The User Datagram Protocol UDP IP delivers a
















- Slides: 29

The User Datagram Protocol (UDP) • IP delivers a datagram from one machine to another – Parallel: delivering a letter to a house • UDP delivers a message to a given program on a machine – Parallel: delivering a letter to one of the occupants of a house

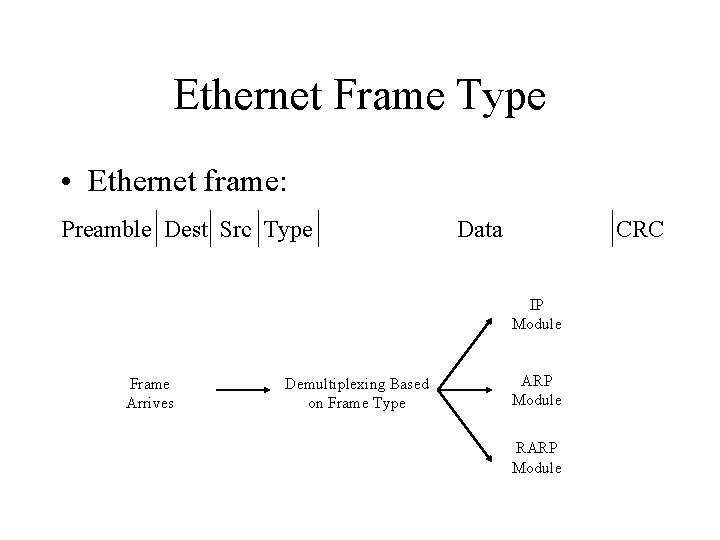
Ethernet Frame Type • Ethernet frame: Preamble Dest Src Type Data CRC IP Module Frame Arrives Demultiplexing Based on Frame Type ARP Module RARP Module

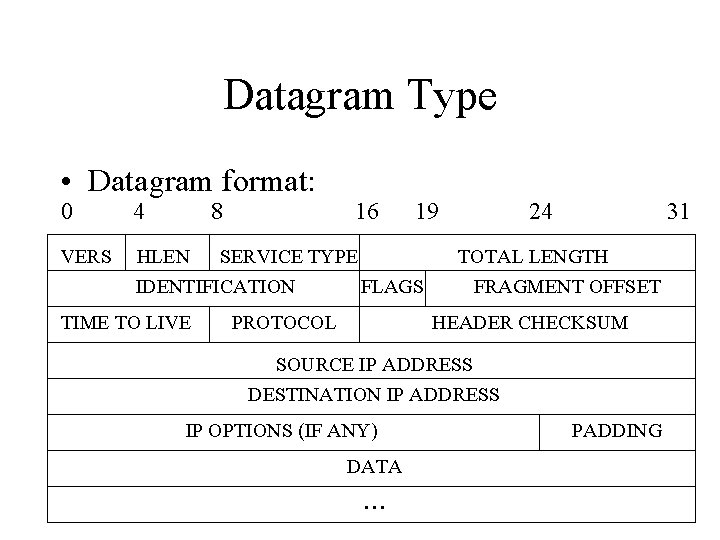
Datagram Type • Datagram format: 0 4 8 VERS HLEN 19 SERVICE TYPE IDENTIFICATION TIME TO LIVE 16 24 31 TOTAL LENGTH FLAGS PROTOCOL FRAGMENT OFFSET HEADER CHECKSUM SOURCE IP ADDRESS DESTINATION IP ADDRESS IP OPTIONS (IF ANY) DATA . . . PADDING

Datagram Type (cont) TCP Module Datagram Arrives Demultiplexing Based on Datagram Type UDP Module ICMP Module

The User Datagram Protocol (UDP) • IP datagram header identifies a destination host • How does the host determine which user/application program gets the datagram once it arrives? • UDP provides a mechanism to distinguish among multiple destinations within a given host

The Ultimate Destination of a Datagram • Simple answer: a process – Sender probably doesn’t know destination’s pid – Would like to be able to contact a process even if it’s pid has changed – Sender probably only knows the name of the function (not the process) – One process can provide multiple functions

The Ultimate Destination of a Datagram • Real answer: protocol ports – Ports identified by positive integers – Operating system provides processes with interface mechanisms for the ports • Basic functions (open, close, read, write) • Blocking • Buffering

