CISSP Cryptography 1 Cryptography Cryptographic Life Cycle Cryptography



























































































- Slides: 114

CISSP Cryptography 1

Cryptography Cryptographic Life Cycle Cryptography Components Symmetric Asymmetric PKI Hashing Key Management Processes Digital Signatures and Non-Repudiation Types of Attacks

Use of Cryptography Protection of data at rest (data resident on a hard drive) Protection of data in transit (data being transmitted across the network) Authentication of origin (source) Authentication of data (data integrity)

Cryptographic Limitations and Governance Limited by its key length, key management practices (expiration periods) and algorithm weaknesses Strong keys are long and must not produce a predictable output NIST tests and approves cryptographic algorithms for government use (i. e. Federal Information Processing Standard (FIPS) 140 -2)

FIPS 140 -2

FIPS 140 -2 Describes the security requirements that will be satisfied by crypto modules protecting sensitive but unclassified material (SBU) ◦ Key generation ◦ Physical chip security ◦ Key storage Provides 4 increasing levels of security (Level 1, 2, 3, 4) Tokens must be hardware cryptographic modules validated at Level 2 or higher, with at least Level 3 security Requires expensive testing and certification processes

Key Terms Cryptography - creates ciphertext out of plaintext using cryptographic algorithms Cryptanalysis – science of breaking cryptographic messages ◦ Work factor – Estimated time, effort, and resources necessary to break a cryptosystem Cryptology – science of secure communications (encompasses both Cryptography and Cryptanalysis) from Latin/Greek meaning. . To hide/conceal

Key Terms Algorithm – mathematical formula, or rules, used to encrypt/decrypt Key – cryptovariable – value that comprises a large sequence of random bits Keyspace – rage of values that can be used to construct a key ◦ Larger keyspace provides for more possible keys so is stronger ◦ 512 bits provides 2 to the power of 512 possible combinations The strength of the encryption comes not from keeping the algorithm secret – but from the size , randomness, and secrecy of the key!!!!!

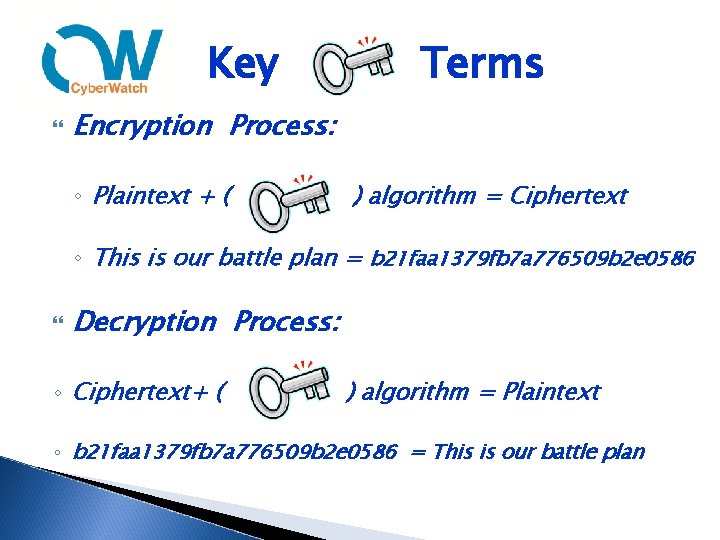
Key Terms Encryption Process: ◦ Plaintext + ( ) algorithm = Ciphertext ◦ This is our battle plan = b 21 faa 1379 fb 7 a 776509 b 2 e 0586 Decryption Process: ◦ Ciphertext+ ( ) algorithm = Plaintext ◦ b 21 faa 1379 fb 7 a 776509 b 2 e 0586 = This is our battle plan

Cryptosystem Services Encryption can provide the following security services: ◦ Confidentiality ◦ Integrity ◦ Authenticity ◦ Non-repudiation (what is this? !)

