Classical Cryptography 2 Cryptanalysis Cryptanalysis n 2 Cryptanalysis

![Cryptanalysis n [2] Cryptanalysis n n Assumption: (Kerckhoffs’ principle) The opponent knows the cryptosystem Cryptanalysis n [2] Cryptanalysis n n Assumption: (Kerckhoffs’ principle) The opponent knows the cryptosystem](https://slidetodoc.com/presentation_image_h2/46e8bd6a994408dc85590eadbf37cd8c/image-2.jpg)









- Slides: 32

Classical Cryptography 2. Cryptanalysis
![Cryptanalysis n 2 Cryptanalysis n n Assumption Kerckhoffs principle The opponent knows the cryptosystem Cryptanalysis n [2] Cryptanalysis n n Assumption: (Kerckhoffs’ principle) The opponent knows the cryptosystem](https://slidetodoc.com/presentation_image_h2/46e8bd6a994408dc85590eadbf37cd8c/image-2.jpg)
Cryptanalysis n [2] Cryptanalysis n n Assumption: (Kerckhoffs’ principle) The opponent knows the cryptosystem being used Attack models: n ciphertext only attack n known plaintext attack n chosen ciphertext attack p 2.

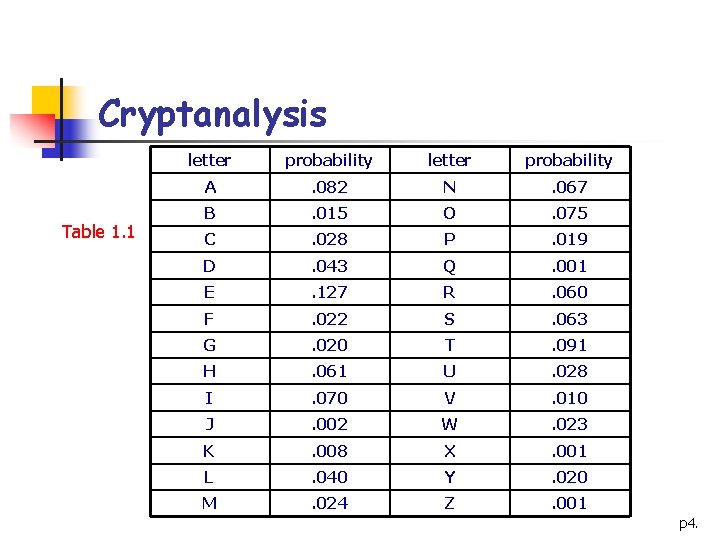
Cryptanalysis n n n Statistical properties of the English language: (see Table 1. 1) n E: probability about 0. 120 n T, A, O, I, N, S, H, R: between 0. 06 and 0. 09 n D, L: 0. 04 n C, U, M, W, F, G, Y, P, B: between 0. 015 and 0. 028 n V, K, J, X, Q, Z: 0. 01 Most common digrams: n TH, HE, IN, ER, AN, ND, … Most common trigrams: n THE, ING, AND, END, … p 3.

Cryptanalysis Table 1. 1 letter probability A . 082 N . 067 B . 015 O . 075 C . 028 P . 019 D . 043 Q . 001 E . 127 R . 060 F . 022 S . 063 G . 020 T . 091 H . 061 U . 028 I . 070 V . 010 J . 002 W . 023 K . 008 X . 001 L . 040 Y . 020 M . 024 Z . 001 p 4.

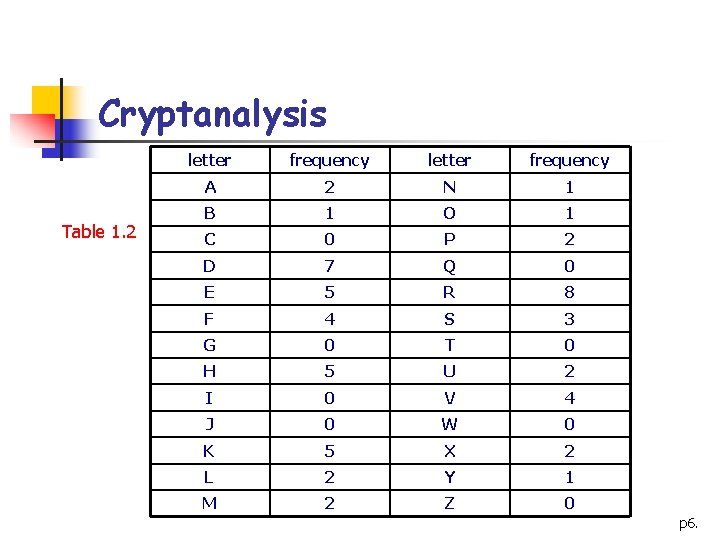
Cryptanalysis n <1> Cryptanalysis of the Affine Cipher n Ciphertext obtained form an Affine Cipher: n FMXVEDKAPHFERBNDKRXRSREFMORUDSDKDVSH VUFEDKAPRKDLYEVLRHHRH n Frequency analysis: Table 1. 2 n Most frequent ciphertext characters: n R: 8 occurrences n D: 7 occurrences n E, H, K: 5 occurrences n We now guess the mapping and solve the equation e. K(x)=ax+b mod 26 p 5.