Communicating with Ports • Sender needs to know: – IP address of the destination machine – Port number (on the destination machine) of the desired service • Each message contains: – Destination IP address and port number – Sender IP address and port number

The User Datagram Protocol (UDP) • Transport layer internetworking protocol – Uses IP to transport messages • Used by application programs to send messages to other application programs • Uses ports to distinguish among multiple programs executing on the destination machine

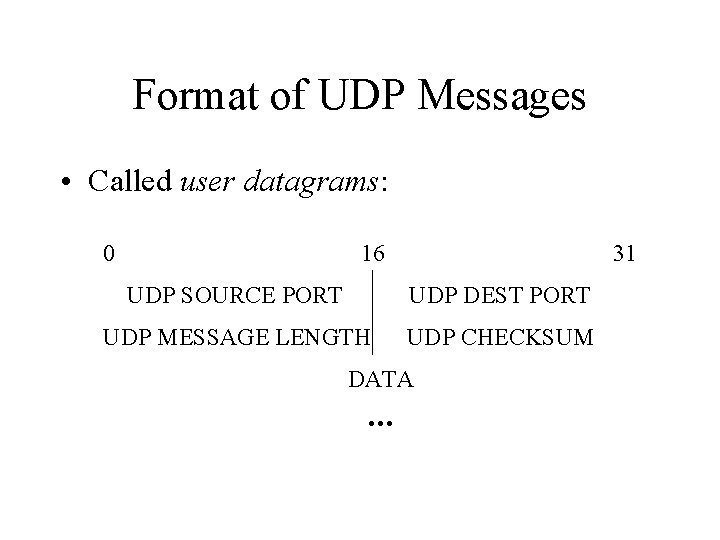
Format of UDP Messages • Called user datagrams: 0 16 31 UDP SOURCE PORT UDP DEST PORT UDP MESSAGE LENGTH UDP CHECKSUM DATA . . .

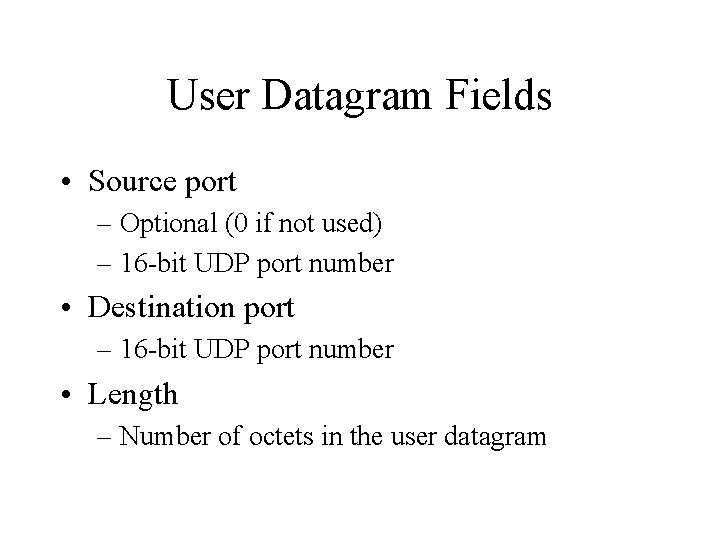
User Datagram Fields • Source port – Optional (0 if not used) – 16 -bit UDP port number • Destination port – 16 -bit UDP port number • Length – Number of octets in the user datagram

User Datagram Fields (cont) • Checksum – Optional (0 if not used) – Provides some reliability (IP won’t) – Uses the same checksum algorithm as IP • 1’s complement addition • What happens if the computed checksum is 0?