Substitution Cipher - each bit, character, block is replaced with another bit, character, or block Caesar Cipher Standard Alphabet: ABCDEFGHIJKLMNOPQRSTUVWXYZ Caesar Alphabet: XYZABCDEFGHIJKLMNOPQRSTUVW http: //www. nsa. gov/kids/games 00010. shtml http: //donpiorsuerte. wordpress. com/2010/05/21/vigenere-cipher/

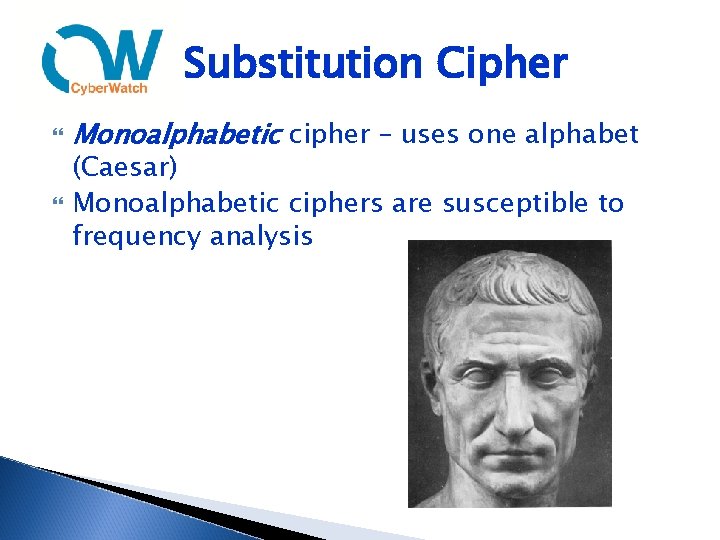
Substitution Cipher Monoalphabetic cipher – uses one alphabet (Caesar) Monoalphabetic ciphers are susceptible to frequency analysis

Weaknesses Substitution and Transposition ciphers vulnerable to Frequency Analysis

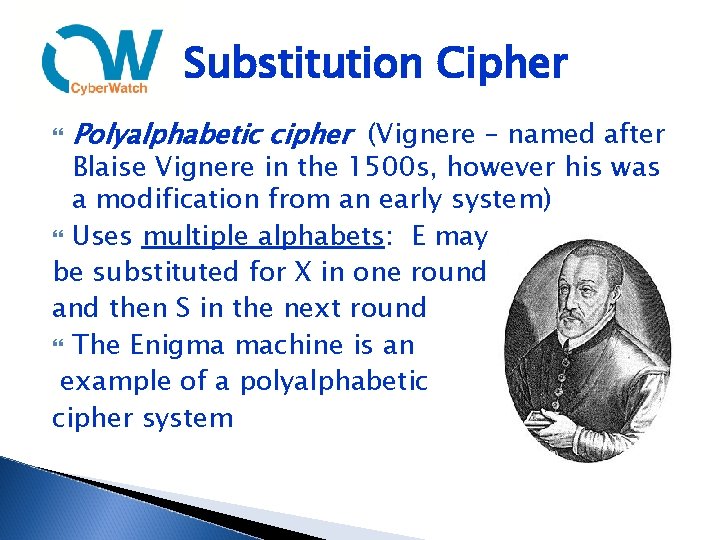
Substitution Cipher Polyalphabetic cipher (Vignere – named after Blaise Vignere in the 1500 s, however his was a modification from an early system) Uses multiple alphabets: E may be substituted for X in one round and then S in the next round The Enigma machine is an example of a polyalphabetic cipher system

Transposition Cipher Transposition cipher More complicated stream cipher Rearranges letters without changing them

One-Time Pad AKA Vernam cipher – a symmetrical stream cipher Basis for modern-day crypto algorithms Doesn’t shift alphabet Combines key with a plaintext via XOR function to create ciphertext Uses a binary mathematic function called Exclusive OR (XOR) ◦ When combining two bits, if both values are the same, the result is 0, if they are different, the result is a 1 Must be: ◦ Made up of random values ◦ Used only one time ◦ Securely distributed to its destination ◦ Secured at sender’s and receivers sites ◦ PAD must be as long as the message

Hash Functions One-way encryption only – never reverse engineered Used to provide integrity If the plaintext changes, the hash changes Used to verify file integrity (i. e. products such as Trip. Wire and other file integrity checkers), as well as with digital signatures

Hashing

Hash Functions Secure Hash Algorithm (SHA-1) – designed by NSA – 160 -bit hash Message Digest 5 (MD 5) – 128 -bit hash – created by Ron Rivest Both have had issues with “collisions” Newer: MD 6 SHA – 2 – includes SHA-224, SHA-256, SHA-384, and SHA-512 HAVAL – Hash of Variable Length – creates MDs of 128, 160, 192, 224, or 256 bits in length, using 3, 4, or 5 rounds

Hash Attacks Birthday attack Named after birthday paradox – fact that in a room with 23 people or more, the odds are greater than 50% that two will share the same birthday Attacker attempts to force a collision (an attack on integrity) Reason we now use SHA-256 for government use as the output length of the hash function must be large enough so that finding two different documents with the same “hash” or MD becomes computationally infeasible.

