Chapter 14 Unicast Routing Protocols RIP OSPF and





- Slides: 66

Chapter 14 Unicast Routing Protocols: RIP, OSPF, and BGP Objectives Upon completion you will be able to: • Distinguish between intradomain and interdomain routing • Understand distance vector routing and RIP • Understand link state routing and OSPF • Understand path vector routing and BGP TCP/IP Protocol Suite 1

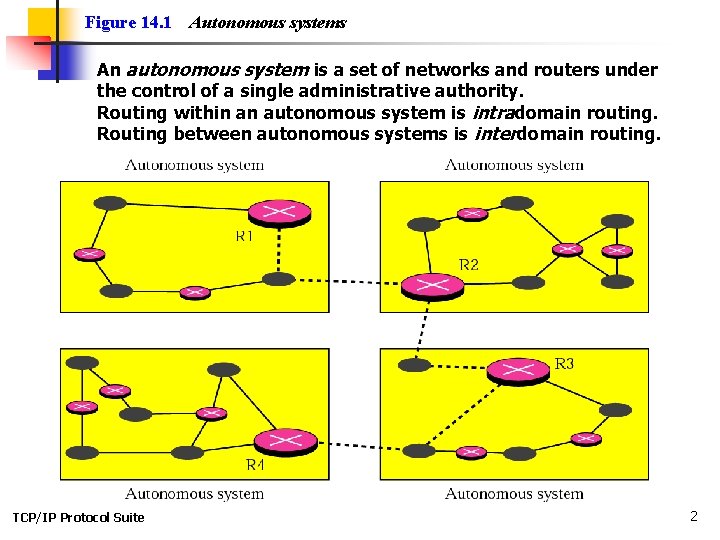
Figure 14. 1 Autonomous systems An autonomous system is a set of networks and routers under the control of a single administrative authority. Routing within an autonomous system is intradomain routing. Routing between autonomous systems is interdomain routing. TCP/IP Protocol Suite 2

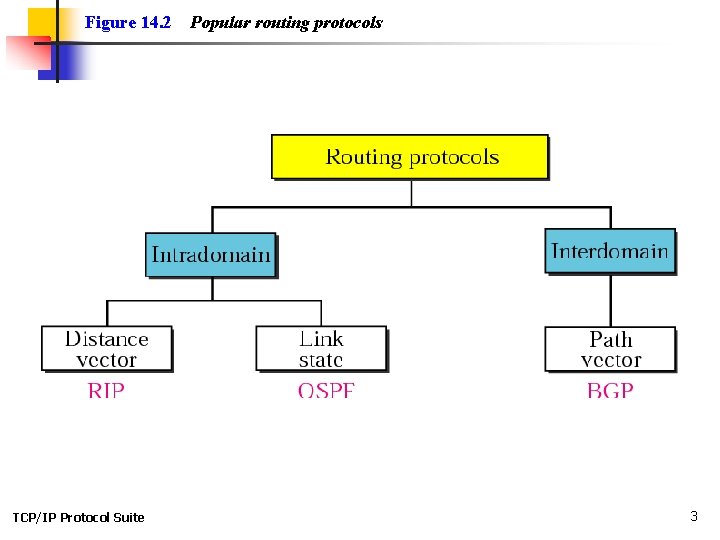
Figure 14. 2 TCP/IP Protocol Suite Popular routing protocols 3

14. 2 DISTANCE VECTOR ROUTING In distance vector routing, the least cost route between any two nodes is the route with minimum distance. In this protocol each node maintains a vector (table) of minimum distances to every node The topics discussed in this section include: Initialization Sharing Updating When to Share Two-Node Loop Instability Three-Node Instability TCP/IP Protocol Suite 4

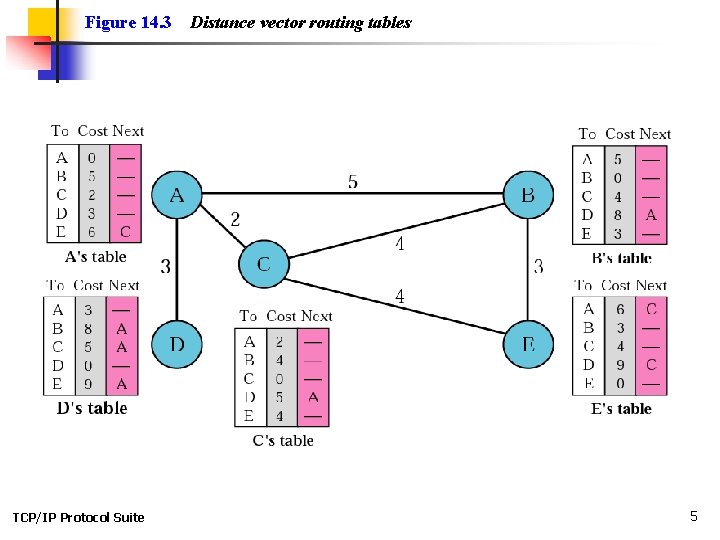
Figure 14. 3 TCP/IP Protocol Suite Distance vector routing tables 5

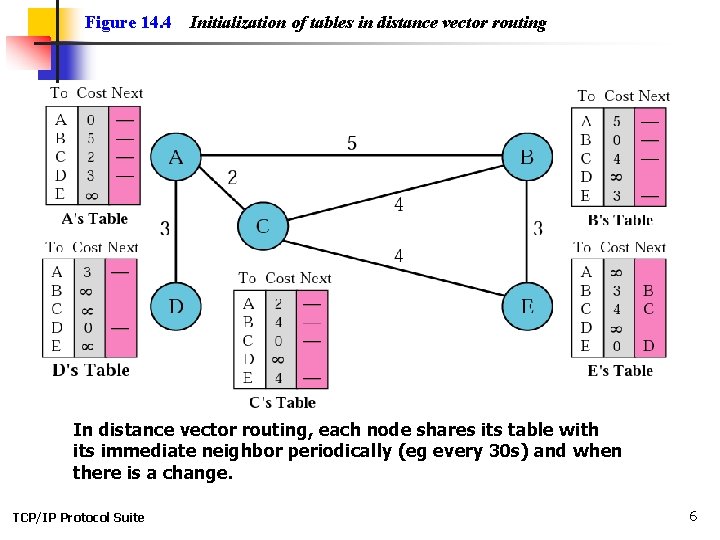
Figure 14. 4 Initialization of tables in distance vector routing In distance vector routing, each node shares its table with its immediate neighbor periodically (eg every 30 s) and when there is a change. TCP/IP Protocol Suite 6

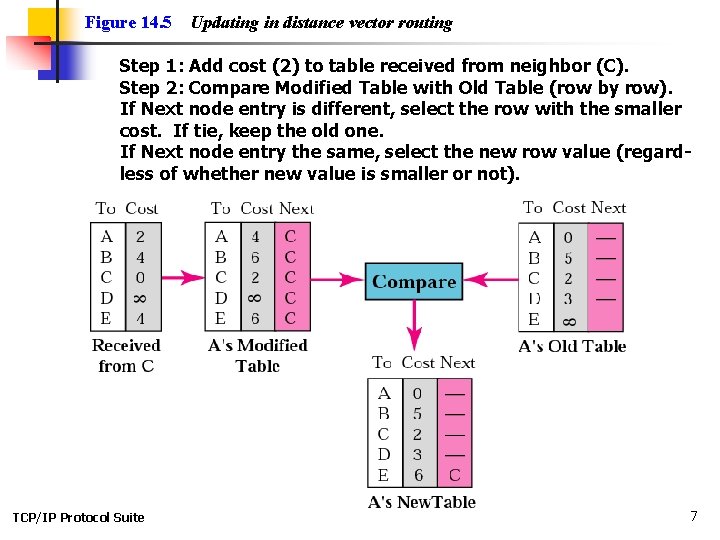
Figure 14. 5 Updating in distance vector routing Step 1: Add cost (2) to table received from neighbor (C). Step 2: Compare Modified Table with Old Table (row by row). If Next node entry is different, select the row with the smaller cost. If tie, keep the old one. If Next node entry the same, select the new row value (regardless of whether new value is smaller or not). TCP/IP Protocol Suite 7

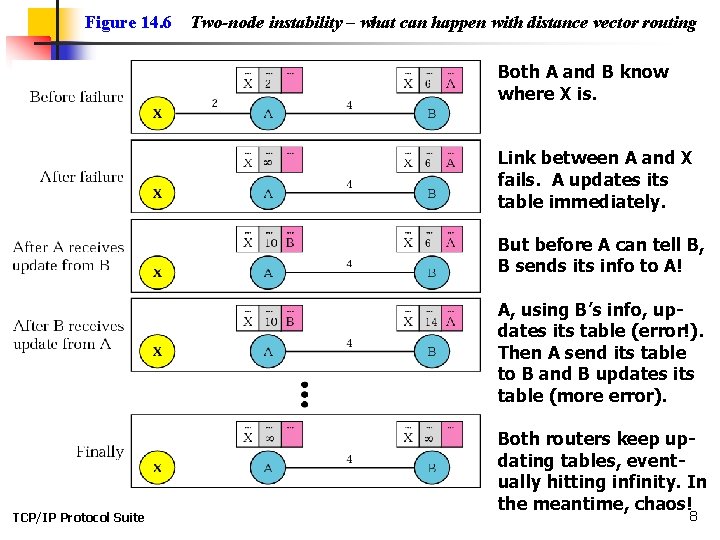
Figure 14. 6 Two-node instability – what can happen with distance vector routing Both A and B know where X is. Link between A and X fails. A updates its table immediately. But before A can tell B, B sends its info to A! A, using B’s info, updates its table (error!). Then A send its table to B and B updates its table (more error). TCP/IP Protocol Suite Both routers keep updating tables, eventually hitting infinity. In the meantime, chaos! 8

