Crime Prevention Part II Crime Prevention in the







![The Internet "As the Internet [ Internet expands], more and more commerce takes place The Internet "As the Internet [ Internet expands], more and more commerce takes place](https://slidetodoc.com/presentation_image_h/74d1229d36651e056a0839c873a947d5/image-8.jpg)


























































- Slides: 81

Crime Prevention Part II Crime Prevention in the TECHNOLOGY AGE Institute for Criminal Justice Studies ©TCLEOSE Course #2102 Crime Prevention Curriculum Part II is the intellectual property of CSCS-ICJS (2009)

The Technology Age: Tips to Keep Your Information Safe and Secure National Crime Prevention Council 2008

Goal of This Presentation To teach you as a Crime Prevention Practitioner how to inform Practitioner communities of various types of online information theft and security risks and to provide safety risks tips to help adults have a safe and tips secure experience online

LEARNING OBJECTIVES • Learning Objective: The student will be able to Objective: describe, identity and explain technology theft and explore ways in which criminals access information. • Learning Objective: The student will be able to learn Objective: and explain tips to keep information secure from theft. • Learning Objective: The student will be able to explain Objective: facts regarding Internet Service Providers and the security of your personal information • Learning Objective: The student will be able to identify Objective: and explain how newsgroups, personal web pages, and web browsing expose and jeopardize personal information • Learning Objective: The student will be able to Objective: understand, identify and explain how spyware, spamming, and phishing collect personal information and how you can protect yourself from them

LEARNING OBJECTIVES • Learning Objective: The student will be able to identify Objective: and explain tips for safe and secure emailing. • Learning Objective: The student will be able to identify Objective: and explain ways to shop safely online. • Learning Objective: The student will be able to Objective: recognize online auction fraud and recommend ways to avoid it • Learning Objective: The student will be able to identify, Objective: explain and recommend tips for secure wireless and home computing

The INTERNET

The Internet is a powerful resource. Benefits of the Internet include being able to; Access and share information Communicate with ease Conduct financial transactions Plan trips and vacations Conduct business Learn—it’s the world’s largest library Shop Have fun
![The Internet As the Internet Internet expands more and more commerce takes place The Internet "As the Internet [ Internet expands], more and more commerce takes place](https://slidetodoc.com/presentation_image_h/74d1229d36651e056a0839c873a947d5/image-8.jpg)
The Internet "As the Internet [ Internet expands], more and more commerce takes place in it. It only makes sense that more criminal activity would take place, and it does allow this anonymous ability for criminals to do it…. . . “Greg Regan, U. S. Secret Service

How Much Information Is Truly Available? There is an enormous amount of information available on the available Internet. Think about the type of business, transactions, and informationtransactions sharing you conduct online. sharing

Crime Fighting Goes Online As a result of the Internet, criminals have found a new place to prowl. Within the last five years, cybercrime has really grown.

In 2006, the FBI Computer Crime Survey estimated annual losses from all types of from computer crime at crime $67 billion a year!

The Numbers 81% of our home computers lack basic protection. AOL and the National Cyber Security Alliance, Online Safety Study, December 2005

The Numbers Each time someone is caught by a phishing scam, it costs about $850. – Consumer Reports, State of the Net 2008, August 2008 Last year, identity theft hurt 8. 9 million Americans and cost each victim an average of $6, 383. – Javelin Strategy and Research, 2008 Identity Fraud Survey Consumer Report

Identity Theft

What Is Identity Theft? Stealing the identity of another person and using it to conduct a variety of activities

What Is Identity Theft? The intent is to use that identity for personal gain, generally with the intent to defraud others by establishing credit, running up debt, or taking over existing financial accounts

Why Worry About Identity Theft? One in 33 households discovered at least one instance of identity theft during the last 6 months. Households headed by persons ages 18– 24 and households with the highest incomes were the most likely victims of identity theft. One in five victimized households spent at least one month resolving problems resulting from Identity theft.