Symmetric Encryption AKA “Secret Key” (Sometimes also called “Private Key” Uses same key (one key) to encrypt and decrypt Fast!! “Key Exchange” is a problem

Symmetric Encryption Modes – Stream Ciphers Steam Cipher – each bit is independently encrypted in a stream ◦ Require more randomness and processing power than block ciphers ◦ Fast when plaintext is short, but more prone to attack because the engine that generates the stream does not vary

Symmetric Encryption Modes – Block Ciphers Block ciphers encrypt blocks of data each round (DES and AES) Plaintext message is divided into separate blocks of 8 – 16 bytes and then each block is encrypted independently Cipher is reset to its original state after each block is processed Can be easily implemented at the software level Considered more secure because the output is more random

Symmetric Encryption Algorithms

Data Encryption Standard (DES) Designed by IBM, based on Lucifer symmetric cipher Uses a 64 -bit block size (encrypts 64 -bits each round) – however the 8 -bit parity is ignored so the effective key length is only 56 bits Note: May also be DEA on the exam!

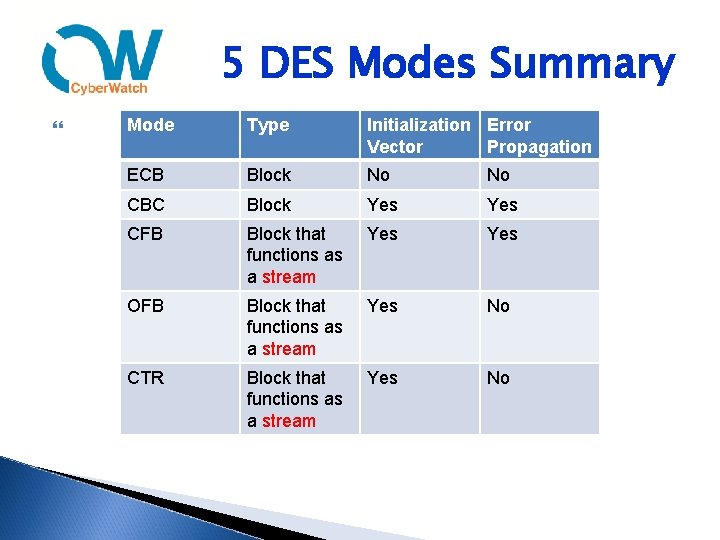
5 DES Modes Can use 5 different modes to encrypt Basic differences are ◦ block versus emulated stream ◦ use of initialization vectors (random values used with keys to ensure patterns are not created during the encryption process) – prevent two messages encrypted with same key from producing the same ciphertext ◦ How errors in encryption propagate to subsequent blocks

5 DES Modes Electronic Code Book (ECB) ◦ Simplest and weakest for of DES ◦ No Initialization vector or chaining ◦ Two plaintexts with partial identical portions (i. e. a letter header) encrypted with the same key have partial identical ciphertext portions ◦ Can also leave plaintext patterns evident in the ciphertext Cipher Block Chaining (CBC) ◦ Block mode that XORs the previous encrypted block to the next block of plaintext to be encrypted ◦ 1 st encrypted block is an initialization vector that contains random data ◦ Chaining destroys patterns ◦ Encryption errors propagate

5 DES Modes Cipher Feedback (CFB) ◦ Similar to CBC, except is a stream mode cipher and uses feedback to destroy patters Output Feedback (OFB) ◦ Same as CFB, but uses a subkey before it is XORed to the plaintext so errors do not propagate Counter ◦ Similar to OFB, but uses a counter as the “feedback” that can be an ascending number

5 DES Modes Summary Mode Type Initialization Error Vector Propagation ECB Block No No CBC Block Yes CFB Block that functions as a stream Yes OFB Block that functions as a stream Yes No CTR Block that functions as a stream Yes No

Single DES Original DES (encrypting 64 -bit blocks of data with a 56 -bit key using 16 rounds of encryption Work factor became the issue as technology advanced, making it vulnerable to brute force key attack ◦ 1998 – cracked in 56 hours using multiple PCs by Electronic Frontier Foundation (EFF) by “Deep Crack”

Triple DES (3 DES) DES…. 3 times per block (three iterations of DES) Uses three unique keys (1 TDES EDE (Encrypt, Decrypt, Encrypt order), 2 TDES EDE, and 3 TDES EDE) – note the differences on page 710 Recommended standard in 1999