Figure 14. 6 Two-node instability – what can happen with distance vector routing Possible Solutions to two-node instability: 1. Define infinity to be a much smaller value, such as 100. Then it doesn’t take too long to become stable. But now you can’t use distance vector routing in large networks. 2. Split Horizon – instead of flooding entire table to each node, only part of its table is sent. More precisely, if node B thinks that the optimum router to reach X is via A, then B does not need to advertise this piece of info to A – the info has already come from A. 3. Split Horizon and Poison Reverse – Normally, the distance vector protocol uses a timer. If there is no news about a route, the node deletes the route from its table. So when A never hears from B about the route to X, it deletes it. Instead, Node B still advertises the value for X, but if the source of info is A, it replaces the distance with infinity, saying “Do not use this value; what I know about this route comes from you. ” TCP/IP Protocol Suite 9

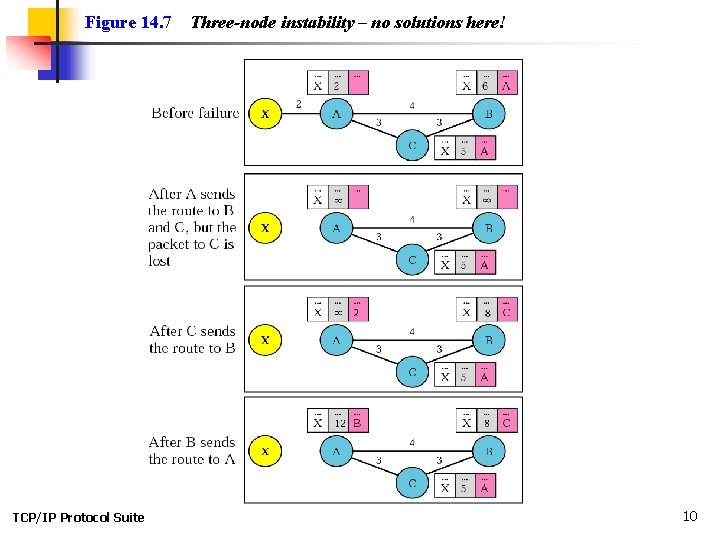
Figure 14. 7 TCP/IP Protocol Suite Three-node instability – no solutions here! 10

14. 3 RIP The Routing Information Protocol (RIP) is an intradomain routing protocol used inside an autonomous system. It is a very simple protocol based on distance vector routing. The topics discussed in this section include: RIP Message Format Requests and Responses Timers in RIP Version 2 Encapsulation TCP/IP Protocol Suite 11

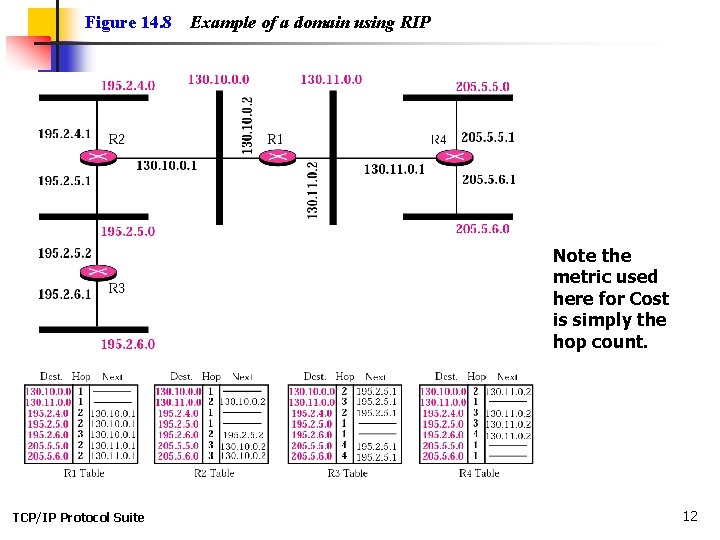
Figure 14. 8 Example of a domain using RIP Note the metric used here for Cost is simply the hop count. TCP/IP Protocol Suite 12

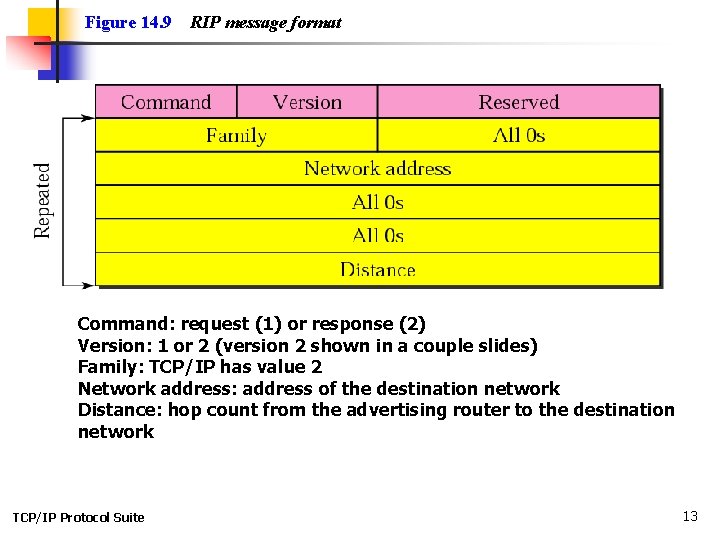
Figure 14. 9 RIP message format Command: request (1) or response (2) Version: 1 or 2 (version 2 shown in a couple slides) Family: TCP/IP has value 2 Network address: address of the destination network Distance: hop count from the advertising router to the destination network TCP/IP Protocol Suite 13

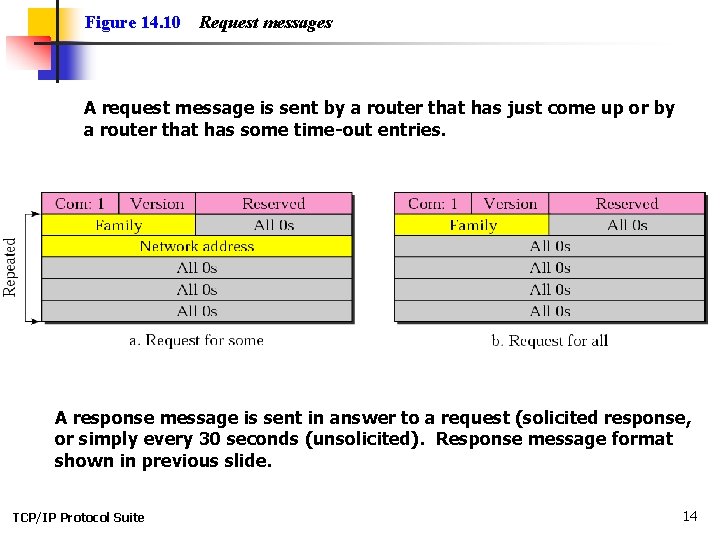
Figure 14. 10 Request messages A request message is sent by a router that has just come up or by a router that has some time-out entries. A response message is sent in answer to a request (solicited response, or simply every 30 seconds (unsolicited). Response message format shown in previous slide. TCP/IP Protocol Suite 14

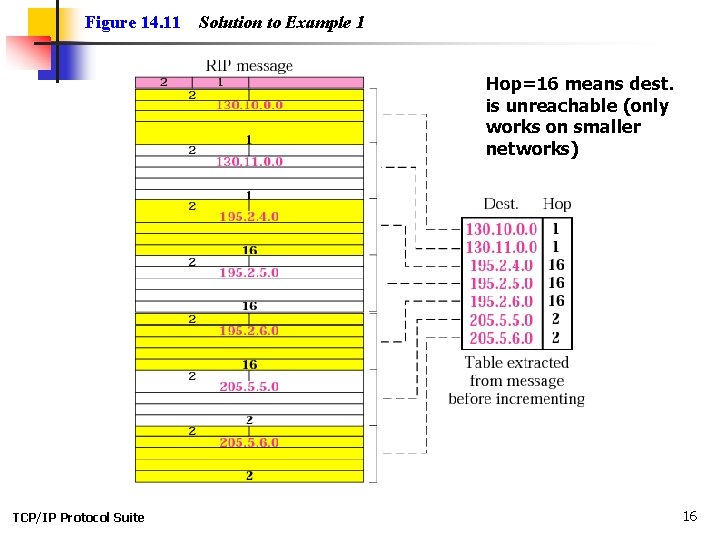
Example 1 Figure 14. 11 shows the update message sent from router R 1 to router R 2 in Figure 14. 8. The message is sent out of interface 130. 10. 0. 2. The message is prepared with the combination of split horizon and poison reverse strategy in mind. Router R 1 has obtained information about networks 195. 2. 4. 0, 195. 2. 5. 0, and 195. 2. 6. 0 from router R 2. When R 1 sends an update message to R 2, it replaces the actual value of the hop counts for these three networks with 16 (infinity) to prevent any confusion for R 2. The figure also shows the table extracted from the message. Router R 2 uses the source address of the IP datagram carrying the RIP message from R 1 (130. 10. 02) as the next hop address. TCP/IP Protocol Suite See Next Slide 15

Figure 14. 11 Solution to Example 1 Hop=16 means dest. is unreachable (only works on smaller networks) TCP/IP Protocol Suite 16

