Positioning Juniper Network Security 1 Copyright 2015 Juniper






































- Slides: 90

Positioning Juniper Network Security 1 Copyright © 2015 Juniper Networks, Inc.

Agenda Juniper Security Vision – Software Defined Secure Networks Trends, Solutions, Use Cases and Deployments Juniper Security Services Portfolio Positioning Juniper Security Hardware Juniper Security Management Sizing Juniper Security 2 Copyright © 2015 Juniper Networks, Inc.

Software-Defined Secure Networks Juniper’s Innovation in Secure Enterprise Networks

Threats are Everywhere Perimeter security isn’t enough. Malware walks in with your employee! Stop Threats. Faster. Increasing sophistication Increasing variability Threats are already inside Keeping data secure throughout your network is key! 4 Copyright © 2016 Juniper Networks, Inc.

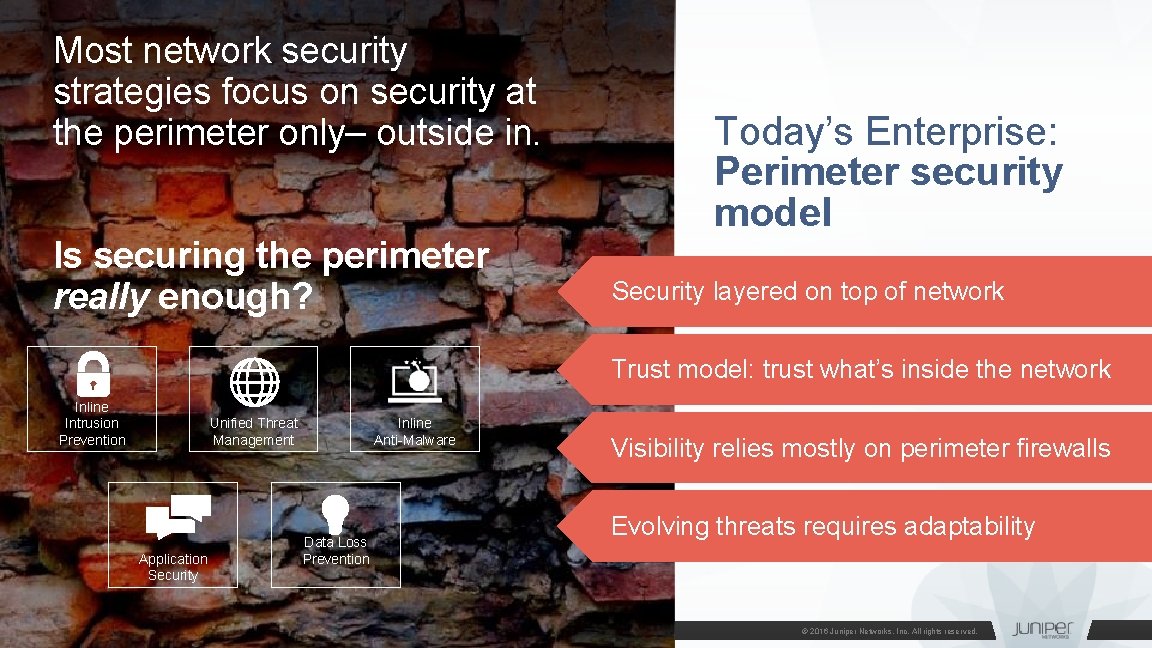
Most network security strategies focus on security at the perimeter only– outside in. Is securing the perimeter really enough? Today’s Enterprise: Perimeter security model Security layered on top of network Trust model: trust what’s inside the network Inline Intrusion Prevention Unified Threat Management Application Security 5 JUNIPER NETWORKS CONFIDENTIAL Inline Anti-Malware Data Loss Prevention Visibility relies mostly on perimeter firewalls Evolving threats requires adaptability © 2016 Juniper Networks, Inc. All rights reserved.

A Change in Mindset Stop talking about Network Security. Start talking about Secure Networks. Realize threats are everywhere. They are already inside. They walked in your front door Recognize perimeter security isn’t enough Detection and Enforcement should be enabled anywhere Acknowledge security is everyone’s problem – horizontal and vertical 6 Copyright © 2016 Juniper Networks, Inc.

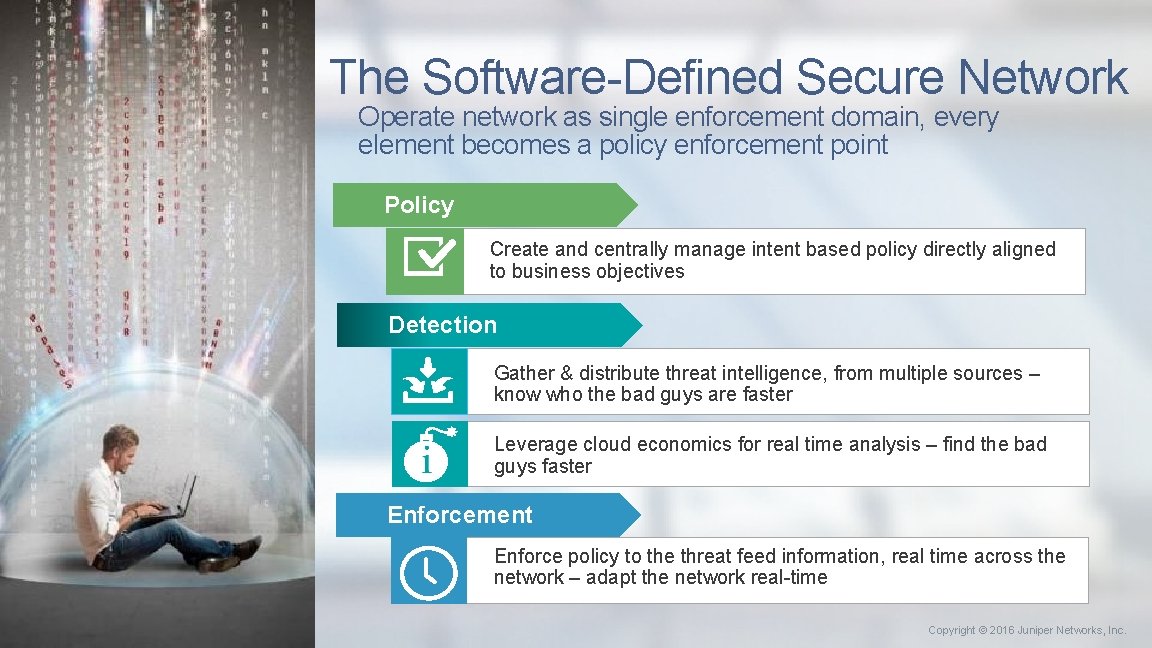
The Software-Defined Secure Network Operate network as single enforcement domain, every element becomes a policy enforcement point Policy Create and centrally manage intent based policy directly aligned to business objectives Detection Gather & distribute threat intelligence, from multiple sources – know who the bad guys are faster Leverage cloud economics for real time analysis – find the bad guys faster Enforcement Enforce policy to the threat feed information, real time across the network – adapt the network real-time 7 Copyright © 2016 Juniper Networks, Inc.

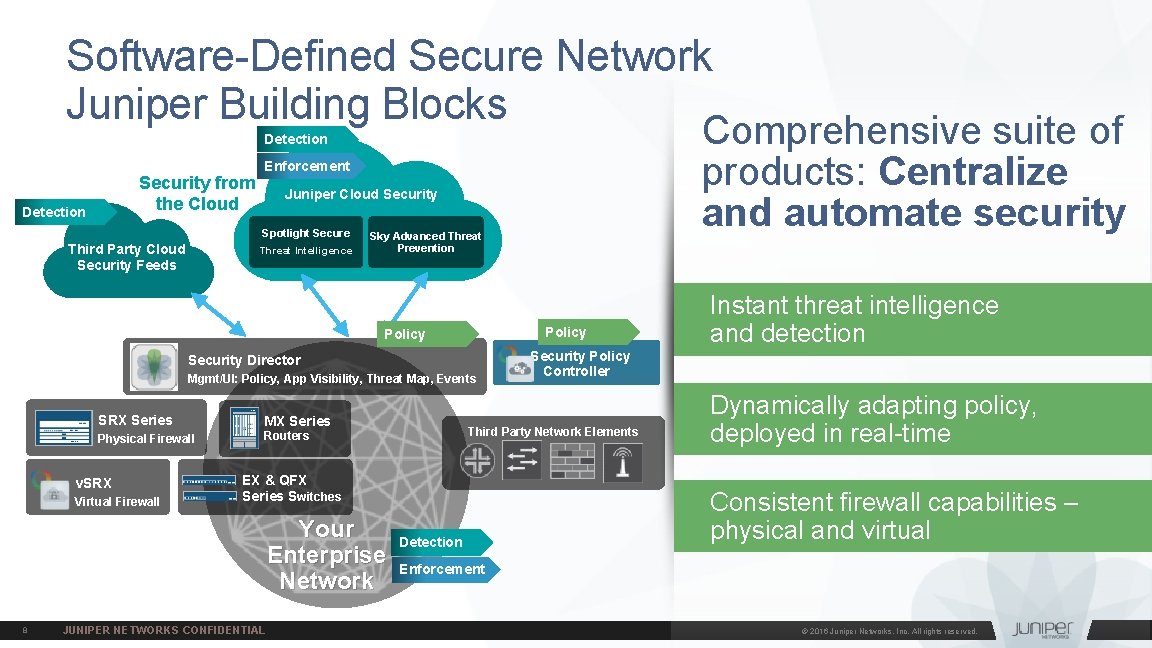
Software-Defined Secure Network Juniper Building Blocks Comprehensive suite of products: Centralize and automate security Detection Security from the Cloud Detection Enforcement Juniper Cloud Security Spotlight Secure Threat Intelligence Third Party Cloud Security Feeds Sky Advanced Threat Prevention Policy Security Director Mgmt/UI: Policy, App Visibility, Threat Map, Events SRX Series MX Series Physical Firewall Routers v. SRX Virtual Firewall Your Enterprise Network 8 JUNIPER NETWORKS CONFIDENTIAL Security Policy Controller Third Party Network Elements EX & QFX Series Switches Detection Instant threat intelligence and detection Dynamically adapting policy, deployed in real-time Consistent firewall capabilities – physical and virtual Enforcement © 2016 Juniper Networks, Inc. All rights reserved.

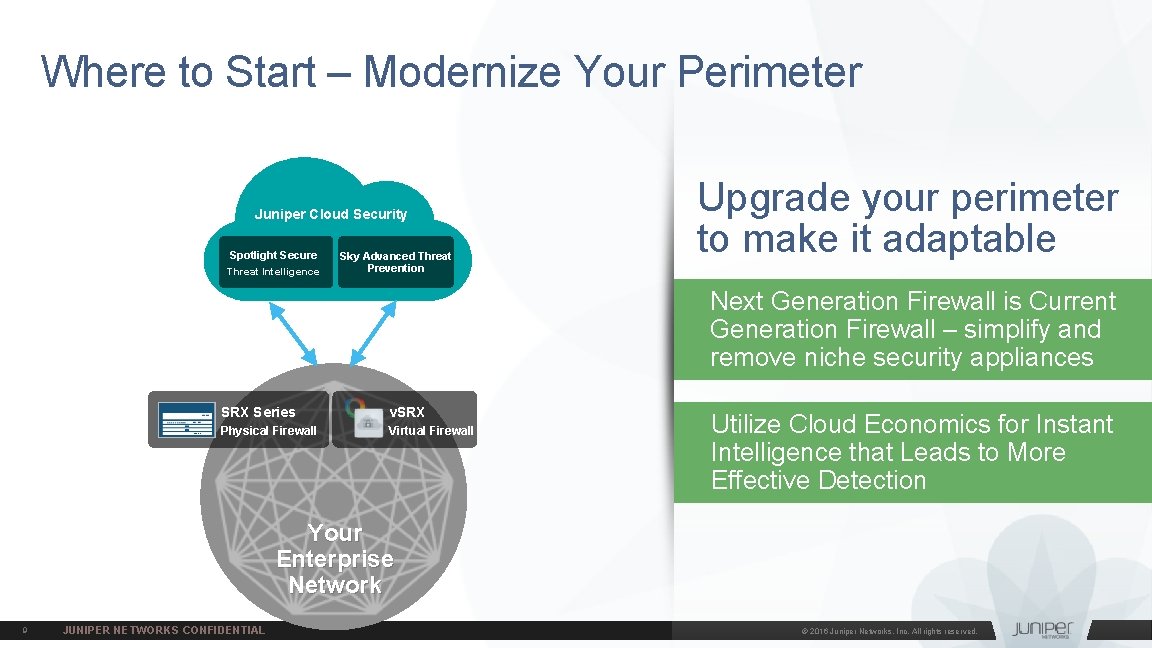
Where to Start – Modernize Your Perimeter Juniper Cloud Security Spotlight Secure Threat Intelligence Sky Advanced Threat Prevention Upgrade your perimeter to make it adaptable Next Generation Firewall is Current Generation Firewall – simplify and remove niche security appliances SRX Series v. SRX Physical Firewall Virtual Firewall Utilize Cloud Economics for Instant Intelligence that Leads to More Effective Detection Your Enterprise Network 9 JUNIPER NETWORKS CONFIDENTIAL © 2016 Juniper Networks, Inc. All rights reserved.

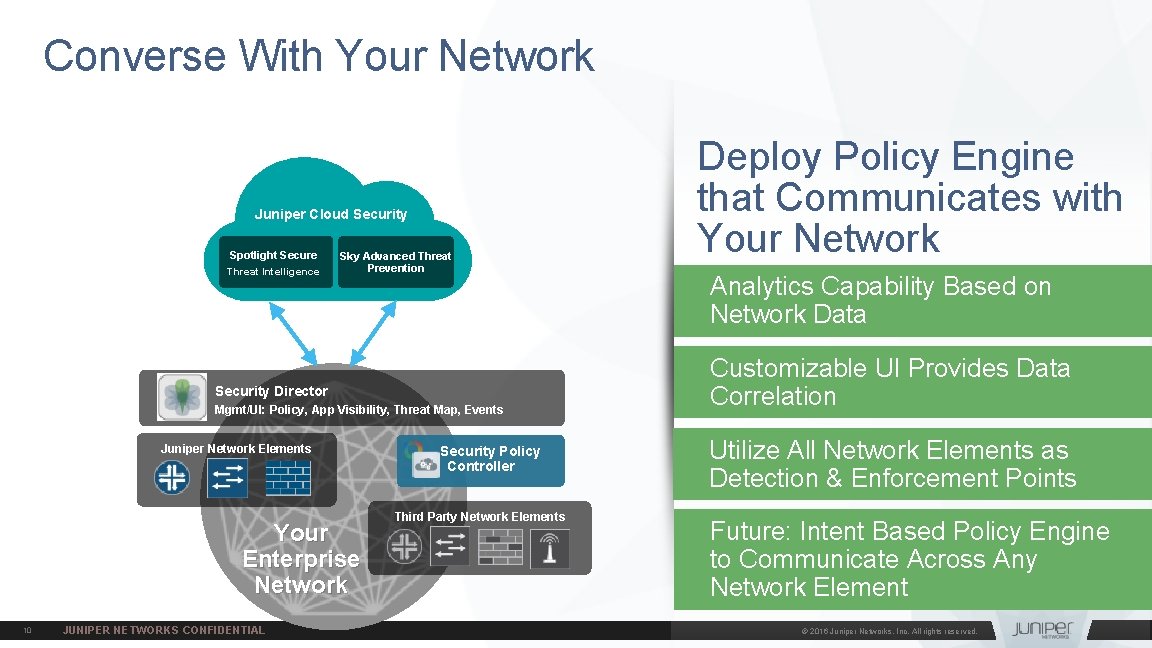
Converse With Your Network Juniper Cloud Security Spotlight Secure Threat Intelligence Sky Advanced Threat Prevention Security Director Mgmt/UI: Policy, App Visibility, Threat Map, Events Juniper Network Elements Your Enterprise Network 10 JUNIPER NETWORKS CONFIDENTIAL Security Policy Controller Third Party Network Elements Deploy Policy Engine that Communicates with Your Network Analytics Capability Based on Network Data Customizable UI Provides Data Correlation Utilize All Network Elements as Detection & Enforcement Points Future: Intent Based Policy Engine to Communicate Across Any Network Element © 2016 Juniper Networks, Inc. All rights reserved.

Juniper’s Security Vision From Network Security to Secure Networks Only one in the industry with building blocks for tomorrow’s Software-Defined Secure Network § Simplified Policy and Management across all network elements § Adaptable Security Solution based on real time threat intelligence information § Cost Effective Detection and Enforcement utilizing the entire network to protect you The Juniper Software-Defined Secure Network dynamically adapts to changing threat landscape…so you don’t have to! Copyright © 2014 Juniper Networks, Inc.

Software-Defined Secure Networks Executive Summary Story Outline and Components Today’s layered security model (based on perimeter security) is not enough to protect against new sophisticated threats and the increasing surface area of possible attacks. SDSN is the future of network security by embracing SDN by leveraging the cloud to solve current network security issues more effectively. SDSN evolves the old guard security mindset around policy, detection, and enforcement. The main components include: 1. Leveraging the network as points of threat detection and enforcement. 2. Leveraging the economy of cloud to share threat intelligence at scale to accelerate and adapt detection. 3. Implementing a centralized controller/policy engine to dynamically adapt policy that stays ahead of constantly evolving threats and attacks. The Software Defined Secure Networks BDM Presentation

Software-Defined Secure Networks Video https: //www. youtube. com/watch? v=d. TMGw 5 Byi 8 E&feature=youtu. be

Industry Trends and Drivers 14 Copyright © 2015 Juniper Networks, Inc.

Market Situation Hackers are popping up everywhere Security incident every 7 minutes $ Cost increasing per security incident Data breaches – 6 successful per day Source: Verizon 2015 Data Breach Investigation Report. 15 Copyright © 2015 Juniper Networks, Inc.

Cybercrime Happens 60% of initial compromises took 1 minute or less time 43% of companies experienced a data breach in the past year $12 M 16 Average cost due to data breach Results in… Increased cost Lost revenue Reputation damage Performance degradation Heavy fines Career limiting Copyright © 2015 Juniper Networks, Inc.

Industry Drivers for Cyber Security Growth Compliance • Regulatory • Governance Protection • Theft • Brand reputation • Intellectual property • Customer data • Employee data Coverage • New threat vectors • New malware “Stay off the Front Page” 17 Copyright © 2015 Juniper Networks, Inc.

Solutions, Use Cases and Deployments 18 Copyright © 2015 Juniper Networks, Inc.

Security Problems Change Based on What You Are Protecting Enterprise Branch Offices • Increasing attacks and eavesdropping • Increasing application monitoring/control • Fewer local knowledgeable resources • Local and cloud assets need protecting • Wide range of security needs depending on what goes on in the branch 19 Enterprise Regional Offices • Growing data breaches Data Centers and Cloud • Increased cyber attacks • Unpredictable traffic volumes • Application availability critical Copyright © 2015 Juniper Networks, Inc.

Focus of this Deck Enterprise Branch Offices Enterprise Regional Offices *Data Center and Cloud Positioning deck coming soon 20 Copyright © 2015 Juniper Networks, Inc.

