Chapter 23 ProcesstoProcess Delivery UDP TCP and SCTP































































- Slides: 145

Chapter 23 Process-to-Process Delivery: UDP, TCP, and SCTP 23. 1 Copyright © The Mc. Graw-Hill Companies, Inc. Permission required for reproduction or display.

Transport layer duties 23. 2

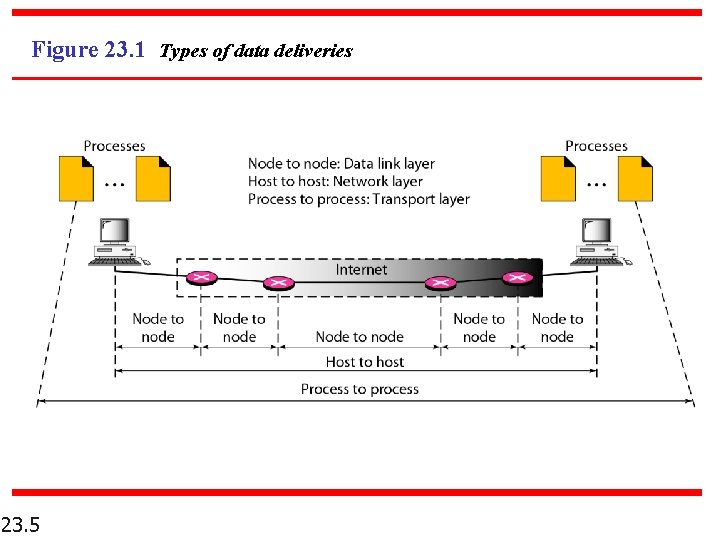
23 -1 PROCESS-TO-PROCESS DELIVERY Overview: The transport layer is responsible for process-to-process delivery—the delivery of a packet, part of a message, from one process to another. Two processes communicate in a client/server relationship. 23. 3

Note The transport layer is responsible for process-to-process delivery – the delivery of a packet, part of a message, from one process to another. 23. 4

Figure 23. 1 Types of data deliveries 23. 5

Client/Server Paradigm 23. 6

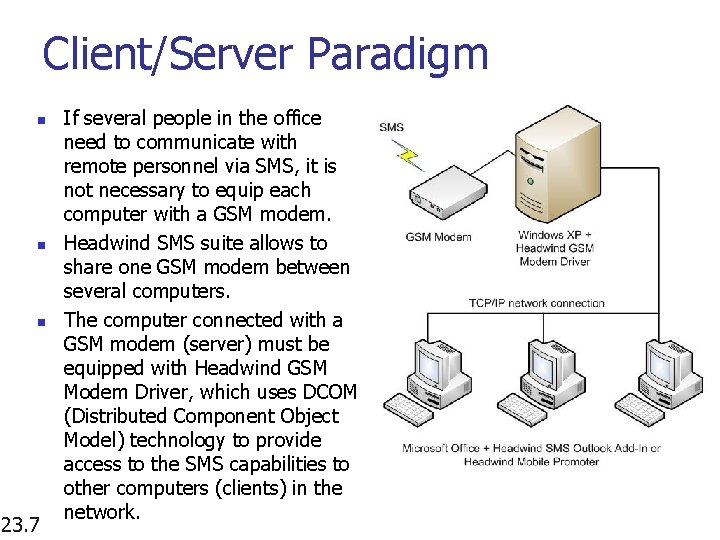
Client/Server Paradigm n n n 23. 7 If several people in the office need to communicate with remote personnel via SMS, it is not necessary to equip each computer with a GSM modem. Headwind SMS suite allows to share one GSM modem between several computers. The computer connected with a GSM modem (server) must be equipped with Headwind GSM Modem Driver, which uses DCOM (Distributed Component Object Model) technology to provide access to the SMS capabilities to other computers (clients) in the network.

Client/Server Paradigm n 23. 8 Operating systems today support both multiuser and multiprogramming environments.

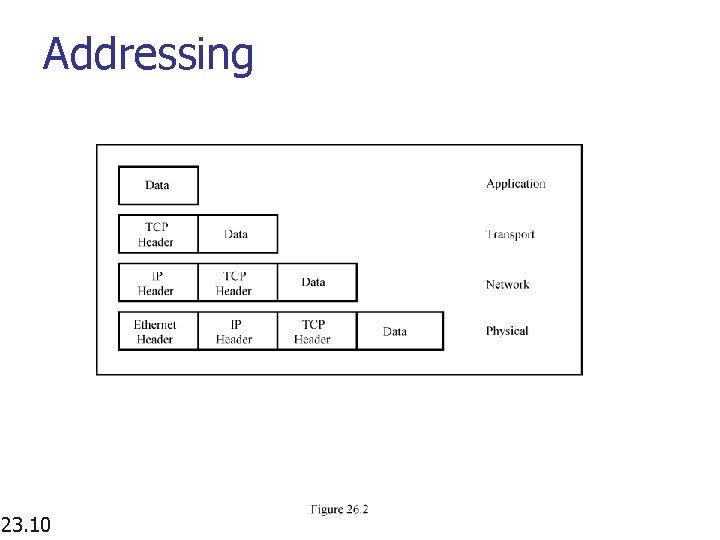
Addressing 23. 9

Addressing 23. 10

Addressing 23. 11

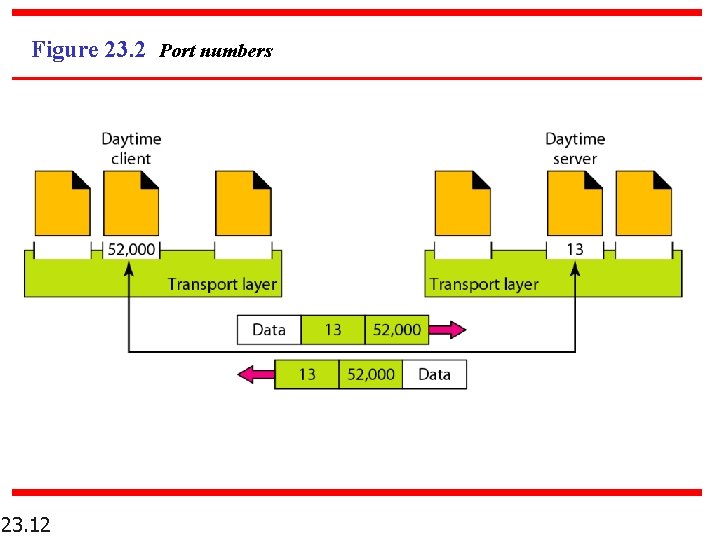
Figure 23. 2 Port numbers 23. 12

Figure 23. 3 IP addresses versus port numbers 23. 13

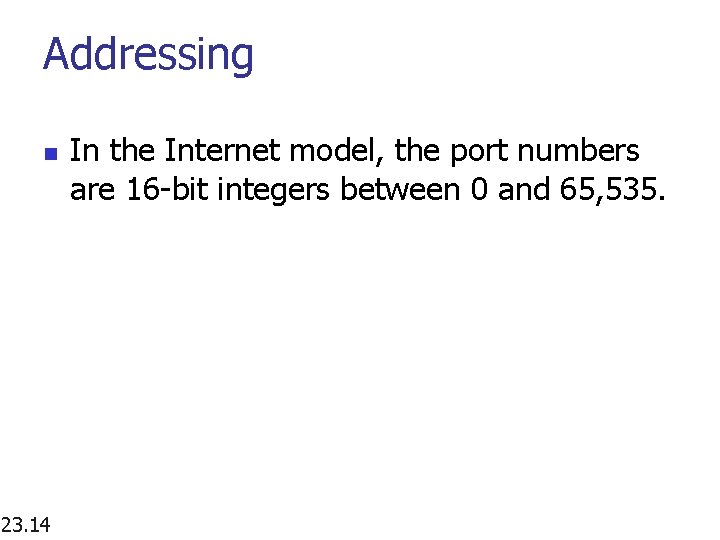
Addressing n 23. 14 In the Internet model, the port numbers are 16 -bit integers between 0 and 65, 535.

Summary In the client-server paradigm, an application program on the local host, called the client, needs services from an application program on the remote host, called a server. The server program is assigned a universal port number called a well-known port number. The client program is assigned a random port number called the ephemeral port number. 23. 15

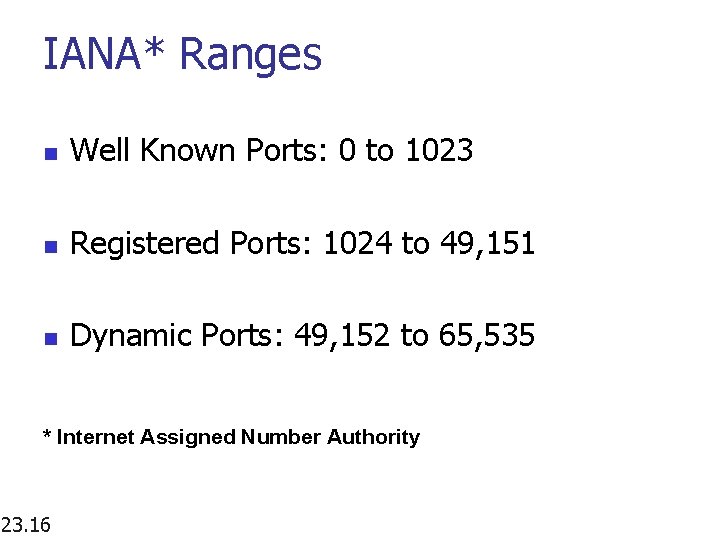
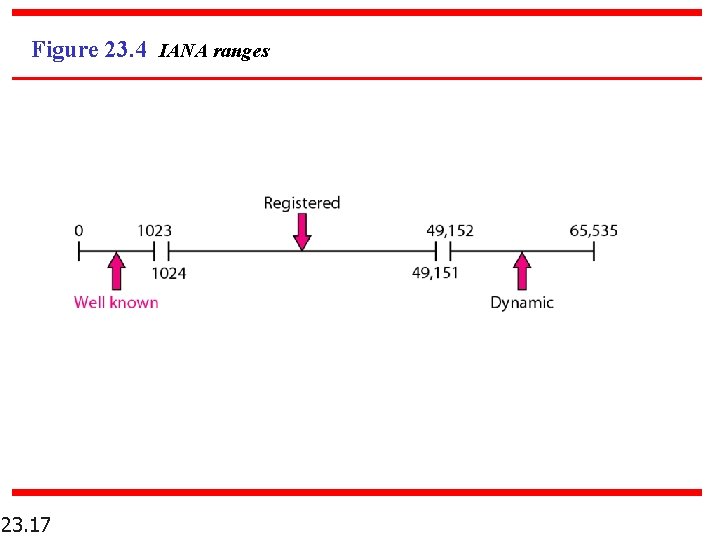
IANA* Ranges n Well Known Ports: 0 to 1023 n Registered Ports: 1024 to 49, 151 n Dynamic Ports: 49, 152 to 65, 535 * Internet Assigned Number Authority 23. 16

Figure 23. 4 IANA ranges 23. 17

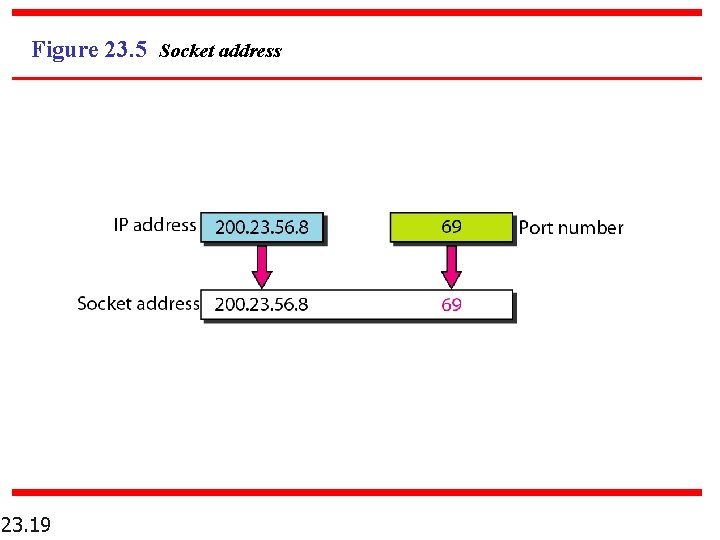
Socket Addresses n 23. 18 Process to Process delivery needs two identifiers, IP address, and port number, at each end to make a connection.

Figure 23. 5 Socket address 23. 19

Socket Addresses n 23. 20 A Transport Layer protocol needs a pair of socket addresses; the client socket address and the server socket address.

Review n n 23. 21 The transport layer is where data is encapsulated into segments. These segments are then sent using either TCP or UDP protocols. TCP is a connection-oriented protocol, which means the sender does not send any data to the destination node until the destination node acknowledges that it is listening to the sender.

