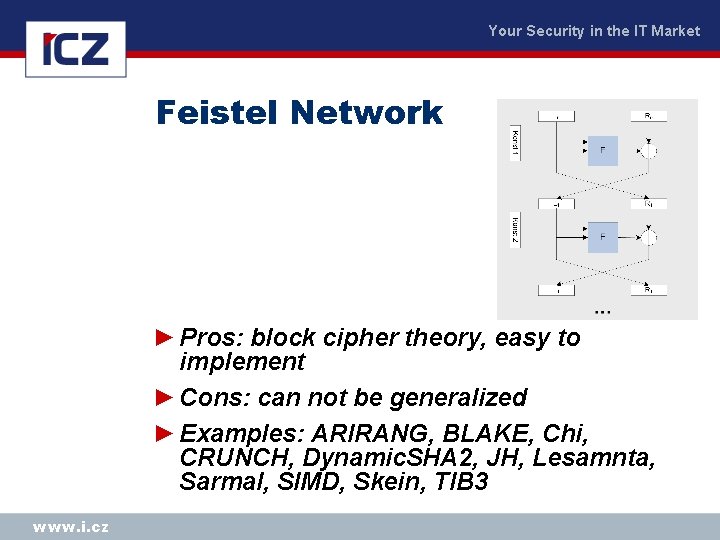
Your Security in the IT Market Feistel Network ► Pros: block cipher theory, easy to implement ► Cons: can not be generalized ► Examples: ARIRANG, BLAKE, Chi, CRUNCH, Dynamic. SHA 2, JH, Lesamnta, Sarmal, SIMD, Skein, TIB 3 www. i. cz

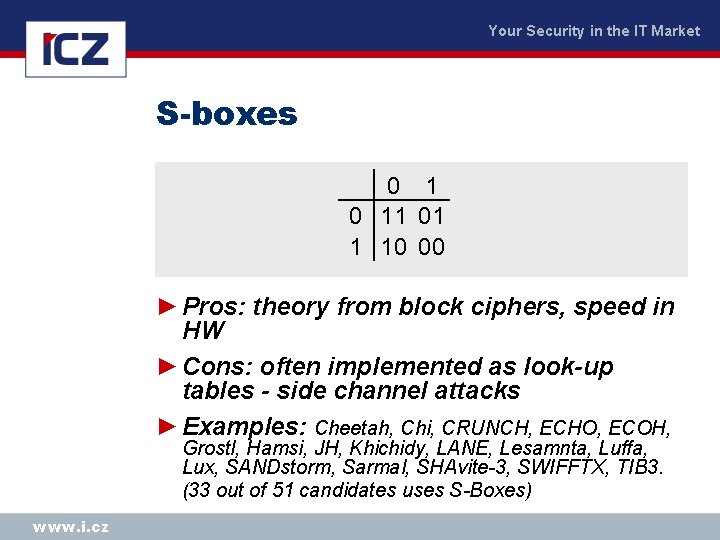
Your Security in the IT Market S-boxes 0 11 01 1 10 00 ► Pros: theory from block ciphers, speed in HW ► Cons: often implemented as look-up tables - side channel attacks ► Examples: Cheetah, Chi, CRUNCH, ECHO, ECOH, Grostl, Hamsi, JH, Khichidy, LANE, Lesamnta, Luffa, Lux, SANDstorm, Sarmal, SHAvite-3, SWIFFTX, TIB 3. (33 out of 51 candidates uses S-Boxes) www. i. cz

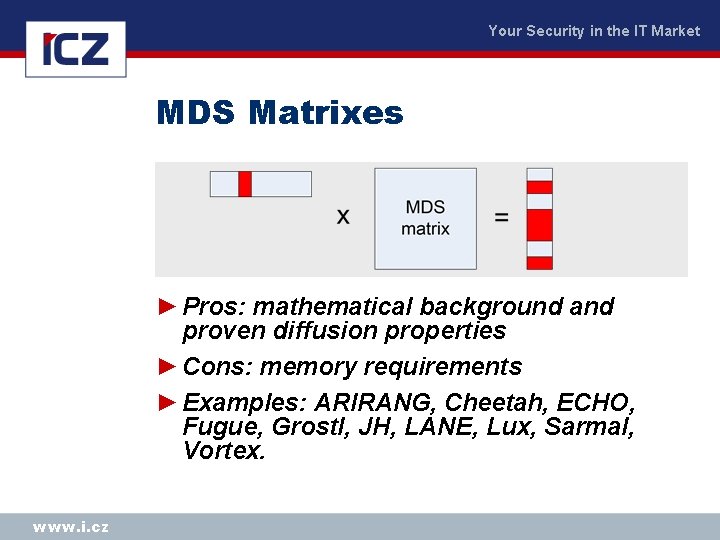
Your Security in the IT Market MDS Matrixes ► Pros: mathematical background and proven diffusion properties ► Cons: memory requirements ► Examples: ARIRANG, Cheetah, ECHO, Fugue, Grostl, JH, LANE, Lux, Sarmal, Vortex. www. i. cz

Your Security in the IT Market Where to look at candidates: ► NIST webpage: http: //csrc. nist. gov/groups/ST/hash/sha 3/index. html ► Hash ZOO http: //ehash. iaik. tugraz. at/index. php? title= The_SHA-3_Zoo&oldid=3106 ► Ebash http: //bench. cr. yp. to/resultshash. html ► Classification of the SHA-3 Candidates Cryptology e. Print Archive: Report 511/2008, http: //eprint. iacr. org/ www. i. cz

Your Security in the IT Market Conclusion ► Do not use MD 5, MD 4, MD 2 ► SHA-1 is not recommended after 2009 ► Use SHA-2 instead (no weaknesses) or ► SHA-3 standard is coming in 2 -3 years ► Cryptanalysis of current submissions is expected ► Second round candidates coming soon (june-august 2009, 15(? ) algorithms) www. i. cz

Your Security in the IT Market Thank you for your attention. Daniel Joščák daniel. joscak@i. cz +420 724 429 248 S. ICZ a. s. www. i. cz MFF UK, Dept. of Algebra www. i. cz