Linear Cryptanalysis of DES M Matsui 1 Linear







- Slides: 16

Linear Cryptanalysis of DES M. Matsui. 1. Linear Cryptanalysis Method for DES Cipher. EUROCRYPT 93, 1994. 2. The first experimental cryptanalysis of the Data Encryption Standard. CRYPT 0 94, 1994.

Linear Approximations •

Using Linear Approximations of DES •

Using Linear Approximations of DES How do we find linear approximations in DES? • consider 3 -round DES, without IP and IP-1. • start with an S-BOX – S 5.

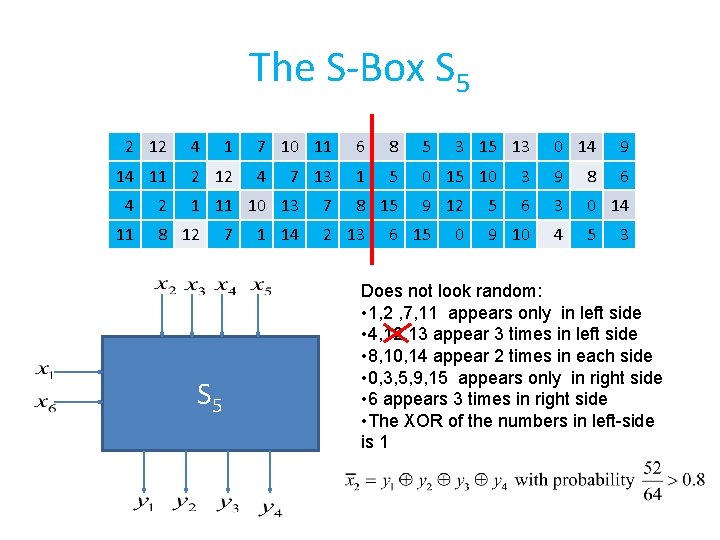
The S-Box S 5 2 12 14 11 2 4 1 2 12 7 10 11 6 8 5 4 1 5 0 15 10 9 12 7 13 1 11 10 13 8 12 S 5 7 1 14 7 8 15 2 13 6 15 3 15 13 0 0 14 9 3 9 8 6 6 3 0 14 9 10 4 5 5 3 Does not look random: • 1, 2 , 7, 11 appears only in left side • 4, 12, 13 appear 3 times in left side • 8, 10, 14 appear 2 times in each side • 0, 3, 5, 9, 15 appears only in right side • 6 appears 3 times in right side • The XOR of the numbers in left-side is 1

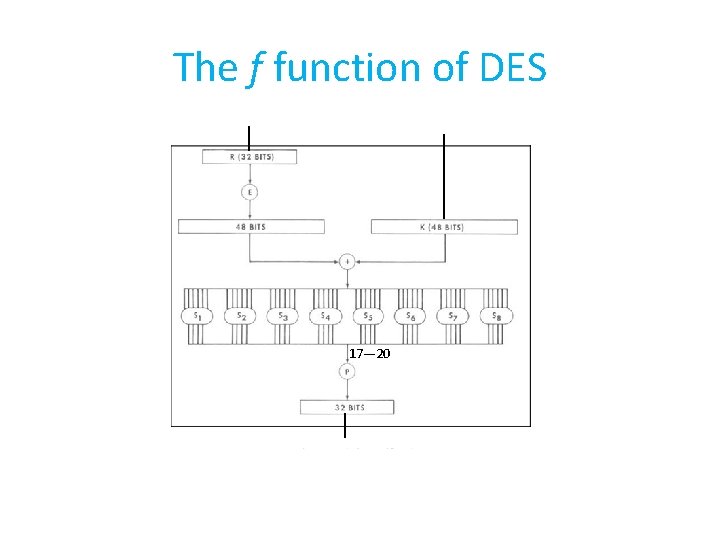
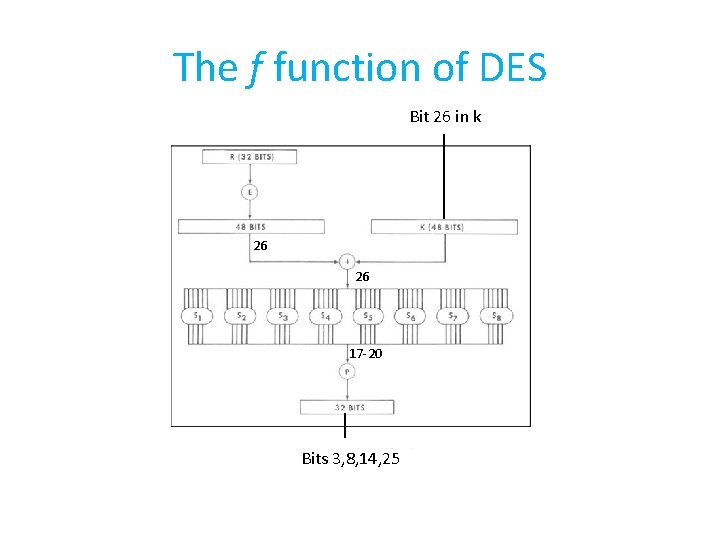
The f function of DES 17— 20