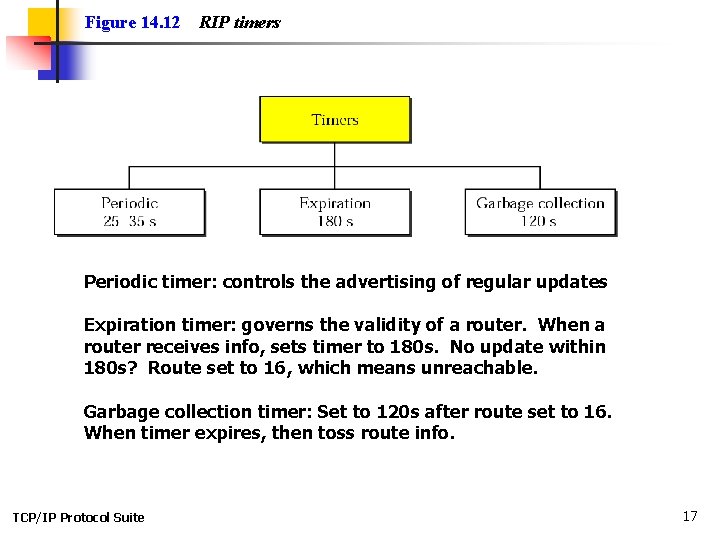
Figure 14. 12 RIP timers Periodic timer: controls the advertising of regular updates Expiration timer: governs the validity of a router. When a router receives info, sets timer to 180 s. No update within 180 s? Route set to 16, which means unreachable. Garbage collection timer: Set to 120 s after route set to 16. When timer expires, then toss route info. TCP/IP Protocol Suite 17

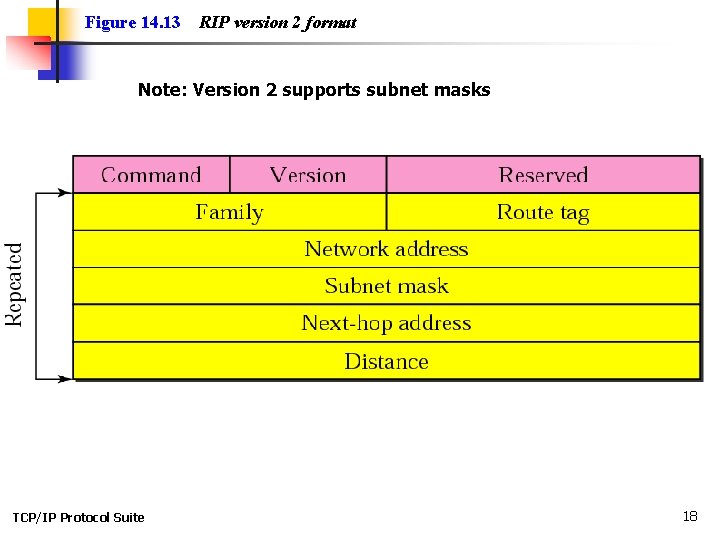
Figure 14. 13 RIP version 2 format Note: Version 2 supports subnet masks TCP/IP Protocol Suite 18

14. 4 LINK STATE ROUTING In link state routing, if each node in the domain has the entire topology of the domain, the node can use Dijkstra’s algorithm to build a routing table. The topics discussed in this section include: Building Routing Tables TCP/IP Protocol Suite 19

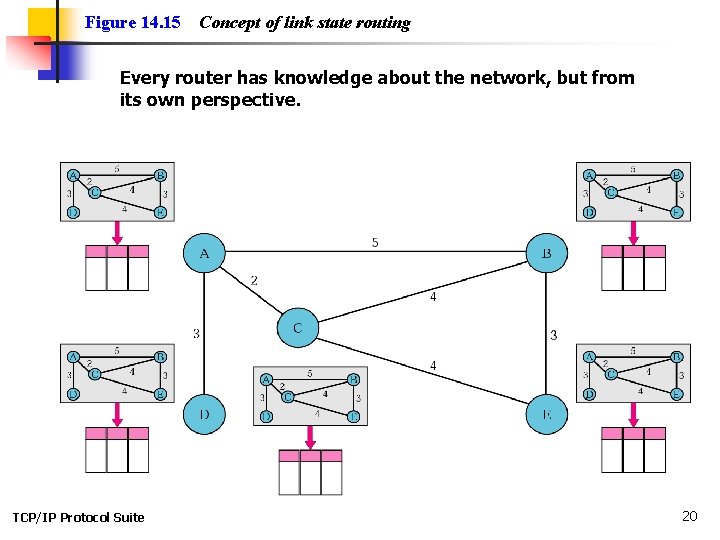
Figure 14. 15 Concept of link state routing Every router has knowledge about the network, but from its own perspective. TCP/IP Protocol Suite 20

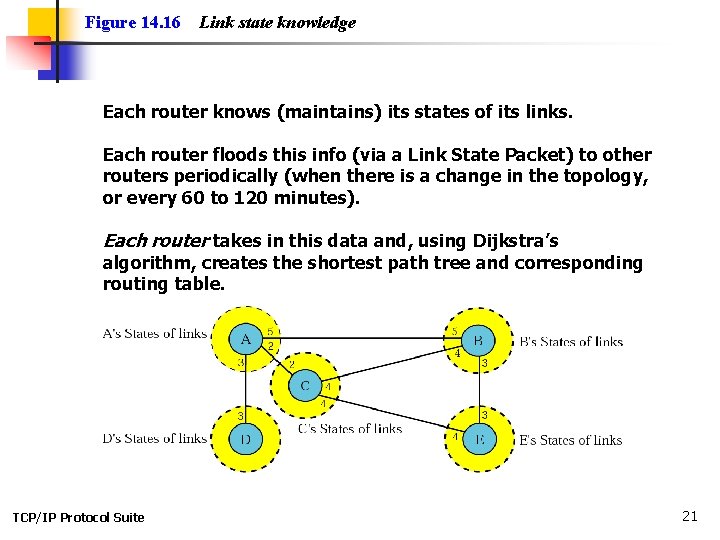
Figure 14. 16 Link state knowledge Each router knows (maintains) its states of its links. Each router floods this info (via a Link State Packet) to other routers periodically (when there is a change in the topology, or every 60 to 120 minutes). Each router takes in this data and, using Dijkstra’s algorithm, creates the shortest path tree and corresponding routing table. TCP/IP Protocol Suite 21

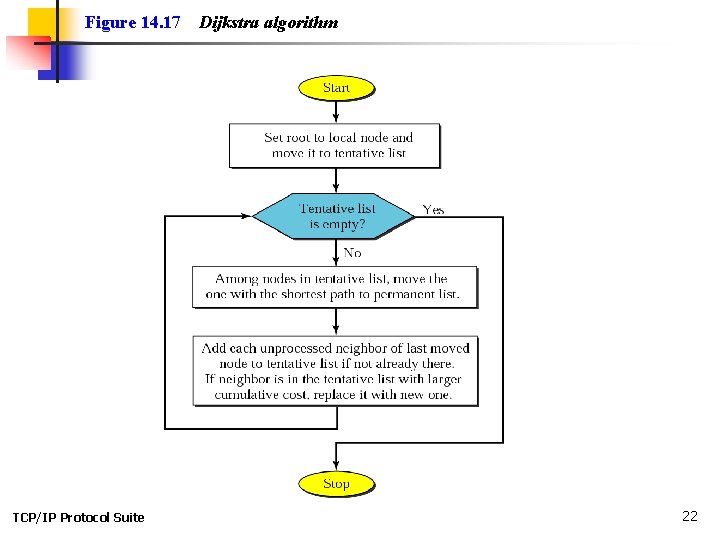
Figure 14. 17 TCP/IP Protocol Suite Dijkstra algorithm 22

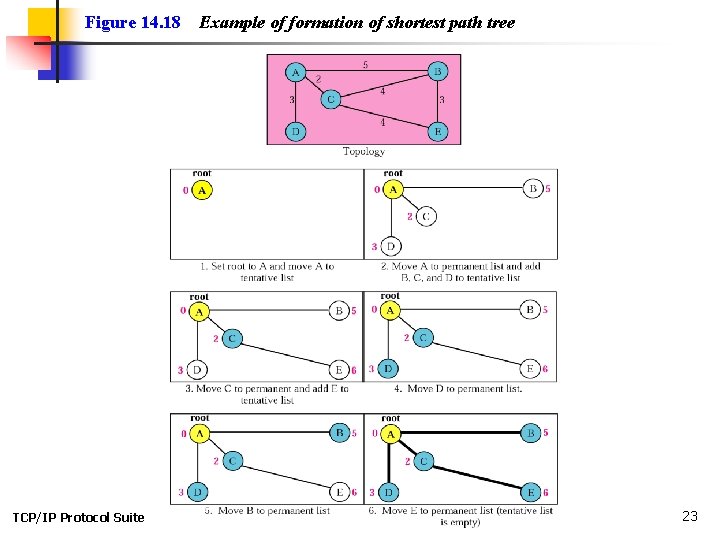
Figure 14. 18 TCP/IP Protocol Suite Example of formation of shortest path tree 23

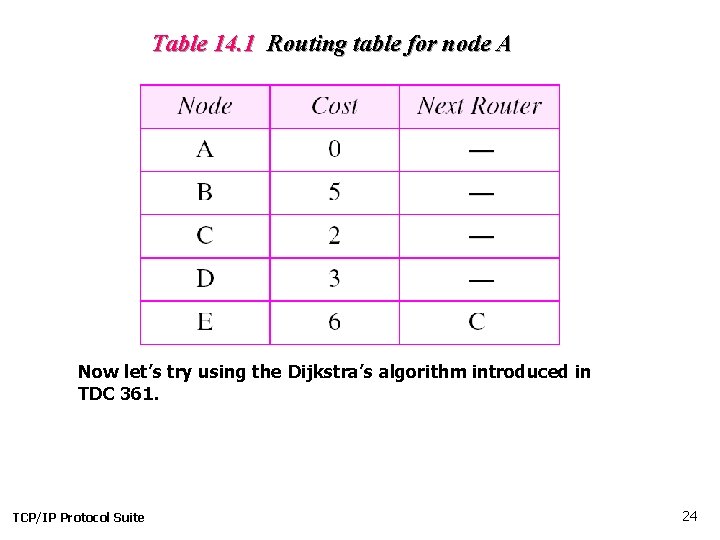
Table 14. 1 Routing table for node A Now let’s try using the Dijkstra’s algorithm introduced in TDC 361. TCP/IP Protocol Suite 24