Cryptanalysis Table 1. 2 letter frequency A 2 N 1 B 1 O 1 C 0 P 2 D 7 Q 0 E 5 R 8 F 4 S 3 G 0 T 0 H 5 U 2 I 0 V 4 J 0 W 0 K 5 X 2 L 2 Y 1 M 2 Z 0 p 6.

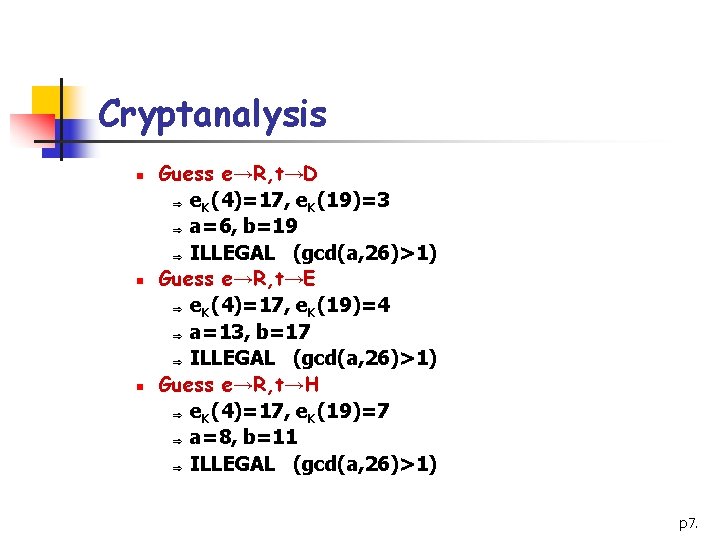
Cryptanalysis n n n Guess e→R, t→D Þ e. K(4)=17, e. K(19)=3 Þ a=6, b=19 Þ ILLEGAL (gcd(a, 26)>1) Guess e→R, t→E Þ e. K(4)=17, e. K(19)=4 Þ a=13, b=17 Þ ILLEGAL (gcd(a, 26)>1) Guess e→R, t→H Þ e. K(4)=17, e. K(19)=7 Þ a=8, b=11 Þ ILLEGAL (gcd(a, 26)>1) p 7.

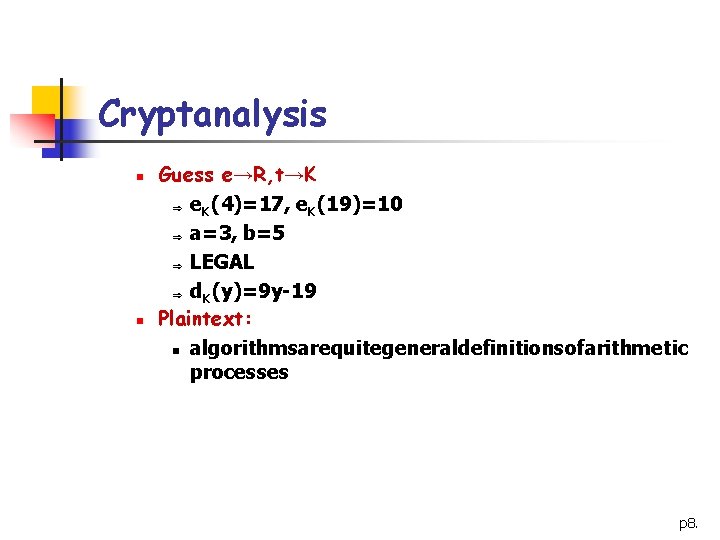
Cryptanalysis n n Guess e→R, t→K Þ e. K(4)=17, e. K(19)=10 Þ a=3, b=5 Þ LEGAL Þ d. K(y)=9 y-19 Plaintext: n algorithmsarequitegeneraldefinitionsofarithmetic processes p 8.

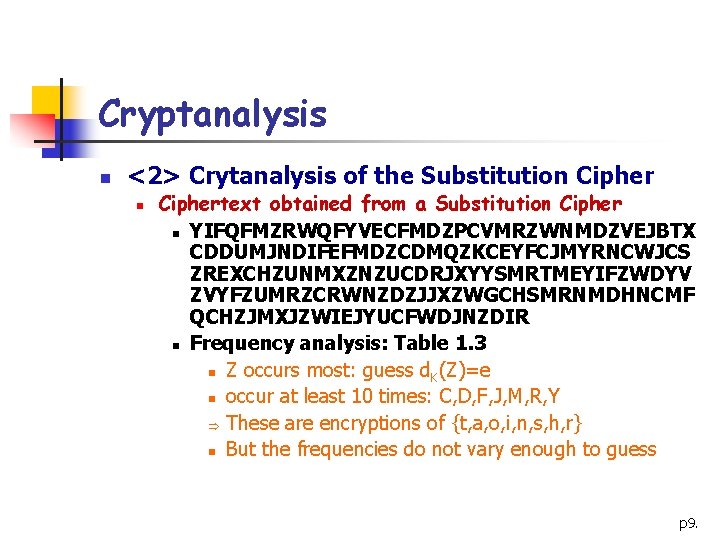
Cryptanalysis n <2> Crytanalysis of the Substitution Ciphertext obtained from a Substitution Cipher n YIFQFMZRWQFYVECFMDZPCVMRZWNMDZVEJBTX CDDUMJNDIFEFMDZCDMQZKCEYFCJMYRNCWJCS ZREXCHZUNMXZNZUCDRJXYYSMRTMEYIFZWDYV ZVYFZUMRZCRWNZDZJJXZWGCHSMRNMDHNCMF QCHZJMXJZWIEJYUCFWDJNZDIR n Frequency analysis: Table 1. 3 n Z occurs most: guess d. K(Z)=e n occur at least 10 times: C, D, F, J, M, R, Y Þ These are encryptions of {t, a, o, i, n, s, h, r} n But the frequencies do not vary enough to guess p 9.