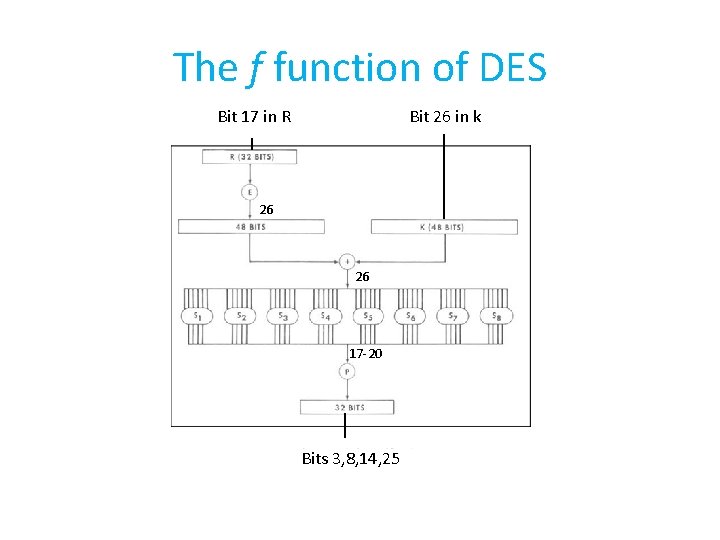
The permutation P We need to trace the bits 17 -20 that come from to S 5 After P they are bits 3, 8, 14, 25 16 7 20 21 29 12 28 17 1 15 23 26 5 18 31 10 2 8 24 14 32 27 3 9 19 13 30 6 22 11 4 25

The f function of DES Bit 26 in k 26 26 17 -20 Bits 3, 8, 14, 25

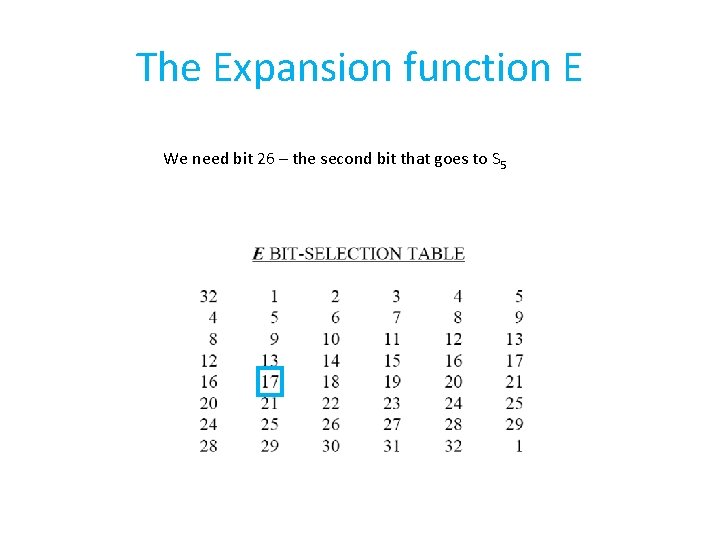
The Expansion function E We need bit 26 – the second bit that goes to S 5

