Wireless Internet Protocols and Performance Carey Williamson i


































- Slides: 138

Wireless Internet: Protocols and Performance Carey Williamson i. CORE Professor Department of Computer Science University of Calgary C. Williamson Wireless 2003 Tutorial 1

Tutorial Outline r 1. Introduction/Motivation (10 min) r 2. Networking Terminology (10 min) r 3. IEEE 802. 11 b WLANs (30 min) r 4. TCP (20 min) r 5. HTTP (15 min) r r ---- Coffee Break Here ---- (10: 30 -10: 45 am) 6. Wireless TCP Performance: Part 1 (15 min) 7. Wireless TCP Performance: Part 2 (15 min) 8. Wireless Web Performance (30 min) 9. Summary, Questions, Discussion (10 min) C. Williamson Wireless 2003 Tutorial 2

1. Wireless Internet: Introduction C. Williamson Wireless 2003 Tutorial 3

What Is Wireless Networking? r The use of infra-red (IR) or radio frequency (RF) signals to share information and resources between devices r A hot computer industry buzzword: m m Lots of advertising by companies and media Wireless Broadband, 3 G wireless, 4 G, WAP, i. Mode, Bluetooth, Wi. Fi r Mobile Internet, Pervasive Computing, Nomadic Computing, M-commerce m Ubiquitous; Global; Revolutionary C. Williamson Wireless 2003 Tutorial 4

Two Popular 2. 4 GHz Standards: r IEEE 802. 11 m Fast (11 b) m High Power m Long range m Single-purpose m Ethernet replacement m Easily Available r Bluetooth m Slow m Low Power m Short range m Flexible m Cable replacement m “Vapourware” (? ) • Apple Airport, i. Book, G 4 • Cisco Aironet 350 C. Williamson Wireless 2003 Tutorial 5

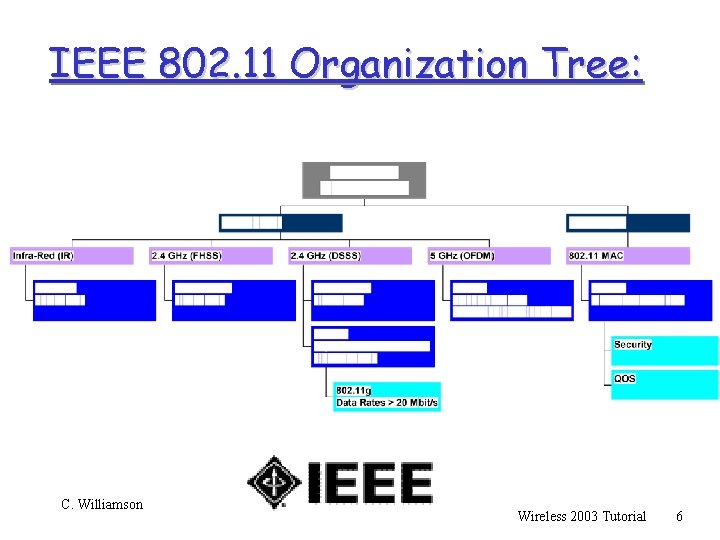
IEEE 802. 11 Organization Tree: C. Williamson Wireless 2003 Tutorial 6

Pros and Cons of 802. 11: r Pro: m High bandwidth (up to 11 Mbps) m Two modes of operation: infrastructure vs. ad hoc r Con: m Incompatibility between old and new cards m Signal blocked by reinforced concrete or tinted glass m High channel BER can degrade performance (lots!) m No standard for hand-off between base stations m Some channel numbers overlap spectrum m High power consumption in laptops C. Williamson Wireless 2003 Tutorial 7

Bluetooth r Think USB, not Ethernet r Cable replacement technology r Created by Ericsson r PAN - Personal Area Network m 1 -2 Mbps connections m 1600 hops per second FHSS m Includes synchronous, asynchronous, voice connections m Piconet routing r Small, low-power, short-range, cheap, versatile radios r Used as Internet connection, phone, or headset r Master/slave configuration and scheduling C. Williamson Wireless 2003 Tutorial 8

Security r Wireless sniffers, “war driving” r IEEE 802. 11: m ESSID – Extended Services Set ID m WEP – Wired Equivalent Privacy (useless) m NAT - Network Address Translation (firewall) r Bluetooth Security m FHSS, with rapid hop sequence m Short range m Encrypted transmissions (optional) C. Williamson Wireless 2003 Tutorial 9

Guerrilla. net r An underground alternative to the wired Internet r A grassroots movement established in 1996 m 802. 11 Wireless LAN cards m Roof mounted antennae m Free software (Free. BSD) r Multi-hop routing, Internet connectivity r About $500 per node (and dropping) r Other networks popping up in SF, Seattle, London C. Williamson Wireless 2003 Tutorial 10

Future of Wireless r Higher data rates r Better security r Wider selection of products r Lower prices r Zero configuration networking r More end-user focus r Better software r Less visible r More popular C. Williamson Wireless 2003 Tutorial 11

2. Background: Networking Terminology C. Williamson Wireless 2003 Tutorial 12

Wireless Internet Technologies r Mobile devices (e. g. , notebooks, laptops, PDAs, cell phones, wearable computers) r Wireless network access m m m Bluetooth (1 Mbps, up to 3 meters) IEEE 802. 11 b (11 Mbps, up to 100 meters) IEEE 802. 11 a (55 Mbps, up to 20 meters) r Operating modes: m Infrastructure mode (access point) m Ad hoc mode r Wireless Web, Wi. Fi “hot spots” C. Williamson Wireless 2003 Tutorial 13

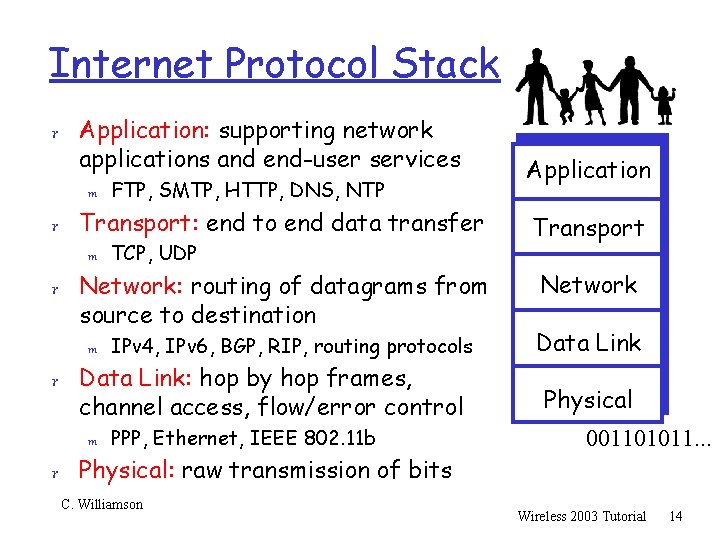
Internet Protocol Stack r Application: supporting network applications and end-user services m FTP, SMTP, HTTP, DNS, NTP Application r Transport: end to end data transfer m TCP, UDP Transport r Network: routing of datagrams from Network source to destination m IPv 4, IPv 6, BGP, RIP, routing protocols r Data Link: hop by hop frames, channel access, flow/error control m PPP, Ethernet, IEEE 802. 11 b Data Link Physical 001101011. . . r Physical: raw transmission of bits C. Williamson Wireless 2003 Tutorial 14

Internet Protocol Stack r Application: m e. g. , Hyper-Text Transfer Protocol (HTTP) r Transport: m Transmission Control Protocol (TCP) m User Datagram Protocol (UDP) r Network: m Internet Protocol (IP, IPv 4, IPv 6) r Data Link: m e. g. , IEEE 802. 3 Ethernet, IEEE 802. 11 b r Physical: m Device specific, network specific C. Williamson Application Transport Network Data Link Physical 001101011. . . Wireless 2003 Tutorial 15

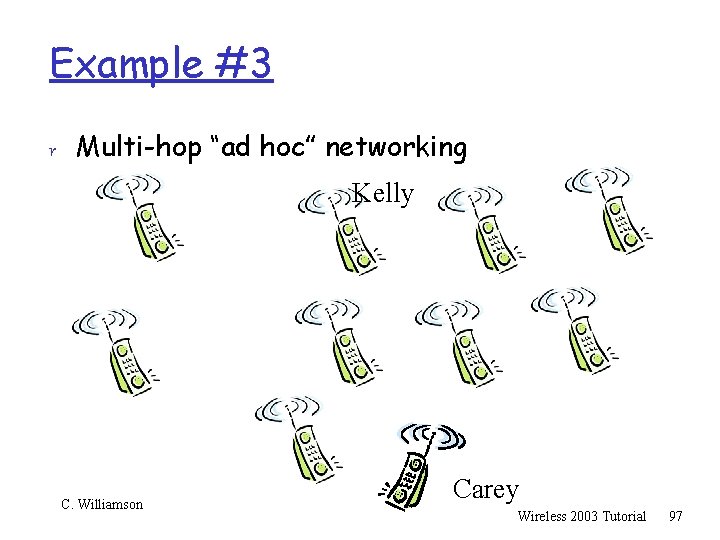
Multi-Hop Wireless Ad Hoc Networks r Routing protocols used to improve wireless connections r Infrastructure-free, dynamic r True Peer-to-Peer routing r Fault tolerant r Examples: AODV, DSDV, TORA, DSR, . . . C. Williamson Wireless 2003 Tutorial 16

Example: r Multi-hop “ad hoc” networking Kelly C. Williamson Carey Wireless 2003 Tutorial 17

3. IEEE 802. 11 b Wireless LANs C. Williamson Wireless 2003 Tutorial 18

The Basics r In several respects, the IEEE 802. 11 b wireless LAN (WLAN) standard is similar to that for IEEE 802. 3 (Ethernet) LANs r Similarities: m LAN; limited geographic coverage; multiple stations; shared transmission medium; CSMAbased Medium Access Control protocol; 48 -bit MAC addresses; comparable data rates (11 Mbps vs 10 Mbps) C. Williamson Wireless 2003 Tutorial 19

The Basics (Cont’d) r But there also distinct differences: m wireless (air interface) versus wired (coax) m wireless propagation environment (multipath) m higher error rate due to interference, etc. m successful frames are ACKed by receiver m mobile stations; “hidden node” problem; potential asymmetries m CSMA/CA versus CSMA/CD m multiple data transmission rates (1, 2, 5. 5, 11) C. Williamson Wireless 2003 Tutorial 20

Some Features r Infrastructure mode vs “ad hoc” mode r Access Point (AP) sends “beacon frames” m Mobiles choose AP based on signal strength r Multiple channel access protocols supported m CSMA/CA (DCF); PCF; RTS/CTS r MAC-layer can provide error control, retransmission, rate adaptation, etc. r Direct Sequence Spread Spectrum (DSSS) m signal spread across 14 22 -MHz channels C. Williamson Wireless 2003 Tutorial 21

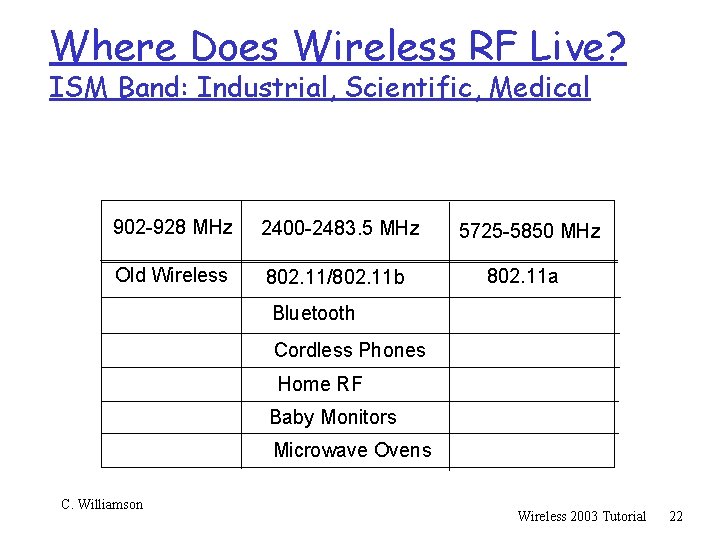
Where Does Wireless RF Live? ISM Band: Industrial, Scientific, Medical 902 -928 MHz 2400 -2483. 5 MHz Old Wireless 802. 11/802. 11 b 5725 -5850 MHz 802. 11 a Bluetooth Cordless Phones Home RF Baby Monitors Microwave Ovens C. Williamson Wireless 2003 Tutorial 22

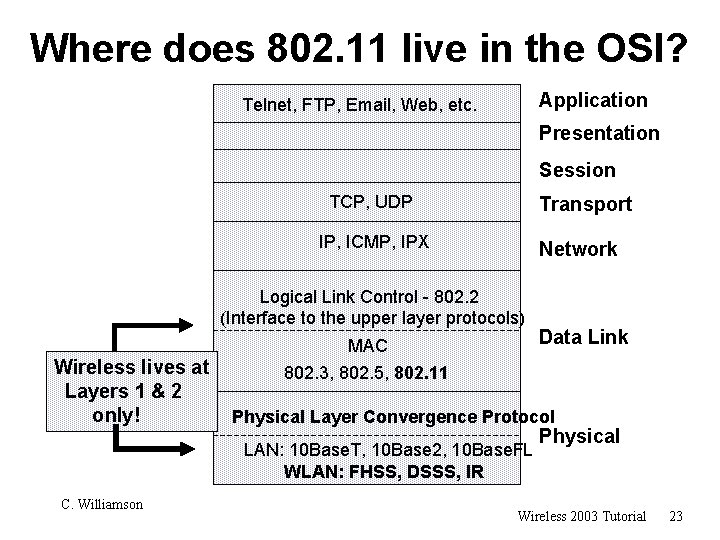
Where does 802. 11 live in the OSI? Application Telnet, FTP, Email, Web, etc. Presentation Session TCP, UDP Transport IP, ICMP, IPX Network Logical Link Control - 802. 2 (Interface to the upper layer protocols) MAC Wireless lives at Layers 1 & 2 only! 802. 3, 802. 5, 802. 11 Physical Layer Convergence Protocol LAN: 10 Base. T, 10 Base 2, 10 Base. FL WLAN: FHSS, DSSS, IR C. Williamson Data Link Physical Wireless 2003 Tutorial 23

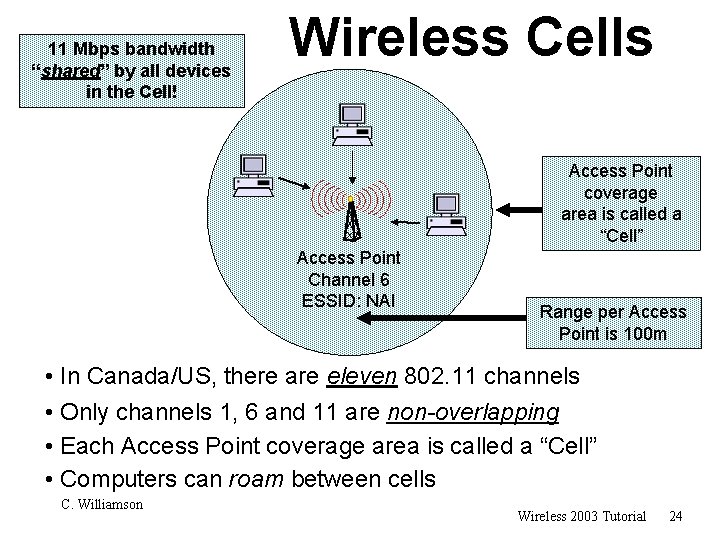
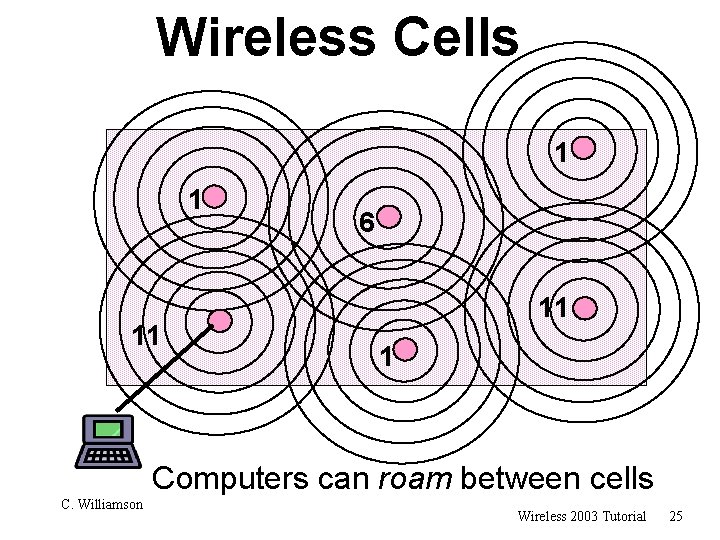
11 Mbps bandwidth “shared” by all devices in the Cell! Wireless Cells Access Point coverage area is called a “Cell” Access Point Channel 6 ESSID: NAI Range per Access Point is 100 m • In Canada/US, there are eleven 802. 11 channels • Only channels 1, 6 and 11 are non-overlapping • Each Access Point coverage area is called a “Cell” • Computers can roam between cells C. Williamson Wireless 2003 Tutorial 24