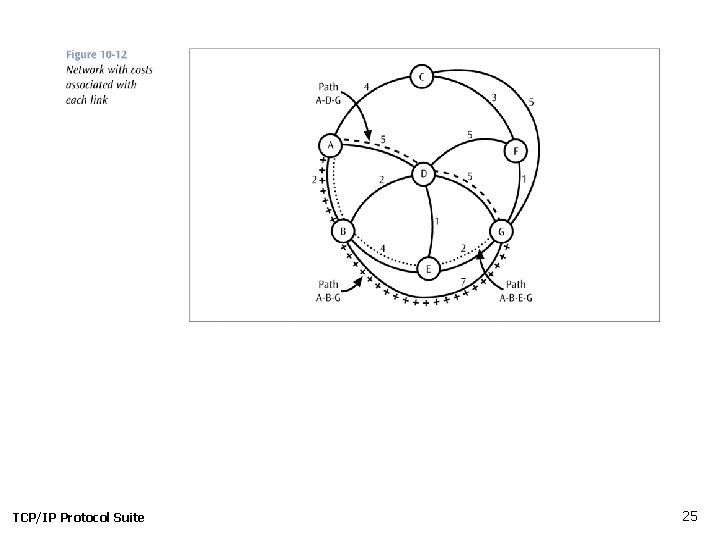
TCP/IP Protocol Suite 25

14. 5 OSPF The Open Shortest Path First (OSPF) protocol is an intradomain routing protocol based on link state routing. Its domain is also an autonomous system. The topics discussed in this section include: Areas Metric Types of Links Graphical Representation OSPF Packets Link State Update Packet Other Packets Encapsulation TCP/IP Protocol Suite 26

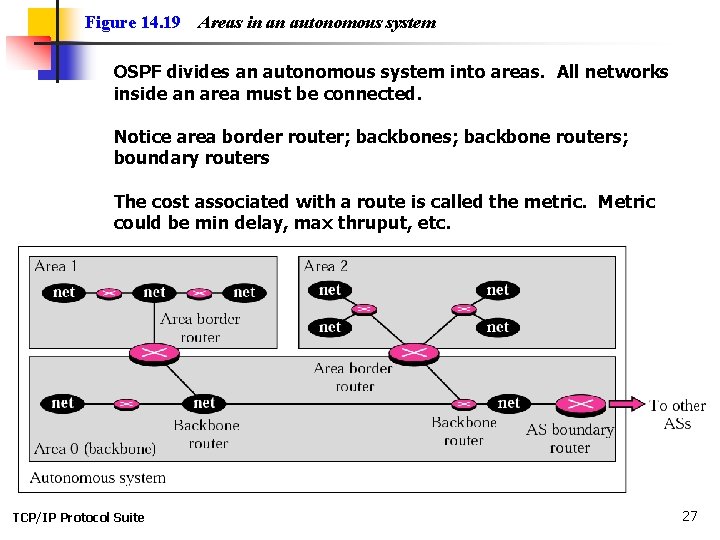
Figure 14. 19 Areas in an autonomous system OSPF divides an autonomous system into areas. All networks inside an area must be connected. Notice area border router; backbones; backbone routers; boundary routers The cost associated with a route is called the metric. Metric could be min delay, max thruput, etc. TCP/IP Protocol Suite 27

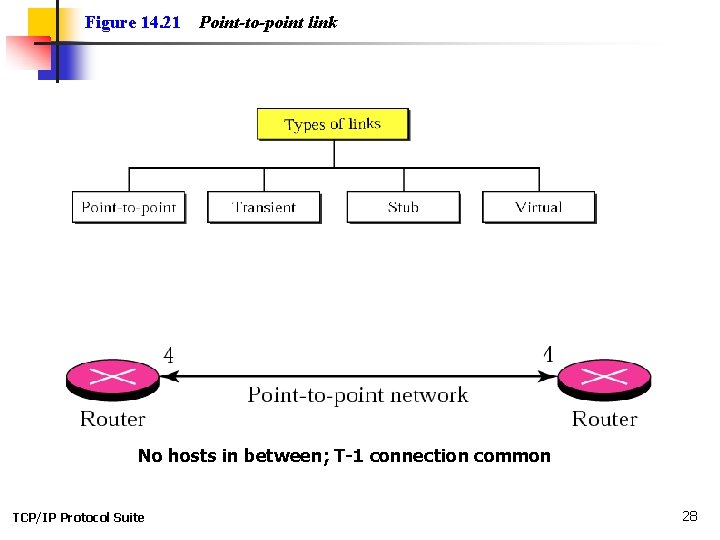
Figure 14. 21 Point-to-point link No hosts in between; T-1 connection common TCP/IP Protocol Suite 28

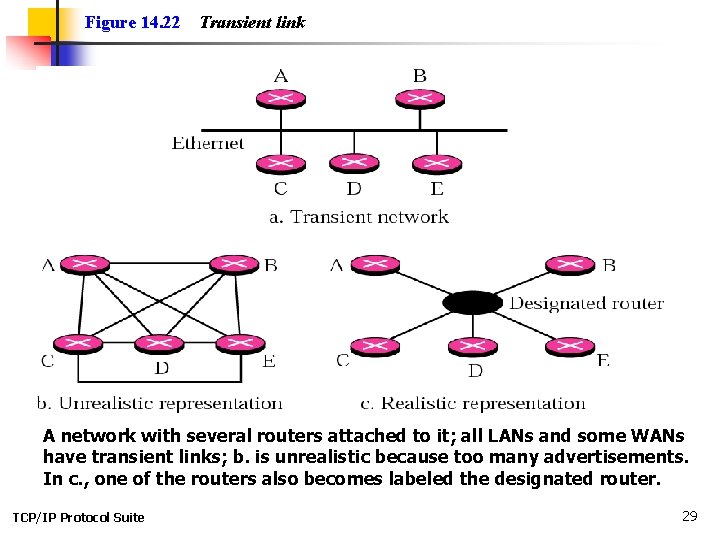
Figure 14. 22 Transient link A network with several routers attached to it; all LANs and some WANs have transient links; b. is unrealistic because too many advertisements. In c. , one of the routers also becomes labeled the designated router. TCP/IP Protocol Suite 29

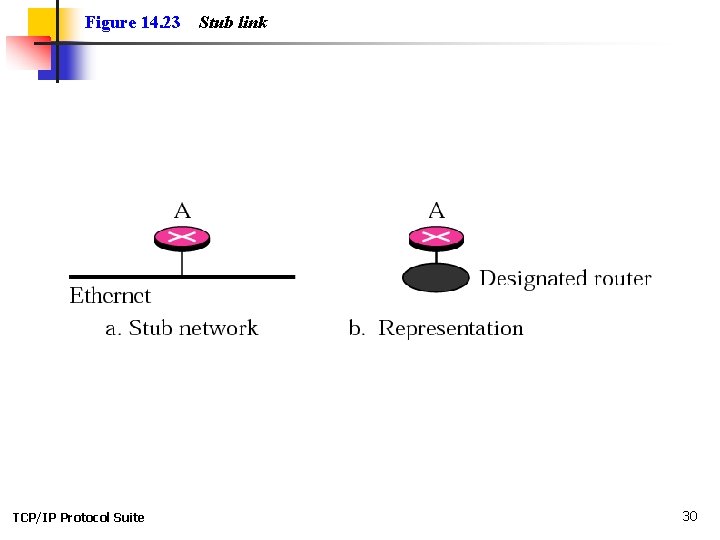
Figure 14. 23 TCP/IP Protocol Suite Stub link 30

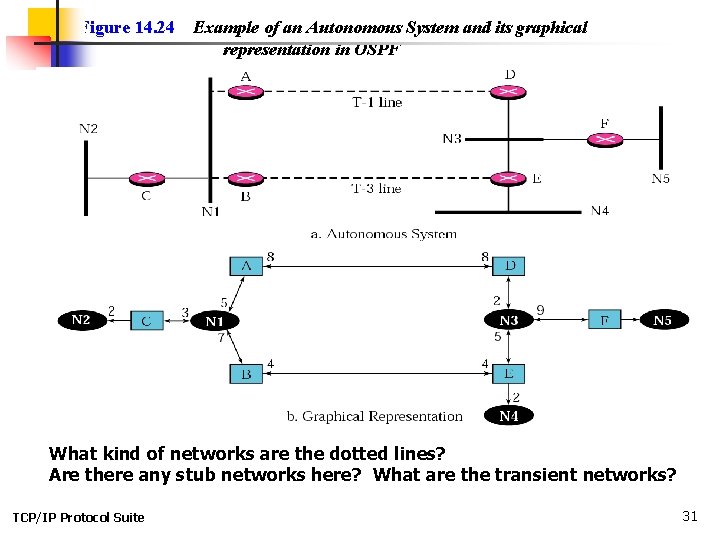
Figure 14. 24 Example of an Autonomous System and its graphical representation in OSPF What kind of networks are the dotted lines? Are there any stub networks here? What are the transient networks? TCP/IP Protocol Suite 31