Where and How Do Criminals Get My Information? Theft (or “borrowing”) of your wallet, purse, or personal files, most often by someone you know Telephone calls asking you to “update records” Theft of incoming bills showing account numbers Theft of outgoing mail and bill payments

Where and How Do Criminals Get My Information? (continued) Redirected mail Phishing Rummaging through trash Discarded or unattended credit card receipts or second impressions of credit cards If your mail is delivered to a place where others can easily access it

How to Protect Yourself From Identity Theft Do not give out personal information. Shred all documents that contain personal information or keep them locked in a cabinet. Minimize the number of identification cards you carry. Protect your Social Security Number Don’t risk it, shred it

From commercial to home use!

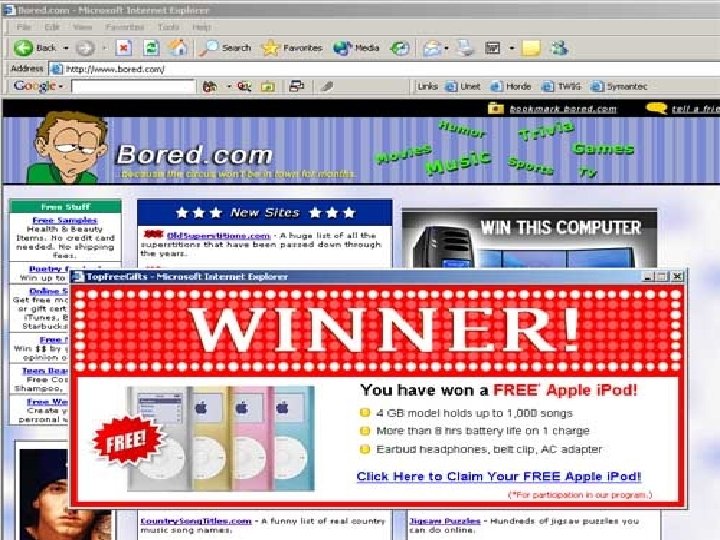
How to Protect Yourself From Identity Theft (continued) Protect your computer from online intruders Install firewalls Install antivirus software Avoid free stuff Keep your security programs up-todate Create complex usernames and passwords


How to Prevent Identity Theft (continued) Be careful about phone card and ATM machine usage Protect your credit card number(s) Make a list or make a photocopy of all your credit cards, both sides. Order your free credit reports at annualcreditreport. com

Steps to Take if You Are a Victim 1. Place a fraud alert on your credit reports, and review your credit reports 2. Close the accounts that you believe have been compromised or opened 3. File a complaint with the Federal Trade Commission, www. ftc. gov; www. ftc. gov 1877 -ID-THEFT (438 -4338); 4. File a report with your local police or the police in the community where the identity theft took place.

Your Internet Service Provider (ISP)

Facts About Your ISP People can find out details about your Internet presence by using an old UNIX command known as "finger. ” “Finger” allows people to ask your ISP who its customers are.

Facts About Your ISP Check your contract with your ISP to make sure that it won't sell your information to others.

Newsgroups, Personal Web Pages, and Web Browsing

What Is a Newsgroup or Blog? A newsgroup is a discussion group that focuses on a particular topic. Blogs have replaced some of the uses of newsgroups.


Bloggers BEWARE! Posting a message to a blog or newsgroup lets everyone in the world know that you exist, as well as what some of your specific interests are.

Bloggers BEWARE! If you have a signature file that includes your address and telephone number, everyone has access to that data. These messages stay on the Internet for an indefinite period of time.

