Dynamic Spectrum Access Security Issues Timothy R Newman











- Slides: 32

Dynamic Spectrum Access Security Issues Timothy R. Newman, Ph. D. Virginia Tech

Dynamic Spectrum Access �What is DSA? �Dynamically changing channel in response to environmental stimuli �Why do we want DSA? �Commercial: Inefficient spectrum usage �Military: Ease spectrum management tasks avoid jamming

DSA Current State �Where is DSA technology currently at? �DARPA XG radio program has come and gone � WNa. N program now pushing SOME development � No REAL deployment of these radios yet �Commercial companies now involved � Microsoft, Google, Dell HP, Intel, Philips, Samsung, …. � First “white space” network in Oct. 2009, Claudville, VA. � No adaptation but it’s a first step �Estimate at least 7 -9 solid prototype DSA systems exist

DSA Current State �Where is DSA technology currently at? (cont. . ) �Majority of the current prototype devices using energy detection techniques for signal detection �Final consensus – TRL 6 �What’s next for DSA? �Army purchase WNa. N radios for deployment? �SSC integrating DSA technology with ARGON’s Hy. NET wireless mesh network system (US Army) �Ultimate white space network deployed for WORLDWIDE broadband access!!!

Cognitive Radio and DSA Security �CR security is slowly coming into focus for academia and industry �SDR Forum session devoted to CR/SDR security �Publications with CR/SDR security topics are on the rise �Two DARPA programs on CR/SDR security proposed �Security research for CR/SDR is still largely overlooked �XG program had NO output related to security of DSA protocols �None of the current prototypes have any DSA specific security features

DSA Radio Security Analysis �What are the primary DSA security issues? �Primary User Emulation � Spoofing the intended primary user �Spectral Honey Pot threats � Forcing the victim DSA radio to operate on a specific channel �DSA Do. S threats � “I can sense and hop faster than you!”– PHY level threat � LPD jamming – Waveform level threat

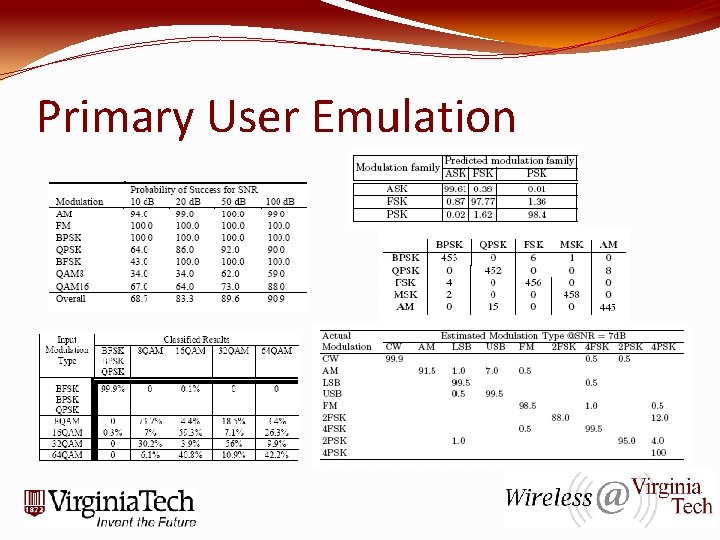
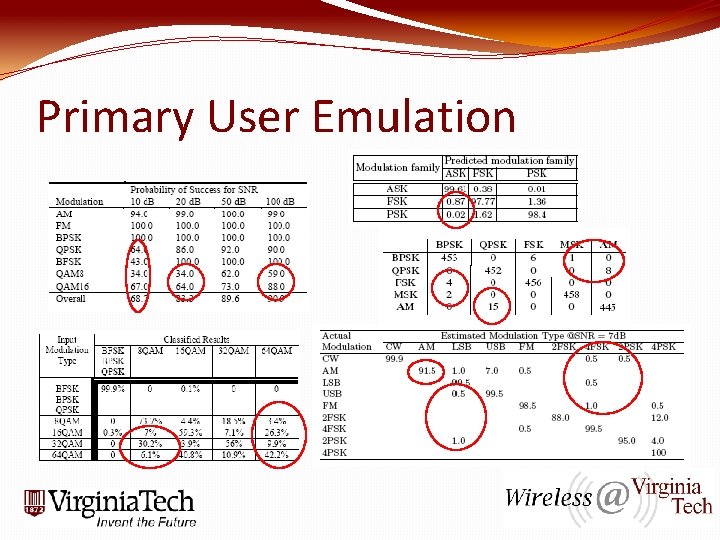
Primary User Emulation �PUE threat is the baseline for many other DSA related attacks �Once you can manipulate the radio the floodgates are open, you’ve got root!! �Classifiers and Detectors are all over and have been for a long time �DSA brings a new twist – Detection/Classification affects communication parameters �Energy Detection is usually “settled” for to gain low complexity and processing speed �Problem now: Any error is a possible hole