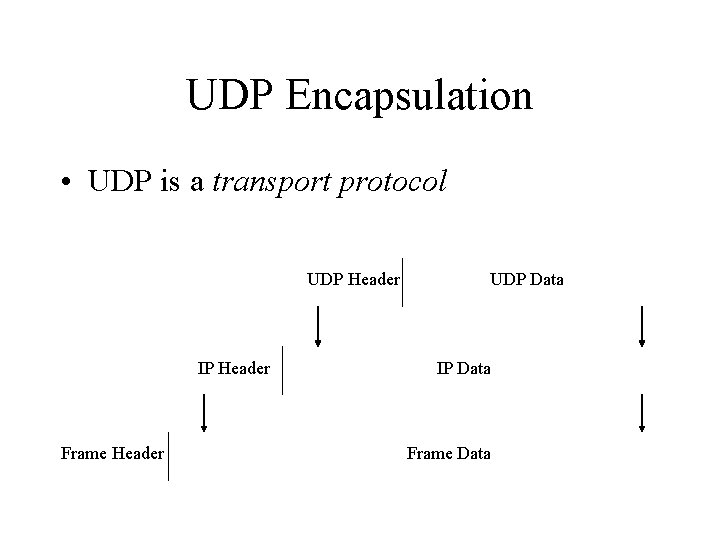
UDP Encapsulation • UDP is a transport protocol UDP Header IP Header Frame Header UDP Data IP Data Frame Data

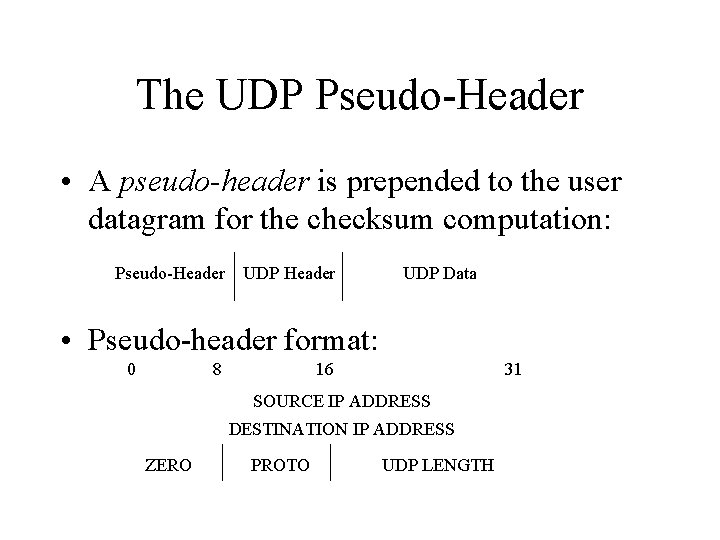
The UDP Pseudo-Header • A pseudo-header is prepended to the user datagram for the checksum computation: Pseudo-Header UDP Data • Pseudo-header format: 0 8 16 31 SOURCE IP ADDRESS DESTINATION IP ADDRESS ZERO PROTO UDP LENGTH

The UDP Pseudo-Header • The checksum in the UDP header is computed over: – The pseudo-header – UDP header (with 0’s in the checksum field) – UDP data area • The pseudo-header is not: – Transmitted with the user datagram – Reflected in the length field in the UDP header

The UDP Pseudo-Header (cont) • Purpose - to verify that the user datagram has reached its correct destination • Recall - a correct destination includes: – A specific machine – A specific port • The UDP header specifies the port • How can the IP address be checked?

Checking the IP Address with the Pseudo-Header • Checksum computed by sender covers the destination IP address in the pseudo-header • Receiver recreates pseudo-header using IP addresses from the header of the IP datagram that carried the UDP message • Receiver computes checksum and compares

UDP Layering Violation • Problems: – How is the destination IP address known so it can be added to the pseudo-header? – How is the source IP address known so it can be added to the pseudo-header? • Layering violation - UDP must interact with IP to learn the source IP address

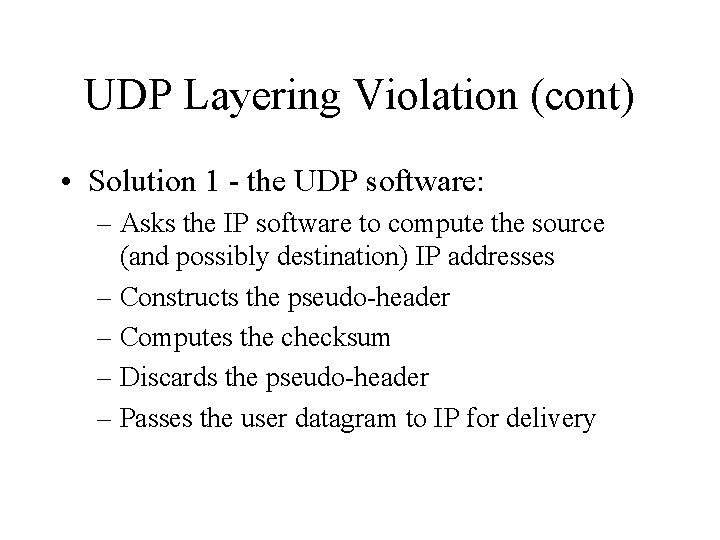
UDP Layering Violation (cont) • Solution 1 - the UDP software: – Asks the IP software to compute the source (and possibly destination) IP addresses – Constructs the pseudo-header – Computes the checksum – Discards the pseudo-header – Passes the user datagram to IP for delivery