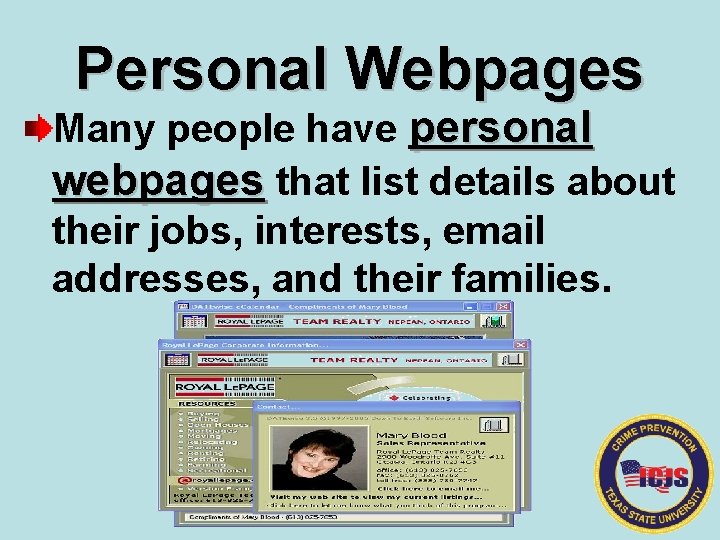
Personal Webpages Many people have personal webpages that list details about their jobs, interests, email addresses, and their families.

Personal Webpages Try to limit the personal information and pictures on your webpage. Remember, the information is available for the entire world to see. Companies that want to spam you now have access to that information.

Web Browsing Web browsing leaves tracks all over cyberspace, considered live “footprints. ” Whenever you visit a website, the site records that you were there. Consider configuring your web browser to ask you before accepting cookies.


Web Browsing Site asks you to volunteer personal information. Assume that the information is available to the world. Web browsers maintain a cache file that keeps the recent images and text that you have viewed, similar to your history files on your personal computer.

What is Spyware?

What Is Spyware and How Does It Work? Spyware, also called adware, is adware software that is designed to track your every move online through a variety of techniques including; Recording your keystrokes Tracking the websites you visit Stealing your online passwords Burying you with pop-up ads

Results of Spyware? Loss of privacy More advertising Home page hijacking Reduced performance Security risks System instability

How to Protect Yourself From Spyware Install a program to block spyware Install a program to remove spyware Avoid pop-ups Avoid the “free” stuff “free” Take advantage of your ISP’s security “free” downloads

Protecting Yourself From Spam and Phishing

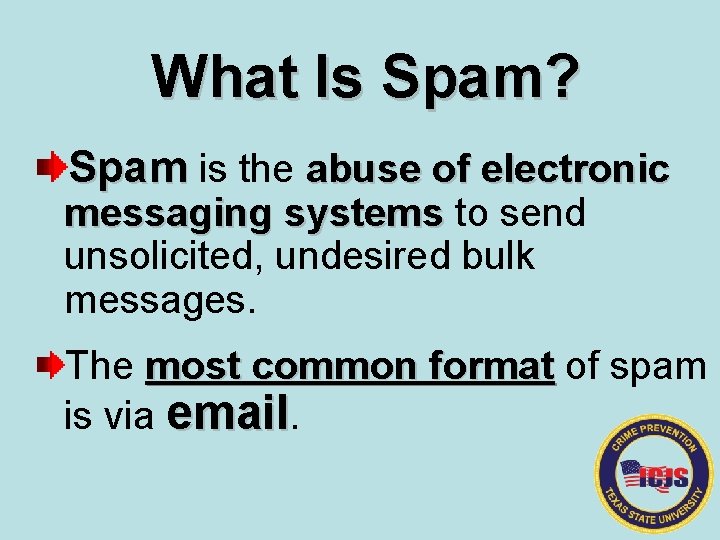
What Is Spam? Spam is the abuse of electronic messaging systems to send systems unsolicited, undesired bulk messages. The most common format of spam format is via email.

SPAM PORN

What Is Spam? Spam email topics include low-cost drugs, investment scams, and porn. Phishing is email that steals.


Tips to Protect and Limit Spam Maintain a spam email account. Never reply to phishing emails. Don't open spam emails. Screen for spam. Get a spam filter. Get unlisted.