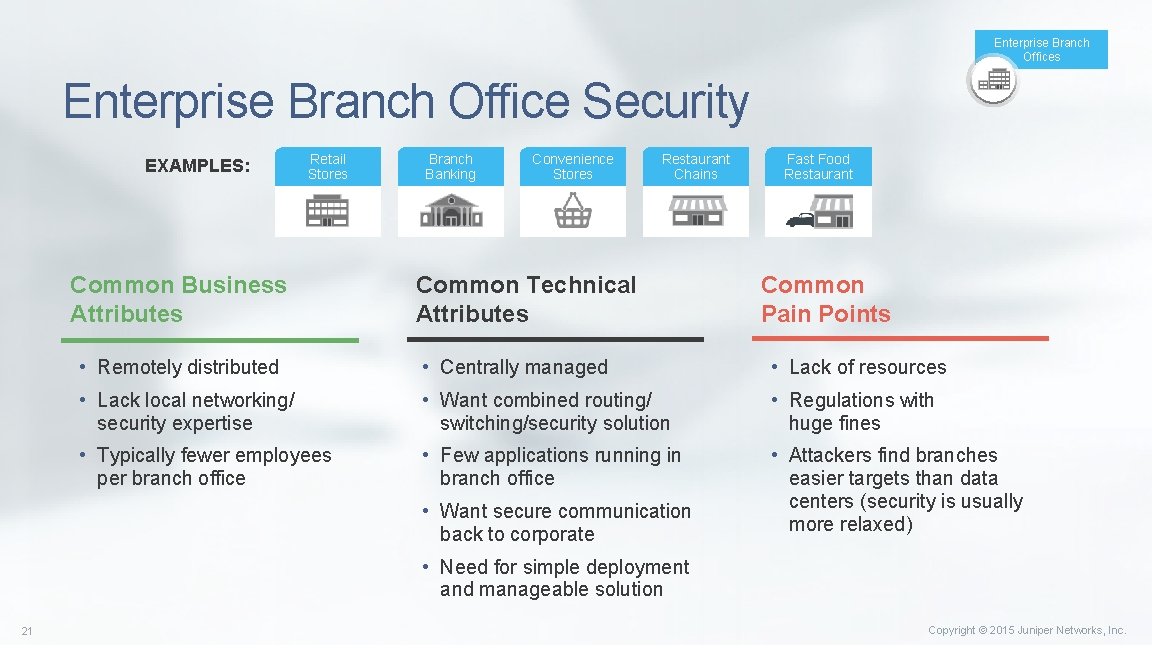
Enterprise Branch Offices Enterprise Branch Office Security EXAMPLES: Retail Stores Common Business Attributes Branch Banking Convenience Stores Restaurant Chains Common Technical Attributes Fast Food Restaurant Common Pain Points • Remotely distributed • Centrally managed • Lack of resources • Lack local networking/ security expertise • Want combined routing/ switching/security solution • Regulations with huge fines • Typically fewer employees per branch office • Few applications running in branch office • Attackers find branches easier targets than data centers (security is usually more relaxed) • Want secure communication back to corporate • Need for simple deployment and manageable solution 21 Copyright © 2015 Juniper Networks, Inc.

Enterprise Branch Offices Needs for a Secure Connected Branch Security Devices Deployment Options Connectivity Focused on go-to-market and management Encrypted traffic Prioritizes local applications Protects data in transit 22 Sold by partners/direct sales and managed by headquarters Sold and managed by service provider as managed service with Customer Premise Equipment (CPE) Copyright © 2015 Juniper Networks, Inc.

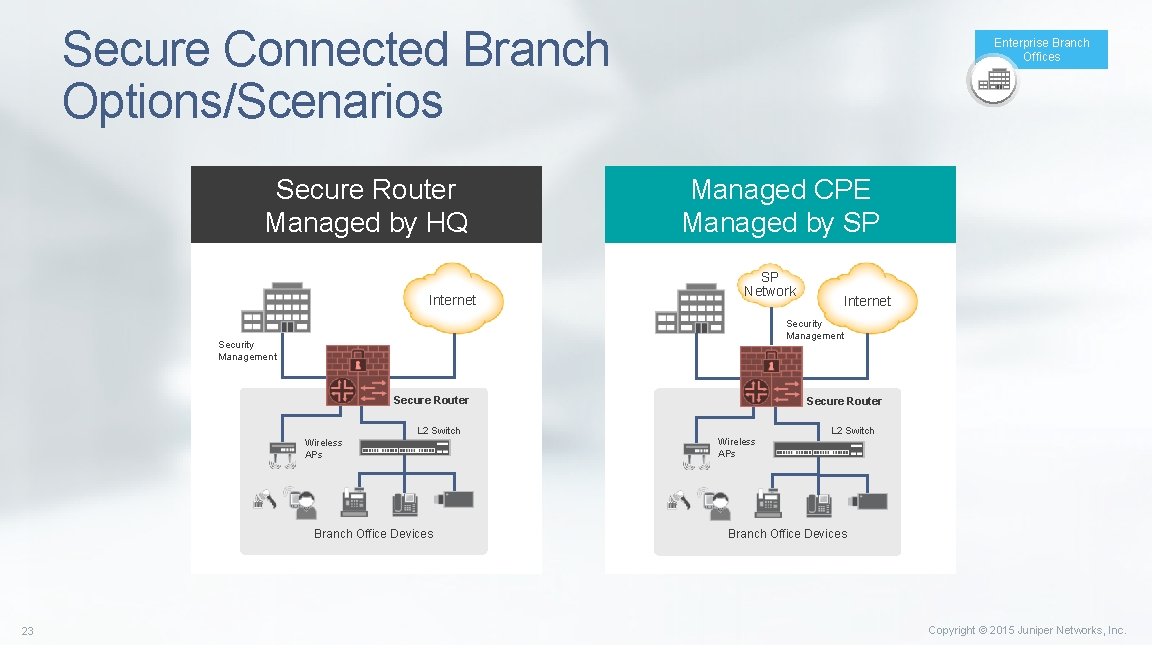
Secure Connected Branch Options/Scenarios Secure Router Managed by HQ Internet Enterprise Branch Offices Managed CPE Managed by SP SP Network Security Management Secure Router L 2 Switch Wireless APs Branch Office Devices 23 Internet L 2 Switch Wireless APs Branch Office Devices Copyright © 2015 Juniper Networks, Inc.

Enterprise Regional Offices Enterprise Regional Office Security EXAMPLES: Regional Office College Campus Common Business Attributes • Fewer remotely distributed offices • Larger buildings/campuses • May have local networking/ security expertise • More knowledge workers 24 Headquarters Financial Institutions Enterprise Campus Common Technical Attributes • Managed locally or centrally • Dedicated security appliance separate from router • Many various applications run network Insurance Real Estate Hospitals Common Pain Points • Manual processes, human error, policy misconfigurations • Application visibility, especially due to encrypted traffic • Network performance • Want to maximize threat protection Copyright © 2015 Juniper Networks, Inc.

Enterprise Regional Offices Needs for a Secure Enterprise Edge Security Devices Use Case: NGFW Deployment Options Create, manage and enforce security policy Services include some or all Firewall, Application Control, Intrusion Prevention, User Firewall, Anti-Virus, Anti-Spam, URL Filtering, Threat Intelligence Feeds, Sandboxing, Honeypots In-line – visibility, blocking, networking Application, user and network visibility Protection of network assets, users and data 25 Secure wire – visibility, blocking, no networking Out-of-band – visibility, no blocking, no networking Copyright © 2015 Juniper Networks, Inc.

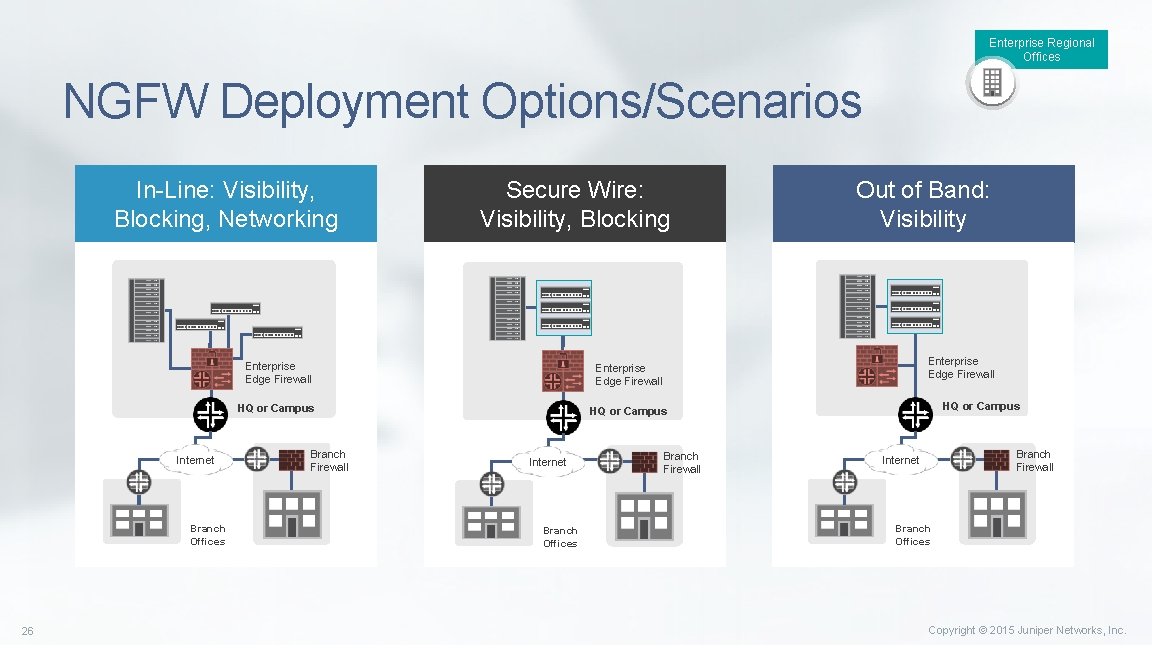
Enterprise Regional Offices NGFW Deployment Options/Scenarios In-Line: Visibility, Blocking, Networking Internet Branch Offices 26 Secure Wire: Visibility, Blocking Enterprise Edge Firewall HQ or Campus Branch Firewall Internet Branch Offices Out of Band: Visibility Branch Firewall HQ or Campus Branch Firewall Internet Branch Offices Copyright © 2015 Juniper Networks, Inc.

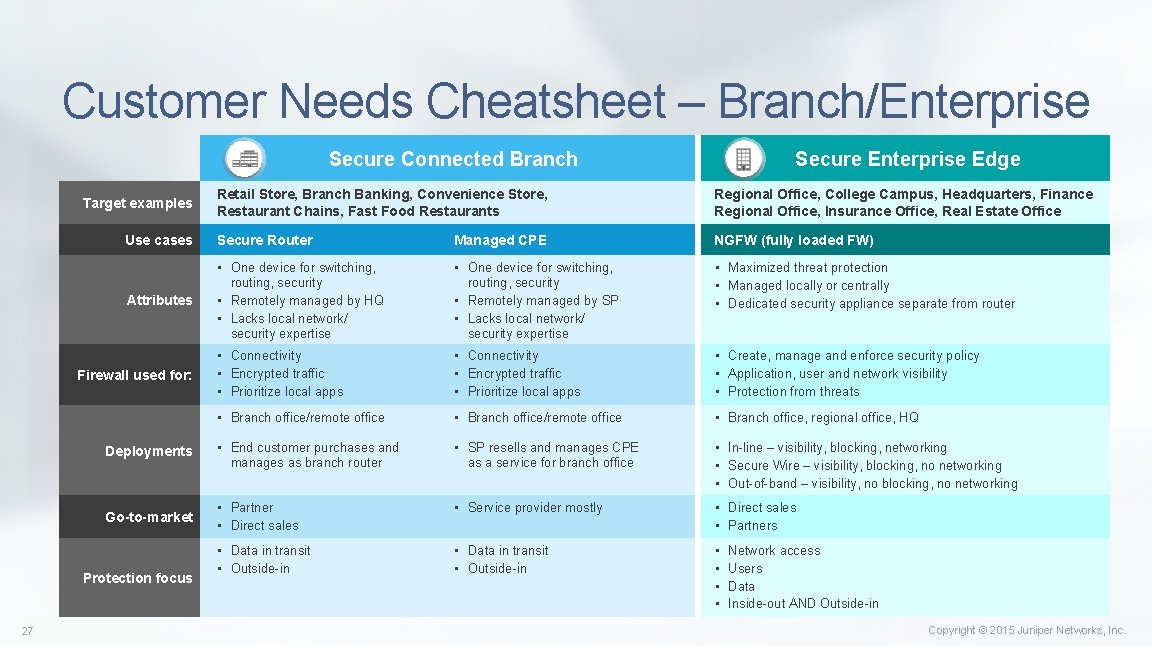
Customer Needs Cheatsheet – Branch/Enterprise Secure Connected Branch Retail Store, Branch Banking, Convenience Store, Restaurant Chains, Fast Food Restaurants Regional Office, College Campus, Headquarters, Finance Regional Office, Insurance Office, Real Estate Office Use cases Secure Router Managed CPE NGFW (fully loaded FW) Attributes • One device for switching, routing, security • Remotely managed by HQ • Lacks local network/ security expertise • One device for switching, routing, security • Remotely managed by SP • Lacks local network/ security expertise • Maximized threat protection • Managed locally or centrally • Dedicated security appliance separate from router • Connectivity • Encrypted traffic • Prioritize local apps • Create, manage and enforce security policy • Application, user and network visibility • Protection from threats • Branch office/remote office • Branch office, regional office, HQ Deployments • End customer purchases and manages as branch router • SP resells and manages CPE as a service for branch office • In-line – visibility, blocking, networking • Secure Wire – visibility, blocking, no networking • Out-of-band – visibility, no blocking, no networking Go-to-market • Partner • Direct sales • Service provider mostly • Direct sales • Partners • Data in transit • Outside-in • • Target examples Firewall used for: Protection focus 27 Secure Enterprise Edge Network access Users Data Inside-out AND Outside-in Copyright © 2015 Juniper Networks, Inc.

Focus of this Deck Data Centers and Cloud *Enterprise Branch and Enterprise Regional Office seen in a different deck 28 Copyright © 2015 Juniper Networks, Inc.

Data Center/Cloud Every Company Has Data • Data is stored somewhere, no matter how big or small the company • Depending on company strategy – sometimes centrally located, sometimes distributed in the cloud, often both (whether they mean to or not) • Data is backed up (hopefully) in separate location • Data must be protected at rest, in use and in transit • Protection of data is on the top of mind for companies – board room discussions “Stay off the Front Page” 29 Copyright © 2015 Juniper Networks, Inc.

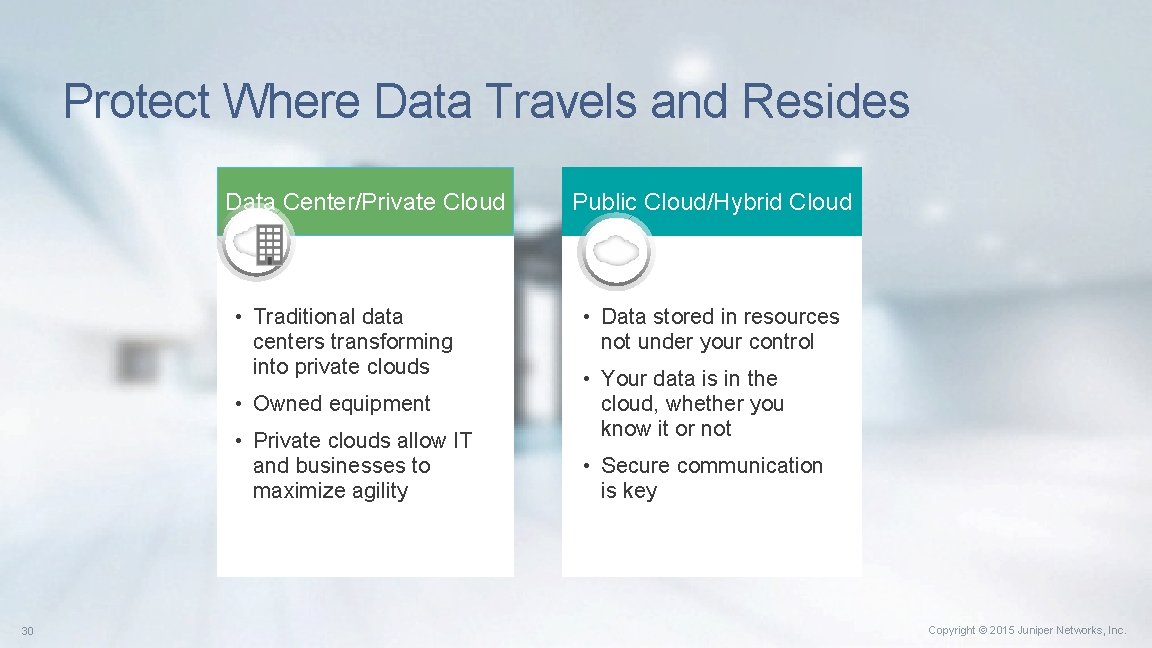
Protect Where Data Travels and Resides Data Center/Private Cloud • Traditional data centers transforming into private clouds • Owned equipment • Private clouds allow IT and businesses to maximize agility 30 Public Cloud/Hybrid Cloud • Data stored in resources not under your control • Your data is in the cloud, whether you know it or not • Secure communication is key Copyright © 2015 Juniper Networks, Inc.

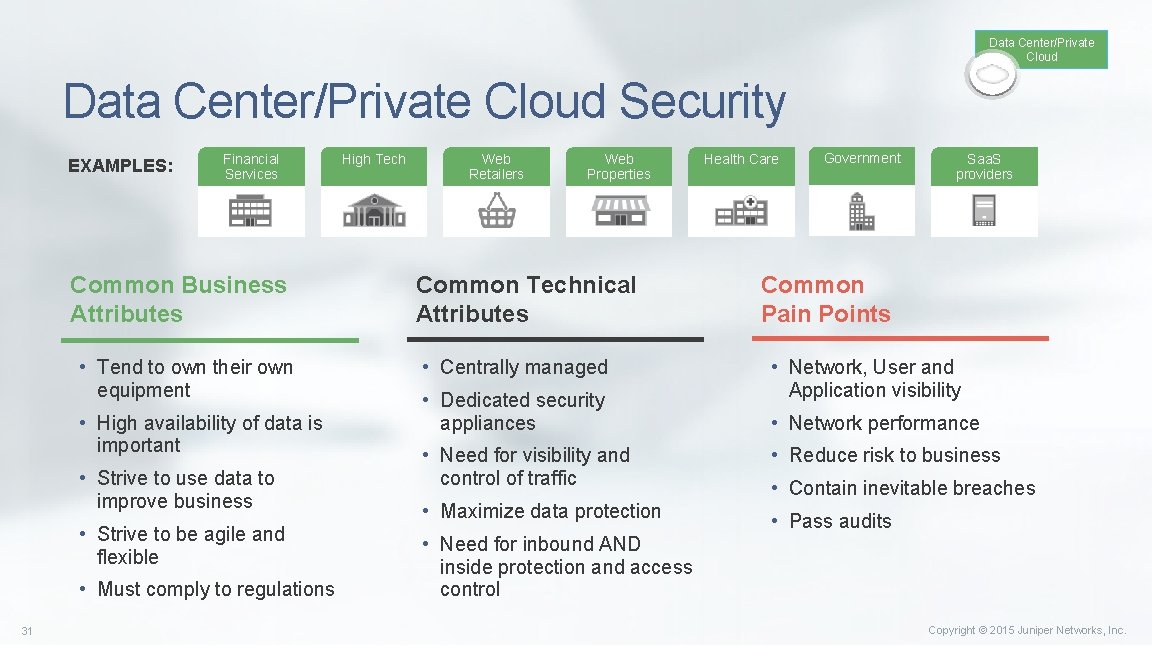
Data Center/Private Cloud Security EXAMPLES: Financial Services Common Business Attributes • Tend to own their own equipment • High availability of data is important • Strive to use data to improve business • Strive to be agile and flexible • Must comply to regulations 31 High Tech Web Retailers Web Properties Common Technical Attributes • Centrally managed • Dedicated security appliances Health Care Government Saa. S providers Common Pain Points • Network, User and Application visibility • Network performance • Need for visibility and control of traffic • Reduce risk to business • Maximize data protection • Pass audits • Need for inbound AND inside protection and access control • Contain inevitable breaches Copyright © 2015 Juniper Networks, Inc.

