Cryptographic Hash Function A hash function H accepts










- Slides: 24

Cryptographic Hash Function

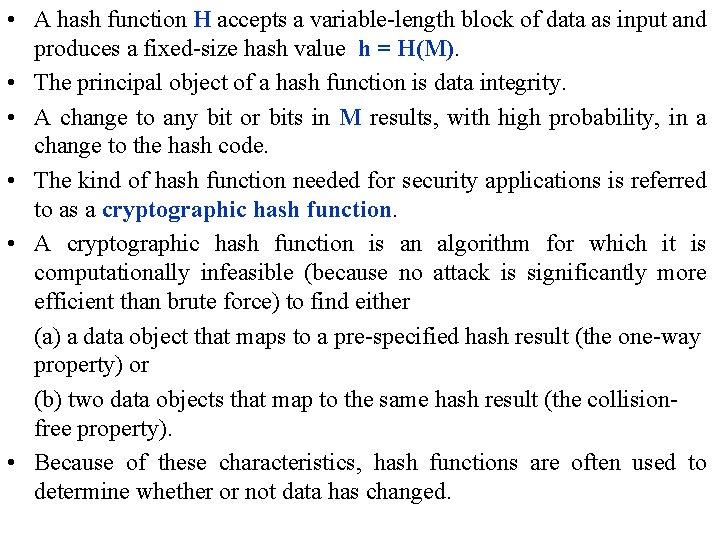
• A hash function H accepts a variable-length block of data as input and produces a fixed-size hash value h = H(M). • The principal object of a hash function is data integrity. • A change to any bit or bits in M results, with high probability, in a change to the hash code. • The kind of hash function needed for security applications is referred to as a cryptographic hash function. • A cryptographic hash function is an algorithm for which it is computationally infeasible (because no attack is significantly more efficient than brute force) to find either (a) a data object that maps to a pre-specified hash result (the one-way property) or (b) two data objects that map to the same hash result (the collisionfree property). • Because of these characteristics, hash functions are often used to determine whether or not data has changed.

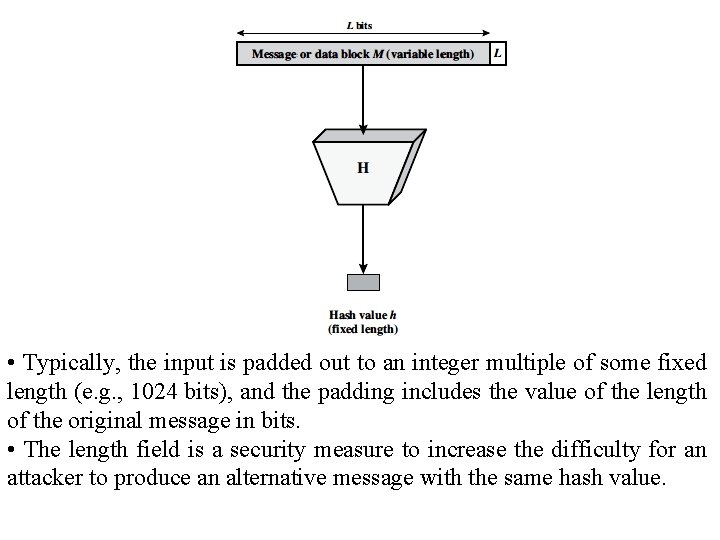
• Typically, the input is padded out to an integer multiple of some fixed length (e. g. , 1024 bits), and the padding includes the value of the length of the original message in bits. • The length field is a security measure to increase the difficulty for an attacker to produce an alternative message with the same hash value.

Applications of Cryptographic Hash Functions 1. Message Authentication • Message authentication is a mechanism or service used to verify the integrity of a message. • Message authentication assures that data received are exactly as sent (i. e. , contain no modification, insertion, deletion, or replay). • In many cases, there is a requirement that the authentication mechanism assures that purported identity of the sender is valid. • When a hash function is used to provide message authentication, the hash function value is often referred to as a message digest.

