Introduction to Cryptography 1 Cryptography Cryptography Original meaning













- Slides: 18

Introduction to Cryptography 1

Cryptography • Cryptography – Original meaning: the art of secret writing – Send information in a way that prevents others from reading it – Other services: • Integrity checking • Authentication – Process data into unintelligible form, reversible, without data loss 2

Encryption/Decryption plaintext encryption ciphertext decryption plaintext • Plaintext: a message in its original form • Ciphertext: a message in the transformed, unrecognized form • Encryption: the process for producing ciphertext from plaintext • Decryption: the reverse of encryption • Key: a secret value used to control encryption/decryption 3

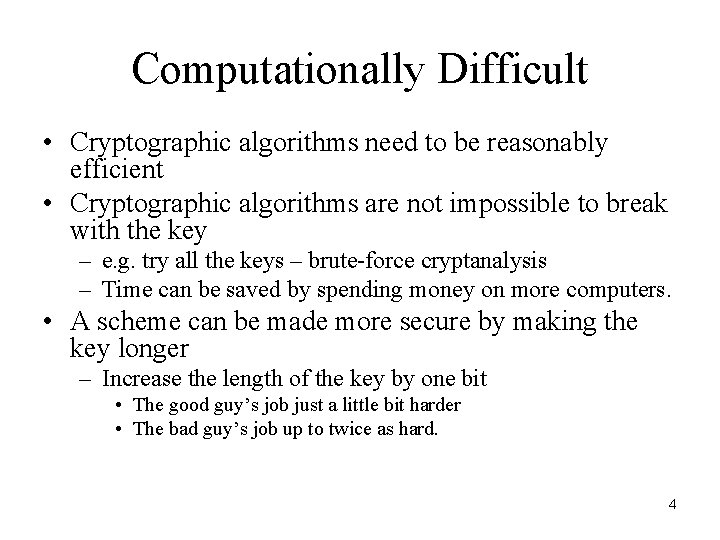
Computationally Difficult • Cryptographic algorithms need to be reasonably efficient • Cryptographic algorithms are not impossible to break with the key – e. g. try all the keys – brute-force cryptanalysis – Time can be saved by spending money on more computers. • A scheme can be made more secure by making the key longer – Increase the length of the key by one bit • The good guy’s job just a little bit harder • The bad guy’s job up to twice as hard. 4

To Publish or Not to Publish • Not to publish the algorithms – We can achieve better security if we keep the algorithm secret – Hard to keep secret if widely used – Reverse Engineering • Publish the algorithms – Security of the algorithms depend on the secrecy of the keys – Less unknown vulnerabilities if all the smart (good) people examine the algorithm • Common practice – Commercial: published – Military: kept secret 5

Some Trivial Cipher • Caesar cipher: – Substitution cipher – Replace each letter with the one 3 letters later – A -> D, O -> R • Caption Midnight Secret Decoder rings – Pick a secret n between 1 and 25 – Shift variable by n: HAL -> IBM if n is 1 • Monoalphabetic cipher – Arbitrary mapping of one letter to another – 26!, approximately 4 x 1026 – Statistical analysis of letter frequencies 6

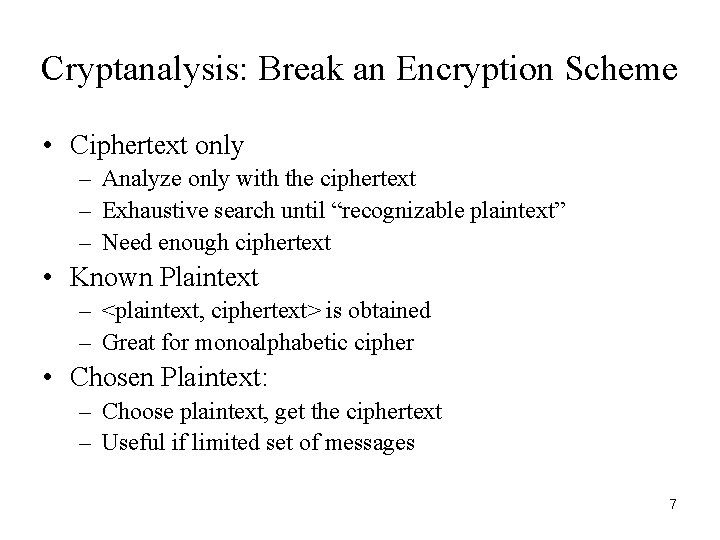
Cryptanalysis: Break an Encryption Scheme • Ciphertext only – Analyze only with the ciphertext – Exhaustive search until “recognizable plaintext” – Need enough ciphertext • Known Plaintext – <plaintext, ciphertext> is obtained – Great for monoalphabetic cipher • Chosen Plaintext: – Choose plaintext, get the ciphertext – Useful if limited set of messages 7