International Data Encryption Algorithm (IDEA) Current US Symmetric Encryption Standard Block cipher Encrypts 128 -bit blocks of data 128 -bit keys (10 rounds of encryption) 192 -bit keys (12 rounds of encryption) 256 -bit keys (14 rounds of encryption) Used in Pretty Good Privacy (PGP)

Blowfish and Twofish Open algorithms, unpatented and freely available - created by Bruce Schneirer Blowfish ◦ Uses 32 -bit through 448 -bit keys (default is 128) ◦ Encrypts 64 -bit blocks Twofish ◦ AES finalist ◦ Encrypts 128 -bit blocks using 128 -bit through 256 -bit keys ◦ http: //en. wikipedia. org/wiki/Bruce_Schneier

RC 5 and RC 6 Developed by RSA Labs RC 5 ◦ 32 -bit (testing purposes), 64 -bit (replacement for DES), or 12 -bit blocks with key size ranges from 0 – 2040 bits RC 6 ◦ AES finalist based on RC 5 ◦ Stronger than RC 5 ◦ Encrypts 128 -bit blocks using 128, 192, or 256 -bit keys

Advanced Encryption Standard (AES) Rijndael DES as the government symmetric standard (approved by NIST in Approved by NIST in 2000 Block cipher supporting 128 -, 192 -, and 256 -bit encryption ◦ AES performs three steps on every block (128 bits) of plaintext ◦ Within Step 2, multiple rounds are performed depending on the key size ◦ Within each round, bytes are substituted and rearranged, then special multiplication is performed based on the new arrangement

Asymmetric Encryption

Diffie-Hellman Key Agreement Protocol First to solves the key exchange problem!!!! Allows 2 parties to security agree on a symmetric key via a public channel with no prior key exchange Created in 1976 Uses discrete logarithms Ralph Merkle, Martin Hellman, Whitfield Diffie

Asymmetric Encryption (aka Public Key Cryptography) Merkle-Hellman knapsack cryptosystem, developed by Ralph Merkle and Martin Hellman in 1978 was one of the first ◦ Faster than RSA ◦ Ooopss…. broken

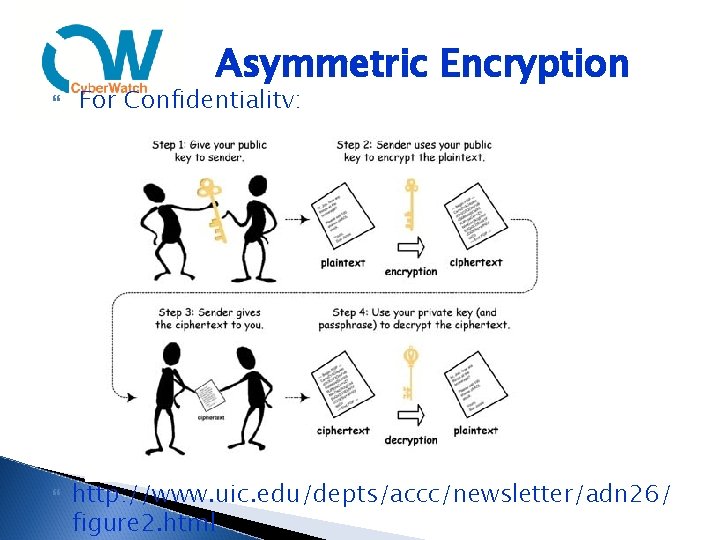
Asymmetric Encryption (aka Public Key Cryptography) Uses 2 keys ◦ Public and private Public – anyone can know Private – guard with your life ◦ Mathematically-related – can’t “reverse engineer” one to derive the other ◦ What is encrypted by one key can only be decrypted by the opposite key ◦ Relies on prime number factoring and discrete logarithms for its strength Key usage differs depending on whether or not we want to achieve confidentiality, versus authenticity/integrity and, thusly, non-repudiation

Asymmetric Encryption For Confidentiality: http: //www. uic. edu/depts/accc/newsletter/adn 26/ figure 2. html