Primary User Emulation

Primary User Emulation

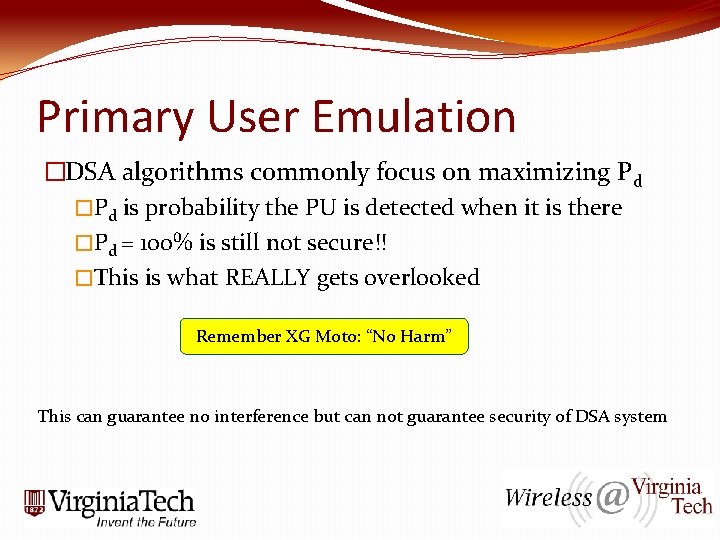
Primary User Emulation �DSA algorithms commonly focus on maximizing Pd �Pd is probability the PU is detected when it is there �Pd = 100% is still not secure!! �This is what REALLY gets overlooked Remember XG Moto: “No Harm” This can guarantee no interference but can not guarantee security of DSA system

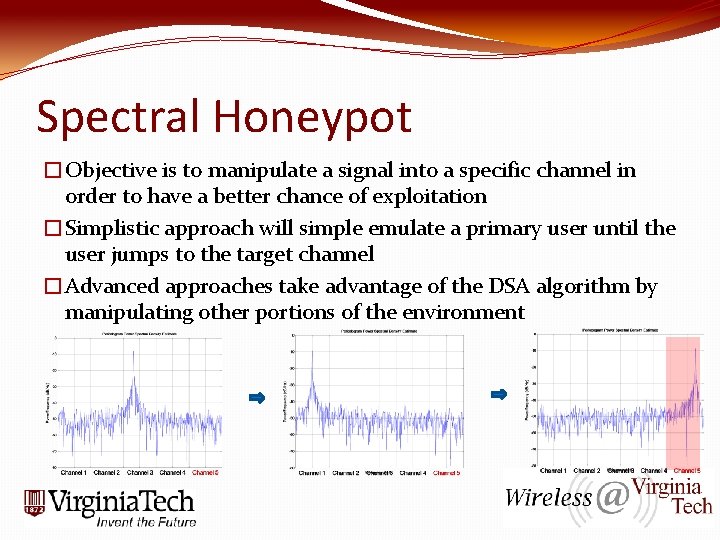
Spectral Honeypot �Objective is to manipulate a signal into a specific channel in order to have a better chance of exploitation �Simplistic approach will simple emulate a primary user until the user jumps to the target channel �Advanced approaches take advantage of the DSA algorithm by manipulating other portions of the environment