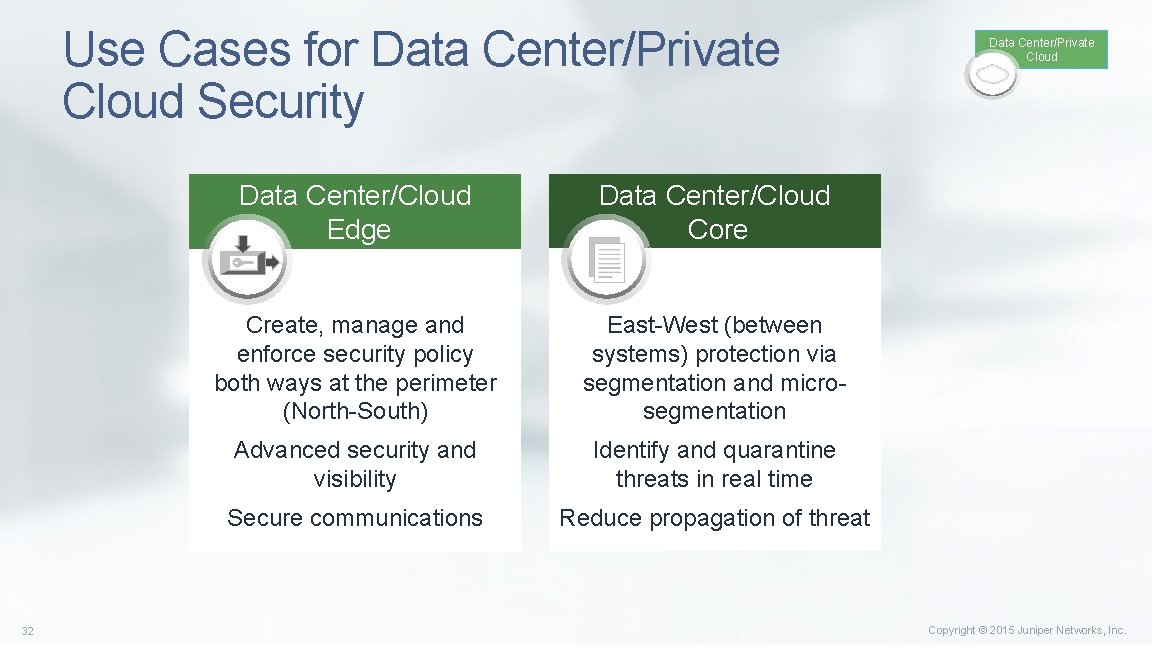
Use Cases for Data Center/Private Cloud Security 32 Data Center/Cloud Edge Data Center/Cloud Core Create, manage and enforce security policy both ways at the perimeter (North-South) East-West (between systems) protection via segmentation and microsegmentation Advanced security and visibility Identify and quarantine threats in real time Secure communications Reduce propagation of threat Data Center/Private Cloud Copyright © 2015 Juniper Networks, Inc.

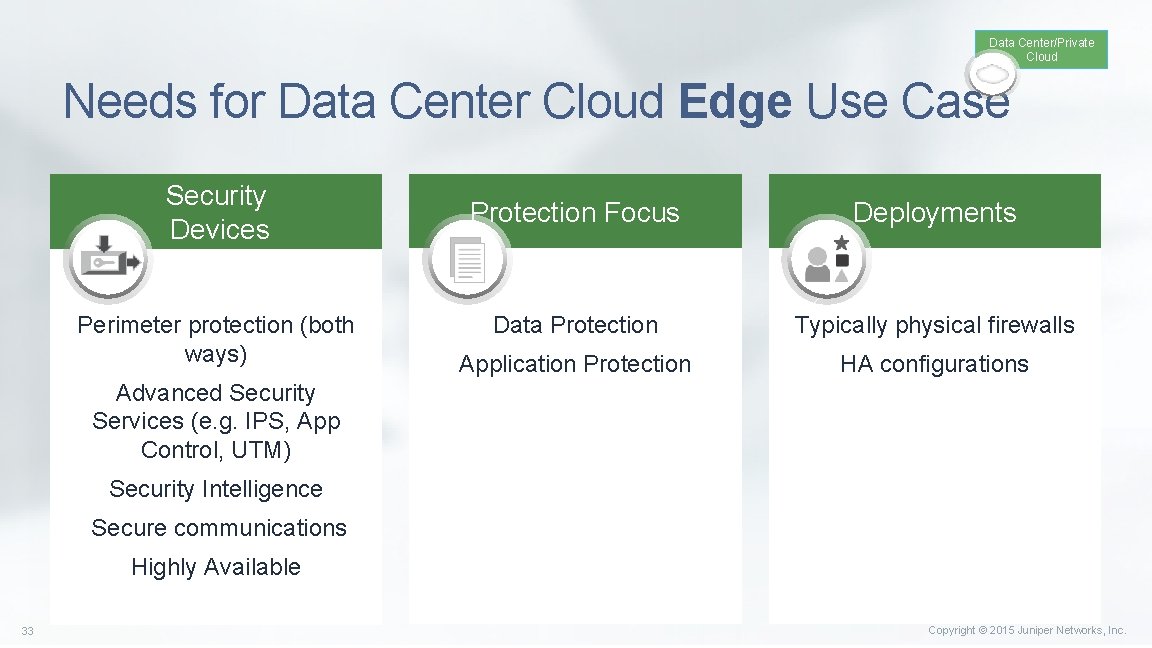
Data Center/Private Cloud Needs for Data Center Cloud Edge Use Case Security Devices Perimeter protection (both ways) Protection Focus Deployments Data Protection Typically physical firewalls Application Protection HA configurations Advanced Security Services (e. g. IPS, App Control, UTM) Security Intelligence Secure communications Highly Available 33 Copyright © 2015 Juniper Networks, Inc.

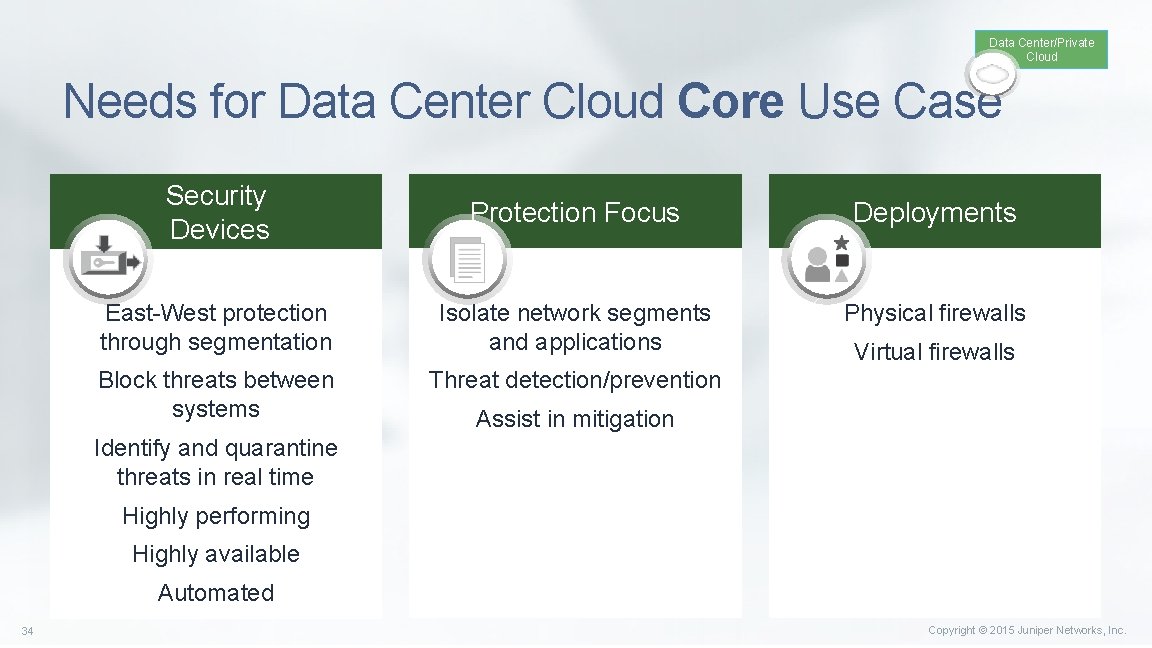
Data Center/Private Cloud Needs for Data Center Cloud Core Use Case Security Devices Protection Focus Deployments East-West protection through segmentation Isolate network segments and applications Physical firewalls Block threats between systems Threat detection/prevention Virtual firewalls Assist in mitigation Identify and quarantine threats in real time Highly performing Highly available Automated 34 Copyright © 2015 Juniper Networks, Inc.

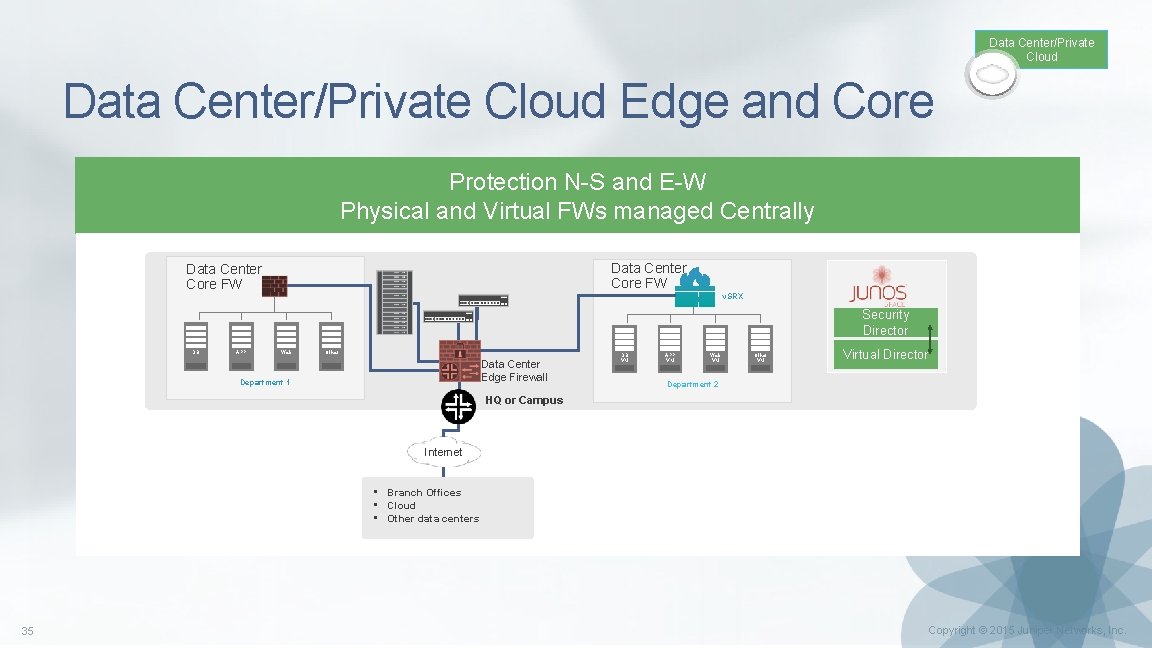
Data Center/Private Cloud Edge and Core Protection N-S and E-W Physical and Virtual FWs managed Centrally Data Center Core FW v. SRX Security Director DB APP Web Other Data Center Edge Firewall Department 1 DB VM APP VM Web VM Other VM Virtual Director Department 2 HQ or Campus Internet • Branch Offices • Cloud • Other data centers 35 Copyright © 2015 Juniper Networks, Inc.

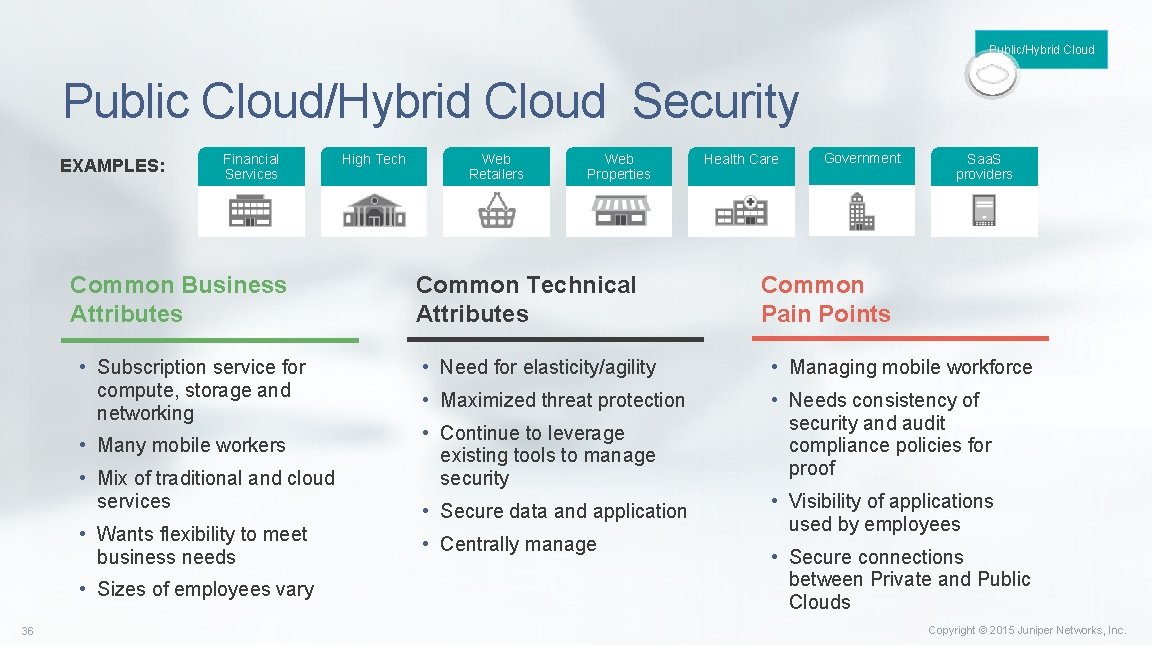
Public/Hybrid Cloud Public Cloud/Hybrid Cloud Security EXAMPLES: Financial Services Common Business Attributes • Subscription service for compute, storage and networking • Many mobile workers • Mix of traditional and cloud services • Wants flexibility to meet business needs • Sizes of employees vary 36 High Tech Web Retailers Web Properties Common Technical Attributes Health Care Government Saa. S providers Common Pain Points • Need for elasticity/agility • Managing mobile workforce • Maximized threat protection • Needs consistency of security and audit compliance policies for proof • Continue to leverage existing tools to manage security • Secure data and application • Centrally manage • Visibility of applications used by employees • Secure connections between Private and Public Clouds Copyright © 2015 Juniper Networks, Inc.

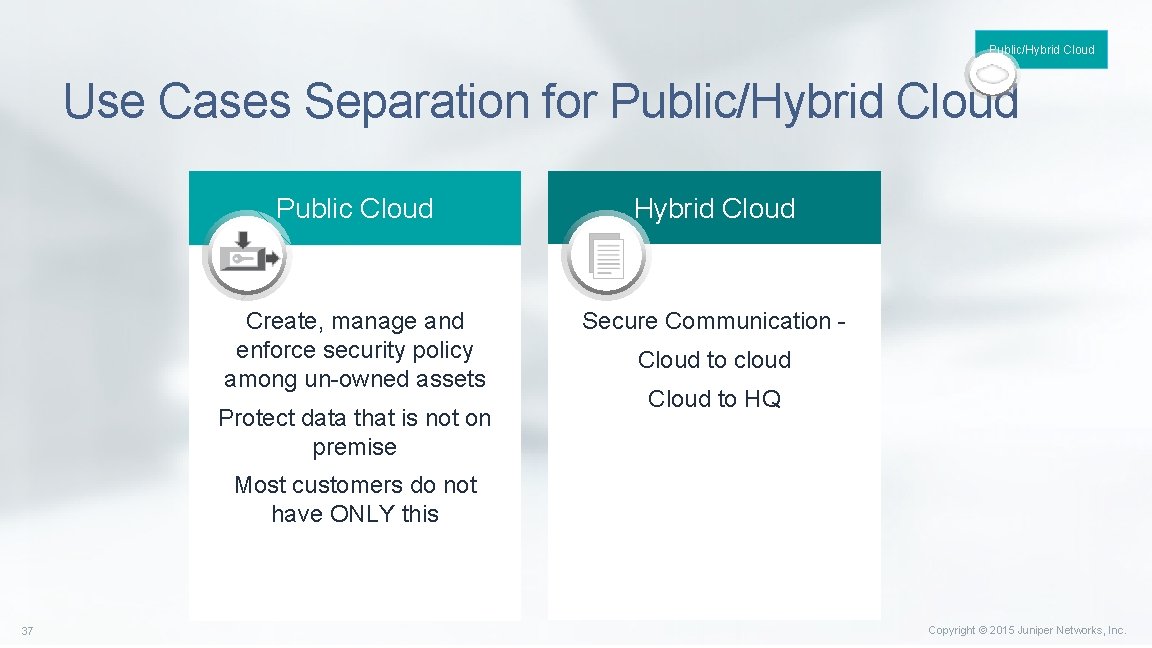
Public/Hybrid Cloud Use Cases Separation for Public/Hybrid Cloud Public Cloud Hybrid Cloud Create, manage and enforce security policy among un-owned assets Secure Communication - Protect data that is not on premise Cloud to cloud Cloud to HQ Most customers do not have ONLY this 37 Copyright © 2015 Juniper Networks, Inc.

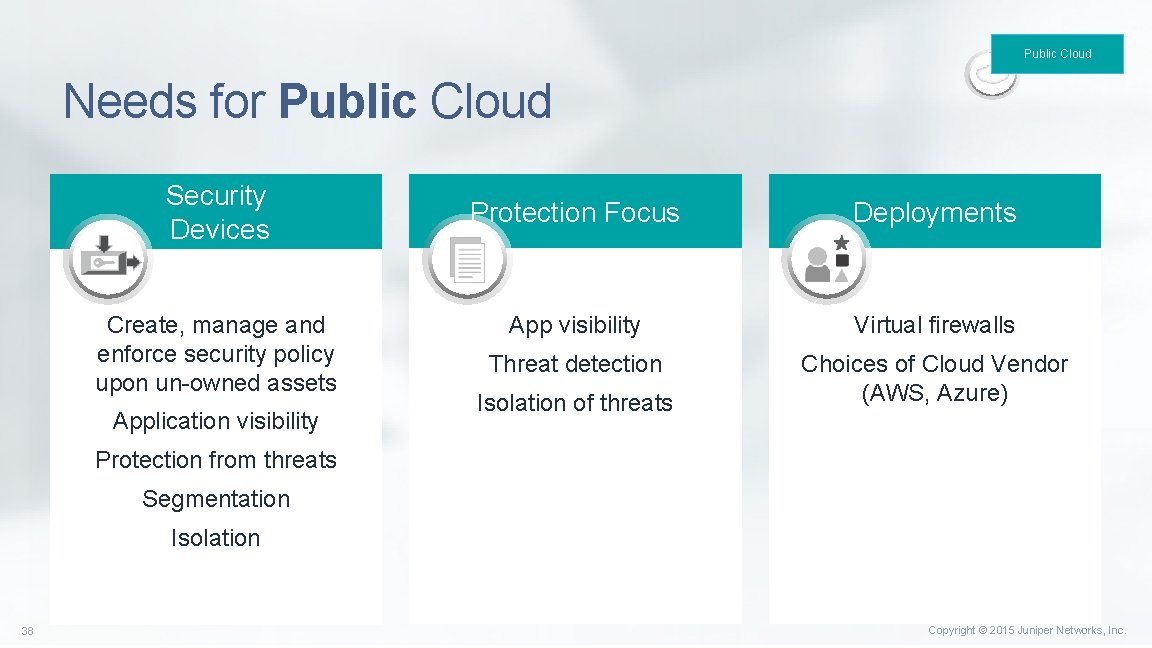
Public Cloud Needs for Public Cloud Security Devices Create, manage and enforce security policy upon un-owned assets Application visibility Protection Focus Deployments App visibility Virtual firewalls Threat detection Choices of Cloud Vendor (AWS, Azure) Isolation of threats Protection from threats Segmentation Isolation 38 Copyright © 2015 Juniper Networks, Inc.