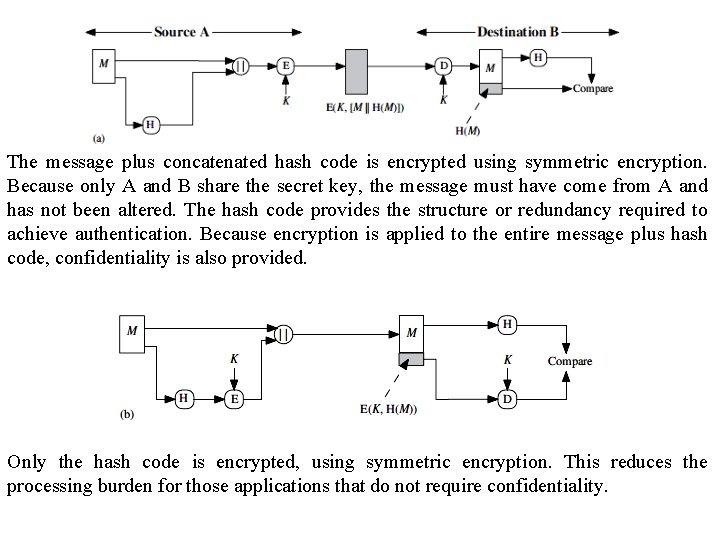
The message plus concatenated hash code is encrypted using symmetric encryption. Because only A and B share the secret key, the message must have come from A and has not been altered. The hash code provides the structure or redundancy required to achieve authentication. Because encryption is applied to the entire message plus hash code, confidentiality is also provided. Only the hash code is encrypted, using symmetric encryption. This reduces the processing burden for those applications that do not require confidentiality.

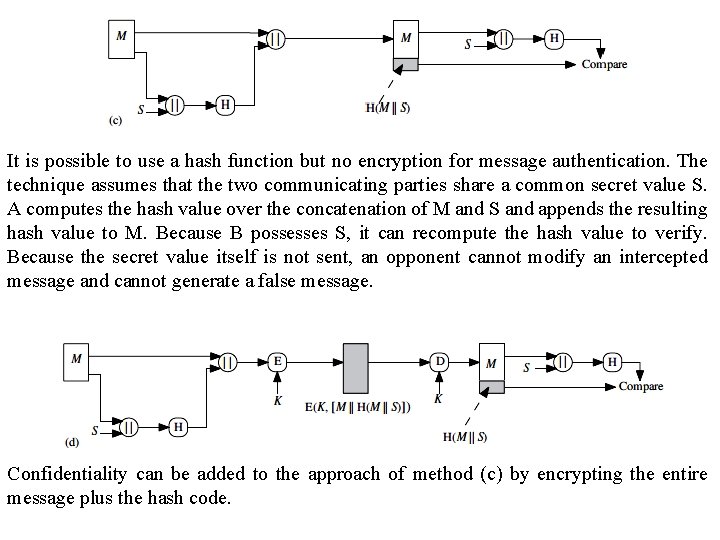
It is possible to use a hash function but no encryption for message authentication. The technique assumes that the two communicating parties share a common secret value S. A computes the hash value over the concatenation of M and S and appends the resulting hash value to M. Because B possesses S, it can recompute the hash value to verify. Because the secret value itself is not sent, an opponent cannot modify an intercepted message and cannot generate a false message. Confidentiality can be added to the approach of method (c) by encrypting the entire message plus the hash code.

• More commonly, message authentication is achieved using a message authentication code (MAC), also known as a keyed hash function. • Typically, MACs are used between two parties that share a secret key to authenticate information exchanged between those parties. • A MAC function takes as input a secret key and a data block and produces a hash value, referred to as the MAC. This can then be transmitted with or stored with the protected message. • If the integrity of the message needs to be checked, the MAC function can be applied to the message and the result compared with the stored MAC value. • An attacker who alters the message will be unable to alter the MAC value without knowledge of the secret key. Note that the verifying party also knows who the sending party is because no one else knows the secret key. • Note that the combination of hashing and encryption results in an overall function that is, in fact, a MAC (Figure 11. 2 b). • That is, E(K, H(M)) is a function of a variable-length message M and a secret key K, and it produces a fixed-size output that is secure against an opponent who does not know the secret key.

2. Digital Signatures • Another important application, which is similar to the message authentication application, is the digital signature. • The operation of the digital signature is similar to that of the MAC. • In the case of the digital signature, the hash value of a message is encrypted with a user’s private key. Anyone who knows the user’s public key can verify the integrity of the message that is associated with the digital signature. • In this case, an attacker who wishes to alter the message would need to know the user’s private key.