Wireless Cells 1 1 11 6 11 1 Computers can roam between cells C. Williamson Wireless 2003 Tutorial 25

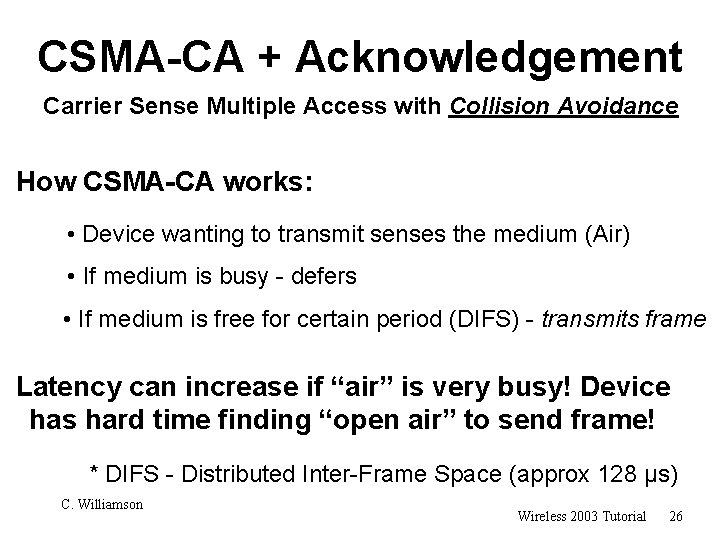
CSMA-CA + Acknowledgement Carrier Sense Multiple Access with Collision Avoidance How CSMA-CA works: • Device wanting to transmit senses the medium (Air) • If medium is busy - defers • If medium is free for certain period (DIFS) - transmits frame Latency can increase if “air” is very busy! Device has hard time finding “open air” to send frame! * DIFS - Distributed Inter-Frame Space (approx 128 µs) C. Williamson Wireless 2003 Tutorial 26

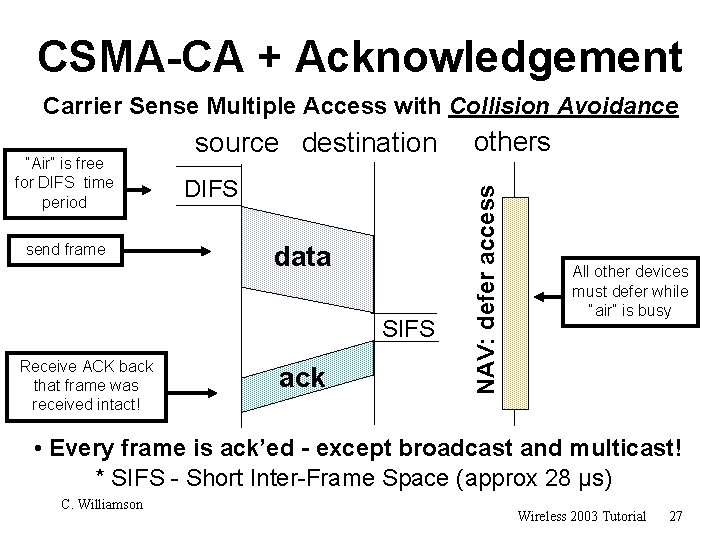
CSMA-CA + Acknowledgement Carrier Sense Multiple Access with Collision Avoidance send frame DIFS data SIFS Receive ACK back that frame was received intact! ack others NAV: defer access “Air” is free for DIFS time period source destination All other devices must defer while “air” is busy • Every frame is ack’ed - except broadcast and multicast! * SIFS - Short Inter-Frame Space (approx 28 µs) C. Williamson Wireless 2003 Tutorial 27

MAC-Layer Retransmission r If no ACK received “right away”, then the sender retransmits the frame again at the MAC layer m m m indicates frame (or ACK) was lost/corrupted very short timeout (e. g. , 1 msec) exponential backoff (doubling) if repeated loss r Typically recovers before TCP would notice r Max retransmission limit (e. g. , 8) r May do MAC-layer rate adaptation or frame fragmentation if channel error rate is high C. Williamson Wireless 2003 Tutorial 28

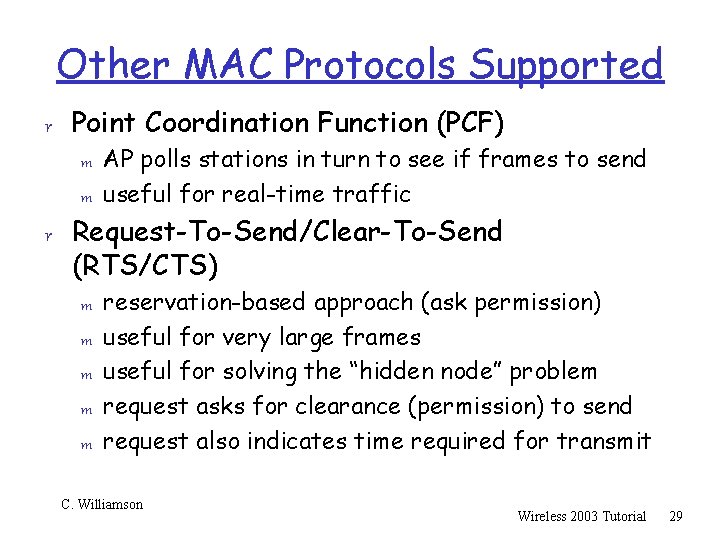
Other MAC Protocols Supported r Point Coordination Function (PCF) m AP polls stations in turn to see if frames to send m useful for real-time traffic r Request-To-Send/Clear-To-Send (RTS/CTS) m m m reservation-based approach (ask permission) useful for very large frames useful for solving the “hidden node” problem request asks for clearance (permission) to send request also indicates time required for transmit C. Williamson Wireless 2003 Tutorial 29

Frame Formats r Two frame formats available: m long preamble m short preamble r Configuration option for NIC and AP r Variable-size frames (max 2312 data bytes) r 16 -bit Cyclic Redundancy Code (CRC) for error checking of frames C. Williamson Wireless 2003 Tutorial 30

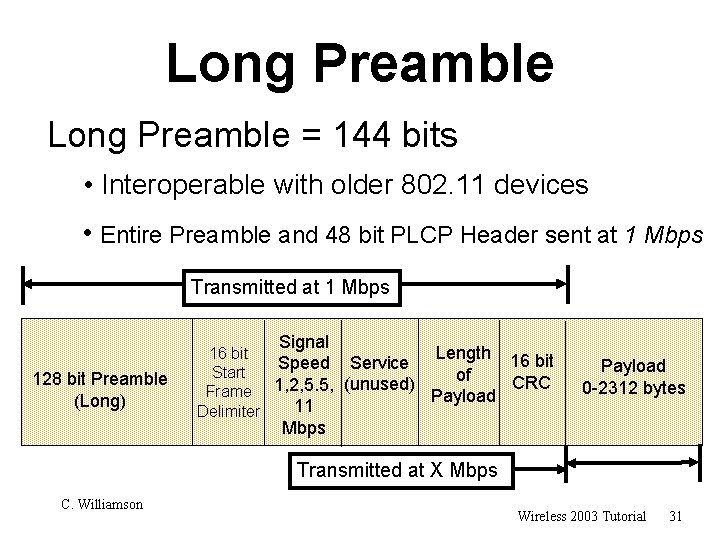
Long Preamble = 144 bits • Interoperable with older 802. 11 devices • Entire Preamble and 48 bit PLCP Header sent at 1 Mbps Transmitted at 1 Mbps Signal 128 bit Preamble (Long) 16 bit Length 16 bit Service Speed Start of CRC (unused) 1, 2, 5. 5, Frame Payload 11 Delimiter Payload 0 -2312 bytes Mbps Transmitted at X Mbps C. Williamson Wireless 2003 Tutorial 31

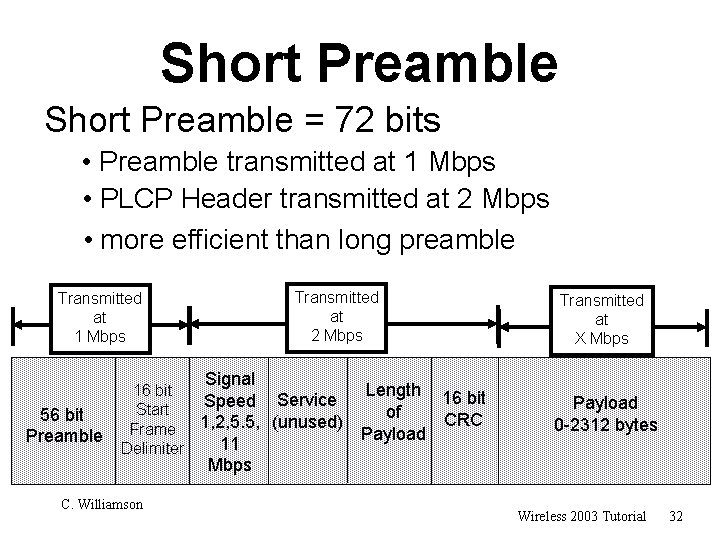
Short Preamble = 72 bits • Preamble transmitted at 1 Mbps • PLCP Header transmitted at 2 Mbps • more efficient than long preamble Transmitted at 2 Mbps Transmitted at 1 Mbps Signal 56 bit Preamble 16 bit Speed Service Start 1, 2, 5. 5, (unused) Frame 11 Delimiter Length 16 bit of CRC Payload Transmitted at X Mbps Payload 0 -2312 bytes Mbps C. Williamson Wireless 2003 Tutorial 32

Even More Features r Power Management m mobile nodes can “sleep” to save power m AP will buffer frames until client requests them m AP can use virtual bitmap field in beacons to indicate which stations have data waiting r Security m Wired Equivalent Privacy (WEP) m not secure at all! C. Williamson Wireless 2003 Tutorial 33

Summary r IEEE 802. 11 b (Wi. Fi) is a wireless LAN technology that is rapidly growing in popularity r Convenient, inexpensive, easy to use r Growing number of “hot spots” everywhere m airports, hotels, bookstores, Starbucks, etc r Estimates: 70% of WLANs are insecure! C. Williamson Wireless 2003 Tutorial 34

4. TCP 101: Transmission Control Protocol C. Williamson Wireless 2003 Tutorial 35

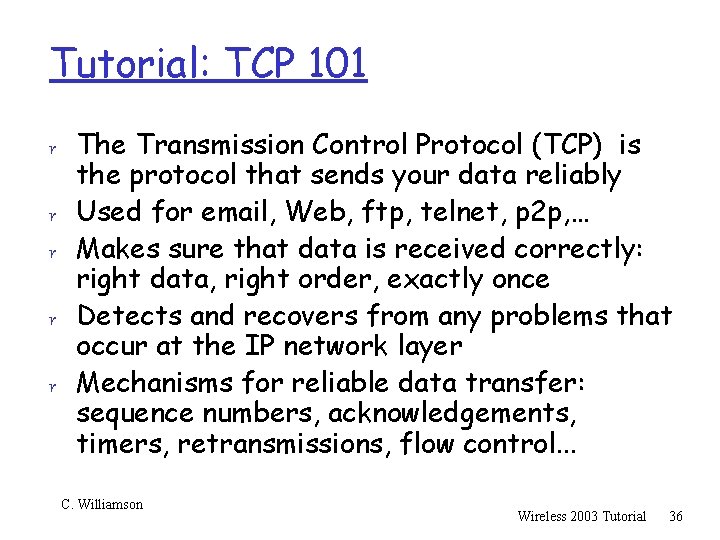
Tutorial: TCP 101 r The Transmission Control Protocol (TCP) is r r the protocol that sends your data reliably Used for email, Web, ftp, telnet, p 2 p, … Makes sure that data is received correctly: right data, right order, exactly once Detects and recovers from any problems that occur at the IP network layer Mechanisms for reliable data transfer: sequence numbers, acknowledgements, timers, retransmissions, flow control. . . C. Williamson Wireless 2003 Tutorial 36

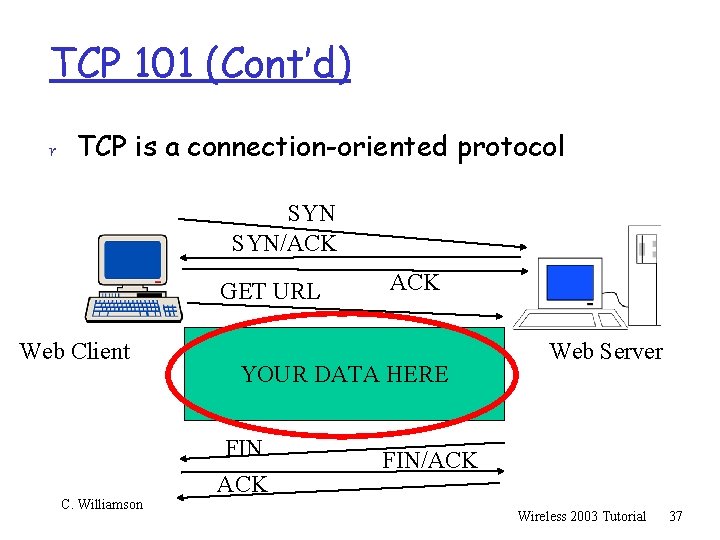
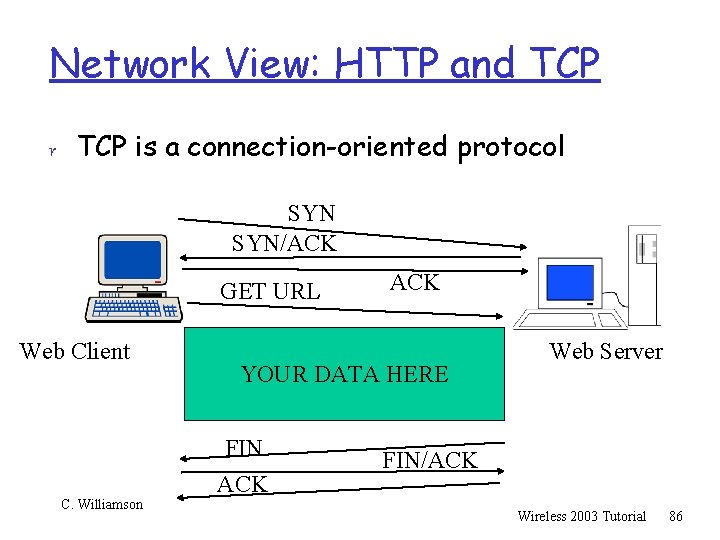
TCP 101 (Cont’d) r TCP is a connection-oriented protocol SYN/ACK GET URL Web Client C. Williamson ACK YOUR DATA HERE FIN ACK Web Server FIN/ACK Wireless 2003 Tutorial 37

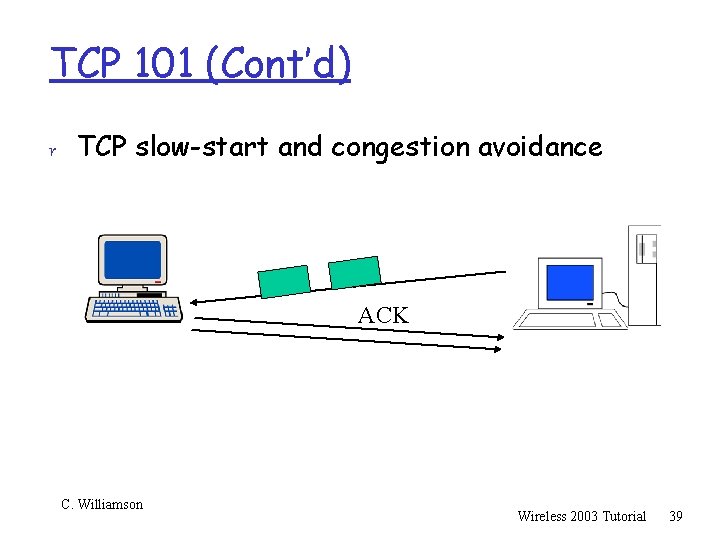
TCP 101 (Cont’d) r TCP slow-start and congestion avoidance ACK C. Williamson Wireless 2003 Tutorial 38

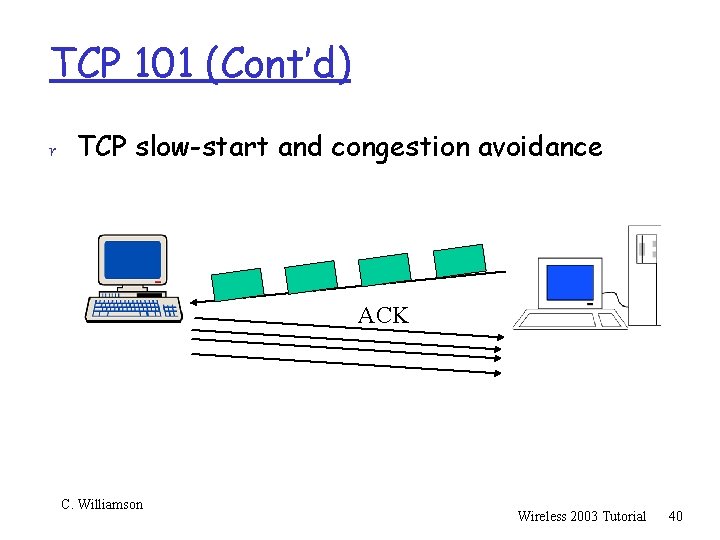
TCP 101 (Cont’d) r TCP slow-start and congestion avoidance ACK C. Williamson Wireless 2003 Tutorial 39