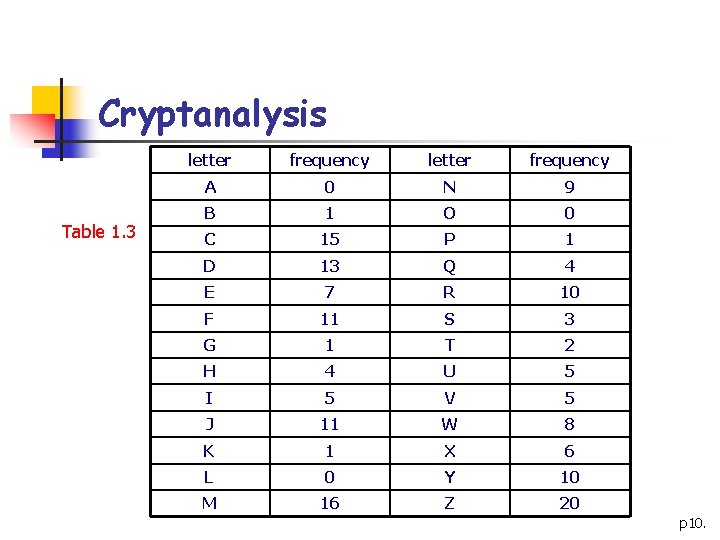
Cryptanalysis Table 1. 3 letter frequency A 0 N 9 B 1 O 0 C 15 P 1 D 13 Q 4 E 7 R 10 F 11 S 3 G 1 T 2 H 4 U 5 I 5 V 5 J 11 W 8 K 1 X 6 L 0 Y 10 M 16 Z 20 p 10.

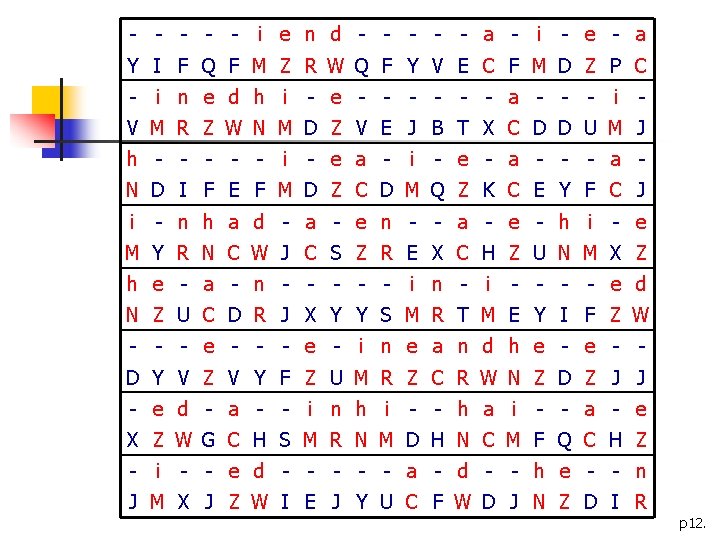
Cryptanalysis n n We now look at digrams: -Z or Zn 4 times: DZ, ZW n Guess d. K(W)=d: ed→ZW n 3 times: NZ, ZU n Guess dk(N)=h: he→NZ n We have ZRW: guess dk(R)=n, end→ZRW n We have CRW: guess dk(C)=a, and→CRW We have RNM, which decrypts to nhn Suggest h- begins a word: M should be a vowel n We have CM: guess dk(M)=i (ai is more likely than ao) p 11.

- - - i e n d - - - a - i - e - a Y I F Q F M Z R W Q F Y V E C F M D Z P C - i n e d h i - e - - - a - - - i V M R Z W N M D Z V E J B T X C D D U M J h - - - i - e a - i - e - a - - - a N D I F E F M D Z C D M Q Z K C E Y F C J i - n h a d - a - e n - - a - e - h i - e M Y R N C W J C S Z R E X C H Z U N M X Z h e - a - n - - - i n - i - - e d N Z U C D R J X Y Y S M R T M E Y I F Z W - - - e - i n e a n d h e - D Y V Z V Y F Z U M R Z C R W N Z D Z J J - e d - a - - i n h i - - h a i - - a - e X Z W G C H S M R N M D H N C M F Q C H Z - i - - e d - - - a - d - - h e - - n J M X J Z W I E J Y U C F W D J N Z D I R p 12.