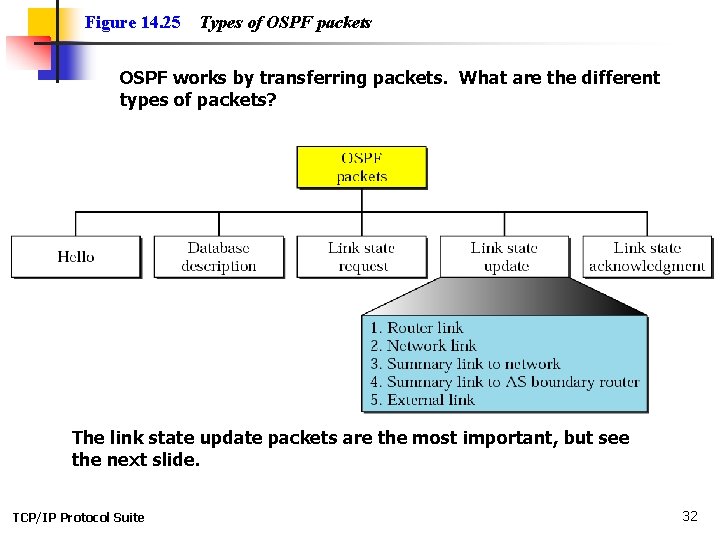
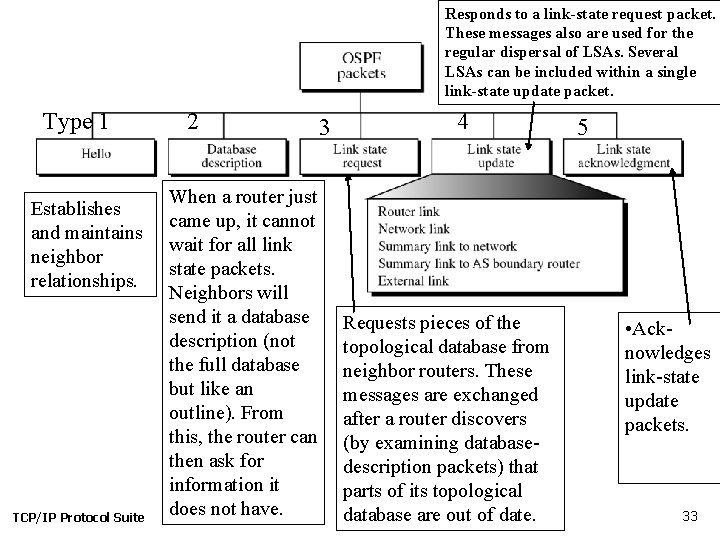
Figure 14. 25 Types of OSPF packets OSPF works by transferring packets. What are the different types of packets? The link state update packets are the most important, but see the next slide. TCP/IP Protocol Suite 32

Responds to a link-state request packet. These messages also are used for the regular dispersal of LSAs. Several LSAs can be included within a single link-state update packet. Type 1 Establishes and maintains neighbor relationships. TCP/IP Protocol Suite 2 When a router just came up, it cannot wait for all link state packets. Neighbors will send it a database description (not the full database but like an outline). From this, the router can then ask for information it does not have. 3 4 Requests pieces of the topological database from neighbor routers. These messages are exchanged after a router discovers (by examining databasedescription packets) that parts of its topological database are out of date. 5 • Acknowledges link-state update packets. 33

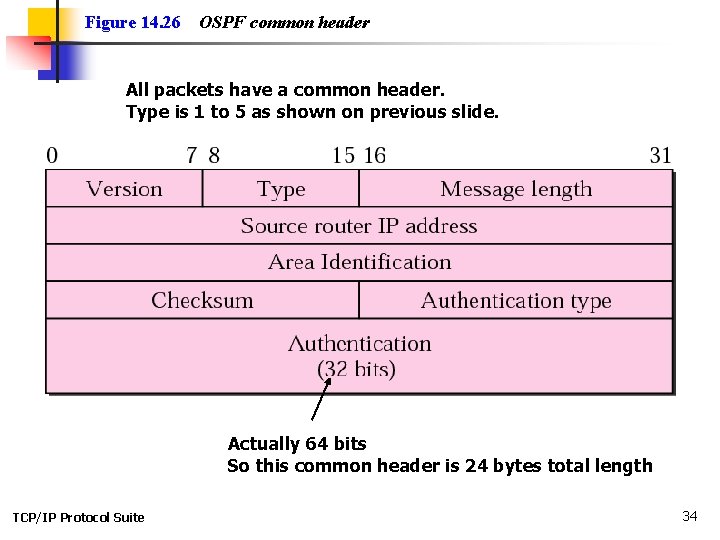
Figure 14. 26 OSPF common header All packets have a common header. Type is 1 to 5 as shown on previous slide. Actually 64 bits So this common header is 24 bytes total length TCP/IP Protocol Suite 34

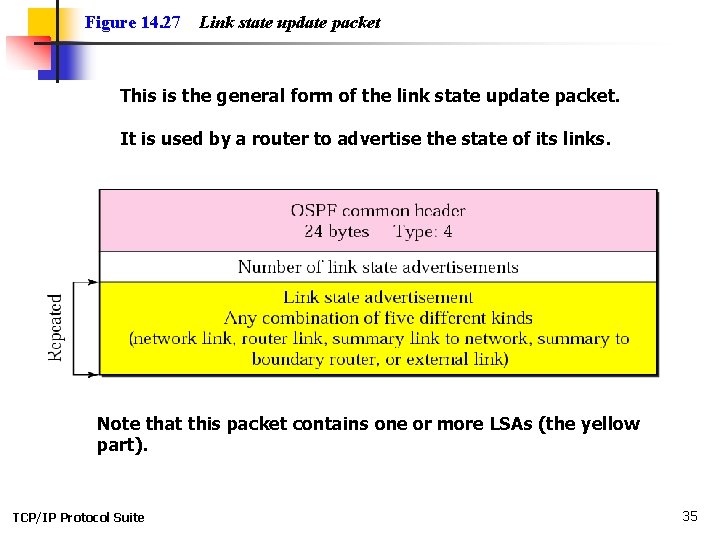
Figure 14. 27 Link state update packet This is the general form of the link state update packet. It is used by a router to advertise the state of its links. Note that this packet contains one or more LSAs (the yellow part). TCP/IP Protocol Suite 35

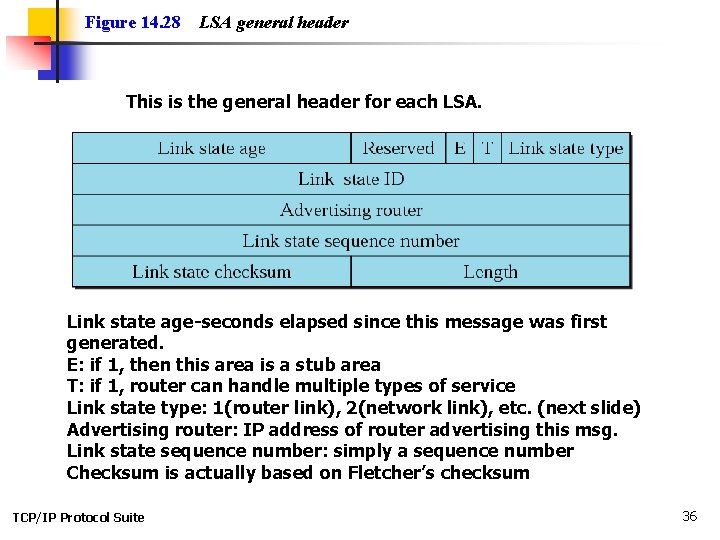
Figure 14. 28 LSA general header This is the general header for each LSA. Link state age-seconds elapsed since this message was first generated. E: if 1, then this area is a stub area T: if 1, router can handle multiple types of service Link state type: 1(router link), 2(network link), etc. (next slide) Advertising router: IP address of router advertising this msg. Link state sequence number: simply a sequence number Checksum is actually based on Fletcher’s checksum TCP/IP Protocol Suite 36

Link-state advertisement (Link-state update) types • Router Links (RL) (Type 1) are generated by all routers. These links describe the state of the router interfaces inside a particular area. These links are only flooded inside the router's area. • Network Links (NL) (type 2) are generated by a DR (Designated Router) of a particular segment; these are an indication of the routers connected to that segment. • Summary Links (SL) are the inter-area links (type 3); these links will list the networks inside other areas but still belonging to the autonomous system. Summary links are injected by the ABR (Area Border Router) from the backbone into other areas and from other areas into the backbone. These links are used for aggregation between areas. • AS boundary router summary links are type 4 links that point to the ASBR (Autonomous System Boundary Router). This is to make sure that all routers know the way to exit the autonomous system. • External Links (EL) (type 5), these are injected by the ASBR into the domain. TCP/IP Protocol Suite 37

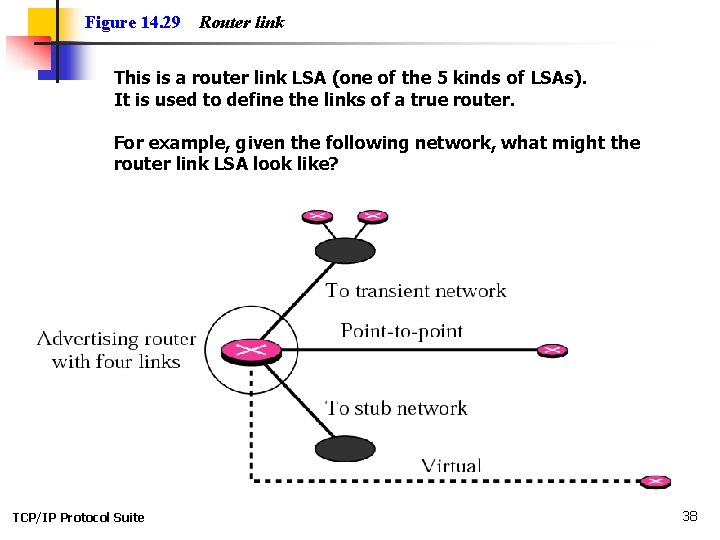
Figure 14. 29 Router link This is a router link LSA (one of the 5 kinds of LSAs). It is used to define the links of a true router. For example, given the following network, what might the router link LSA look like? TCP/IP Protocol Suite 38