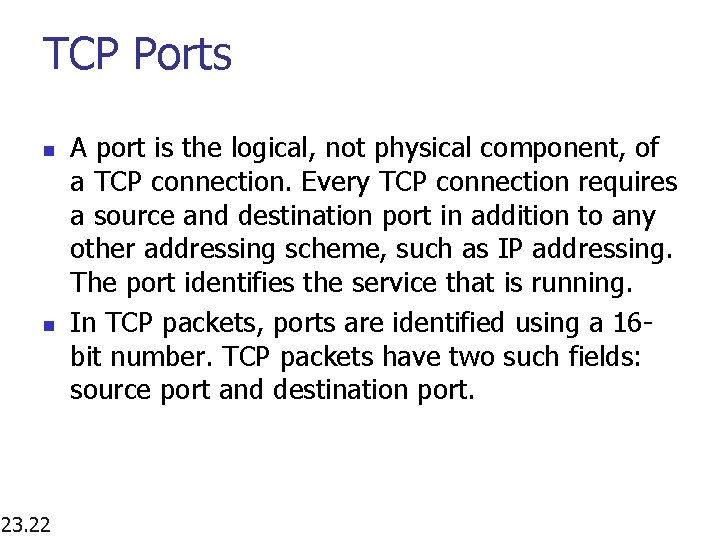
TCP Ports n n 23. 22 A port is the logical, not physical component, of a TCP connection. Every TCP connection requires a source and destination port in addition to any other addressing scheme, such as IP addressing. The port identifies the service that is running. In TCP packets, ports are identified using a 16 bit number. TCP packets have two such fields: source port and destination port.

TCP Ports n n 23. 23 Ports also help network administrators to identify, stop, or disable services that are not really needed. As a network administrator or IT professional, you should be familiar with ports and control their use. Open ports are an invitation for attacks. Port numbers can go up to 65, 535 but only the first 1023 ports are considered well-known. Let’s check www. iana. org for a list of well-known ports.

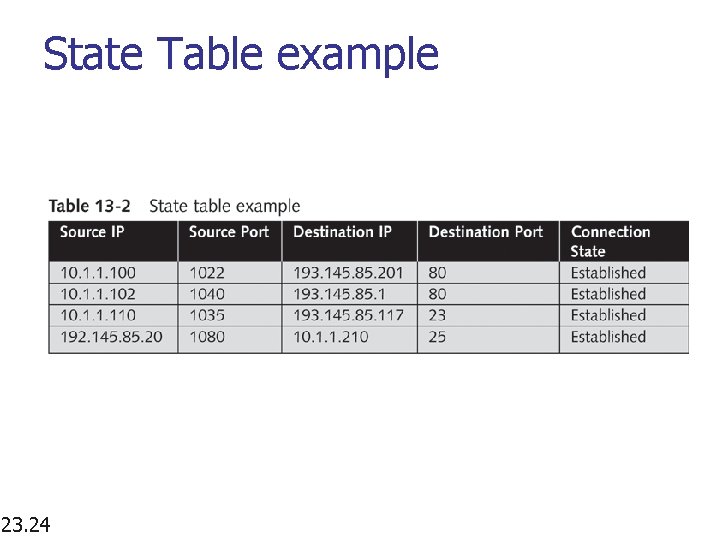
State Table example 23. 24

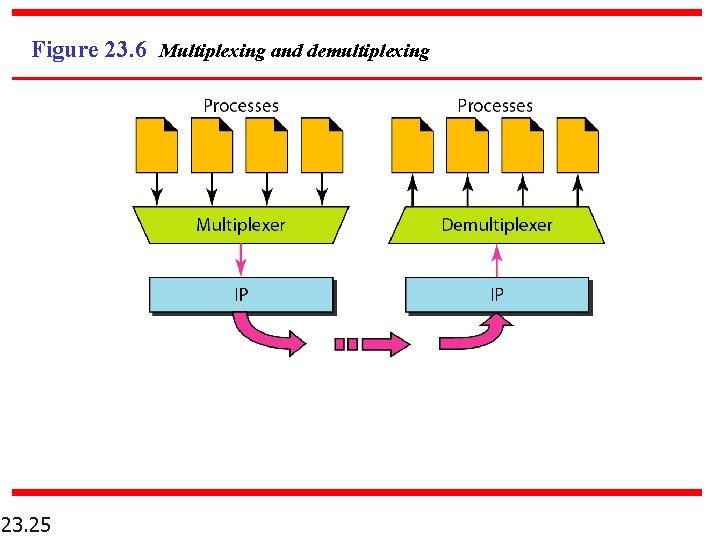
Figure 23. 6 Multiplexing and demultiplexing 23. 25

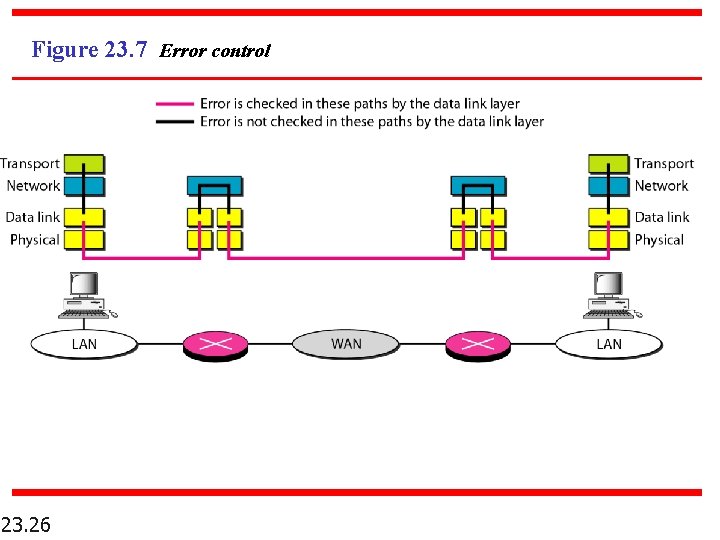
Figure 23. 7 Error control 23. 26

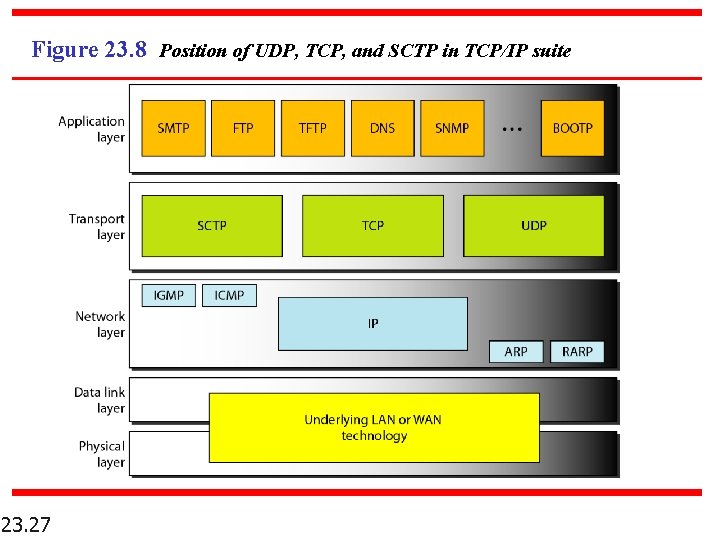
Figure 23. 8 Position of UDP, TCP, and SCTP in TCP/IP suite 23. 27

23 -2 USER DATAGRAM PROTOCOL (UDP) Overview: The User Datagram Protocol (UDP) is called a connectionless, unreliable transport protocol. It does not add anything to the services of IP except to provide process-to-process communication instead of host-to-host communication. 23. 28

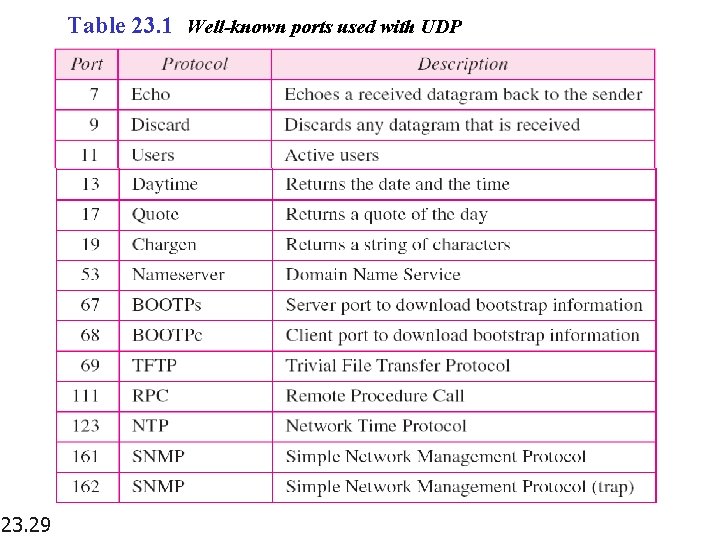
Table 23. 1 Well-known ports used with UDP 23. 29

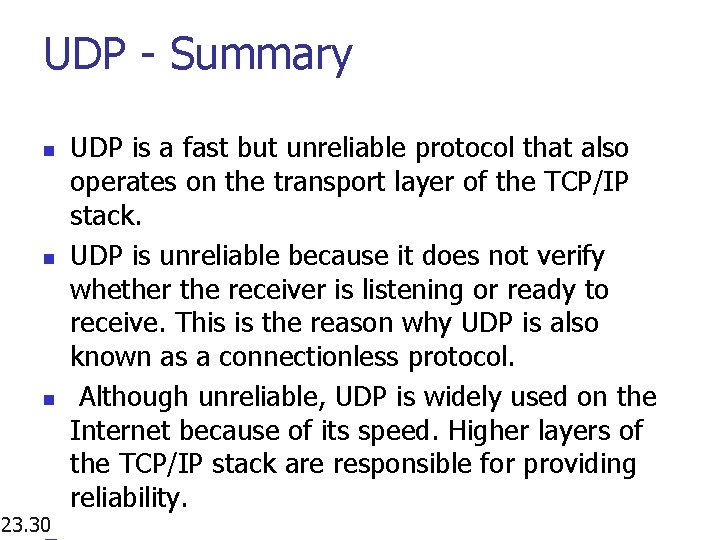
UDP - Summary n n n 23. 30 UDP is a fast but unreliable protocol that also operates on the transport layer of the TCP/IP stack. UDP is unreliable because it does not verify whether the receiver is listening or ready to receive. This is the reason why UDP is also known as a connectionless protocol. Although unreliable, UDP is widely used on the Internet because of its speed. Higher layers of the TCP/IP stack are responsible for providing reliability.

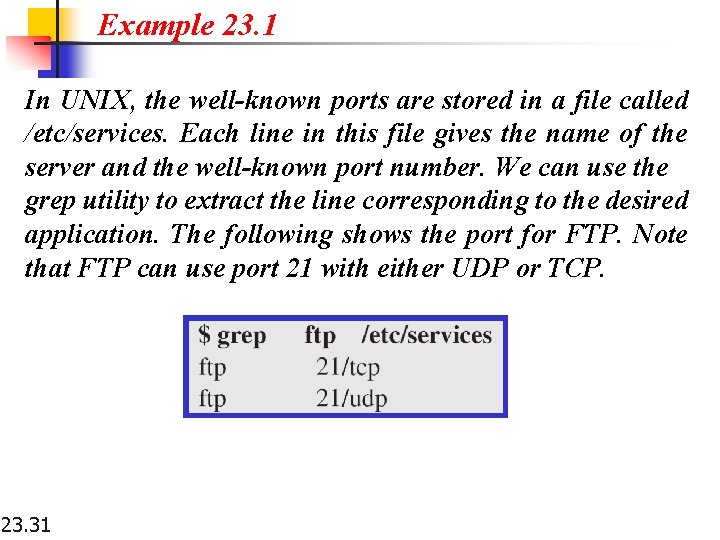
Example 23. 1 In UNIX, the well-known ports are stored in a file called /etc/services. Each line in this file gives the name of the server and the well-known port number. We can use the grep utility to extract the line corresponding to the desired application. The following shows the port for FTP. Note that FTP can use port 21 with either UDP or TCP. 23. 31

Example 23. 1 (continued) SNMP uses two port numbers (161 and 162), each for a different purpose. 23. 32

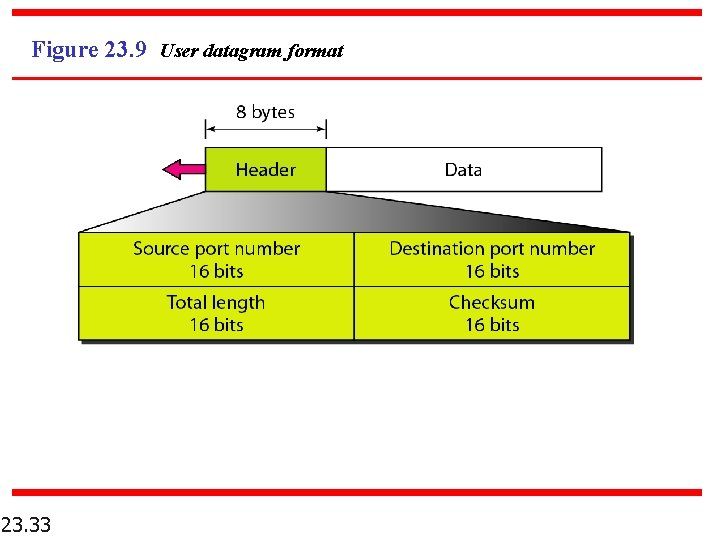
Figure 23. 9 User datagram format 23. 33

