Differential Cryptanalysis Richard Newman Differential Cryptanalysis Takes inputs

![Simple-DES (S-DES) IP: [1. . 8] → [2 6 3 1 4 8 5 Simple-DES (S-DES) IP: [1. . 8] → [2 6 3 1 4 8 5](https://slidetodoc.com/presentation_image_h2/0e107d0da4e70073a15b5866b0a2e132/image-5.jpg)
![Simple-DES (S-DES) Key generation: 10 -bit key is first permuted PC-1: [1. . 10] Simple-DES (S-DES) Key generation: 10 -bit key is first permuted PC-1: [1. . 10]](https://slidetodoc.com/presentation_image_h2/0e107d0da4e70073a15b5866b0a2e132/image-6.jpg)





- Slides: 23

Differential Cryptanalysis Richard Newman

Differential Cryptanalysis Takes inputs with known difference (XOR) Predicts XOR of corresponding outputs, based on structure of cipher When input pair – output pair are found that have the predicted differences, assume internal states follow predictions also Work backwards to find subkeys that would produce observed pairs, each gets a vote Most popular subkeys collected Bits that agree amongst subkeys are “known”

Differential Cryptanalysis A function f is linear if f(x+y) = f(x) + f(y) A cipher is linear if given any two inputs p 1 and p 2, and their corresponding outputs c 1 and c 2, we have c 1 XOR c 2 = p 1 XOR p 2. Onetime pad is linear: E(p 1+p 2) = E(p 1)+E(p 2) DES is not linear (and neither are S-boxes) Non-linearity and effect of (sub-) key on output suggests that information about the (sub-) key can be discovered by examining the relationship between input deltas and output deltas