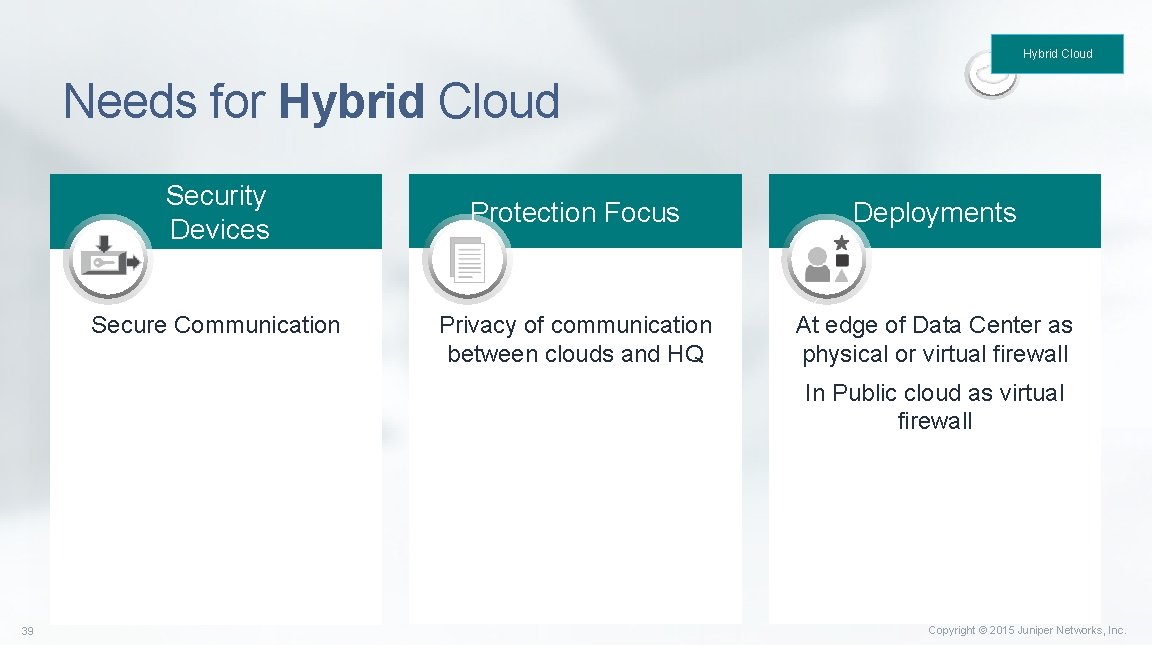
Hybrid Cloud Needs for Hybrid Cloud Security Devices Secure Communication Protection Focus Deployments Privacy of communication between clouds and HQ At edge of Data Center as physical or virtual firewall In Public cloud as virtual firewall 39 Copyright © 2015 Juniper Networks, Inc.

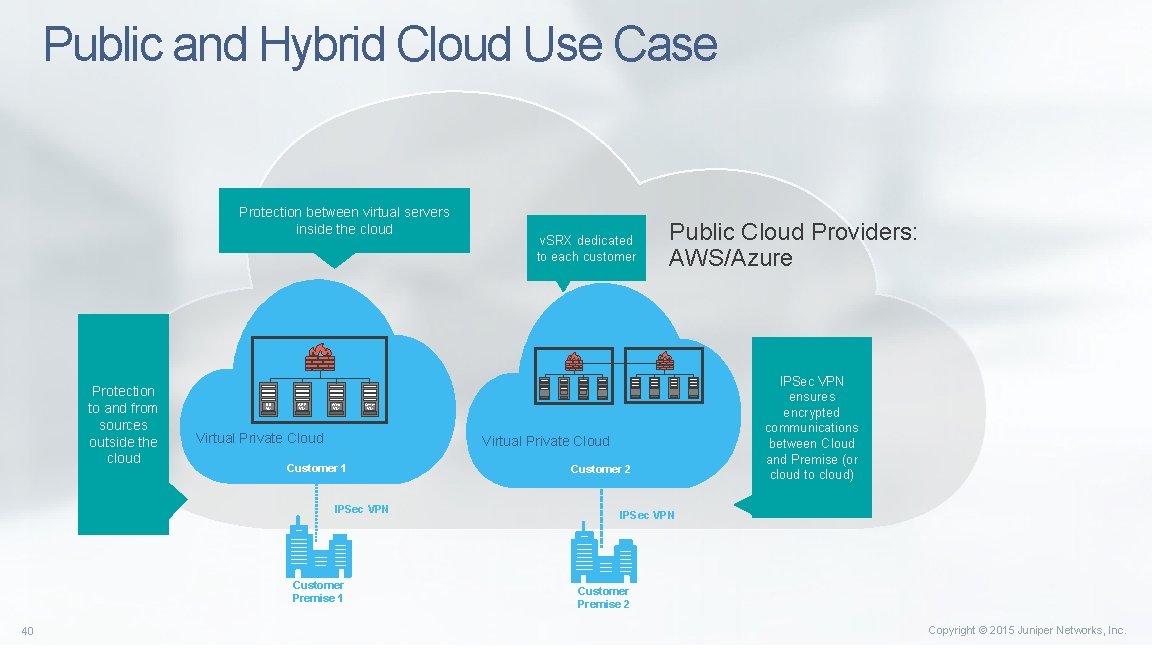
Public and Hybrid Cloud Use Case Protection between virtual servers inside the cloud Protection to and from sources outside the cloud DB VM APP VM Web VM Public Cloud Providers: AWS/Azure Other VM Virtual Private Cloud Customer 1 IPSec VPN Customer Premise 1 40 v. SRX dedicated to each customer Customer 2 IPSec VPN ensures encrypted communications between Cloud and Premise (or cloud to cloud) IPSec VPN Customer Premise 2 Copyright © 2015 Juniper Networks, Inc.

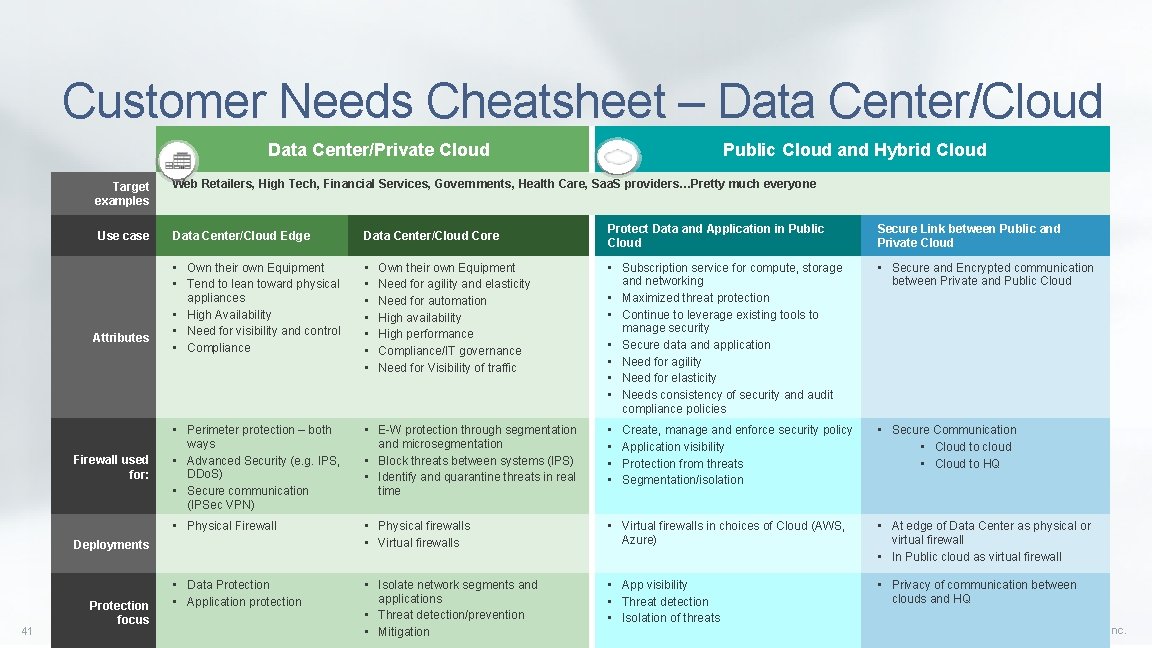
Customer Needs Cheatsheet – Data Center/Cloud Data Center/Private Cloud Target examples Web Retailers, High Tech, Financial Services, Governments, Health Care, Saa. S providers…Pretty much everyone Use case Data Center/Cloud Edge Data Center/Cloud Core • Own their own Equipment • Tend to lean toward physical appliances • High Availability • Need for visibility and control • Compliance • • Perimeter protection – both ways • Advanced Security (e. g. IPS, DDo. S) • Secure communication (IPSec VPN) Attributes Firewall used for: Protect Data and Application in Public Cloud Secure Link between Public and Private Cloud • Subscription service for compute, storage and networking • Maximized threat protection • Continue to leverage existing tools to manage security • Secure data and application • Need for agility • Need for elasticity • Needs consistency of security and audit compliance policies • Secure and Encrypted communication between Private and Public Cloud • E-W protection through segmentation and microsegmentation • Block threats between systems (IPS) • Identify and quarantine threats in real time • • • Secure Communication • Cloud to cloud • Cloud to HQ • Physical Firewall • Physical firewalls • Virtual firewalls in choices of Cloud (AWS, Azure) • At edge of Data Center as physical or virtual firewall • In Public cloud as virtual firewall • Data Protection • Application protection • Isolate network segments and applications • Threat detection/prevention • Mitigation • App visibility • Threat detection • Isolation of threats • Privacy of communication between clouds and HQ Deployments 41 Public Cloud and Hybrid Cloud Protection focus Own their own Equipment Need for agility and elasticity Need for automation High availability High performance Compliance/IT governance Need for Visibility of traffic Create, manage and enforce security policy Application visibility Protection from threats Segmentation/isolation Copyright © 2015 Juniper Networks, Inc.

Juniper Security Services Portfolio 42 Copyright © 2015 Juniper Networks, Inc.

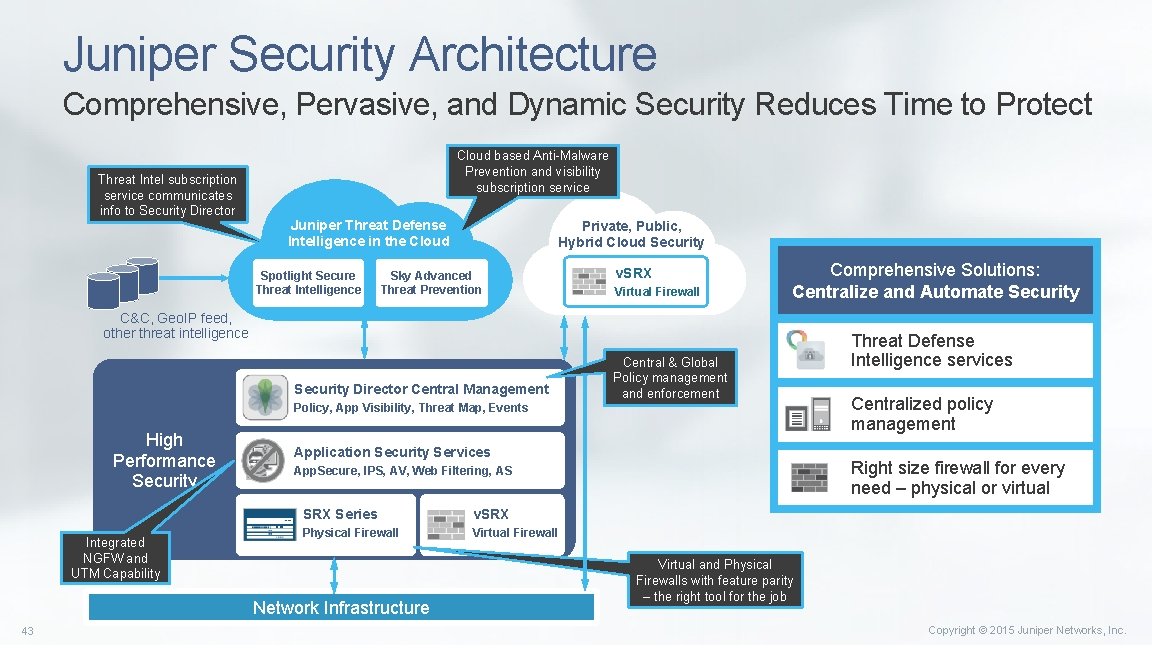
Juniper Security Architecture Comprehensive, Pervasive, and Dynamic Security Reduces Time to Protect Threat Intel subscription service communicates info to Security Director Cloud based Anti-Malware Prevention and visibility subscription service Juniper Threat Defense Intelligence in the Cloud Spotlight Secure Threat Intelligence Private, Public, Hybrid Cloud Security Sky Advanced Threat Prevention v. SRX Virtual Firewall Comprehensive Solutions: Centralize and Automate Security C&C, Geo. IP feed, other threat intelligence Security Director Central Management Central & Global Policy management and enforcement Policy, App Visibility, Threat Map, Events High Performance Security Integrated NGFW and UTM Capability Application Security Services v. SRX Physical Firewall Virtual Firewall Network Infrastructure 43 Centralized policy management Right size firewall for every need – physical or virtual App. Secure, IPS, AV, Web Filtering, AS SRX Series Threat Defense Intelligence services Virtual and Physical Firewalls with feature parity – the right tool for the job Copyright © 2015 Juniper Networks, Inc.

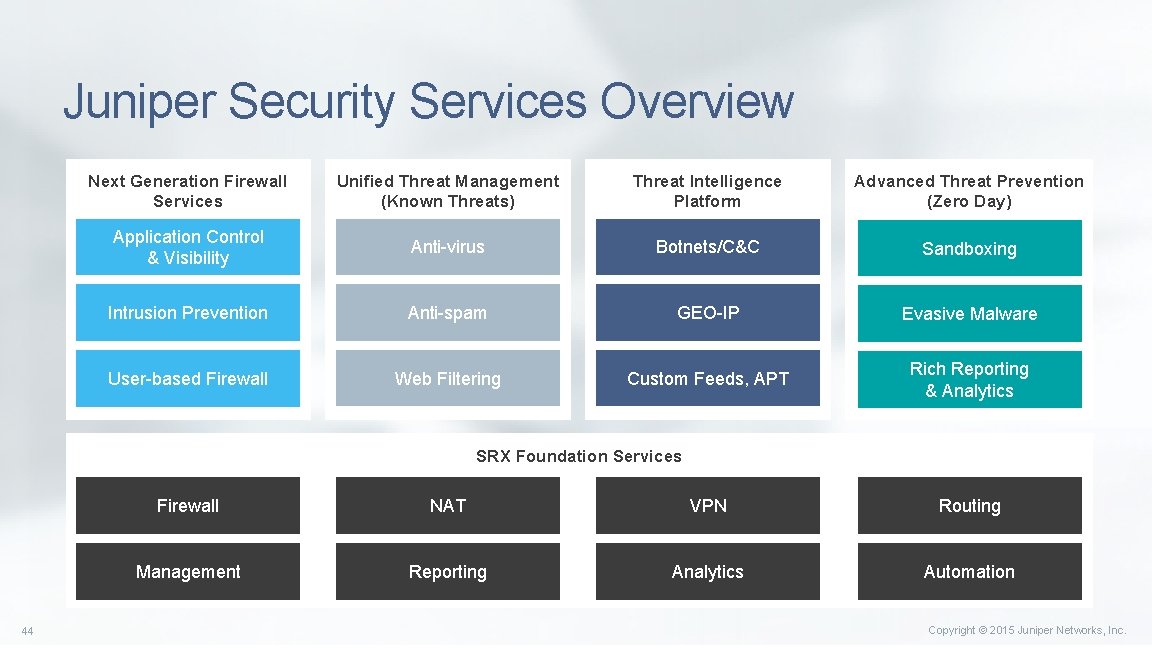
Juniper Security Services Overview Next Generation Firewall Services Unified Threat Management (Known Threats) Threat Intelligence Platform Advanced Threat Prevention (Zero Day) Application Control & Visibility Anti-virus Botnets/C&C Sandboxing Intrusion Prevention Anti-spam GEO-IP Evasive Malware User-based Firewall Web Filtering Custom Feeds, APT Rich Reporting & Analytics SRX Foundation Services 44 Firewall NAT VPN Routing Management Reporting Analytics Automation Copyright © 2015 Juniper Networks, Inc.

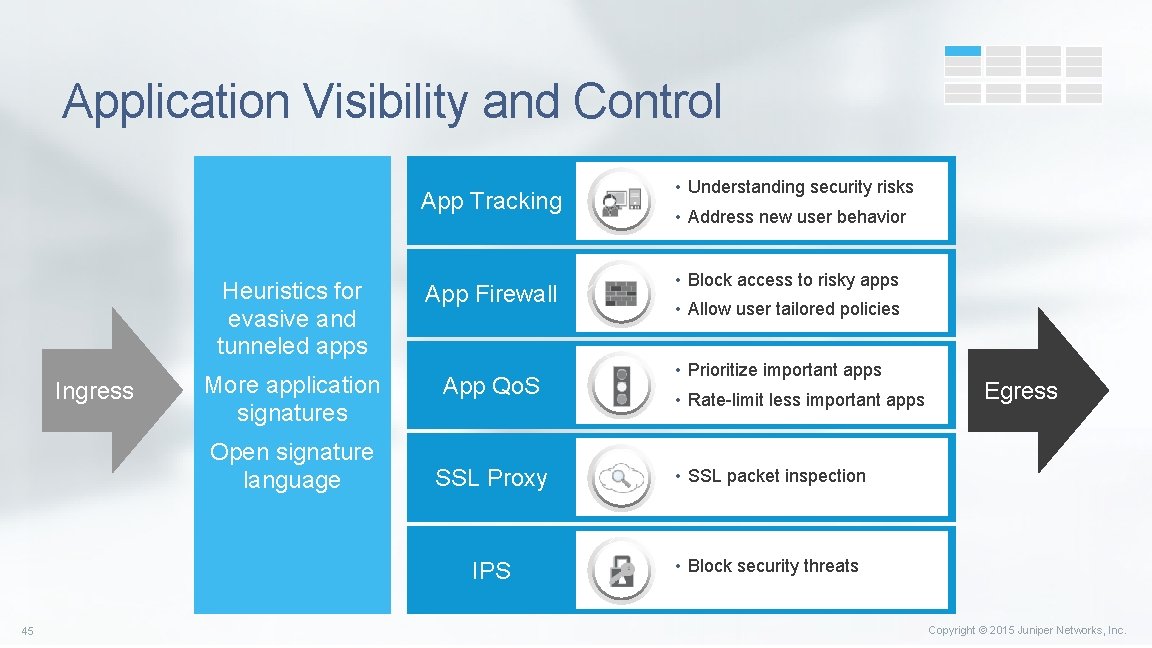
Application Visibility and Control App Tracking Heuristics for evasive and tunneled apps Ingress More application signatures Open signature language 45 App Firewall App Qo. S • Understanding security risks • Address new user behavior • Block access to risky apps • Allow user tailored policies • Prioritize important apps • Rate-limit less important apps SSL Proxy • SSL packet inspection IPS • Block security threats Egress Copyright © 2015 Juniper Networks, Inc.