DSA Denial of Service �Straightforward DSA Do. S – Sense and Hop faster than the receivers �DSA radio networks must rendezvous on another channel if a PU appears �What if a PU appears before network can rendezvous? �Waveform level �Commonly DSA algorithm interleave the sensing and communication �Synchronize and jam only the communication time blocks

Analyzing a Real Radio! �Shared Spectrum DSA 2100 – Wi. MAX DSA Radio �Phase 3 contractor for DARPA XG Program �Interesting Radio Characteristics �Wavesat chipset: 802. 16 -2004 �Agility - 138 MHz – 3 GHz �Bandwidth - 1. 75 MHz, 3. 5 MHz, or 7 MHz �Tuning speed – 300 μs �TX spur level - -60 d. Bc �DSA Channel Selection Algorithms �Least occupied �Least energy �Random

Analyzing a Real Radio! �DSA Specific Parameters �Co-channel sample rate: 10 Hz �Non-occupancy period: 5 sec �Detection Algorithm: Energy detection �Freq. Range for analysis: 350 – 450 MHz, 400 – 480 MHz ** Non-occupancy period – Time a channel should be “blocked out” if a PU signal is detected

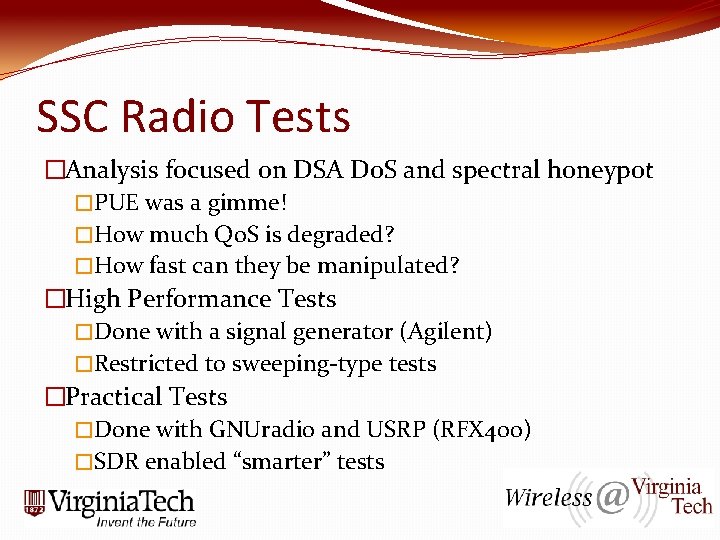
SSC Radio Tests �Analysis focused on DSA Do. S and spectral honeypot �PUE was a gimme! �How much Qo. S is degraded? �How fast can they be manipulated? �High Performance Tests �Done with a signal generator (Agilent) �Restricted to sweeping-type tests �Practical Tests �Done with GNUradio and USRP (RFX 400) �SDR enabled “smarter” tests

DSA Denial of Service �DSA Do. S = Never able to rendezvous �Signal generator parameters �Pulse sweep time - Amount of time pulse dwells in a channel before going to channel + 1 �Signal Power – Is the detection threshold really enforced? �Channel Step Size – 1 MHz (2 MHz probably would’ve been better)

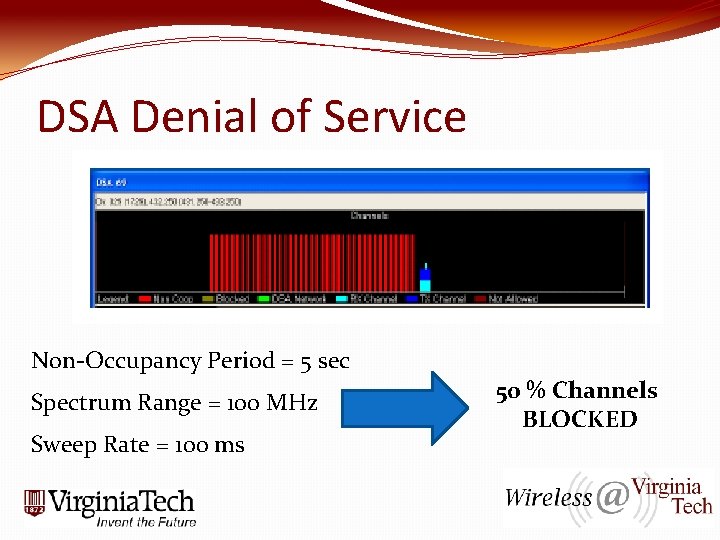
DSA Denial of Service Non-Occupancy Period = 5 sec Spectrum Range = 100 MHz Sweep Rate = 100 ms 50 % Channels BLOCKED