TCP 101 (Cont’d) r TCP slow-start and congestion avoidance ACK C. Williamson Wireless 2003 Tutorial 40

TCP 101 (Cont’d) r This (exponential growth) “slow start” process continues until either: m m m packet loss: after a brief recovery phase, you enter a (linear growth) “congestion avoidance” phase based on slow-start threshold found limit reached: slow-start threshold, or maximum advertised receive window size all done: terminate connection and go home C. Williamson Wireless 2003 Tutorial 41

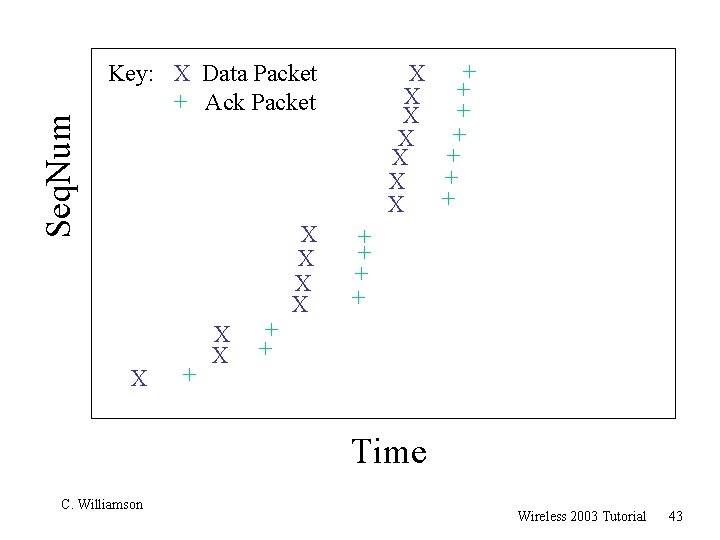
Tutorial: TCP 201 r There is a beautiful way to plot and visualize the dynamics of TCP behaviour r Called a “TCP Sequence Number Plot” r Plot packet events (data and acks) as points in 2 -D space, with time on the horizontal axis, and sequence number on the vertical axis r Example: Consider a 14 -packet transfer C. Williamson Wireless 2003 Tutorial 42

Seq. Num + X + X Key: X Data Packet + Ack Packet X + X X + + Time C. Williamson Wireless 2003 Tutorial 43

So What? r What can it tell you? r Everything!!! C. Williamson Wireless 2003 Tutorial 44

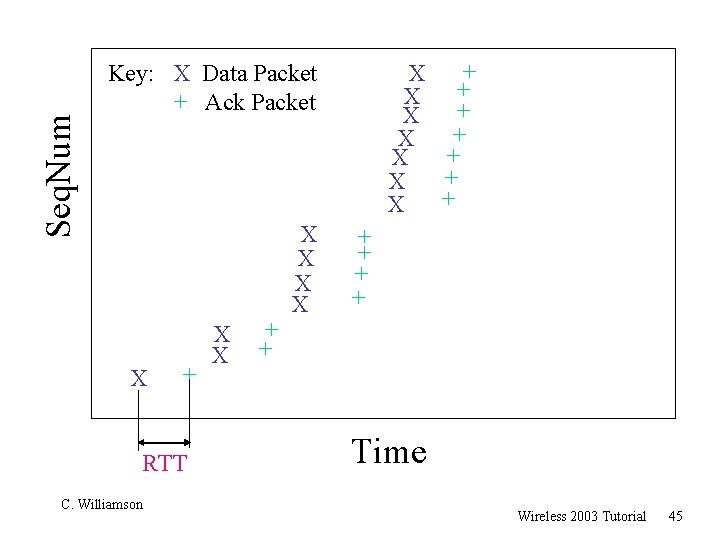
Seq. Num + X + X Key: X Data Packet + Ack Packet X + RTT C. Williamson X X + + Time Wireless 2003 Tutorial 45

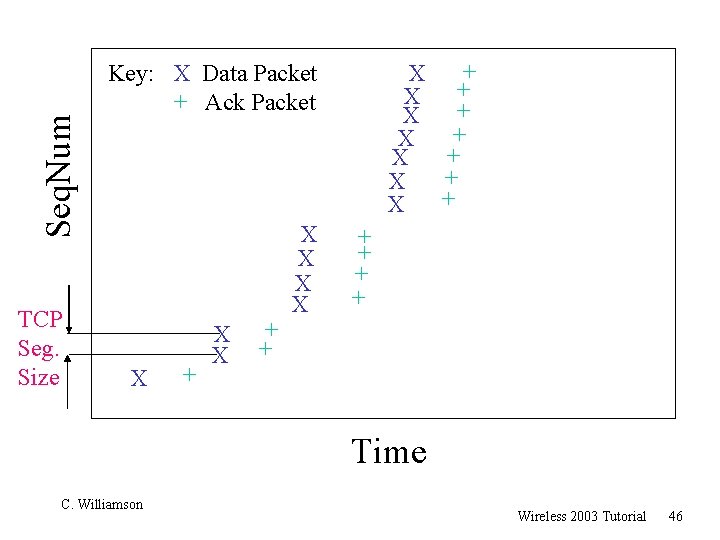
Seq. Num TCP Seg. Size + X + X Key: X Data Packet + Ack Packet X + X X + + Time C. Williamson Wireless 2003 Tutorial 46

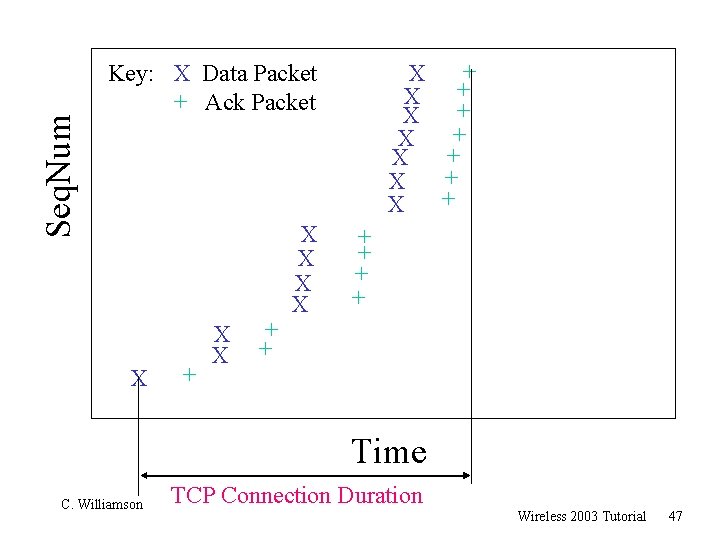
Seq. Num + X + X Key: X Data Packet + Ack Packet X + X X + + Time C. Williamson TCP Connection Duration Wireless 2003 Tutorial 47

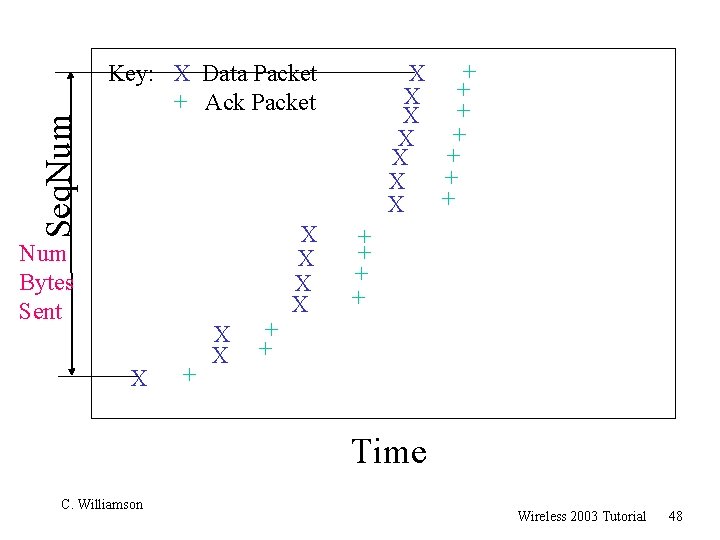
Seq. Num + X + X Key: X Data Packet + Ack Packet Num Bytes Sent X + X X + + Time C. Williamson Wireless 2003 Tutorial 48

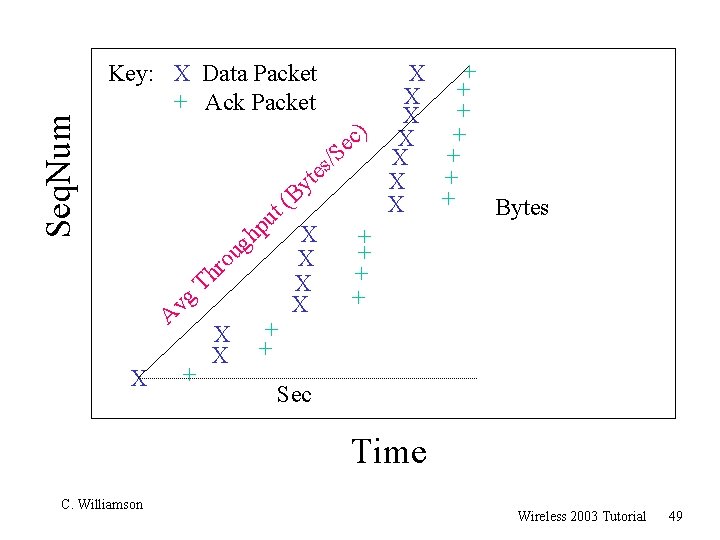
Seq. Num + X + X ) X + c e + X /S s e t + X y + (B X Bytes t u p X h + g + X ou r + X Th + X vg A X + X + Sec Key: X Data Packet + Ack Packet Time C. Williamson Wireless 2003 Tutorial 49

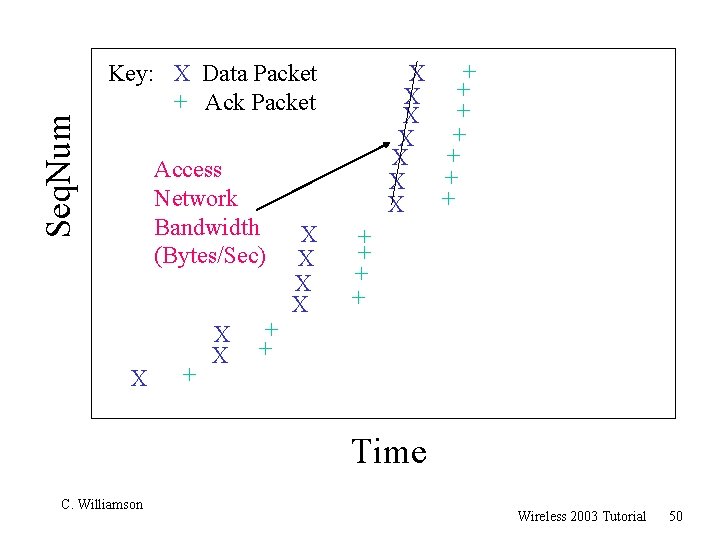
Seq. Num + X + X Key: X Data Packet + Ack Packet Access Network Bandwidth (Bytes/Sec) X + X X + + Time C. Williamson Wireless 2003 Tutorial 50

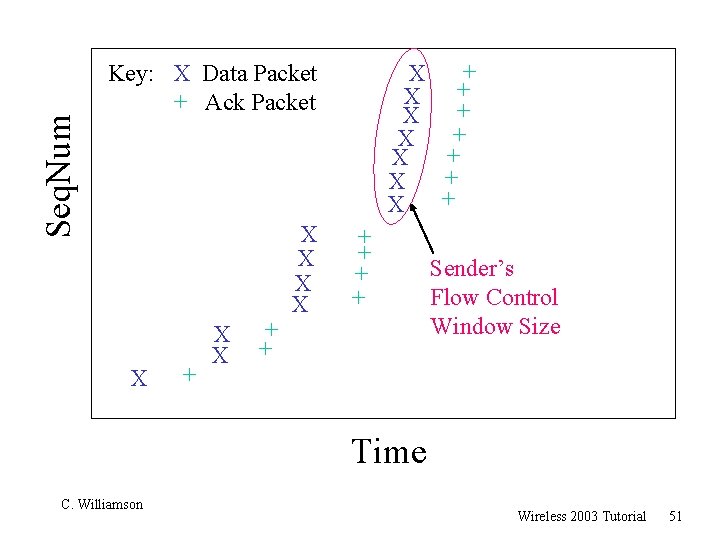
Seq. Num + X + X Key: X Data Packet + Ack Packet X + X X + + Sender’s Flow Control Window Size Time C. Williamson Wireless 2003 Tutorial 51

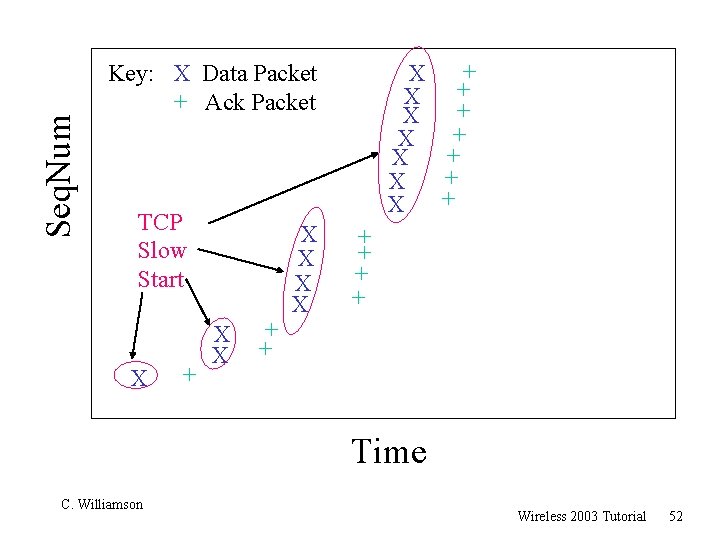
Seq. Num + X + X Key: X Data Packet + Ack Packet TCP Slow Start X + X X + + Time C. Williamson Wireless 2003 Tutorial 52

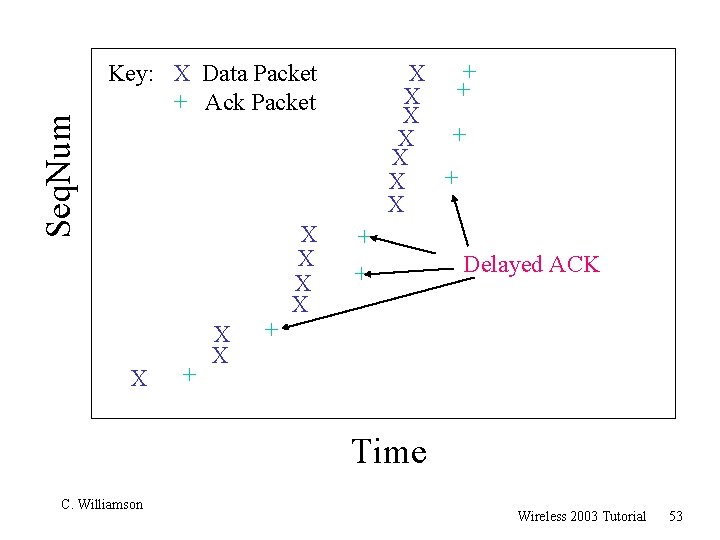
Seq. Num + X X Key: X Data Packet + Ack Packet X + X X X X + + Delayed ACK Time C. Williamson Wireless 2003 Tutorial 53