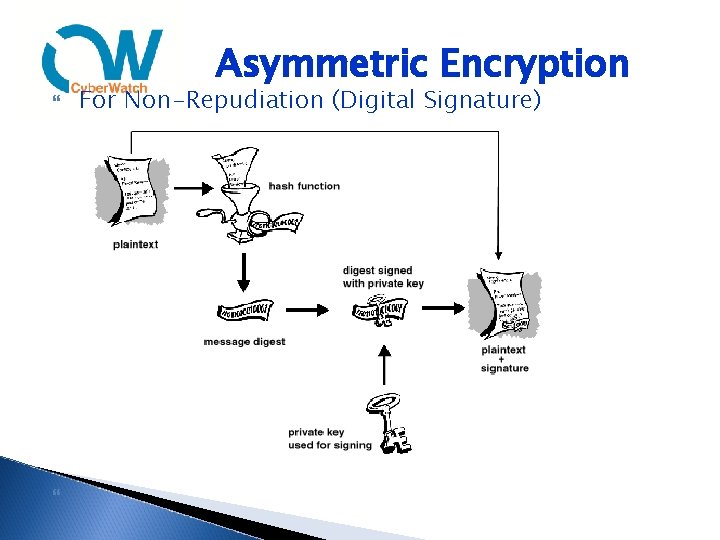
Asymmetric Encryption For Non-Repudiation (Digital Signature)

RSA Named after Ron Rivest (RC 4 fame), Adi Shamir, and Leonard Adleman and developed at MIT in 1978 Most popular asymmetric algorithm and worldwide de facto standard Used for digital signatures, key exchange, and encryption, providing confidentiality and authenticity Shamir, Rivest, Adleman www. boiledbeans. net

Elliptic Curve Cryptography Uses a one-way function with discrete logarithms as applied to elliptic curves Much stronger than systems just using discrete logarithms and stronger than factoring prime numbers as there is no known sub-exponential algorithm for it Requires fewer computational sources as shorter keys can be used Often used on lower-power devices

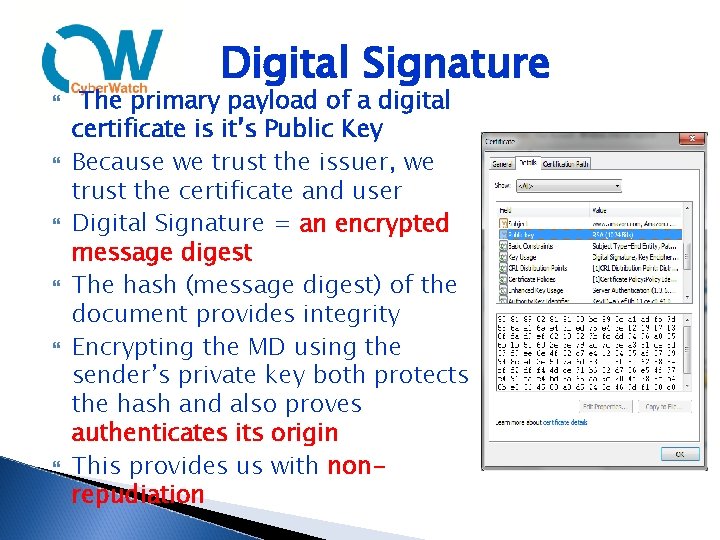
Digital Signature The primary payload of a digital certificate is it’s Public Key Because we trust the issuer, we trust the certificate and user Digital Signature = an encrypted message digest The hash (message digest) of the document provides integrity Encrypting the MD using the sender’s private key both protects the hash and also proves authenticates its origin This provides us with nonrepudiation

Digital Signature Standard (DSS) Federal standard for digital signatures Developed by NIST in 1991 Requires the use of DSA, RSA, ECC and SHA DSA developed by NSA, slower than RSA so not used in Federal PKIs

El Gamal Public key algorithm used for digital signatures, encryption, and key exchange Based not on factoring large numbers but on calculating discrete logarithms in a finite field Extension of Diffie-Hellman Used in GNU Privacy Guard software and recent versions of PGP Usually the slowest of asymmetric algorithms

Hybrid Crypto. Systems Uses both symmetric and asymmetric encryption ◦ Asymmetric for key exchange ◦ Symmetric for bulk data transfer SSL is an example When ready to checkout – Amazon’s digital cert is sent to you Your browser extracts the public key M/S’s cryptomodule generates 4 session keys Encrypting the session keys using Amazon’s public key , your system sends these to Amazon ◦ Amazon extracts the session keys, using its private key ◦ Your system now encrypts the credit card/order info using the sessions keys ◦ ◦

MAC vs. HMAC vs CBCMAC MAC concatenates a message with a symmetric key. Provides authentication. Hashed Message Authentication Code (HMAC) concatenates a message with a symmetric key and puts the result through a hashing algorithm. Key exchange is still an issue. IPSec uses HMAC. Provides integrity and authentication. CBC-MAC – Cipher Block Chaining Message Authentication Code (CBC-MAC) uses the CBC mode of symmetric block cipher (i. e. DES) to create a MAC. Provides integrity and authentication.