The f function of DES Bit 17 in R Bit 26 in k 26 26 17 -20 Bits 3, 8, 14, 25

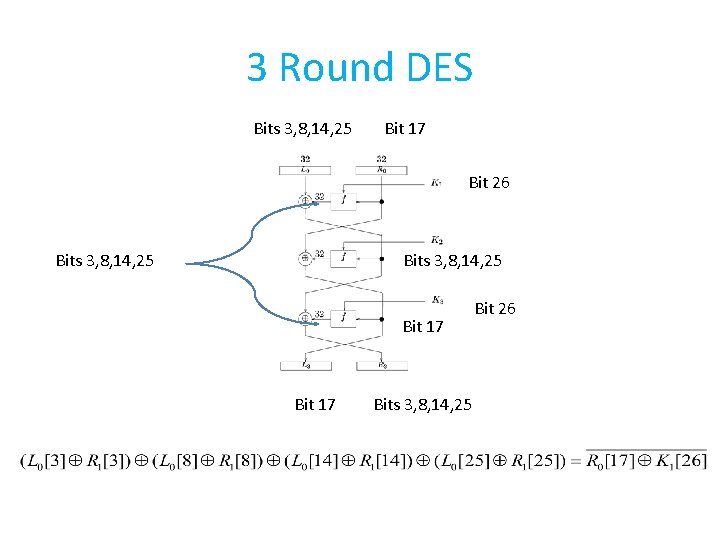
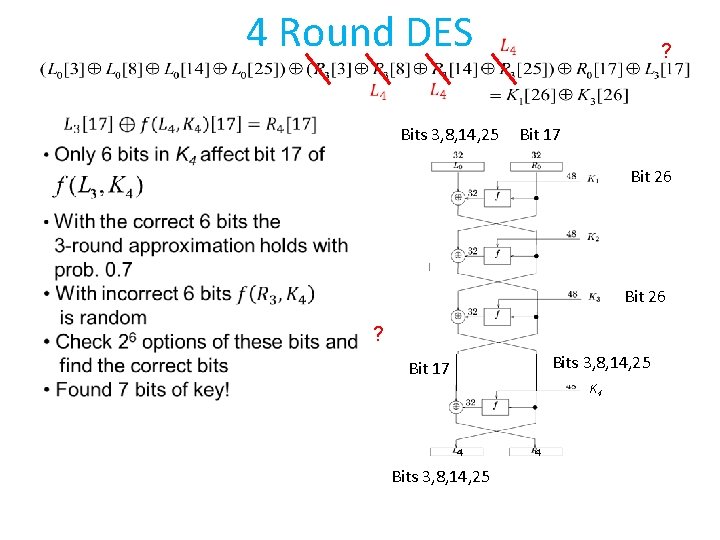
3 Round DES Bits 3, 8, 14, 25 Bit 17 Bit 26 Bits 3, 8, 14, 25 Bit 17 Bits 3, 8, 14, 25 Bit 26

The Attack on 3 Round DES • From first round with probability 52/64 • From third round with probability 52/64 • Thus, with probability (52/64) 2+(12/64)2 0. 7 • Finds one bit of the key

Linear cryptanalysis: Learning One Bit • If a bit of the outputs has a 1/2+p linear approximation in i-round DES, then – Get O(1/p 2) message, encryption pairs • For each pair compute “the bit” of the key • Take the value that appears more times • Get correct value with high probability • Learn one bit of key • Can do better…

4 Round DES ? Bits 3, 8, 14, 25 Bit 17 Bit 26 K K Bit 26 ? Bits 3, 8, 14, 25 Bit 17 K 4 4 Bits 3, 8, 14, 25 4

Linear cryptanalysis • If a bit of the outputs has a 1/2+p linear approximation in i-round DES, then we choose O(1/p 2) messages in (i+1)-round DES and compute 7 bits of the key. • Can do the same trick with first round and last i -rounds, get another 7 bits • Use exhaustive search to find the other 42 bits.

Known Attacks • 8 rounds: 221 plaintexts (40 seconds) • 12 rounds: 233 plaintexts (50 hours) • 16 rounds: 243 plaintexts (50 days, 12 computers) – Uses two 14 -rounds approximation – Using each approximation it finds 13 bits – Finds 30 bits by exhaustive search