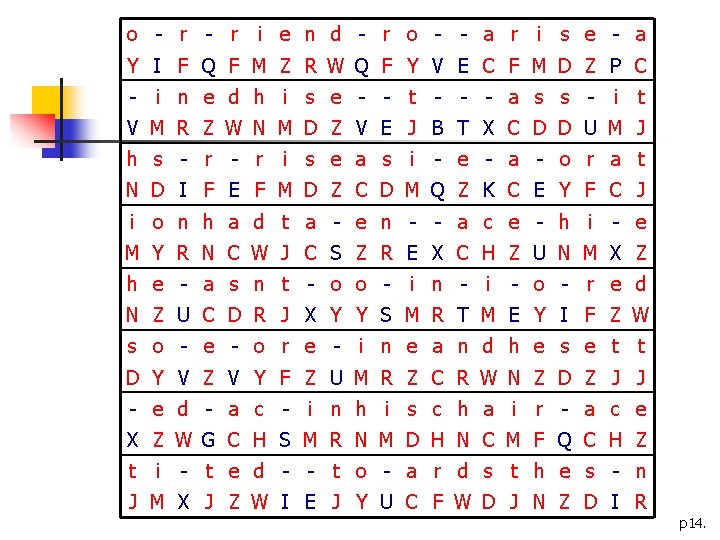
Cryptanalysis n n n We have DZ(4 times) and ZD(2 times) n Guess d. K(D)∈{r, s, t} Since o is a common letter n Guess e. K(o)∈{F, J, Y} n We have CFM and CJM: guess d. K(Y)=o (aoi is impossible) Guess NMD→his : d. K(D)=s Guess HNCMF→chair: d. K(H)=c, d. K(F)=r d. K(J)=t: the→JNZ p 13.

o - r i e n d - r o - - a r i s e - a Y I F Q F M Z R W Q F Y V E C F M D Z P C - i n e d h i s e - - t - - - a s s - i t V M R Z W N M D Z V E J B T X C D D U M J h s - r i s e a s i - e - a - o r a t N D I F E F M D Z C D M Q Z K C E Y F C J i o n h a d t a - e n - - a c e - h i - e M Y R N C W J C S Z R E X C H Z U N M X Z h e - a s n t - o o - i n - i - o - r e d N Z U C D R J X Y Y S M R T M E Y I F Z W s o - e - o r e - i n e a n d h e s e t t D Y V Z V Y F Z U M R Z C R W N Z D Z J J - e d - a c - i n h i s c h a i r - a c e X Z W G C H S M R N M D H N C M F Q C H Z t i - t e d - - t o - a r d s t h e s - n J M X J Z W I E J Y U C F W D J N Z D I R p 14.

Cryptanalysis n Now easy to determine the others nd. K(I)=u d. K(Q)=f n d. K(V)=m d. K(E)=p n d. K(P)=x d. K(B)=y n d. K(T)=g d. K(X)=l n d. K(U)=w d. K(K)=v n d. K(S)=k d. K(G)=b p 15.

o u r f r i e n d f r o m p a r i s e x a Y I F Q F M Z R W Q F Y V E C F M D Z P C m i n e d h i s e m p t y g l a s s w i t V M R Z W N M D Z V E J B T X C D D U M J h s u r p r i s e a s i f e v a p o r a t N D I F E F M D Z C D M Q Z K C E Y F C J i o n h a d t a k e n p l a c e w h i l e M Y R N C W J C S Z R E X C H Z U N M X Z h e w a s n t l o o k i n g i p o u r e d N Z U C D R J X Y Y S M R T M E Y I F Z W s o m e m o r e w i n e a n d h e s e t t D Y V Z V Y F Z U M R Z C R W N Z D Z J J l e d b a c k i n h i s c h a i r f a c e X Z W G C H S M R N M D H N C M F Q C H Z t i l t e d u p t o w a r d s t h e s u n J M X J Z W I E J Y U C F W D J N Z D I R p 16.

Cryptanalysis n <3> Cryptanalysis of the Vigenère Cipher n Kasiski test: n Search the ciphertext for pairs of identical segments (length at least 3) n Record the distance between the starting positions of the 2 segments n If we obtain several such distances d 1, d 2, …, we would conjecture that the key length m divides all of the di’s n m divides the gcd of the di’s p 17.

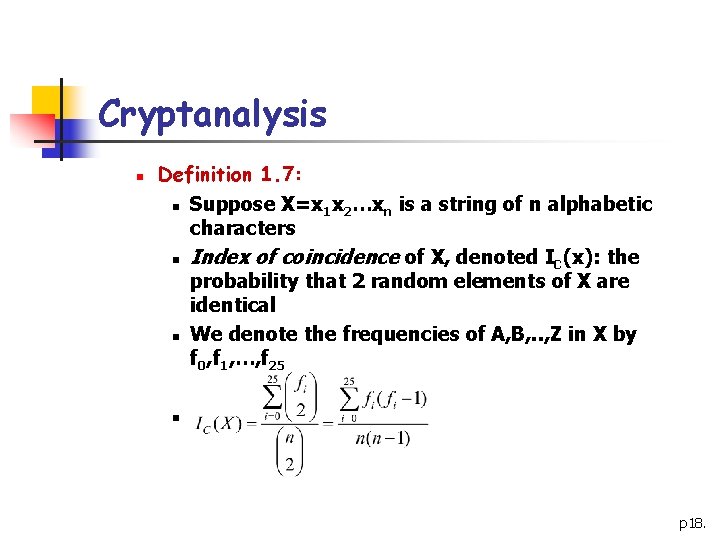
Cryptanalysis n Definition 1. 7: n Suppose X=x 1 x 2…xn is a string of n alphabetic characters n Index of coincidence of X, denoted IC(x): the probability that 2 random elements of X are identical n We denote the frequencies of A, B, . . , Z in X by f 0, f 1, …, f 25 n p 18.