Attacks Eavesdropping and sniffing are considered passive attacks Altering messages, modifying system files are considered active attacks

Attacks Cipher-Only Attacks – attacker has the ciphertext and attempts to derive the key – most difficult Brute Force - brute force – every key is randomly generated and used Known Plaintext –Attacker has samples of both the plaintext (a crib) and the ciphertext and relies on matching to derive the key that was used. Chosen Plaintext – attacker can select the plaintext that will be encrypted in the hopes that the resulting ciphertext may reveal the key ◦ Batch chosen-plaintext – attacker chooses all plaintext before any are encrypted ◦ Adaptive chosen plaintext- interactive process, choosing subsequent plaintexts based on previous encyrptions

Attacks Known key – game up Differential cryptanalysis – seeks to find the difference between related encrypted plaintexts – goal is to find the key Linear cryptanalysis – attacker carries out a known plaintext attack on several different messages encrypted with the same key, evaluating the probability of input values ending up in a specific combination

Attacks Side-channel attack – uses physical data to break a cryptosystems, such as monitoring CPU cycles or power consumption used while encrypting or decrypting Replay Attacks – passive – attacker resubmits captured data

PKI – 80% Policy/20% Technology Public Key Infrastructure - programs, data formats, procedures, communication protocols, security policies, and public key cryptographic mechanisms that establish trust levels for communication Digital certificates – signed with the CA’s digital signature Digital Signature Standard (DSS) – NIST standard that specifies the algorithms strong enough to satisfy government use.

PKI – 80% Policy/20% Technology Certificate Authorities (CAs) – Entities (internal or external) that authenticate the identity of the person or organization before issuing a certificate. Certificate Revocation List (CRL) – a list that contains the certificates that have been revoked (not expired). Located in the Repository with the Digital Certificates. Online Certificate Status Protocol (OCSP) – online revocation checking Registration Authority – (RA) – Performs the registration duties/identity-proofing duties for the CA

So You Think You Know PKI? Why do you escrow keys used for confidentiality? Why don’t you escrow keys used for digital signing? What do you call it when a subscriber loses control of his or her private key? What is the difference between suspension and revocation? What version of certificate standard are we presently using? Expired certificates get placed onto a _____?

Key Management Addresses: ◦ Key Escrow ◦ Key Backup ◦ Key Expiration/Rollover ◦ Key Storage ◦ Key Length ◦ Key Lifetime

Key Management Use long keys – the longer the better (but computationally slower) Change the keys often (but not too often as you risk losing access to previously encrypted data). The more the key is used, the more frequently it should be changed. Store and transmit securely Keys should be backed up and escrowed. Keys should be properly destroyed when no longer in use (? !? !? )

X. 509 Digital Certificates

Questions I Know You Know How does Alice get Bob’s Public Key? ◦ Certificate Authority (CA) Repository ◦ Out-of-band transaction ◦ In a digital certificate exchange (i. e. SSL) Isn’t this prone to a Man-in-the-Middle attack? ◦ Only if the recipient is being stupid and not paying attention to the error messages (i. e. Burp. Proxy) What can defeat non-repudiation? ◦ Not protecting the private key’s authentication information (i. e. a soft token/password activated) ◦ Key loggers with soft tokens ◦ Incorrect time stamps (use NTP) So why don’t we just use Asymmetric Encryption? ◦ Slower!!!

And so we meet Bob and Alice Assume Bob and Alice have exchanged public keys (remembering that they zealously guard their private keys) If Bob wants to send Alice a love letter via interoffice mail, which key is used to ensure confidentiality? If he wants to make certain that Alice knows it came from him, which key is used to ensure authenticity?

And so we meet Bob and Alice If a symmetric key is encrypted with a receiver’s public key, what security service is provided? If data is encrypted with sender’s private key, which security service is provided? If sender encrypts data with recipient’s private key, which security service is provided?