Email Protection Tips

How Many Email Addresses Should I Have? Many… Personal: For friends and family Business: For coworkers and business associates Secure: For secure information Disposable: For spamming sites


E-mail Protection: Encryption If you want to prevent people from reading your email messages (and files on your computer), you can get an email and data encryption software package


Shopping Safely Online

Online Shopping Tips Shop with companies you know and always initiate the transaction Keep your password private Use a secure browser Pay by credit card Keep personal information private Save all transaction https//www. information

Online Auction Fraud www. ripoff. com

Facts About Online Auctions Millions of people take part in Internet auctions every day. Survey said: online auction fraud Survey is the number one fraud committed over the Internet, with an average loss of $1, 531 per consumer. Source: National Consumers League, 2008 Survey www. nclnet. org

How Auction Fraud Works Failure to deliver goods Nonpayment for goods delivered Misrepresentation of the merchandise Hidden charges Fake bidding Credit card fraud Black market goods Bogus escrow services

Online Auction Safety Tips Understand how the auction works Check out the seller before you bid Be careful if the seller is a private individual Be cautious if the seller is from another country Seller who tries to raise Beware of “shills” sale price artificially by making fictitious bids himself!

Online Auction Safety Tips (continued) USE CAUTION: Collectibles and CAUTION other expensive items VERIFY: Delivery, returns, VERIFY warranties, & service (before you pay) VERIFY: information on the auction VERIFY site about insurance Pay by credit card by Look for bonded sellers

Online Auction Safety Tips (continued) Consider using an escrow service for expensive purchases Try mediation to resolve disputes Inform auction sites about suspected fraud Source: National Consumers League’s Internet Fraud Watch www. fraud. org

General Safety Tips When Computing at Home

Home Computing Safety Tips Overview Secure your computer Use a website rating service Safeguard private information Turn on parental controls Consider biometric security

General Safety Tips When Computing Wireless


Wireless Safety Tips Overview Get wireless protection Have complete, updated security sweep for spyware, viruses, etc. Obtain a virtual private network Use computer locks Obtain biometric security

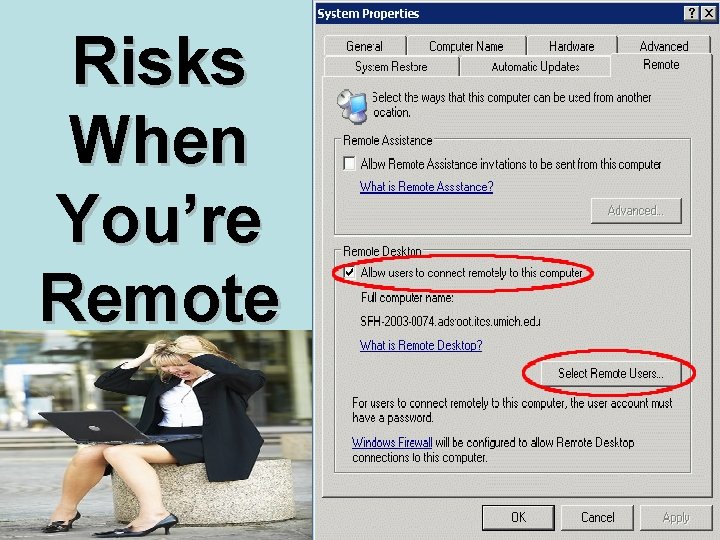
Risks When You’re Remote

Dangers of Wireless No wires, no security As easy as eavesdropping Beware of rogue hotspots

Safeguards and Solutions Encryption is the key. Avoid connecting to any Wi-Fi network unless you either know it’s network legitimate and secure or you can set up a secure VPN connection. Make sure your personal firewall on your laptop is turned on and updated.