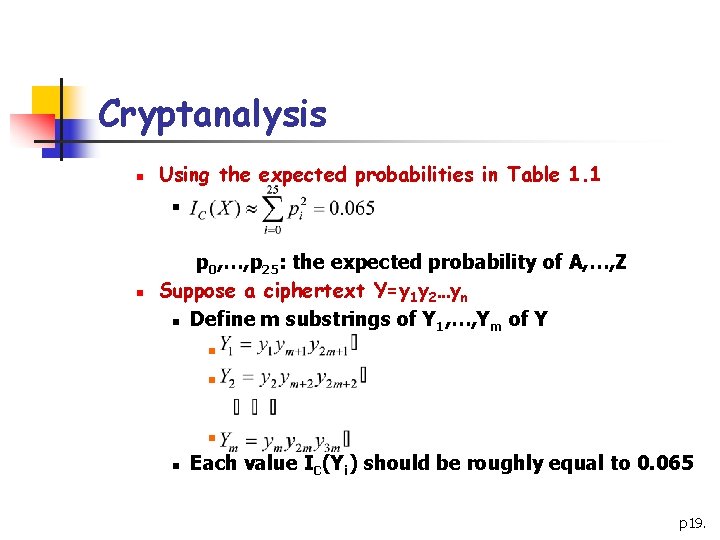
Cryptanalysis n Using the expected probabilities in Table 1. 1 n n p 0, …, p 25: the expected probability of A, …, Z Suppose a ciphertext Y=y 1 y 2…yn n Define m substrings of Y 1, …, Ym of Y n n Each value IC(Yi) should be roughly equal to 0. 065 p 19.

Cryptanalysis n If m is not the keyword length n Yi will look much more random n A completely random string will have n p 20.

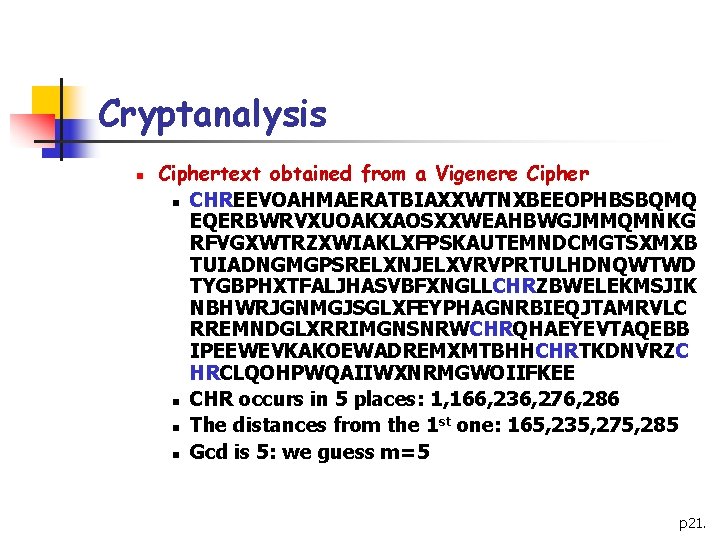
Cryptanalysis n Ciphertext obtained from a Vigenere Cipher n CHREEVOAHMAERATBIAXXWTNXBEEOPHBSBQMQ EQERBWRVXUOAKXAOSXXWEAHBWGJMMQMNKG RFVGXWTRZXWIAKLXFPSKAUTEMNDCMGTSXMXB TUIADNGMGPSRELXNJELXVRVPRTULHDNQWTWD TYGBPHXTFALJHASVBFXNGLLCHRZBWELEKMSJIK NBHWRJGNMGJSGLXFEYPHAGNRBIEQJTAMRVLC RREMNDGLXRRIMGNSNRWCHRQHAEYEVTAQEBB IPEEWEVKAKOEWADREMXMTBHHCHRTKDNVRZC HRCLQOHPWQAIIWXNRMGWOIIFKEE n CHR occurs in 5 places: 1, 166, 236, 276, 286 st one: 165, 235, 275, 285 n The distances from the 1 n Gcd is 5: we guess m=5 p 21.

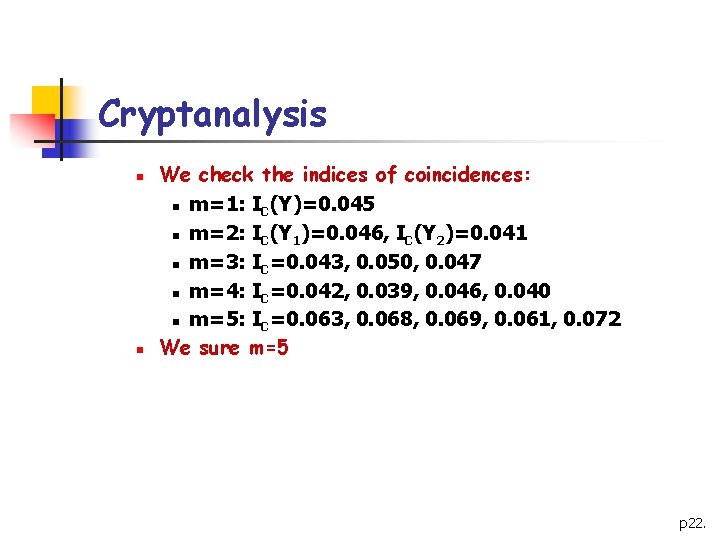
Cryptanalysis n n We check the indices of coincidences: n m=1: IC(Y)=0. 045 n m=2: IC(Y 1)=0. 046, IC(Y 2)=0. 041 n m=3: IC=0. 043, 0. 050, 0. 047 n m=4: IC=0. 042, 0. 039, 0. 046, 0. 040 n m=5: IC=0. 063, 0. 068, 0. 069, 0. 061, 0. 072 We sure m=5 p 22.