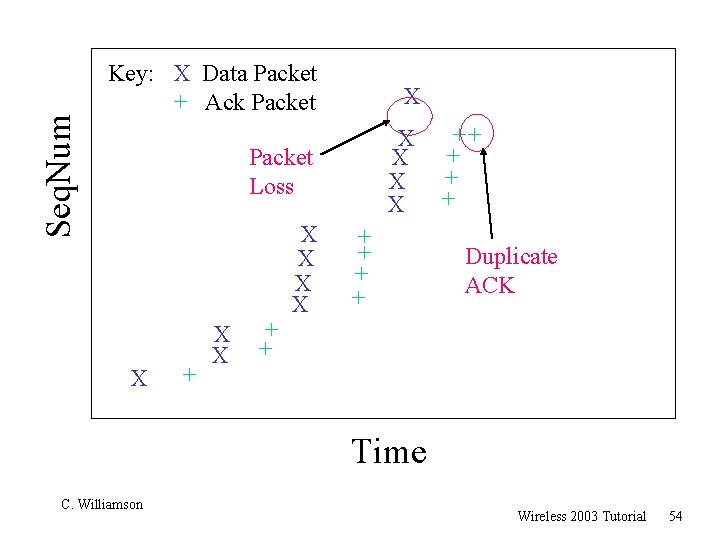
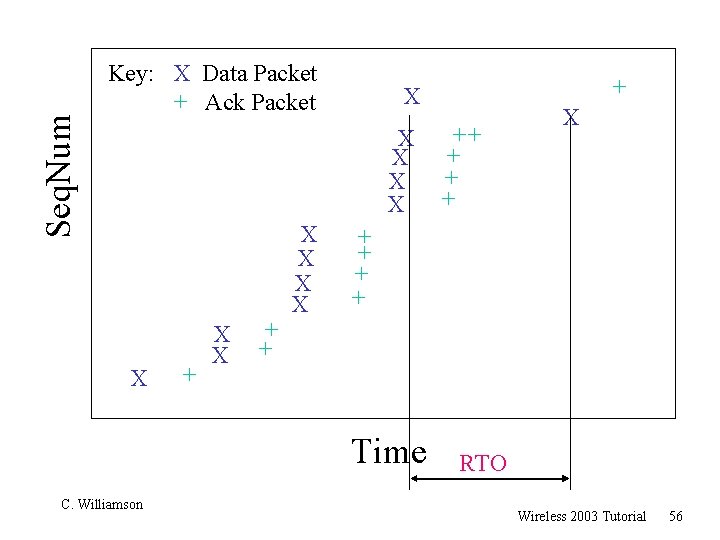
Seq. Num Key: X Data Packet + Ack Packet X Packet Loss X X X + + X X + + ++ + Duplicate ACK Time C. Williamson Wireless 2003 Tutorial 54

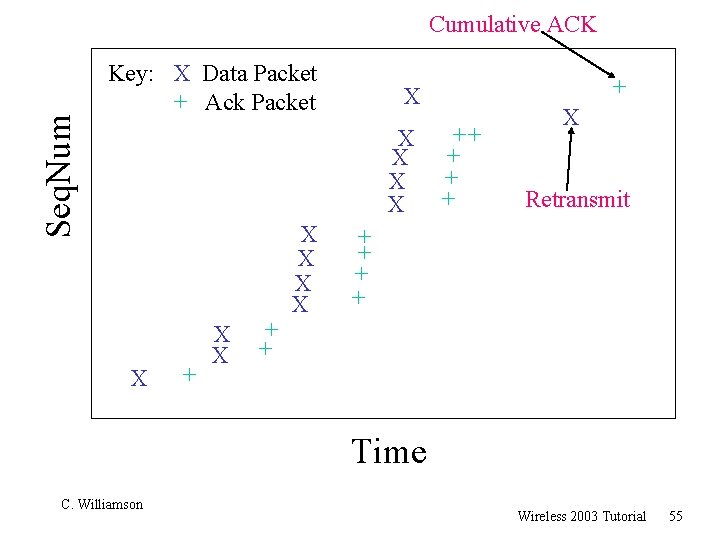
Seq. Num Cumulative ACK Key: X Data Packet + Ack Packet X X X + + X X + X ++ + X Retransmit + + Time C. Williamson Wireless 2003 Tutorial 55

Seq. Num Key: X Data Packet + Ack Packet X X X + + X X ++ + X + + Time C. Williamson + X RTO Wireless 2003 Tutorial 56

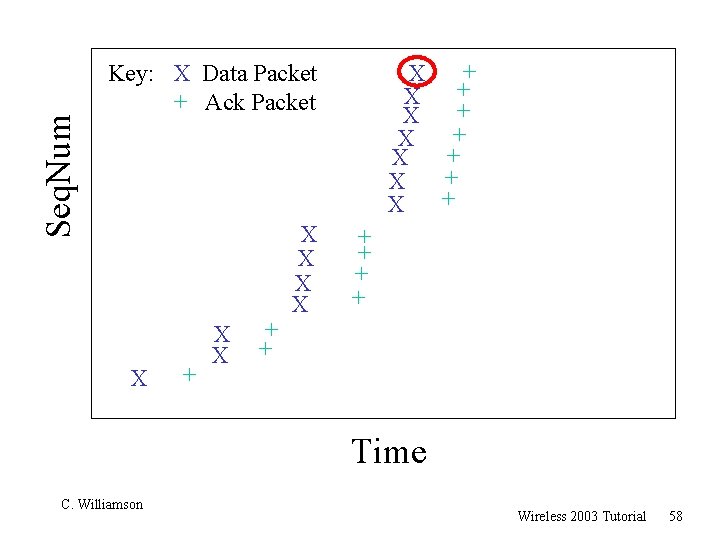
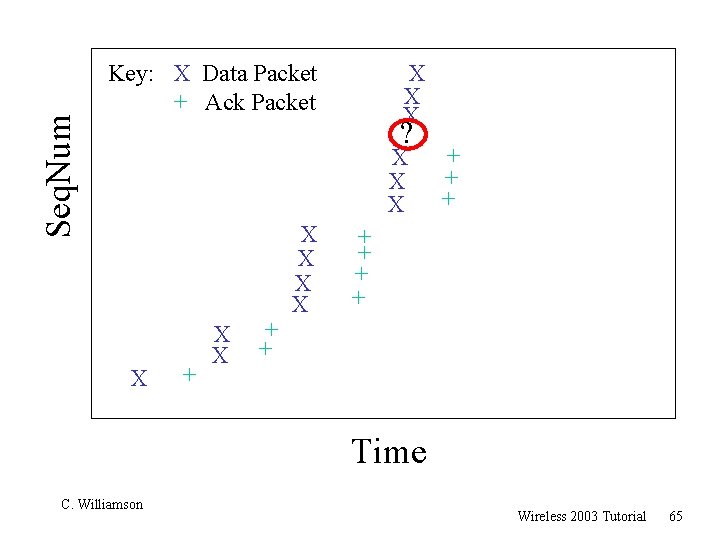
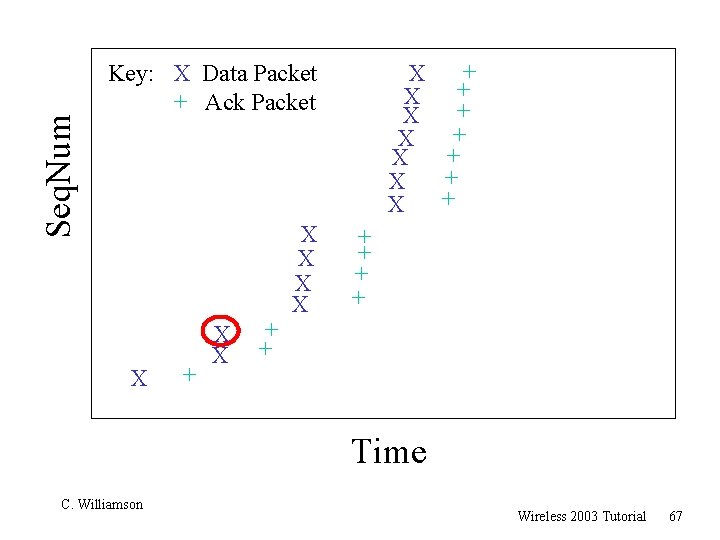
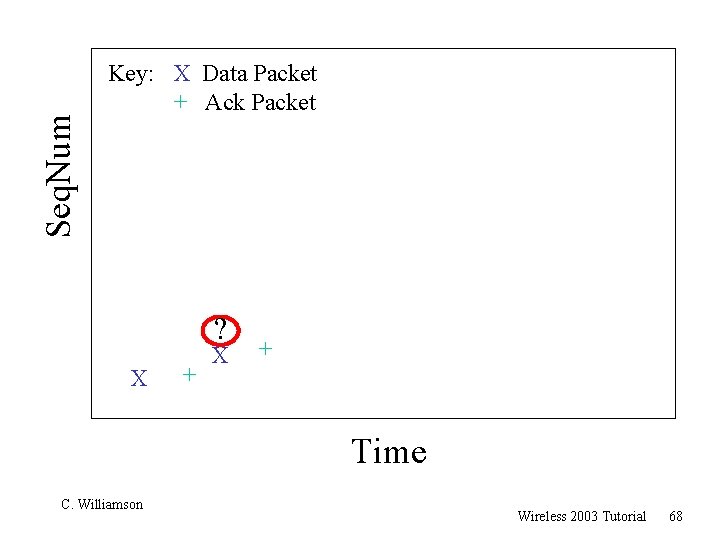
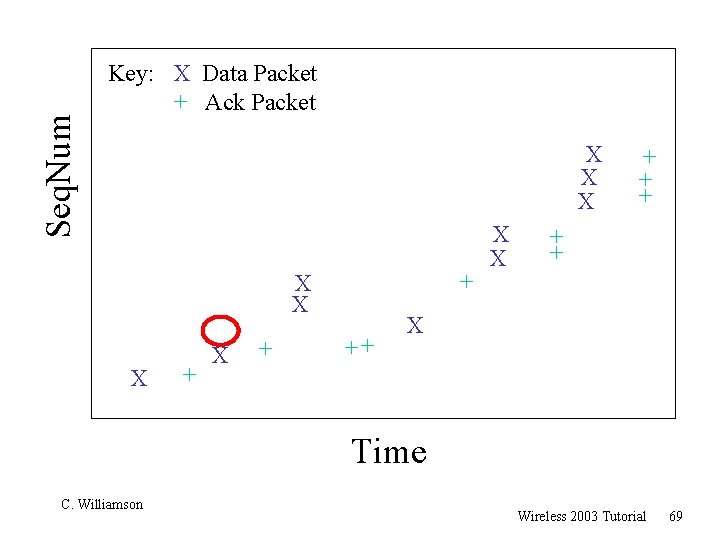
TCP 201 (Cont’d) r What happens when a packet loss occurs? r Quiz Time. . . m Consider a 14 -packet Web document m For simplicity, consider only a single packet loss C. Williamson Wireless 2003 Tutorial 57

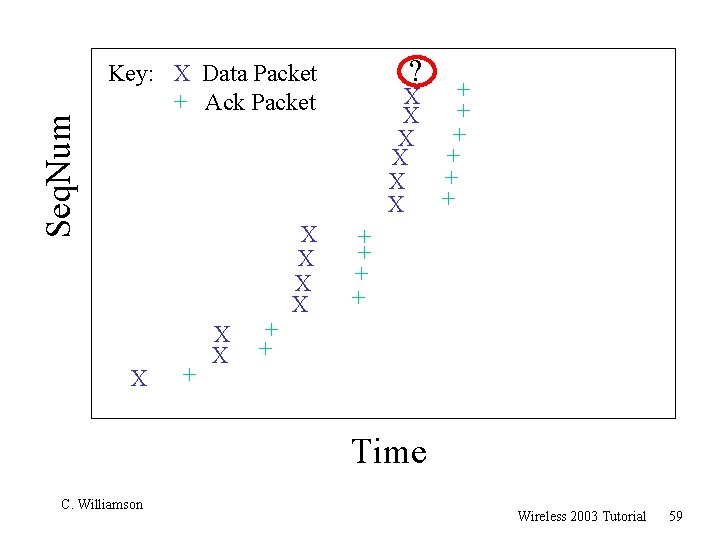
Seq. Num + X + X Key: X Data Packet + Ack Packet X + X X + + Time C. Williamson Wireless 2003 Tutorial 58

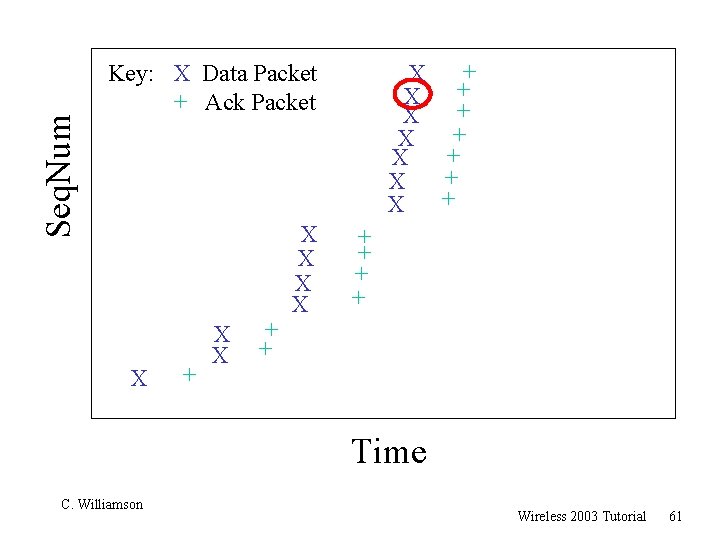
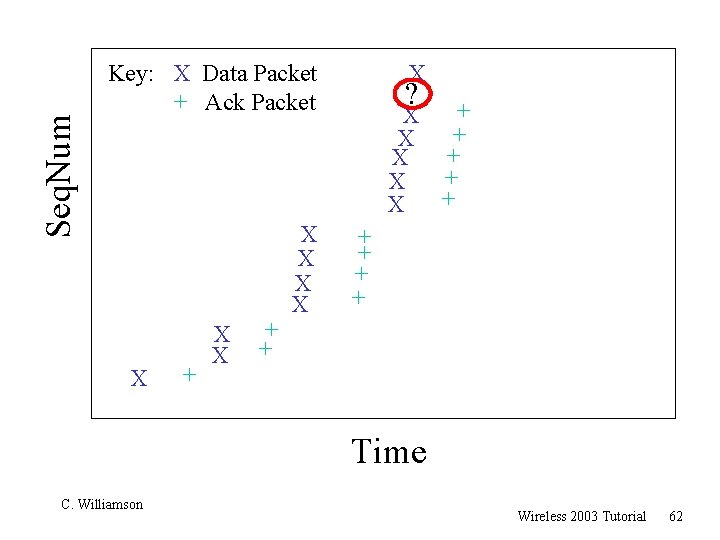
Seq. Num ? Key: X Data Packet + Ack Packet X + X X + X + X + X + + Time C. Williamson Wireless 2003 Tutorial 59

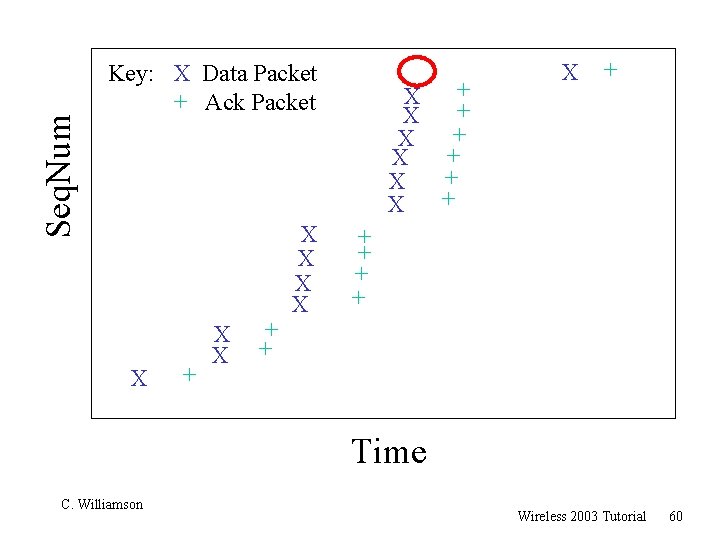
Seq. Num Key: X Data Packet + Ack Packet X + X X + X + X + X X + + + Time C. Williamson Wireless 2003 Tutorial 60

Seq. Num + X + X Key: X Data Packet + Ack Packet X + X X + + Time C. Williamson Wireless 2003 Tutorial 61

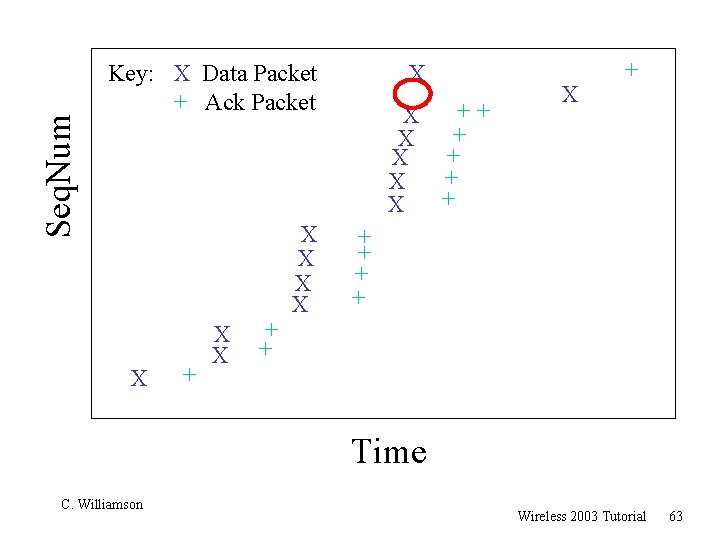
Seq. Num Key: X Data Packet + Ack Packet X + X X + + X X X ? + X + X + X + + Time C. Williamson Wireless 2003 Tutorial 62

Seq. Num Key: X Data Packet + Ack Packet X + X X + + X X X ++ X + X + X X + + + Time C. Williamson Wireless 2003 Tutorial 63