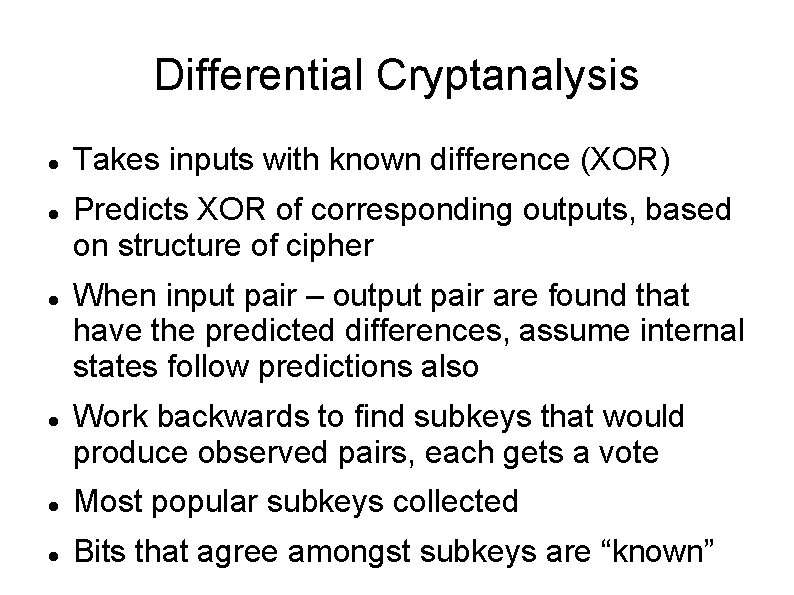
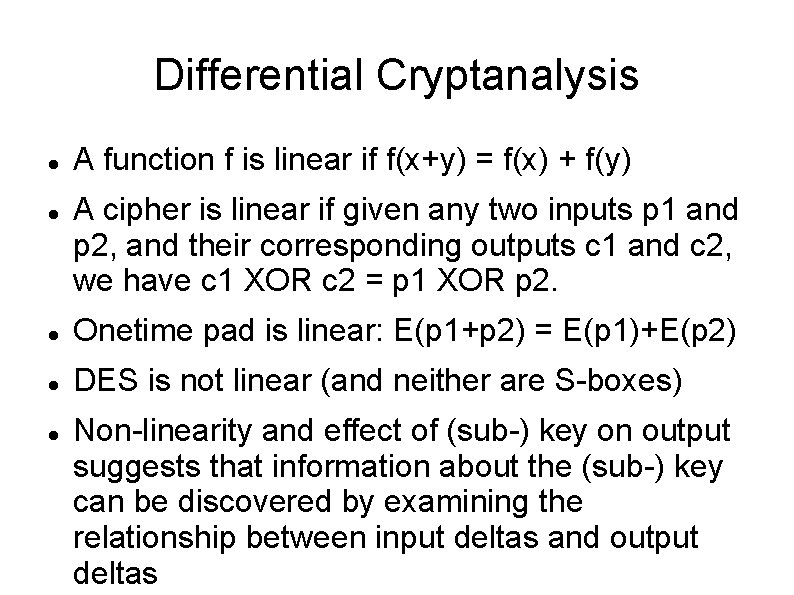
Simple-DES (S-DES) Invented by Shaefer 1996 as tool Operates on 8 -bit blocks Uses 10 - bit key Has two rounds Rest is similar to DES: IP, EP, S-boxes, P-box, Feistel structure, sub-key generation
![SimpleDES SDES IP 1 8 2 6 3 1 4 8 5 Simple-DES (S-DES) IP: [1. . 8] → [2 6 3 1 4 8 5](https://slidetodoc.com/presentation_image_h2/0e107d0da4e70073a15b5866b0a2e132/image-5.jpg)
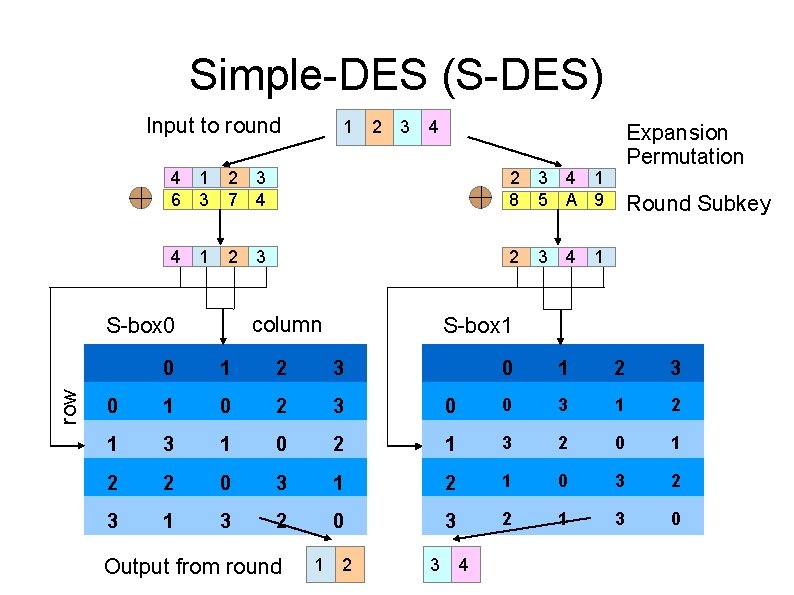
Simple-DES (S-DES) IP: [1. . 8] → [2 6 3 1 4 8 5 7] IP-1: [1. . 8] → [4 1 3 5 7 2 8 6] EP: [1 2 3 4] → [4 1 2 3 4 1] 8 -bit subkey XORed with EP output First 4 bits to S-box S 0, last 4 to S 1 First and last bits to S-box pick row (1 of 4) Middle two bits pick column, output is 2 bits P-box: [1. . 4] → [2 4 3 1]
![SimpleDES SDES Key generation 10 bit key is first permuted PC1 1 10 Simple-DES (S-DES) Key generation: 10 -bit key is first permuted PC-1: [1. . 10]](https://slidetodoc.com/presentation_image_h2/0e107d0da4e70073a15b5866b0a2e132/image-6.jpg)
Simple-DES (S-DES) Key generation: 10 -bit key is first permuted PC-1: [1. . 10] → [3 5 2 7 4 10 1 9 8 6] Permuted key split into two 5 -bit halves Each half shifted left one bit in first round, shifted twice more for second round PC-2: [1. . 10] → [6 3 7 4 8 5 10 9] (8 bits) Subkey is XORed with EP output in round

Simple-DES (S-DES) Input to round 2 3 4 4 1 6 3 2 3 7 4 2 3 4 1 8 5 A 9 4 1 2 2 3 column S-box 0 row 1 3 Expansion Permutation Round Subkey 4 1 S-box 1 0 1 2 3 0 1 0 2 3 0 0 3 1 2 1 3 1 0 2 1 3 2 0 1 2 2 0 3 1 2 1 0 3 2 3 1 3 2 0 3 2 1 3 0 Output from round 1 2 3 4