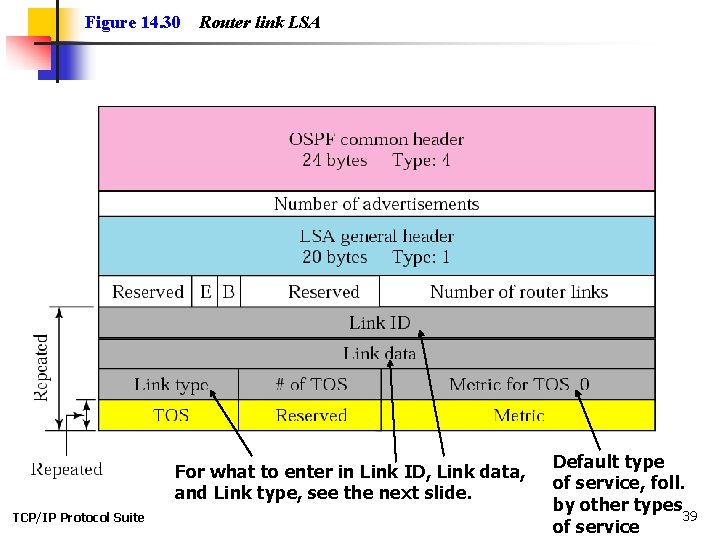
Figure 14. 30 Router link LSA For what to enter in Link ID, Link data, and Link type, see the next slide. TCP/IP Protocol Suite Default type of service, foll. by other types 39 of service

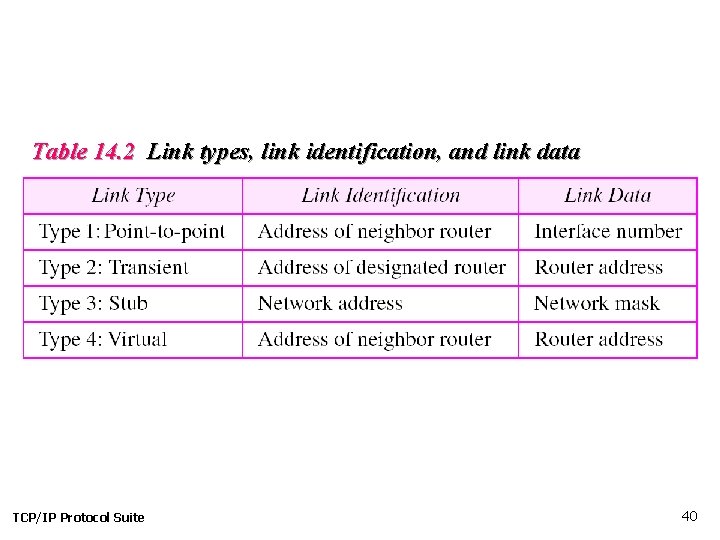
Table 14. 2 Link types, link identification, and link data TCP/IP Protocol Suite 40

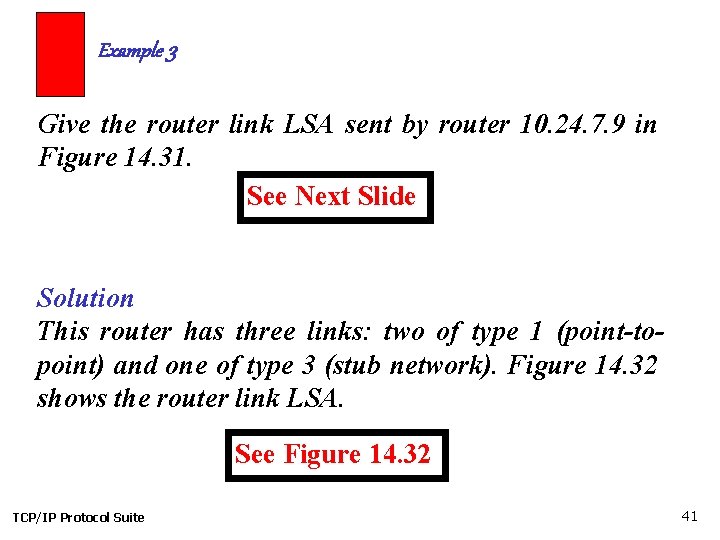
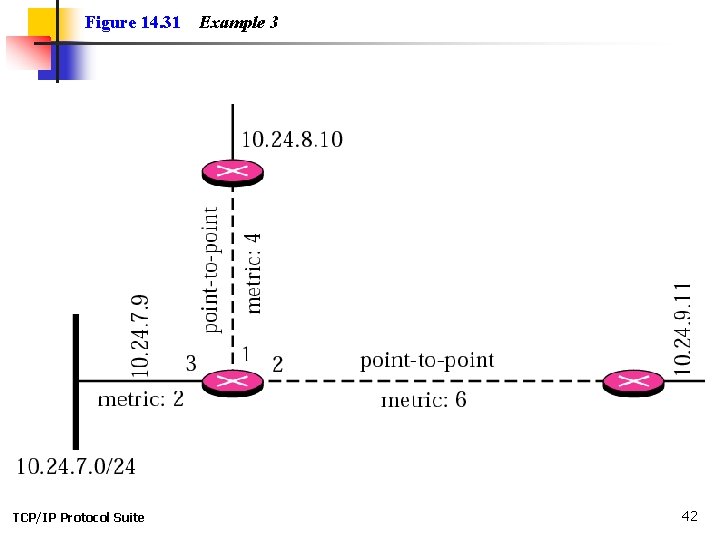
Example 3 Give the router link LSA sent by router 10. 24. 7. 9 in Figure 14. 31. See Next Slide Solution This router has three links: two of type 1 (point-topoint) and one of type 3 (stub network). Figure 14. 32 shows the router link LSA. See Figure 14. 32 TCP/IP Protocol Suite 41

Figure 14. 31 TCP/IP Protocol Suite Example 3 42

Figure 14. 32 TCP/IP Protocol Suite Solution to Example 3 43

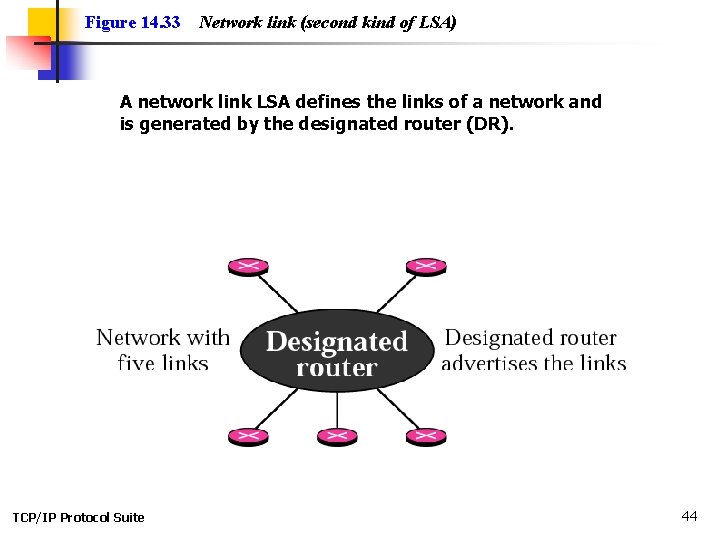
Figure 14. 33 Network link (second kind of LSA) A network link LSA defines the links of a network and is generated by the designated router (DR). TCP/IP Protocol Suite 44

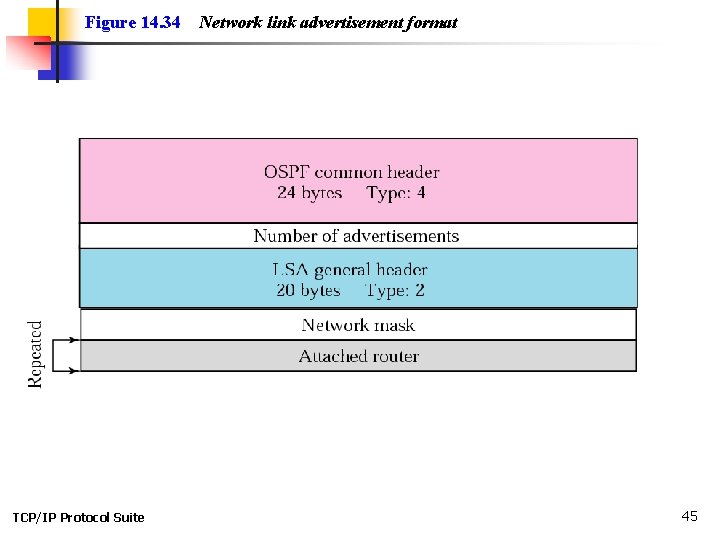
Figure 14. 34 TCP/IP Protocol Suite Network link advertisement format 45