DSA Denial of Service �Adding a bit of intelligence (sensing) �Using GNUradio we can easily put together a waveform that can sense the location of the signal and send a pulse �Pulse power only needs to be just above detection threshold �What happens if DSA radio ALWAYS sees a PU?

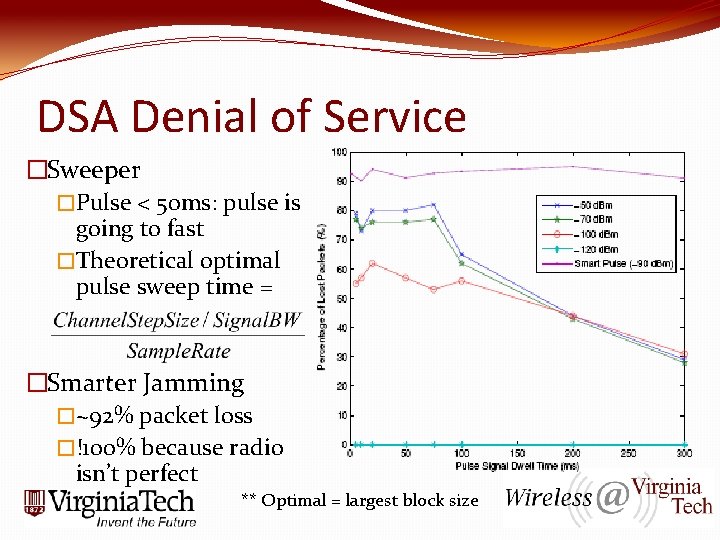
DSA Denial of Service �Sweeper �Pulse < 50 ms: pulse is going to fast �Theoretical optimal pulse sweep time = �Smarter Jamming �~92% packet loss �!100% because radio isn’t perfect ** Optimal = largest block size

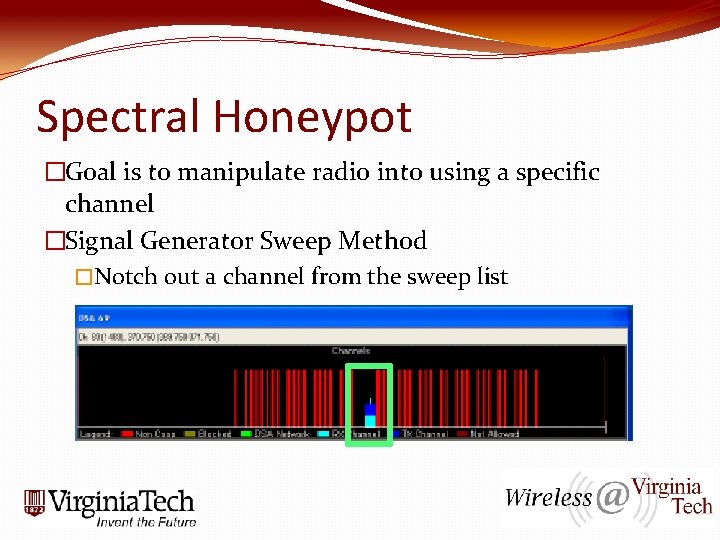
Spectral Honeypot �Goal is to manipulate radio into using a specific channel �Signal Generator Sweep Method �Notch out a channel from the sweep list