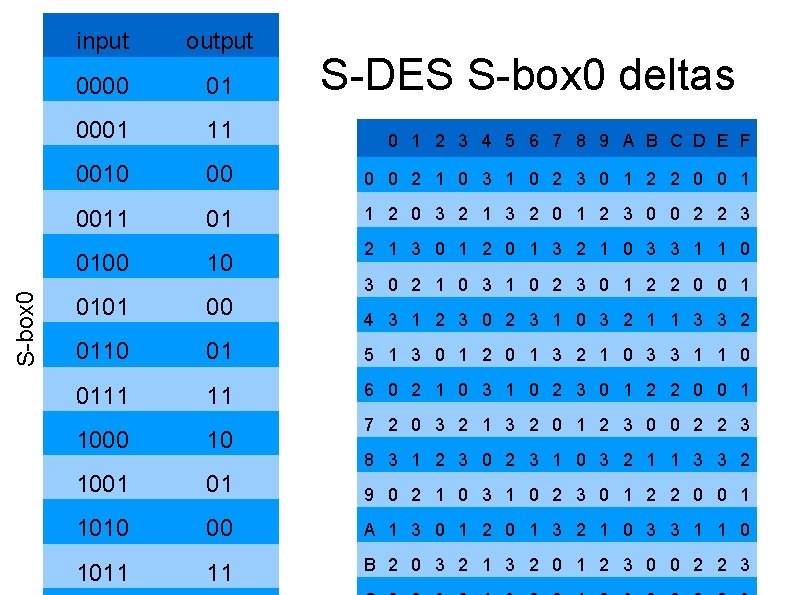
S-box 0 input output 0000 01 0001 11 0 1 2 3 4 5 6 7 8 9 A B C D E F 0010 00 0 0 2 1 0 3 1 0 2 3 0 1 2 2 0 0 1 0011 01 1 2 0 3 2 1 3 2 0 1 2 3 0 0 2 2 3 S-DES S-box 0 deltas 2 1 3 0 1 2 0 1 3 2 1 0 3 3 1 1 0 0100 10 0101 00 0110 01 5 1 3 0 1 2 0 1 3 2 1 0 3 3 1 1 0 0111 11 6 0 2 1 0 3 1 0 2 3 0 1 2 2 0 0 1 3 0 2 1 0 3 1 0 2 3 0 1 2 2 0 0 1 4 3 1 2 3 0 2 3 1 0 3 2 1 1 3 3 2 7 2 0 3 2 1 3 2 0 1 2 3 0 0 2 2 3 1000 10 1001 01 9 0 2 1 0 3 1 0 2 3 0 1 2 2 0 0 1 1010 00 A 1 3 0 1 2 0 1 3 2 1 0 3 3 1 1 0 1011 11 B 2 0 3 2 1 3 2 0 1 2 3 0 0 2 2 3 8 3 1 2 3 0 2 3 1 0 3 2 1 1 3 3 2

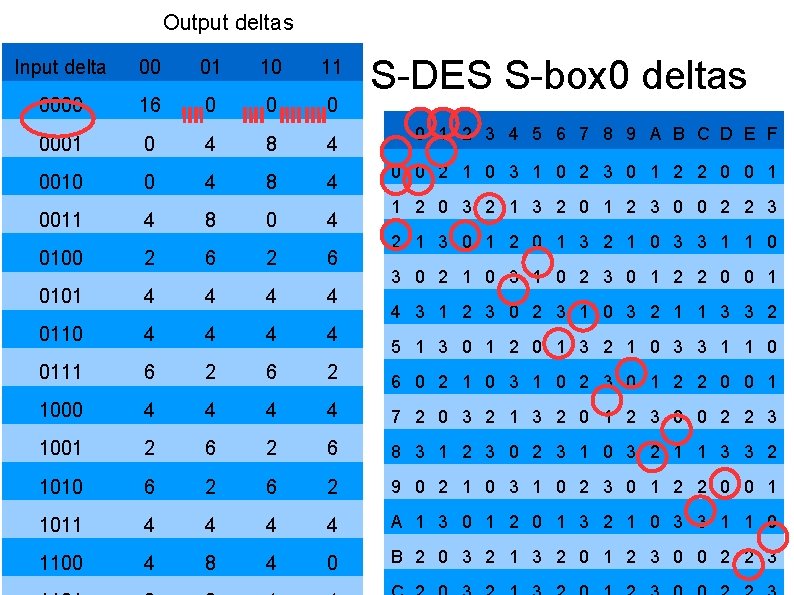
Output deltas Input delta 00 01 10 11 0000 16 0 0001 0 4 8 4 0010 0 4 8 4 0011 4 8 0 4 S-DES S-box 0 deltas 0 1 2 3 4 5 6 7 8 9 A B C D E F 0 0 2 1 0 3 1 0 2 3 0 1 2 2 0 0 1 1 2 0 3 2 1 3 2 0 1 2 3 0 0 2 2 3 2 1 3 0 1 2 0 1 3 2 1 0 3 3 1 1 0 0100 2 6 0101 4 4 0110 4 4 0111 6 2 6 0 2 1 0 3 1 0 2 3 0 1 2 2 0 0 1 1000 4 4 7 2 0 3 2 1 3 2 0 1 2 3 0 0 2 2 3 1001 2 6 8 3 1 2 3 0 2 3 1 0 3 2 1 1 3 3 2 1010 6 2 9 0 2 1 0 3 1 0 2 3 0 1 2 2 0 0 1 1011 4 4 A 1 3 0 1 2 0 1 3 2 1 0 3 3 1 1 0 1100 4 8 4 0 B 2 0 3 2 1 3 2 0 1 2 3 0 0 2 2 3 3 0 2 1 0 3 1 0 2 3 0 1 2 2 0 0 1 4 3 1 2 3 0 2 3 1 0 3 2 1 1 3 3 2 5 1 3 0 1 2 0 1 3 2 1 0 3 3 1 1 0