Safeguards and Solutions Avoid using websites that require password access when using a wireless hotspot Look around when you are online for prying eyes Keep your laptop with you at all times

DEFINE & PROCESS • Describe identity theft and explore ways in which criminals access information • How can one keep information secure from theft • Explain how newsgroups, personal web pages, and web browsing expose and jeopardize personal information • What can one do for safe and secure emailing • Explain ways to shop safely online • How can you recognize online auction fraud and list some ways to avoid it • What did you learn about secure wireless and home computing • Explain how spyware, spamming, and phishing collect personal information and how you can protect yourself from them

Resources

Resources National Crime Prevention Council www. nccp. org NCPC has a comprehensive Identity Theft campaign. Learn how you can keep your identity to yourself. Order a copy of Preventing Identity Theft: A Guide for Consumers or download it in PDF format. Other resources include Reproducible brochures — Identity Theft (PDF) and Protecting (PDF) Your Privacy (PDF) Article — Evolving with Technology Newspaper Mats — ID Theft (PDF) and Seniors and Fraud (PDF)

Resources National Crime Prevention Council (continued) Public service campaigns that focus on cyber-security and safety Partners including the Forum to Advance the Mobile Experience (FAME) and the Chief Marketing Officer Council (CMO Council) Download tip sheets and the publication Mind What You Do Online, report Internet crimes, and visit the security store www. bytecrime. org

Resources Identity Theft Resource Center www. identitytheft. org Justice Department Identity Theft www. usdoj. gov/criminal/fraud/website/idtheft. html National Criminal Justice Reference Service www. ncjrs. org/spotlight/identity_theft/summary. html

Resources Internet Safety and Ethics Cyber. Angels www. cyberangles. org Get. Net. Wise www. getnetwise. org Internet Keep Safe Coalition www. ikeepsafe. org Wired Safety www. wiredpatrol. org

Resources Telecommunications Fraud Federal Trade Commission www. ftc. gov Federal Communications Commission www, fcc. gov National Fraud Information Center www. fraud. org National Consumers League www. nclnet. org

Resources Safe Home Computing About. com www. netsecurity. about. com National Cyber Security Alliance www. staysafepnline. info

The National Crime Prevention Council 2345 Crystal Drive Fifth Floor Arlington, VA 22202 202 -466 -6272 FAX 202 -296 -1356 www. ncpc. org

Contact Information Institute for Criminal Justice Studies 350 N. Guadalupe, Suite 140, PMB 164 San Marcos, Texas 78666. ©TCLEOSE Course #2101 Crime Prevention Curriculum Part I is the intellectual property of CSCS-ICJS (2009)