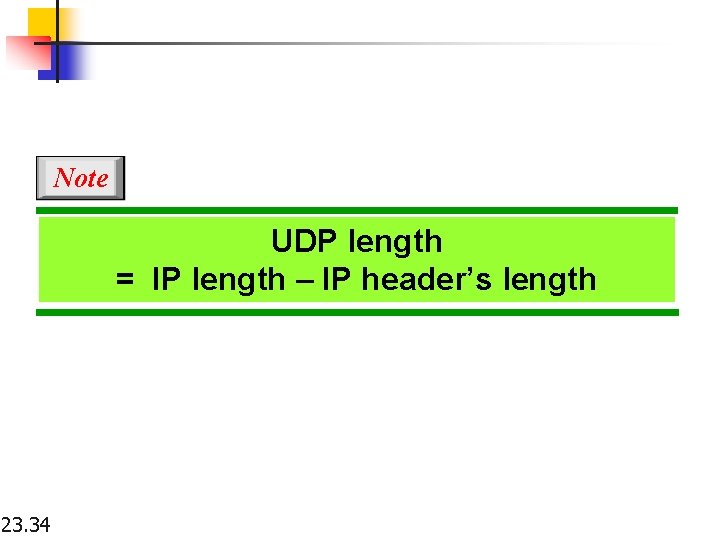
Note UDP length = IP length – IP header’s length 23. 34

Figure 23. 10 Pseudoheader for checksum calculation 23. 35

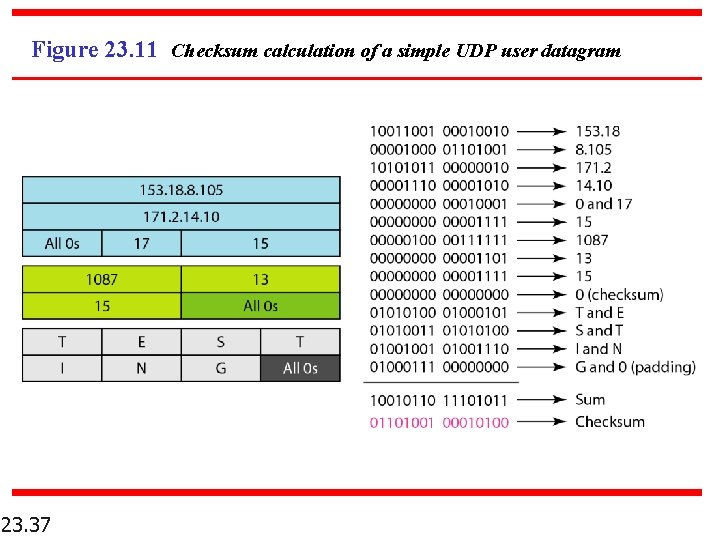
Example 23. 2 Figure 23. 11 shows the checksum calculation for a very small user datagram with only 7 bytes of data. Because the number of bytes of data is odd, padding is added for checksum calculation. The pseudoheader as well as the padding will be dropped when the user datagram is delivered to IP. 23. 36

Figure 23. 11 Checksum calculation of a simple UDP user datagram 23. 37

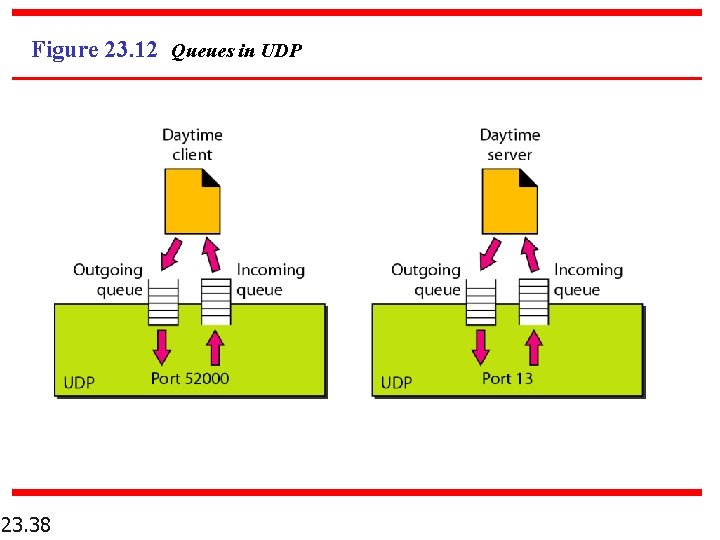
Figure 23. 12 Queues in UDP 23. 38

23 -3 TCP Overview: TCP is a connection-oriented protocol; it creates a virtual connection between two TCPs to send data. In addition, TCP uses flow and error control mechanisms at the transport level. Topics discussed in this section: TCP Services TCP Features Segment A TCP Connection Flow Control Error Control 23. 39

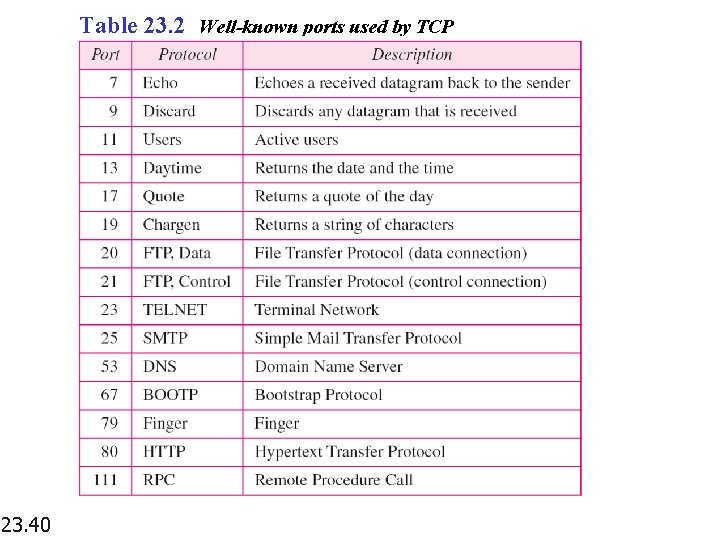
Table 23. 2 Well-known ports used by TCP 23. 40

Figure 23. 13 Stream delivery 23. 41

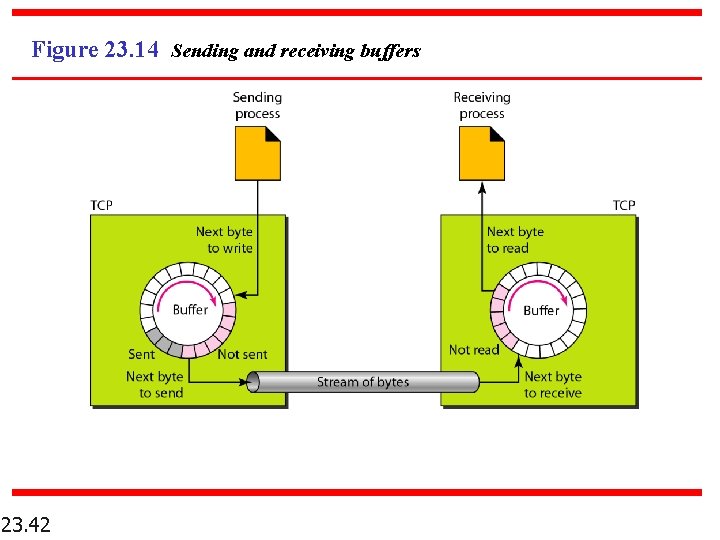
Figure 23. 14 Sending and receiving buffers 23. 42

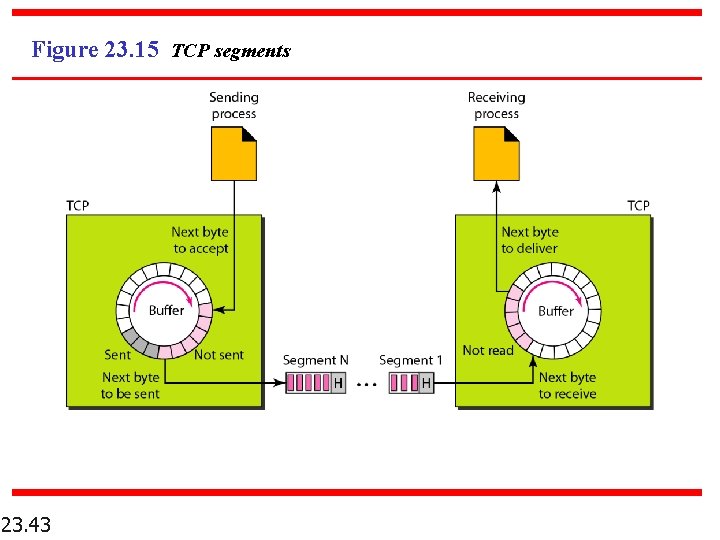
Figure 23. 15 TCP segments 23. 43

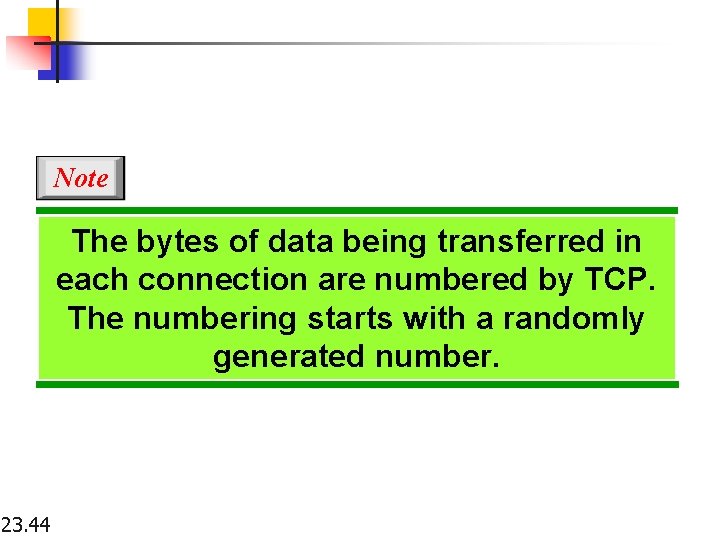
Note The bytes of data being transferred in each connection are numbered by TCP. The numbering starts with a randomly generated number. 23. 44

Example Imagine a TCP connection is transferring a file of 6000 bytes. The first byte is numbered 10, 010. What are the sequence numbers for each segment if data are sent in five segments with the first four segments carrying 1000 bytes and the last segment carrying 2000 bytes? Solution The following shows the sequence number for each segment: Segment 1 ==> sequence number: 10, 010 (range: 10, 010 to 11, 009) Segment 2 ==> sequence number: 11, 010 (range: 11, 010 to 12, 009) Segment 3 ==> sequence number: 12, 010 (range: 12, 010 to 13, 009) Segment 4 ==> sequence number: 13, 010 (range: 13, 010 to 14, 009) Segment 5 ==> sequence number: 14, 010 (range: 14, 010 to 16, 009) 23. 45

Note The value in the sequence number field of a segment defines the number of the first data byte contained in that segment. 23. 46

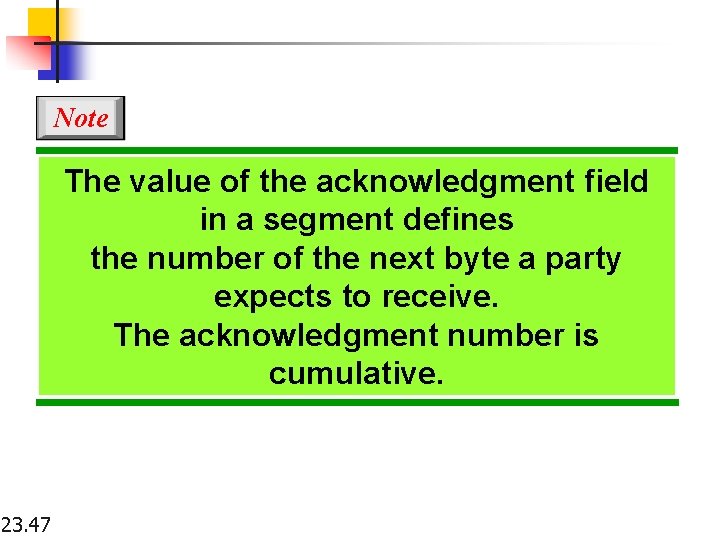
Note The value of the acknowledgment field in a segment defines the number of the next byte a party expects to receive. The acknowledgment number is cumulative. 23. 47