Intrusion Prevention System – New IPS 2. 0 Engine Decrypt Ingress Inspect Report Block Among leaders in detection efficacy Improved overall branch SRX performance Egress Reduced memory footprint 46 Copyright © 2015 Juniper Networks, Inc.

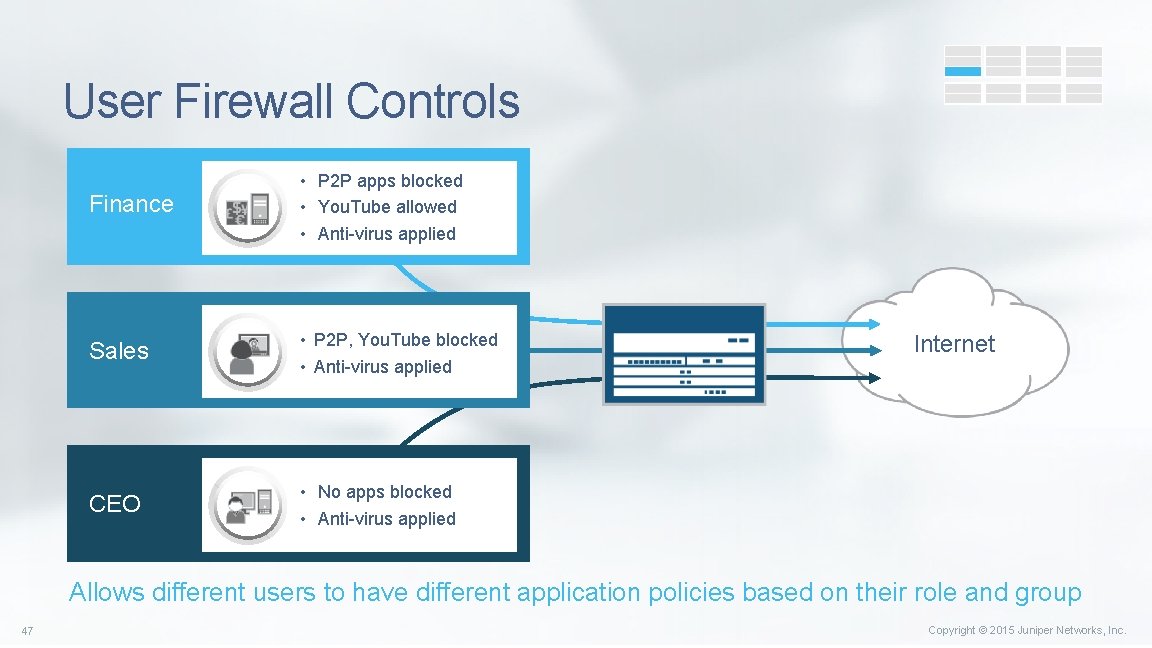
User Firewall Controls Finance • P 2 P apps blocked • You. Tube allowed • Anti-virus applied Sales • P 2 P, You. Tube blocked • Anti-virus applied CEO • No apps blocked • Anti-virus applied Internet Allows different users to have different application policies based on their role and group 47 Copyright © 2015 Juniper Networks, Inc.

Unified Threat Management Services Anti-Virus • Protection from top-tier AV partner • Reputation-enhanced capabilities Anti-Spam • Multilayered spam protection • Protection against APTs Web Filtering 48 • Block malicious URLs • Prevent lost productivity Copyright © 2015 Juniper Networks, Inc.

Spotlight Secure Threat Intelligence Platform Taking action at the point of enforcement • Open platform for threat detection and advanced malware prevention • Connects multiple intelligence sources to the enforcement points • Single point of administrative control • Enables security efficiencies that matter to the business 49 Copyright © 2015 Juniper Networks, Inc.

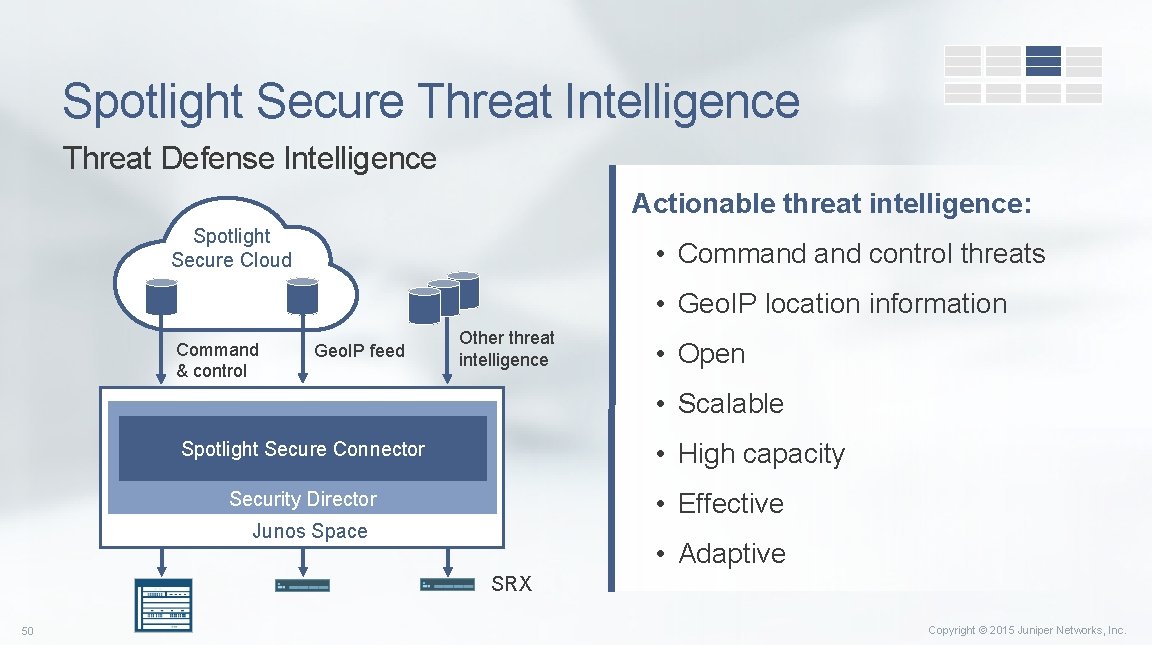
Spotlight Secure Threat Intelligence Threat Defense Intelligence Actionable threat intelligence: Spotlight Secure Cloud • Command control threats • Geo. IP location information Command & control Geo. IP feed Other threat intelligence • Open • Scalable • High capacity Spotlight Secure Connector • Effective Security Director Junos Space • Adaptive SRX 50 Copyright © 2015 Juniper Networks, Inc.

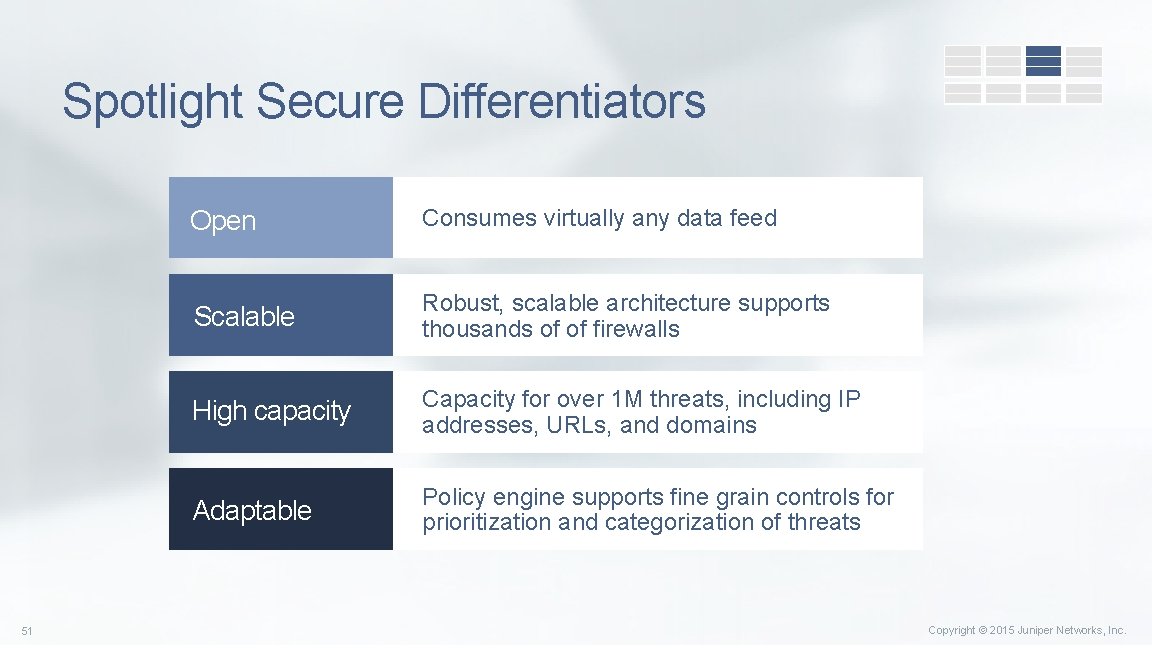
Spotlight Secure Differentiators 51 Open Consumes virtually any data feed Scalable Robust, scalable architecture supports thousands of of firewalls High capacity Capacity for over 1 M threats, including IP addresses, URLs, and domains Adaptable Policy engine supports fine grain controls for prioritization and categorization of threats Copyright © 2015 Juniper Networks, Inc.

Sky Advanced Threat Prevention Advanced Anti-malware Service in the Cloud-based Advanced Anti-malware Service With SRX Series • Delivers protection against sophisticated “Zero-day” threats • Watches ingress/egress traffic for malware and indicators of compromise • Delivers deep inspection, actionable reporting, inline malware blocking Advanced Threat Prevention • • 52 Integration with SRX enables detection and prevention of threats Efficacy against sophisticated malware leveraging deception techniques Actionable output (compromised host quarantine, rich reporting) Augments sandboxing with additional analysis to detect evasive malware Copyright © 2015 Juniper Networks, Inc.

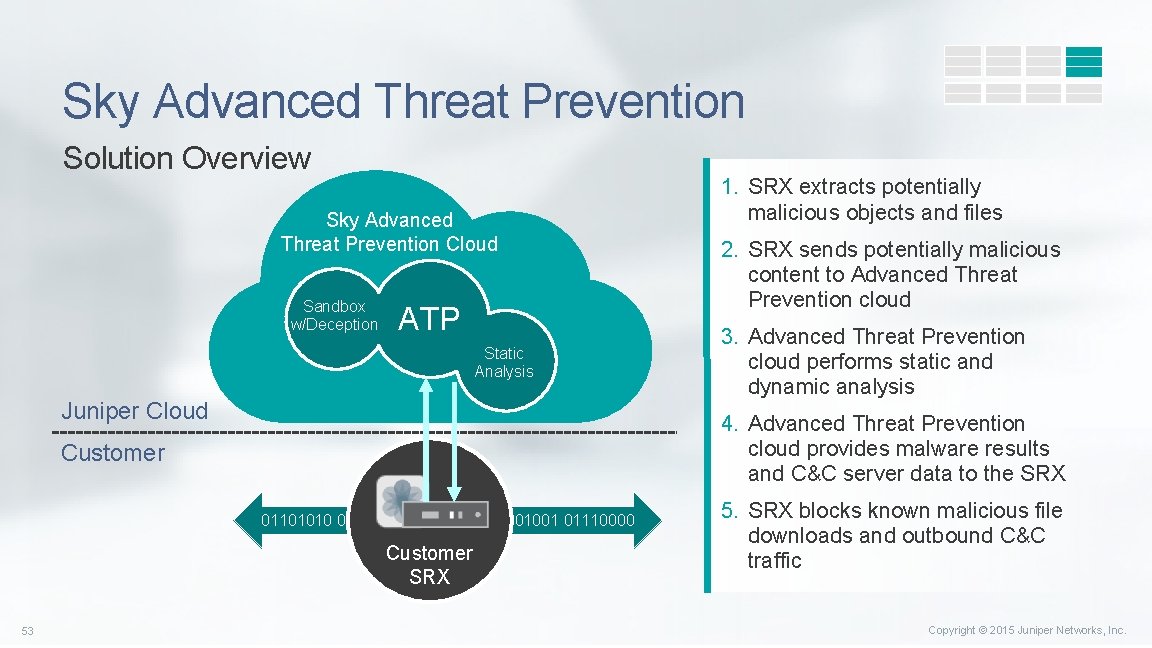
Sky Advanced Threat Prevention Solution Overview Sky Advanced Threat Prevention Cloud Sandbox w/Deception ATP Static Analysis Juniper Cloud 2. SRX sends potentially malicious content to Advanced Threat Prevention cloud 3. Advanced Threat Prevention cloud performs static and dynamic analysis 4. Advanced Threat Prevention cloud provides malware results and C&C server data to the SRX Customer 01101010 01110101 01101110 01101001 01110000 Customer SRX 53 1. SRX extracts potentially malicious objects and files 5. SRX blocks known malicious file downloads and outbound C&C traffic Copyright © 2015 Juniper Networks, Inc.

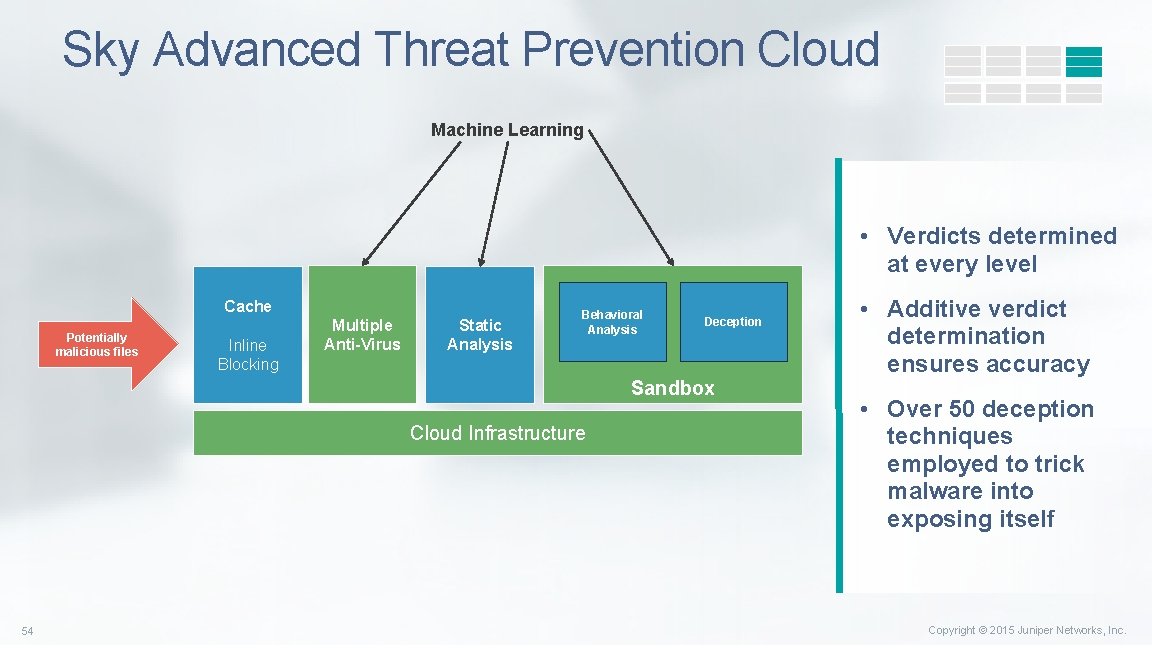
Sky Advanced Threat Prevention Cloud Machine Learning • Verdicts determined at every level Cache Potentially malicious files Inline Blocking Multiple Anti-Virus Static Analysis Behavioral Analysis Deception Sandbox Cloud Infrastructure 54 • Additive verdict determination ensures accuracy • Over 50 deception techniques employed to trick malware into exposing itself Copyright © 2015 Juniper Networks, Inc.

Sky Advanced Threat Prevention Key Differentiators Integrated with SRX for detection and inline blocking Network wide remediation • Actionable intelligence on compromised hosts sent to every SRX in the network (via Spotlight Secure threat intelligence service) • Customers can implement quarantine policies when infected clients are detected in the network Progressive verdicts for higher degree of accuracy • • Cache lookup Static analysis combined with multiple anti-virus engines Advanced Threat Prevention adds machine learning to improve verdict accuracy Dynamic analysis (sandboxing) Deception based techniques • Tricks evasive malware into identifying itself • Minimizes false positives 55 Copyright © 2015 Juniper Networks, Inc.

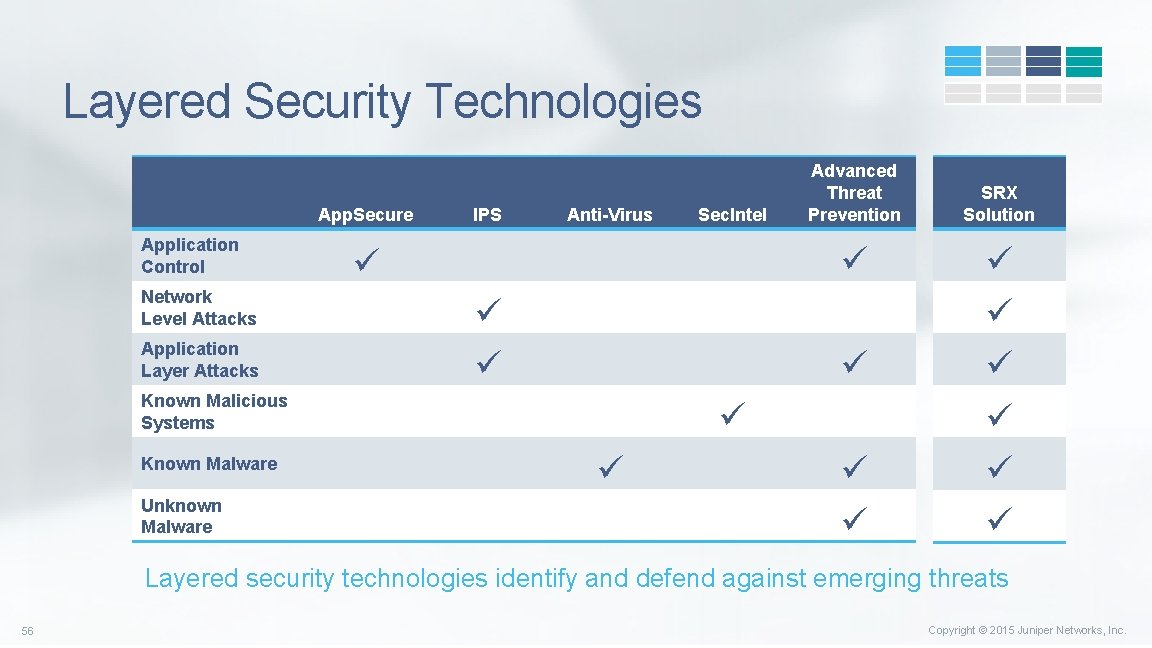
Layered Security Technologies App. Secure Application Control Network Level Attacks Application Layer Attacks IPS Anti-Virus Known Malicious Systems Known Malware Unknown Malware Sec. Intel Advanced Threat Prevention SRX Solution Layered security technologies identify and defend against emerging threats 56 Copyright © 2015 Juniper Networks, Inc.