Types of Cryptographic functions • Secret Key Cryptography – One key • Public Key Cryptography – Two keys: public, private • Hash function – No key 8

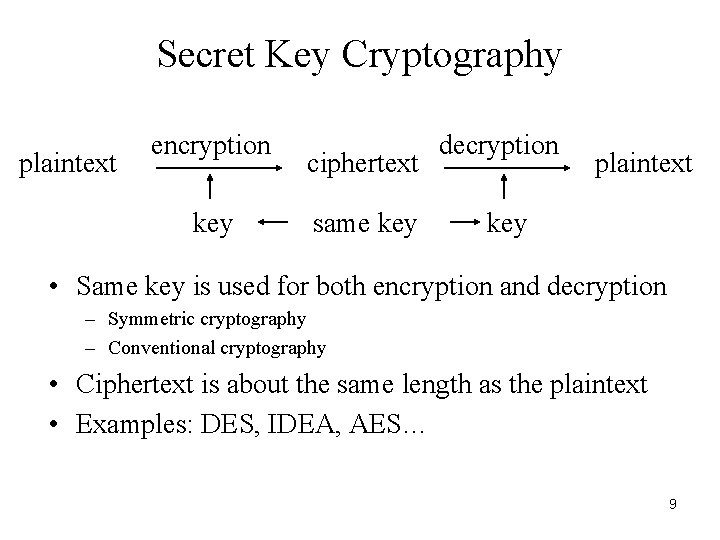
Secret Key Cryptography plaintext encryption key ciphertext same key decryption plaintext key • Same key is used for both encryption and decryption – Symmetric cryptography – Conventional cryptography • Ciphertext is about the same length as the plaintext • Examples: DES, IDEA, AES… 9

Secret Key Cryptography cont’d • Transmitting over an insecure channel – Challenge: how to share the key? • Secure storage on insecure media • Strong Authentication: prove knowledge of a secret without revealing it – Send challenge r, and verify the returned encrypted{r} • Challenge should be chosen from a large pool • Integrity Check: a fixed-length cryptographic checksum for a message – Send MIC (Message Integrity Code) along with the message 10

Public Key Cryptography plaintext encryption ciphertext public key decryption plaintext private key • Invented/published in 1975 • Each individual has two keys: – Private key is kept secret – Public key is publicly known • Much slower than secret key cryptography • Also known as – Asymmetric cryptography 11

Public Key Cryptography cont’d plaintext signing private key • Digital Signature Signed message verification plaintext public key – Only the party with the private key can generate a digital signature – Verification of the signature only requires the knowledge of the public key – The signer cannot deny he/she has done so. 12