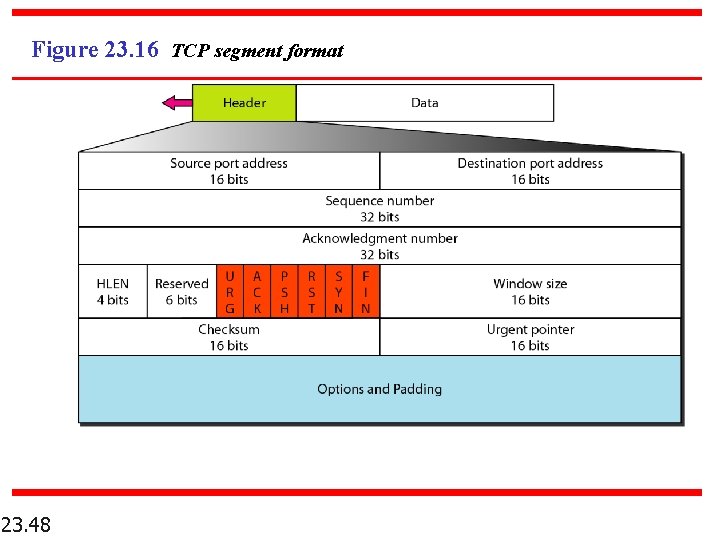
Figure 23. 16 TCP segment format 23. 48

Header fields 23. 49 q Source port address: A 16 -bit value that defines the port number of the application program in the host that is sending the segment q Destination port address: A 16 -bit value that defines the port number of the application program in the host that is receiving the segment q Sequence number: A 32 -bit value that defines the number assigned to the first byte of data contained in this segment q Acknowledge number: A 16 -bit value that defines the byte number that the sender of the segment is expecting to receive from the other party q Header length: A 4 -bit value that indicates the number of 4 -byte words in the TCP header q Reserved: A 6 -bit field reserved for future use q Control: A 6 -bit field that defines 6 different control bits or flags, as shown in figure 22. 15

Header fields (cont. ) q Window size: A 16 -bit value in bytes that the other party must maintain q Checksum: A 16 -bit checksum; its calculation follows the UDP procedure q Urgent pointer: A 16 -bit value, which is valid only if the urgent flag is set, is used when the segment contains urgent data q Options: There can be up to 40 bytes of optional information in the TCP header 23. 50

Figure 23. 17 Control field 23. 51

Table 23. 3 Description of flags in the control field 23. 52

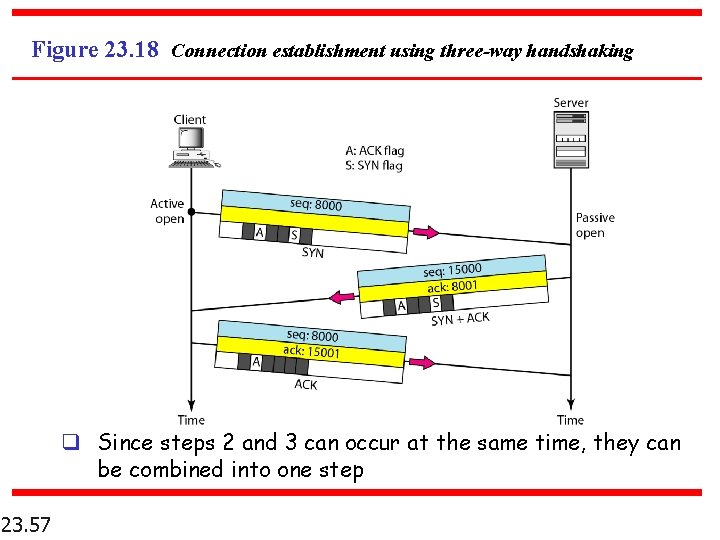
The TCP three-way handshake process n n n 23. 53 : Host A sends a TCP packet with the SYN flag set (that is, a SYN packet) to Host B. After receiving the packet, Host B sends Host A its own SYN packet with an ACK flag (a SYN-ACK packet) set. In response to the SYN-ACK packet from Host B, Host A sends Host B a TCP packet with the ACK flag set (an ACK packet).

TCP SEGMENT HEADERS n n 23. 54 As an IT professional, it is important for you to clearly understand the critical components of a TCP header. Hackers usually try to exploit these components to discover vulnerabilities and perform attacks. Critical components include: TCP flags Initial Sequence Number (ISN) Source and destination port

Initial Sequence Number (ISN) n n 23. 55 Let’s define ISN as a 32 -bit number that tracks the packets received by the node and enables the reassembly of large packets that have been broken up into smaller packets. Two hosts exchange their ISNs during steps 1 and 2 of the TCP three-way handshake.

Note of Interest n 23. 56 Kevin Mitnick, the legendary hacker, is now a security consultant to corporations worldwide and a cofounder of Defensive Thinking. Find out more about him at http: //en. wikipedia. org/wiki/Kevin_Mitnick

Figure 23. 18 Connection establishment using three-way handshaking q Since steps 2 and 3 can occur at the same time, they can be combined into one step 23. 57

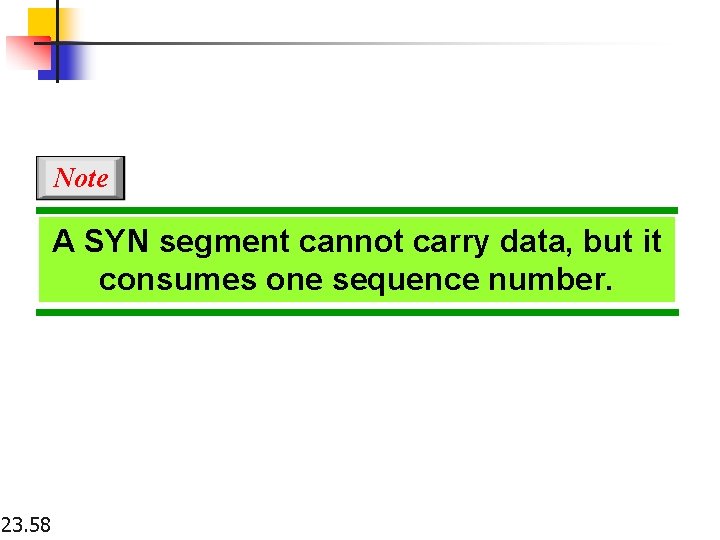
Note A SYN segment cannot carry data, but it consumes one sequence number. 23. 58

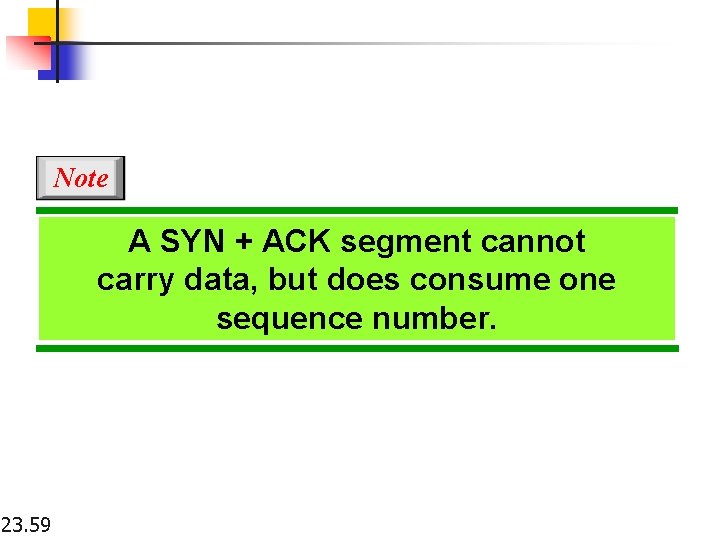
Note A SYN + ACK segment cannot carry data, but does consume one sequence number. 23. 59

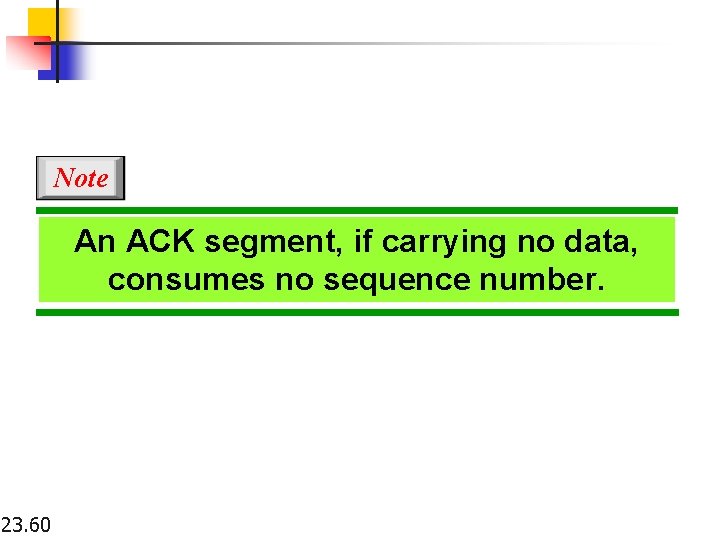
Note An ACK segment, if carrying no data, consumes no sequence number. 23. 60

SYN Flooding n 23. 61 The connection establishment procedure in TCP is susceptible to a serious security problem called the SYN flooding attack.

23. 62

SYN Flooding n n 23. 63 The TCP server then sends the SYN + ACK segments to the fake clients, which are lost. During this time, however, a lot of resources are occupied without being used. If, during this short time, the number of SYN segments is large, the server eventually runs out of resources and may crash. This SYN flooding attack belongs to a type of security attack known as a denial-of-service attack, in which an attacker monopolizes a system with so many service requests that the system collapses and denies service to every request.

SYN Flooding n n n 23. 64 Some implementations of TCP have strategies to alleviate the effects of a SYN attack. Some have imposed a limit on connection requests during a specified period of time. Others filter out datagrams coming from unwanted source addresses. One recent strategy is to postpone resource allocation until the entire connection is set up, using what is called a cookie. SCTP, the new transport layer protocol that we discuss in the next section, uses this strategy.

Figure 23. 19 Data transfer 23. 65

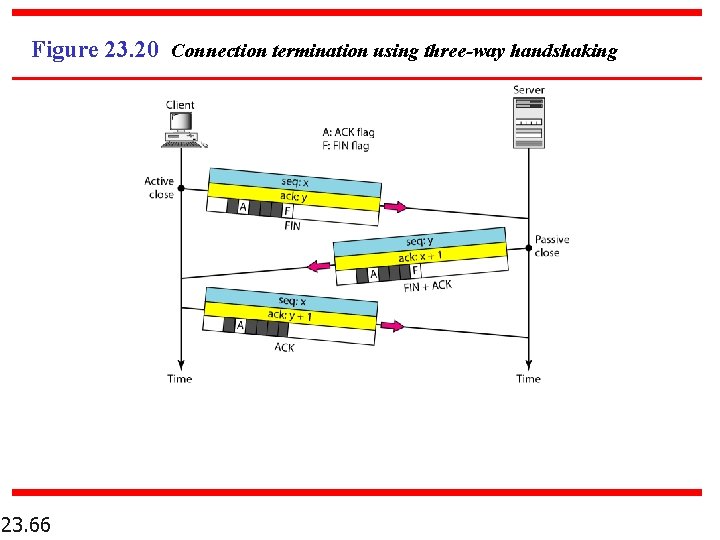
Figure 23. 20 Connection termination using three-way handshaking 23. 66

Note The FIN segment consumes one sequence number if it does not carry data. 23. 67

Note The FIN + ACK segment consumes one sequence number if it does not carry data. 23. 68

Structure of the OSI Reference Model (continued) 23. 69

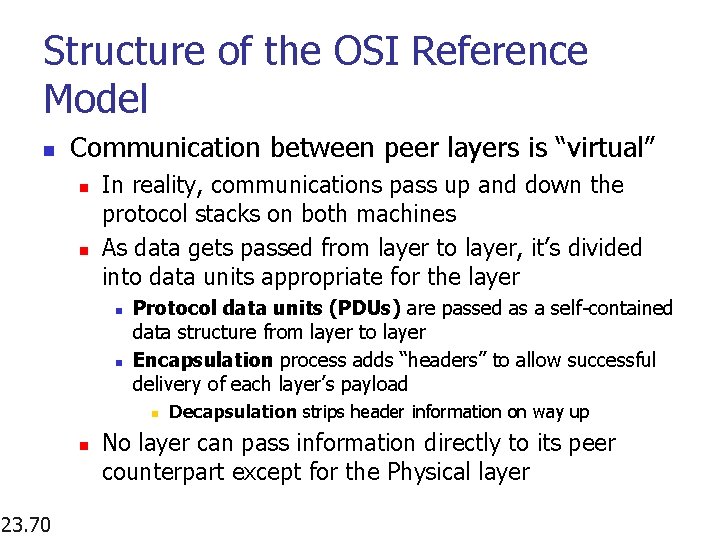
Structure of the OSI Reference Model n Communication between peer layers is “virtual” n n In reality, communications pass up and down the protocol stacks on both machines As data gets passed from layer to layer, it’s divided into data units appropriate for the layer n n Protocol data units (PDUs) are passed as a self-contained data structure from layer to layer Encapsulation process adds “headers” to allow successful delivery of each layer’s payload n n 23. 70 Decapsulation strips header information on way up No layer can pass information directly to its peer counterpart except for the Physical layer