Positioning Juniper Security Hardware 57 Copyright © 2015 Juniper Networks, Inc.

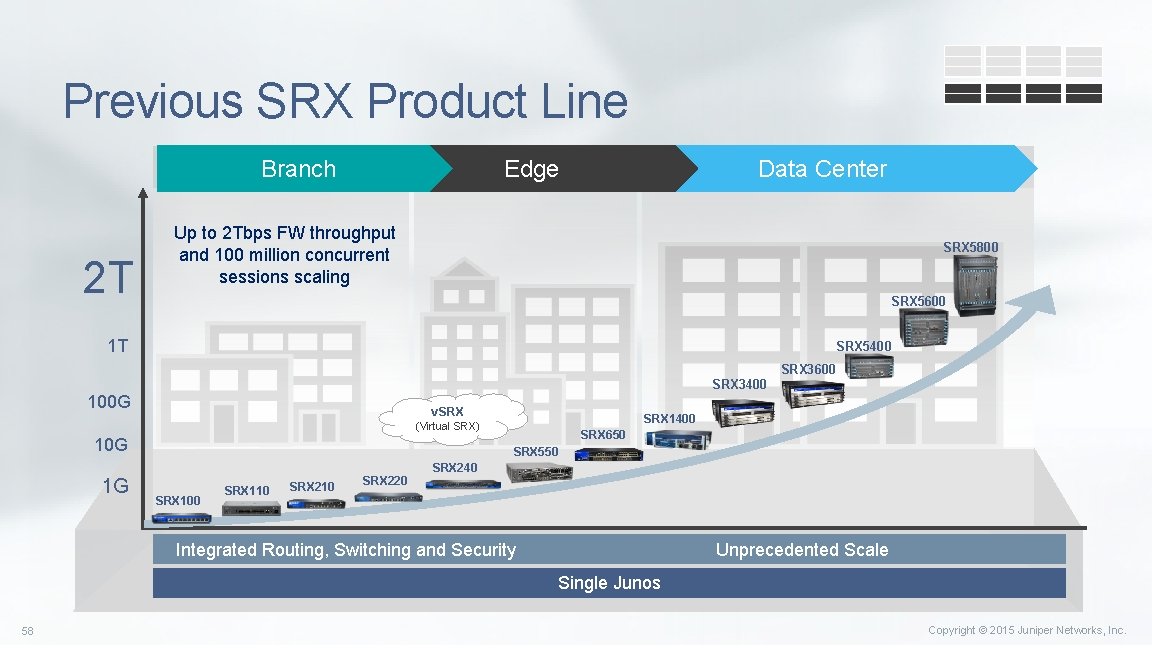
Previous SRX Product Line Branch 2 T Edge Data Center Up to 2 Tbps FW throughput and 100 million concurrent sessions scaling SRX 5800 SRX 5600 1 T SRX 5400 SRX 3600 SRX 3400 100 G v. SRX 1400 (Virtual SRX) 10 G 1 G SRX 650 SRX 550 SRX 100 SRX 110 SRX 220 SRX 240 Integrated Routing, Switching and Security Unprecedented Scale Single Junos 58 Copyright © 2015 Juniper Networks, Inc.

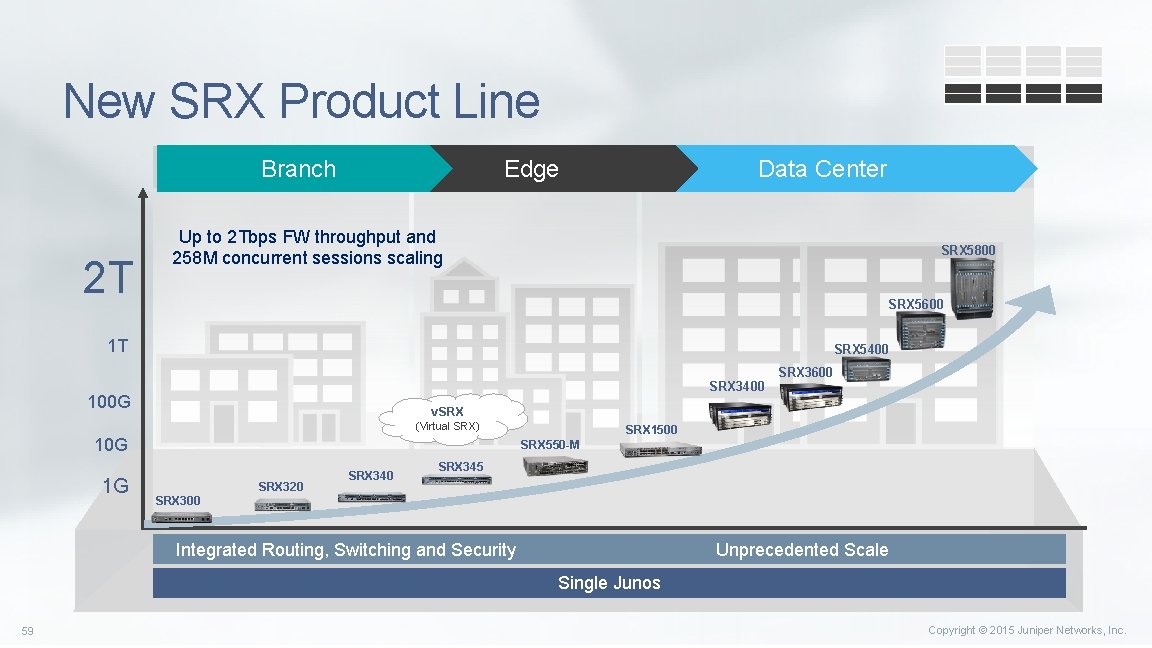
New SRX Product Line Branch 2 T Edge Data Center Up to 2 Tbps FW throughput and 258 M concurrent sessions scaling SRX 5800 SRX 5600 1 T SRX 5400 SRX 3600 SRX 3400 100 G v. SRX (Virtual SRX) 10 G 1 G SRX 1500 SRX 550 -M SRX 320 SRX 345 SRX 300 Integrated Routing, Switching and Security Unprecedented Scale Single Junos 59 Copyright © 2015 Juniper Networks, Inc.

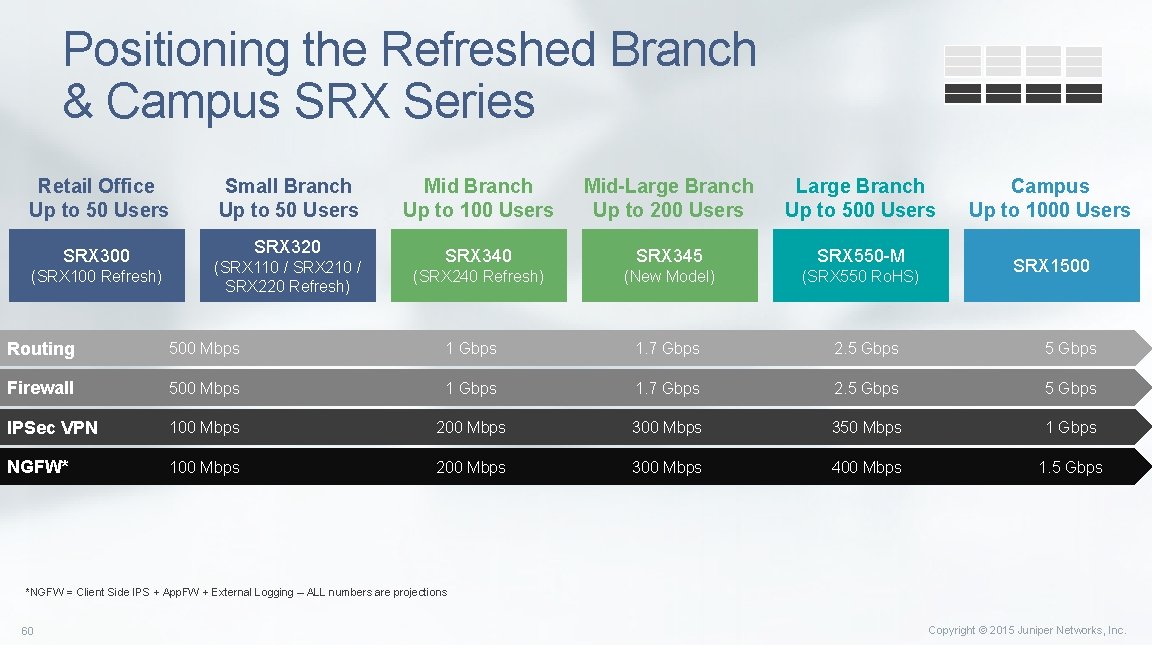
Positioning the Refreshed Branch & Campus SRX Series Retail Office Up to 50 Users SRX 300 (SRX 100 Refresh) Small Branch Up to 50 Users SRX 320 (SRX 110 / SRX 220 Refresh) Mid Branch Up to 100 Users Mid-Large Branch Up to 200 Users Large Branch Up to 500 Users SRX 340 SRX 345 SRX 550 -M (SRX 240 Refresh) (New Model) (SRX 550 Ro. HS) Campus Up to 1000 Users SRX 1500 Routing 500 Mbps 1 Gbps 1. 7 Gbps 2. 5 Gbps Firewall 500 Mbps 1 Gbps 1. 7 Gbps 2. 5 Gbps IPSec VPN 100 Mbps 200 Mbps 350 Mbps 1 Gbps NGFW* 100 Mbps 200 Mbps 300 Mbps 400 Mbps 1. 5 Gbps *NGFW = Client Side IPS + App. FW + External Logging – ALL numbers are projections 60 Copyright © 2015 Juniper Networks, Inc.

SRX 300 • Ideal for small sites, retail office • Up to 50 users • Full security features • Firewall and VPN • UTM: IPS, App. Secure, antivirus, web-filtering, and anti-spam • Threat Intelligence • Routing and switching features • Fanless (no noise) • Typical use cases • Secure Router • Managed CPE 61 Features On-board Ethernet Power Over Ethernet (802. 3 af, 802. 3 at) WAN Slots JUNOS Software Version Support Firewall Performance (large packets) SRX 300 8 x GE (w/ 2 x. SFP) No None JUNOS 15. 1 X 1000 Mbps Firewall Performance (IMIX) 500 Mbps Firewall Performance (Firewall + Routing PPS 64 byte) 200 Kpps VPN Performance – AES 256+SHA-1 3 DES+SHA 1 100 Mbps NGFW Performance (IPS, App. FW, logging) 100 Mbps Connections Per Second (CPS) 5 K CPS Maximum Concurrent Sessions 64 K Spotlight Secure Enforcement Yes High Availability AES 128 MAC-Sec A/A, A/P 2 SFP Ports Copyright © 2015 Juniper Networks, Inc.

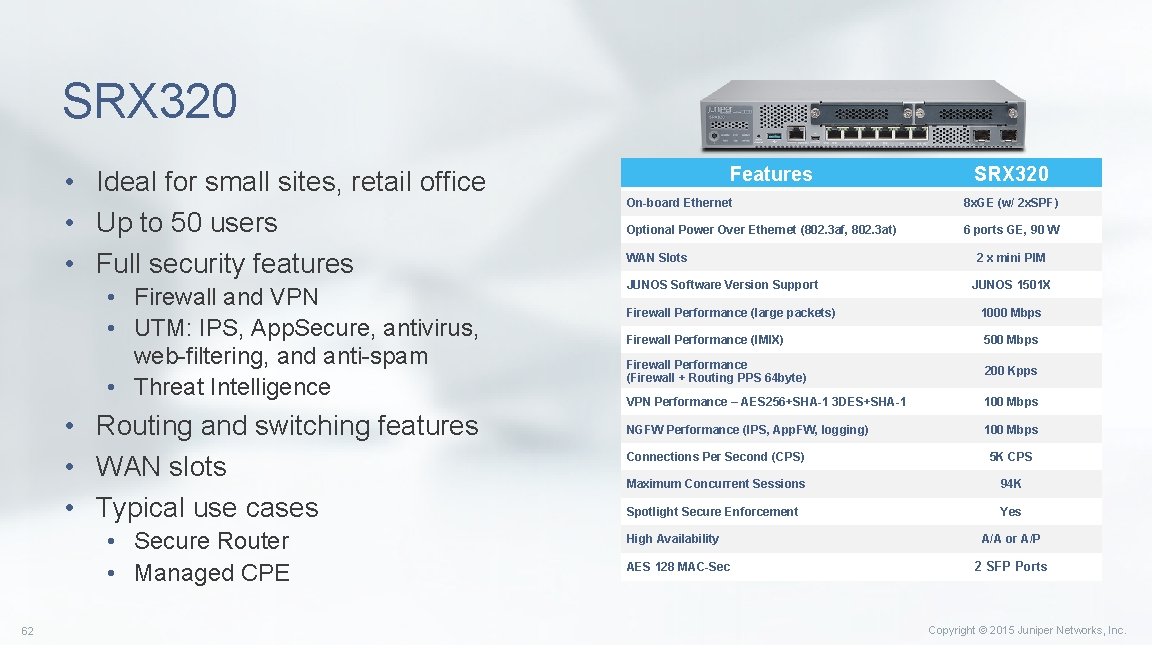
SRX 320 • Ideal for small sites, retail office • Up to 50 users • Full security features • Firewall and VPN • UTM: IPS, App. Secure, antivirus, web-filtering, and anti-spam • Threat Intelligence • Routing and switching features • WAN slots • Typical use cases • Secure Router • Managed CPE 62 Features SRX 320 On-board Ethernet 8 x. GE (w/ 2 x. SPF) Optional Power Over Ethernet (802. 3 af, 802. 3 at) 6 ports GE, 90 W WAN Slots JUNOS Software Version Support 2 x mini PIM JUNOS 1501 X Firewall Performance (large packets) 1000 Mbps Firewall Performance (IMIX) 500 Mbps Firewall Performance (Firewall + Routing PPS 64 byte) 200 Kpps VPN Performance – AES 256+SHA-1 3 DES+SHA-1 100 Mbps NGFW Performance (IPS, App. FW, logging) 100 Mbps Connections Per Second (CPS) 5 K CPS Maximum Concurrent Sessions 94 K Spotlight Secure Enforcement Yes High Availability AES 128 MAC-Sec A/A or A/P 2 SFP Ports Copyright © 2015 Juniper Networks, Inc.

SRX 300 and SRX 320 Compared 63 Specification SRX 300 SRX 320 RAM / storage 4 GB / 8 GB On-board ports 8 x. GE (w 2 x SFP) MAC-sec ports 2 x SFP Optional Po. E+ ports 0 6 (90 W) WAN slots 0 2 x Mini. PIM Acoustics 0 d. BA 35 d. BA Power Adapter 60 W External 75 W / 280 W Forwarding capacity 200 Kpps Routing / firewall 500 Mbps IPSec VPN 100 Mbps IPS 200 Mbps NGFW 100 Mbps Concurrent session 64, 000 Copyright © 2015 Juniper Networks, Inc.

SRX 340 • Ideal for enterprise medium-sized branch offices • Up to 100 users • Ideal office-in-a-box solution for managed services or commercial business • Full security features • Firewall and VPN • UTM: IPS, App. Secure, antivirus, web-filtering, and anti-spam • Threat Intelligence • Routing and switching features • Typical use cases 64 • NGFW • Managed CPE Features On-board Ethernet SRX 340 16 x. GE (w/ 8 x. SFP) WAN Slots 4 x mini PIM JUNOS Software Version Support JUNOS 15. 1 X Firewall Performance (large packets) 3 Gbps Firewall Performance (IMIX) 1 Gbps Firewall Performance (Firewall + Routing PPS 64 byte) 350 Kpps VPN Performance – AES 256+SHA-1 3 DES+SHA-1 400 Mbps NGFW Performance (IPS, App. FW, logging) 200 Mbps Connections Per Second (CPS) 10 K CPS Maximum Concurrent Sessions 256 K Spotlight Secure Enforcement High Availability AES 128 MAC-Sec Out-of-Band Management Port Field Upgradable SSD Yes A/A or A/P 16 SFP Ports 1 GE 1 Copyright © 2015 Juniper Networks, Inc.

SRX 345 • Ideal for enterprise medium sized branch offices • Up to 200 users • Ideal office-in-a-box solution for managed services or commercial business • Full security features • Firewall and VPN • UTM: IPS, App. Secure, antivirus, web-filtering, and anti-spam • Threat Intelligence • Routing and switching features • Typical Use Cases 65 • NGFW • Managed CPE Features On-board Ethernet SRX 345 16 x. GE (w/ 8 x. SFP) WAN Slots 4 x mini PIM JUNOS Software Version Support JUNOS 15. 1 X Firewall Performance (large packets) 5 Gbps Firewall Performance (IMIX) 1. 7 Gbps Firewall Performance (Firewall + Routing PPS 64 byte) 550 Kpps VPN Performance – AES 256+SHA-1 3 DES+SHA-1 300 Mbps NGFW Performance (IPS, App. FW, logging) 300 Mbps Connections Per Second (CPS) 15 K CPS Maximum Concurrent Sessions 375 K Spotlight Secure Enforcement High Availability AES 128 MAC-Sec Out-of-Band Management Port Field upgradable SSD Yes A/A or A/P 16 SFP Ports 1 GE 1 Copyright © 2015 Juniper Networks, Inc.

SRX 340 and SRX 345 Compared 66 Specification SRX 340 SRX 345 RAM / storage 4 GB / 8 GB On-board ports 16 x. GE (w 8 x SFP) MAC-sec ports 16 x GE OOB management 1 x GE WAN slots 4 x Mini. PIM Acoustics 35 d. BA Power Supply 180 W Internal Forwarding capacity 400 Kpps 550 Kpps Routing / firewall 1 Gbps 1. 7 Gbps IPSec VPN 200 Mbps 300 Mbps IPS 400 Mbps 600 Mbps NGFW 200 Mbps 300 Mbps Concurrent session 256, 000 375, 000 Copyright © 2015 Juniper Networks, Inc.

SRX 550 • Ideal for large enterprise branch office • Ideal office-in-a-box solution for managed services or commercial business • Up to 500 users • SRX 550 offers: • Comprehensive routing and security services • High density on-board and modular switch ports, copper and SFP • Application awareness and control • Business continuity and resiliency • Typical use cases • NGFW • Larger secure router • CPE 67 Features On-board Ethernet Power Over Ethernet (802. 3 af, 802. 3 at) WAN Slots JUNOS Software Version Support SRX 550 10 x. GE (6 Copper, 4 x. SFP) 40 ports GE, 500 W 2 x mini PIM, 6 x GPIM JUNOS 15. 1 X Firewall Performance (large packets) 8 Gbps* Firewall Performance (IMIX) 2. 5 Gbps Firewall Performance (Firewall + Routing PPS 64 byte) 800 Kpps VPN Performance – AES 256+SHA-1 3 DES+SHA-1 350 Mbps NGFW Performance (IPS, App. FW, logging) 300 Mbps Connections Per Second (CPS) 27 K CPS Maximum Concurrent Sessions 512 K* Spotlight Secure Enforcement High Availability Field Upgradable SSD *Planned 1 H 16 with 4 G memory sku Yes A/A or A/P 1 Copyright © 2015 Juniper Networks, Inc.