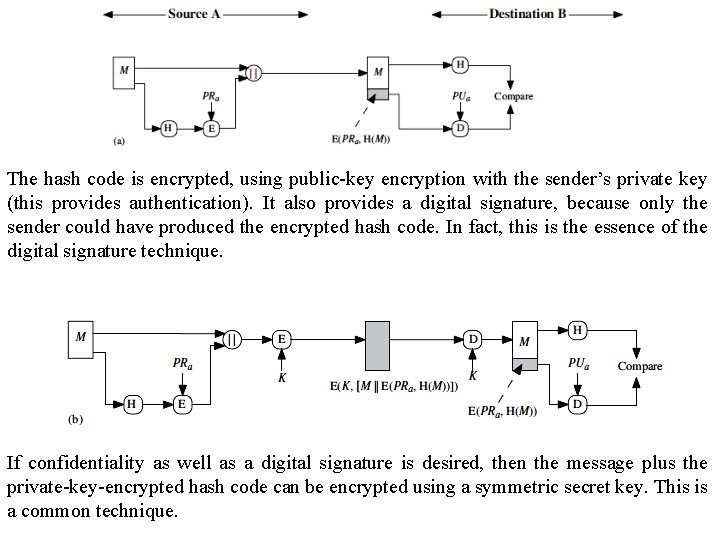
The hash code is encrypted, using public-key encryption with the sender’s private key (this provides authentication). It also provides a digital signature, because only the sender could have produced the encrypted hash code. In fact, this is the essence of the digital signature technique. If confidentiality as well as a digital signature is desired, then the message plus the private-key-encrypted hash code can be encrypted using a symmetric secret key. This is a common technique.

3. Other Applications • Hash functions are commonly used to create a one-way password file, in which a hash of a password is stored by an operating system rather than the password itself. • Thus, the actual password is not retrievable by a hacker who gains access to the password file. • In simple terms, when a user enters a password, the hash of that password is compared to the stored hash value for verification. • This approach to password protection is used by most operating systems. • Hash functions can be used for intrusion detection and virus detection. Store H(F) for each file on a system and secure the hash values (e. g. , on a CD-R that is kept secure). One can later determine if a file has been modified by recomputing H(F). An intruder would need to change F without changing H(F).

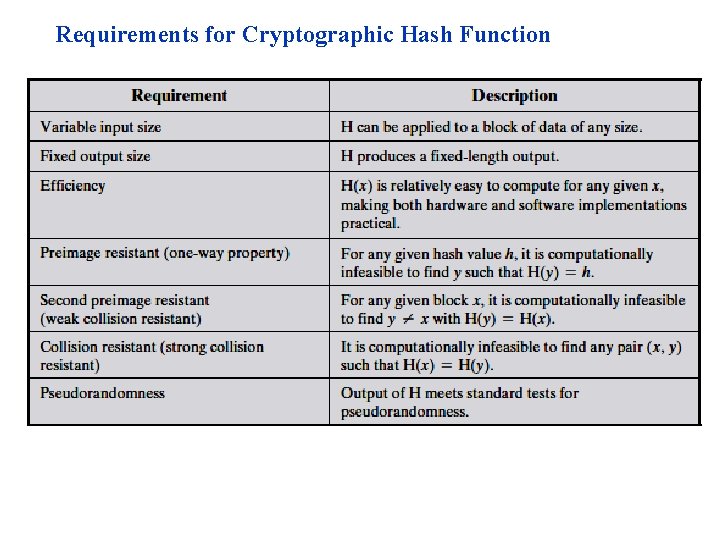
Properties of Hash Functions • In order to be an effective cryptographic tool, the hash function is desired to possess following properties − • Pre-Image Resistance – This property means that it should be computationally hard to reverse a hash function. – In other words, if a hash function h produced a hash value z, then it should be a difficult process to find any input value x that hashes to z. – This property protects against an attacker who only has a hash value and is trying to find the input. • Second Pre-Image Resistance – This property means given an input and its hash, it should be hard to find a different input with the same hash. – In other words, if a hash function h for an input x produces hash value h(x), then it should be difficult to find any other input value y such that h(y) = h(x). – This property of hash function protects against an attacker who has an input value and its hash, and wants to substitute different value as legitimate value in place of original input value.

• Collision Resistance – This property means it should be hard to find two different inputs of any length that result in the same hash. This property is also referred to as collision free hash function. – In other words, for a hash function h, it is hard to find any two different inputs x and y such that h(x) = h(y). – Since, hash function is compressing function with fixed hash length, it is impossible for a hash function not to have collisions. This property of collision free only confirms that these collisions should be hard to find. – This property makes it very difficult for an attacker to find two input values with the same hash. – Also, if a hash function is collision-resistant then it is second pre-image resistant.