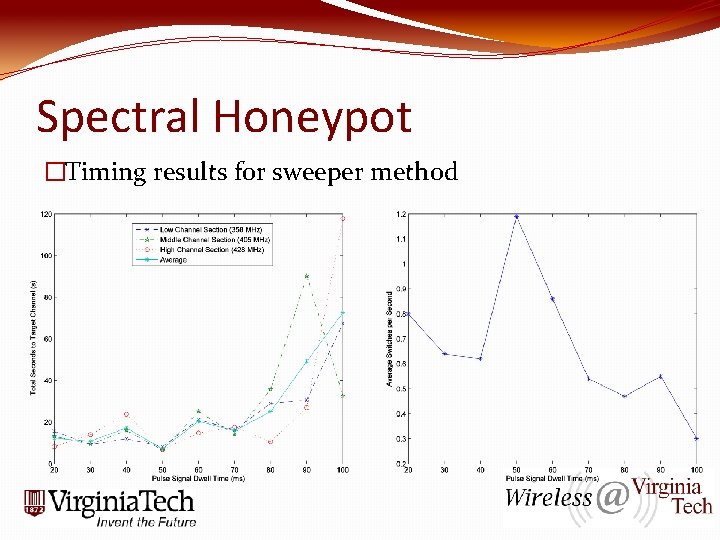
Spectral Honeypot �Timing results for sweeper method

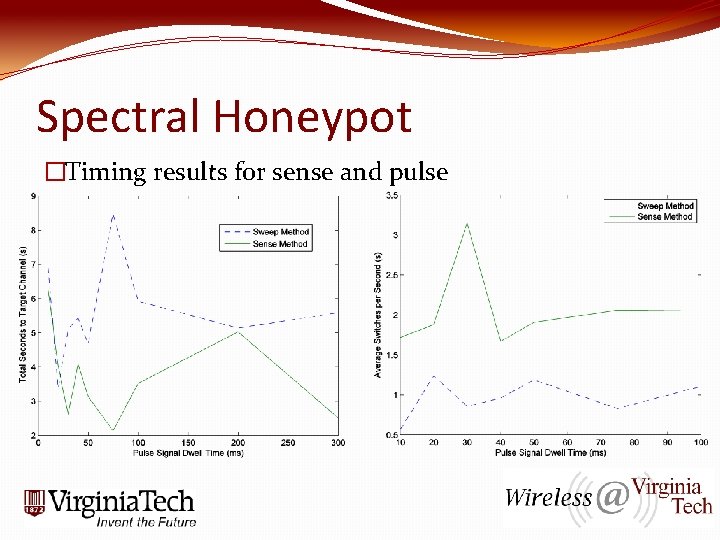
Spectral Honeypot �Timing results for sense and pulse

Security Analysis - Take Aways �What do we get from this analysis? �Motto of this specific DSA technology is “No Harm” � Focus is on existing systems Qo. S, not their own �No Harm to existing systems may mean ZERO communication for the DSA radios �Manipulation is possible when radios use an unauthenticated environment when making decisions �Non-occupancy period is a critical hole

DSA Security Mitigation �Primary User Emulation Denial �Signal Detection != Signal Classification � Robust classification is the objective � Unique feature selection is critical �Embed signatures � Watermarking techniques �Non-Occupancy Period �Randomize in order to create “holes” in the jamming block �Embedding “common sense” �Integrate security cognition into the system to filter for obvious malicious acts

Future Generation of CR Threats �Cognitive Radio technology is adding more autonomous operating into the wireless device �Increased exposure to possible threats �Threats to this technology is analogous to social networking attacks rather than traditional network attacks �Sensory Manipulation (DSA) �Belief Manipulation (Learning Attacks) �Cognitive Radio Viruses (Learning Network Attacks) �ETA until radios are using advanced AI: long…

Other SDR/CR related items at VT

Cognitive Radio Network Testbed �Defense University Research Instrumentation Program (DURIP) grant for CR testbed equipment. �Physical testbed deployed throughout a new campus building �Total size of testbed is 48 nodes � 12 nodes per floor �No restrictions on other wireless systems inside building �Reservation System for Nodes

CR Testbed Hardware Custom RF Daughterboard Host PC Servers � Motorola RFIC 4 � 100 MHz – 4 GHz � 20 MHz instantaneous bw � Highly variable receive gain � 25 d. B – 50 d. B � Multiple TX (3) and RX (5) paths � Sideband Rejection � 40 d. B - 60 d. B �Intel Xeon Quadcore 2. 13 GHz � 6 GB RAM, Gigabit Ethernet �Upgradable to Intel Nehalem for future �Much different from existing testbeds