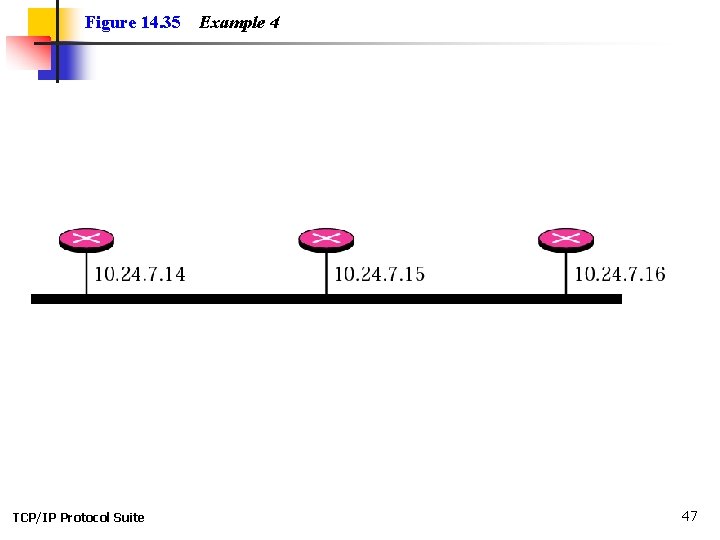
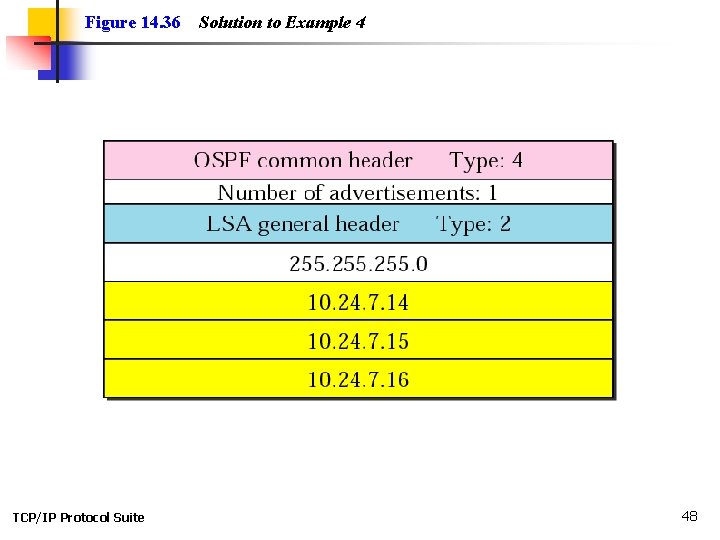
Example 4 Give the network link LSA in Figure 14. 35. See Next Slide Solution. See Figure 14. 36 TCP/IP Protocol Suite 46

Figure 14. 35 TCP/IP Protocol Suite Example 4 47

Figure 14. 36 TCP/IP Protocol Suite Solution to Example 4 48

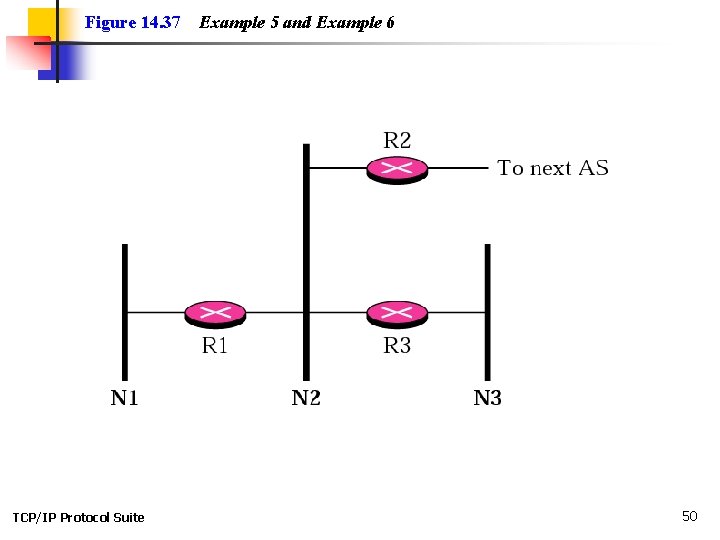
Example 5 In Figure 14. 37, which router(s) sends out router link LSAs? See Next Slide Solution All routers advertise router link LSAs. a. R 1 has two links, N 1 and N 2. b. R 2 has one link, N 1. c. R 3 has two links, N 2 and N 3. TCP/IP Protocol Suite 49

Figure 14. 37 TCP/IP Protocol Suite Example 5 and Example 6 50

Example 6 In Figure 14. 37, which router(s) sends out the network link LSAs? Solution All three network must advertise network links: a. Advertisement for N 1 is done by R 1 because it is the only attached router and therefore the designated router. b. Advertisement for N 2 can be done by either R 1, R 2, or R 3, depending on which one is chosen as the designated router. c. Advertisement for N 3 is done by R 3 because it is the only attached router and therefore the designated router. TCP/IP Protocol Suite 51

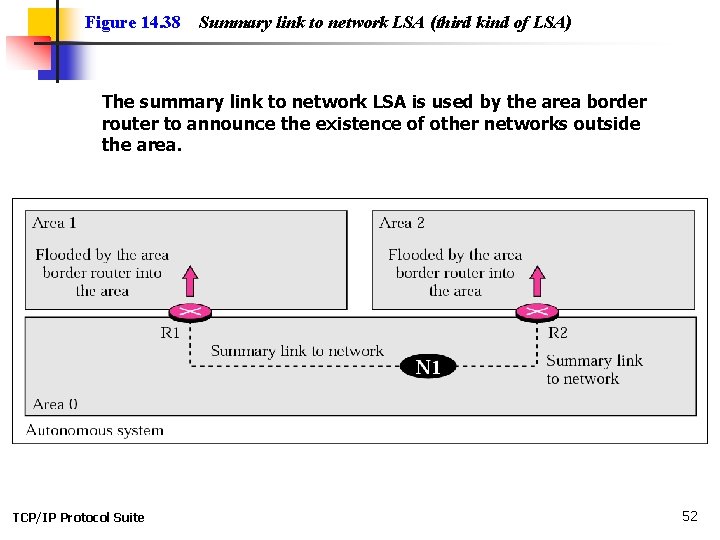
Figure 14. 38 Summary link to network LSA (third kind of LSA) The summary link to network LSA is used by the area border router to announce the existence of other networks outside the area. TCP/IP Protocol Suite 52

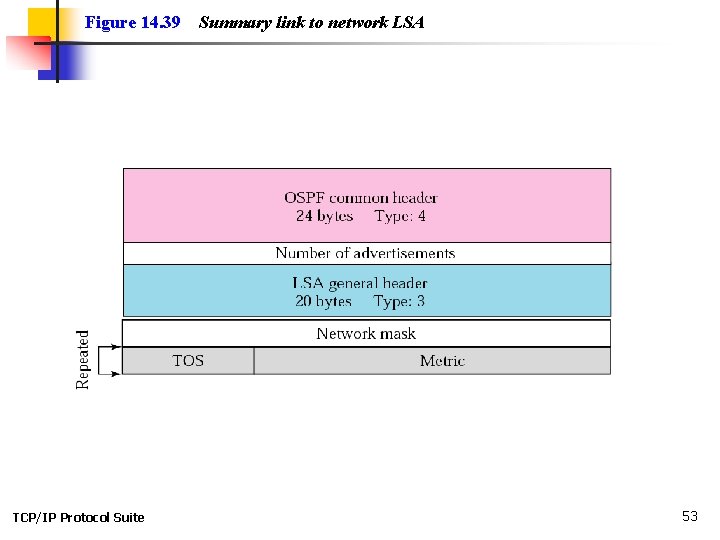
Figure 14. 39 TCP/IP Protocol Suite Summary link to network LSA 53

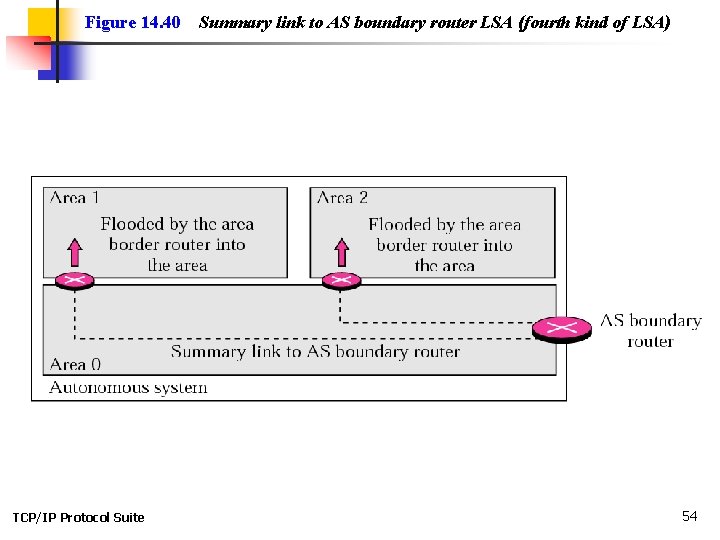
Figure 14. 40 TCP/IP Protocol Suite Summary link to AS boundary router LSA (fourth kind of LSA) 54

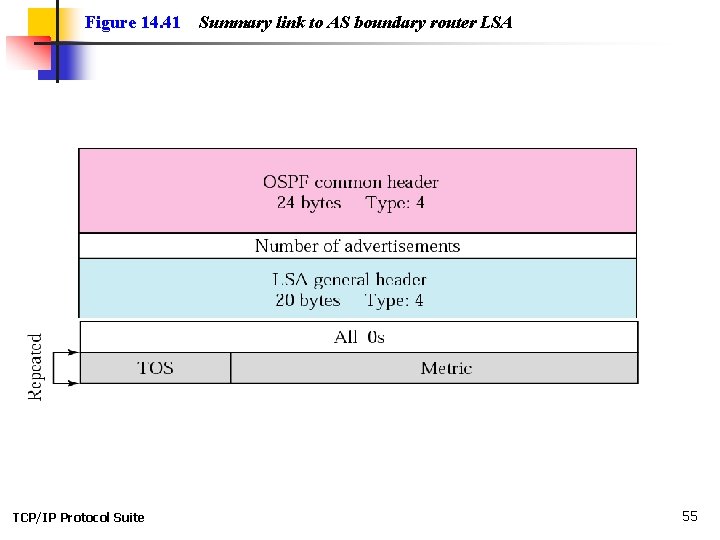
Figure 14. 41 TCP/IP Protocol Suite Summary link to AS boundary router LSA 55