Requirements for Cryptographic Hash Function

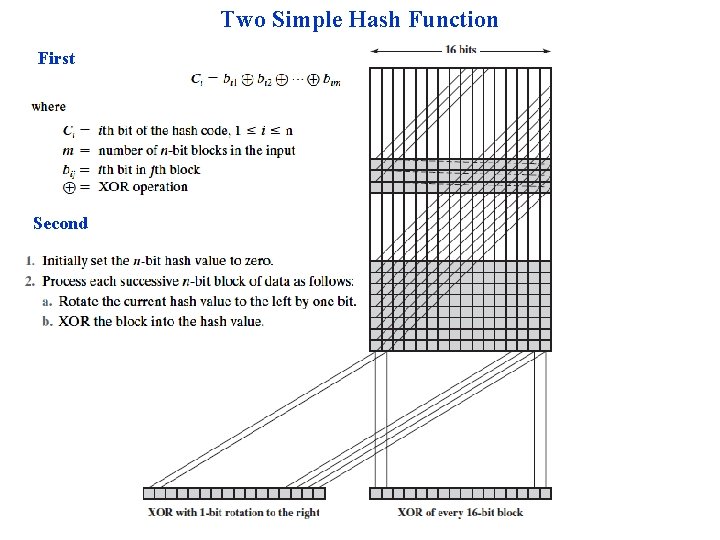
Two Simple Hash Function First Second

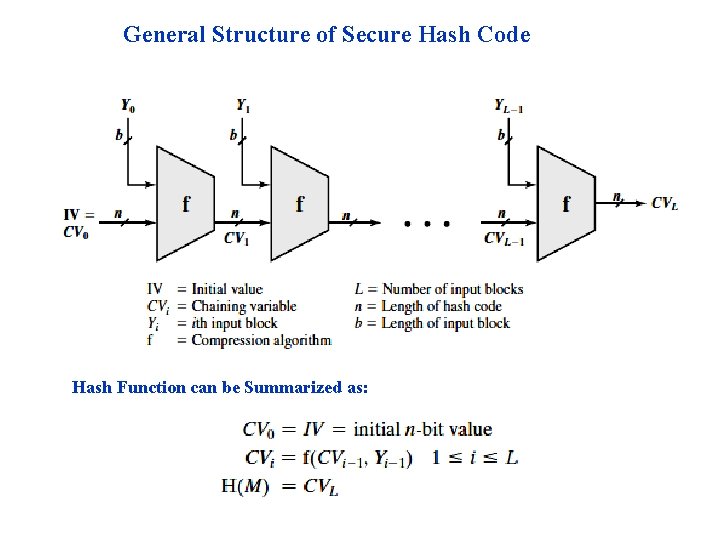
General Structure of Secure Hash Code Hash Function can be Summarized as:

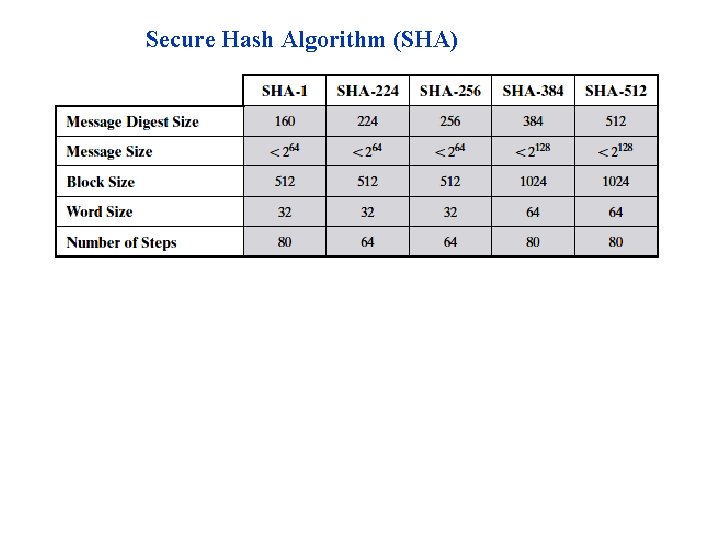
Secure Hash Algorithm (SHA)

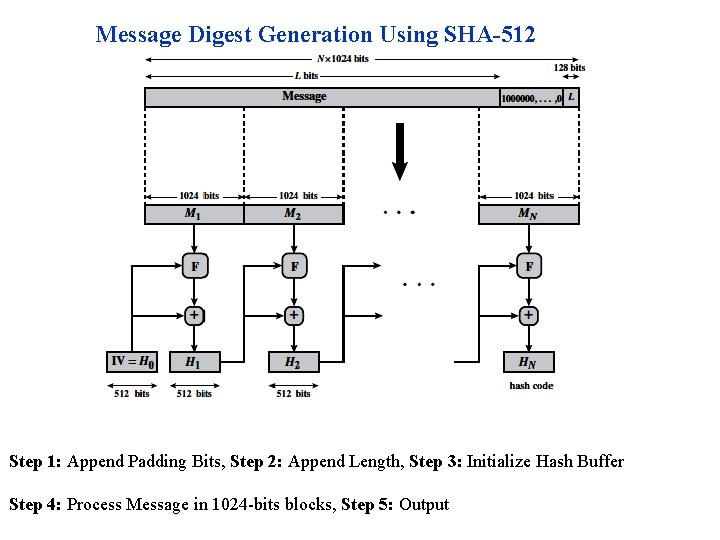
Message Digest Generation Using SHA-512 Step 1: Append Padding Bits, Step 2: Append Length, Step 3: Initialize Hash Buffer Step 4: Process Message in 1024 -bits blocks, Step 5: Output