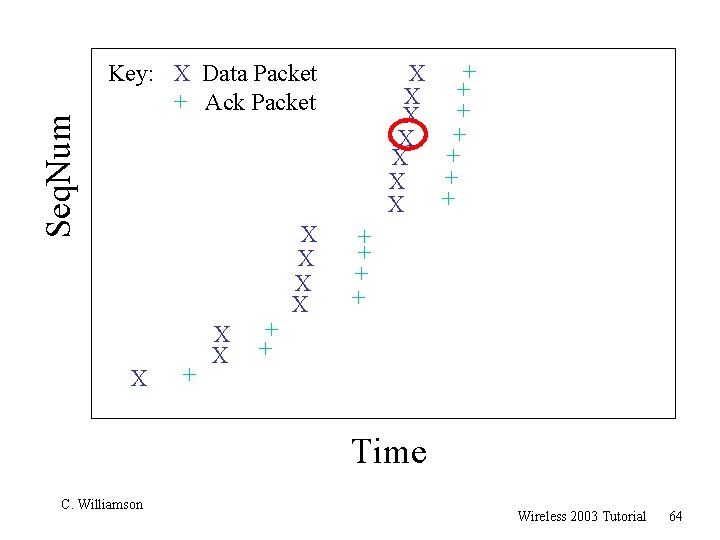
Seq. Num + X + X Key: X Data Packet + Ack Packet X + X X + + Time C. Williamson Wireless 2003 Tutorial 64

Seq. Num Key: X Data Packet + Ack Packet X X X ? X X + + X X + + + + Time C. Williamson Wireless 2003 Tutorial 65

Seq. Num Key: X Data Packet + Ack Packet X X X X + + X X + X +++ + + + Time C. Williamson Wireless 2003 Tutorial 66

Seq. Num + X + X Key: X Data Packet + Ack Packet X + X X + + Time C. Williamson Wireless 2003 Tutorial 67

Seq. Num Key: X Data Packet + Ack Packet ? X + Time C. Williamson Wireless 2003 Tutorial 68

Seq. Num Key: X Data Packet + Ack Packet X X X + X + ++ X X + + + X Time C. Williamson Wireless 2003 Tutorial 69

TCP 201 (Cont’d) r Main observation: m “Not all packet losses are created equal” r Losses early in the transfer have a huge adverse impact on the transfer latency r Losses near the end of the transfer always cost at least a retransmit timeout r Losses in the middle may or may not hurt, depending on congestion window size at the time of the loss C. Williamson Wireless 2003 Tutorial 70

Congratulations! r You are now a TCP expert! C. Williamson Wireless 2003 Tutorial 71

5. HTTP: Hyper. Text Transfer Protocol C. Williamson Wireless 2003 Tutorial 72

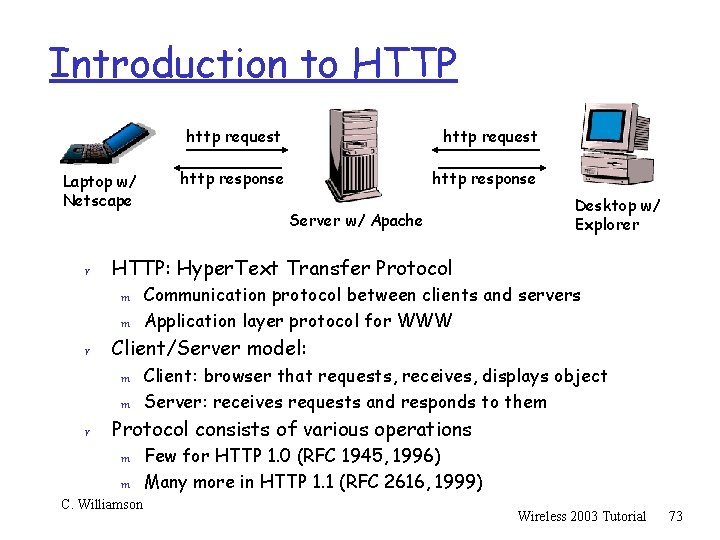
Introduction to HTTP Laptop w/ Netscape r m http response Server w/ Apache Desktop w/ Explorer Communication protocol between clients and servers Application layer protocol for WWW Client/Server model: m m r http request HTTP: Hyper. Text Transfer Protocol m r http request Client: browser that requests, receives, displays object Server: receives requests and responds to them Protocol consists of various operations m m C. Williamson Few for HTTP 1. 0 (RFC 1945, 1996) Many more in HTTP 1. 1 (RFC 2616, 1999) Wireless 2003 Tutorial 73

Request Generation r User clicks on something r Uniform Resource Locator (URL): m m http: //www. cnn. com http: //www. cpsc. ucalgary. ca https: //www. paymybills. com ftp: //ftp. kernel. org r Different URL schemes map to different services r Hostname is converted from a name to a 32 -bit IP address (DNS lookup, if needed) r Connection is established to server (TCP) C. Williamson Wireless 2003 Tutorial 74

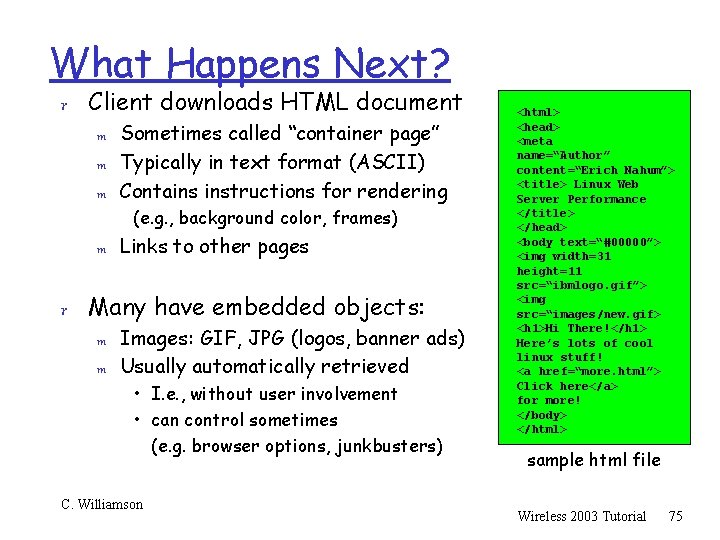
What Happens Next? r Client downloads HTML document m Sometimes called “container page” m Typically in text format (ASCII) m Contains instructions for rendering (e. g. , background color, frames) m Links to other pages r Many have embedded objects: m Images: GIF, JPG (logos, banner ads) m Usually automatically retrieved • I. e. , without user involvement • can control sometimes (e. g. browser options, junkbusters) C. Williamson <html> <head> <meta name=“Author” content=“Erich Nahum”> <title> Linux Web Server Performance </title> </head> <body text=“#00000”> <img width=31 height=11 src=“ibmlogo. gif”> <img src=“images/new. gif> <h 1>Hi There!</h 1> Here’s lots of cool linux stuff! <a href=“more. html”> Click here</a> for more! </body> </html> sample html file Wireless 2003 Tutorial 75

Web Server Role r Respond to client requests, typically a browser m Can be a proxy, which aggregates client requests (e. g. , AOL) m Could be search engine spider or robot (e. g. , Keynote) r May have work to do on client’s behalf: m Is the client’s cached copy still good? m Is client authorized to get this document? r Hundreds or thousands of simultaneous clients r Hard to predict how many will show up on some day (e. g. , “flash crowds”, diurnal cycle, global presence) r Many requests are in progress concurrently C. Williamson Wireless 2003 Tutorial 76

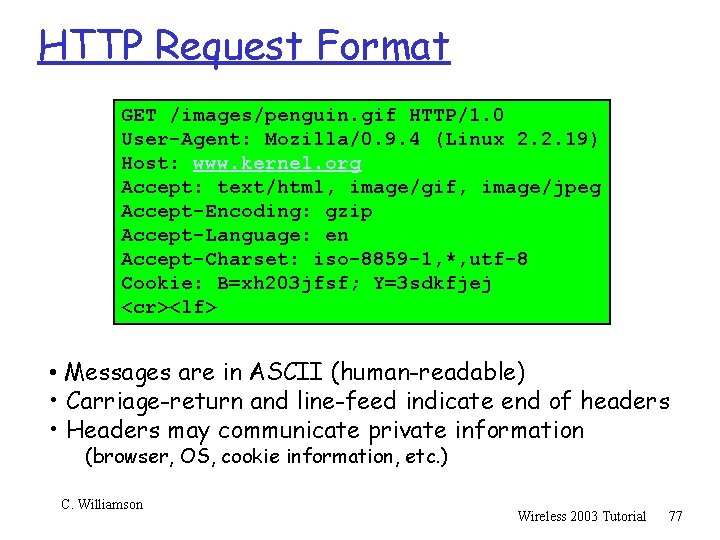
HTTP Request Format GET /images/penguin. gif HTTP/1. 0 User-Agent: Mozilla/0. 9. 4 (Linux 2. 2. 19) Host: www. kernel. org Accept: text/html, image/gif, image/jpeg Accept-Encoding: gzip Accept-Language: en Accept-Charset: iso-8859 -1, *, utf-8 Cookie: B=xh 203 jfsf; Y=3 sdkfjej <cr><lf> • Messages are in ASCII (human-readable) • Carriage-return and line-feed indicate end of headers • Headers may communicate private information (browser, OS, cookie information, etc. ) C. Williamson Wireless 2003 Tutorial 77

Request Types Called Methods: r GET: retrieve a file (95% of requests) r HEAD: just get meta-data (e. g. , mod time) r POST: submitting a form to a server r PUT: store enclosed document as URI r DELETE: removed named resource r LINK/UNLINK: in 1. 0, gone in 1. 1 r TRACE: http “echo” for debugging (added in 1. 1) r CONNECT: used by proxies for tunneling (1. 1) r OPTIONS: request for server/proxy options (1. 1) C. Williamson Wireless 2003 Tutorial 78

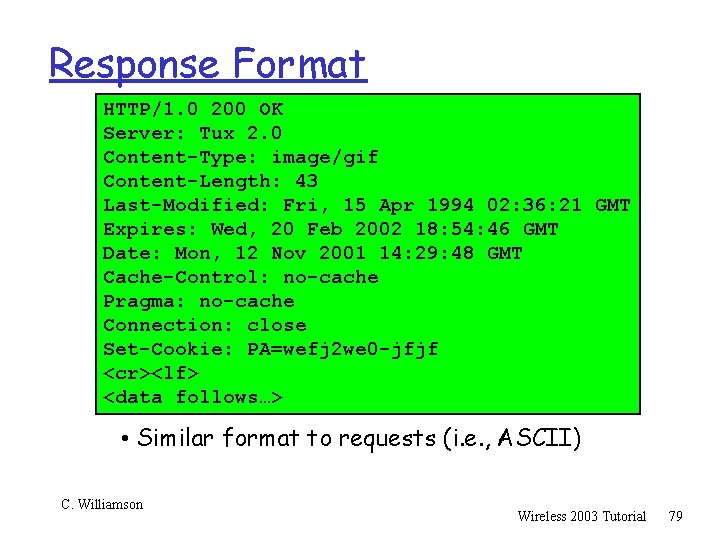
Response Format HTTP/1. 0 200 OK Server: Tux 2. 0 Content-Type: image/gif Content-Length: 43 Last-Modified: Fri, 15 Apr 1994 02: 36: 21 GMT Expires: Wed, 20 Feb 2002 18: 54: 46 GMT Date: Mon, 12 Nov 2001 14: 29: 48 GMT Cache-Control: no-cache Pragma: no-cache Connection: close Set-Cookie: PA=wefj 2 we 0 -jfjf <cr><lf> <data follows…> • Similar format to requests (i. e. , ASCII) C. Williamson Wireless 2003 Tutorial 79

Response Types r 1 XX: Informational (def’d in 1. 0, used in 1. 1) 100 Continue, 101 Switching Protocols r 2 XX: Success 200 OK, 206 Partial Content r 3 XX: Redirection 301 Moved Permanently, 304 Not Modified r 4 XX: Client error 400 Bad Request, 403 Forbidden, 404 Not Found r 5 XX: Server error 500 Internal Server Error, 503 Service Unavailable, 505 HTTP Version Not Supported C. Williamson Wireless 2003 Tutorial 80

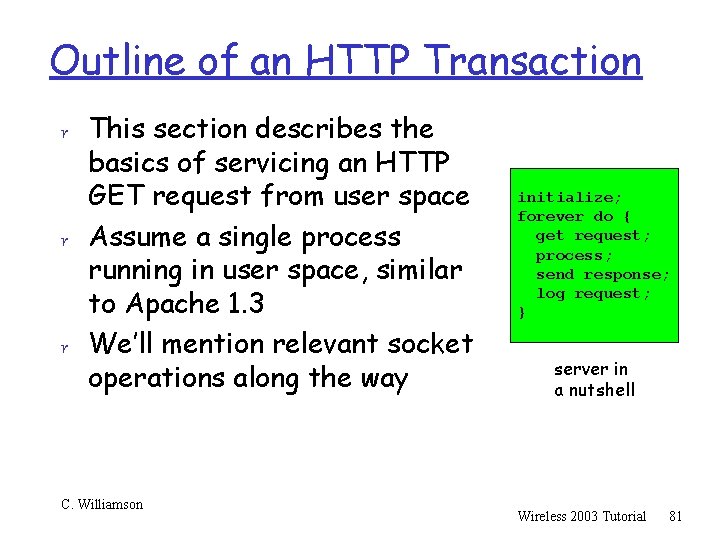
Outline of an HTTP Transaction r This section describes the basics of servicing an HTTP GET request from user space r Assume a single process running in user space, similar to Apache 1. 3 r We’ll mention relevant socket operations along the way C. Williamson initialize; forever do { get request; process; send response; log request; } server in a nutshell Wireless 2003 Tutorial 81

Readying a Server s = socket(); bind(s, 80); listen(s); while (1) { newconn = r r r /* allocate listen socket */ /* bind to TCP port 80 */ /* indicate willingness to accept */ accept(s); /* accept new connection */b First thing a server does is notify the OS it is interested in WWW server requests; these are typically on TCP port 80. Other services use different ports (e. g. , SSL is on 443) Allocate a socket and bind()'s it to the address (port 80) Server calls listen() on the socket to indicate willingness to receive requests Calls accept() to wait for a request to come in (and blocks) When the accept() returns, we have a new socket which represents a new connection to a client C. Williamson Wireless 2003 Tutorial 82

Processing a Request remote. IP = getsockname(newconn); remote. Host = gethostbyname(remote. IP); gettimeofday(current. Time); read(newconn, req. Buffer, sizeof(req. Buffer)); req. Info = server. Parse(req. Buffer); r r r getsockname() called to get the remote host name m for logging purposes (optional, but done by most) m again for logging purposes m both for Date header and for logging m “GET /images/jul 4/flag. gif” gethostbyname() called to get name of other end gettimeofday() is called to get time of request read() is called on new socket to retrieve request is determined by parsing the data C. Williamson Wireless 2003 Tutorial 83

Processing a Request (cont) file. Name = parse. Out. File. Name(request. Buffer); file. Attr = stat(file. Name); server. Check. File. Stuff(file. Name, file. Attr); open(file. Name); r stat() called to test file path m m m r to see if file exists/is accessible may not be there, may only be available to certain people "/microsoft/top-secret/plans-for-world-domination. html" stat() also used for file meta-data m m e. g. , size of file, last modified time "Has file changed since last time I checked? “ r might have to stat() multiple files and directories r assuming all is OK, open() called to open the file C. Williamson Wireless 2003 Tutorial 84

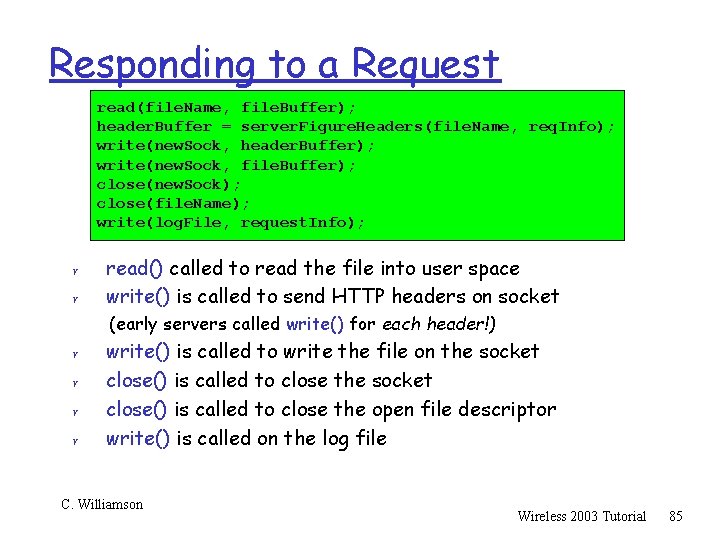
Responding to a Request read(file. Name, file. Buffer); header. Buffer = server. Figure. Headers(file. Name, req. Info); write(new. Sock, header. Buffer); write(new. Sock, file. Buffer); close(new. Sock); close(file. Name); write(log. File, request. Info); r r read() called to read the file into user space write() is called to send HTTP headers on socket (early servers called write() for each header!) r r write() is called to write the file on the socket close() is called to close the open file descriptor write() is called on the log file C. Williamson Wireless 2003 Tutorial 85