UDP Layering Violation (cont) • Solution 2 - the UDP software: – Encapsulates a user datagram inside an IP datagram – Obtains a source (and dest) IP address from IP – Stores the IP address(es) in the datagram header – Computes the UDP checksum – Passes the datagram to the IP layer (IP will need to fill in a few fields in the IP header)

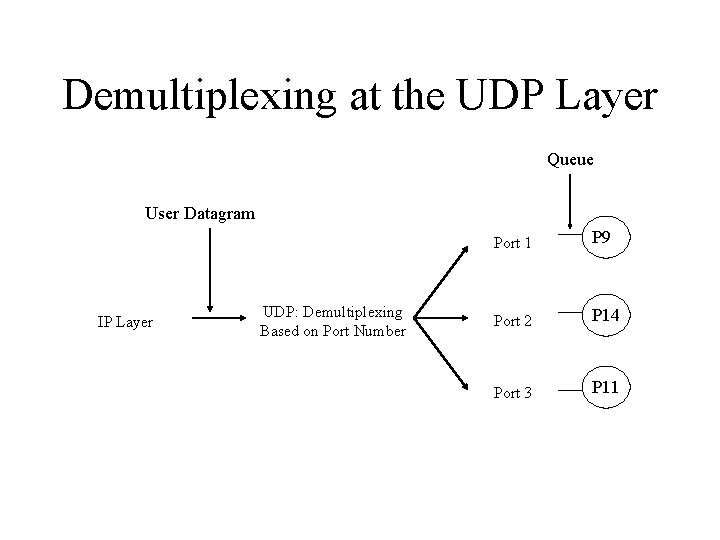
Demultiplexing at the UDP Layer Queue User Datagram IP Layer UDP: Demultiplexing Based on Port Number Port 1 P 9 Port 2 P 14 Port 3 P 11

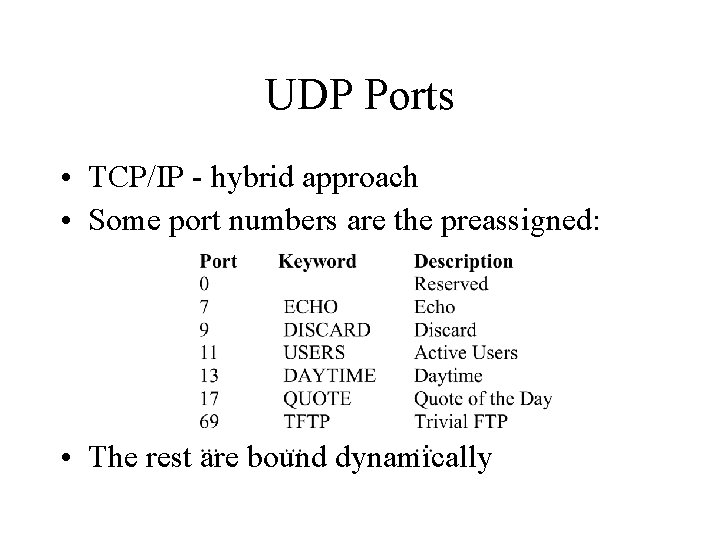
UDP Port Numbers • Universal assignment - central authority specifies which port will perform which service • Dynamic binding: – Ports are assigned to services as requested – Mechanism provided to ask a remote computer “What port is service X? ”

UDP Ports • TCP/IP - hybrid approach • Some port numbers are the preassigned: • The rest are bound dynamically