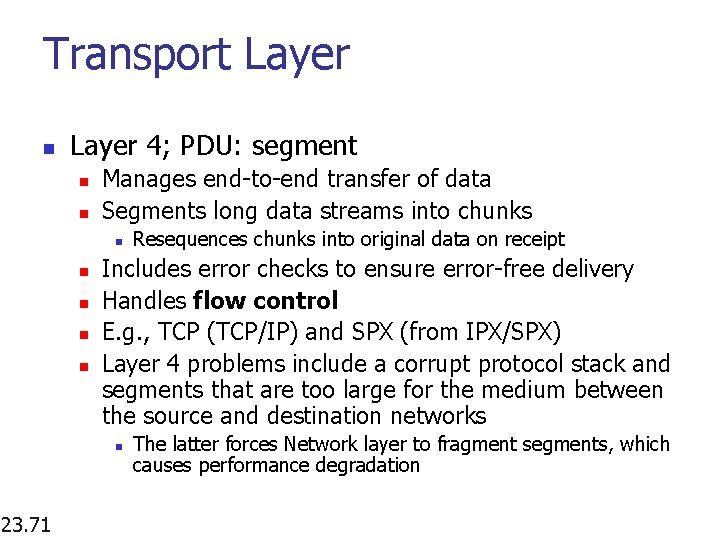
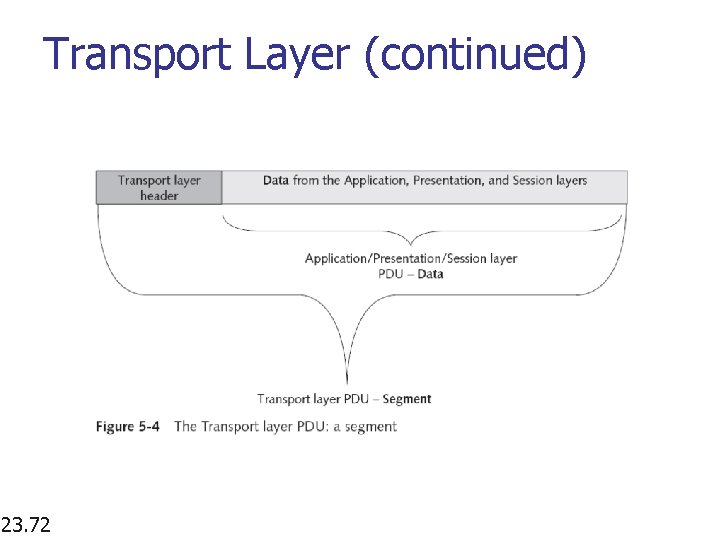
Transport Layer n Layer 4; PDU: segment n n Manages end-to-end transfer of data Segments long data streams into chunks n n n Includes error checks to ensure error-free delivery Handles flow control E. g. , TCP (TCP/IP) and SPX (from IPX/SPX) Layer 4 problems include a corrupt protocol stack and segments that are too large for the medium between the source and destination networks n 23. 71 Resequences chunks into original data on receipt The latter forces Network layer to fragment segments, which causes performance degradation

Transport Layer (continued) 23. 72

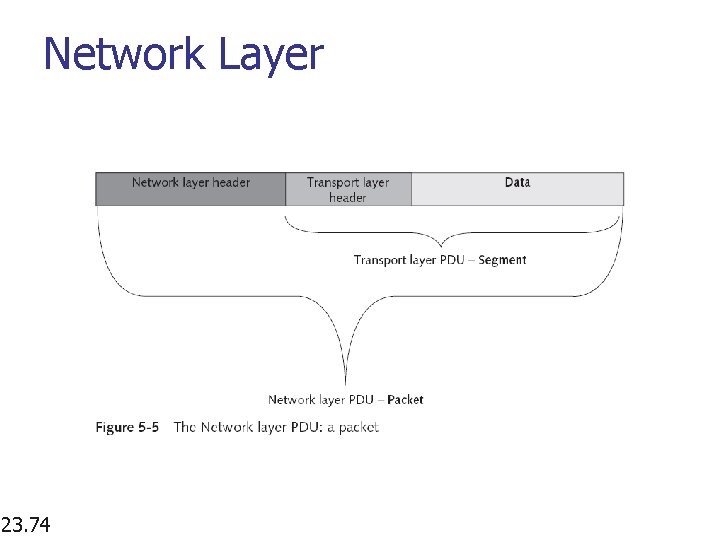
Network Layer n Layer 3; PDU: packet n n n 23. 73 Handles addressing messages for delivery Translates logical addresses into physical addresses Determines how to route transmissions from sender to receiver (routing process) Traffic cop for network activity and handles routing and access control (during routing process) E. g. , IP (from TCP/IP) and IPX (from SPX/IPX) Possible problems: incorrect IP addresses or subnet masks, incorrect router configuration, and router operation errors

Network Layer 23. 74

Understanding Types of Data Frames n Unicast frame: addressed to only one computer n n Broadcast frame: created for all computers on a network n n Destination address is a value of all binary 1 s Multicast frame: created for any computers on a network that “listen” to a shared network address n 23. 75 Adapters read the frames and pass them to higher layers only if the destination address in the frame header matches their own address A special kind of address allows any interested receiver to read these data streams

Connectionless Versus Connection. Oriented Protocols n Protocols that use connectionless delivery place data on the network and assume it will get through n n n Connectionless protocols aren’t entirely reliable Are fast: little overhead, don’t waste time establishing/managing/tearing down connections Connection-oriented protocols are more reliable and, consequently, slower n Two computers establish a connection before data transfer begins n n 23. 76 In a connection, data is sent in an orderly fashion Ensures that all data is received and is accurate, or that suitable error messages are generated

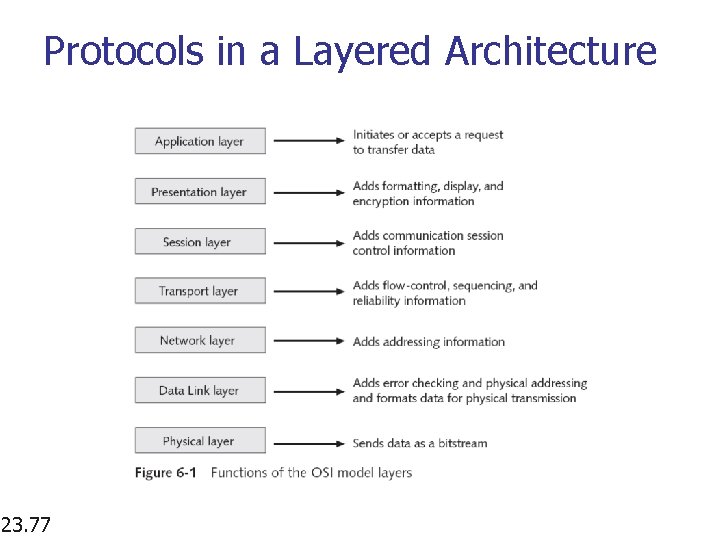
Protocols in a Layered Architecture 23. 77

Transport Protocols n Transport protocols can be connectionoriented (reliable) or connectionless (best-effort) delivery n Transmission Control Protocol (TCP) n n Sequential Packet Exchange (SPX) n n Novell’s connection-oriented protocol used to guarantee data delivery Net. BIOS/Net. BEUI n n 23. 78 Responsible for reliable data delivery in TCP/IP Net. BIOS establishes/manages communications between computers and provides naming services Net. BEUI provides data transport services for these communications

TCP/IP Network Layer Protocols n Internet Protocol version 4 (IPv 4) is a Network layer protocol that provides source and destination addressing and routing for the TCP/IP suite n n Internet Control Message Protocol (ICMP) is a Network layer protocol used to send error and control messages between systems or devices n n 23. 79 Connectionless protocol; fast but unreliable The Ping utility uses ICMP to request a response from a remote host to verify availability Address Resolution Protocol (ARP) resolves logical (IP) addresses to physical (MAC) addresses

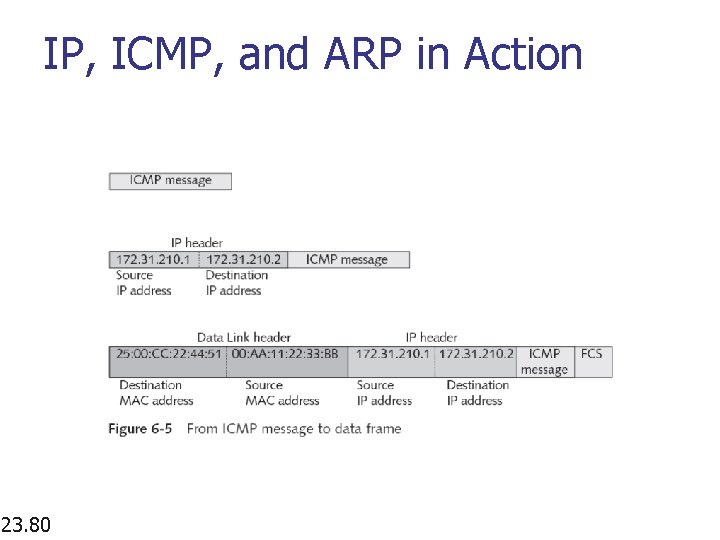
IP, ICMP, and ARP in Action 23. 80

TCP/IP Transport Layer Protocols n Transmission Control Protocol (TCP) is the primary Internet transport protocol n n Connection oriented using a three-way handshake Message fragmentation and reassembly Uses acknowledgements to ensure that all data was received and to provide flow control User Datagram Protocol (UDP) is connectionless n Generally faster, although less reliable, than TCP n n n 23. 81 Doesn’t segment data or resequence packets Doesn’t use acknowledgements for reliability Used by NFS and DNS

TCP/IP Application Layer Protocols n Domain Name System (DNS) n n Hypertext Transport Protocol (HTTP) n n Remote terminal emulation; operates at layers 7 -5 Simple Mail Transport Protocol (SMTP) n 23. 82 For file transfer and directory and file manipulation Telnet n n To transfer Web pages from Web server to browser File Transfer Protocol (FTP) n n Session layer name-to-address resolution protocol Operates at layers 7 -5; provides messaging services

Flow Control n 23. 83 TCP uses a sliding window, as discussed in Chapter 11, to handle flow control.

Figure 23. 22 Sliding window 23. 84

Note A sliding window is used to make transmission more efficient as well as to control the flow of data so that the destination does not become overwhelmed with data. TCP sliding windows are byte-oriented. 23. 85

Note: n 23. 86 The size of the window at one end is determined by the lesser of two values: receiver window (rwnd) or congestion window (cwnd). The receiver window is the value advertised by the opposite end in a segment containing acknowledgement.