Network View: HTTP and TCP r TCP is a connection-oriented protocol SYN/ACK GET URL Web Client C. Williamson ACK YOUR DATA HERE FIN ACK Web Server FIN/ACK Wireless 2003 Tutorial 86

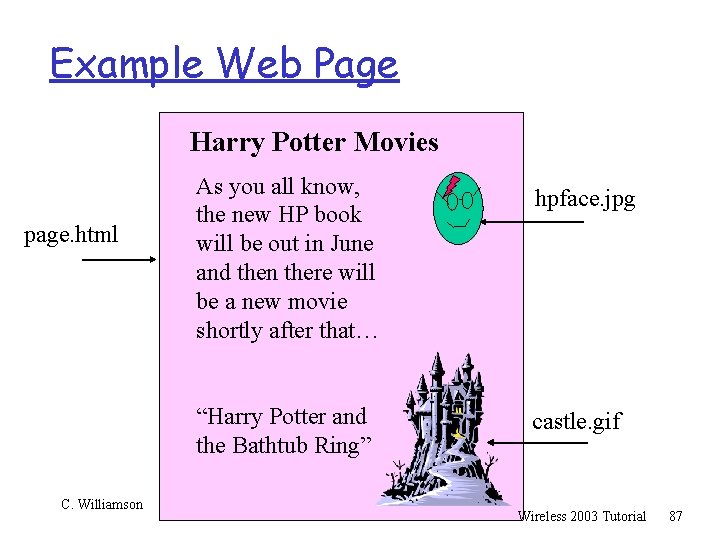
Example Web Page Harry Potter Movies page. html C. Williamson As you all know, the new HP book will be out in June and then there will be a new movie shortly after that… hpface. jpg “Harry Potter and the Bathtub Ring” castle. gif Wireless 2003 Tutorial 87

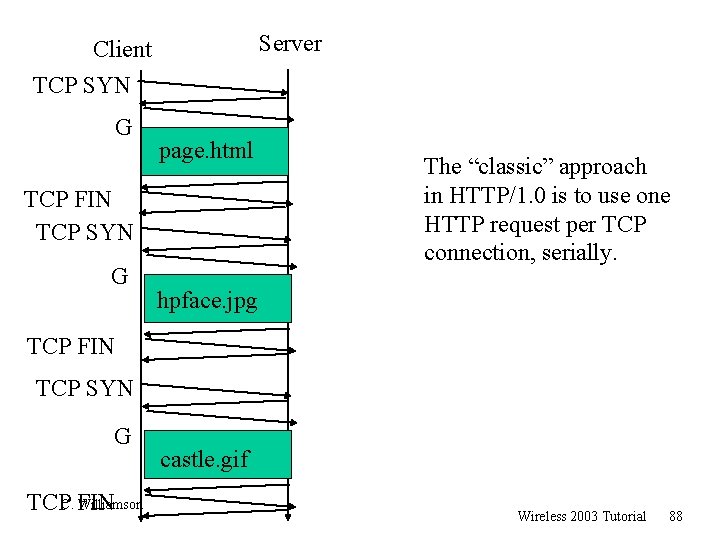
Server Client TCP SYN G page. html TCP FIN TCP SYN G The “classic” approach in HTTP/1. 0 is to use one HTTP request per TCP connection, serially. hpface. jpg TCP FIN TCP SYN G Williamson TCPC. FIN castle. gif Wireless 2003 Tutorial 88

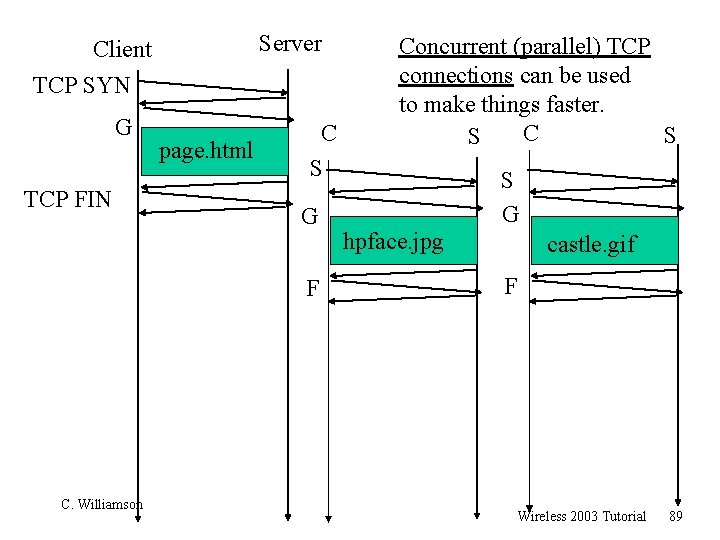
Server Client TCP SYN G TCP FIN page. html C S G F C. Williamson Concurrent (parallel) TCP connections can be used to make things faster. C S S S G hpface. jpg castle. gif F Wireless 2003 Tutorial 89

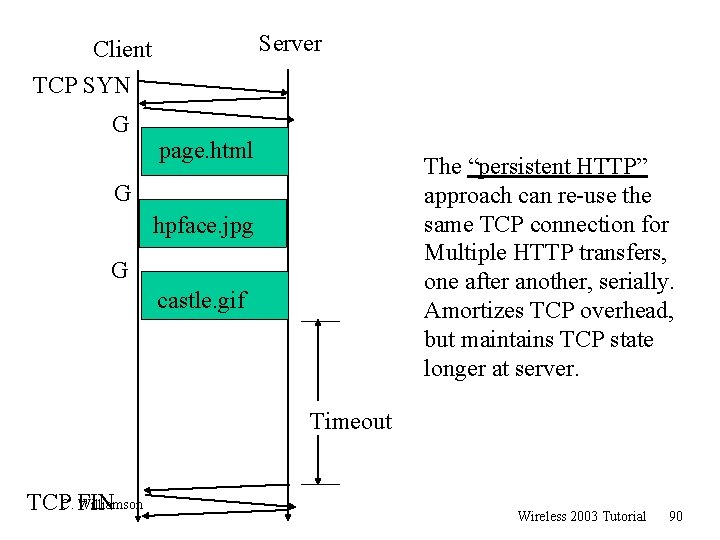
Server Client TCP SYN G page. html The “persistent HTTP” approach can re-use the same TCP connection for Multiple HTTP transfers, one after another, serially. Amortizes TCP overhead, but maintains TCP state longer at server. G hpface. jpg G castle. gif Timeout Williamson TCPC. FIN Wireless 2003 Tutorial 90

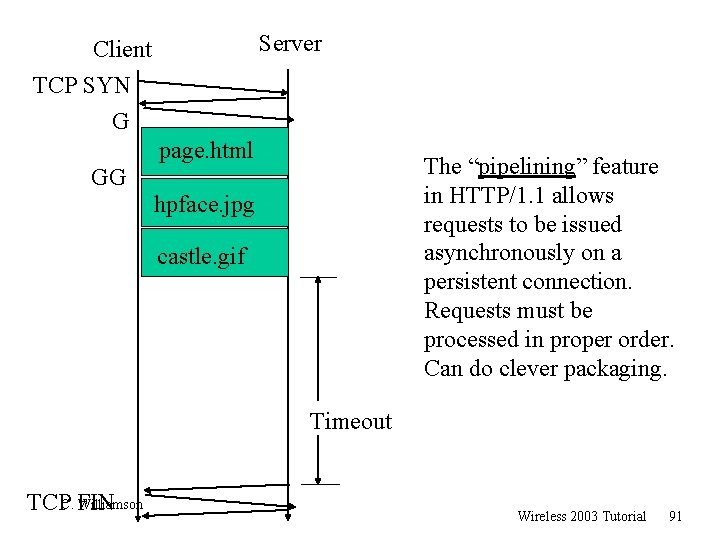
Server Client TCP SYN G page. html The “pipelining” feature in HTTP/1. 1 allows requests to be issued asynchronously on a persistent connection. Requests must be processed in proper order. Can do clever packaging. GG hpface. jpg castle. gif Timeout Williamson TCPC. FIN Wireless 2003 Tutorial 91

Summary of Web and HTTP r The major application on the Internet m Majority of traffic is HTTP (or HTTP-related) r Client/server model: m Clients make requests, servers respond to them m Done mostly in ASCII text (helps debugging!) r Various headers and commands m Too many to go into detail here m Many web books/tutorials exist (e. g. , Krishnamurthy & Rexford 2001) C. Williamson Wireless 2003 Tutorial 92

6. Wireless TCP: Performance Issues (Part 1) C. Williamson Wireless 2003 Tutorial 93

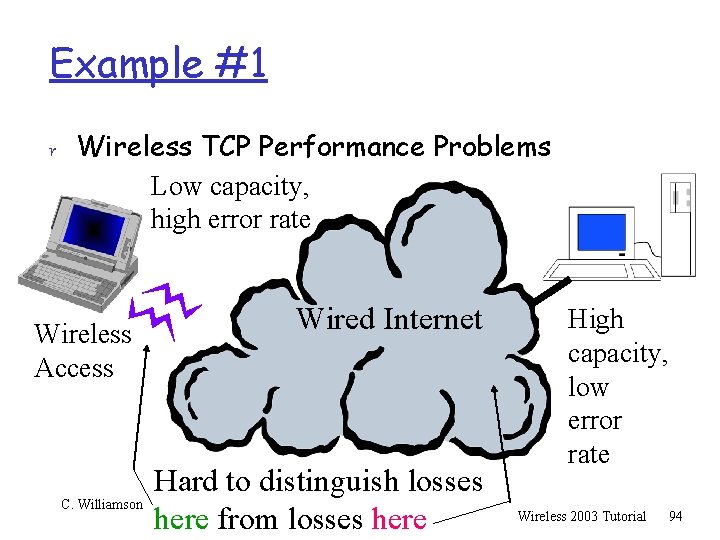
Example #1 r Wireless TCP Performance Problems Low capacity, high error rate Wireless Access C. Williamson Wired Internet Hard to distinguish losses here from losses here High capacity, low error rate Wireless 2003 Tutorial 94

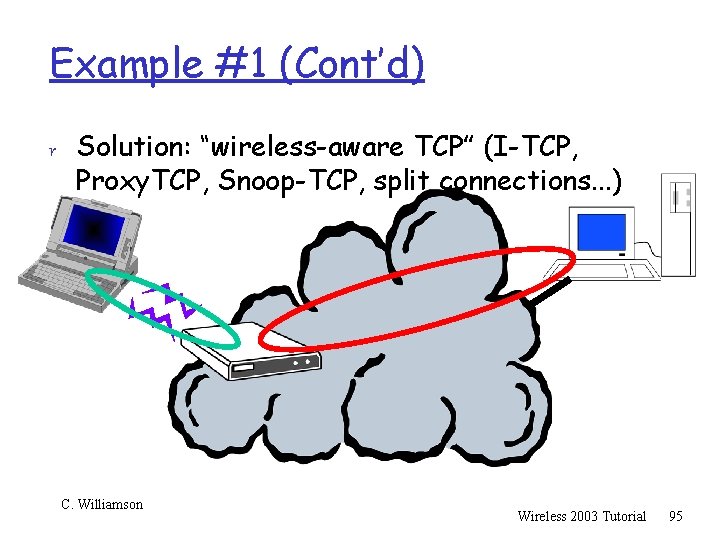
Example #1 (Cont’d) r Solution: “wireless-aware TCP” (I-TCP, Proxy. TCP, Snoop-TCP, split connections. . . ) C. Williamson Wireless 2003 Tutorial 95

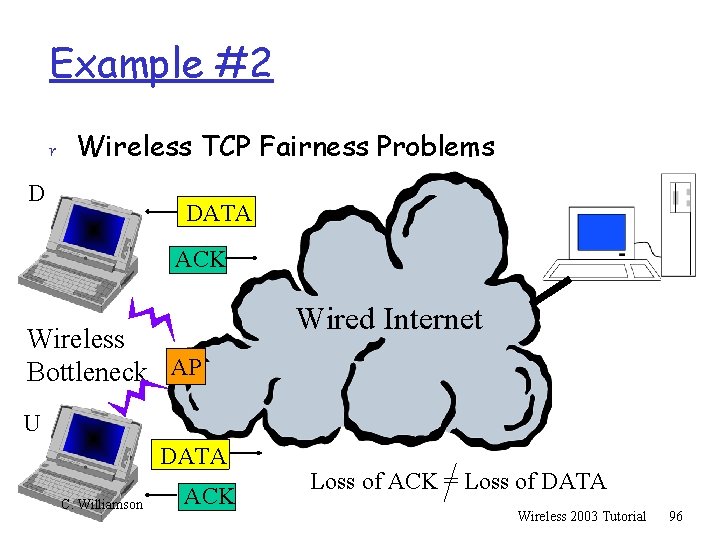
Example #2 r Wireless TCP Fairness Problems D DATA ACK Wireless Bottleneck AP Wired Internet U DATA C. Williamson ACK Loss of ACK = Loss of DATA Wireless 2003 Tutorial 96

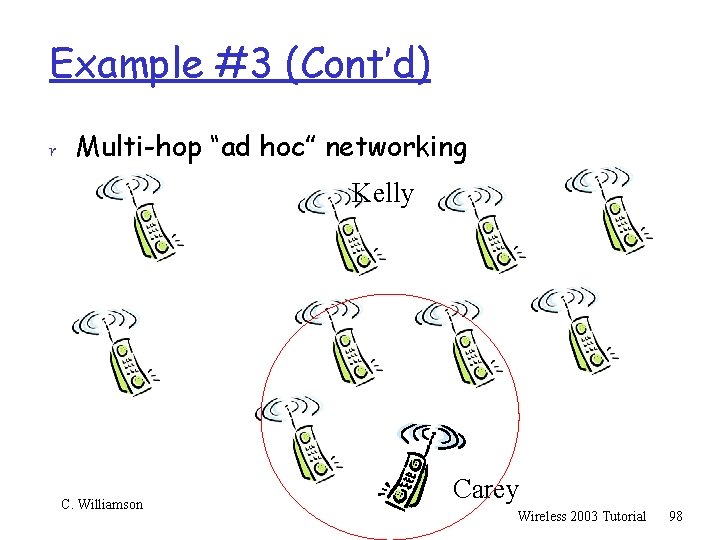
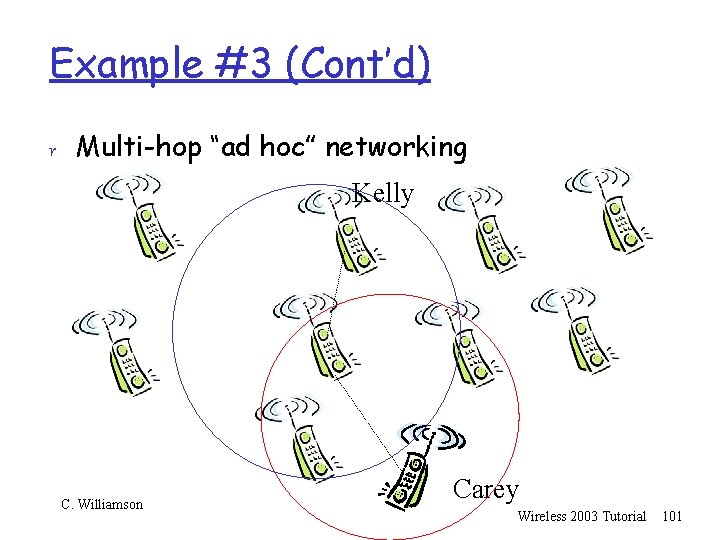
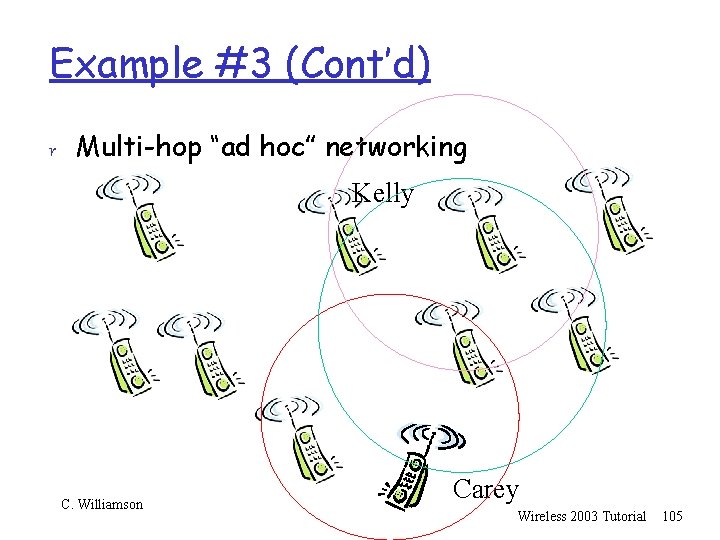
Example #3 r Multi-hop “ad hoc” networking Kelly C. Williamson Carey Wireless 2003 Tutorial 97