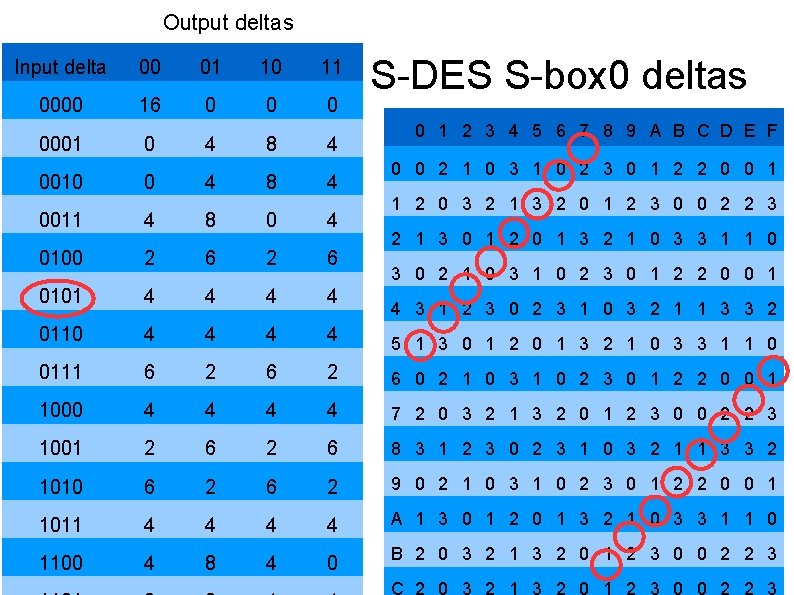
Output deltas Input delta 00 01 10 11 0000 16 0 0001 0 4 8 4 0010 0 4 8 4 S-DES S-box 0 deltas 0 1 2 3 4 5 6 7 8 9 A B C D E F 0 0 2 1 0 3 1 0 2 3 0 1 2 2 0 0 1 1 2 0 3 2 1 3 2 0 1 2 3 0 0 2 2 3 0011 4 8 0 4 0100 2 6 0101 4 4 0110 4 4 5 1 3 0 1 2 0 1 3 2 1 0 3 3 1 1 0 0111 6 2 6 0 2 1 0 3 1 0 2 3 0 1 2 2 0 0 1 1000 4 4 7 2 0 3 2 1 3 2 0 1 2 3 0 0 2 2 3 1001 2 6 8 3 1 2 3 0 2 3 1 0 3 2 1 1 3 3 2 1010 6 2 9 0 2 1 0 3 1 0 2 3 0 1 2 2 0 0 1 1011 4 4 A 1 3 0 1 2 0 1 3 2 1 0 3 3 1 1 0 1100 4 8 4 0 B 2 0 3 2 1 3 2 0 1 2 3 0 0 2 2 3 2 1 3 0 1 2 0 1 3 2 1 0 3 3 1 1 0 3 0 2 1 0 3 1 0 2 3 0 1 2 2 0 0 1 4 3 1 2 3 0 2 3 1 0 3 2 1 1 3 3 2