Cognitive Radio Network Testbed �Current Testbed Status � 5 PC nodes with USRP and RFX 400 daughterboard �Power and network installed throughout building �Server’s are racked and ready �Waiting on USRP 2’s to be delivered �Management back-end is being developed

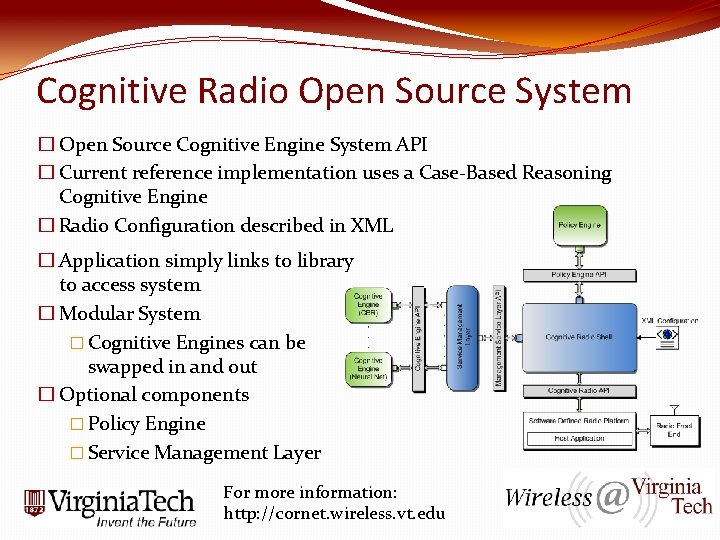
Cognitive Radio Open Source System � Open Source Cognitive Engine System API � Current reference implementation uses a Case-Based Reasoning Cognitive Engine � Radio Configuration described in XML � Application simply links to library to access system � Modular System � Cognitive Engines can be swapped in and out � Optional components � Policy Engine � Service Management Layer For more information: http: //cornet. wireless. vt. edu

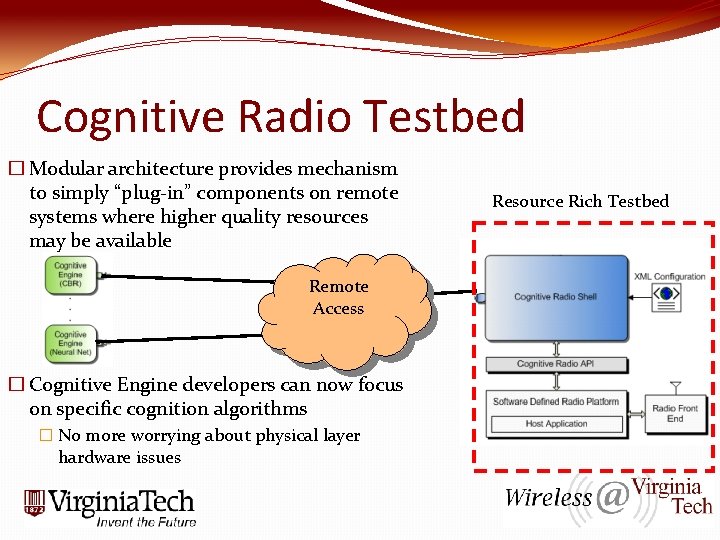
Cognitive Radio Testbed � Modular architecture provides mechanism to simply “plug-in” components on remote systems where higher quality resources may be available Remote Access � Cognitive Engine developers can now focus on specific cognition algorithms � No more worrying about physical layer hardware issues Resource Rich Testbed

Cognitive Radio Open Source System � Integrated into both OSSIE and GNUradio for intelligent control of waveforms and applications � Demonstrated DSA application with “hot-swappable” cognitive engine � Service Management Layer component provides the service oriented architecture support � Manages services and capabilities provided to the cognitive radio by components � Translates radio missions into operations and instructions for CROSS components � Mission 1: Jam all enemy signals � Mission 2: Covert Jam Signals � Detect signals � Signal Classifications � Enemy using Wifi? � Optimize Power for jamming � Detect wifi channel � Jam signal � Jam Wifi � Monitor for resurgence on multiple channels