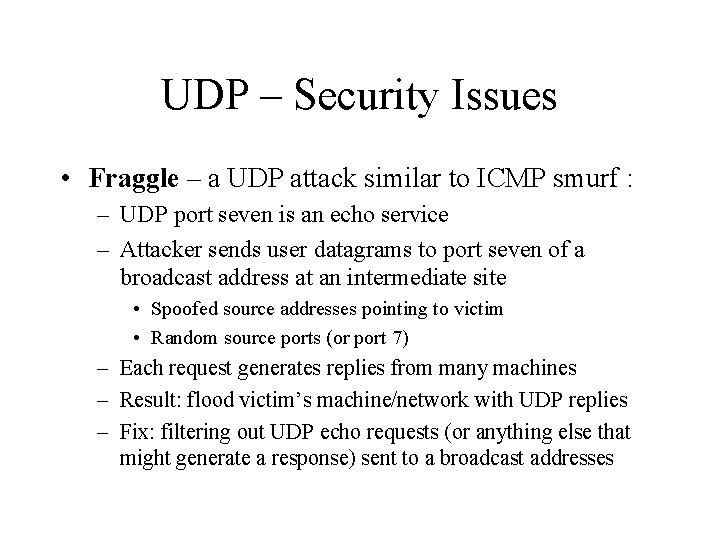
UDP – Security Issues • Fraggle – a UDP attack similar to ICMP smurf : – UDP port seven is an echo service – Attacker sends user datagrams to port seven of a broadcast address at an intermediate site • Spoofed source addresses pointing to victim • Random source ports (or port 7) – Each request generates replies from many machines – Result: flood victim’s machine/network with UDP replies – Fix: filtering out UDP echo requests (or anything else that might generate a response) sent to a broadcast addresses

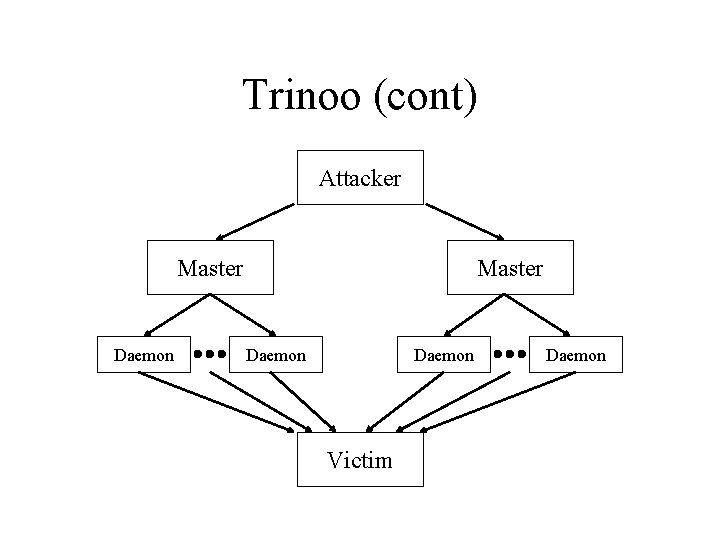
Trinoo • Distributed denial of service attack tool that enables an attacker to inundate a victim with UDP traffic from many different hosts simultaneously – Daemon program • Setup: – Search for machines and attempt to break into them using a number of different exploits – Install the trinoo daemon • Attack: – When given a victim by a master server, sends a large number of UDP packets to random ports on the victim – Master server

Trinoo (cont) • Master servers – Each master server controls a number of daemons on different hosts (commands are password protected) – An attacker normally controls a number of master servers (on different hosts) • Commands are password protected: – – Start/stop it running Test that it is alive/listening Ask for a list of all the daemons that it controls Instruct it to order its daemons to attack a given victim

Trinoo (cont) Attacker Master Daemon Victim Daemon

Trinoo (cont) • August, 1999: – Trinoo daemons running on over 200 different machines flooded a University of Minnesota host for several days • February, 2000: – Trinoo (and other distributed denial of service tools) used to attack several major e-commerce sites on the Web

Summary • UDP is a transport layer internetworking protocol – Uses IP to transport messages • Used by application programs to send messages to other application programs • Uses ports to distinguish among multiple programs executing on the destination machine