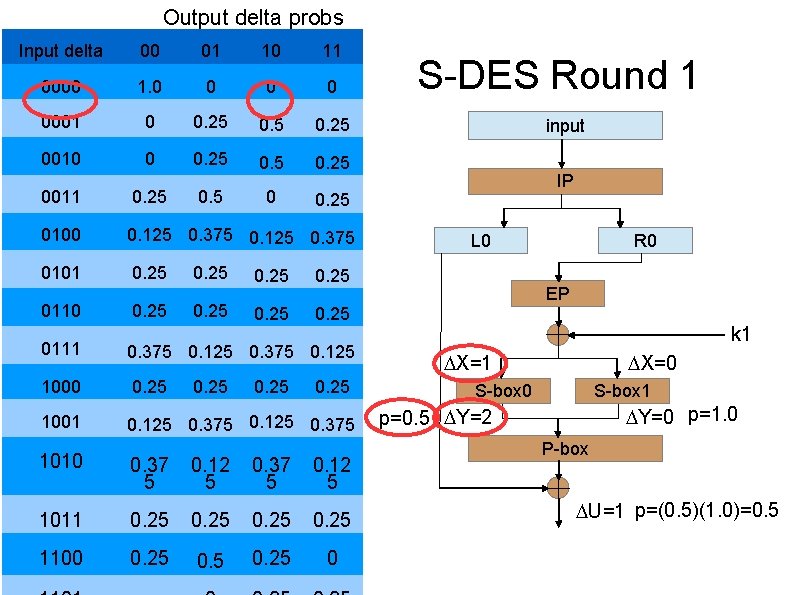
Output delta probs Input delta 00 01 10 11 0000 1. 0 0 0001 0 0. 25 0010 0 0. 25 0011 0. 25 0100 0. 125 0. 375 0101 0. 25 0110 0. 25 0111 0. 375 0. 125 1000 0. 25 1001 0. 125 0. 375 0. 25 1010 0. 37 5 0. 12 5 1011 0. 25 1100 0. 25 0 S-DES Round 1 input IP L 0 R 0 EP k 1 X=1 X=0 S-box 1 Y=0 p=1. 0 p=0. 5 Y=2 P-box U=1 p=(0. 5)(1. 0)=0. 5

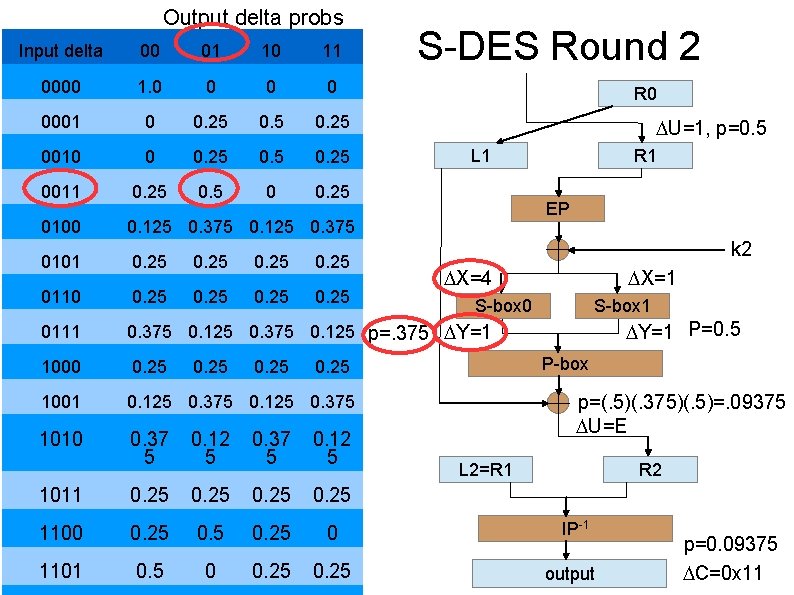
Output delta probs S-DES Round 2 Input delta 00 01 10 11 0000 1. 0 0 0001 0 0. 25 0010 0 0. 25 0011 0. 25 0. 5 0 0. 25 0100 0. 125 0. 375 0101 0. 25 0110 0. 25 0111 0. 375 0. 125 p=. 375 Y=1 1000 0. 25 1001 0. 125 0. 375 1010 0. 37 5 0. 12 5 1011 0. 25 1100 0. 25 0 1101 0. 5 0 0. 25 R 0 U=1, p=0. 5 L 1 R 1 EP k 2 X=4 X=1 S-box 0 S-box 1 Y=1 P=0. 5 P-box 0. 25 p=(. 5)(. 375)(. 5)=. 09375 U=E L 2=R 1 R 2 IP-1 output p=0. 09375 C=0 x 11