Example #3 (Cont’d) r Multi-hop “ad hoc” networking Kelly C. Williamson Carey Wireless 2003 Tutorial 98

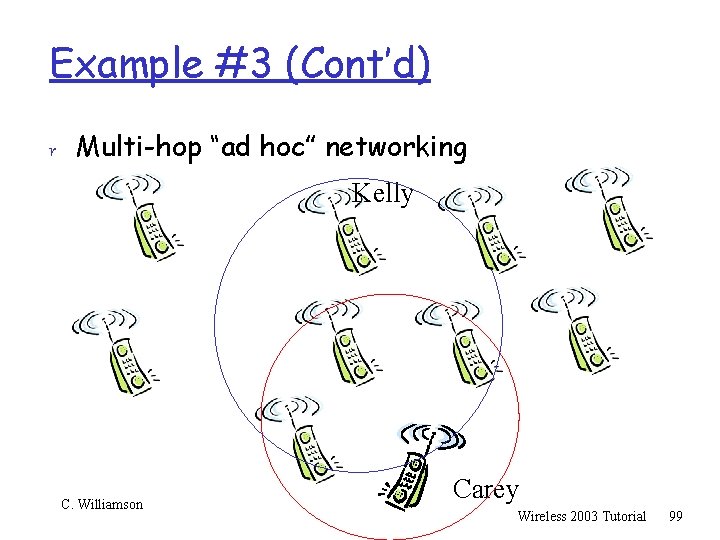
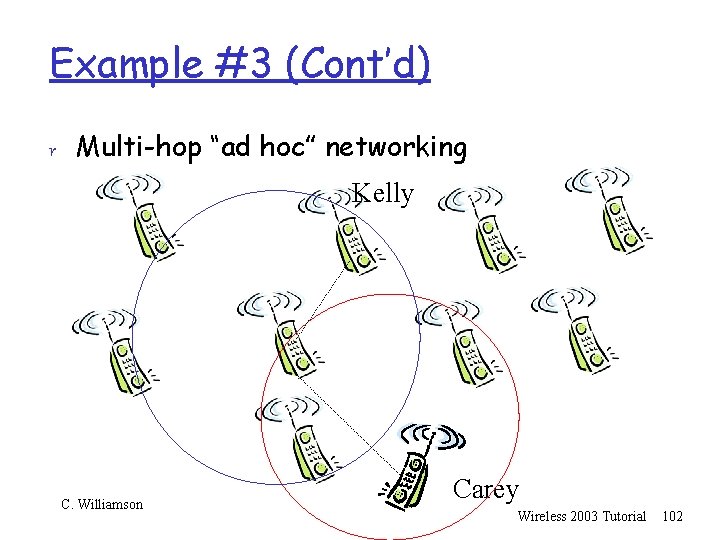
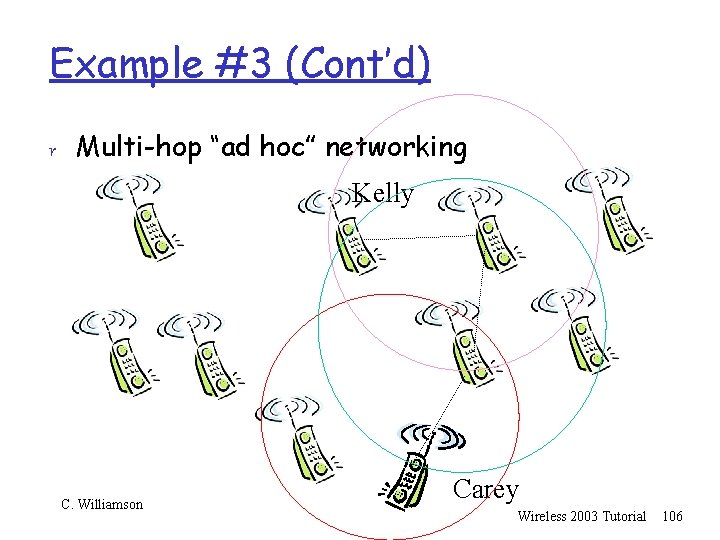
Example #3 (Cont’d) r Multi-hop “ad hoc” networking Kelly C. Williamson Carey Wireless 2003 Tutorial 99

Example #3 (Cont’d) r Multi-hop “ad hoc” networking Kelly C. Williamson Carey Wireless 2003 Tutorial 100

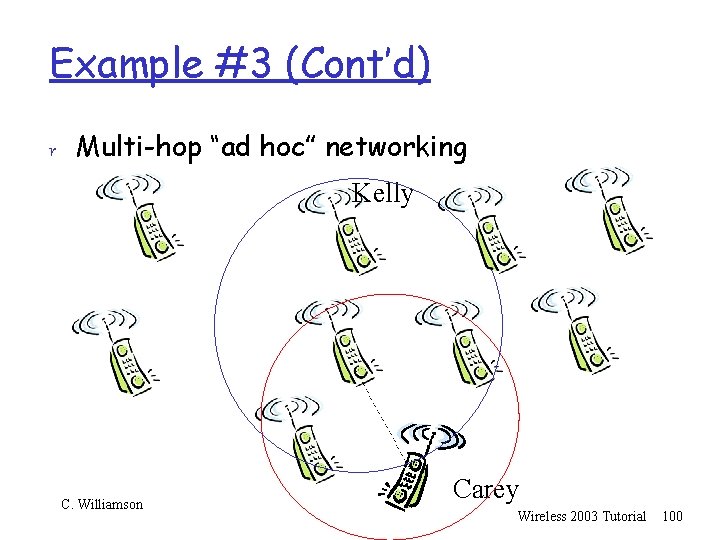
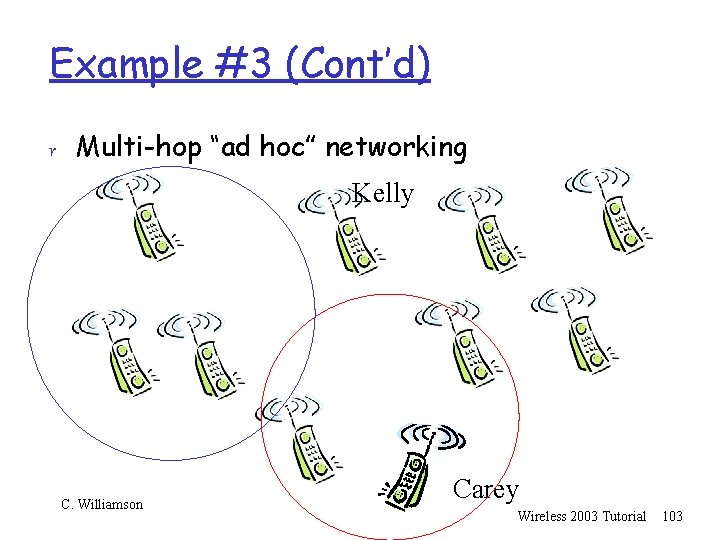
Example #3 (Cont’d) r Multi-hop “ad hoc” networking Kelly C. Williamson Carey Wireless 2003 Tutorial 101

Example #3 (Cont’d) r Multi-hop “ad hoc” networking Kelly C. Williamson Carey Wireless 2003 Tutorial 102

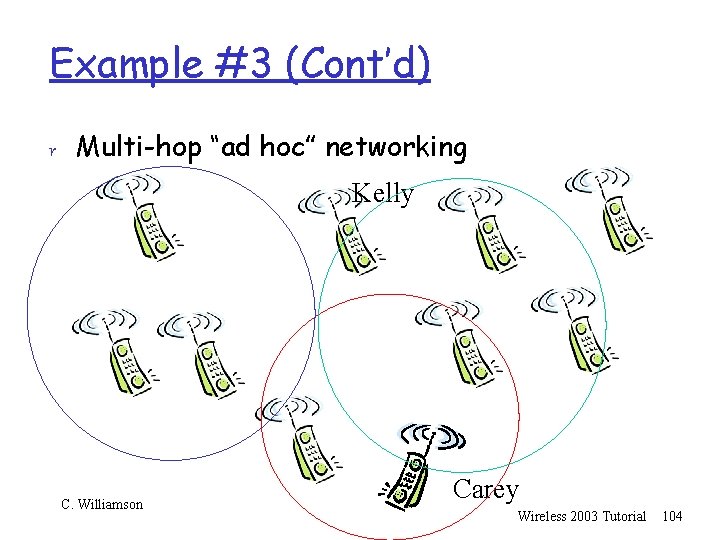
Example #3 (Cont’d) r Multi-hop “ad hoc” networking Kelly C. Williamson Carey Wireless 2003 Tutorial 103

Example #3 (Cont’d) r Multi-hop “ad hoc” networking Kelly C. Williamson Carey Wireless 2003 Tutorial 104

Example #3 (Cont’d) r Multi-hop “ad hoc” networking Kelly C. Williamson Carey Wireless 2003 Tutorial 105

Example #3 (Cont’d) r Multi-hop “ad hoc” networking Kelly C. Williamson Carey Wireless 2003 Tutorial 106

Example #3 (Cont’d) r Two interesting subproblems: m Dynamic ad hoc routing: node movement can disrupt the IP routing path at any time, disrupting TCP connection; yet another way to lose packets!!!; possible solution: Explicit Loss Notification (ELN)? Handoff? Route prediction? m TCP flow control: the bursty nature of TCP packet transmissions can create contention for the shared wireless channel among forwarding nodes; collisions between DATA and ACKs possible solution: rate-based flow control? Burst mode? Spatial reuse of channels? C. Williamson Wireless 2003 Tutorial 107

Summary of Wireless TCP r TCP is the “four wheel drive” of TP’s r Wireless is a newly emerging technology with rapidly growing deployment popularity r “TCP” and “Wireless” don’t fit together all that well r Making TCP smarter about wireless helps! C. Williamson Wireless 2003 Tutorial 108

7. Wireless TCP: Performance Issues (Part 2) C. Williamson Wireless 2003 Tutorial 109

Motivation r TCP performance often degrades over wireless networks; reasons “well-known” r Solutions to improve TCP performance over wireless links exist, but how well do they work in a real wireless LAN environment? r How do link-layer mechanisms interact with TCP and affect the overall performance? r Where is the bottleneck in the network protocol processing path, and why? C. Williamson Wireless 2003 Tutorial 110

Background - TCP r Widely used on the Internet (e. g. Web) r Connection-oriented, reliable byte stream r Window-based flow control r Slow start and congestion avoidance r Fast retransmission, fast recovery r Other extensions, including TCP SACK r Many different versions in use C. Williamson Wireless 2003 Tutorial 111

Background – IEEE 802. 11 b r An “Ethernet-like” LAN standard (11 Mbps) r Infrastructure mode and ad hoc mode r Carrier-sense multiple access with collision avoidance (CSMA/CA) to reduce collisions r MAC-layer: positive acknowledgment and retransmissions (to recover from channel errors) r Dynamic rate adaptation: can choose data transmission rate of 1, 2, 5. 5, or 11 Mbps C. Williamson Wireless 2003 Tutorial 112

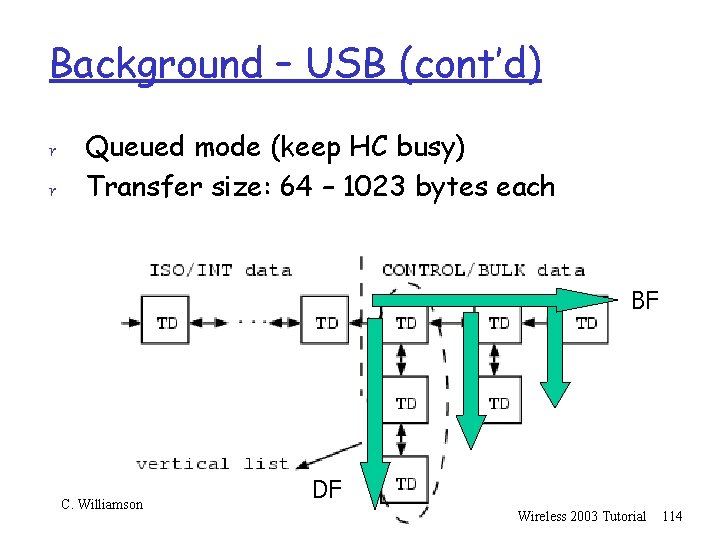
Background – USB r Widely used industry standard for connecting a r r r computer to its peripherals (bus topology) Lots of USB-based (wireless) network cards Data transfers managed by Host Controller (HC) Synchronous bus: 1 msec slots for transfers Transfer requests are handled using vertical and horizontal linked-list data structures Two processing modes for HC: m Breadth-First or Depth-First r High Speed Bandwidth Reclamation (HSBR) C. Williamson Wireless 2003 Tutorial 113

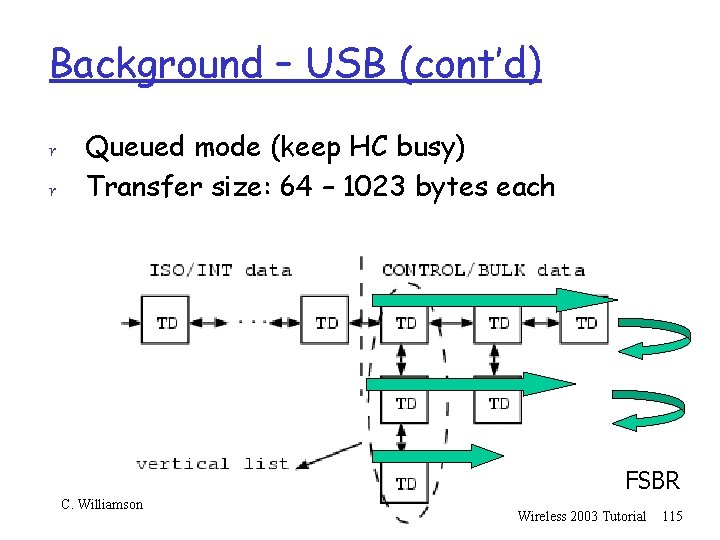
Background – USB (cont’d) r r Queued mode (keep HC busy) Transfer size: 64 – 1023 bytes each BF C. Williamson DF Wireless 2003 Tutorial 114

Background – USB (cont’d) r r Queued mode (keep HC busy) Transfer size: 64 – 1023 bytes each FSBR C. Williamson Wireless 2003 Tutorial 115

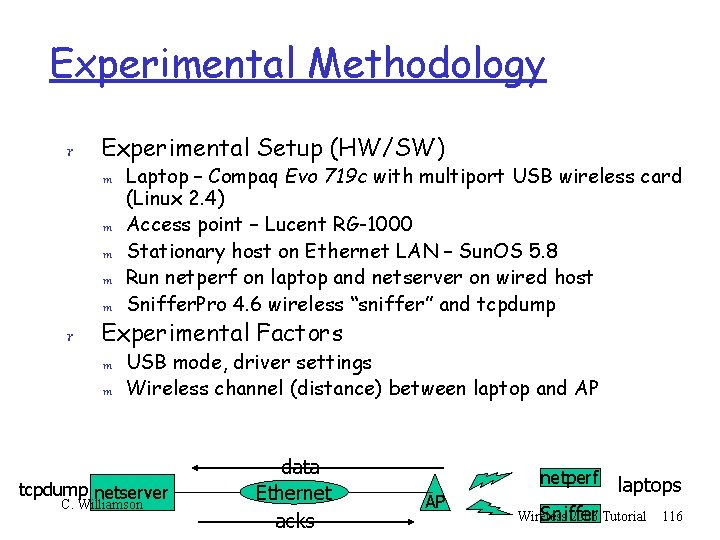
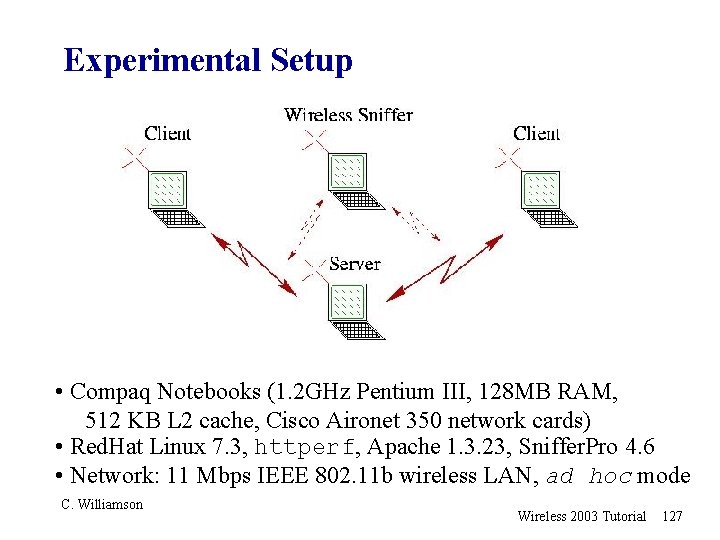
Experimental Methodology r Experimental Setup (HW/SW) m m m r Laptop – Compaq Evo 719 c with multiport USB wireless card (Linux 2. 4) Access point – Lucent RG-1000 Stationary host on Ethernet LAN – Sun. OS 5. 8 Run netperf on laptop and netserver on wired host Sniffer. Pro 4. 6 wireless “sniffer” and tcpdump Experimental Factors m m USB mode, driver settings Wireless channel (distance) between laptop and AP tcpdump netserver C. Williamson data Ethernet acks netperf AP laptops Sniffer Wireless 2003 Tutorial 116