New Mid-Range SRX 1500 for Enterprise Replaces SRX 650, SRX 1400 Modular Interfaces • • 12 x 1 GE (Cu) + 4 x 1 GE (SFP) 4 x 10 GE (SFP+) 2 x PIM slots (for future use) Dedicated HA control port (SFP) • Dedicated OOB mgmt (1 x. GE) 68 Power, Storage & Dimensions • • • 16 G e. SATA + 100 G SSD Dual power supply (AC / DC) Average power: 150 W Size: 1 RU Front to back airflow Firewall Performance • • • Firewall (IMIX): 6. 0 Gbps VPN (IMIX): 1. 0 Gbps App. ID (HTTP): 5. 0 Gbps IPS recommended: 3. 0 Gbps NGFW: 1. 5 Gbps Copyright © 2015 Juniper Networks, Inc.

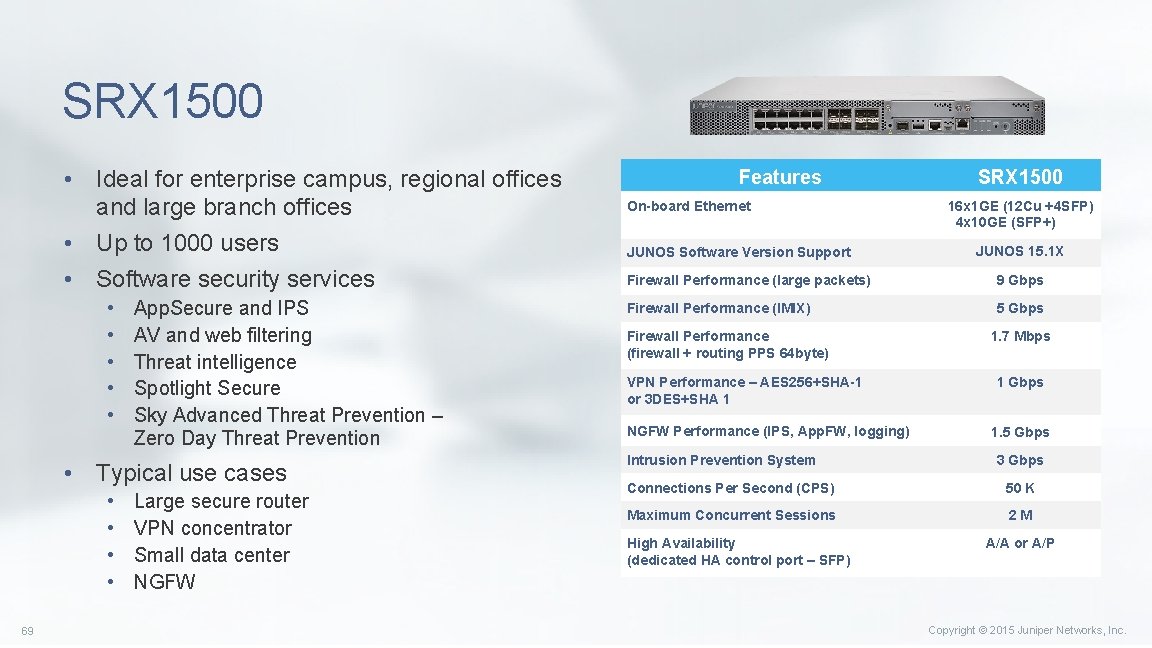
SRX 1500 • Ideal for enterprise campus, regional offices and large branch offices • Up to 1000 users • Software security services • • • App. Secure and IPS AV and web filtering Threat intelligence Spotlight Secure Sky Advanced Threat Prevention – Zero Day Threat Prevention • Typical use cases • • 69 Large secure router VPN concentrator Small data center NGFW Features On-board Ethernet JUNOS Software Version Support SRX 1500 16 x 1 GE (12 Cu +4 SFP) 4 x 10 GE (SFP+) JUNOS 15. 1 X Firewall Performance (large packets) 9 Gbps Firewall Performance (IMIX) 5 Gbps Firewall Performance (firewall + routing PPS 64 byte) VPN Performance – AES 256+SHA-1 or 3 DES+SHA 1 NGFW Performance (IPS, App. FW, logging) Intrusion Prevention System 1. 7 Mbps 1 Gbps 1. 5 Gbps 3 Gbps Connections Per Second (CPS) 50 K Maximum Concurrent Sessions 2 M High Availability (dedicated HA control port – SFP) A/A or A/P Copyright © 2015 Juniper Networks, Inc.

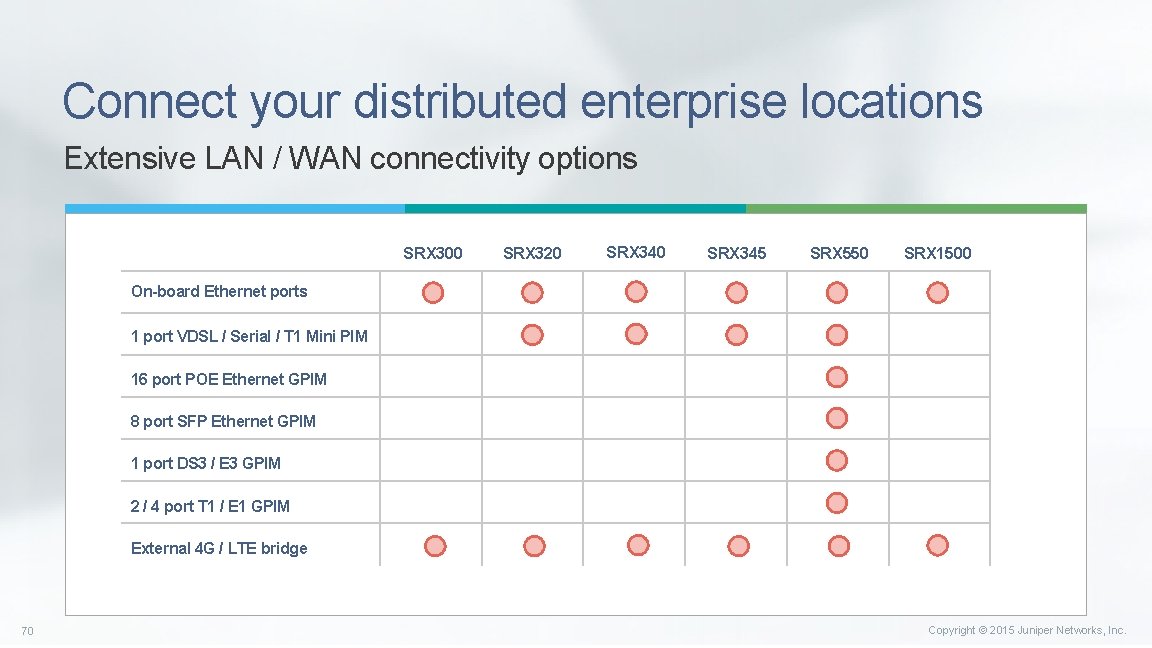
Connect your distributed enterprise locations Extensive LAN / WAN connectivity options SRX 300 SRX 320 SRX 345 SRX 550 SRX 1500 On-board Ethernet ports 1 port VDSL / Serial / T 1 Mini PIM 16 port POE Ethernet GPIM 8 port SFP Ethernet GPIM 1 port DS 3 / E 3 GPIM 2 / 4 port T 1 / E 1 GPIM External 4 G / LTE bridge 70 Copyright © 2015 Juniper Networks, Inc.

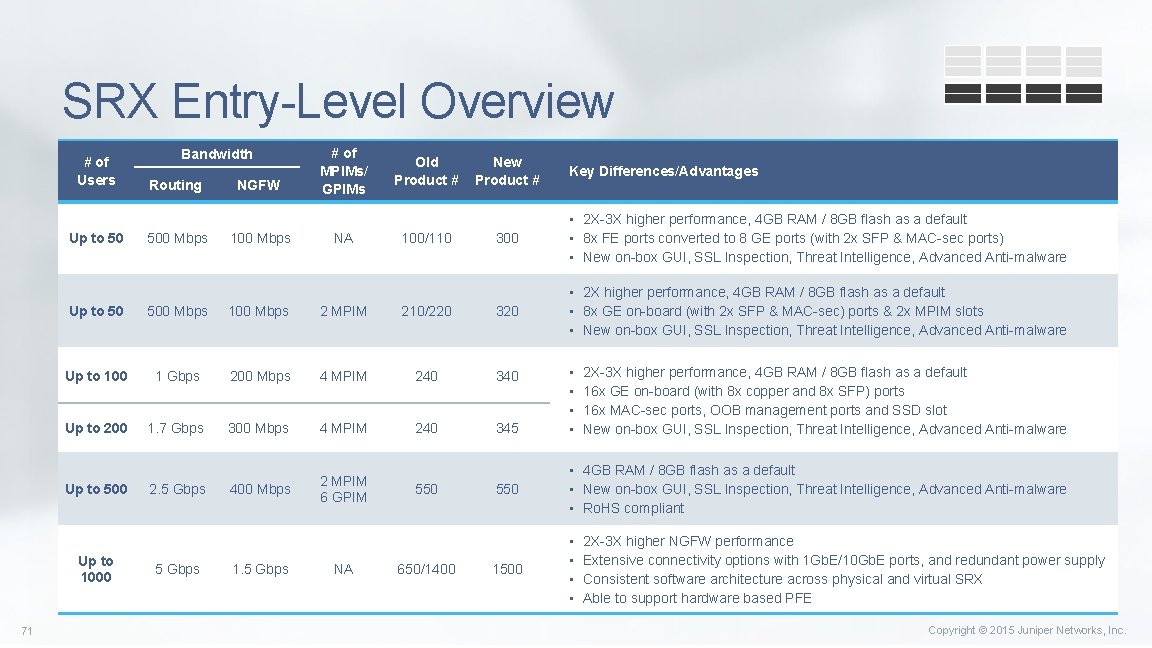
SRX Entry-Level Overview # of Users Up to 50 Routing 500 Mbps NGFW 100 Mbps # of MPIMs/ GPIMs NA Old Product # 100/110 New Product # 300 • 2 X higher performance, 4 GB RAM / 8 GB flash as a default • 8 x GE on-board (with 2 x SFP & MAC-sec) ports & 2 x MPIM slots • New on-box GUI, SSL Inspection, Threat Intelligence, Advanced Anti-malware 500 Mbps 100 Mbps 2 MPIM 210/220 320 Up to 100 1 Gbps 200 Mbps 4 MPIM 240 340 Up to 200 1. 7 Gbps 300 Mbps 4 MPIM 240 345 400 Mbps 2 MPIM 6 GPIM Up to 1000 2. 5 Gbps 1. 5 Gbps NA 550 650/1400 Key Differences/Advantages • 2 X-3 X higher performance, 4 GB RAM / 8 GB flash as a default • 8 x FE ports converted to 8 GE ports (with 2 x SFP & MAC-sec ports) • New on-box GUI, SSL Inspection, Threat Intelligence, Advanced Anti-malware Up to 500 71 Bandwidth • • 2 X-3 X higher performance, 4 GB RAM / 8 GB flash as a default 16 x GE on-board (with 8 x copper and 8 x SFP) ports 16 x MAC-sec ports, OOB management ports and SSD slot New on-box GUI, SSL Inspection, Threat Intelligence, Advanced Anti-malware 550 • 4 GB RAM / 8 GB flash as a default • New on-box GUI, SSL Inspection, Threat Intelligence, Advanced Anti-malware • Ro. HS compliant 1500 • • 2 X-3 X higher NGFW performance Extensive connectivity options with 1 Gb. E/10 Gb. E ports, and redundant power supply Consistent software architecture across physical and virtual SRX Able to support hardware based PFE Copyright © 2015 Juniper Networks, Inc.

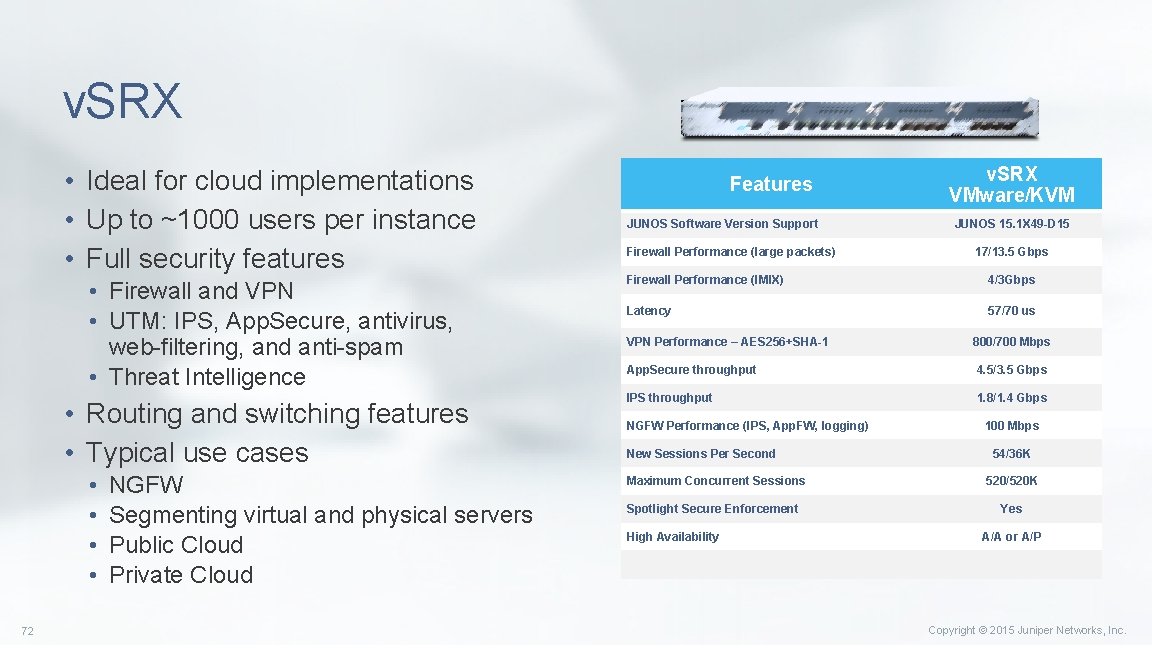
v. SRX • Ideal for cloud implementations • Up to ~1000 users per instance • Full security features • Firewall and VPN • UTM: IPS, App. Secure, antivirus, web-filtering, and anti-spam • Threat Intelligence • Routing and switching features • Typical use cases • • 72 NGFW Segmenting virtual and physical servers Public Cloud Private Cloud Features JUNOS Software Version Support Firewall Performance (large packets) v. SRX VMware/KVM JUNOS 15. 1 X 49 -D 15 17/13. 5 Gbps Firewall Performance (IMIX) 4/3 Gbps Latency 57/70 us VPN Performance – AES 256+SHA-1 800/700 Mbps App. Secure throughput 4. 5/3. 5 Gbps IPS throughput 1. 8/1. 4 Gbps NGFW Performance (IPS, App. FW, logging) New Sessions Per Second Maximum Concurrent Sessions Spotlight Secure Enforcement High Availability 100 Mbps 54/36 K 520/520 K Yes A/A or A/P Copyright © 2015 Juniper Networks, Inc.

SRX 3400 • Ideal for medium to large enterprises and Service Provider networks • Software Security Services • App. Secure and IPS • AV and web filtering • Threat intelligence • Combination IOC/SPC card Features On-board Ethernet JUNOS Software Version Support SRX 3400 8 10/1000 + 4 SFP (on-board) 16 SFP Gb. E, 16 10/1000, or 2 XFP 10 GB (SR or L) JUNOS 12. 1 X 46 Firewall Performance (Large Packets) 30 Gbps Firewall Performance (IMIX) 10 Gbps Firewall Performance (Firewall + Routing PPS 64 byte) 3. 5 Mpps VPN Performance – AES 256+SHA-1 or 3 DES+SHA 1 8 Gbps App. Secure 16 Gbps Intrusion Prevention System 8 Gbps Connections Per Second (CPS) 150 K Maximum Concurrent Sessions 3 M High Availability A/A or A/P line cards 73 power supply slot cover Copyright © 2015 Juniper Networks, Inc.

SRX 3600 Features • Ideal for medium to large enterprises and Service Provider networks • Software Security Services • App. Secure and IPS • AV and web filtering • Threat intelligence • Combination IOC/SPC card power supply 74 line cards slot cover On-board Ethernet JUNOS Software Version Support SRX 3600 8 10/1000 + 4 SFP (on-board) 16 SFP Gb. E, 16 10/1000, or 2 XFP 10 GB (SR or LR) JUNOS 12. 1 X 46 Firewall Performance (Large Packets) 55 Gbps Firewall Performance (IMIX) 20 Gbps Firewall Performance (Firewall + Routing PPS 64 byte) 6. 5 Mpps VPN Performance – AES 256+SHA-1 or 3 DES+SHA 1 15 Gbps App. Secure 24 Gbps Intrusion Prevention System 15 Gbps Connections Per Second (CPS) 270 K Maximum Concurrent Sessions 6 M High Availability A/A or A/P Copyright © 2015 Juniper Networks, Inc.

SRX 5400 Features • Ideal for medium to large enterprises and Service Provider networks • Software Security Services • App. Secure and IPS • AV and web filtering • Threat intelligence • Next-generation, high-performance line cards power supply On-Board Ports 100 GE – CFP/CFP 2 40 GE – QSFPP 10 GE – SFPP/XFP 1 GE - SFP JUNOS Software Version Support JUNOS 15. 1 X 49 -D 30 Firewall Performance (large Packets)* 480 Gbps Firewall Performance (IMIX)* 468 Gbps Firewall Performance (Firewall + Routing PPS 64 byte) /with Express Path 9 Mpps /98 Mpps VPN Performance – AES 256+SHA-1 or 3 DES+SHA 1 35 Gbps App. Secure (NGFW) 42 Gbps Intrusion Prevention System 22 Gbps Connections Per Second (CPS) 420 K Maximum Concurrent Sessions 42 M High Availability IOC 2 card SRX 5400 A/A or A/P SPC 2 Card SCB and RE card slot cover 75 *Performance with Express Path enabled; throughput without Express Path: 65 Gbps large packet, 25 Gbps IMIX Copyright © 2015 Juniper Networks, Inc.

SRX 5600 Features • Ideal for large enterprise, Service Provider, and public sector networks • Software Security Services • App. Secure and IPS • AV and web filtering • Threat intelligence • Next-generation, high-performance line cards SPC 2 Card IOC 2 card SRX 5600 On-board Ethernet 100 GE – CFP/CFP 2 40 GE – QSFPP 10 GE – SFPP, XFP 1 GE - SFP JUNOS Software Version Support JUNOS 15. 1 X 49 -D 30 Firewall Performance (large Packets)* 960 Gbps Firewall Performance (IMIX)* 936 Gbps Firewall Performance (Firewall + Routing PPS 64 byte) /with Express Path 23 Mpps /390 Mpps VPN Performance – AES 256+SHA-1 100 Gbps App. Secure (NGFW) 114 Gbps Intrusion Prevention System 58 Gbps Connections Per Second (CPS) 1 M Maximum Concurrent Sessions 114 M High Availability A/A or A/P SCBE and RE card 76 *Performance with Express Path enabled; throughput without Express Path: 130 Gbps Large Packet, 70 Gbps IMIX Note: IDP Performance is with Recommended policy and using 44 KB HTTP. VPN performance is based on 1420 packet size Copyright © 2015 Juniper Networks, Inc.