Link Encryption vs. End-To-End Encryption Link Encryption (online encryption) ◦ provided by service providers ◦ encrypts all of the data along a communications path ◦ protects against packet sniffers - routing needs to decrypt headers End-to-end encryption ◦ headers, addresses, routing, and trailer information are not encrypted

Email Standards Multipurpose Internet Mail Extension (MIME) – dictates how email attachments are handled Secure MIME (S/MIME) – standard for digitally encrypting and signing email Privacy-Enhanced Mail (PEM) – standard for providing secure email over the Internet Message Security Protocol (MSP) – PEM for military used to secure email messages

Email Standards Pretty Good Privacy – (PGP) ◦ Developed by Phil Zimmerman in 1991 ◦ Public Key Encryption for email ◦ Each user generates and distributes his or her public key and users sign each other’s public keys, creating a web of trust ◦ Uses passphrases to encrypt the users private key that is stored on the hard drive ◦ Users keep a keyring of public keys

Securing the Internet HTTPS/SSL (Secure Sockets Layer) ◦ Developed by Netscape ◦ SSL v 3 is TLS ◦ Secures Web servers as well as used for VPNs S-HTTP ◦ secures individual messages sent between computers Secure Electronic Transaction (SET) ◦ Proposed by VISA and M/C to send encrypted credit card numbers of the Internet Secure Shell (SSH) ◦ Tunneling protocol for connecting to a remote computer (used to secure Telnet, rlogin, FTP, etc. )

Hiding Alternatives

Hiding Alternatives Steganography Digital Watermarking

Steganography A “concealment” cipher Greek steganos (covered or secret) and -graphy (writing or drawing) and thus means, literally, covered writing. The ability to hide data inside another file. Using stego tools today, suspects can hide data and files in jpgs and wav files.

Steganography One of the following images has the airport map hidden below – can you detect which image is the “carrier” file with the hidden data?

Steganography Image A:

Steganography Image B:

Steganography If you guessed Image A – you’d be correct. Image A is a JPEG stego file containing btv_map. gif using a tool called “Camouflage”. Many work by replacing the “least significant bits” in the carrier file with the bits from the target file “Digital Watermarking” – embedded logo – used to verify the owner of the file. ◦ Visible Watermarking – logos or “Draft” ◦ Invisible Watermarking – uses steganography Pictures, by the way, were retrieved from an excellent

IPSec! Internet Protocol Security – suite of protocols for securing IPv 4 and IPv 6 and setting up Virtual Private Network Includes 2 protocols: ◦ Authentication Header (AH) – provides authentication and integrity ◦ Encapsulating Security Payload (ESP) - encryption Each that can be used in 2 modes: ◦ Tunnel mode – used by gateways, encrypts entire packet ◦ Transport mode – only encrypts the data (not the header information AH is used with ESP in transport mode as the original headers are not encrypted Tunnel mode typically uses ESP alone

IPSec Each device has at least one Security Association (SA) that is used to negotiate the ESP or AH parameters Each SA connection is identified by a unique 32 -bit number known as the Security Parameter Index (SPI). The SA process is managed by the Internet Security Association and Key Management Protocol (ISAKMP) Key exchange protocol used is IKE – Internet Key Exchange


Questions An employee allows another employee to have access to his digital signature password. What do you do to his certificate? ◦ ◦ A. Suspend it B. Destroy it C. Revoke it D. Transfer it

Questions An employee allows another employee to have access to his digital signature password. What do you do to his certificate? ◦ ◦ A. Suspend it B. Destroy it C. Revoke it D. Transfer it

Questions Which algorithm provides for key distribution, but does not provide for integrity or nonrepudiation? ◦ ◦ A. Diffie-Helman B. RSA C. AES D. El. Gamal

Questions Which algorithm provides for key distribution, but does not provide for integrity or nonrepudiation? ◦ ◦ A. Diffie-Helman B. RSA C. AES D. El. Gamal

Questions Which type of encryption only uses one shared key to encrypt and decrypt? ◦ ◦ A. B. C. D. Public key Asymmetric Symmetric TCB Key

Questions Which type of encryption only uses one shared key to encrypt and decrypt? ◦ ◦ A. B. C. D. Public key Asymmetric Symmetric TCB Key

Questions Which type of cipher operates in real time on a single character or single bits of data? A. Block B. Rolling C. Stream D. Continuous

Questions Which type of cipher operates in real time on a single character or single bits of data? A. Block B. Rolling C. Stream D. Continuous

Questions Which of the following is not a good choice to secure email? A. PGP B. SSH C. S/MIME D. PEM

Questions Which of the following is not a good choice to secure email? A. PGP B. SSH C. S/MIME D. PEM

Questions Which of the following is NOT an example of symmetric encryption? A. B. C. D. Merkle-Hellman IDEA RC 5 Twofish HINT…. .