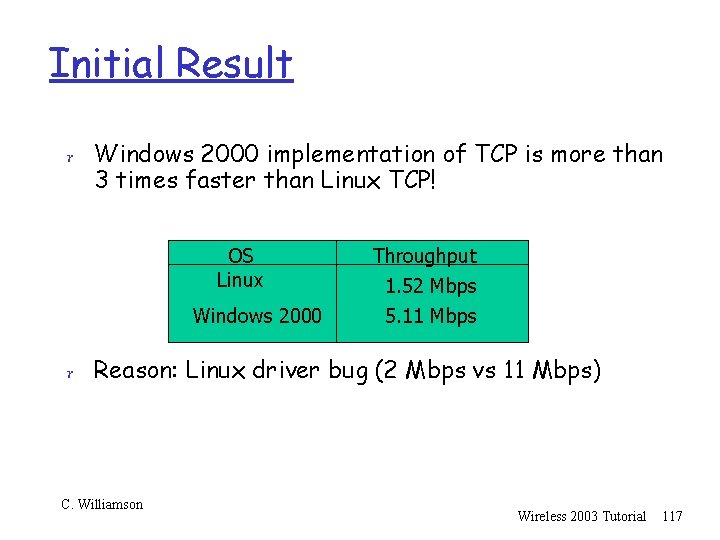
Initial Result r Windows 2000 implementation of TCP is more than 3 times faster than Linux TCP! OS Linux Windows 2000 Throughput 1. 52 Mbps 5. 11 Mbps r Reason: Linux driver bug (2 Mbps vs 11 Mbps) C. Williamson Wireless 2003 Tutorial 117

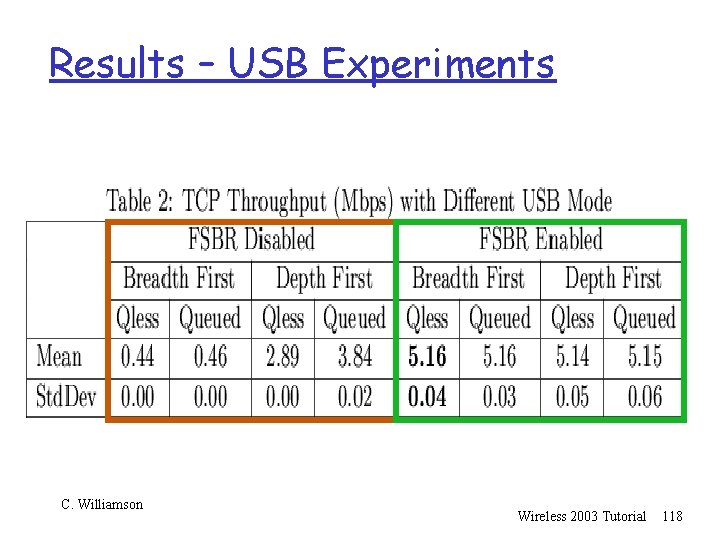
Results – USB Experiments C. Williamson Wireless 2003 Tutorial 118

Results – USB Experiments r With FSBR disabled, USB is the bottleneck r With FSBR enabled (the default in Linux), the wireless network is the bottleneck r Queued mode makes no difference with FSBR on, but helps when FSBR is turned off r Queued mode (even with FSBR turned on) may be very important when higher speed wireless link is used (e. g. IEEE 802. 11 a) C. Williamson Wireless 2003 Tutorial 119

Results – Wireless Problems r We observed unusually high collision rates on the wireless channel for TCP transfers, which we call the TCP data/ACK collision problem m m Scenario: laptop and AP are 1 m apart For TCP, MAC-layer retransmit rate: 4. 58 -4. 73% For UDP, MAC-layer retransmit rate: 0. 47 -0. 98% In general, a retransmission rate of 1. 75%-7. 2% has been seen for other vendor HW/SW (N = 1) For TCP, disabling MAC-layer retransmission degrades throughput by 23% C. Williamson Wireless 2003 Tutorial 120

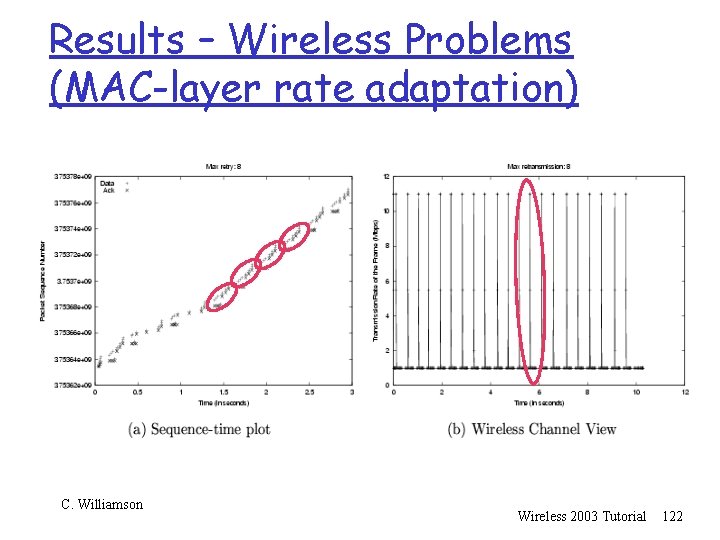
Results – Wireless Problems r The MAC-layer rate adaptation problem m Scenario: laptop and AP are 100 m apart m Lousy TCP throughput, lots of retransmits m Reason: the multiplicative increase and multiplicative decrease (MIMD) bandwidth probing mechanism causes network thrashing and wastes battery power m The small congestion window causes temporary deadlock if the TCP receiver uses delayed Ack C. Williamson Wireless 2003 Tutorial 121

Results – Wireless Problems (MAC-layer rate adaptation) C. Williamson Wireless 2003 Tutorial 122

Summary of Observations TCP performance on WLAN can be wacky! (at least for Compaq Multiport 802. 11 b USB wireless card under Linux 2. 4) r Several factors can affect overall performance r m m Poorly configured USB bus could be the bottleneck Linux TCP implementation bug makes TCP unable to recognize the first spurious timeout Poor MAC-layer rate adaptation algorithm can cause a “network thrashing” problem TCP’s data/ACK structure may induce excessive collisions at the MAC layer on wireless LANs C. Williamson Wireless 2003 Tutorial 123

7. Wireless Web: Performance Issues C. Williamson Wireless 2003 Tutorial 124

Introduction and Motivation § Observation: the same wireless technology that allows a Web client to be mobile also allows Web servers to be mobile § Idea: portable, short-lived, ad hoc networks § Possible applications: o classroom area networks, seminars o press conferences, media events o sporting events, gaming, exhibitions o conferences and trade shows o disaster recovery sites, field work, etc. C. Williamson Wireless 2003 Tutorial 125

Objectives § to assess feasibility of portable networks § to benchmark the performance capabilities and limitations of an Apache Web server in a wireless ad hoc network § to identify the performance bottlenecks § to understand impacts of different factors o number of clients o Web object size o persistent connections o transmit power (energy consumption) o wireless channel conditions C. Williamson Wireless 2003 Tutorial 126

Experimental Setup • Compaq Notebooks (1. 2 GHz Pentium III, 128 MB RAM, 512 KB L 2 cache, Cisco Aironet 350 network cards) • Red. Hat Linux 7. 3, httperf, Apache 1. 3. 23, Sniffer. Pro 4. 6 • Network: 11 Mbps IEEE 802. 11 b wireless LAN, ad hoc mode C. Williamson Wireless 2003 Tutorial 127

Experimental Setup (Cont’d) • IEEE 802. 11 b: a standard for wireless LANs Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA), up to 11 Mbps data rate at physical layer • ad hoc mode frames are addressed directly from sender to receiver • httperf Web benchmarking software tool developed at HP Labs • Web server: Apache (version 1. 3. 23) Process-based, flexible, powerful, HTTP/1. 1 -compliant • Sniffer. Pro 4. 6 real-time capture, recording all wireless channel activity, enabling protocol analysis at MAC, IP, TCP and HTTP layers C. Williamson Wireless 2003 Tutorial 128

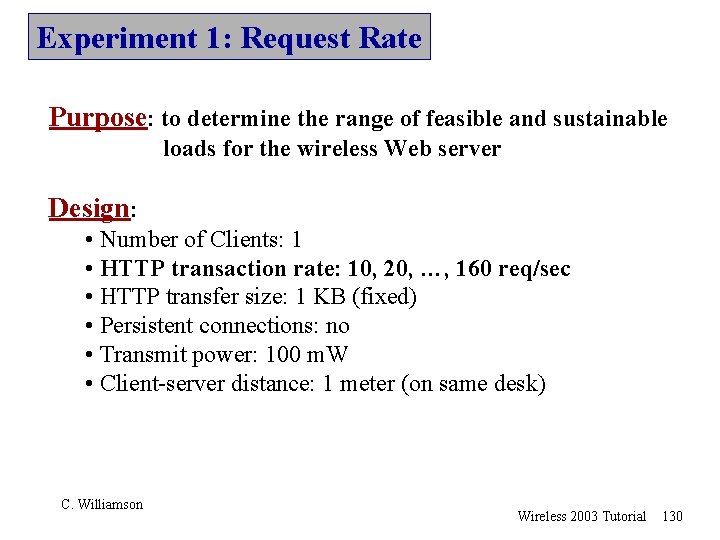
Experimental Design • Impacts of different factors on wireless Web server performance (one-factor-at-a-time) Experimental Factors and Levels Factor Number of Clients HTTP Transaction Rate (per-client) Levels 1, 2, 4 10, 20, 30, …, 160 HTTP Transfer Size (KB) Persistent Connections HTTP Requests per Connection Transmit Power (m. W) 1, 2, 4, 8, …, 100 no, yes 1, 5, 10, 15, …, 60 1, 5, 20, 30, 50, 100 Client-Server Distance (m) 1, 100 • Performance metrics – HTTP transaction rate, throughput, response time, error rate at Application Layer, – TCP connection duration at Network Layer – Transmit queue behaviour at Link Layer, 129

Experiment 1: Request Rate Purpose: to determine the range of feasible and sustainable loads for the wireless Web server Design: • Number of Clients: 1 • HTTP transaction rate: 10, 20, …, 160 req/sec • HTTP transfer size: 1 KB (fixed) • Persistent connections: no • Transmit power: 100 m. W • Client-server distance: 1 meter (on same desk) C. Williamson Wireless 2003 Tutorial 130

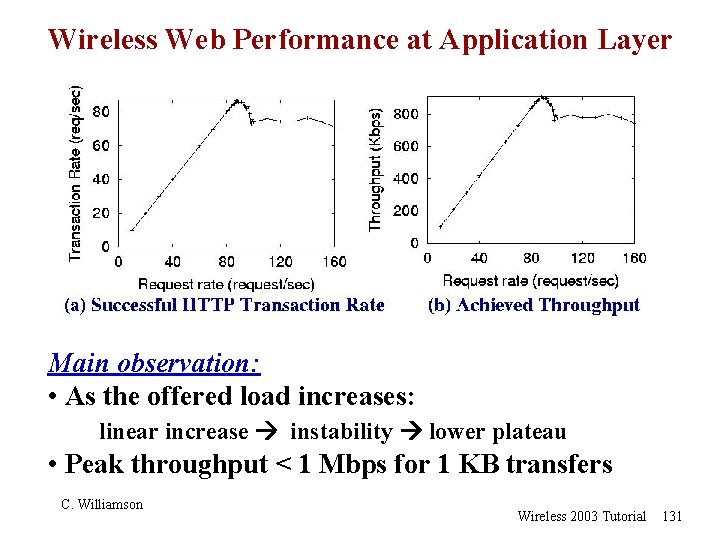
Wireless Web Performance at Application Layer Main observation: • As the offered load increases: linear increase instability lower plateau • Peak throughput < 1 Mbps for 1 KB transfers C. Williamson Wireless 2003 Tutorial 131

Experiment 2: Transfer Size Purpose: to study impact of HTTP response size Design: • Number of Clients: 1 • HTTP transaction rate: 10 req/sec (fixed) • HTTP transfer size (KB): 1, 2, 4, 8, … • Persistent connections: no • Transmit power: 100 m. W • Client-server distance: 1 meter (on same desk) C. Williamson Wireless 2003 Tutorial 132

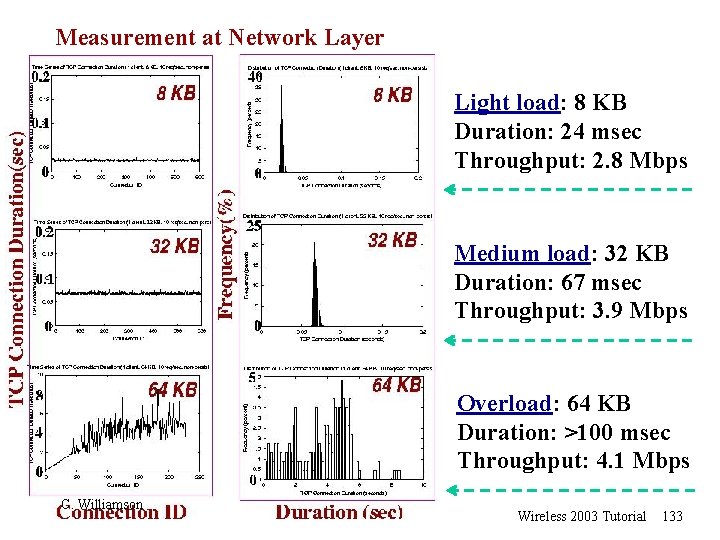
Measurement at Network Layer Light load: 8 KB Duration: 24 msec Throughput: 2. 8 Mbps Medium load: 32 KB Duration: 67 msec Throughput: 3. 9 Mbps Overload: 64 KB Duration: >100 msec Throughput: 4. 1 Mbps C. Williamson Wireless 2003 Tutorial 133

Experiment 3: Persistent Connections: • Multiple HTTP transactions can be sent on the same TCP connection. • amortize overhead of TCP connection processing • reduce memory consumption for TCP state Purpose of this experiment: to study impact of persistent connection on wireless Web performance Design: • Number of Clients: 1 and 2 • HTTP transaction rate: 10 req/sec (fixed) • HTTP transfer size: 1 KB (fixed) • Persistent connections: yes • Transmit power: 100 m. W • Client-server distance: 1 meter (on same desk) C. Williamson Wireless 2003 Tutorial 134

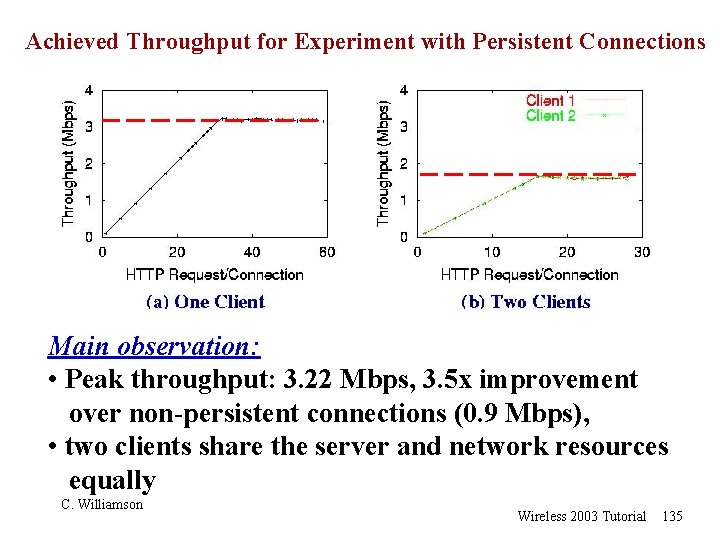
Achieved Throughput for Experiment with Persistent Connections Main observation: • Peak throughput: 3. 22 Mbps, 3. 5 x improvement over non-persistent connections (0. 9 Mbps), • two clients share the server and network resources equally C. Williamson Wireless 2003 Tutorial 135

Summary and Conclusions v What we did: wireless Web server, portable nw • Application-layer measurements (httperf) • Network-layer measurements (Wireless Sniffer) v Our results show: • Server capability: 100 conn/sec for non-persistent HTTP with throughputs up to 4 Mbps (adequate? ) • Bottleneck: at wireless network interface • Some “network thrashing” for large HTTP transfers when the network utilization is high (aborts, resets) • Effect of wireless channel on performance at TCP and HTTP-level (MAC-layer retransmits) • Power consumption issue for mobile client and server C. Williamson Wireless 2003 Tutorial 136

8. Summary, Questions, and Discussion C. Williamson Wireless 2003 Tutorial 137

Credits r Thanks to the following people for the use of their slides and/or knowledge: m m m David Schwab, U of Saskatchewan Erich Nahum, IBM Sniffer Technologies Network Associates IEEE Guangwei Bai and Tianbo Kuang, U of C C. Williamson Wireless 2003 Tutorial 138