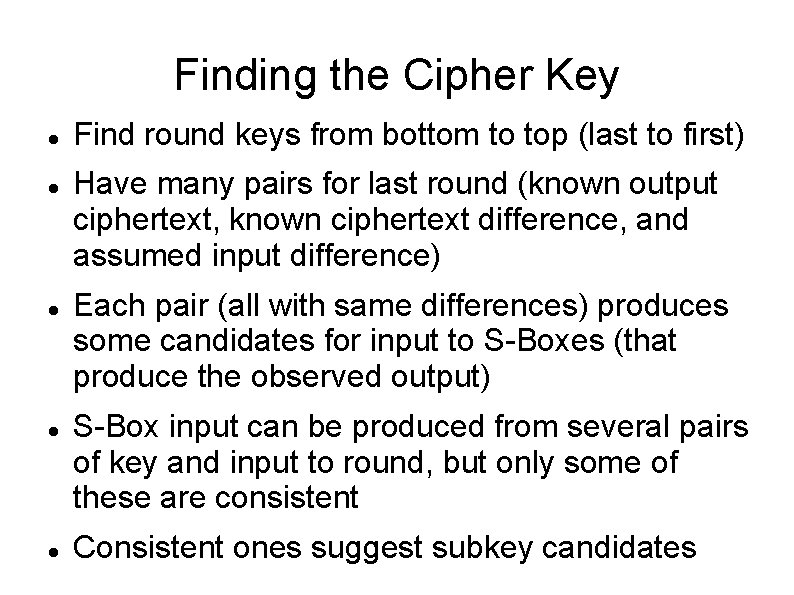
Finding the Cipher Key Find round keys from bottom to top (last to first) Have many pairs for last round (known output ciphertext, known ciphertext difference, and assumed input difference) Each pair (all with same differences) produces some candidates for input to S-Boxes (that produce the observed output) S-Box input can be produced from several pairs of key and input to round, but only some of these are consistent Consistent ones suggest subkey candidates

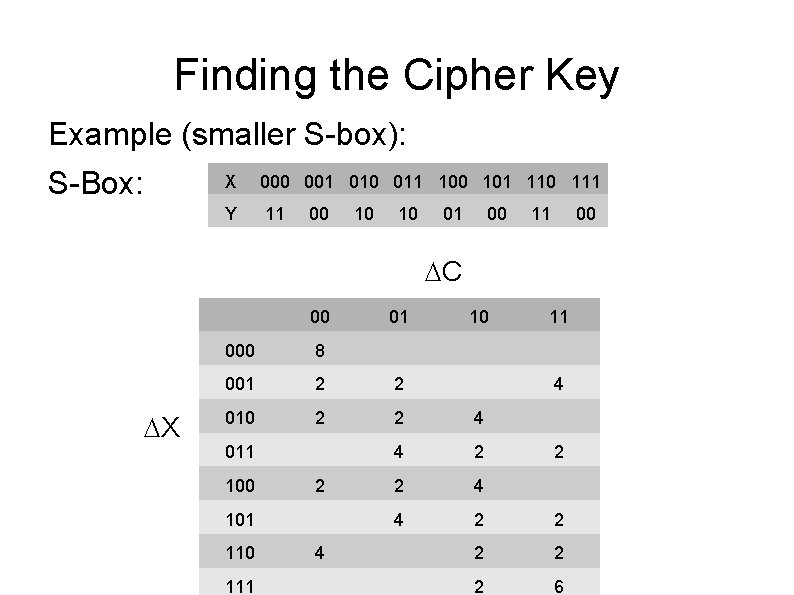
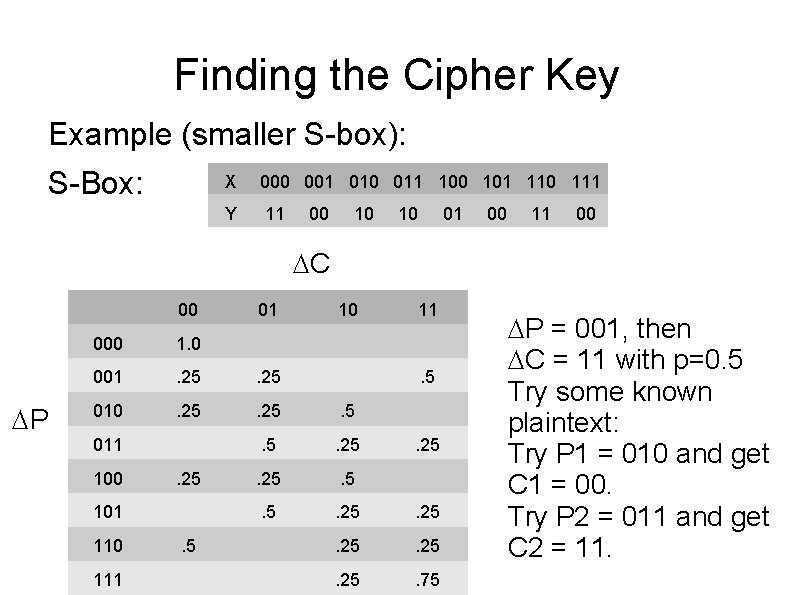
Finding the Cipher Key Example (smaller S-box): S-Box: X 000 001 010 011 100 101 110 111 Y 11 00 10 10 01 00 11 00 C 00 X 01 10 11 000 8 001 2 2 010 2 2 4 4 2 2 2 6 011 100 2 101 110 111 4 4 2