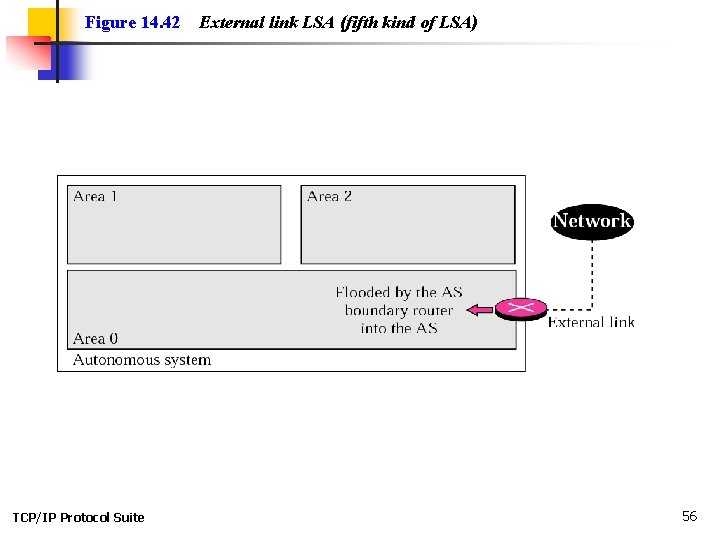
Figure 14. 42 TCP/IP Protocol Suite External link LSA (fifth kind of LSA) 56

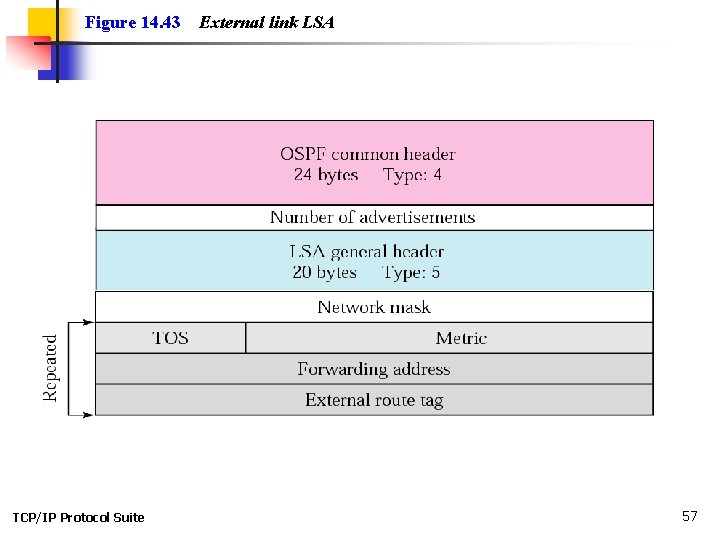
Figure 14. 43 TCP/IP Protocol Suite External link LSA 57

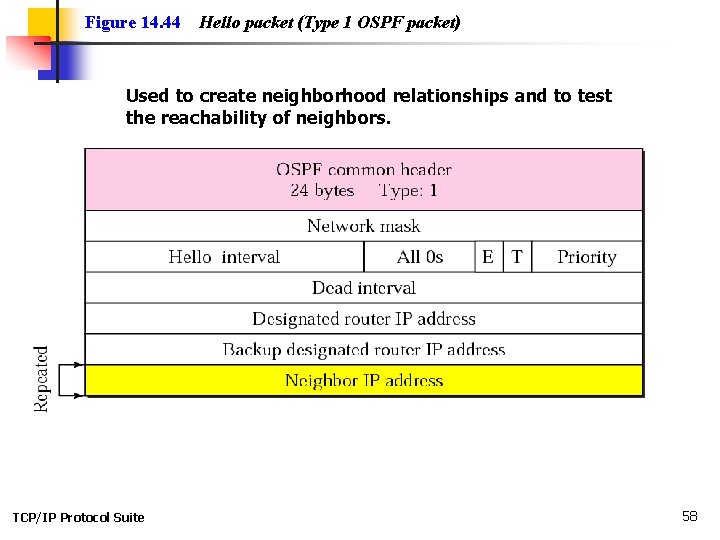
Figure 14. 44 Hello packet (Type 1 OSPF packet) Used to create neighborhood relationships and to test the reachability of neighbors. TCP/IP Protocol Suite 58

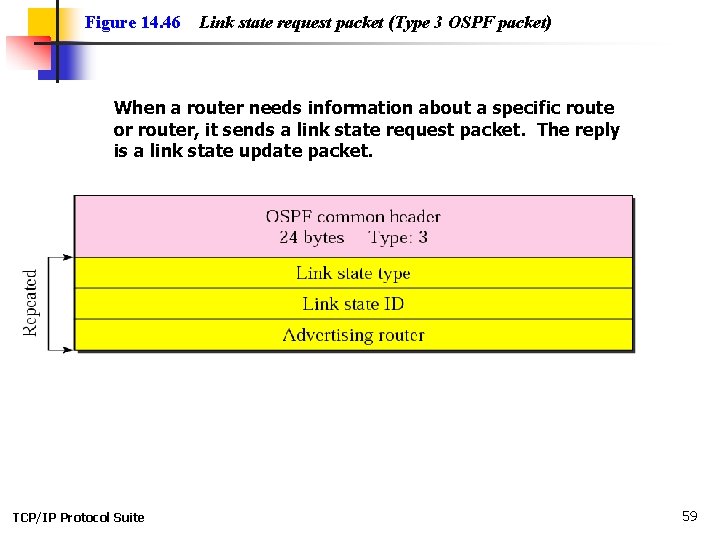
Figure 14. 46 Link state request packet (Type 3 OSPF packet) When a router needs information about a specific route or router, it sends a link state request packet. The reply is a link state update packet. TCP/IP Protocol Suite 59

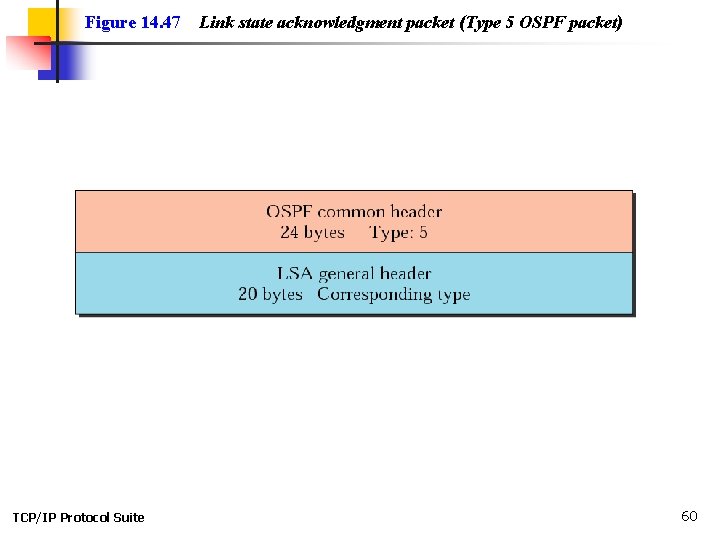
Figure 14. 47 TCP/IP Protocol Suite Link state acknowledgment packet (Type 5 OSPF packet) 60

Note: OSPF packets are encapsulated in IP datagrams. TCP/IP Protocol Suite 61

14. 6 PATH VECTOR ROUTING Path vector routing is similar to distance vector routing. There is at least one node, called the speaker node, in each AS that creates a routing table and advertises it to speaker nodes in the neighboring ASs. Only the speaker nodes communicate. The speaker node advertises the path, not the metric of the nodes. TCP/IP Protocol Suite 62

14. 7 BGP Border Gateway Protocol (BGP) is an interdomain routing protocol using path vector routing. It first appeared in 1989 and has gone through four versions. BGP interconnects three different types of AS: 1. Stub AS, e. g. a corporate network 2. Multihomed AS, e. g. a large corporate network with connections to multiple ASs, but does not allow traffic to pass thru (transient) 3. Transit AS - one that allows transient traffic, such as an Internet backbone TCP/IP Protocol Suite 63

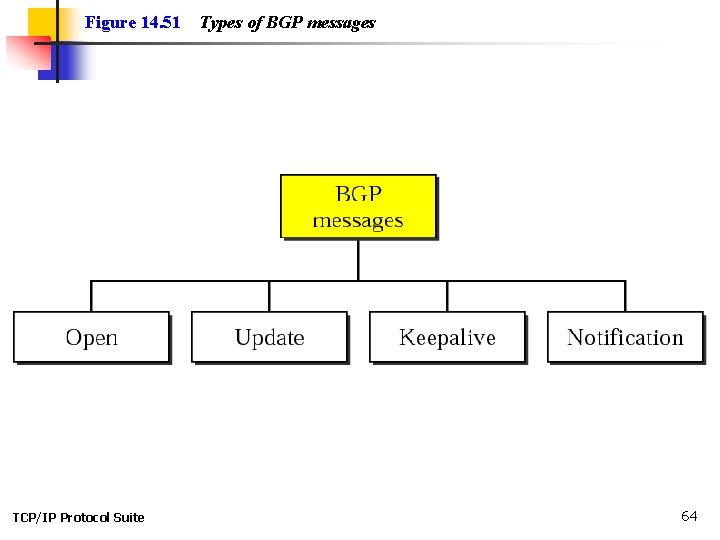
Figure 14. 51 TCP/IP Protocol Suite Types of BGP messages 64

Note: BGP supports classless addressing and CIDR. TCP/IP Protocol Suite 65

Note: BGP uses the services of TCP on port 179. TCP/IP Protocol Suite 66