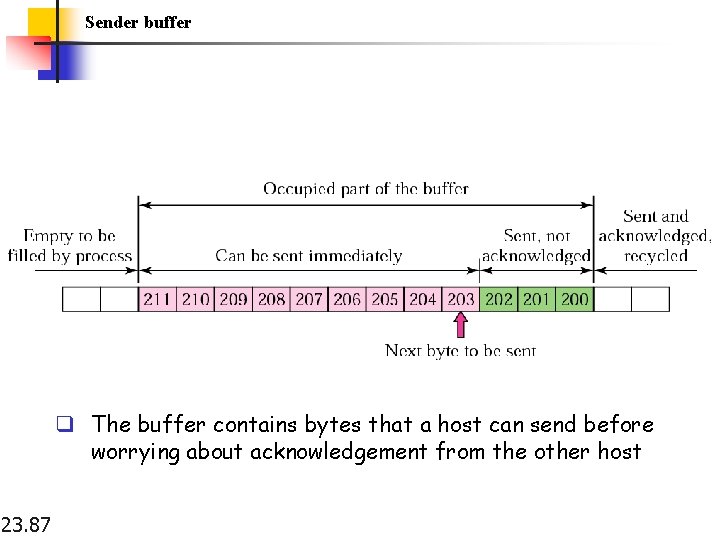
Sender buffer q The buffer contains bytes that a host can send before worrying about acknowledgement from the other host 23. 87

Receiver window q The receiver window establishes how many bytes the receiver can store 23. 88

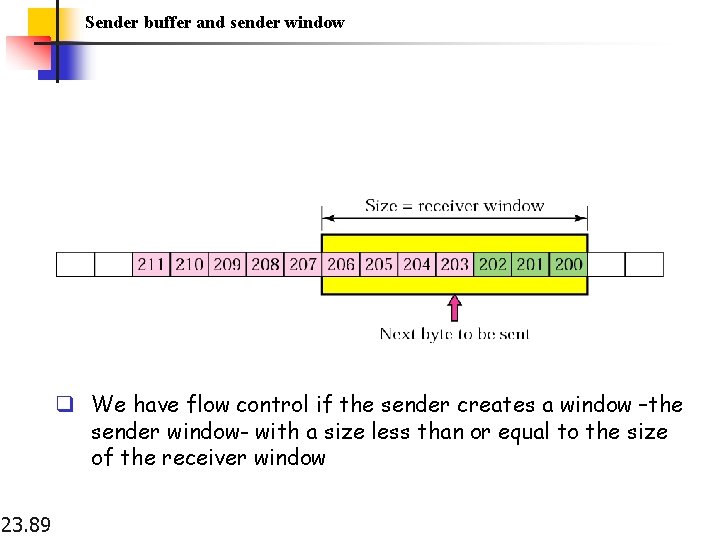
Sender buffer and sender window q We have flow control if the sender creates a window –the sender window- with a size less than or equal to the size of the receiver window 23. 89

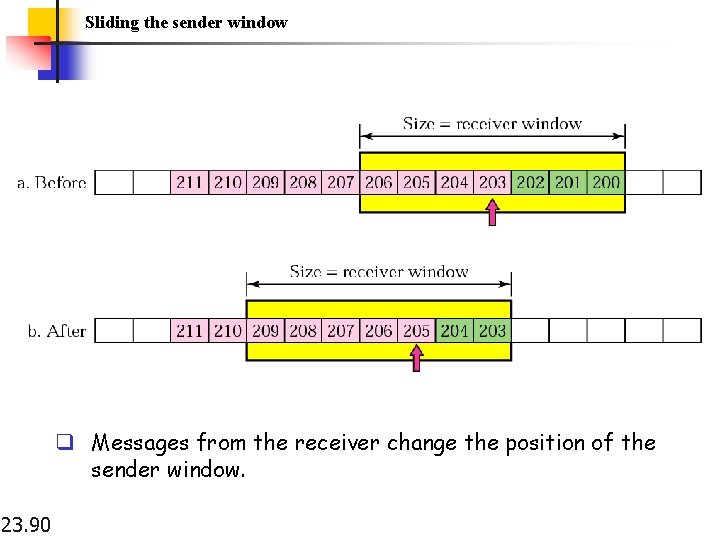
Sliding the sender window q Messages from the receiver change the position of the sender window. 23. 90

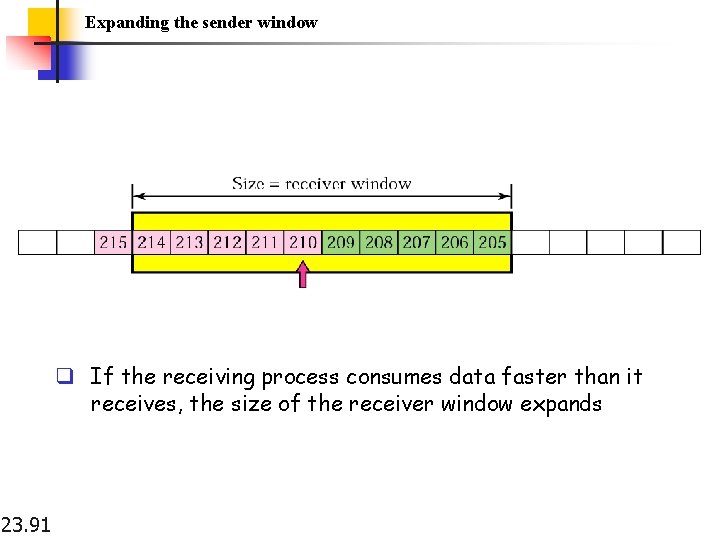
Expanding the sender window q If the receiving process consumes data faster than it receives, the size of the receiver window expands 23. 91

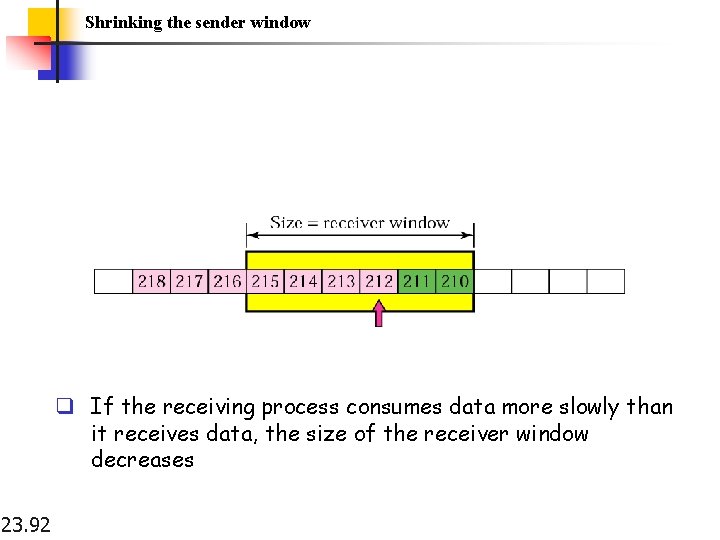
Shrinking the sender window q If the receiving process consumes data more slowly than it receives data, the size of the receiver window decreases 23. 92

Example 23. 4 What is the value of the receiver window (rwnd) for host A if the receiver, host B, has a buffer size of 5000 bytes and 1000 bytes of received and unprocessed data? Solution The value of rwnd = 5000 − 1000 = 4000. Host B can receive only 4000 bytes of data before overflowing its buffer. Host B advertises this value in its next segment to A. 23. 93

Example 23. 5 What is the size of the window for host A if the value of rwnd is 3000 bytes and the value of cwnd is 3500 bytes? Solution The size of the window is the smaller of rwnd and cwnd, which is 3000 bytes. 23. 94

Example 23. 6 Figure 23. 23 (next slide) shows an unrealistic example of a sliding window. The sender has sent bytes up to 202. We assume that cwnd is 20 (in reality this value is thousands of bytes). The receiver has sent an acknowledgment number of 200 with an rwnd of 9 bytes (in reality this value is thousands of bytes). The size of the sender window is the minimum of rwnd and cwnd, or 9 bytes. Bytes 200 to 202 are sent, but not acknowledged. Bytes 203 to 208 can be sent without worrying about acknowledgment. Bytes 209 and above cannot be sent. 23. 95

Figure 23. 23 Example 23. 6 23. 96

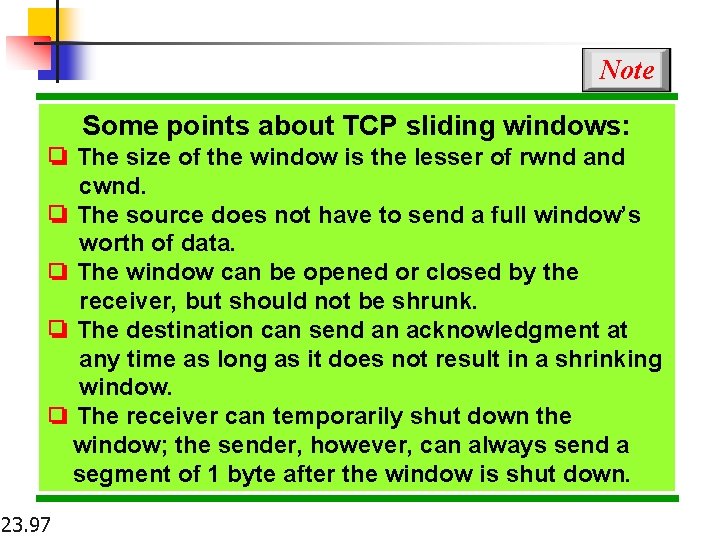
Note Some points about TCP sliding windows: ❏ The size of the window is the lesser of rwnd and cwnd. ❏ The source does not have to send a full window’s worth of data. ❏ The window can be opened or closed by the receiver, but should not be shrunk. ❏ The destination can send an acknowledgment at any time as long as it does not result in a shrinking window. ❏ The receiver can temporarily shut down the window; the sender, however, can always send a segment of 1 byte after the window is shut down. 23. 97

Error Control TCP is a reliable transport layer protocol. n This means that an application program that delivers a stream of data to TCP relies on TCP to deliver the entire stream to the application program on the other end in order, without error, and without any part lost or duplicated n 23. 98

TCP uses acknowledgements to conform the receipt of data segments. Control segments that carry no data but consume a sequence number are also acknowledged. Note ACK segments do not consume sequence numbers and are not acknowledged. 23. 99

The heart of the error control mechanism is the retransmission of segments. When a segment is corrupted, lost, or delayed, it is retransmitted. Note In modern implementations, a retransmission occurs if the retransmission timer expires or three duplicate ACK segments have arrived. 23. 100

Note that no retransmission occurs of segments that do not consume sequence numbers. In particular, there is no transmission for an ACK segment. Note No retransmission timer is set for an ACK segment. 23. 101

Out-of-order segments: Note Data may arrive out of order and be temporarily stored by the receiving TCP, but TCP guarantees that no out-of-order segment is delivered to the process. 23. 102

Key Terms n n n 23. 103 ACK —A TCP flag that acknowledges a TCP packet with SYN-ACK flags set. connection-oriented —A method of transferring data over a network that requires a session connection before data is sent. With TCP/IP, this step is accomplished by sending a SYN packet. connectionless — With a connectionless protocol, no session connection is required before data is transmitted. UDP and IP are examples of connectionless protocols. initial sequence number (ISN) —A number that keeps track of what packets a node has received. Internet Assigned Numbers Authority (IANA) — The organization responsible for assigning IP addresses.

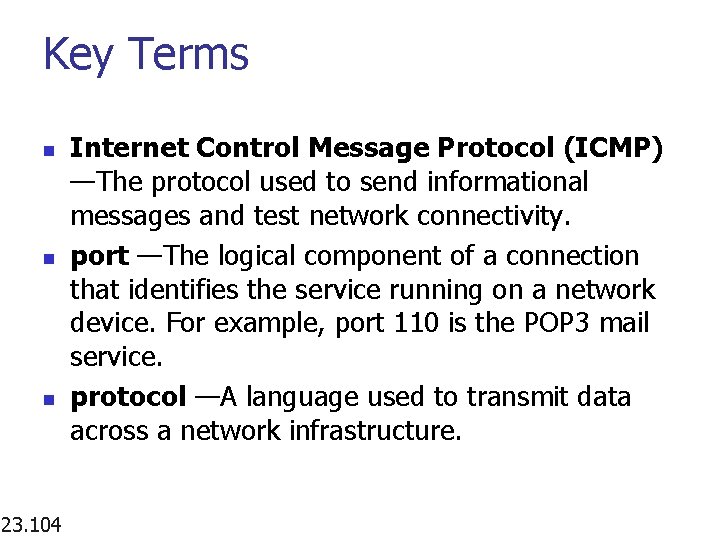
Key Terms n n n 23. 104 Internet Control Message Protocol (ICMP) —The protocol used to send informational messages and test network connectivity. port —The logical component of a connection that identifies the service running on a network device. For example, port 110 is the POP 3 mail service. protocol —A language used to transmit data across a network infrastructure.

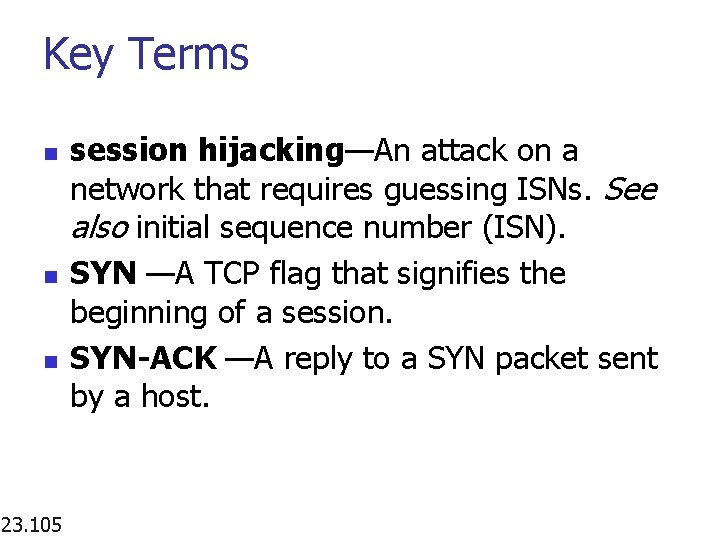
Key Terms n n n 23. 105 session hijacking—An attack on a network that requires guessing ISNs. See also initial sequence number (ISN). SYN —A TCP flag that signifies the beginning of a session. SYN-ACK —A reply to a SYN packet sent by a host.