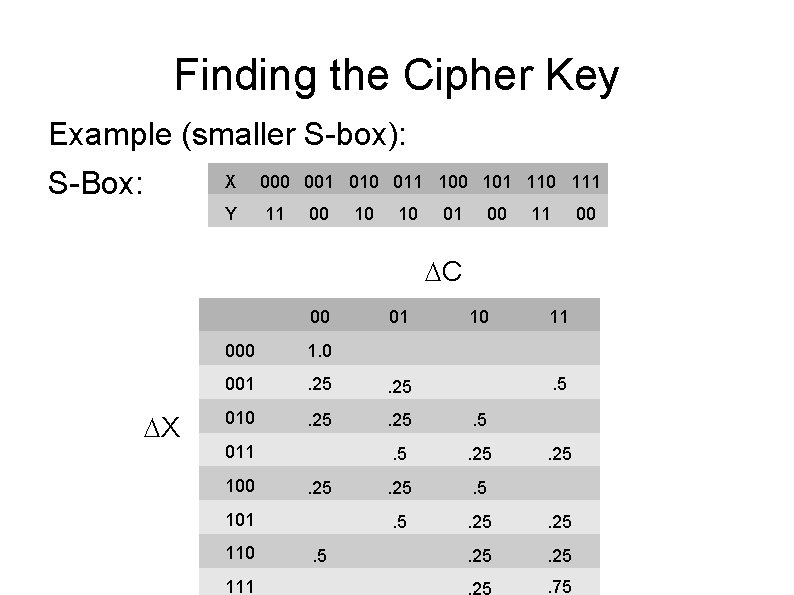
Finding the Cipher Key Example (smaller S-box): S-Box: X 000 001 010 011 100 101 110 111 Y 11 00 10 10 01 00 11 00 C 00 X 01 10 11 000 1. 0 001 . 25 010 . 25 . 5 . 5 . 25 011 100 . 25 101 110 111 . 5 . 25 . 75

Finding the Cipher Key Since X depends only on P, we do NOT have to know the key K ahead of time! Get a bunch of inputs with a known X Find those whose C is the high probability value (e. g. , X is 111 and C is 11) – Note that this actually has to be for as many rounds as the cipher uses, but here we will just illustrate with a single round

Finding the Cipher Key Example (smaller S-box): S-Box: X 000 001 010 011 100 101 110 111 Y 11 00 10 10 01 00 11 00 C 00 P 01 10 11 000 1. 0 001 . 25 010 . 25 . 5 . 5 . 25 . 75 011 100 . 25 101 110 111 . 5 . 25 P = 001, then C = 11 with p=0. 5 Try some known plaintext: Try P 1 = 010 and get C 1 = 00. Try P 2 = 011 and get C 2 = 11.

Finding the Cipher Key From the plaintext-ciphertext pairs, and the known (and desired) deltas, Figure which inputs after XORing with key produce desired output Then for each of these, determine what the key would have to be for that plaintext