Cyrptography Review Which of the following is NOT an example of symmetric encryption? A. B. C. D. Merkle-Hellman IDEA RC 5 Twofish Ralph Merkle, Martin Hellman, Whitfield Diffie

Question: A birthday attack requires a good deal of diligence. What would be the attacker’s goal? A. Facilitate a replay attack in order to authenticate to a system B. Gain unauthorized access to confidential data C. Make undetected changes to a document D. Spoof the source of origin of the sender

Question: A birthday attack requires a good deal of diligence. What would be the attacker’s goal? A. Facilitate a replay attack in order to authenticate to a system B. Gain unauthorized access to confidential data C. Make undetected changes to a document D. Spoof the source of origin of the sender

Question: Ed wants to send Eve a confidential email. Which key is used to accomplish this? ◦ ◦ A. B. C. D. Eva’s private key Eva’s public key Ed’s private key Ed’s public key

Question: Ed wants to send Eve a confidential email. Which key is used to accomplish this? ◦ ◦ A. B. C. D. Eva’s private key Eva’s public key Ed’s private key Ed’s public key

Question: Place the following four steps in the proper order to demonstrate how a digital signature works: 1. Encrypt the digest with your private key. 2. Compare the message digest to the one your created. 3. Generate a message digest. Decrypt the signature with the sender’s public key. A. 4, 2, 1, 3 B. 1, 4, 3, 2 C. 3, 1, 4, 2 D. 3, 4, 2, 1

Question: Place the following four steps in the proper order to demonstrate how a digital signature works: 1. Encrypt the digest with your private key. 2. Compare the message digest to the one your created. 3. Generate a message digest. 4. Decrypt the signature with the sender’s public key. A. 4, 2, 1, 3 B. 1, 4, 3, 2 C. 3, 1, 4, 2 D. 3, 4, 2, 1

Question: Which alogrithms are no longer recommended for use? A. RSA B. DES C. IPSEC D. AES

Questions Which algorithms are no longer recommended for use? A. RSA B. DES C. IPSEC D. AES

Question Storing private keys with a third party is referred to as: A. B. C. D. Key backup Key escrow Key caching Key exchange

Question Storing private keys with a third party is referred to as: A. B. C. D. Key backup Key escrow Key caching Key exchange

Question T or F. Digital Certificates contain a public and private key

Question T or F. Digital Certificates contain a public and private key

Questions Which key length is not supported by AES? A. B. C. D. 128 -bit 192 -bit 256 -bit 512 -bit

Questions Which key length is not supported by AES? A. B. C. D. 128 -bit 192 -bit 256 -bit 512 -bit

El Gamal Which of the following is not a characteristic of the El Gamal algorithm? A. Slow B. Used for digital signatures, encryption, and key agreement C. A public key algorithm D. Extension of Diffie-Hellman

El Gamal Which of the following is not a characteristic of the El Gamal algorithm? A. Slow B. Used for digital signatures, encryption, and key agreement C. A public key algorithm D. Extension of Diffie-Hellman

Question A differential cryptanalysis is: A. An attack where the attacker uses the mathematical structure of the algorithms to reverse engineer the encryption key. B. An attack on the ciphertext itself. C. An attack where the differences in the plaintext and cipertext are compared to find the key value. D. An attack on the plaintext itself.

Question A differential cryptanalysis is: A. An attack where the attacker uses the mathematical structure of the algorithms to reverse engineer the encryption key. B. An attack on the ciphertext itself. C. An attack where the differences in the plaintext and cipertext are compared to find the key value. D. An attack on the plaintext itself.

Question A control for a replay attack would be: A. B. C. D. Use timestamps and sequence numbers. Use digital certificates and digital signatures. Authenticity and integrity checkers. Use private keys and MACs.

Question A control for a replay attack would be: A. B. C. D. Use timestamps and sequence numbers. Use digital certificates and digital signatures. Authenticity and integrity checkers. Use private keys and MACs.

Question A PKI does NOT include: A. B. C. D. Lightweight Directory Access Protocol (LDAP) Timestamping Internet Key Exchange (IKE) Certificate Revocation

Question A PKI does NOT include: A. B. C. D. Lightweight Directory Access Protocol (LDAP) Timestamping Internet Key Exchange (IKE) Certificate Revocation

Question Asymmetric Cryptography provides which of the following security services? A. B. C. D. Confidentiality Integrity Authenticity Non-repudiation

Question Asymmetric Cryptography provides which of the following security services? A. B. C. D. Confidentiality Integrity Authenticity Non-repudiation

Question Which of the following would be a replacement for Telnet, FTP and other insecure protocols when logging in over an untrusted network? A. B. C. D. rlogin SSH S-Telnet TLS

Question Which of the following would be a replacement for Telnet, FTP and other insecure protocols when logging in over an untrusted network? A. B. C. D. rlogin SSH S-Telnet TLS