S E E Y O U T O MO R R O W ! 8: 00 AM – Ready to LEARN More! THAT’S ALL FOLKS!
 Primary prevention secondary prevention tertiary prevention
Primary prevention secondary prevention tertiary prevention 25 situational crime prevention techniques
25 situational crime prevention techniques Victimization theory
Victimization theory Ron clarke 1992
Ron clarke 1992 Malaysia crime prevention foundation
Malaysia crime prevention foundation Crime prevention institute
Crime prevention institute Saps sandton
Saps sandton Crime prevention 9th edition
Crime prevention 9th edition National crime prevention council cyberbullying
National crime prevention council cyberbullying Developmental crime prevention
Developmental crime prevention Target hardening crime prevention
Target hardening crime prevention Cyber crime prevention luxembourg
Cyber crime prevention luxembourg Situational crime prevention definition
Situational crime prevention definition Gấu đi như thế nào
Gấu đi như thế nào Thiếu nhi thế giới liên hoan
Thiếu nhi thế giới liên hoan Vẽ hình chiếu vuông góc của vật thể sau
Vẽ hình chiếu vuông góc của vật thể sau Một số thể thơ truyền thống
Một số thể thơ truyền thống Các châu lục và đại dương trên thế giới
Các châu lục và đại dương trên thế giới Thế nào là hệ số cao nhất
Thế nào là hệ số cao nhất Hệ hô hấp
Hệ hô hấp Tư thế ngồi viết
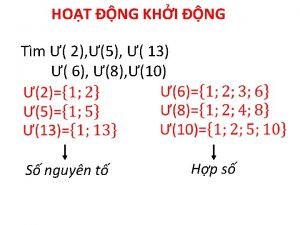
Tư thế ngồi viết Số.nguyên tố
Số.nguyên tố Hát kết hợp bộ gõ cơ thể
Hát kết hợp bộ gõ cơ thể đặc điểm cơ thể của người tối cổ
đặc điểm cơ thể của người tối cổ Cách giải mật thư tọa độ
Cách giải mật thư tọa độ Thang điểm glasgow
Thang điểm glasgow ưu thế lai là gì
ưu thế lai là gì Thẻ vin
Thẻ vin Cái miệng nó xinh thế
Cái miệng nó xinh thế Thơ thất ngôn tứ tuyệt đường luật
Thơ thất ngôn tứ tuyệt đường luật Các châu lục và đại dương trên thế giới
Các châu lục và đại dương trên thế giới Từ ngữ thể hiện lòng nhân hậu
Từ ngữ thể hiện lòng nhân hậu Bổ thể
Bổ thể Tư thế ngồi viết
Tư thế ngồi viết Diễn thế sinh thái là
Diễn thế sinh thái là Lp html
Lp html Giọng cùng tên là
Giọng cùng tên là Làm thế nào để 102-1=99
Làm thế nào để 102-1=99 Hát lên người ơi
Hát lên người ơi Hổ sinh sản vào mùa nào
Hổ sinh sản vào mùa nào đại từ thay thế
đại từ thay thế Vẽ hình chiếu vuông góc của vật thể sau
Vẽ hình chiếu vuông góc của vật thể sau Công thức tính độ biến thiên đông lượng
Công thức tính độ biến thiên đông lượng Thế nào là mạng điện lắp đặt kiểu nổi
Thế nào là mạng điện lắp đặt kiểu nổi Tỉ lệ cơ thể trẻ em
Tỉ lệ cơ thể trẻ em Lời thề hippocrates
Lời thề hippocrates Các loại đột biến cấu trúc nhiễm sắc thể
Các loại đột biến cấu trúc nhiễm sắc thể Vẽ hình chiếu đứng bằng cạnh của vật thể
Vẽ hình chiếu đứng bằng cạnh của vật thể Phản ứng thế ankan
Phản ứng thế ankan Quá trình desamine hóa có thể tạo ra
Quá trình desamine hóa có thể tạo ra Môn thể thao bắt đầu bằng từ chạy
Môn thể thao bắt đầu bằng từ chạy Khi nào hổ mẹ dạy hổ con săn mồi
Khi nào hổ mẹ dạy hổ con săn mồi điện thế nghỉ
điện thế nghỉ Thế nào là sự mỏi cơ
Thế nào là sự mỏi cơ Trời xanh đây là của chúng ta thể thơ
Trời xanh đây là của chúng ta thể thơ Part part whole addition
Part part whole addition Footed wares
Footed wares Unit ratio definition
Unit ratio definition The part of a shadow surrounding the darkest part
The part of a shadow surrounding the darkest part Brainpop ratios
Brainpop ratios Part to part variation
Part to part variation What is a technical description
What is a technical description Secu virginia
Secu virginia Puncture resistant container
Puncture resistant container Tabletop foodservice equipment on legs
Tabletop foodservice equipment on legs International standards on drug use prevention
International standards on drug use prevention Prevention and control of poliomyelitis
Prevention and control of poliomyelitis European centre for disease prevention and control
European centre for disease prevention and control Sport prevention plus wellness
Sport prevention plus wellness Junos network secure
Junos network secure Fall prevention interventions
Fall prevention interventions Questioning attitude human performance
Questioning attitude human performance Levels of prevention of diabetes mellitus
Levels of prevention of diabetes mellitus Accident prevention signs and tags training ppt
Accident prevention signs and tags training ppt Chapter 19 disease transmission and infection prevention
Chapter 19 disease transmission and infection prevention Colorado division of fire prevention and control jprs
Colorado division of fire prevention and control jprs Defect prevention
Defect prevention Secondary prevention
Secondary prevention Health promotion and levels of disease prevention
Health promotion and levels of disease prevention The global prevention project
The global prevention project Identity theft prevention program
Identity theft prevention program Méthode itamami
Méthode itamami