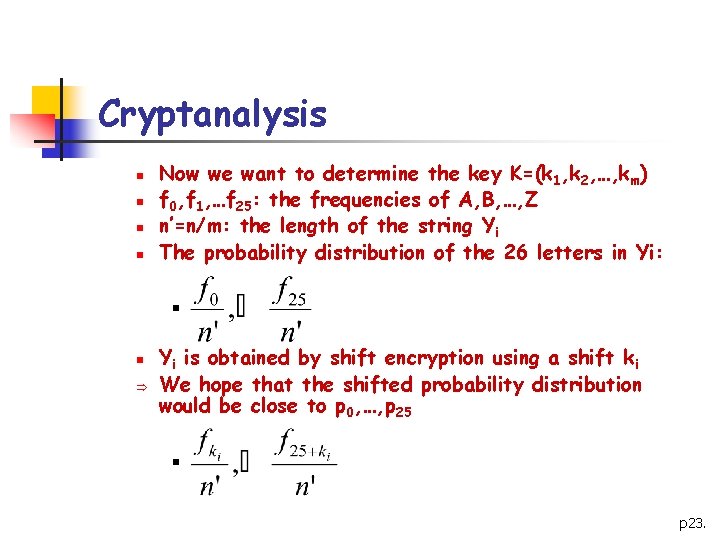
Cryptanalysis n n Now we want to determine the key K=(k 1, k 2, …, km) f 0, f 1, …f 25: the frequencies of A, B, …, Z n’=n/m: the length of the string Yi The probability distribution of the 26 letters in Yi: n n Þ Yi is obtained by shift encryption using a shift ki We hope that the shifted probability distribution would be close to p 0, …, p 25 n p 23.

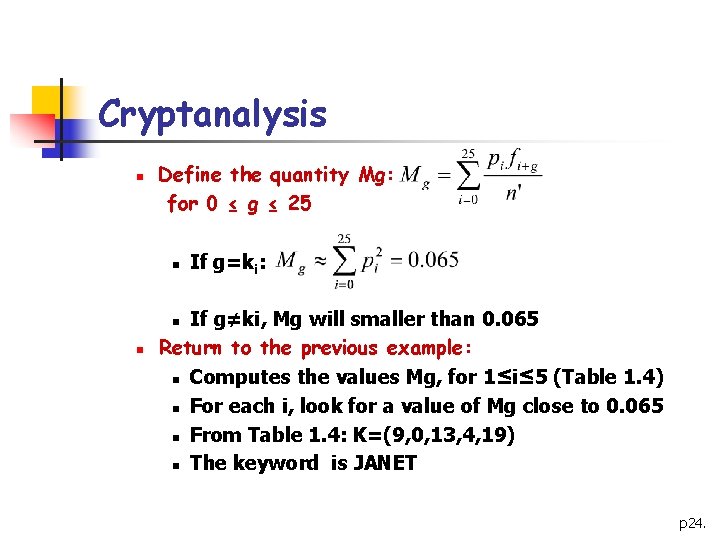
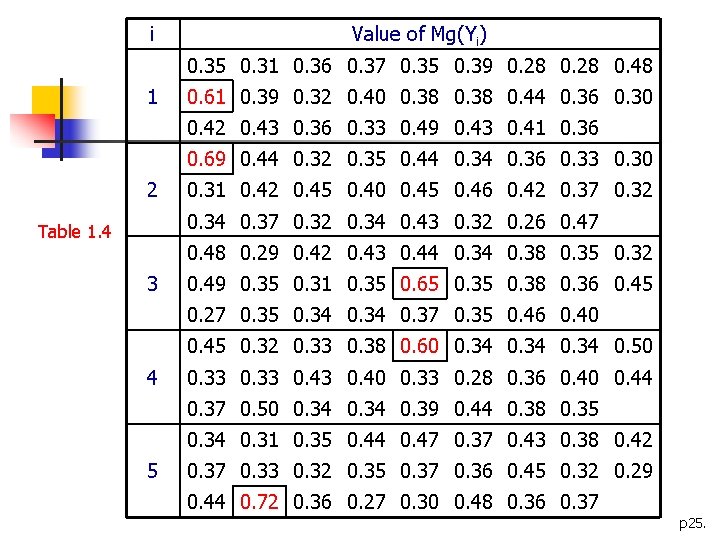
Cryptanalysis n Define the quantity Mg: for 0 ≤ g ≤ 25 n If g=ki: If g≠ki, Mg will smaller than 0. 065 Return to the previous example: n Computes the values Mg, for 1≤i≤ 5 (Table 1. 4) n For each i, look for a value of Mg close to 0. 065 n From Table 1. 4: K=(9, 0, 13, 4, 19) n The keyword is JANET n n p 24.