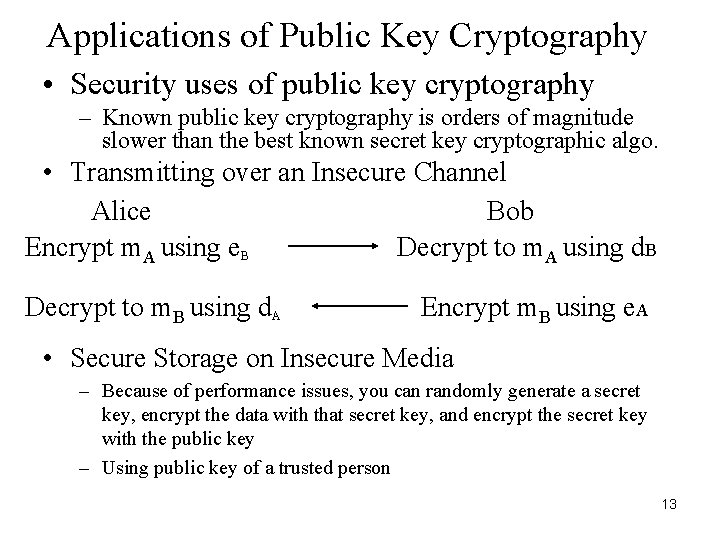
Applications of Public Key Cryptography • Security uses of public key cryptography – Known public key cryptography is orders of magnitude slower than the best known secret key cryptographic algo. • Transmitting over an Insecure Channel Alice Bob Encrypt m. A using e. B Decrypt to m. A using d. B Decrypt to m. B using d. A Encrypt m. B using e. A • Secure Storage on Insecure Media – Because of performance issues, you can randomly generate a secret key, encrypt the data with that secret key, and encrypt the secret key with the public key – Using public key of a trusted person 13

Applications of Public Key Cryptography • Authentication – No need to store secrets, only public keys. – Alice wants to verify Bob’s identity Alice Encrypt r using eb Bob Decrypt to r using db r – Secret key cryptography: need to share secret key for every person to communicate with 14

Case Study: Applications of Public Key Cryptography in SSH 2 • Assume that bsun@galaxy 1. cs. lamar. edu tries to log into mensa. cs. lamar. edu as bsun: – Run “ssh-keygen” at galaxy 1. cs. lamar. edu – Copy the generated public key in id_rsa. pub to. /ssh/authorized_keys in mensa. cs. lamar. edu – id_rsa (at galaxy 1. cs. lamar. edu) holds the generated private key 15

Applications of Public Key Cryptography • Digital Signatures • Authorship: Prove who generate the information • Integrity: the information has not been modified • Non-repudiation: cannot do with secret key cryptography 16

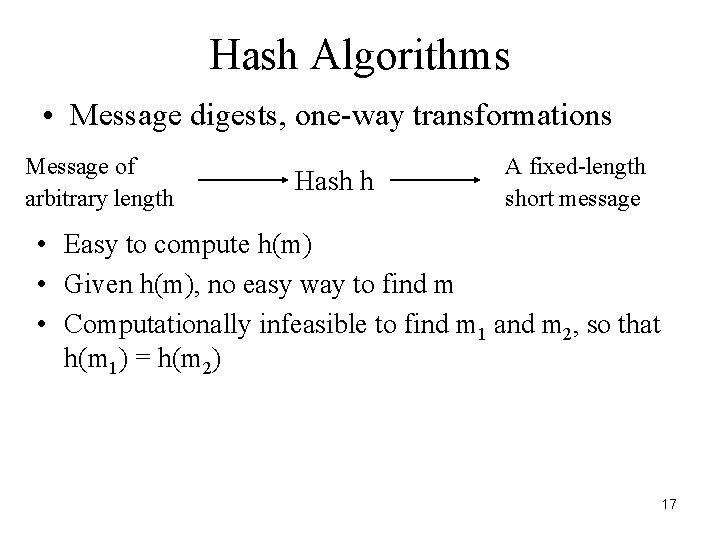
Hash Algorithms • Message digests, one-way transformations Message of arbitrary length Hash h A fixed-length short message • Easy to compute h(m) • Given h(m), no easy way to find m • Computationally infeasible to find m 1 and m 2, so that h(m 1) = h(m 2) 17

Applications of Hash Algorithms • Password hashing – Store the hash of the password • Message integrity – Keyed Hash • Alice and Bob agree on a secret key k • Alice computes h(m|k) and sends it with m • Does not require encryption • Message Fingerprint – For a large data structure: save the message digest of the data on the tamper-proof backing store. • Digital Signature Efficiency – Compute a message digest and sign it • Public key algorithms are processor-intensive 18