Key Terms n n 23. 106 TCP flag —The six flags in a TCP header are switches that can be set to on or off to indicate the status of a port or service. three-way handshake —The method the transport layer uses to create a connection-oriented session.

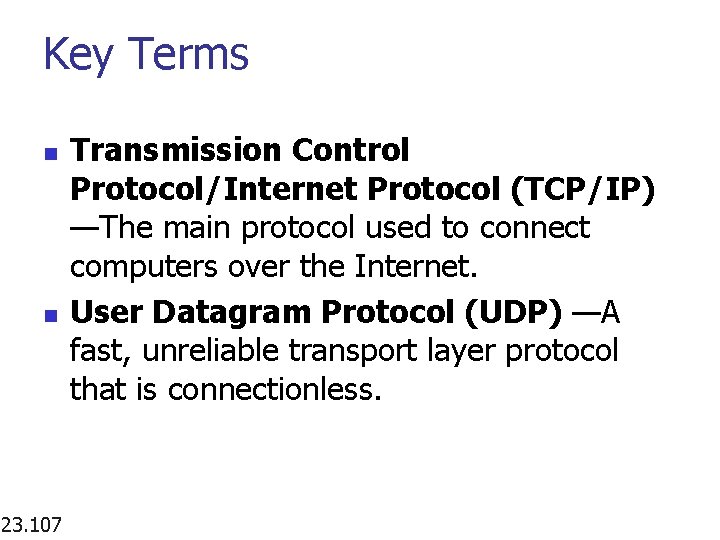
Key Terms n n 23. 107 Transmission Control Protocol/Internet Protocol (TCP/IP) —The main protocol used to connect computers over the Internet. User Datagram Protocol (UDP) —A fast, unreliable transport layer protocol that is connectionless.

23 -4 SCTP Overview: Stream Control Transmission Protocol (SCTP) is a new reliable, message-oriented transport layer protocol. SCTP, however, is mostly designed for Internet applications that have recently been introduced. These new applications need a more sophisticated service than TCP can provide. Topics discussed in this section: SCTP Services and Features Packet Format An SCTP Association Flow Control and Error Control 23. 108

UDP is a message-oriented protocol. A process delivers a message to UDP, which is encapsulated in a user datagram and sent over the network. n UDP conserves the message boundaries; each message is independent of any other message. n 23. 109

TCP is a byte-oriented protocol. n It receives a message or messages from a process, stores them as a stream of bytes, and sends them in segments. n 23. 110

SCTP n 23. 111 SCTP combines the best features of UDP and TCP. SCTP is a reliable messageoriented protocol

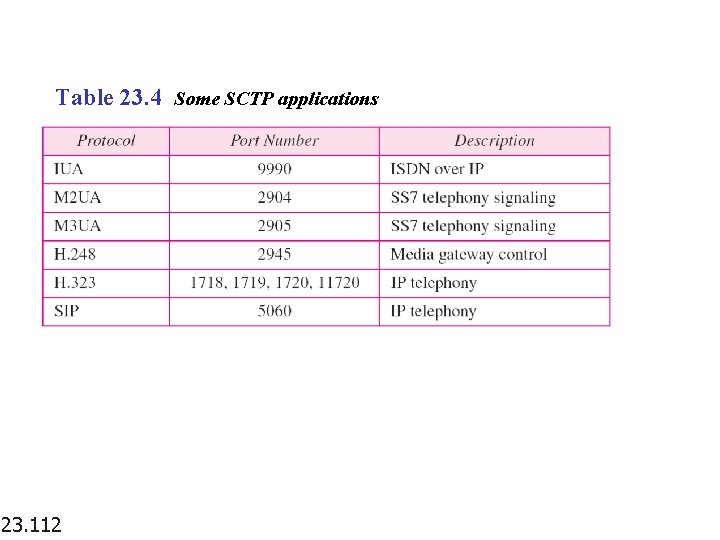
Table 23. 4 Some SCTP applications 23. 112

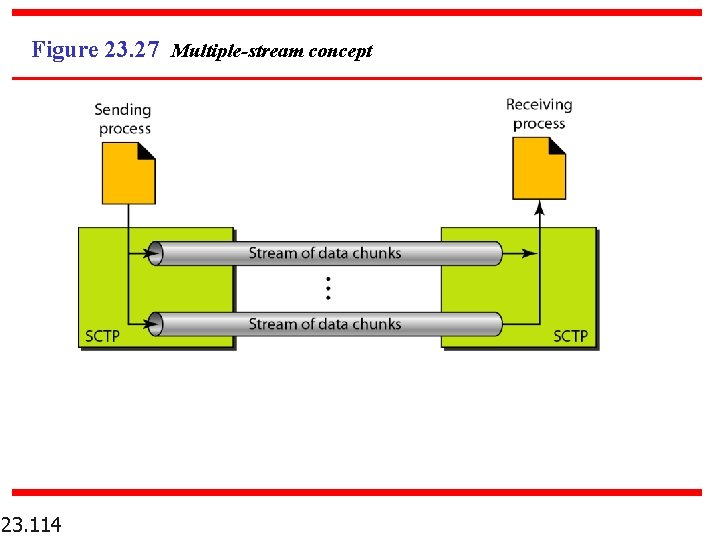
Note An association in SCTP can involve multiple streams. 23. 113

Figure 23. 27 Multiple-stream concept 23. 114

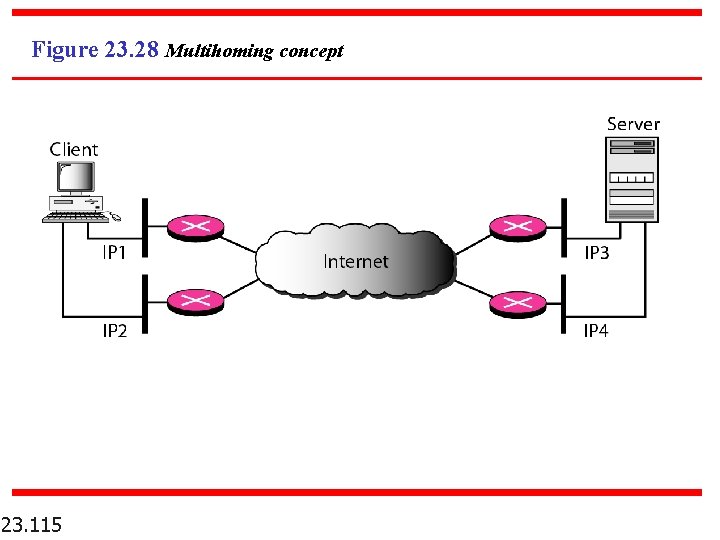
Figure 23. 28 Multihoming concept 23. 115

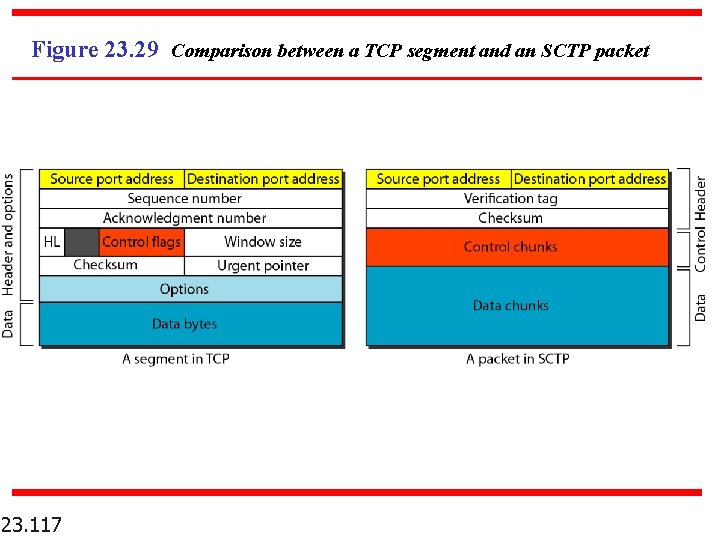
SCTP “Packets” n 23. 116 Data are carried as data chunks, control information is carried as control chunks.

Figure 23. 29 Comparison between a TCP segment and an SCTP packet 23. 117

SCTP “Packets” Steps 1 through 8 – p. 739 -740. 23. 118

SCTP “Packets” Steps 1 through 8 – p. 739 -740. 23. 119

SCTP “Packets” Steps 1 through 8 – p. 739 -740. 23. 120

Note SCTP association allows multiple IP addresses for each end. 23. 121

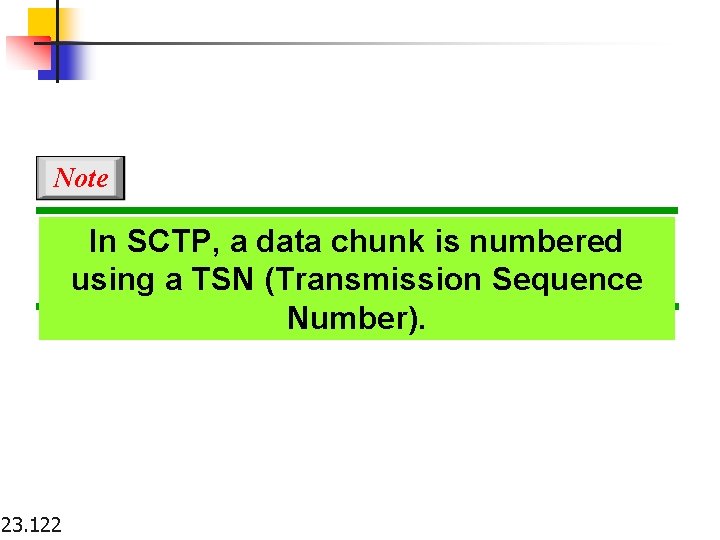
Note In SCTP, a data chunk is numbered using a TSN (Transmission Sequence Number). 23. 122

Note To distinguish between different streams, SCTP uses an SI (Stream Identifier). 23. 123

Note To distinguish between different data chunks belonging to the same stream, SCTP uses SSNs (Stream Sequence Numbers). 23. 124

Note TCP has segments; SCTP has packets. 23. 125

Note In SCTP, control information and data information are carried in separate chunks. 23. 126

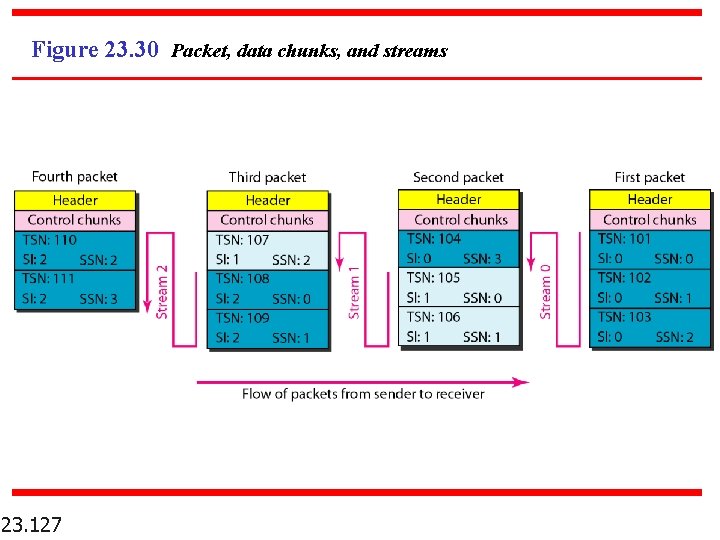
Figure 23. 30 Packet, data chunks, and streams 23. 127

Note Data chunks are identified by three items: TSN, SI, and SSN. TSN is a cumulative number identifying the association; SI defines the stream; SSN defines the chunk in a stream. TSN = Transmission Sequence Number SI = Stream Identifier SSN = Stream Sequence Number 23. 128

Note In SCTP, acknowledgment numbers are used to acknowledge only data chunks; control chunks are acknowledged by other control chunks if necessary. 23. 129

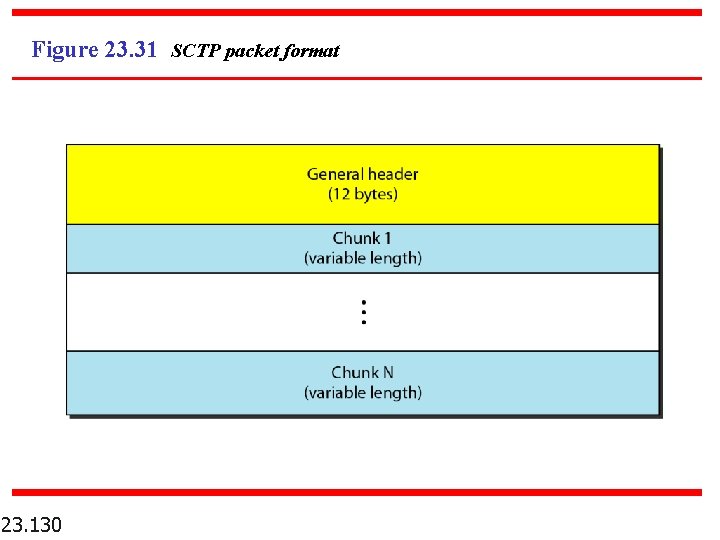
Figure 23. 31 SCTP packet format 23. 130