i Value of Mg(Yi) 0. 35 0. 31 0. 36 0. 37 0. 35 0. 39 0. 28 0. 48 1 0. 61 0. 39 0. 32 0. 40 0. 38 0. 44 0. 36 0. 30 0. 42 0. 43 0. 36 0. 33 0. 49 0. 43 0. 41 0. 36 0. 69 0. 44 0. 32 0. 35 0. 44 0. 36 0. 33 0. 30 2 0. 31 0. 42 0. 45 0. 40 0. 45 0. 46 0. 42 0. 37 0. 32 0. 34 0. 43 0. 32 0. 26 0. 47 Table 1. 4 0. 48 0. 29 0. 42 0. 43 0. 44 0. 38 0. 35 0. 32 3 0. 49 0. 35 0. 31 0. 35 0. 65 0. 38 0. 36 0. 45 0. 27 0. 35 0. 34 0. 37 0. 35 0. 46 0. 40 0. 45 0. 32 0. 33 0. 38 0. 60 0. 34 0. 50 4 0. 33 0. 43 0. 40 0. 33 0. 28 0. 36 0. 40 0. 44 0. 37 0. 50 0. 34 0. 39 0. 44 0. 38 0. 35 0. 34 0. 31 0. 35 0. 44 0. 47 0. 37 0. 43 0. 38 0. 42 5 0. 37 0. 33 0. 32 0. 35 0. 37 0. 36 0. 45 0. 32 0. 29 0. 44 0. 72 0. 36 0. 27 0. 30 0. 48 0. 36 0. 37 p 25.

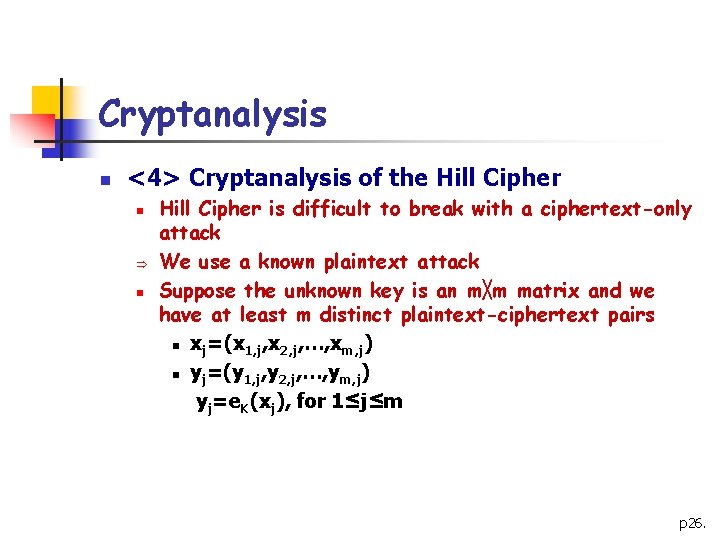
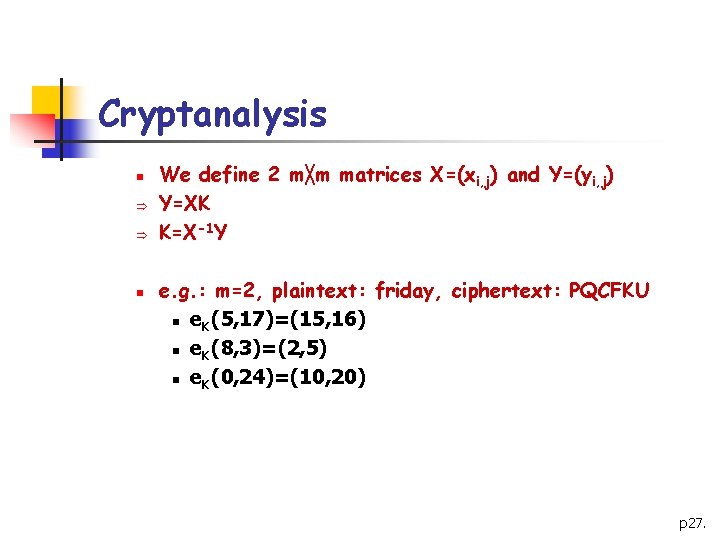
Cryptanalysis n <4> Cryptanalysis of the Hill Cipher n Þ n Hill Cipher is difficult to break with a ciphertext-only attack We use a known plaintext attack Suppose the unknown key is an m╳m matrix and we have at least m distinct plaintext-ciphertext pairs n xj=(x 1, j, x 2, j, …, xm, j) n yj=(y 1, j, y 2, j, …, ym, j) yj=e. K(xj), for 1≤j≤m p 26.

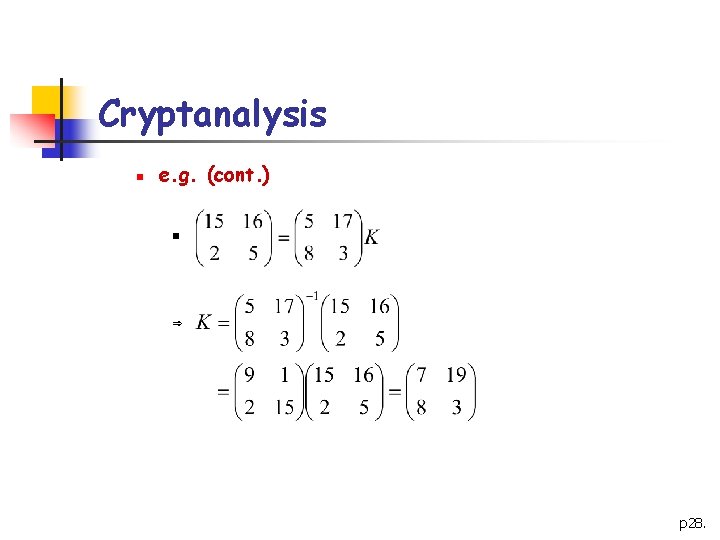
Cryptanalysis n Þ Þ n We define 2 m╳m matrices X=(xi, j) and Y=(yi, j) Y=XK K=X-1 Y e. g. : m=2, plaintext: friday, ciphertext: PQCFKU n e. K(5, 17)=(15, 16) n e. K(8, 3)=(2, 5) n e. K(0, 24)=(10, 20) p 27.