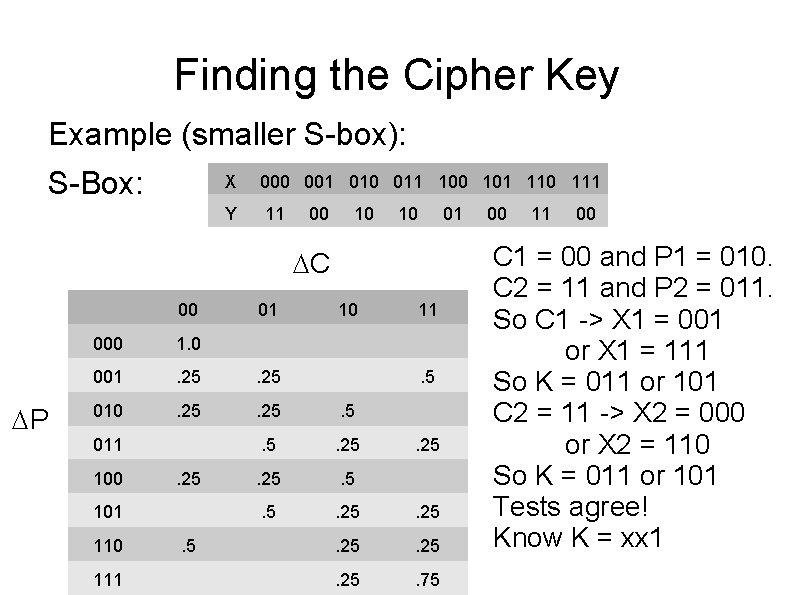
Finding the Cipher Key Example (smaller S-box): S-Box: X 000 001 010 011 100 101 110 111 Y 11 00 10 10 01 C 00 P 01 10 11 000 1. 0 001 . 25 010 . 25 . 5 . 5 . 25 . 75 011 100 . 25 101 110 111 . 5 . 25 00 11 00 C 1 = 00 and P 1 = 010. C 2 = 11 and P 2 = 011. So C 1 -> X 1 = 001 or X 1 = 111 So K = 011 or 101 C 2 = 11 -> X 2 = 000 or X 2 = 110 So K = 011 or 101 Tests agree! Know K = xx 1

Finding the Cipher Key From the plaintext-ciphertext pairs, and the known (and desired) deltas, From all the pairs, get the most popular key or keys, assume the actual key is one of these If only one very popular, assume that is the key and try to confirm it on other plaintext-ciphertext pairs If multiple popular keys, look for the bits they have in common, and assume that these are correct Then brute force the rest

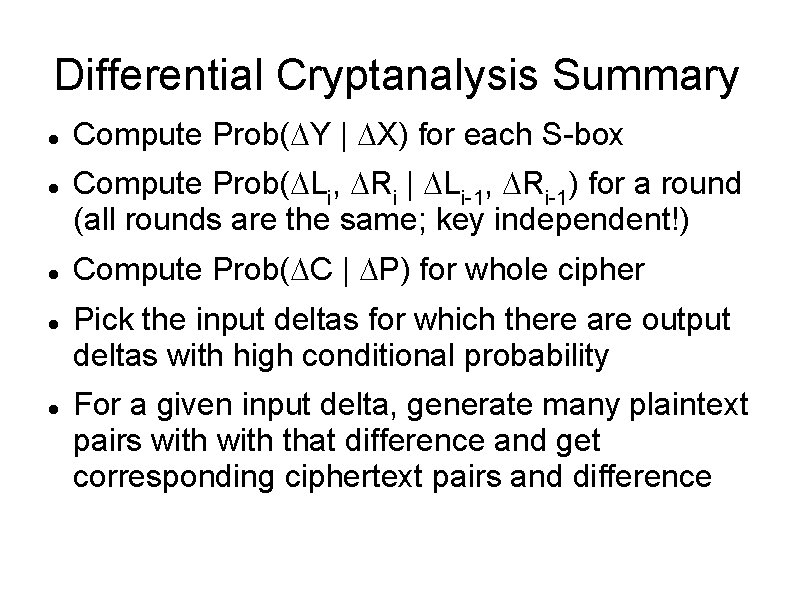
Differential Cryptanalysis Summary Compute Prob( Y | X) for each S-box Compute Prob( Li, Ri | Li-1, Ri-1) for a round (all rounds are the same; key independent!) Compute Prob( C | P) for whole cipher Pick the input deltas for which there are output deltas with high conditional probability For a given input delta, generate many plaintext pairs with that difference and get corresponding ciphertext pairs and difference

Differential Cryptanalysis Summary For each plaintext pair whose ciphertext pair produces the highest probability ciphertext difference, assume internal states are as computed (maximum likelihood) For a given “good” ciphertext pair, run the invertable computations backwards to get the outputs of the last set of S-boxes, Yi' For each of these output pairs, find the set of inputs that will produce that pair (there may be many of these)

Differential Cryptanalysis Summary Save each pair of possible inputs that can produce the known outputs For each of these saved pairs, determine the subkey that will produce the assumed difference for each input pair Take the most popular keys and determine bits where the keys agree in all sets Assume these bits are known, guess the rest