Note In an SCTP packet, control chunks come before data chunks. 23. 131

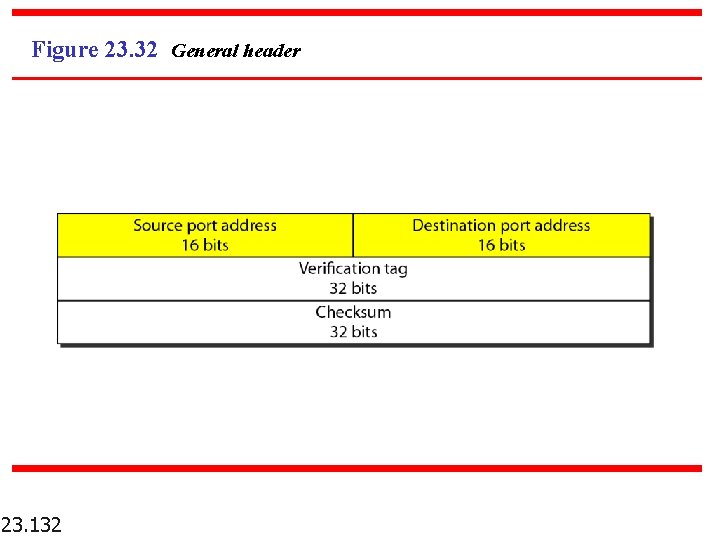
Figure 23. 32 General header 23. 132

Table 23. 5 Chunks 23. 133

Note A connection in SCTP is called an association. 23. 134

Note No other chunk is allowed in a packet carrying an INIT or INIT ACK chunk. A COOKIE ECHO or a COOKIE ACK chunk can carry data chunks. 23. 135

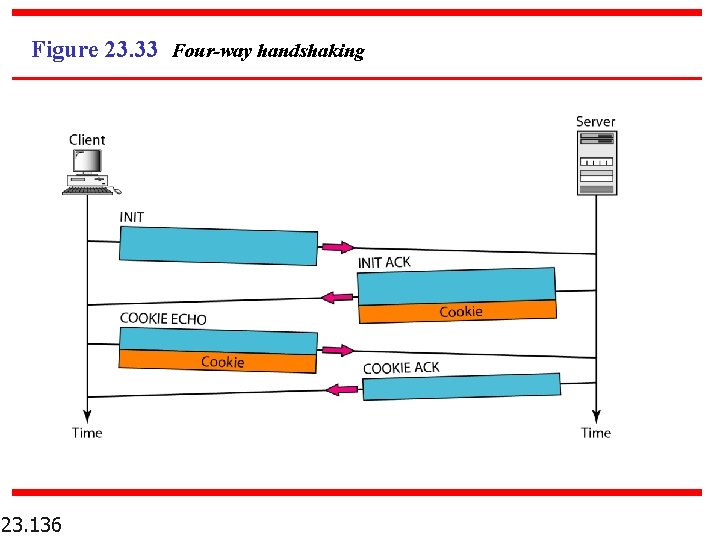
Figure 23. 33 Four-way handshaking 23. 136

Note In SCTP, only DATA chunks consume TSNs; DATA chunks are the only chunks that are acknowledged. 23. 137

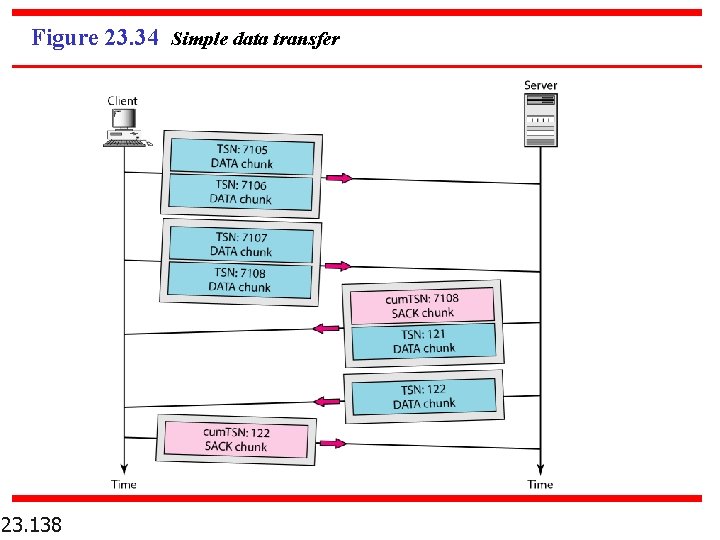
Figure 23. 34 Simple data transfer 23. 138

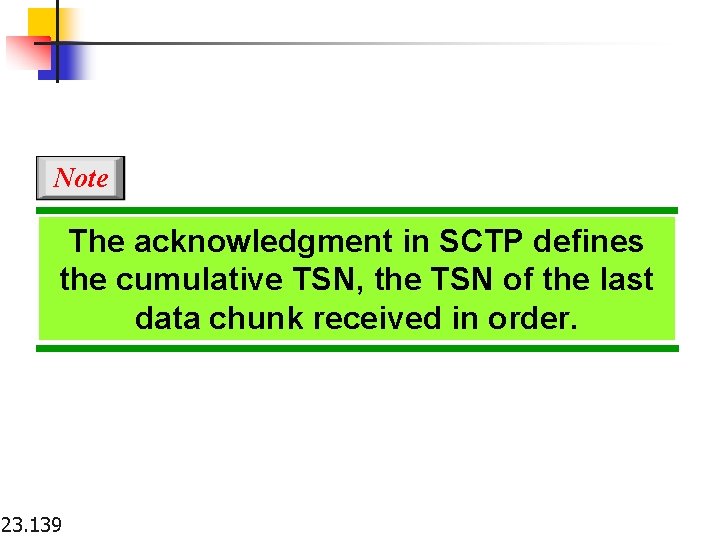
Note The acknowledgment in SCTP defines the cumulative TSN, the TSN of the last data chunk received in order. 23. 139

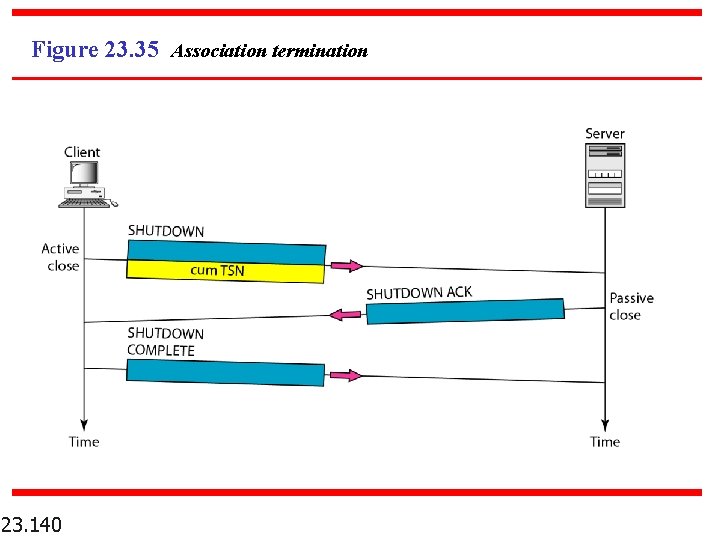
Figure 23. 35 Association termination 23. 140

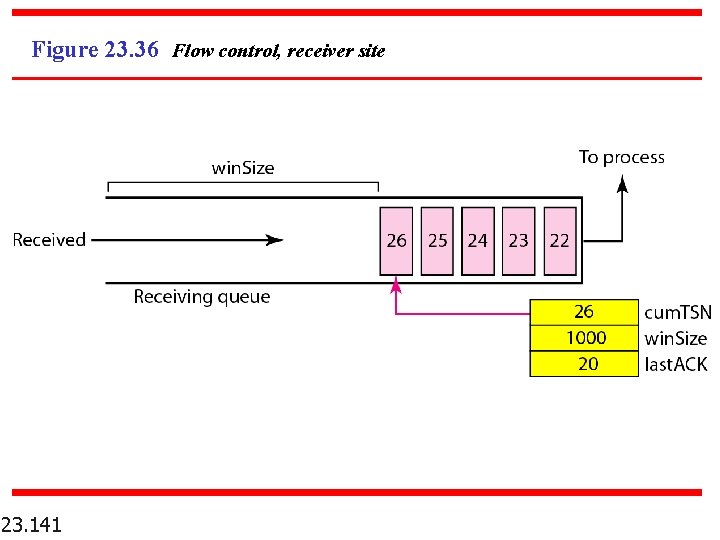
Figure 23. 36 Flow control, receiver site 23. 141

Figure 23. 37 Flow control, sender site 23. 142

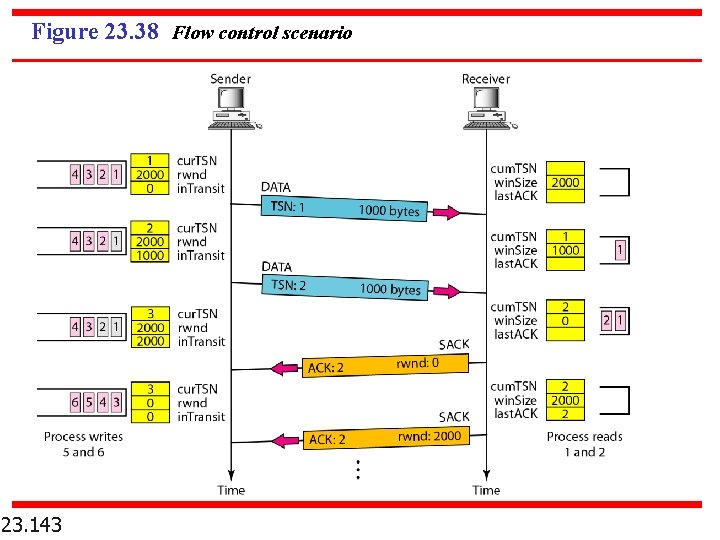
Figure 23. 38 Flow control scenario 23. 143

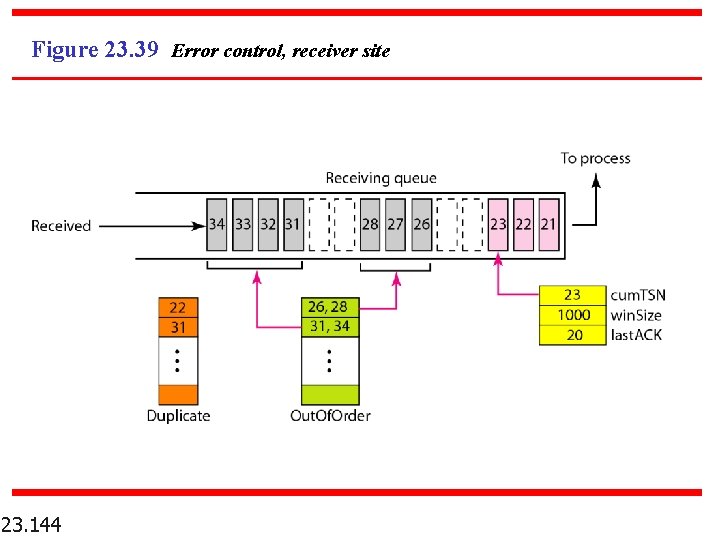
Figure 23. 39 Error control, receiver site 23. 144

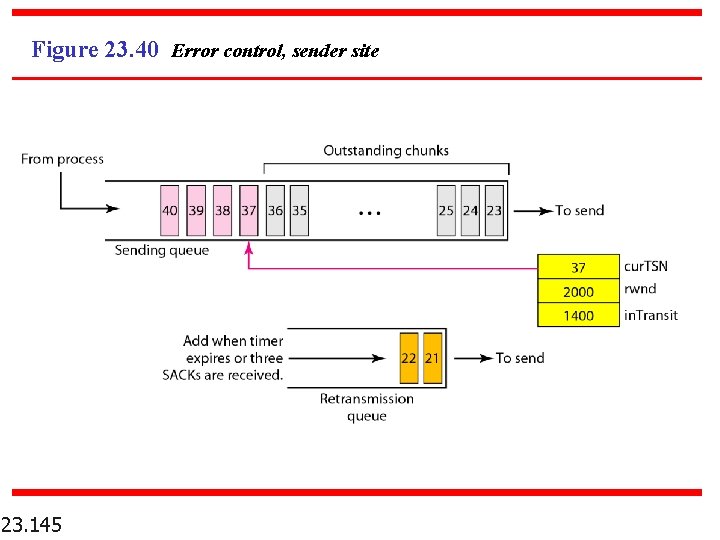
Figure 23. 40 Error control, sender site 23. 145