Cryptanalysis n e. g. (cont. ) n Þ p 28.

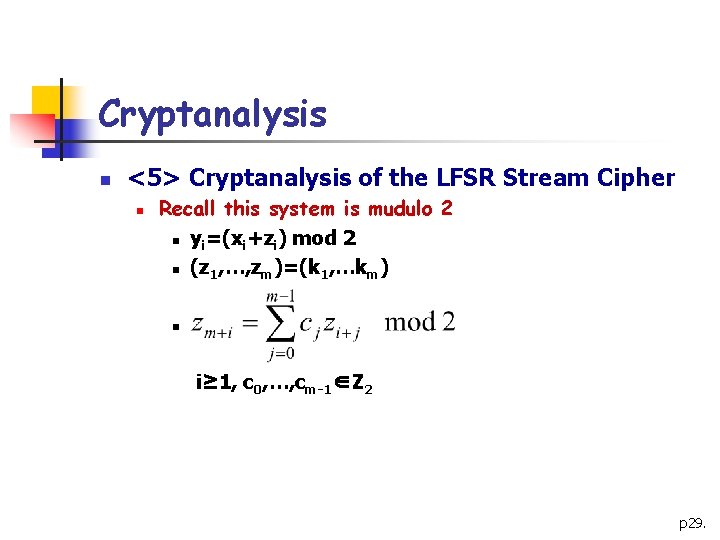
Cryptanalysis n <5> Cryptanalysis of the LFSR Stream Cipher n Recall this system is mudulo 2 n yi=(xi+zi) mod 2 n (z 1, …, zm)=(k 1, …km) n i≥ 1, c 0, …, cm-1∈Z 2 p 29.

Cryptanalysis n n We use a known-plaintext attack here If plaintext length ≥ 2 m n We can solve the system of m linear equations: p 30.

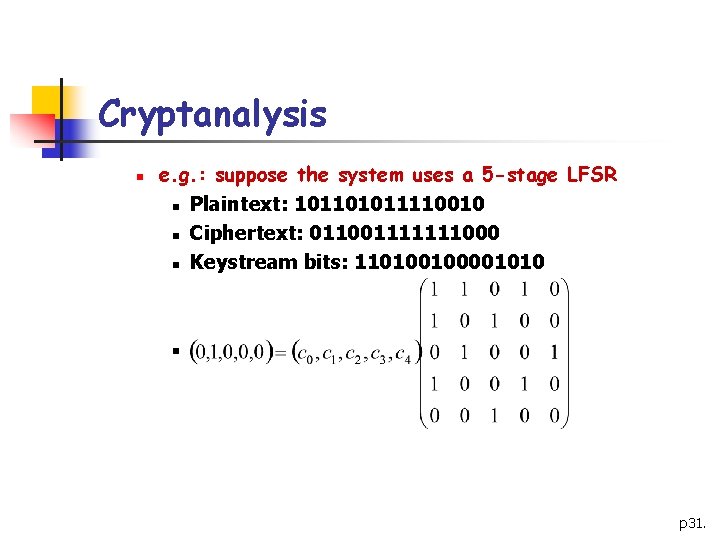
Cryptanalysis n e. g. : suppose the system uses a 5 -stage LFSR n Plaintext: 101101011110010 n Ciphertext: 011001111111000 n Keystream bits: 110100100001010 n p 31.

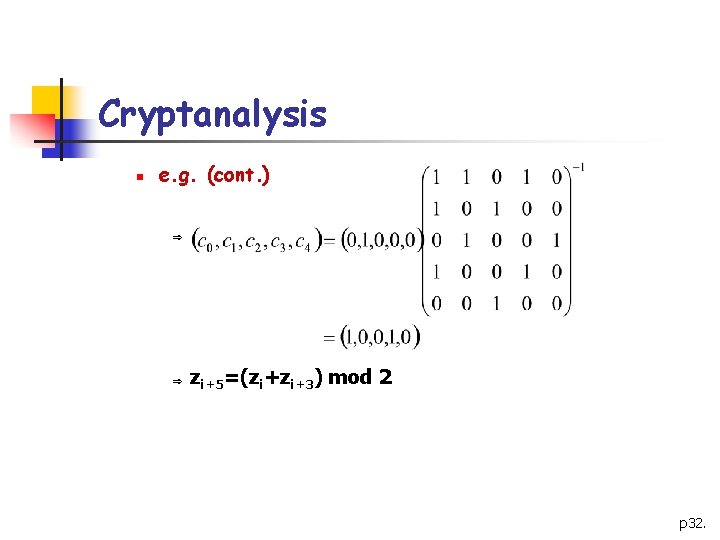
Cryptanalysis n e. g. (cont. ) Þ Þ zi+5=(zi+zi+3) mod 2 p 32.