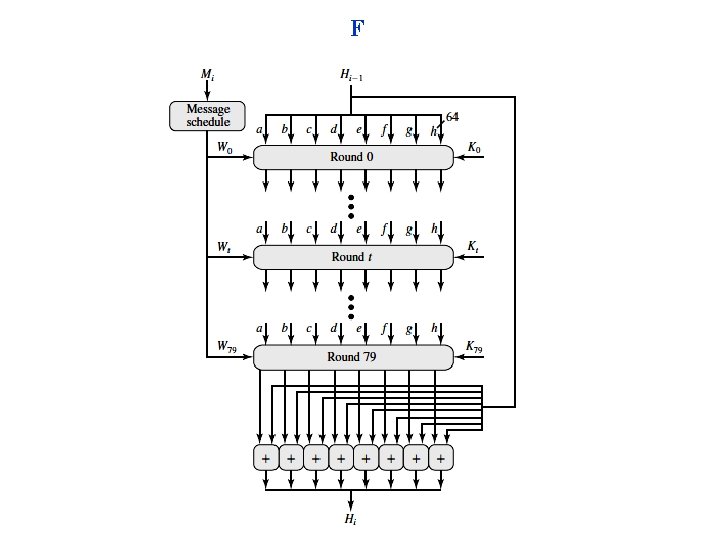
F

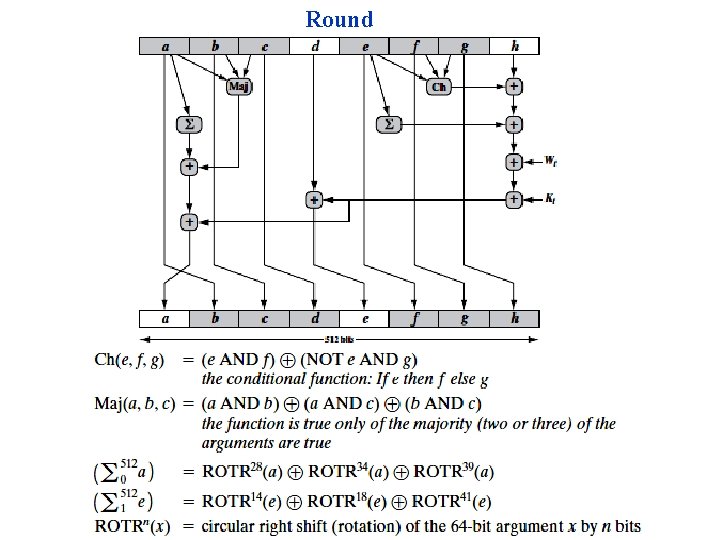
Round

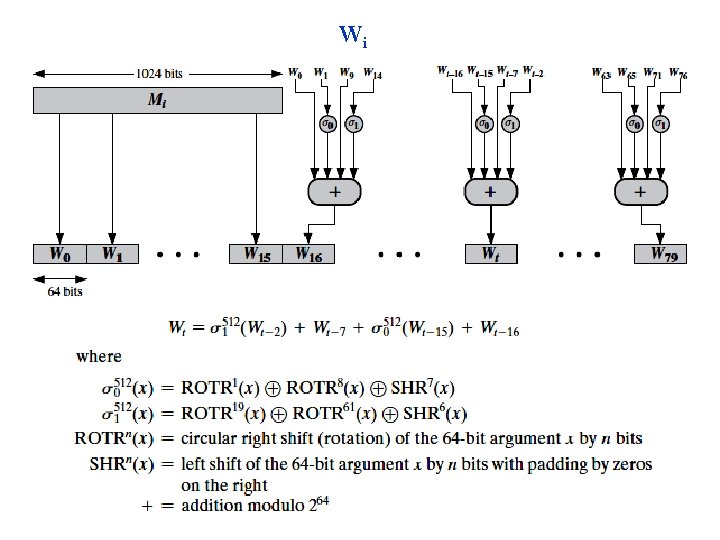
Wi