SRX 5800 Features • Ideal for large enterprise, Service Provider, and public sector networks • Software Security Services • App. Secure and IPS • AV and web filtering • Threat intelligence • Next-generation, high-performance line cards IOC 2 Card SPC 2 card SRX 5800 On-board Ethernet 100 GE – CFP/CFP 2 40 GE - QSFPP 10 GE – SFPP, XFP 1 GE - SFP JUNOS Software Version Support JUNOS 15. 1 X 49 -D 30 Firewall Performance (Large Packets)* 2 Tbps Firewall Performance (IMIX)* 2 Tbps Firewall Performance (Firewall + Routing PPS 64 byte) /with Express Path 50 Mpps /880 Mpps VPN Performance – AES 256+SHA-1 200 Gbps App. Secure (NGFW) 230 Gbps Intrusion Prevention System 120 Gbps Connections Per Second (CPS) 2 M Maximum Concurrent Sessions 234 M High Availability A/A or A/P SCBE and RE card 77 *Performance with Express Path enabled; throughput without Express Path: 320 Gbps Large Packet, 140 Gbps IMIX Note: IDP Performance is with Recommended policy and using 44 KB HTTP. VPN performance is based on 1420 packet size Copyright © 2015 Juniper Networks, Inc.

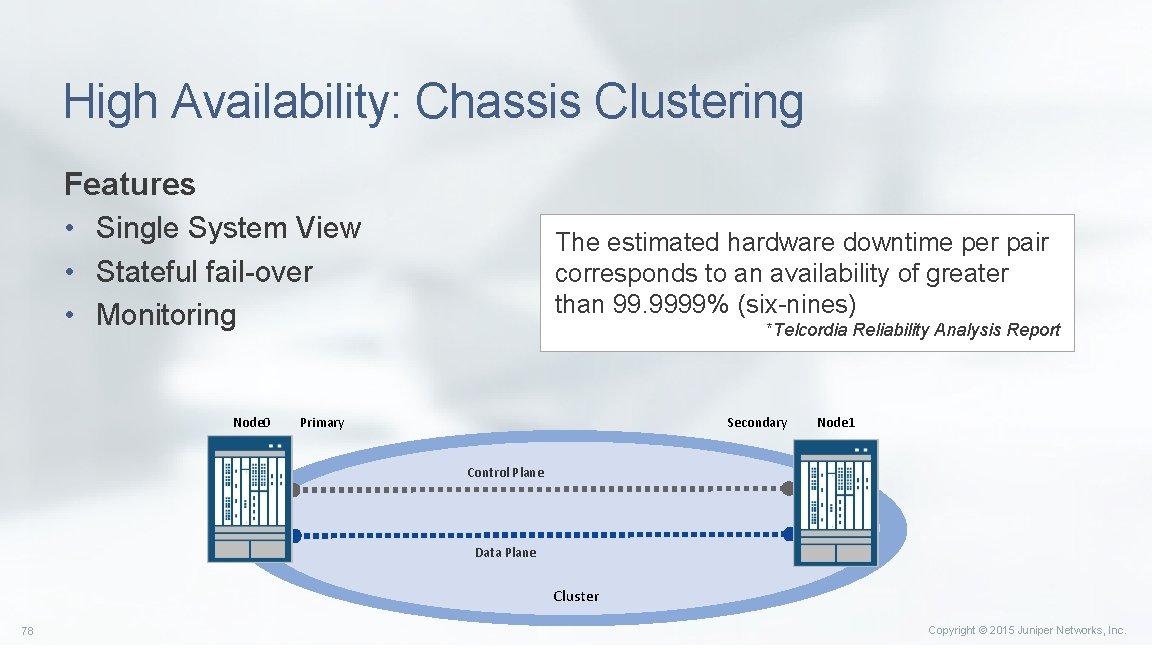
High Availability: Chassis Clustering Features • Single System View • Stateful fail-over • Monitoring Node 0 The estimated hardware downtime per pair corresponds to an availability of greater than 99. 9999% (six-nines) *Telcordia Reliability Analysis Report Primary Secondary Node 1 Control Plane Data Plane Cluster 78 Copyright © 2015 Juniper Networks, Inc.

Ease of Hardware and Software Upgrades • ISHU – In Service Hardware Upgrade • Replace hardware or add/remove cards on cluster • Example: Adding SPC to SRX • ISSU – In Service Software Upgrade • • 79 SRX node SW upgrade while it is in service Upgrade software to higher version, no hardware change Single command to trigger ISSU (without manual intervention) Minimal traffic loss (~1 sec*) at every failover Copyright © 2015 Juniper Networks, Inc.

Introducing Industry’s Fastest Firewall SRX 5800 § Industry leading 2 Terabits per Second IMIX Throughput § Third generation IOC 3 § 240 Gbps Fabric and 2 X bandwidth increase over prior card § SCB 3 § Enhanced midplane § Express Path § Differentiated throughput levels delivered by custom HW and optimized SW § Operational simplicity and agility § Deployed in mixed configurations with existing and new cards § Modular throughput and scale for investment protection 80 Copyright © 2015 Juniper Networks, Inc.

Juniper Security Management 81 Copyright © 2015 Juniper Networks, Inc.

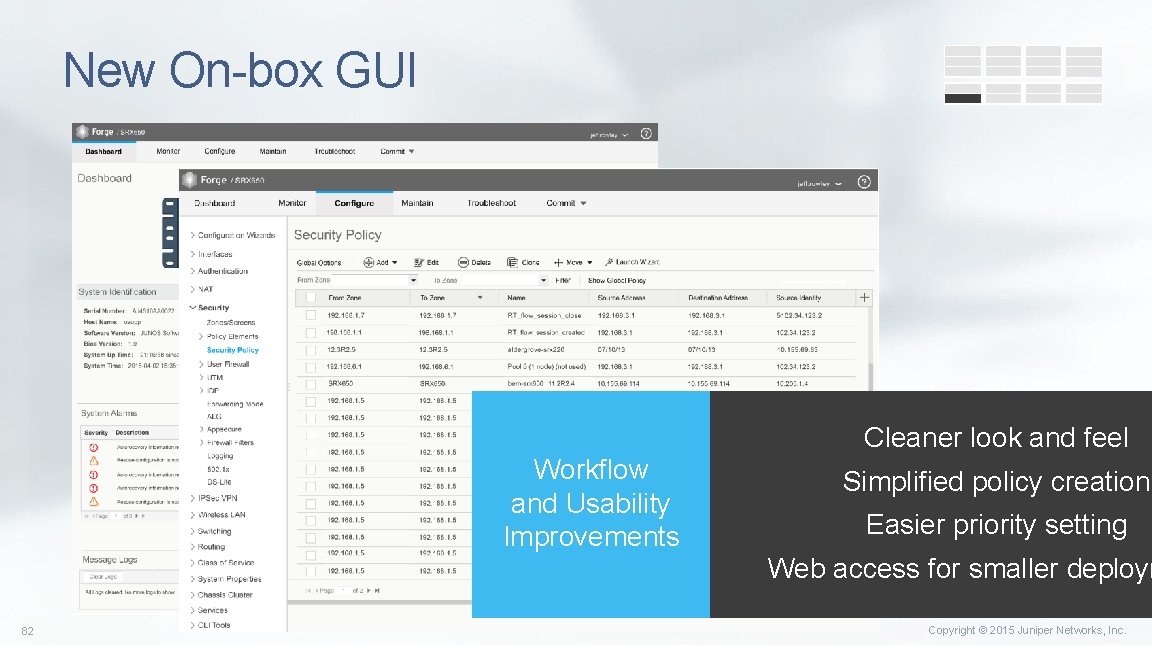
New On-box GUI Cleaner look and feel Workflow and Usability Improvements Simplified policy creation Easier priority setting Web access for smaller deploym 82 Copyright © 2015 Juniper Networks, Inc.

Security Director Scalable Security Management • Delivers scalable, responsive, and accurate policy management • Enables intuitive web-based policy lifecycle management AUTOMATES Firewall management IPsec VPN management Network Address Translation (NAT) management Intrusion prevention (IPS) signature management Application-level and UTM policy management Threat intelligence enforcement 83 Copyright © 2015 Juniper Networks, Inc.

Newly Enhanced Security Director Complete Remodel 84 Dashboard • Fully and easily customizable • Thirty-eight predefined widgets to view what is important to you • Quickly navigate from dashboard to drill down Firewall Policy • Separate views for policy rules and device rules • Instant analysis during creation of rules • Expert recommendations for rule placement and anomalies Threat Map • Integrated map and table of threat event data • Blacklist threatening IP’s with a single click • Hover and click for detailed regional threat data Events and Logs • More visualization for easy scanning • See across multiple event types for better analysis • Summary information for quick overviews Application Visibility • Granular control for applications, users and features • Better visualization for faster analysis • Block user from applications with one click Copyright © 2015 Juniper Networks, Inc.

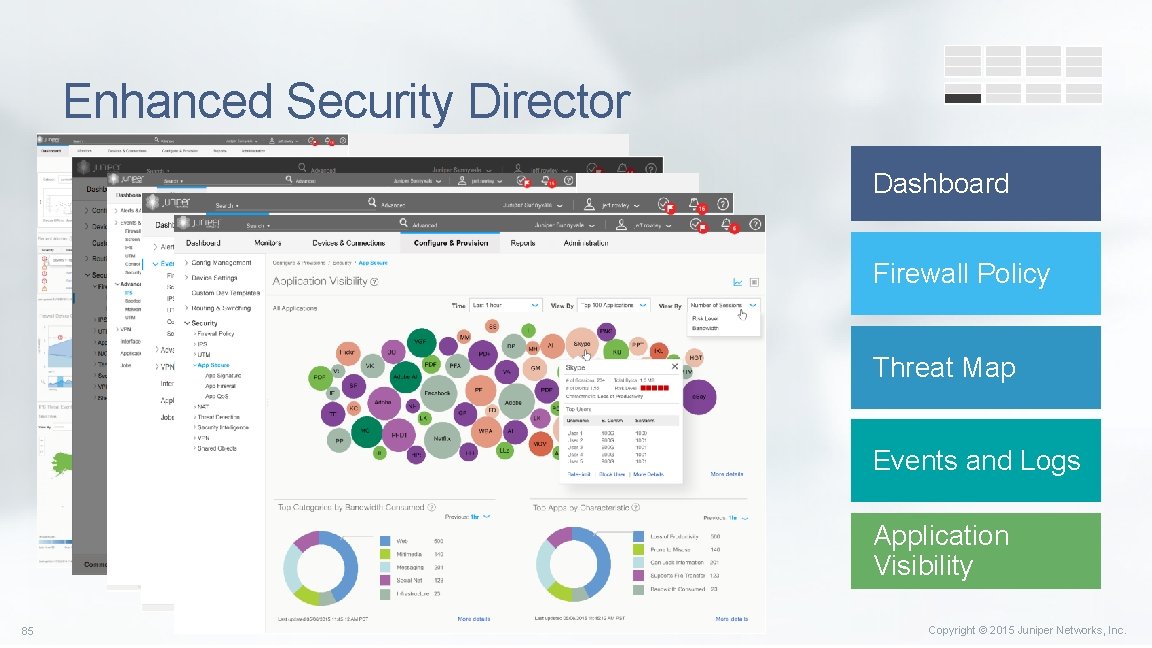
Enhanced Security Director Dashboard Firewall Policy Threat Map Events and Logs Application Visibility 85 Copyright © 2015 Juniper Networks, Inc.

Sizing Juniper Security 86 Copyright © 2015 Juniper Networks, Inc.

How to Size an SRX Questions to Ask 87 How fast is your network link? What security services do you want to have running on the appliance? • Check the VPN max speed to ensure it is at or above line speed • Key for Secure Router use case • Check the NGFW max speed to ensure it is at or above line speed • Key for NGFW use case ? What kind of WAN interface do you need? • All branch devices support on-box Ethernet or SFP interfaces as a WAN interfaces • If you need non. Ethernet WAN interfaces such as DSL and T 1, you must choose SRX 300, 345, or 550 Will your branch office be growing in terms of bandwidth needed, people to support or security services needing to be supported? • Based on budget, you may want to increase the size of the firewall for future growth How many Gb. E ports are required? • • SRX 300, 320 = 8 SRX 340, 345 = 16 SRX 550 = 42 SRX 1500 = 16 1 GE, 4 10 GE Copyright © 2015 Juniper Networks, Inc.

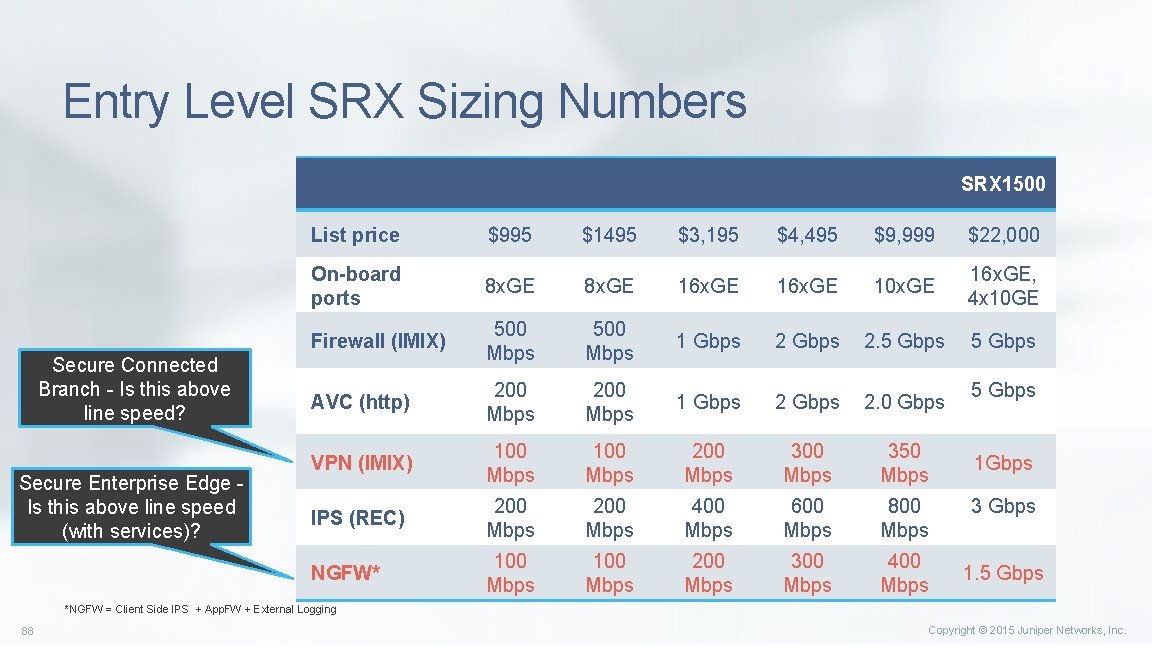
Entry Level SRX Sizing Numbers Product Secure Connected Branch - Is this above line speed? Secure Enterprise Edge Is this above line speed (with services)? SRX 300 SRX 320 SRX 345 SRX 550 SRX 1500 List price $995 $1495 $3, 195 $4, 495 $9, 999 $22, 000 On-board ports 8 x. GE 16 x. GE 10 x. GE 16 x. GE, 4 x 10 GE Firewall (IMIX) 500 Mbps 1 Gbps 2. 5 Gbps AVC (http) 200 Mbps 1 Gbps 2. 0 Gbps VPN (IMIX) 100 Mbps 200 Mbps 350 Mbps IPS (REC) 200 Mbps 400 Mbps 600 Mbps 800 Mbps NGFW* 100 Mbps 200 Mbps 300 Mbps 400 Mbps 5 Gbps 1 Gbps 3 Gbps 1. 5 Gbps *NGFW = Client Side IPS + App. FW + External Logging 88 Copyright © 2015 Juniper Networks, Inc.

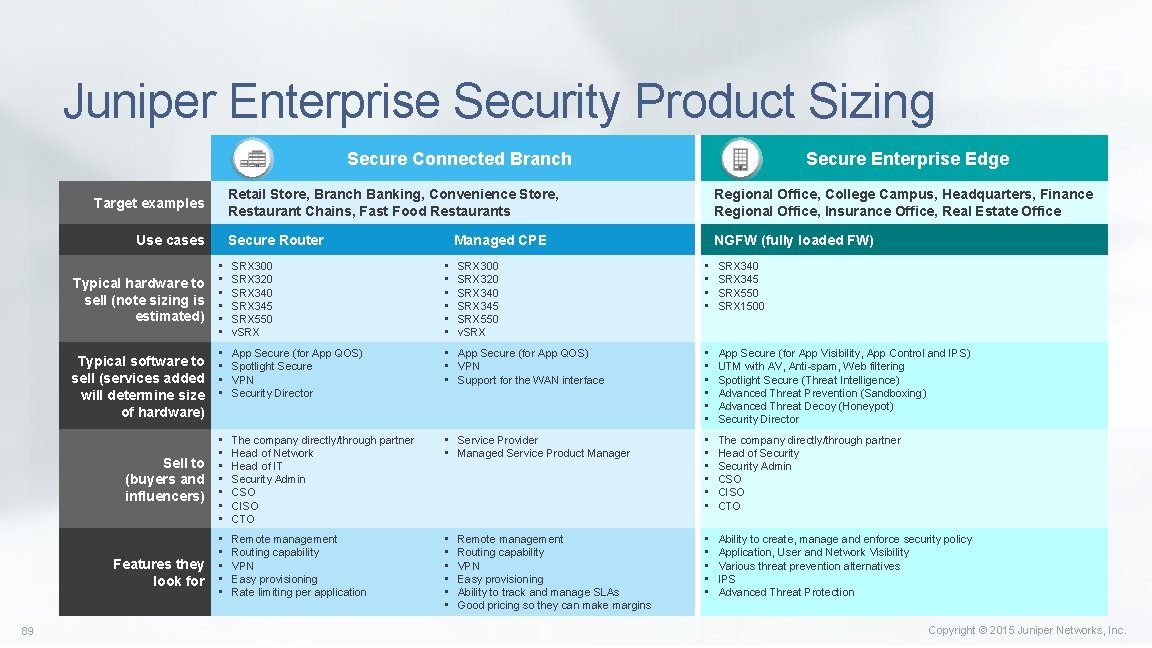
Juniper Enterprise Security Product Sizing Secure Connected Branch Target examples Use cases Typical hardware to sell (note sizing is estimated) Typical software to sell (services added will determine size of hardware) Sell to (buyers and influencers) Features they look for 89 Secure Enterprise Edge Retail Store, Branch Banking, Convenience Store, Restaurant Chains, Fast Food Restaurants Regional Office, College Campus, Headquarters, Finance Regional Office, Insurance Office, Real Estate Office Secure Router NGFW (fully loaded FW) Managed CPE • • • SRX 300 SRX 320 SRX 345 SRX 550 v. SRX • • • SRX 340 SRX 345 SRX 550 SRX 1500 • • App Secure (for App QOS) Spotlight Secure VPN Security Director • App Secure (for App QOS) • VPN • Support for the WAN interface • • • App Secure (for App Visibility, App Control and IPS) UTM with AV, Anti-spam, Web filtering Spotlight Secure (Threat Intelligence) Advanced Threat Prevention (Sandboxing) Advanced Threat Decoy (Honeypot) Security Director • • The company directly/through partner Head of Network Head of IT Security Admin CSO CISO CTO • Service Provider • Managed Service Product Manager • • • The company directly/through partner Head of Security Admin CSO CISO CTO • • • Remote management Routing capability VPN Easy provisioning Rate limiting per application • • • Ability to create, manage and enforce security policy Application, User and Network Visibility Various threat prevention alternatives IPS Advanced Threat Protection SRX 300 SRX 320 SRX 345 SRX 550 v. SRX Remote management Routing capability VPN Easy provisioning Ability to track and manage SLAs Good pricing so they can make margins Copyright © 2015 Juniper Networks, Inc.

Thank You 90 Copyright © 2015 Juniper Networks, Inc.